一.ACL
实验目的:过滤流量,然后匹配规划后,判断该流量通过或拒绝
1.拓扑图

2.配置
基本ACL
其它同理配置

R1
[Huawei]sys R1
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/0
#
return
[R1-GigabitEthernet0/0/0]ip add 192.168.1.254 24
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 192.168.2.254 24
[R1-GigabitEthernet0/0/1]int g0/0/2
[R1-GigabitEthernet0/0/2]ip add 192.168.3.254 24
[R1-GigabitEthernet0/0/2]q
[R1]acl 2000
[R1-acl-basic-2000]ru
[R1-acl-basic-2000]rule de
[R1-acl-basic-2000]rule deny so
[R1-acl-basic-2000]rule deny source 192.168.1.1 0
[R1-acl-basic-2000]dis th
[V200R003C00]
#
acl number 2000
rule 5 deny source 192.168.1.1 0
#
return
[R1-acl-basic-2000]q
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]t
[R1-GigabitEthernet0/0/1]tr
[R1-GigabitEthernet0/0/1]traffic-filter o
[R1-GigabitEthernet0/0/1]traffic-filter outbound ac
[R1-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
[R1-GigabitEthernet0/0/1]q
[R1]dis
[R1]display acl a
Total quantity of nonempty ACL number is 1
Basic ACL 2000, 1 rule
Acl's step is 5
rule 5 deny source 192.168.1.1 0 (4 matches)
[R1]高级ACL
开启Server1服务

Client1去访问
R1
把之前那个指令删了undo xxxxx
[R1]acl 3000
[R1-acl-adv-3000]rule deny tcp so
[R1-acl-adv-3000]rule deny tcp source 192.168.1.1 0 de
[R1-acl-adv-3000]rule deny tcp source 192.168.1.1 0 destination 192.168.2.1 0 de
[R1-acl-adv-3000]rule deny tcp source 192.168.1.1 0 destination 192.168.2.1 0 de
stination-port eq www
[R1-acl-adv-3000]dis th
[V200R003C00]
#
acl number 3000
rule 5 deny tcp source 192.168.1.1 0 destination 192.168.2.1 0 destination-port
eq www //不让192.168.1.1 去访问 192.168.2.1的tcp 80端口(www web 服务)
#
return
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]tra
[R1-GigabitEthernet0/0/0]traf
[R1-GigabitEthernet0/0/0]traffic-fi
[R1-GigabitEthernet0/0/0]traffic-filter in
[R1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000 //将此规则配置在进口方向
[R1-GigabitEthernet0/0/0]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
traffic-filter inbound acl 3000
#
return
[R1-GigabitEthernet0/0/0]Client1不可以访问Server2!

3.测试
基本ACL

从Client1出发,只有Server1不可到达,其他正常!
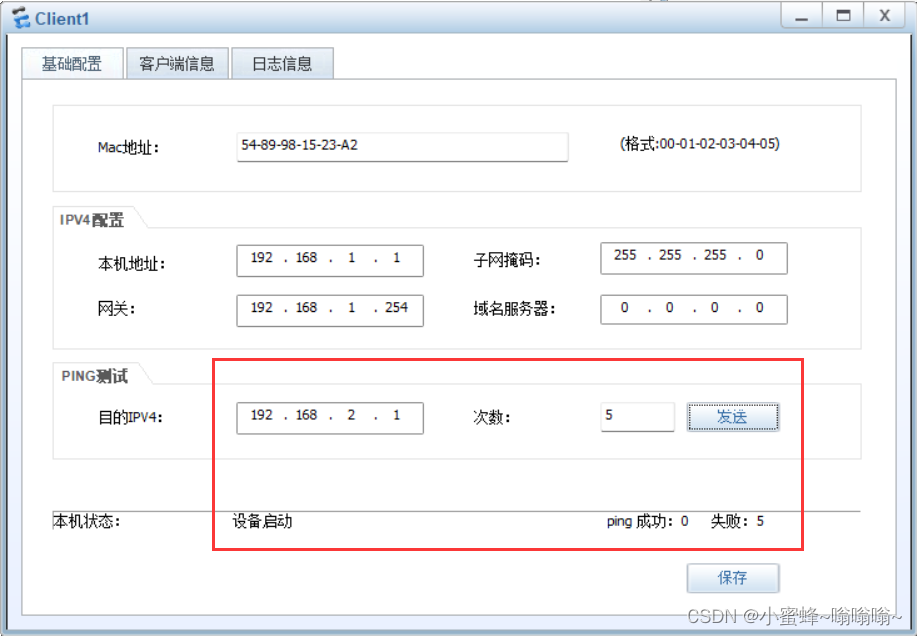

Client2能到

二.NAT
静态 动态
1.拓扑图

2.配置
运营商ISP

企业出口QY
静态NAT
<Huawei>
<Huawei>
<Huawei>u t m
Info: Current terminal monitor is off.
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sys
[Huawei]sysname QY
[QY]int g0/0/0
[QY-GigabitEthernet0/0/0]q
[QY]int g0/0/0
[QY-GigabitEthernet0/0/0]ip add 192.168.1.254 24
[QY-GigabitEthernet0/0/0]int g0/0/1
[QY-GigabitEthernet0/0/1]ip add 200.0.0.1 24
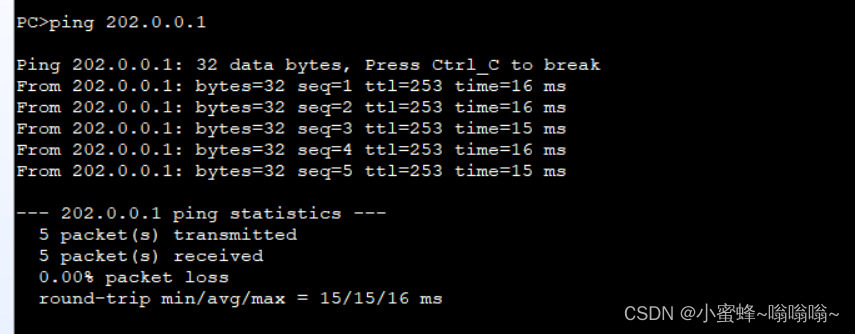
[QY-GigabitEthernet0/0/1]ping 200.0.0.2
PING 200.0.0.2: 56 data bytes, press CTRL_C to break
Reply from 200.0.0.2: bytes=56 Sequence=1 ttl=255 time=80 ms
Reply from 200.0.0.2: bytes=56 Sequence=2 ttl=255 time=20 ms
Reply from 200.0.0.2: bytes=56 Sequence=3 ttl=255 time=20 ms
Reply from 200.0.0.2: bytes=56 Sequence=4 ttl=255 time=20 ms
Reply from 200.0.0.2: bytes=56 Sequence=5 ttl=255 time=20 ms
--- 200.0.0.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/32/80 ms
[QY-GigabitEthernet0/0/1]nat sta
[QY-GigabitEthernet0/0/1]nat static en
[QY-GigabitEthernet0/0/1]nat static enable
[QY-GigabitEthernet0/0/1]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
nat static enable
#
return
[QY-GigabitEthernet0/0/1]nat sta
[QY-GigabitEthernet0/0/1]nat static glo
[QY-GigabitEthernet0/0/1]nat static global 200.0.0.100 in
[QY-GigabitEthernet0/0/1]nat static global 200.0.0.100 inside 192.168.1.1
[QY-GigabitEthernet0/0/1]nat st
[QY-GigabitEthernet0/0/1]nat static gl
[QY-GigabitEthernet0/0/1]nat static global 200.0.0.200 in
[QY-GigabitEthernet0/0/1]nat static global 200.0.0.200 inside 192.168.1.2
[QY-GigabitEthernet0/0/1]动态NAT
[QY-GigabitEthernet0/0/1]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
nat static global 200.0.0.100 inside 192.168.1.1 netmask 255.255.255.255
nat static global 200.0.0.200 inside 192.168.1.2 netmask 255.255.255.255
nat static enable
#
return
[QY-GigabitEthernet0/0/1]undo nat static global 200.0.0.100 inside 192.168.1.1 n
etmask 255.255.255.255
[QY-GigabitEthernet0/0/1]
[QY-GigabitEthernet0/0/1]undo nat static global 200.0.0.200 inside 192.168.1.2
netmask 255.255.255.255
[QY-GigabitEthernet0/0/1]
[QY-GigabitEthernet0/0/1]undo nat static enable
[QY-GigabitEthernet0/0/1]
[QY-GigabitEthernet0/0/1]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
#
return
[QY-GigabitEthernet0/0/1]q
[QY]nat a
[QY]nat address-group 1 200.0.0.10 200.0.0.50
[QY]acl 2000
[QY-acl-basic-2000]dis th
[V200R003C00]
#
acl number 2000
#
return
[QY-acl-basic-2000]rule per
[QY-acl-basic-2000]rule permit so
[QY-acl-basic-2000]rule permit source 192.168.1.0 0.0.0.255
[QY-acl-basic-2000]q
[QY]int g0/0/1
[QY-GigabitEthernet0/0/1]nat ou
[QY-GigabitEthernet0/0/1]nat outbound 2000 a
[QY-GigabitEthernet0/0/1]nat outbound 2000 address-group 1
[QY-GigabitEthernet0/0/1]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
nat outbound 2000 address-group 1
#
return
[QY-GigabitEthernet0/0/1]拓扑图
NAT Service

QY
[QY]int g0/0/1
[QY-GigabitEthernet0/0/1]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
nat outbound 2000 address-group 1
#
return
[QY-GigabitEthernet0/0/1]undo nat outbound 2000 address-group 1
[QY-GigabitEthernet0/0/1]nat
[QY-GigabitEthernet0/0/1]nat se
[QY-GigabitEthernet0/0/1]nat server pr
[QY-GigabitEthernet0/0/1]nat server protocol tcp gl
[QY-GigabitEthernet0/0/1]nat server protocol tcp global cu
[QY-GigabitEthernet0/0/1]nat server protocol tcp global current-interface www in
si
[QY-GigabitEthernet0/0/1]nat server protocol tcp global current-interface www in
side 192.168.1.100 www
Warning:The port 80 is well-known port. If you continue it may cause function fa
ilure.
Are you sure to continue?[Y/N]:y
[QY-GigabitEthernet0/0/1]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/1
ip address 200.0.0.1 255.255.255.0
nat server protocol tcp global current-interface www inside 192.168.1.100 www
#
return
[QY-GigabitEthernet0/0/1]可以通

Easy IP