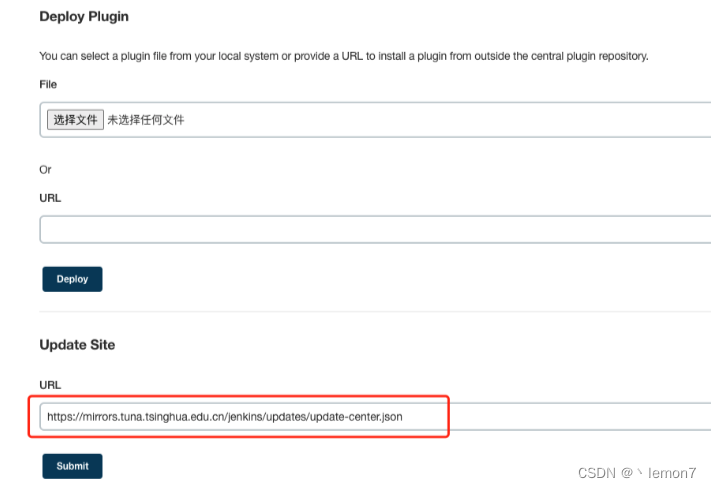
一、[HDCTF2019]bbbbbbrsa
题目所给的信息我汇总到以下代码中
from base64 import b64encode as b32encode
from gmpy2 import invert,gcd,iroot
from Crypto.Util.number import *
from binascii import a2b_hex,b2a_hex
import random
flag = "******************************"
nbit = 128
p = getPrime(nbit)
q = getPrime(nbit)
n = p*q
print p
print n
phi = (p-1)*(q-1)
e = random.randint(50000,70000)
while True:
if gcd(e,phi) == 1:
break;
else:
e -= 1;
c = pow(int(b2a_hex(flag),16),e,n)
print b32encode(str(c))[::-1]
# 2373740699529364991763589324200093466206785561836101840381622237225512234632
p = 177077389675257695042507998165006460849
n = 37421829509887796274897162249367329400988647145613325367337968063341372726061
c = ==gMzYDNzIjMxUTNyIzNzIjMyYTM4MDM0gTMwEjNzgTM2UTN4cjNwIjN2QzM5ADMwIDNyMTO4UzM2cTM5kDN2MTOyUTO5YDM0czM3MjM首先,我们先将c倒序,然后再用base64解码,注意看头部不要被迷惑住了

接下来就是解RSA,知道n,p,且e的范围也给出来了就只用爆破就行
from base64 import b64encode as b32encode
from gmpy2 import invert,gcd,iroot
from Crypto.Util.number import *
from binascii import a2b_hex,b2a_hex
import random
s='==gMzYDNzIjMxUTNyIzNzIjMyYTM4MDM0gTMwEjNzgTM2UTN4cjNwIjN2QzM5ADMwIDNyMTO4UzM2cTM5kDN2MTOyUTO5YDM0czM3MjM'
c=2373740699529364991763589324200093466206785561836101840381622237225512234632
p = 177077389675257695042507998165006460849
n = 37421829509887796274897162249367329400988647145613325367337968063341372726061
q=n//p
for e in range(50000,70000):
d=inverse(e, (p-1)*(q-1))
m=pow(c,d,n)
m=long_to_bytes(m)
if b'flag' in m:
print(m)
break答案:flag{rs4_1s_s1mpl3!#}
二、Keyboard
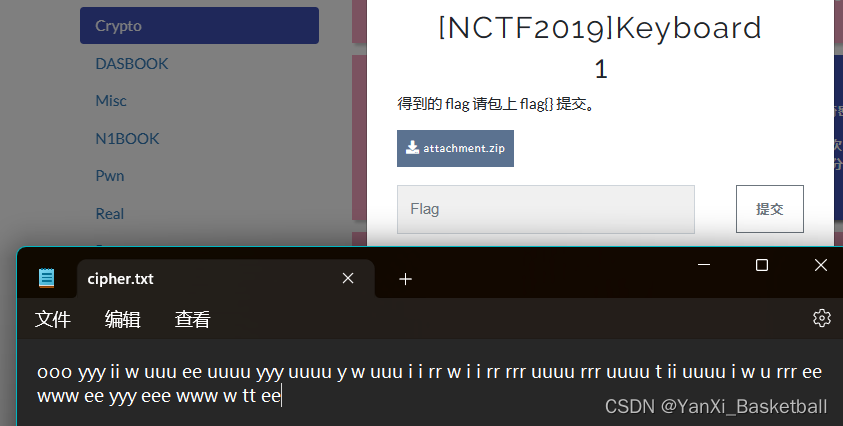
这个题目很有想象力,看到wp的第一步,想不到第二步。参考文章NCTF2019/BUUCTF-Keyboard - 「配枪朱丽叶。」 (hatenablog.com)
密文中的字母只由“wertyui”组成。在手机输入26键中,这些字母头上都有一个数字
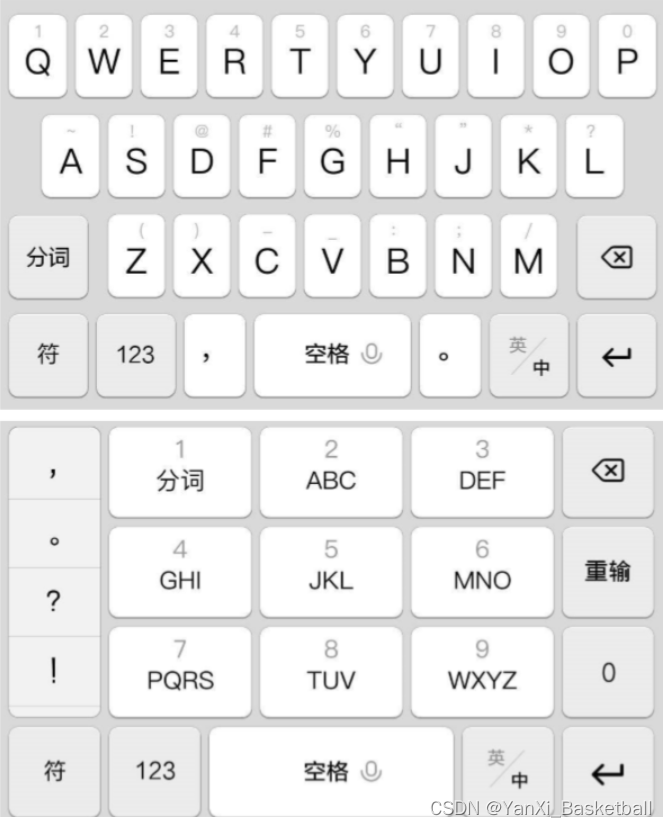
就拿‘ooo'来举例子分析,’o'代表数字9,就表示九宫格中的第九个,出现了3次,就代表‘wxyz'中的第3个,所以‘ooo'表示’y‘。其它的也是这样分析。
文章中的代码如下:
strr = "ooo yyy ii w uuu ee uuuu yyy uuuu y w uuu i i rr w i i rr rrr uuuu rrr uuuu t ii uuuu i w u rrr ee www ee yyy eee www w tt ee".split()
all = {'none1':'','none2':'','w':'abc','e':'def','r':'ghi','t':'jkl','y':'mno','u':'pors','i':'tuv','o':'wxyz'}
for i in strr:
print(all[i[0]][len(i)-1],end="")答案:flag{youaresosmartthatthisisjustapieceofcake}
三、RSA4
N = 331310324212000030020214312244232222400142410423413104441140203003243002104333214202031202212403400220031202142322434104143104244241214204444443323000244130122022422310201104411044030113302323014101331214303223312402430402404413033243132101010422240133122211400434023222214231402403403200012221023341333340042343122302113410210110221233241303024431330001303404020104442443120130000334110042432010203401440404010003442001223042211442001413004
c = 310020004234033304244200421414413320341301002123030311202340222410301423440312412440240244110200112141140201224032402232131204213012303204422003300004011434102141321223311243242010014140422411342304322201241112402132203101131221223004022003120002110230023341143201404311340311134230140231412201333333142402423134333211302102413111111424430032440123340034044314223400401224111323000242234420441240411021023100222003123214343030122032301042243
N = 302240000040421410144422133334143140011011044322223144412002220243001141141114123223331331304421113021231204322233120121444434210041232214144413244434424302311222143224402302432102242132244032010020113224011121043232143221203424243134044314022212024343100042342002432331144300214212414033414120004344211330224020301223033334324244031204240122301242232011303211220044222411134403012132420311110302442344021122101224411230002203344140143044114
c = 112200203404013430330214124004404423210041321043000303233141423344144222343401042200334033203124030011440014210112103234440312134032123400444344144233020130110134042102220302002413321102022414130443041144240310121020100310104334204234412411424420321211112232031121330310333414423433343322024400121200333330432223421433344122023012440013041401423202210124024431040013414313121123433424113113414422043330422002314144111134142044333404112240344
N = 332200324410041111434222123043121331442103233332422341041340412034230003314420311333101344231212130200312041044324431141033004333110021013020140020011222012300020041342040004002220210223122111314112124333211132230332124022423141214031303144444134403024420111423244424030030003340213032121303213343020401304243330001314023030121034113334404440421242240113103203013341231330004332040302440011324004130324034323430143102401440130242321424020323
c = 10013444120141130322433204124002242224332334011124210012440241402342100410331131441303242011002101323040403311120421304422222200324402244243322422444414043342130111111330022213203030324422101133032212042042243101434342203204121042113212104212423330331134311311114143200011240002111312122234340003403312040401043021433112031334324322123304112340014030132021432101130211241134422413442312013042141212003102211300321404043012124332013240431242首先看一下数字特征都是0,1,2,3,4,很可能是5进制,把这一点给看出来后面才好做。对于这种组数少的,我们可以尝试一下中国剩余定理(代码从网上找的)
from gmpy2 import *
def pollard_p_1(n,B):
"""
Factor n = p*q (p is B-smooth)
:param n:
:param B:
:return: d = p
"""
# step 1
a = 2
# step 2
false_range = int(0.8*B)
for j in range(2,false_range):
# We assume n had a factor > 0.8B,so we can do less gcd
a = pow(a, j, n)
d = 0
for j in range(false_range,B+1):
# step 3
a = pow(a, j, n)
# step 4
d = gcd(a-1, n)
# step 5
if 1<d<n:
return d
from gmpy2 import *
# 求两个数的最大公约数gcd函数
def gcd(a,b):
if b == 0:
return a
else :
return gcd(b,a % b)
#判断一个列表任意两个数是否两两互质
def compare(list):
for i in range(0,len(list)):
flag = 1
for j in range(i+1,len(list)):
if gcd(list[i],list[j]) != 1:
print('不能直接使用中国剩余定理!')
exit()
#如果满足条件,就会继续执行,否则退出程序
# 求出输入的m1,m2,..,mk 的乘积m
def product_m(list):
m = 1
for i in list:
m *= i
return m
# 求M1,M2,..,MK 的值 Mj = m / mj 并返回一个名为shang的列表
def get_divsion(list,m):
div = []
for i in list:
div.append(m // i)
return div
# 求一个数a 的逆 再模m 的值 这个函数返回的是一个值不是列表
def get_inverse(a, m):
if gcd(a, m) != 1:
return None
u1, u2, u3 = 1, 0, a
v1, v2, v3 = 0, 1, m
while v3 != 0:
q = u3 // v3
v1, v2, v3, u1, u2, u3 = (u1 - q * v1), (u2 - q * v2), (u3 - q * v3), v1, v2, v3
return u1 % m
# 求Xj 算法为:Xj = (M * M_INVERSE * a) % mj
def get_x(M:int ,M_inverse:int ,a :int,m:int):
product_x = (M * M_inverse * a) % m
return product_x
# 算出最终答案X = X1+X2+...Xk 模数 余数
def get_solution(list_m, list_a):
m = product_m(list_m)
list_M = get_divsion(list_m, m)
list_M_inverse = []
list_X = []
total = 0
for i in range(0,len(list_M)):
list_M_inverse.append(get_inverse(list_M[i], list_m[i]))
for i in range(len(list_M)):
print(type(list_M[i]),type(list_M_inverse[i]),type(list_a[i]),type(m))
list_X.append(get_x(list_M[i],list_M_inverse[i],list_a[i],m))
for x in list_X:
total += x
return total % m
n1 = int(str(331310324212000030020214312244232222400142410423413104441140203003243002104333214202031202212403400220031202142322434104143104244241214204444443323000244130122022422310201104411044030113302323014101331214303223312402430402404413033243132101010422240133122211400434023222214231402403403200012221023341333340042343122302113410210110221233241303024431330001303404020104442443120130000334110042432010203401440404010003442001223042211442001413004),5)
c1 = int(str(310020004234033304244200421414413320341301002123030311202340222410301423440312412440240244110200112141140201224032402232131204213012303204422003300004011434102141321223311243242010014140422411342304322201241112402132203101131221223004022003120002110230023341143201404311340311134230140231412201333333142402423134333211302102413111111424430032440123340034044314223400401224111323000242234420441240411021023100222003123214343030122032301042243),5)
n2 = int(str(302240000040421410144422133334143140011011044322223144412002220243001141141114123223331331304421113021231204322233120121444434210041232214144413244434424302311222143224402302432102242132244032010020113224011121043232143221203424243134044314022212024343100042342002432331144300214212414033414120004344211330224020301223033334324244031204240122301242232011303211220044222411134403012132420311110302442344021122101224411230002203344140143044114),5)
c2 = int(str(112200203404013430330214124004404423210041321043000303233141423344144222343401042200334033203124030011440014210112103234440312134032123400444344144233020130110134042102220302002413321102022414130443041144240310121020100310104334204234412411424420321211112232031121330310333414423433343322024400121200333330432223421433344122023012440013041401423202210124024431040013414313121123433424113113414422043330422002314144111134142044333404112240344),5)
n3 = int(str(332200324410041111434222123043121331442103233332422341041340412034230003314420311333101344231212130200312041044324431141033004333110021013020140020011222012300020041342040004002220210223122111314112124333211132230332124022423141214031303144444134403024420111423244424030030003340213032121303213343020401304243330001314023030121034113334404440421242240113103203013341231330004332040302440011324004130324034323430143102401440130242321424020323),5)
c3 = int(str(10013444120141130322433204124002242224332334011124210012440241402342100410331131441303242011002101323040403311120421304422222200324402244243322422444414043342130111111330022213203030324422101133032212042042243101434342203204121042113212104212423330331134311311114143200011240002111312122234340003403312040401043021433112031334324322123304112340014030132021432101130211241134422413442312013042141212003102211300321404043012124332013240431242),5)
listn=[n1,n2,n3]#,n5,n6,n7,n8,n9,n10,n11,n12,n13,n14,n15,n16,n17,n18,n19,n20]
listc=[c1,c2,c3]#,c5,c6,c7,c8,c9,c10,c11,c12,c13,c14,c15,c16,c17,c18,c19,c20]
m3=get_solution(listn, listc)
print(m3)接下来就是解决e,这种情况下e比较小,直接爆破。
from base64 import b64encode as b32encode
from gmpy2 import invert,gcd,iroot
from Crypto.Util.number import *
from binascii import a2b_hex,b2a_hex
import random
m=259362307225540148883586283191025214233097658309244310540770399135748418469298031742173624766441014006294782333
for e in range(1,10):
m1=iroot(m,e)[0]
m1=long2str(m1)
if b'flag' or b'CTF' in m1:
print(m1)
break答案:noxCTF{D4mn_y0u_h4s74d_wh47_4_b100dy_b4s74rd!}
四、[MRCTF2020]天干地支+甲子

根据转换表,转换成相应的数字
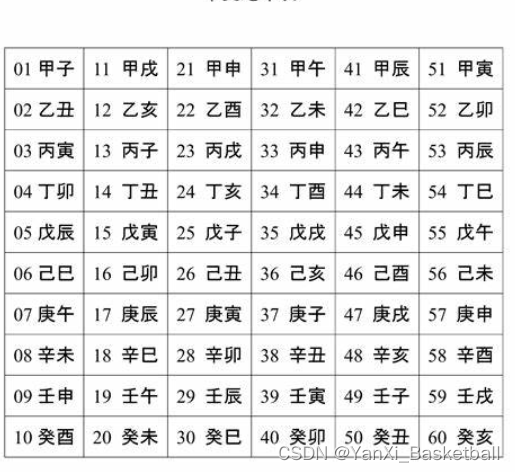
根据提示+甲子,甲子除了代表1外还可以代表60,通过数字转换成ASCII码,两种都试一下
a=[11,51,51,40,46,51,38]
for i in a:
print(chr(i+60),end='')答案:flag{Goodjob}