强网先锋
SpeedUp
要求2的27次方的阶乘的逐位之和
在A244060 - OEIS

然后我们将4495662081进行sha256加密
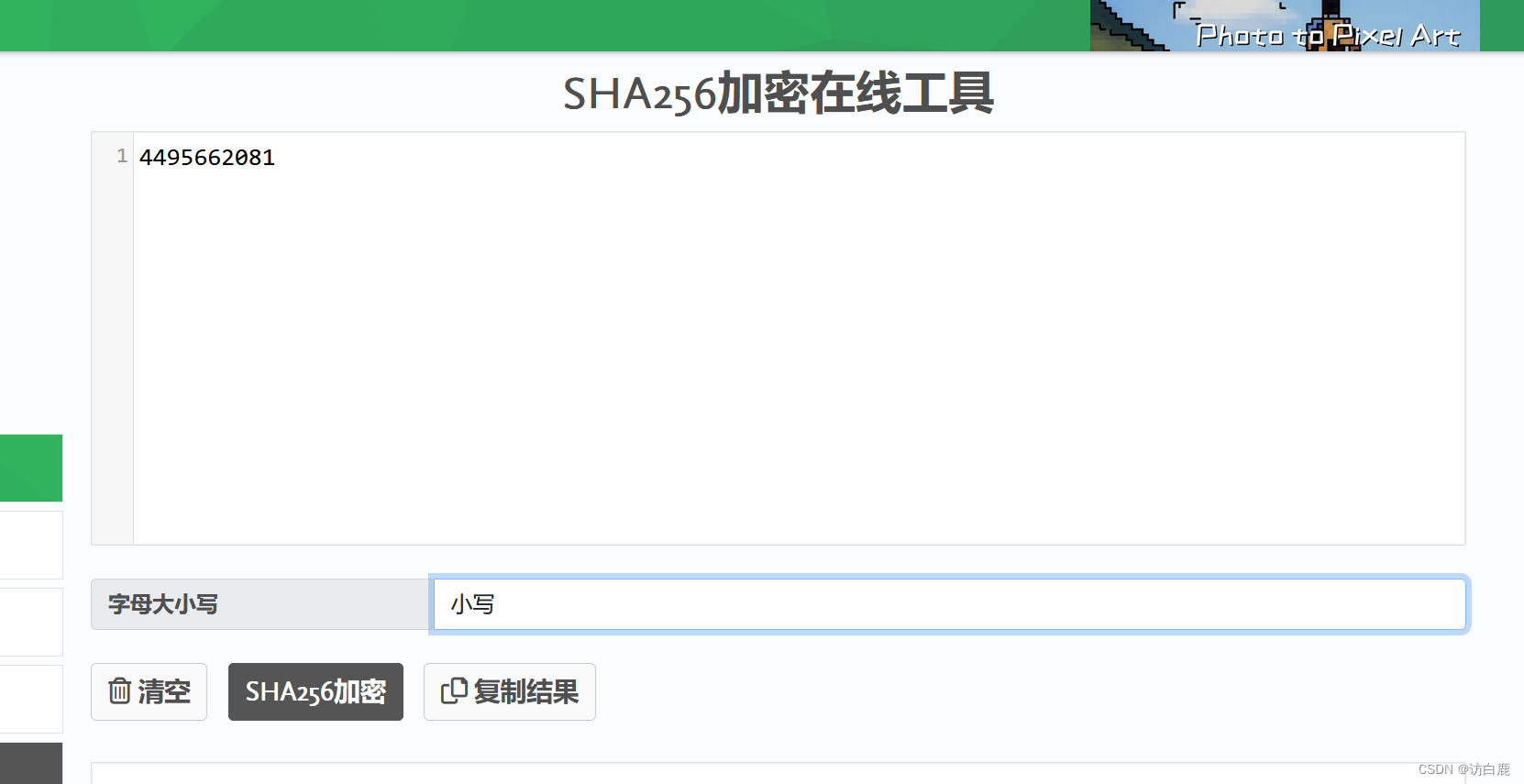
就得到了flag
flag{bbdee5c548fddfc76617c562952a3a3b03d423985c095521a8661d248fad3797}
MISC
easyfuzz
通过尝试输入字符串判断该程序对输入字符的验证规则为9位字符,并且只要满足输入正确字符使最后返回值全部为111111111即可得flag
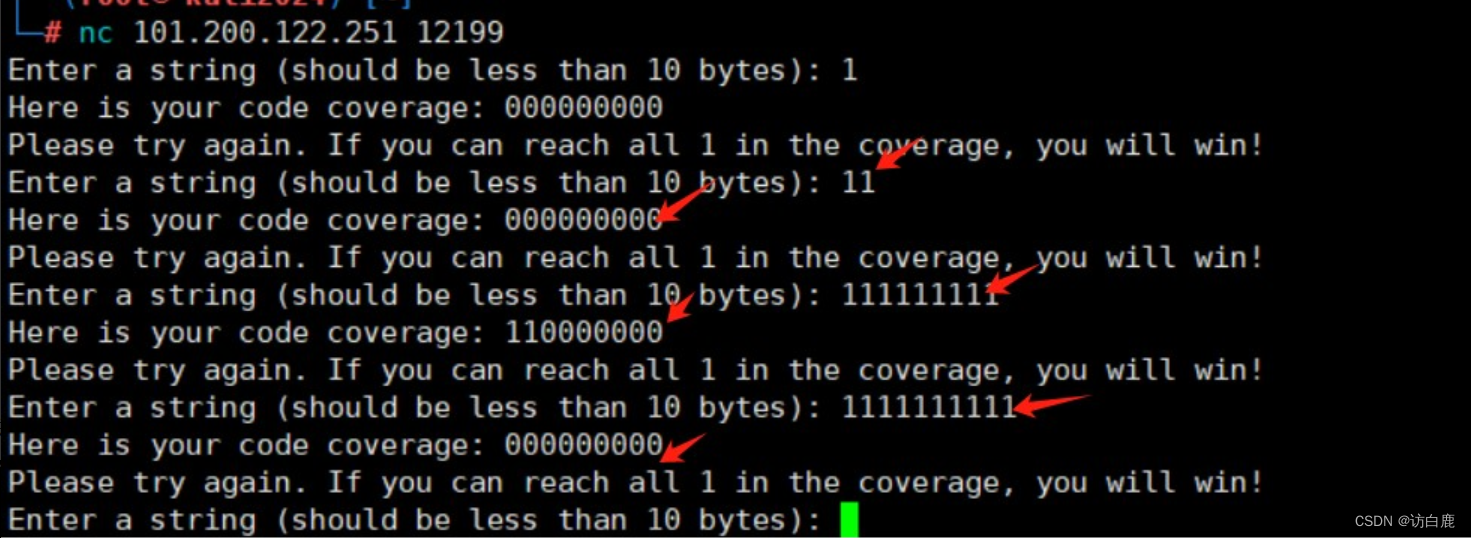
发现前两位字符可以为任何字符,都满足110000000,由此可以对后七位字符进行爆破
逐位爆破得到最后一位为字符串"d"
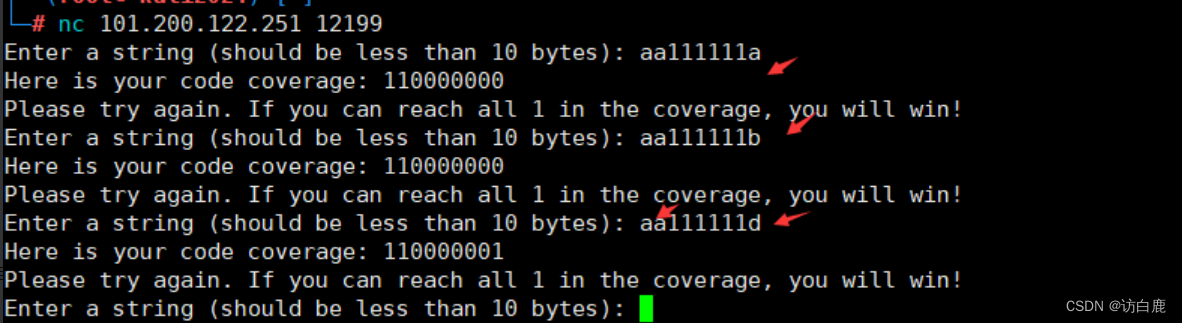
这里还是师傅的脚本,当字符串长度为9位并输入时,将回显不为“Here is your code coverage: 110000000”的结果打印
from pwn import *
from string import printable
conn = remote('101.200.122.251', 12199)
non_matching_strings = []
for i in range(9):
for char in printable:
payload = 'a'*i + char + 'a'*(8-i)
print(conn.recvuntil(b'Enter a string (should be less than 10 bytes):'))
conn.sendline(payload.encode())
response = conn.recvline().decode().strip()
if response != "Here is your code coverage: 110000000":
non_matching_strings.append(payload)
for string in non_matching_strings:
print(string)运行一下即可得到爆破出来的flag

flag:qwb{YouKnowHowToFuzz!}
石头剪刀布
nc连接以后得到一个石头剪刀布的游戏
按照师傅给的顺序
0000011220120220110111222010022012110021012012202100112022100112110020110220210201
也能得到flag
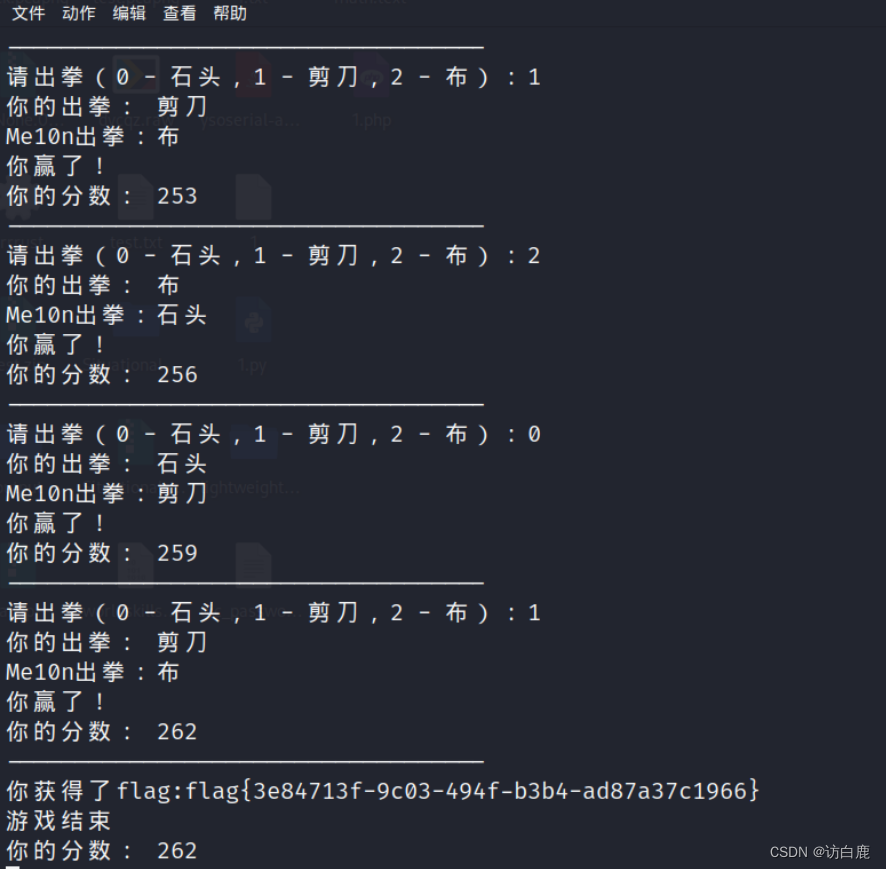
看了师傅们的wp是利用脚本
由于前面5次大模型是随机输出的,因此我们可以考虑从第6次开始求最优解。最坏情况下,前5次全输,需要87步即可达到260分,即第92轮时,因此可以通过本题。
from pwn import remote
ip = '<ip>'
port = '<port>'
class GetStatus:
def __init__(self, _ip=ip, _port=port) -> None:
self.r = remote(_ip, _port)
self.score = 0
def getdiff(self, out):
self.r.sendlineafter('请出拳'.encode(), str(out).encode())
self.r.recvuntil('分数:'.encode())
newscore = int(self.r.recvline().decode())
diff = newscore - self.score
self.score = newscore
return diff
def test_list(self, lis):
for out in lis:
diff = self.getdiff(out)
if self.score >= 260:
return 'win'
return diff
current_best = [0] * 5
diff2out = {
3: 0,
1: 2,
0: 1
}
while len(current_best) <= 100:
current_best.append(0)
c = GetStatus()
diff = c.test_list(current_best)
if c.score >= 260:
c.r.interactive()
break
c.r.close()
current_best[-1] = diff2out[diff]
print(f'Round {len(current_best)}: {current_best}')谍影重重2.0
将数据包导出为json格式,使用脚本提取字段并进行MD5
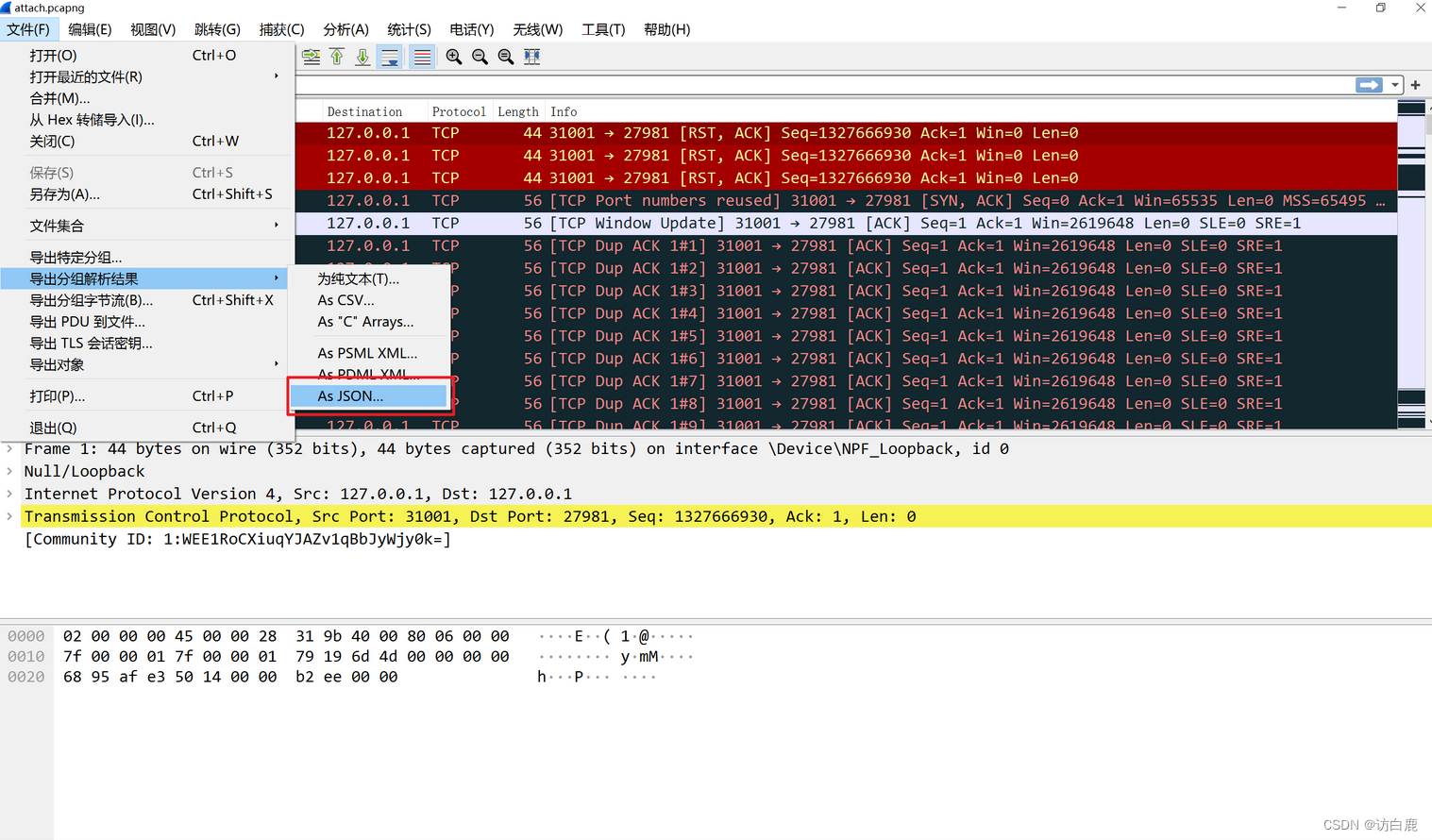
脚本
import json
import pyModeS as pms
import hashlib
with open('123.json', 'r', encoding='utf-8') as file:
data = json.load(file)
info = []
for packet in data:
if 'layers' in packet['_source'] and 'tcp' in packet['_source']['layers']:
tcp_layer = packet['_source']['layers']['tcp']
if 'tcp.payload' in tcp_layer:
tcp_payload = tcp_layer['tcp.payload'].replace(':','')
info.append(tcp_payload)
planes_data = []
for i in info:
msg = i[18:]
if pms.adsb.typecode(msg) >= 19 and pms.adsb.typecode(msg) <= 22:
icao = pms.adsb.icao(msg)
velocity_info = pms.adsb.velocity(msg)
speed, track, vertical_rate, _ = velocity_info
plane_info = {"icao": icao, "speed": speed, "track": track, "vertical_rate": vertical_rate}
planes_data.append(plane_info)
fastest_plane = max(planes_data, key=lambda x: x['speed'])
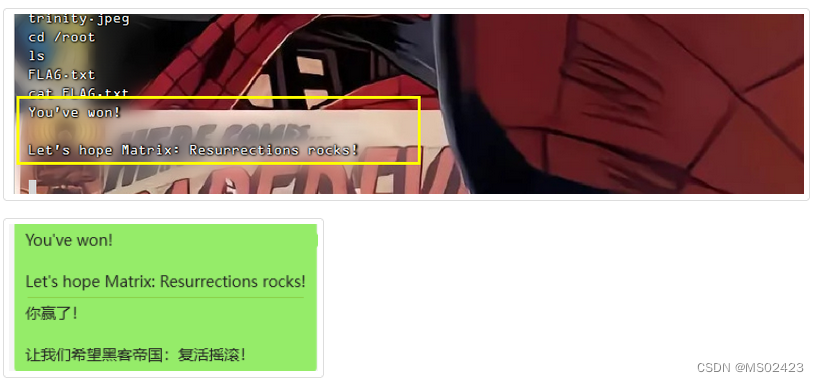
print(hashlib.md5(fastest_plane['icao'].upper().encode()).hexdigest())运行一下即可得到flag
flag{4cf6729b9bc05686a79c1620b0b1967b}