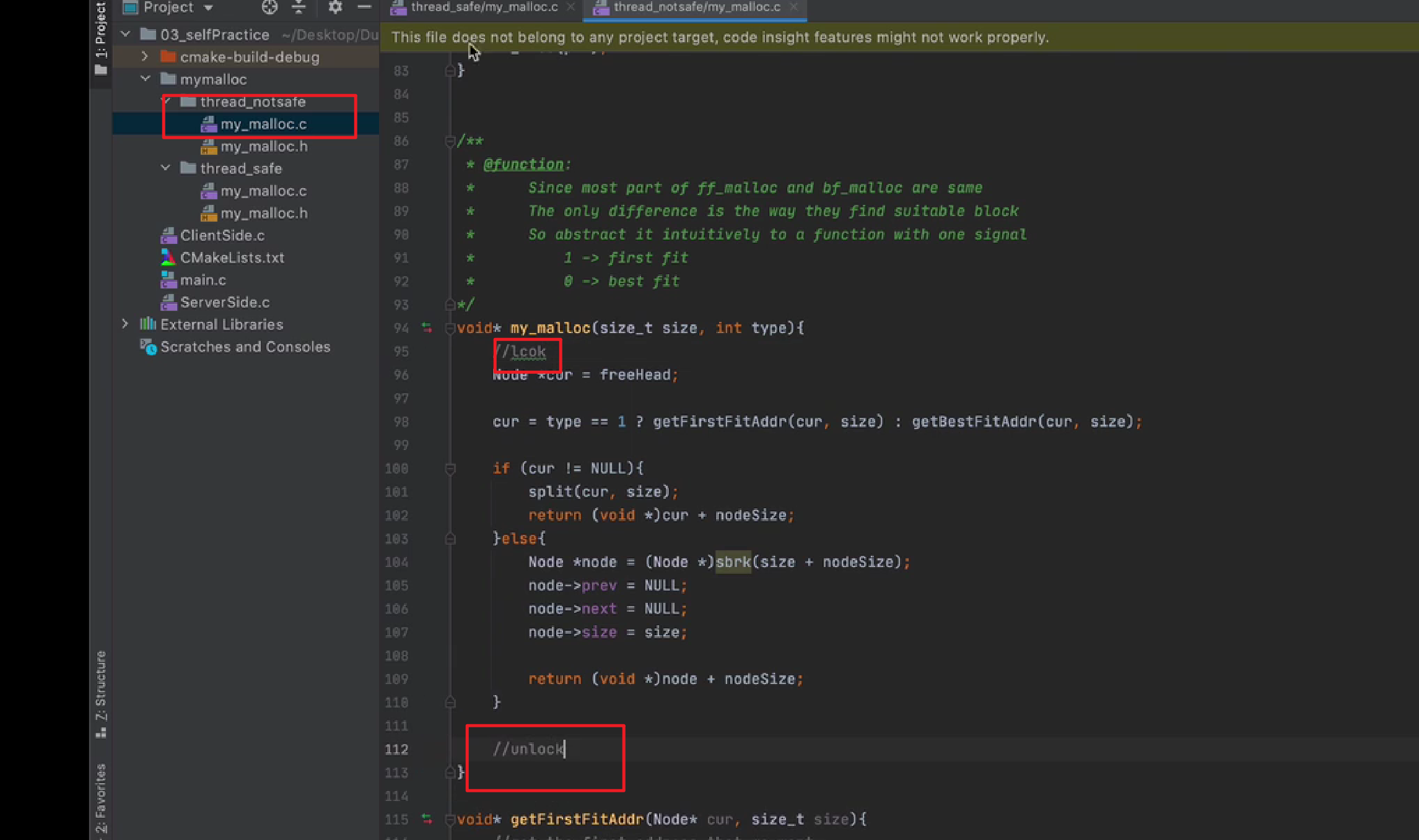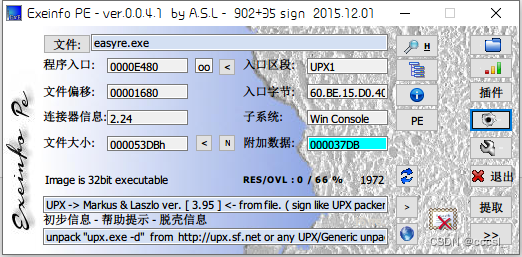
拿到exe文件先查下信息,是一个32位程序,加了壳。
不会脱,直接拿到自动脱壳机潦草结束

看着有点乱,稍微改改 嗯,这样舒服多了。就是将V6扩展到18个字节大小,V5也扩展到12个字节大小,这样更符合源代码的习惯
嗯,这样舒服多了。就是将V6扩展到18个字节大小,V5也扩展到12个字节大小,这样更符合源代码的习惯
后面的解密我采用的是逐字节爆破,在可见字符范围内,狠狠地爆
#include <iostream>
#include <windows.h>
using namespace std;
CHAR encrypt[12] = {
0x2a,0x46,0x27,0x22,0x4e,
0x2c,0x22,0x28,0x49,0x3f,
0x2b,0x40
};
CHAR ida_chars[] =
{
0x7E, 0x7D, 0x7C, 0x7B, 0x7A, 0x79, 0x78, 0x77, 0x76, 0x75,
0x74, 0x73, 0x72, 0x71, 0x70, 0x6F, 0x6E, 0x6D, 0x6C, 0x6B,
0x6A, 0x69, 0x68, 0x67, 0x66, 0x65, 0x64, 0x63, 0x62, 0x61,
0x60, 0x5F, 0x5E, 0x5D, 0x5C, 0x5B, 0x5A, 0x59, 0x58, 0x57,
0x56, 0x55, 0x54, 0x53, 0x52, 0x51, 0x50, 0x4F, 0x4E, 0x4D,
0x4C, 0x4B, 0x4A, 0x49, 0x48, 0x47, 0x46, 0x45, 0x44, 0x43,
0x42, 0x41, 0x40,0x3F, 0x3E, 0x3D, 0x3C, 0x3B, 0x3A, 0x39,
0x38, 0x37, 0x36,
0x35, 0x34, 0x33, 0x32, 0x31, 0x30, 0x2F, 0x2E, 0x2D, 0x2C,
0x2B, 0x2A, 0x29, 0x28, 0x27, 0x26, 0x25, 0x24, 0x23, 0x20,
0x21, 0x22
};
int main()
{
//cout << sizeof(ida_chars) << endl; 95
PCHAR ptr = ida_chars;
for (int i = 0; i < 12; i++)
{
ptr = ida_chars;
for (char j = 33; j < 125; j++)
{
if (ida_chars[j - 1] == encrypt[i])
{
cout << j;
break;
}
}
}
cout << endl;
}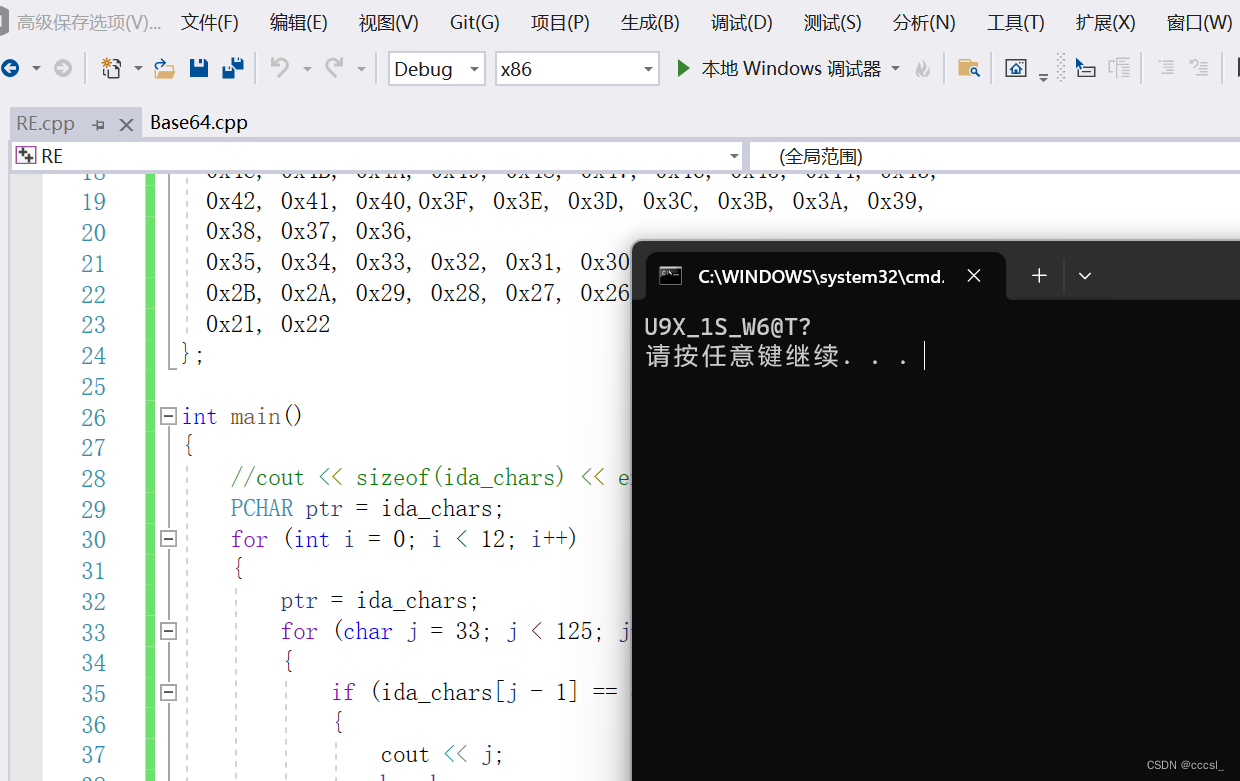
所以flag是:
flag{U9X_1S_W6@T?}
注意不是ACTF{U9X_1S_W6@T?}