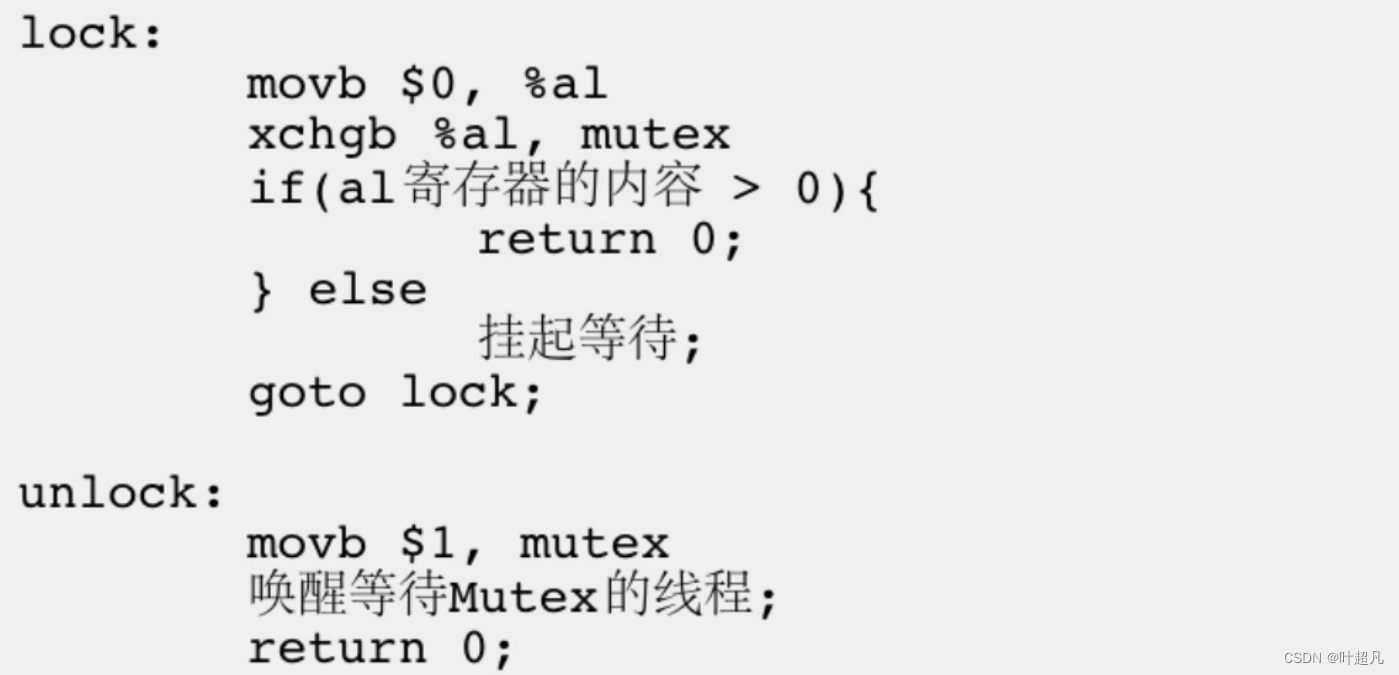
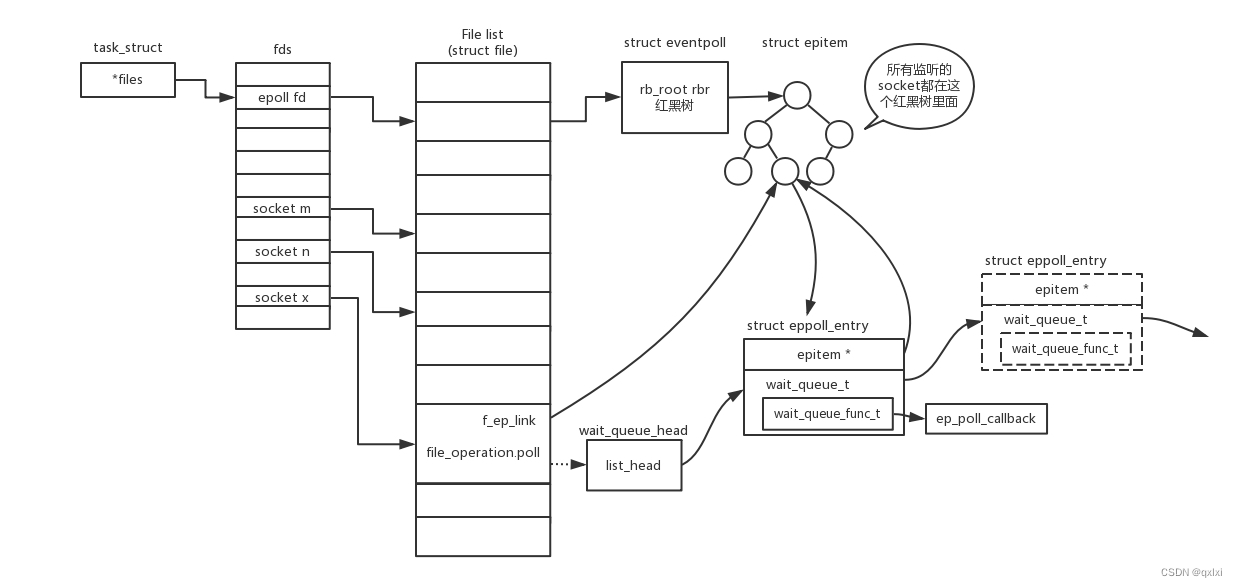
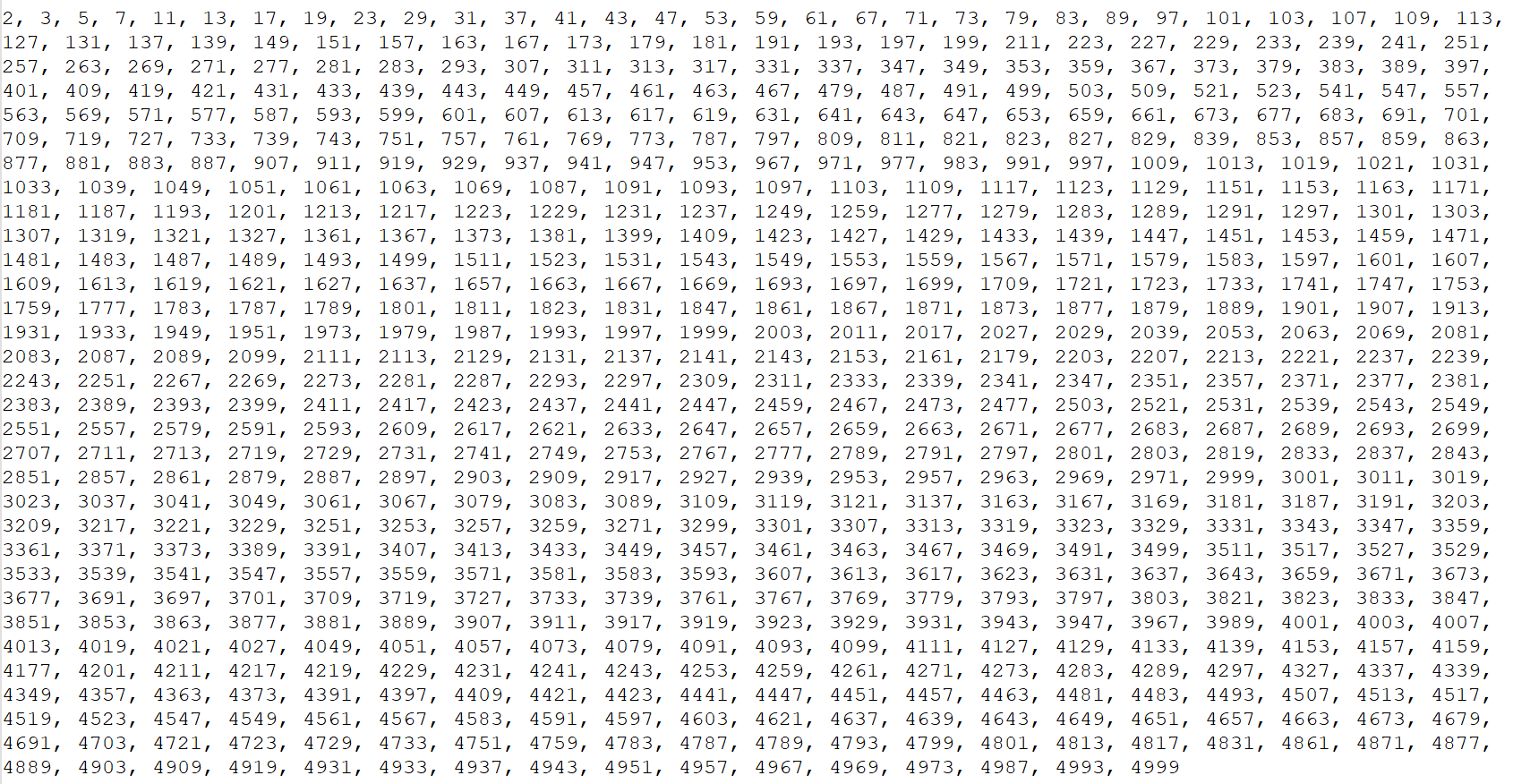师兄新学的Decode姿势
题目给出的
const SM4 = require("gm-crypt").sm4;
var payload =
"inu7s0XGslLFsPe0xok/nxqwtceG0cuMoh7hBbpwyNBrn3g/lMdcFYobv/K++eRgWwI/TIA4qMtjqpNKOet
E3TD0gWoSknGF6OhkRJ3LxrNUZ/Mi8ISz3xrDLawIY8NwbalYcQUGWtVjdC3nJLmAAA67FmSCAn2EOcI1mAt
9yMQ=";
let sm4Config = {
key: "B6*40.2_C9#e4$E3",
mode: "ecb",
cipherType: "base64"
};
let sm4 = new SM4(sm4Config);
var result = sm4.decrypt(payload);
console.log("解密:" + result)
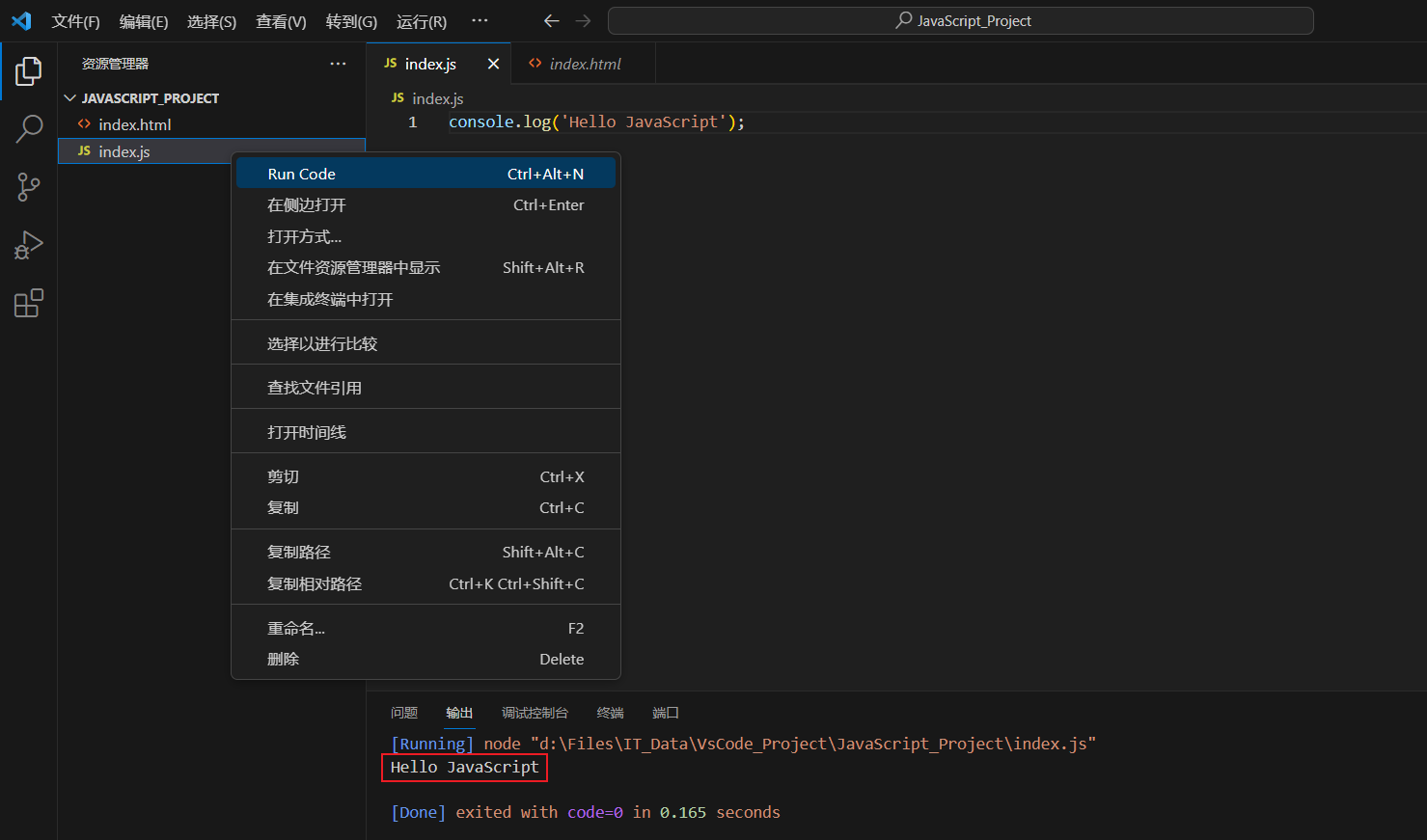
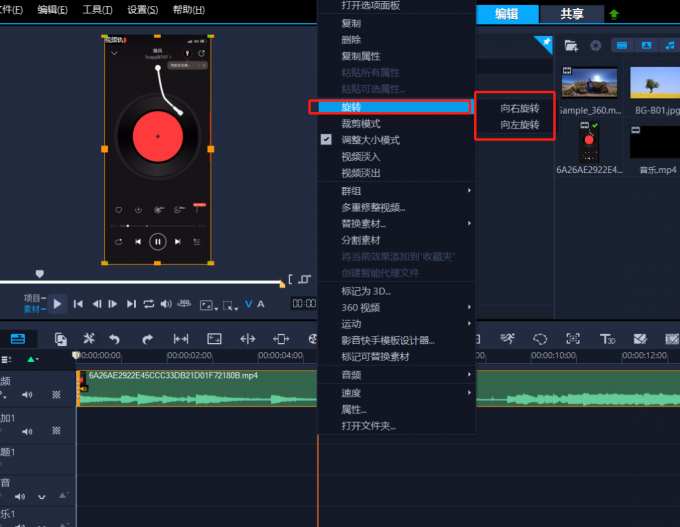
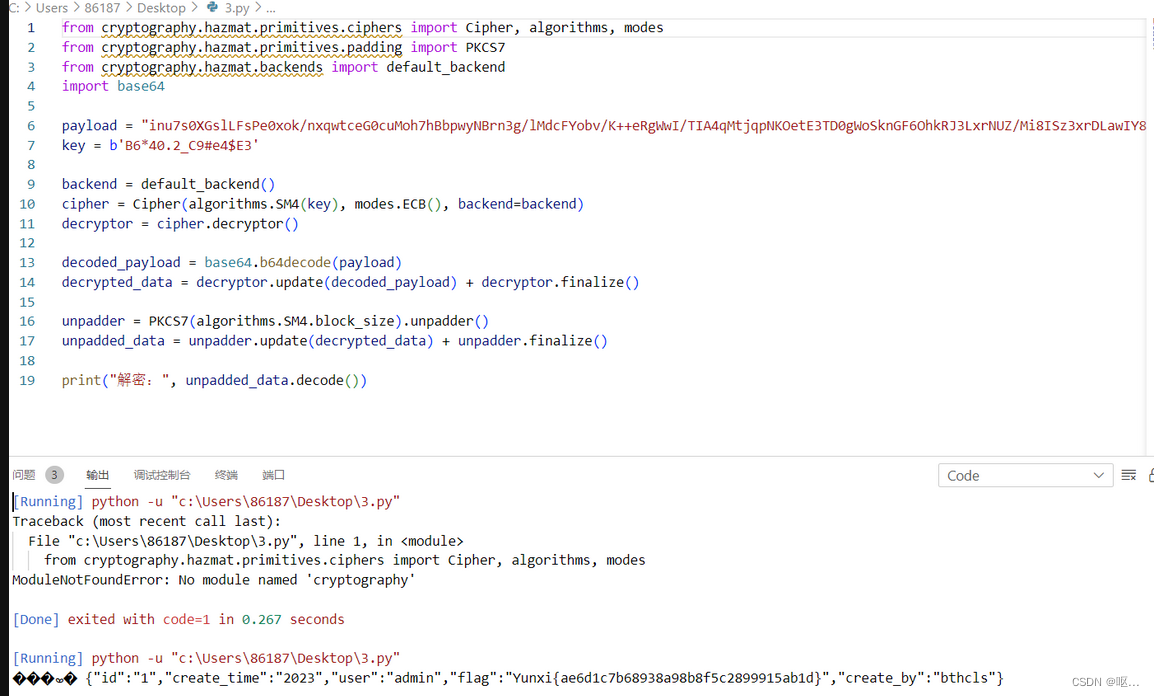
询问后,因为需要node.js环境,就把他转换为python语言 ,这个是借用的
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
from cryptography.hazmat.primitives.padding import PKCS7
from cryptography.hazmat.backends import default_backend
import base64
payload = "inu7s0XGslLFsPe0xok/nxqwtceG0cuMoh7hBbpwyNBrn3g/lMdcFYobv/K++eRgWwI/TIA4qMtjqpNKOetE3TD0gWoSknGF6OhkRJ3LxrNUZ/Mi8ISz3xrDLawIY8NwbalYcQUGWtVjdC3nJLmAAA67FmSCAn2EOcI1mAt9yMQ="
key = b'B6*40.2_C9#e4$E3'
backend = default_backend()
cipher = Cipher(algorithms.SM4(key), modes.ECB(), backend=backend)
decryptor = cipher.decryptor()
decoded_payload = base64.b64decode(payload)
decrypted_data = decryptor.update(decoded_payload) + decryptor.finalize()
unpadder = PKCS7(algorithms.SM4.block_size).unpadder()
unpadded_data = unpadder.update(decrypted_data) + unpadder.finalize()
print("解密:", unpadded_data.decode())
运行结果如下
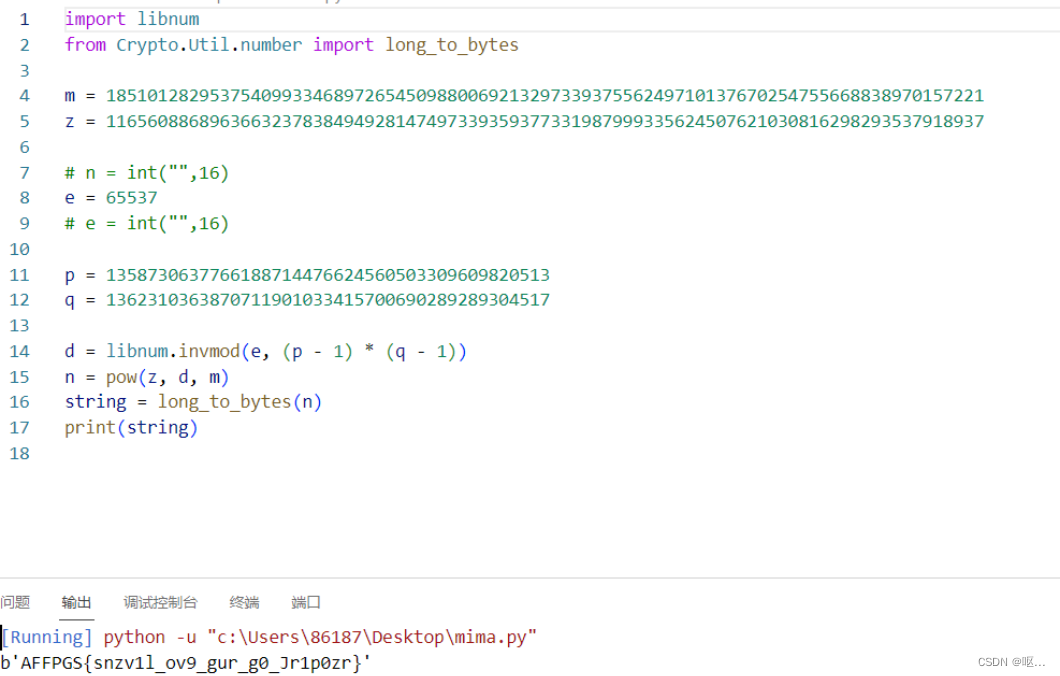
1z_rsa
看代码

简单来说,需要两个质因数p,q满足phi(N) = (p-1)(q-1),那么有N = p * q 。还需要一个定义叫e的质数为公钥,满足gcd(e,phi(N)) = 1(e和phi(N)公约数为1)
yafu分解m
yafu用于自动整数因式分解,在RSA中,当p、q的取值差异过大或过于相近的时候,使用yafu可以快速的把n值分解出p、q值
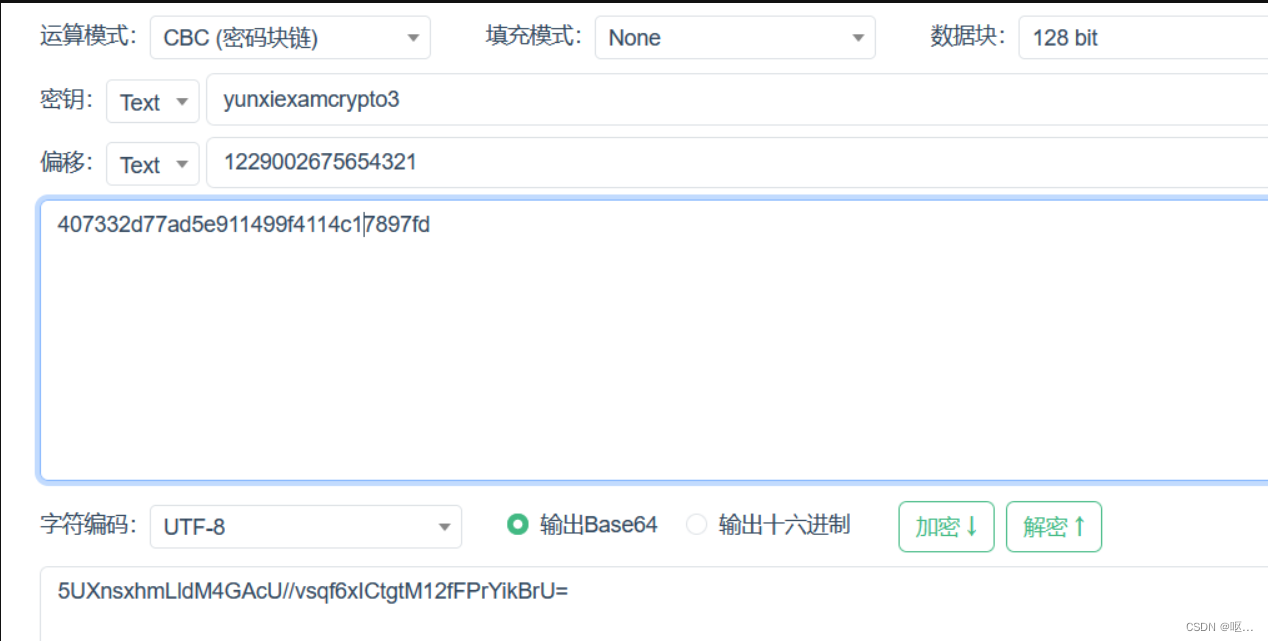
1z_AES
看一下代码,有了密钥和偏移量,可以找一个工具解密一下就可以了