自定义认证授权过滤器
- 自定义认证授权过滤器
- 1、SpringSecurity内置认证流程
- 2、自定义Security认证过滤器
- 2.1 自定义认证过滤器
- 2.2 定义获取用户详情服务bean
- 2.3 定义SecurityConfig类
- 2.4 自定义认证流程测试
- 3、 基于JWT实现无状态认证
- 3.1 认证成功响应JWT实现
- 3.2 SpringSecurity基于Jwt实现认证小结
- 4、自定义Security授权过滤
- 4.1 授权流程说明
- 4.2 授权实现流程
- 4.3 配置自定义授权过滤器
- 5、自定义权限拒绝处理
- 5.1 自定义认证用户权限拒绝处理器
- 5.2 自定义匿名用户拒绝处理器
- 6、自定义认证授权整体流程小结
自定义认证授权过滤器
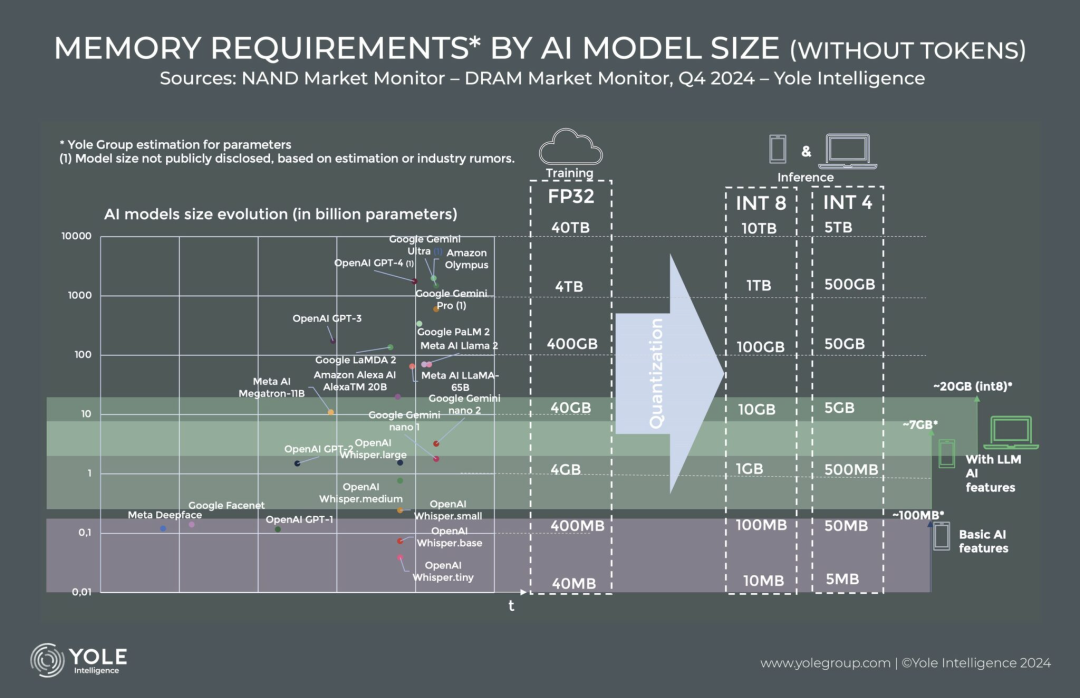
如果对 Spring Security 了解不够请看这篇。 https://blog.csdn.net/m0_62943934/article/details/134815311
需求:
SpringSecurity 内置的认证只能接收 form 表单提交的账户、密码信息。并且内部是使用 HttpServletRequest 的 getParameter 方法获取账户信息的,同时如果需要对需求进行扩展,内置的授权方式就不够看了。
@Nullable
protected String obtainUsername(HttpServletRequest request) {
return request.getParameter(this.usernameParameter);
}
但是,我们需要清楚现在的大部分项目都是基于前后端分离的架构来进行实现的。而这种情况下前段基本都会使用类似于axios这种发送异步请求,而这时账户信息就不能使用 getParameter 方法获取了。需要使用获取流数据的方式,此时就需要我们自己定义认证授权过滤器。
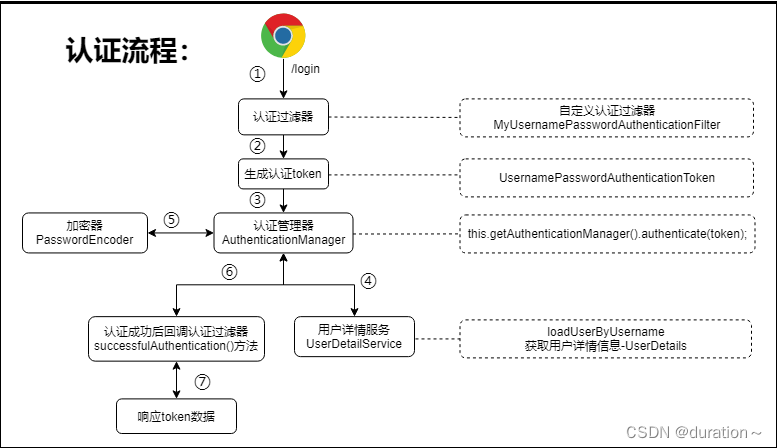
1、SpringSecurity内置认证流程
通过研究SpringSecurity内置基于form表单认证的UsernamePasswordAuthenticationFilter过滤器,我们可以仿照自定义认证过滤器:
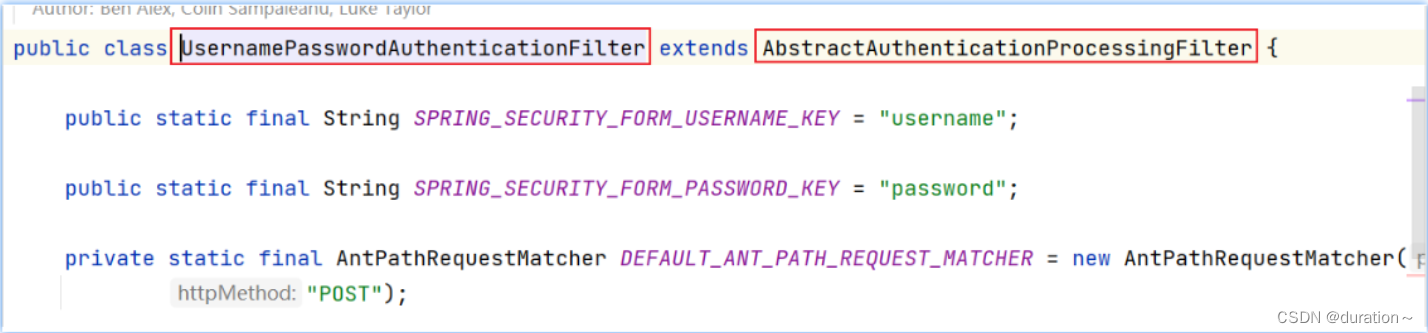
内置认证过滤器的核心流程:
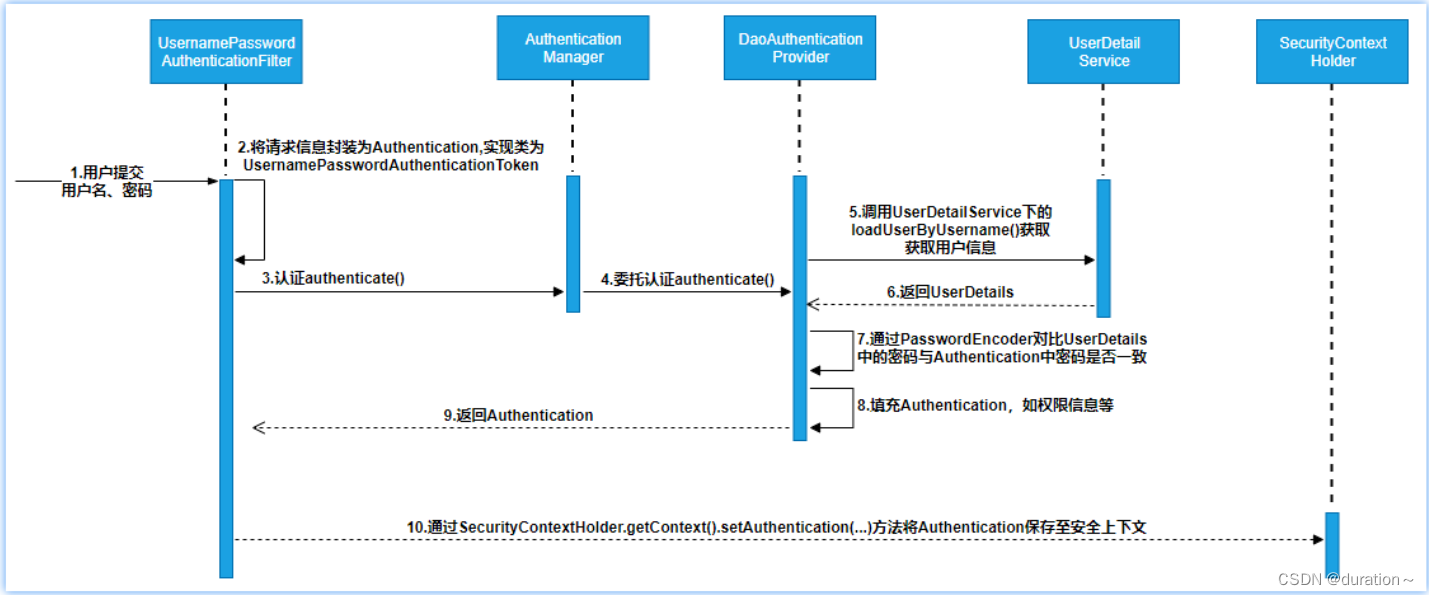
核心流程梳理如下:
- 认证过滤器(UsernamePasswordAuthentionFilter)接收 form 表单提交的账户、密码信息,并封装成UsernamePasswordAuthenticationToken认证凭对象;
- 认证过滤器调用认证管理器AuthenticationManager进行认证处理;
- 认证管理器通过调用用户详情服务获取用户详情UserDetails;
- 认证管理器通过密码匹配器PasswordEncoder进行匹配,如果密码一致,则将用户相关的权限信息一并封装到Authentication认证对象中;
- 认证过滤器将Authentication认证过滤器放到认证上下文,方便请求从上下文获取认证信息;
2、自定义Security认证过滤器
SpringSecurity 内置的认证过滤器是基于post请求且为form表单的方式获取认证数据的,那如何接收前端Json异步提交的数据据实现认证操作呢?
显然,我们可仿照UsernamePasswordAuthentionFilter类自定义一个过滤器并实现认证过滤逻辑;
2.1 自定义认证过滤器
UsernamePasswordAuthentionFilter过滤器继承了模板认证过滤器AbstractAuthenticationProcessingFilter抽象类,我们也可仿照实现:
package com.shen.security.security_test.config;
import com.fasterxml.jackson.databind.ObjectMapper;
import org.springframework.http.MediaType;
import org.springframework.security.authentication.AuthenticationServiceException;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.web.authentication.AbstractAuthenticationProcessingFilter;
import org.springframework.security.web.util.matcher.RequestMatcher;
import javax.servlet.FilterChain;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
import java.util.Collection;
import java.util.HashMap;
import java.util.Map;
/**
* @author shenyang
* @version 1.0
* @Date 2024/3/11 16:29
* 认证过滤器
*
*/
public class MyUserNamePasswordAuthenticationFilter extends AbstractAuthenticationProcessingFilter {
public static final String USERNAME_KEY = "username";
public static final String PASSWORD_KEY = "password";
/**
* 自定义构造器,传入登录认证的url地址
*
* @param defaultFilterProcessesUrl
*/
public MyUserNamePasswordAuthenticationFilter(String defaultFilterProcessesUrl) {
super(defaultFilterProcessesUrl);
}
/**
* 尝试去认证的方法
*
* @param request
* @param response
* @return
* @throws AuthenticationException
* @throws IOException
* @throws ServletException
*/
@Override
public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException, IOException, ServletException {
//请求必须是post请求 并且请求类型必须是json
if (!request.getMethod().equalsIgnoreCase("POST")//忽略大小写
&
! MediaType.APPLICATION_JSON_VALUE.equalsIgnoreCase(request.getContentType())) {
throw new AuthenticationServiceException("Authentication method not supported: " + request.getMethod());
}
//获取post请求ajax的数据流 并且将其数据流中的数据反序列化成Map
HashMap<String,String> userInfo = new ObjectMapper().readValue(request.getInputStream(), HashMap.class);
String username = userInfo.get(USERNAME_KEY);
username = (username != null) ? username : "";
username = username.trim();
String password = userInfo.get(PASSWORD_KEY);
password = password != null ? password : "";
//组装认证的票据对象 将用户名和密码信息封装到认证票据对象下
UsernamePasswordAuthenticationToken authRequest = new UsernamePasswordAuthenticationToken(username, password);
// Allow subclasses to set the "details" property
//setDetails(request, authRequest);
//调用认证管理器认证指定的票据对象 交给认证管理器认证票据对象
return this.getAuthenticationManager().authenticate(authRequest);
}
public MyUserNamePasswordAuthenticationFilter(RequestMatcher requiresAuthenticationRequestMatcher) {
super(requiresAuthenticationRequestMatcher);
}
/**
* 认证成功后执行的方法
* @param request
* @param response
* @param chain 过滤器链
* @param authResult 认证对象信息
* @throws IOException
* @throws ServletException
*/
@Override
protected void successfulAuthentication(HttpServletRequest request, HttpServletResponse response, FilterChain chain, Authentication authResult) throws IOException, ServletException {
User principal = (User) authResult.getPrincipal();
String username = principal.getUsername();
Collection<GrantedAuthority> authorities = principal.getAuthorities();
String password = principal.getPassword();
//响应数据格式json
response.setContentType(MediaType.APPLICATION_JSON_VALUE);
//编码格式
response.setCharacterEncoding("UTF-8");
Map<String,String> infos = new HashMap<>();
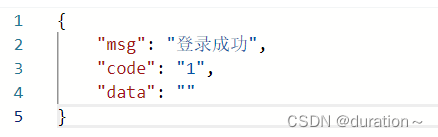
infos.put("msg","登录成功");
infos.put("data","");
infos.put("code","1");
//响应
response.getWriter().write(new ObjectMapper().writeValueAsString(infos));
}
@Override
protected void unsuccessfulAuthentication(HttpServletRequest request, HttpServletResponse response, AuthenticationException failed) throws IOException, ServletException {
//响应数据格式json
response.setContentType(MediaType.APPLICATION_JSON_VALUE);
//编码格式
request.setCharacterEncoding("UTF-8");
Map<String,String> infos = new HashMap<>();
infos.put("msg","登录失败");
infos.put("data","");
infos.put("code","1");
//响应
response.getWriter().write(new ObjectMapper().writeValueAsString(infos));
}
}
2.2 定义获取用户详情服务bean
package com.shen.service;
import com.shen.entity.TbUser;
import com.shen.mapper.TbUserMapper;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.AuthorityUtils;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
import java.util.List;
/**
* @author by shen
* @Date 2024/1/23
* @Description
*/
@Service("userDetailsService")
public class MyUserDetailServiceImpl implements UserDetailsService {
@Autowired
private TbUserMapper tbUserMapper;
/**
* 使用security当用户认证时,会自动将用户的名称注入到该方法中
* 然后我们可以自己写逻辑取加载用户的信息,然后组装成UserDetails认证对象
* @param userName
* @return 用户的基础信息,包含密码和权限集合,security底层会自动比对前端输入的明文密码
* @throws UsernameNotFoundException
*/
@Override
public UserDetails loadUserByUsername(String userName) throws UsernameNotFoundException {
//1.根据用户名称获取用户的账户信息
TbUser dbUser=tbUserMapper.findUserInfoByName(userName);
//判断该用户是否存在
if (dbUser==null) {
throw new UsernameNotFoundException("用户名输入错误!");
}
//2.组装UserDetails对象
//获取当前用户对应的权限集合(自动将以逗号间隔的权限字符串封装到权限集合中)
List<GrantedAuthority> list = AuthorityUtils.commaSeparatedStringToAuthorityList(dbUser.getRoles());
/*
参数1:账户
参数2:密码
参数3:权限集合
*/
User user = new User(dbUser.getUsername(), dbUser.getPassword(), list);
return user;
}
}
2.3 定义SecurityConfig类
配置默认认证过滤器,保证自定义的认证过滤器要在默认的认证过滤器之前;
package com.shen.security.config;
import com.shen.security.filter.MyUserNamePasswordAuthenticationFilter;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.method.configuration.EnableGlobalMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.authentication.UsernamePasswordAuthenticationFilter;
@Configuration
@EnableWebSecurity//开启web安全设置生效
//开启SpringSecurity相关注解支持
@EnableGlobalMethodSecurity(prePostEnabled = true)
public class SecurityConfig extends WebSecurityConfigurerAdapter {
/**
* 配置授权策略
* @param http
* @throws Exception
*/
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf().disable();//禁用跨站请求伪造
http.authorizeRequests()//对资源进行认证处理
.antMatchers("/authentication/form").permitAll()//登录路径无需拦截
.anyRequest().authenticated(); //除了上述资源外,其它资源,只有 认证通过后,才能有权访问
http
//坑-过滤器要添加在默认过滤器之前,否则,登录失效
.addFilterBefore(myUserNamePasswordAuthenticationFilter(), UsernamePasswordAuthenticationFilter.class);
}
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
@Bean
public MyUserNamePasswordAuthenticationFilter myUserNamePasswordAuthenticationFilter() throws Exception {
构造认证过滤器对象,并设置默认登录路径
MyUserNamePasswordAuthenticationFilter myUserNamePasswordAuthenticationFilter =
new MyUserNamePasswordAuthenticationFilter("/authentication/form");
myUserNamePasswordAuthenticationFilter.setAuthenticationManager(authenticationManagerBean());
return myUserNamePasswordAuthenticationFilter;
}
}
2.4 自定义认证流程测试
3、 基于JWT实现无状态认证
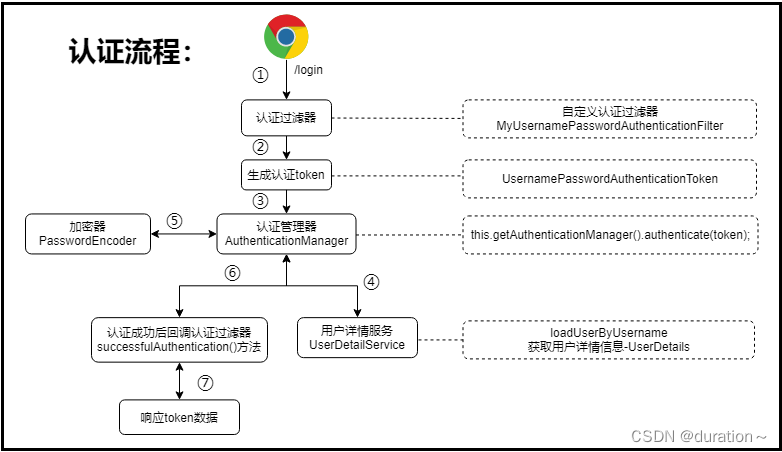
JWT是无状态的,所以在服务器端无需存储和维护认证信息,这样会大大减轻服务器的压力,所以我们可在自定义的认证过滤器认证成功后通过successfulAuthentication方法向前端颁发token认证字符串;
3.1 认证成功响应JWT实现
测试工程导入Jwt工具类,集成流程如下:
/**
* 认证工程处理方法
* @param request
* @param response
* @param chain
* @param authResult
* @throws IOException
* @throws ServletException
*/
@Override
protected void successfulAuthentication(HttpServletRequest request,
HttpServletResponse response,
FilterChain chain,
Authentication authResult) throws IOException, ServletException {
//认证主体信息,此时以填充用户权限信息
UserDetails principal = (UserDetails) authResult.getPrincipal();
//组装响应前端的信息
String username = principal.getUsername();
Collection<? extends GrantedAuthority> authorities = principal.getAuthorities();
//构建JwtToken 加入权限信息是为了将来访问时,jwt解析获取当前用户对应的权限,做授权的过滤
//权限字符串格式:[P5, ROLE_ADMIN]
String token = JwtTokenUtil.createToken(username, authorities.toString());
HashMap<String, String> info = new HashMap<>();
info.put("name",username);
info.put("token",token);
//设置响应格式
response.setContentType(MediaType.APPLICATION_JSON_VALUE);
//内容编码格式
response.setCharacterEncoding("utf-8");
response.getWriter().write(new ObjectMapper().writeValueAsString(info));
}
测试获取认证Token
略
3.2 SpringSecurity基于Jwt实现认证小结
4、自定义Security授权过滤
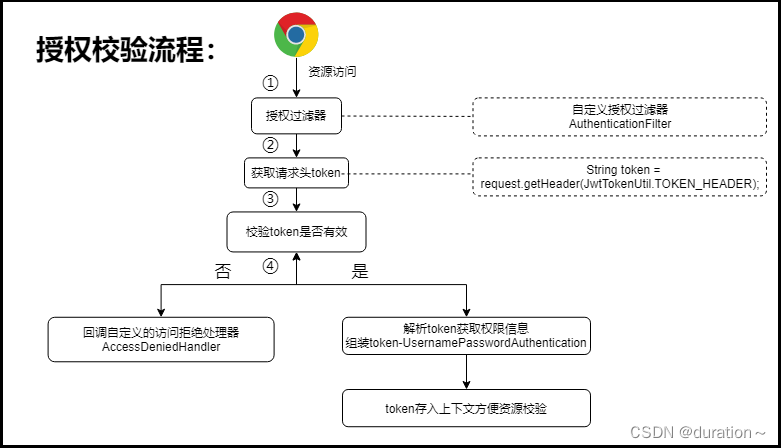
上一小结认证成功后向请求方响应了token信息,那么请求方访问其它系统资源时,就需要带着这个token到后台,后台需要一个授权过滤器获取token信息,并解析用户权限信息,将信息封装到UsernamePasswordAuthentionToken对象存入安全上下文,方便请求时安全过滤处理;
4.1 授权流程说明
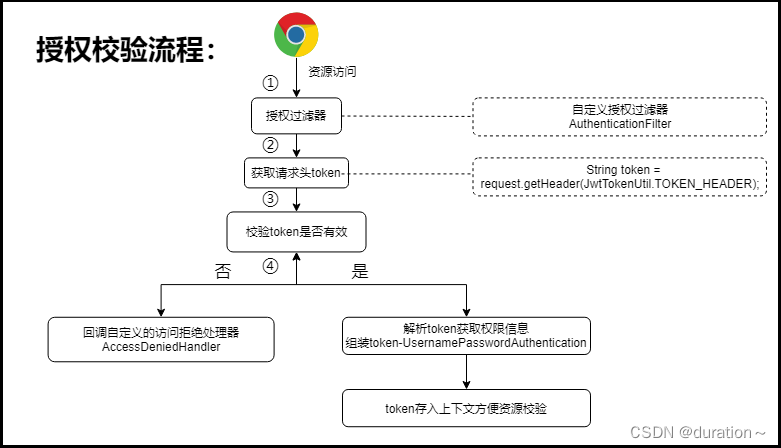
4.2 授权实现流程
定义授权过滤器:
package com.shen.security.config;
import com.google.gson.Gson;
import com.shen.security.utils.JwtTokenUtil;
import org.springframework.http.MediaType;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.authority.AuthorityUtils;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.web.filter.OncePerRequestFilter;
import javax.servlet.FilterChain;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
import java.util.HashMap;
/**
* @author by shen
* @Date 2024/1/23
* @Description 权限认证filter
*/
public class AuthenticationFilter extends OncePerRequestFilter {
@Override
protected void doFilterInternal(HttpServletRequest request,
HttpServletResponse response,
FilterChain filterChain) throws ServletException, IOException {
//1.获取http请求头中携带的jwt票据字符串(注意:如果用户尚未认证,则jwt票据字符串不存在)
String jwtToken = request.getHeader(JwtTokenUtil.TOKEN_HEADER);
//2.判断请求中的票据是否存在
if (StringUtils.isBlank(jwtToken)) {
//如果票据为空,可能用户准备取认证,所以不做拦截,但是此时UsernamePasswordAuthenticationToken对象未生成,那么即使放行本次请求
//后续的过滤器链中也会校验认证票据对象
filterChain.doFilter(request,response);
return;
}
//3.校验票据
Claims claims = JwtTokenUtil.checkJWT(jwtToken);
//票据失效
if (claims==null) {
//票据失效则提示前端票据已经失效,需要重新认证
response.setContentType(MediaType.APPLICATION_JSON_VALUE);
response.setContentType("utf-8");
response.getWriter().write("jwt token failure!!");
return;
}
//4.从合法的票据中获取用户名和权限信息
//用户名
String username = JwtTokenUtil.getUsername(jwtToken);
//权限信息 [P5, ROLE_ADMIN]
String roles = JwtTokenUtil.getUserRole(jwtToken);
//将数组格式的字符串转化成权限对象集合
String comStr = StringUtils.strip(roles, "[]");
List<GrantedAuthority> authorityList = AuthorityUtils.commaSeparatedStringToAuthorityList(comStr);
//5.组装认证成功的票据对象(认证成功时,密码位置null)
UsernamePasswordAuthenticationToken token = new UsernamePasswordAuthenticationToken(username, null, authorityList);
//6.将认证成功的票据对象保存到安全上下文中,方便后续的过滤器直接获取权限信息
SecurityContextHolder.getContext().setAuthentication(token);
//7.发行过滤器
filterChain.doFilter(request,response);
}
}
4.3 配置自定义授权过滤器
/**
* 给访问的资源配置权限过滤
* @param http
* @throws Exception
*/
@Override
protected void configure(HttpSecurity http) throws Exception {
http.csrf().disable();//禁用跨站请求伪造
http.authorizeRequests()//对资源进行认证处理
.antMatchers("/myLogin").permitAll()//登录路径无需拦截
.anyRequest().authenticated(); //除了上述资源外,其它资源,只有 认证通过后,才能有权访问
//添加自定义的认证过滤器:UsernamePasswordAuthenticationFilter是默认的登录认证过滤器,而我们重写了该过滤器,所以访问时,应该先走我们
//自定义的过滤器
http.addFilterBefore(myUsernamePasswordAuthenticationFilter(), UsernamePasswordAuthenticationFilter.class);
//配置授权过滤器,过滤一切资源
http.addFilterBefore( authenticationFilter(),MyUsernamePasswordAuthenticationFilter.class);
}
/**
* 自定义授权过滤器
* 过滤一切被访问的资源
* @return
*/
@Bean
public AuthenticationFilter authenticationFilter(){
AuthenticationFilter filter = new AuthenticationFilter();
return filter;
}
访问测试:
略
5、自定义权限拒绝处理
上一小结当用户未认证访问资源或者认证成功后访问没有权限的资源时,响应给前端的信息不友好,我们可通过自定义权限访问拒绝的处理器来友好提醒用户;
5.1 自定义认证用户权限拒绝处理器
通过实现AccessDeniedHandler接口实现:
/**
* 自定义登录认证策略配置授权策略 -1
* @param http
* @throws Exception
*/
@Override
protected void configure(HttpSecurity http) throws Exception {
//......
http.exceptionHandling()
.accessDeniedHandler(new AccessDeniedHandler() {
@Override
public void handle(HttpServletRequest request,
HttpServletResponse response,
AccessDeniedException e) throws IOException, ServletException {
//认证用户访问资源时权限拒绝处理策略
response.getWriter().write("no permission......reject....");
}
});
}
效果:

5.2 自定义匿名用户拒绝处理器
同样通过实现AuthenticationEntryPoint接口实现:
/**
* 自定义登录认证策略配置授权策略 -1
* @param http
* @throws Exception
*/
@Override
protected void configure(HttpSecurity http) throws Exception {
//......
http.exceptionHandling()
.accessDeniedHandler(new AccessDeniedHandler() {
@Override
public void handle(HttpServletRequest request,
HttpServletResponse response,
AccessDeniedException e) throws IOException, ServletException {
//认证用户访问资源时权限拒绝处理策略
response.getWriter().write("no permission......reject....");
}
})
.authenticationEntryPoint(new AuthenticationEntryPoint(){
@Override
public void commence(HttpServletRequest request,
HttpServletResponse response,
AuthenticationException authException) throws IOException, ServletException {
response.setContentType(MediaType.APPLICATION_JSON_VALUE);
response.setCharacterEncoding("UTF-8");
response.getWriter().write("匿名用户无权访问");
});
}
}
6、自定义认证授权整体流程小结