文章目录
- 前言
- 题目分析
- 还原汇编
- exp
- 后言
前言
兜兜转转终于回到这里了。之前复现了羊城杯较简单点的三题,到这一题vm卡住了,刷了好几道,终于搞定了。
题目分析
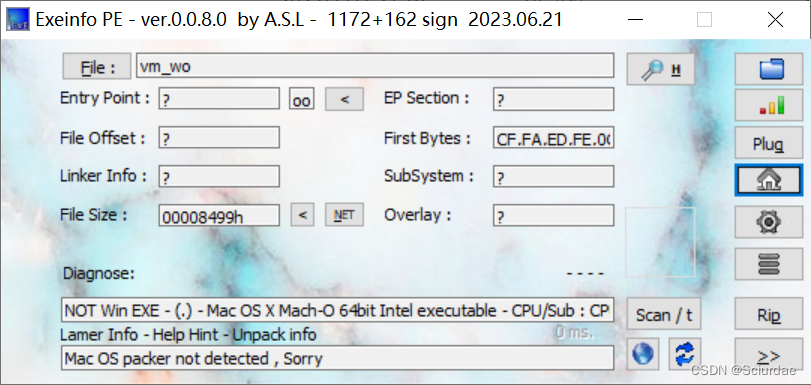
第一次遇到Mac os的题目,幸好还可以做。
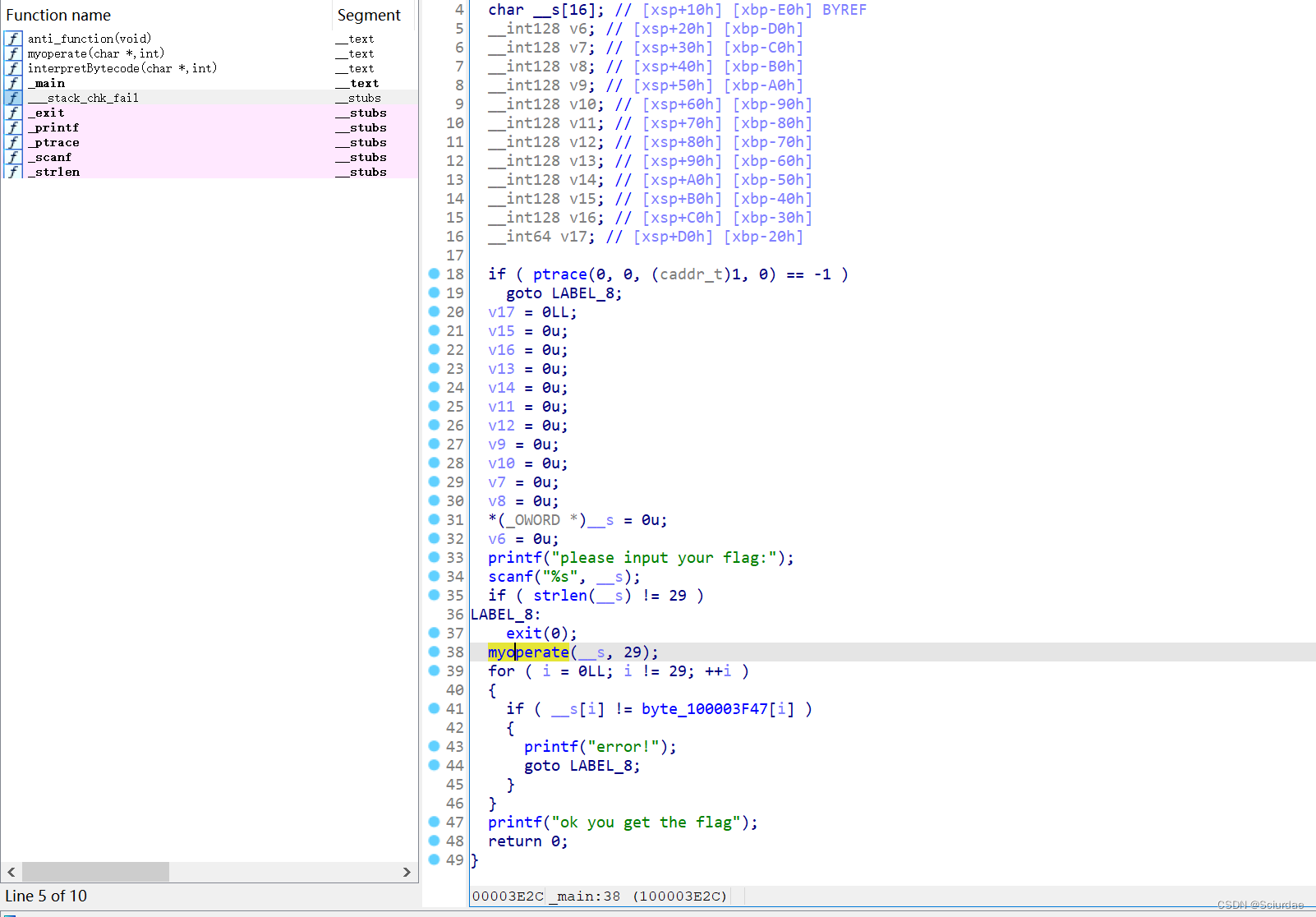
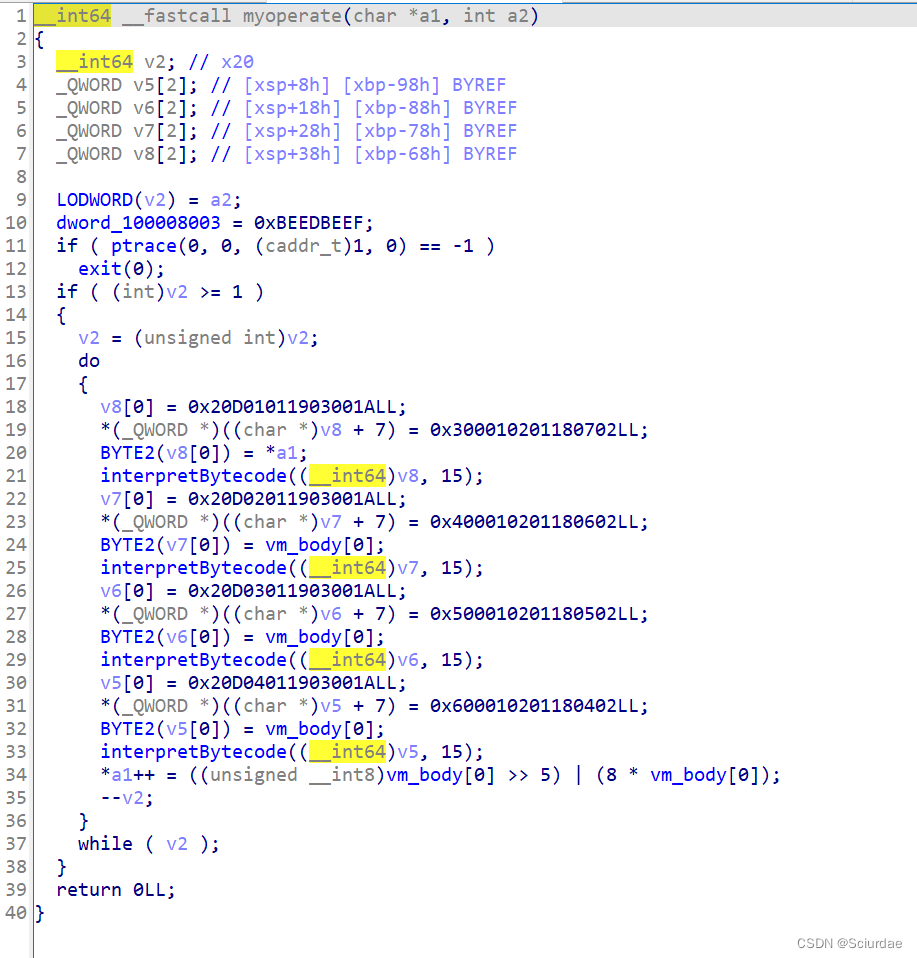
opcode 和 指令操作
密文:
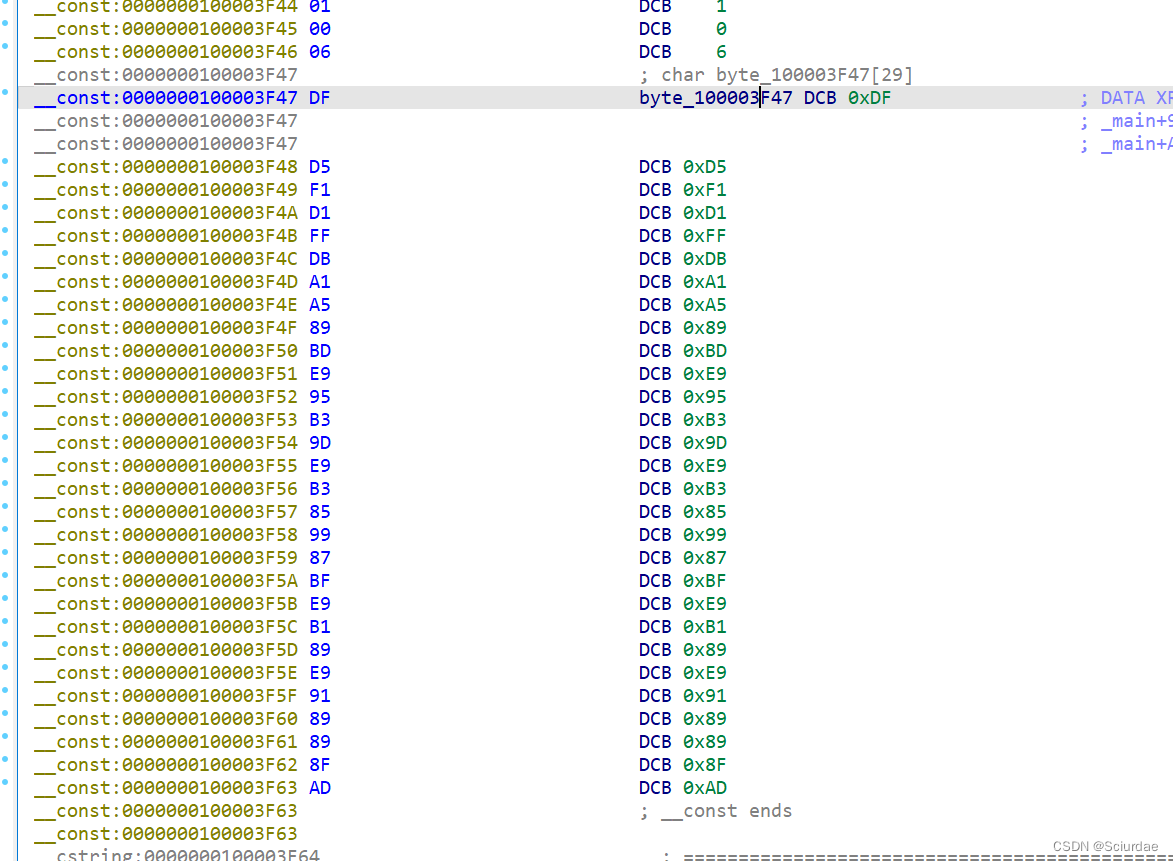
opcode先提取出来,得到:
opcode = [26, 0, 3, 25, 1, 1, 13, 2, 7, 24, 1, 2, 1, 0, 3, 26, 0, 3, 25,
1, 2, 13, 2, 6, 24, 1, 2, 1, 0, 4, 26, 0, 3, 25, 1, 3, 13, 2, 5,
24, 1, 2, 1, 0, 5, 26, 0, 3, 25, 1, 4, 13, 2, 4, 24, 1, 2, 1, 0, 6]

注意这里是,后面的八位拼接上去会把前面的最后一个给覆盖掉。同时数据在内存中是小端序存储,因此还需要逆序一下。
查个重。得到:
[26, 0, 3, 25, 1, 13, 2, 7, 24, 6, 4, 5]
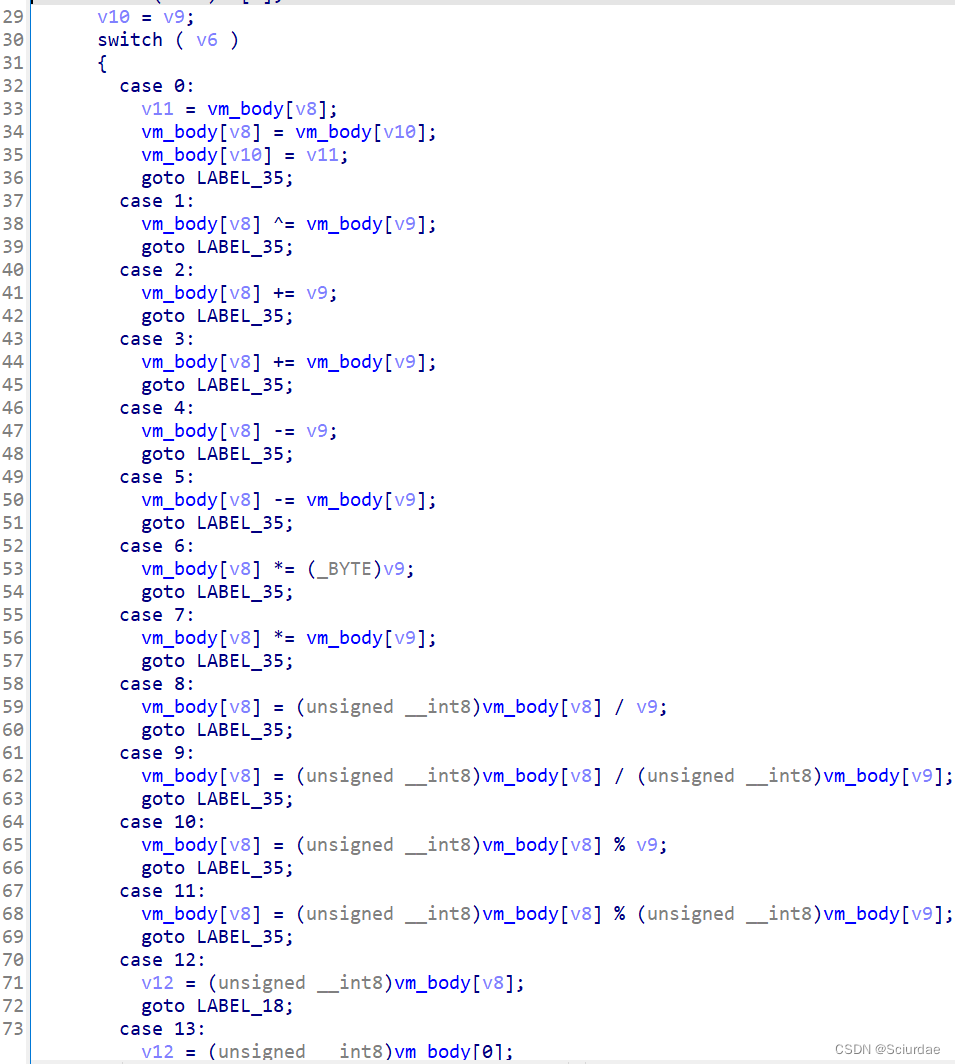
一共26条指令,真的多,但是因为我们opcode很少,可以只还原一部分就OK了。
还原汇编
opcode = [26, 0, 3, 25, 1, 1, 13, 2, 7, 24, 1, 2, 1, 0, 3, 26, 0, 3, 25,
1, 2, 13, 2, 6, 24, 1, 2, 1, 0, 4, 26, 0, 3, 25, 1, 3, 13, 2, 5,
24, 1, 2, 1, 0, 5, 26, 0, 3, 25, 1, 4, 13, 2, 4, 24, 1, 2, 1, 0, 6]
# [26, 0, 3, 25, 1, 13, 2, 7, 24, 6, 4, 5]
i = 0
while opcode[i]:
match opcode[i]:
case 0:
print(f"{i} swap reg%d reg%d" % (opcode[i+1],opcode[i+2]))
case 1:
print(f"{i} xor reg%d reg%d" % (opcode[i+1],opcode[i+2]))
case 2:
print(f"{i} add reg%d %d" % (opcode[i+1],opcode[i+2]))
case 3:
print(f"{i} add reg%d reg%d" % (opcode[i+1],opcode[i+2]))
case 4:
print(f"{i} sub reg%d %d" % (opcode[i+1],opcode[i+2]))
case 5:
print(f"{i} sub reg%d reg%d" % (opcode[i+1],opcode[i+2]))
case 6:
print(f"{i} mul reg%d %d" % (opcode[i+1],opcode[i+2]))
case 7:
print(f"{i} mul reg%d reg%d" % (opcode[i+1],opcode[i+2]))
case 13:
print(f"{i} mov reg%d reg0<<%d" % (opcode[i+1],opcode[i+2]))
case 24:
print(f"{i} reg0 = reg2 | reg1")
case 25:
print(f"{i} mov reg%d reg0>>%d" % (opcode[i+1],opcode[i+2]))
case 26:
print(f"{i} mov reg%d %d" % (opcode[i+1],opcode[i+2]))
i += 3
运行后打印的结果1:
0 mov reg0 3
3 mov reg1 reg0>>1
6 mov reg2 reg0<<7
9 reg0 = reg2 | reg1
12 xor reg0 reg3
15 mov reg0 3
18 mov reg1 reg0>>2
21 mov reg2 reg0<<6
24 reg0 = reg2 | reg1
27 xor reg0 reg4
30 mov reg0 3
33 mov reg1 reg0>>3
36 mov reg2 reg0<<5
39 reg0 = reg2 | reg1
42 xor reg0 reg5
45 mov reg0 3
48 mov reg1 reg0>>4
51 mov reg2 reg0<<4
54 reg0 = reg2 | reg1
57 xor reg0 reg6
这里打印的指令蛮少的,而且也没有和密文比较的地方,推测是单字符加密,解密的话就逆向就好了。
加密逻辑写出来大概就是
s = (s >> 1 | s << 7) & 0xFF
s = s ^ reg3
s = (s >> 2 | s << 6) & 0xFF
s = s ^ reg4
s = (s >> 3 | s << 5) & 0xFF
s = s ^ reg5
s = (s >> 4 | s << 4) & 0xFF
s = s ^ reg6
通过内存可以发现,reg3 到 reg6 就是
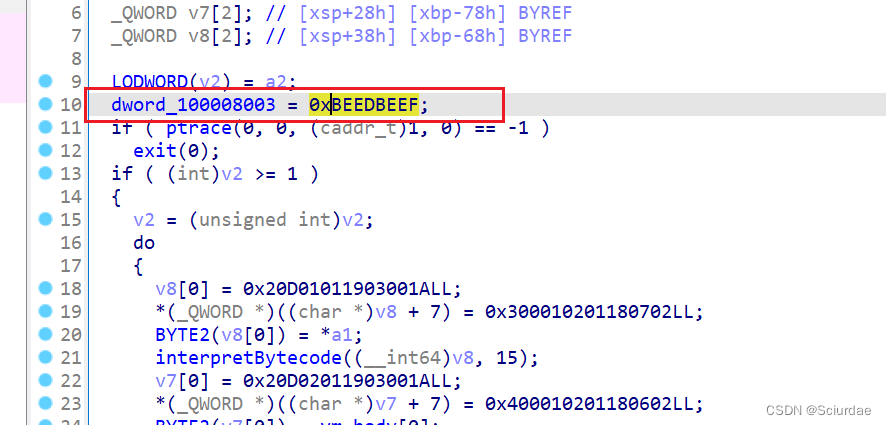
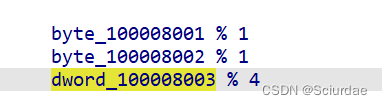
exp
enc = [0xDF, 0xD5, 0xF1, 0xD1, 0xFF, 0xDB, 0xA1, 0xA5, 0x89, 0xBD, 0xE9, 0x95, 0xB3, 0x9D, 0xE9, 0xB3, 0x85, 0x99, 0x87,
0xBF, 0xE9, 0xB1, 0x89, 0xE9, 0x91, 0x89, 0x89, 0x8F, 0xAD]
key = 0xBEEDBEEF.to_bytes(4, 'little')
def decode(s):
s = s ^ key[3]
s = (s << 4 | s >> 4) & 0xFF
s = s ^ key[2]
s = (s << 3 | s >> 5) & 0xFF
s = s ^ key[1]
s = (s << 2 | s >> 6) & 0xFF
s = s ^ key[0]
s = (s << 1 | s >> 7) & 0xFF
return s
flag = []
for i in enc:
i = ((i >> 3) | (i << 5) & 0xFF)
flag.append(decode(i))
print(bytes(flag))
# b'DASCTF{you_are_right_so_cool}'
后言
前面练的。
VM基础知识和EzMachine复现
HGAME 2023 week4vm复现
GWCTF 2019babyvm 复现
NCTF 2018wcyvm 复现