防火墙的技术(NAT NAT-Server 策略路由 ) 第二十课
官方文档分享
菜鸟教程 - 学的不仅是技术,更是梦想!
环境的准备工作
1 配置如图所示的所有的IP地址
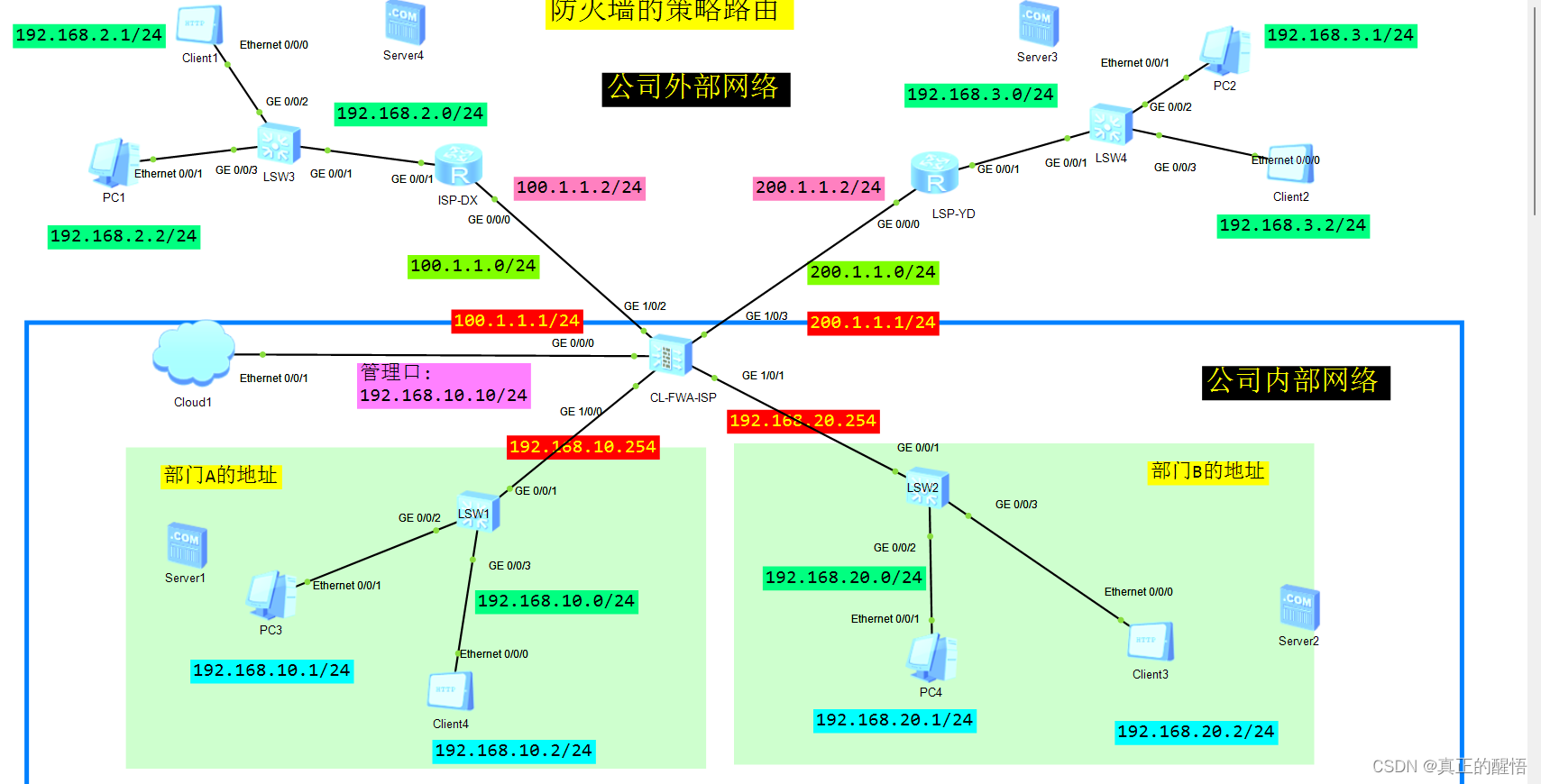
2 配置防火墙中的基本配置 防火墙的默认管理口的ip地址
<USG6000-ISP-LOCAL>display current-configuration
2023-10-28 02:54:08.620
!Software Version V500R005C10SPC300
#
sysname USG6000-ISP-LOCAL
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 23:52
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
web-manager timeout 1440
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 03:15
update schedule av-sdb daily 03:15
update schedule sa-sdb daily 03:15
update schedule cnc daily 03:15
update schedule file-reputation daily 03:15
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%BsCtOPL(zN7,KJ'*MyEVT@'b#SU%B-s==XD8^]NCXi'O@'eT@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%ID^AV4|YP*Gd}N/O*F$T|Q\S[(ML9S.XV%G,$V/`MpP2Q\V|@%@%
level 15
manager-user admin
password cipher @%@%.IM:8s~dkW{pj.:aoz8.T]QwC2XG5S,JG1-z{\'OJUo,]QzT@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.10.10 255.255.255.0
alias GE0/METH
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
#
firewall zone dmz
set priority 50
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
idle-timeout 0 0
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
3 配置正确的密码进入US6000管理系统 配置IP地址


4 在USG6000WEB页面中配置 IP地址
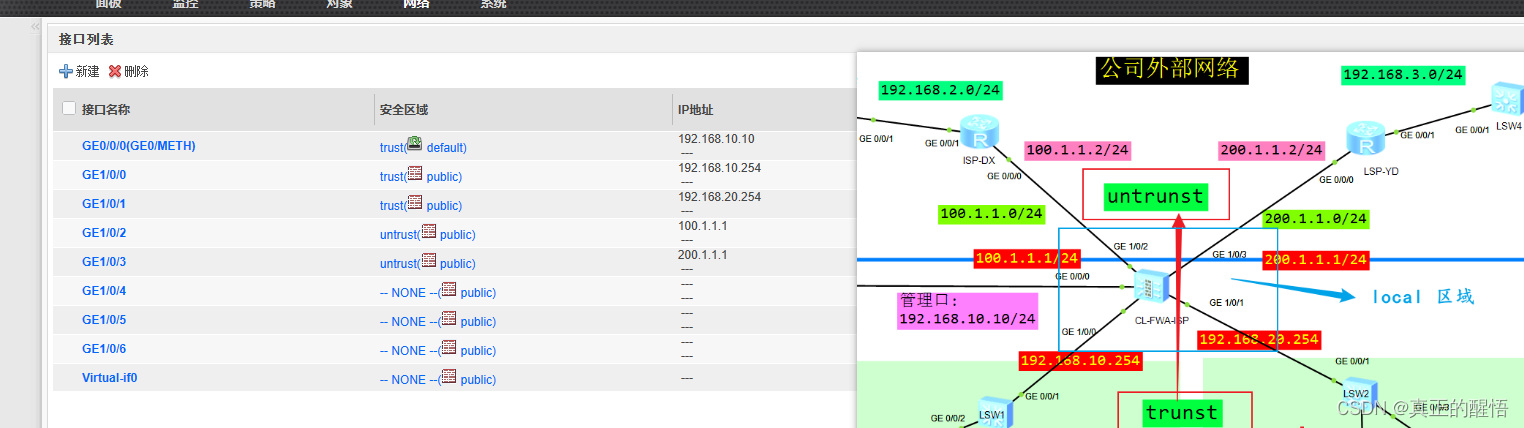
5 配置防火墙中的安全策略
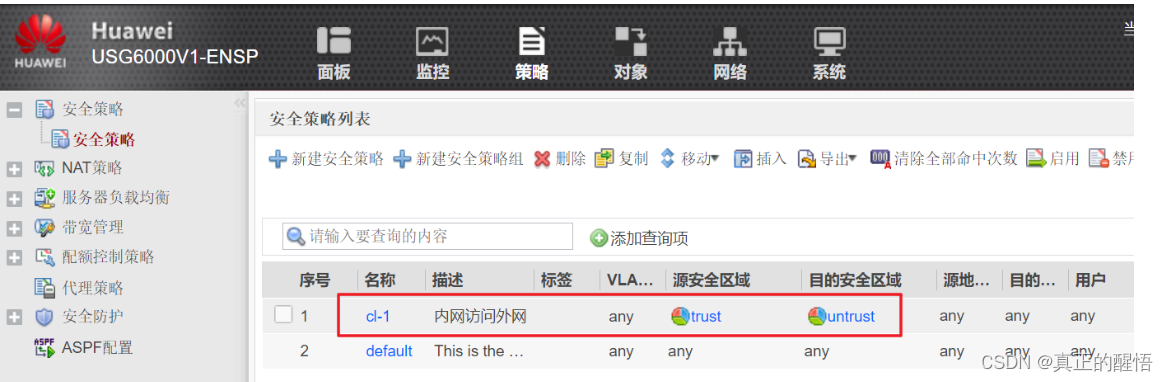
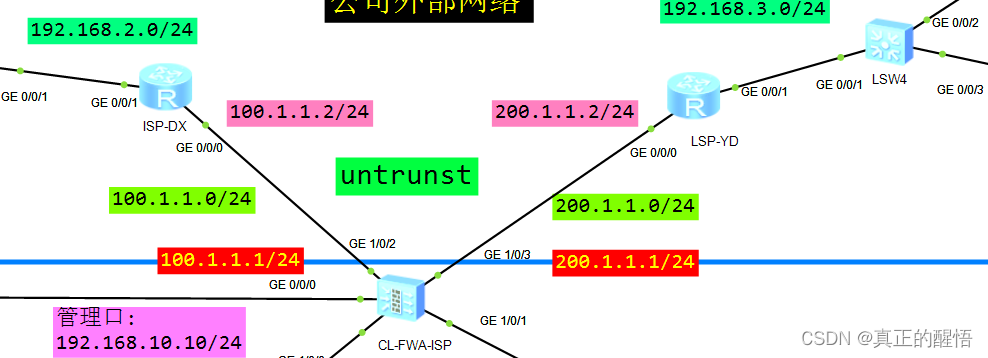
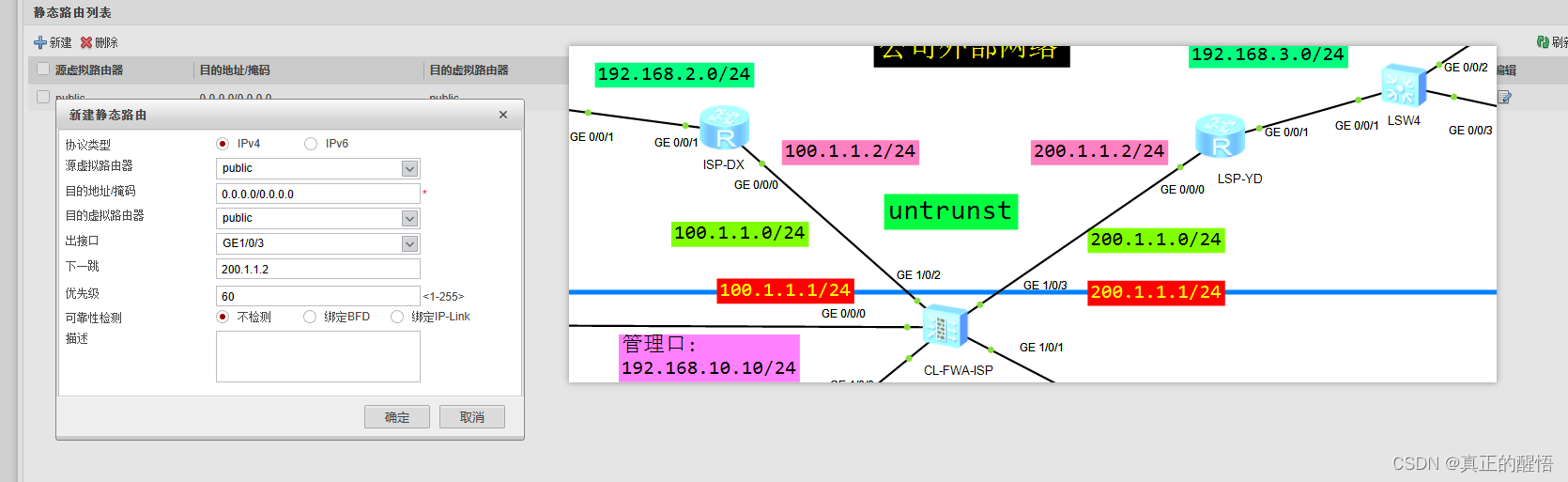
6 配置 静态路由
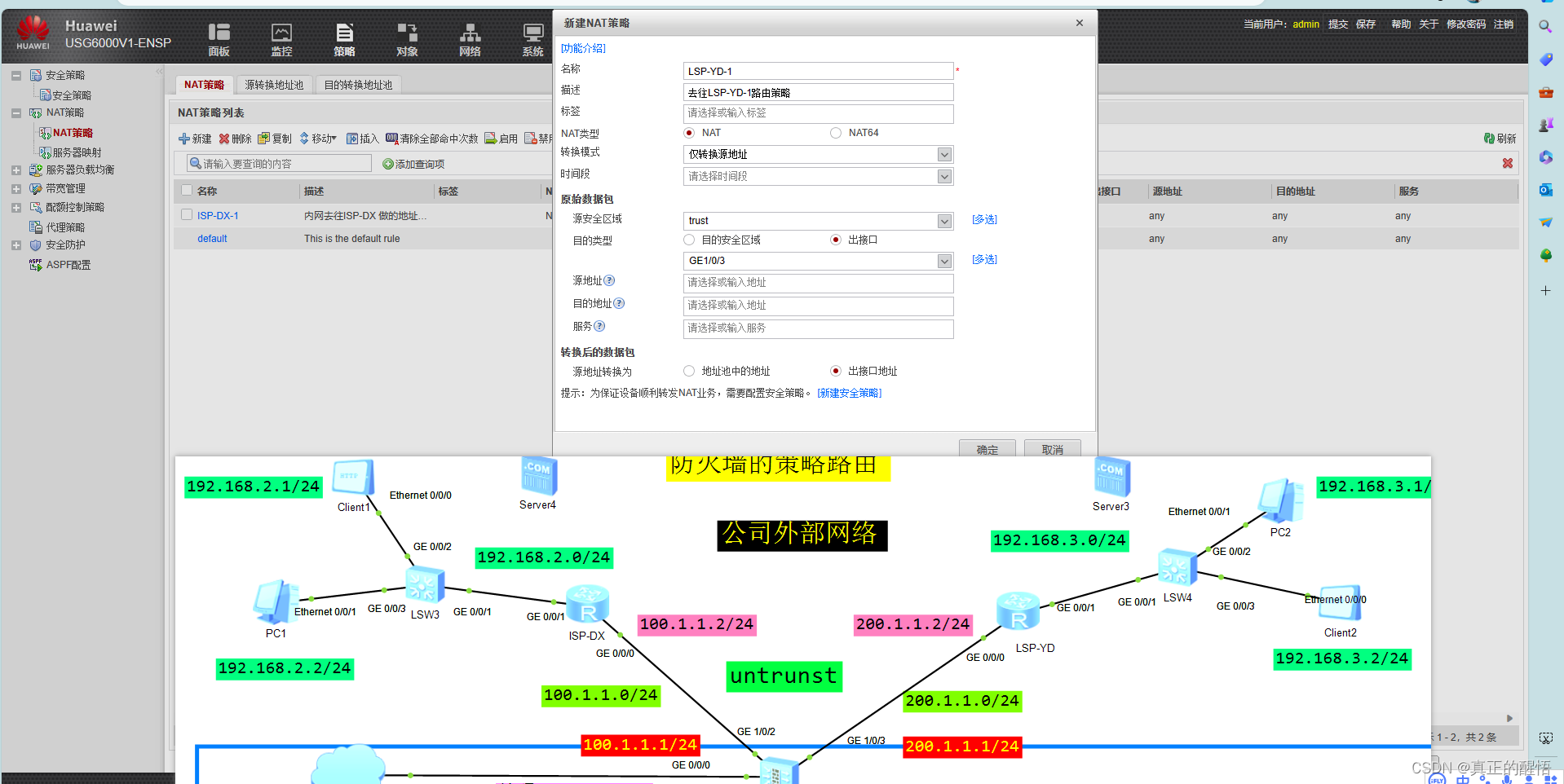
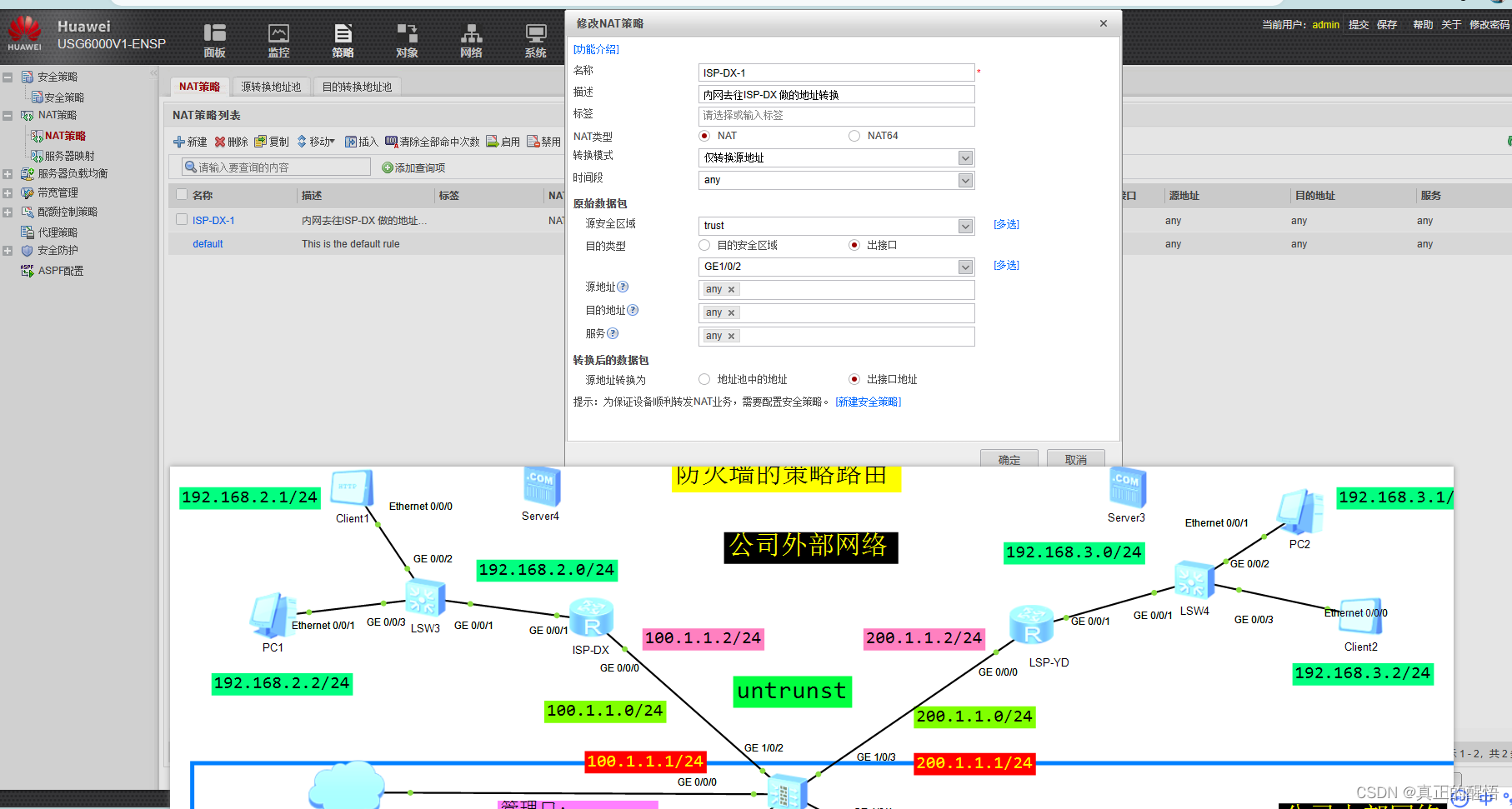
一 防火墙中的NAT
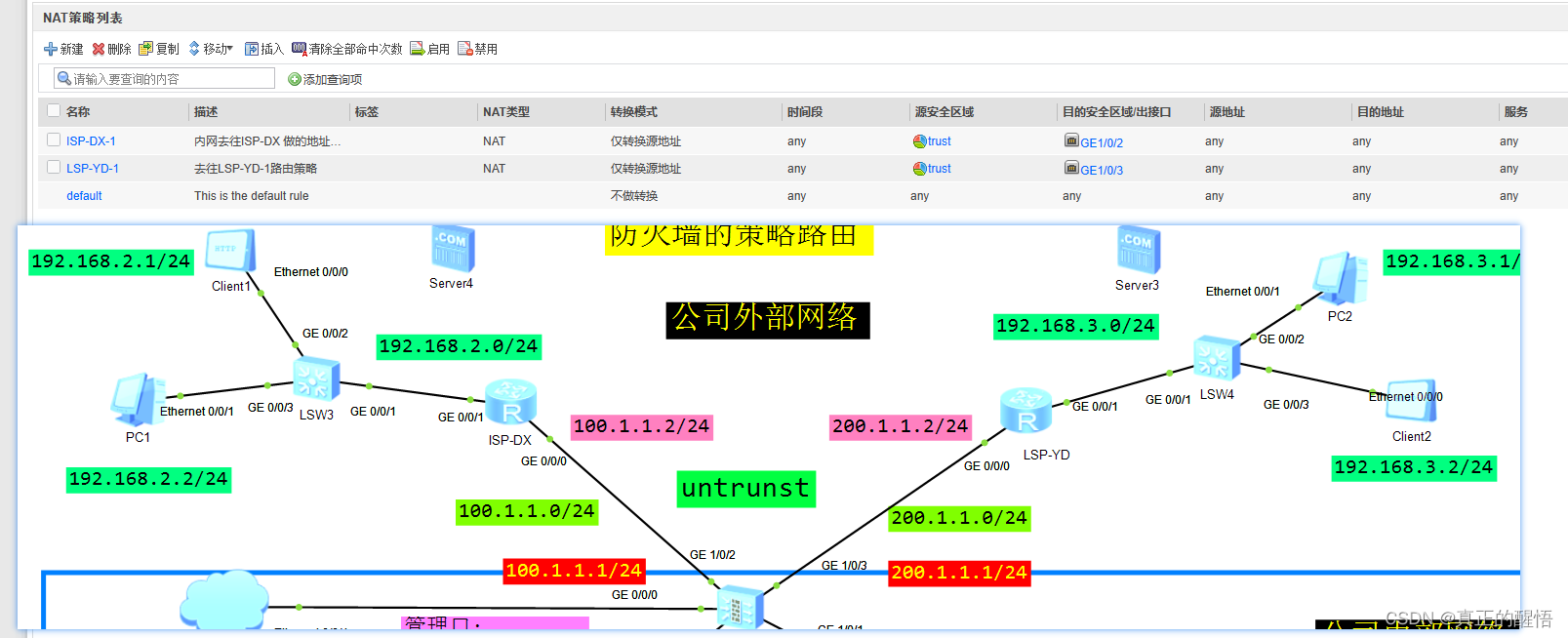
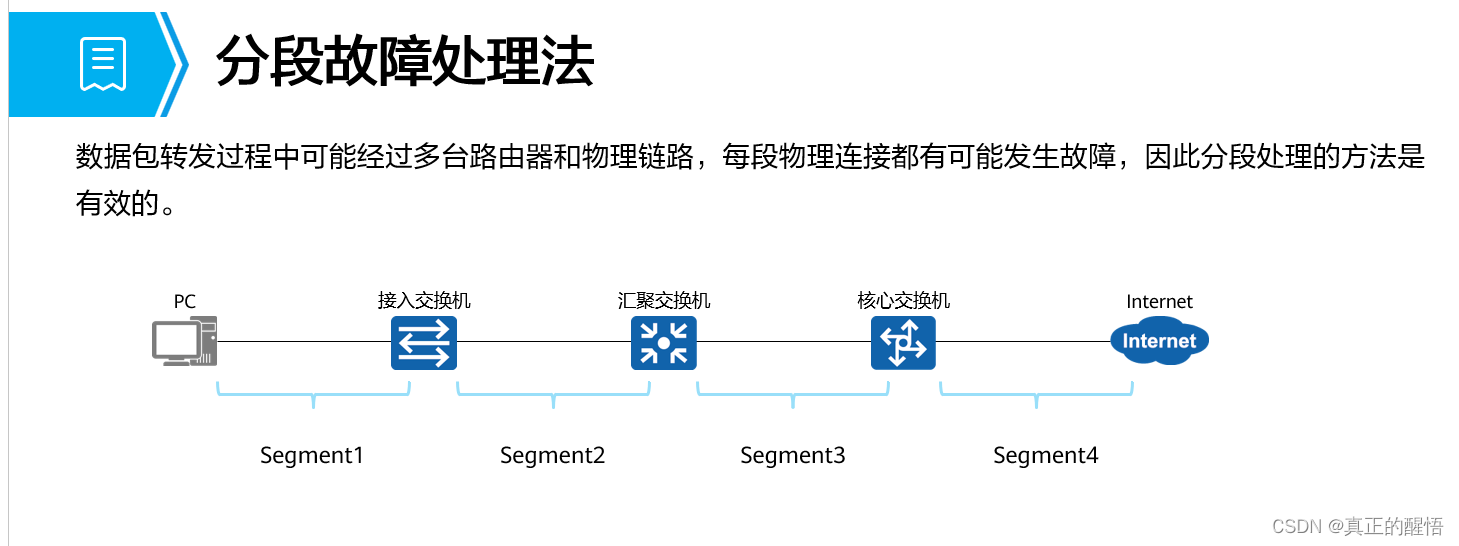
排错流程
如何排除错误?
排错思路一 利用ping 命?令哪里不通ping哪里
Welcome to use PC Simulator!
PC>ping 192.168.10.254
Ping 192.168.10.254: 32 data bytes, Press Ctrl_C to break
From 192.168.10.254: bytes=32 seq=1 ttl=255 time=47 ms
From 192.168.10.254: bytes=32 seq=2 ttl=255 time=31 ms
From 192.168.10.254: bytes=32 seq=3 ttl=255 time=31 ms
From 192.168.10.254: bytes=32 seq=4 ttl=255 time=31 ms
From 192.168.10.254: bytes=32 seq=5 ttl=255 time=31 ms
--- 192.168.10.254 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/34/47 ms
PC>ping 100.1.1.1
Ping 100.1.1.1: 32 data bytes, Press Ctrl_C to break
From 100.1.1.1: bytes=32 seq=1 ttl=255 time=16 ms
From 100.1.1.1: bytes=32 seq=2 ttl=255 time=16 ms
From 100.1.1.1: bytes=32 seq=3 ttl=255 time=15 ms
From 100.1.1.1: bytes=32 seq=4 ttl=255 time=16 ms
From 100.1.1.1: bytes=32 seq=5 ttl=255 time=31 ms
--- 100.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/18/31 ms
PC>ping 100.1.1.2
Ping 100.1.1.2: 32 data bytes, Press Ctrl_C to break
From 100.1.1.2: bytes=32 seq=1 ttl=254 time=47 ms
From 100.1.1.2: bytes=32 seq=2 ttl=254 time=31 ms
From 100.1.1.2: bytes=32 seq=3 ttl=254 time=47 ms
From 100.1.1.2: bytes=32 seq=4 ttl=254 time=47 ms
From 100.1.1.2: bytes=32 seq=5 ttl=254 time=31 ms
--- 100.1.1.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/40/47 ms
PC>ping 192.168.2.2
Ping 192.168.2.2: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 192.168.2.2 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>ping 192.168.2.1
Ping 192.168.2.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
From 192.168.2.1: bytes=32 seq=2 ttl=253 time=63 ms
From 192.168.2.1: bytes=32 seq=3 ttl=253 time=47 ms
From 192.168.2.1: bytes=32 seq=4 ttl=253 time=15 ms
From 192.168.2.1: bytes=32 seq=5 ttl=253 time=94 ms
--- 192.168.2.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 0/54/94 ms
PC>ping 192.168.2.2
Ping 192.168.2.2: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 192.168.2.2 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>tracert 100.1.1.2
traceroute to 100.1.1.2, 8 hops max
(ICMP), press Ctrl+C to stop
1 * * *
2 100.1.1.2 47 ms 47 ms 47 ms
PC>tracert 192.168.2.1
traceroute to 192.168.2.1, 8 hops max
(ICMP), press Ctrl+C to stop
1 * * *
2 100.1.1.2 47 ms 47 ms 46 ms
3 192.168.2.1 32 ms 47 ms 62 ms
PC>tracert 192.168.3.1
traceroute to 192.168.3.1, 8 hops max
(ICMP), press Ctrl+C to stop
1 * * *
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
PC>ping 200.1.1.1
Ping 200.1.1.1: 32 data bytes, Press Ctrl_C to break
From 200.1.1.1: bytes=32 seq=1 ttl=255 time=32 ms
From 200.1.1.1: bytes=32 seq=2 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=3 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=4 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=5 ttl=255 time=16 ms
--- 200.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 16/28/32 ms
PC>ping 200.1.1.2
Ping 200.1.1.2: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 200.1.1.2 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
Welcome to use PC Simulator!
PC>ping 192.168.20.254
Ping 192.168.20.254: 32 data bytes, Press Ctrl_C to break
From 192.168.20.254: bytes=32 seq=1 ttl=255 time=31 ms
From 192.168.20.254: bytes=32 seq=2 ttl=255 time=31 ms
From 192.168.20.254: bytes=32 seq=3 ttl=255 time=31 ms
From 192.168.20.254: bytes=32 seq=4 ttl=255 time=47 ms
From 192.168.20.254: bytes=32 seq=5 ttl=255 time=16 ms
--- 192.168.20.254 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 16/31/47 ms
PC>ping 200.1.1.1
Ping 200.1.1.1: 32 data bytes, Press Ctrl_C to break
From 200.1.1.1: bytes=32 seq=1 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=2 ttl=255 time=47 ms
From 200.1.1.1: bytes=32 seq=3 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=4 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=5 ttl=255 time=16 ms
--- 200.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 16/31/47 ms
PC>ping 200.1.1.2
Ping 200.1.1.2: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 200.1.1.2 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>
PC Simulator has not been started!
Welcome to use PC Simulator!
PC>ping 200.1.1.2
Ping 200.1.1.2: 32 data bytes, Press Ctrl_C to break
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
--- 192.168.20.254 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>ping 200.1.1.2
Ping 200.1.1.2: 32 data bytes, Press Ctrl_C to break
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
From 192.168.20.1: Destination host unreachable
--- 192.168.20.254 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>ping 192.168.20.254
Ping 192.168.20.254: 32 data bytes, Press Ctrl_C to break
From 192.168.20.1: Destination host unreachable
From 192.168.20.254: bytes=32 seq=1 ttl=255 time=47 ms
From 192.168.20.254: bytes=32 seq=2 ttl=255 time=31 ms
From 192.168.20.254: bytes=32 seq=3 ttl=255 time=47 ms
From 192.168.20.254: bytes=32 seq=4 ttl=255 time=31 ms
From 192.168.20.254: bytes=32 seq=5 ttl=255 time=16 ms
--- 192.168.20.254 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 16/34/47 ms
PC>ping 200.1.1.1
Ping 200.1.1.1: 32 data bytes, Press Ctrl_C to break
From 200.1.1.1: bytes=32 seq=1 ttl=255 time=31 ms
From 200.1.1.1: bytes=32 seq=2 ttl=255 time=32 ms
From 200.1.1.1: bytes=32 seq=3 ttl=255 time=47 ms
From 200.1.1.1: bytes=32 seq=4 ttl=255 time=46 ms
From 200.1.1.1: bytes=32 seq=5 ttl=255 time=32 ms
--- 200.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/37/47 ms
PC>ping 200.1.1.2
Ping 200.1.1.2: 32 data bytes, Press Ctrl_C to break
From 200.1.1.2: bytes=32 seq=1 ttl=254 time=94 ms
From 200.1.1.2: bytes=32 seq=2 ttl=254 time=31 ms
From 200.1.1.2: bytes=32 seq=3 ttl=254 time=32 ms
From 200.1.1.2: bytes=32 seq=4 ttl=254 time=31 ms
From 200.1.1.2: bytes=32 seq=5 ttl=254 time=47 ms
--- 200.1.1.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/47/94 ms
PC>ping 192.168.3.2
Ping 192.168.3.2: 32 data bytes, Press Ctrl_C to break
Request timeout!
From 192.168.3.2: bytes=32 seq=2 ttl=253 time=47 ms
From 192.168.3.2: bytes=32 seq=3 ttl=253 time=63 ms
From 192.168.3.2: bytes=32 seq=4 ttl=253 time=62 ms
From 192.168.3.2: bytes=32 seq=5 ttl=253 time=63 ms
--- 192.168.3.2 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 0/58/63 ms
PC>ping 192.168.3.1
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
From 192.168.3.1: bytes=32 seq=2 ttl=126 time=62 ms
From 192.168.3.1: bytes=32 seq=3 ttl=126 time=47 ms
From 192.168.3.1: bytes=32 seq=4 ttl=126 time=62 ms
From 192.168.3.1: bytes=32 seq=5 ttl=126 time=63 ms
--- 192.168.3.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 0/58/63 ms
PC>tracert 192.168.3.1
traceroute to 192.168.3.1, 8 hops max
(ICMP), press Ctrl+C to stop
1 * * *
2 200.1.1.2 31 ms 47 ms 47 ms
3 192.168.3.1 62 ms 63 ms 78 ms
PC>tracert 192.168.2.1
traceroute to 192.168.2.1, 8 hops max
(ICMP), press Ctrl+C to stop
1 * * *
2 100.1.1.2 31 ms 47 ms 31 ms
3 192.168.2.1 94 ms 62 ms 63 ms
排错思路二 抓包分析路径 看到哪里没有通
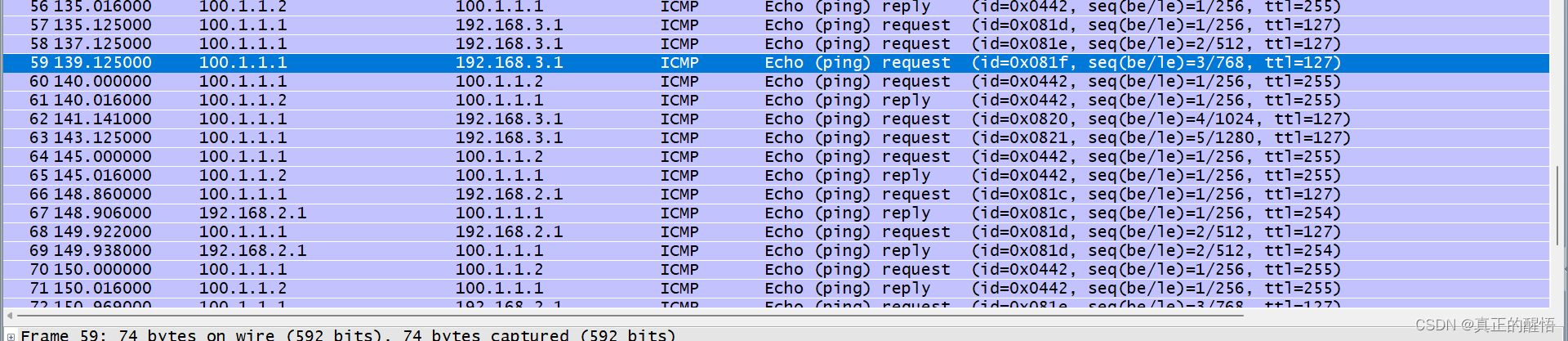
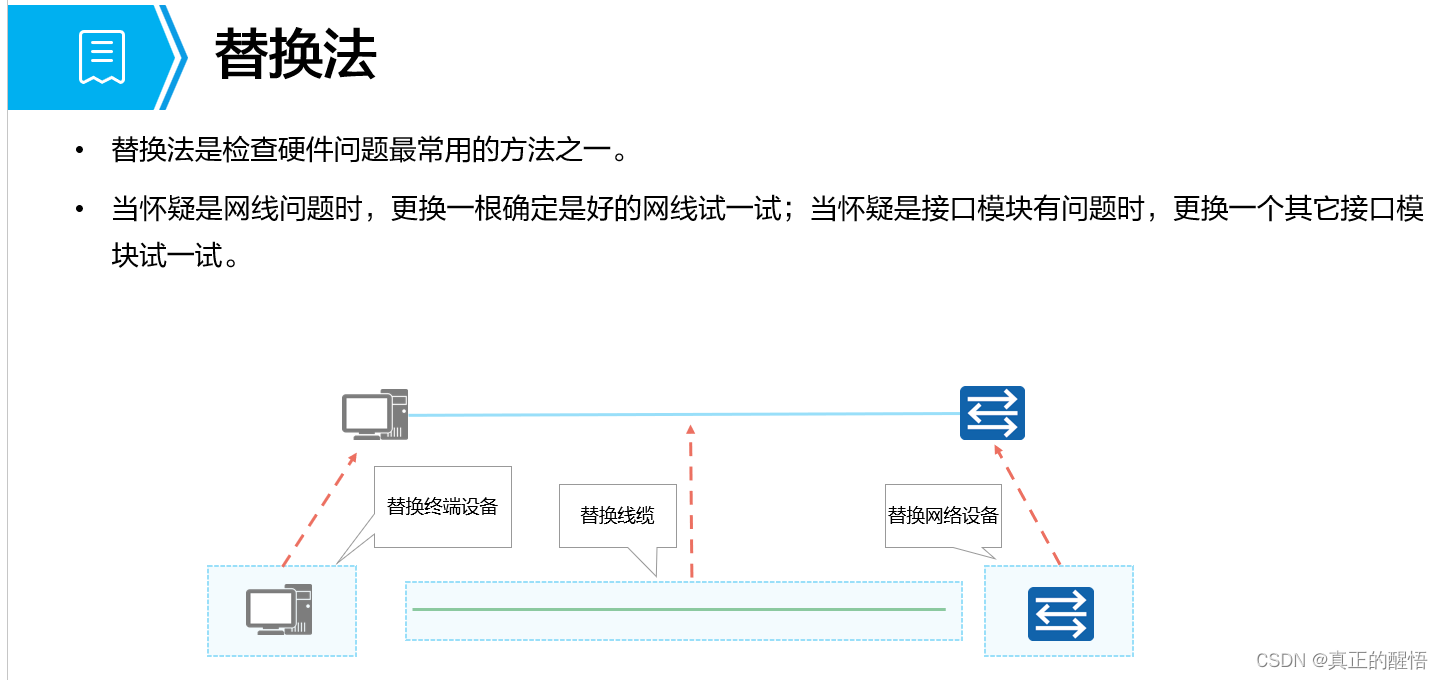
排错思路三 利用以下几种思路
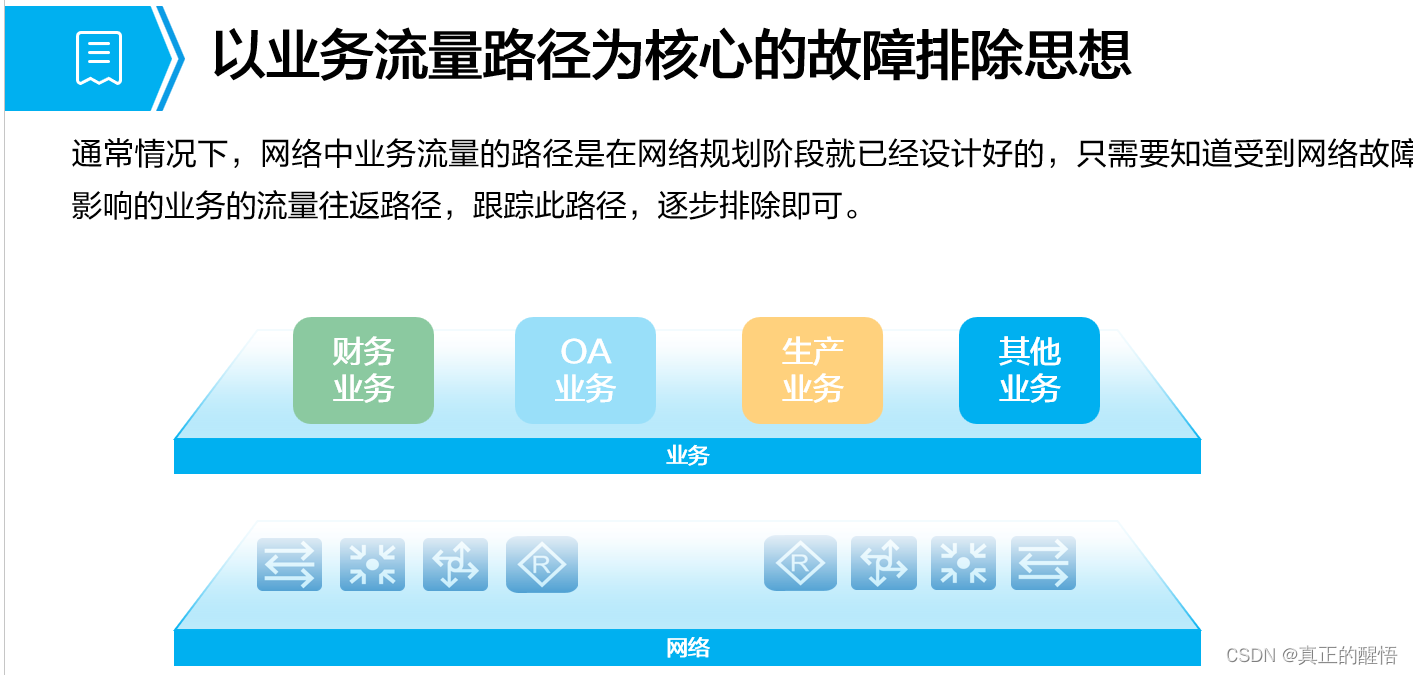
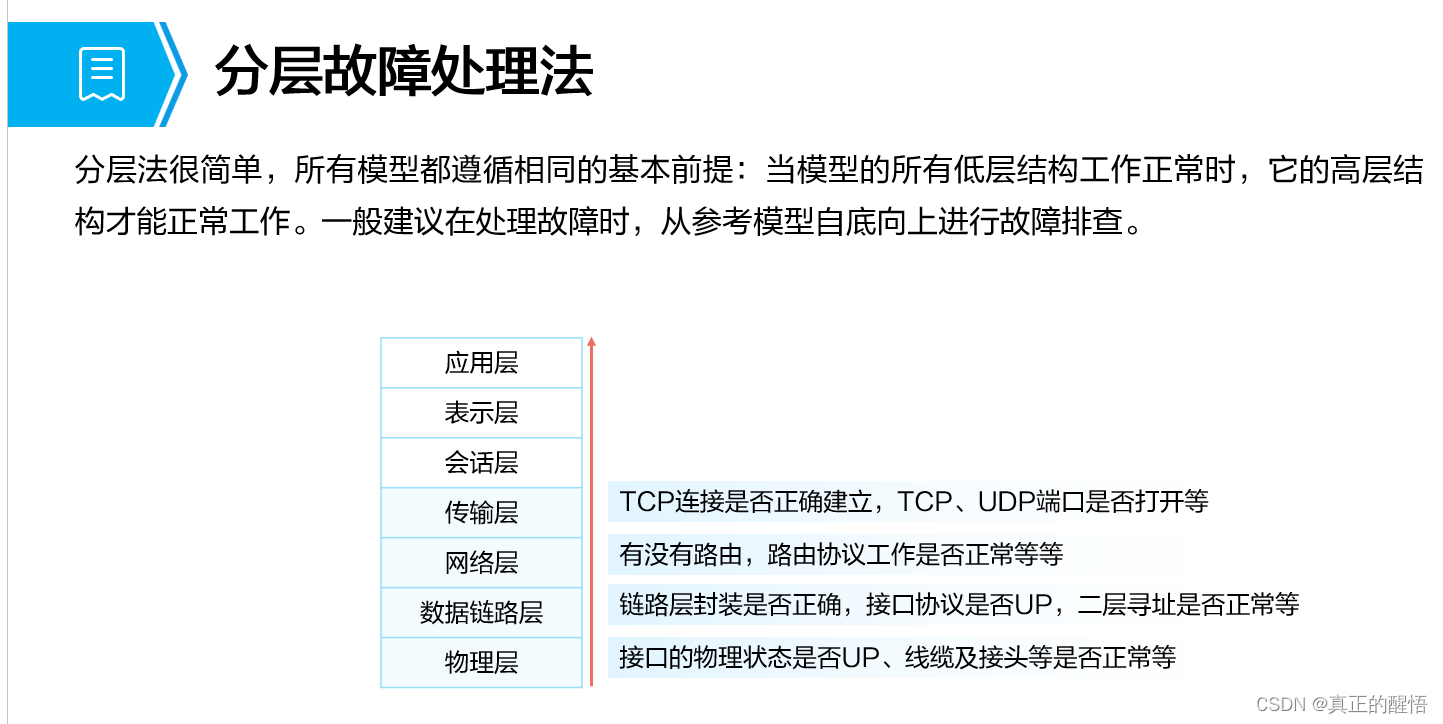

1 IP地址配置信息错误
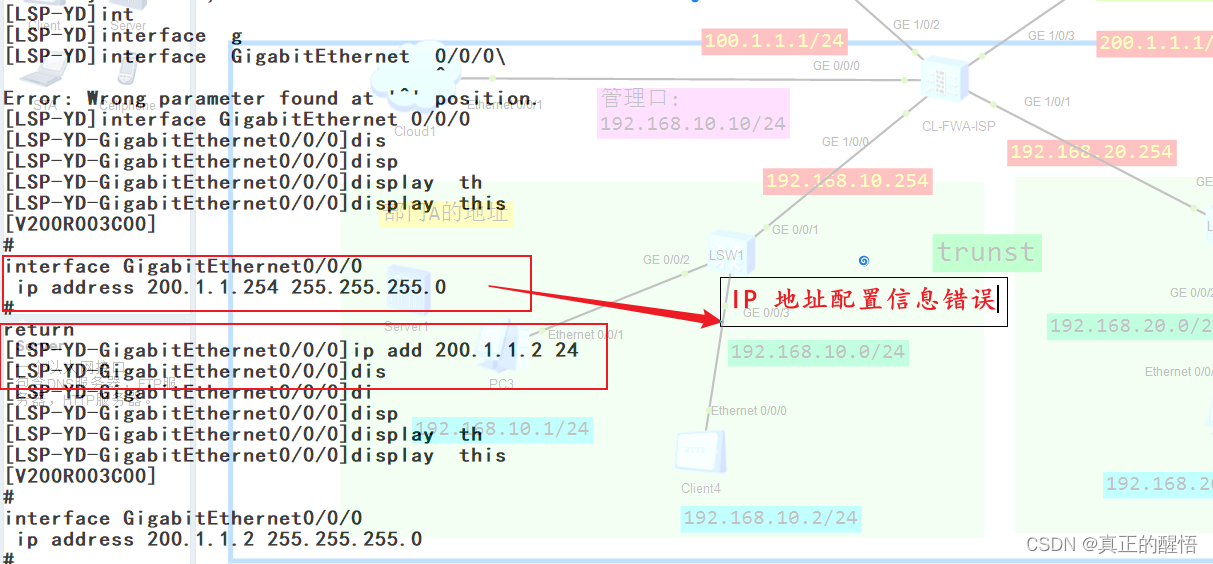

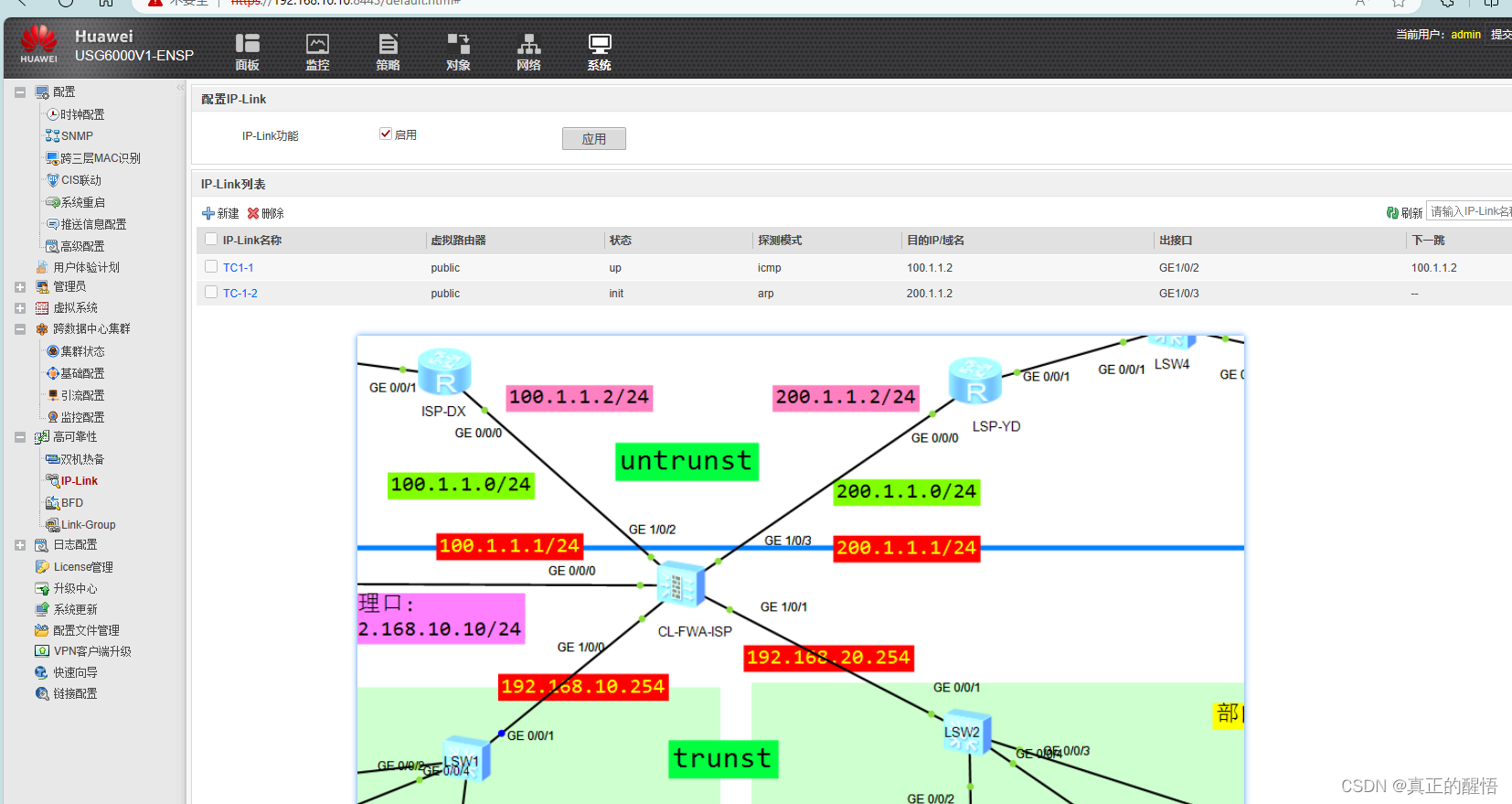
7 IP-Link探测
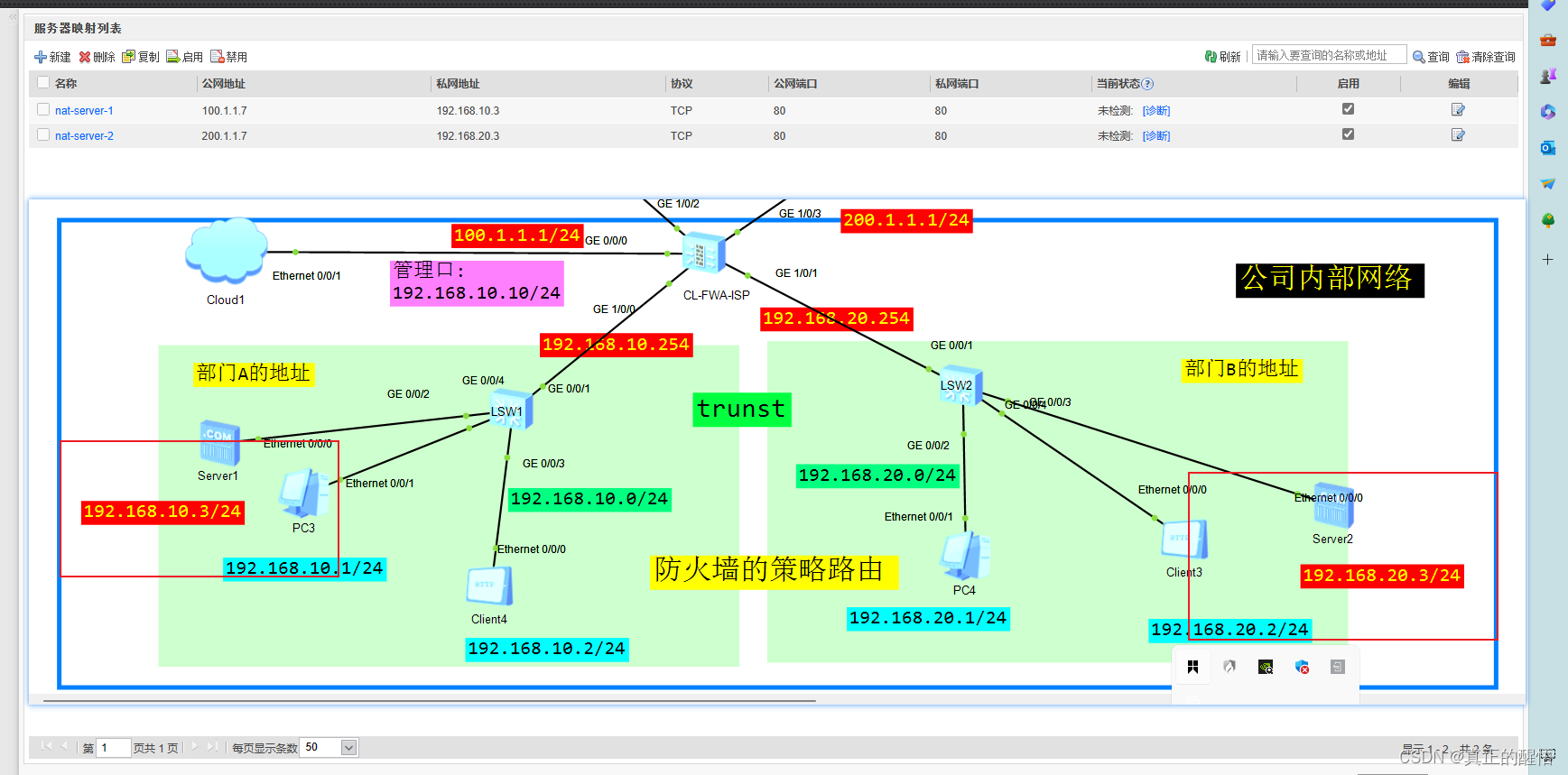
二 防火墙中的NAT-Server
1 新建立起安全策略

 2 配置映射
2 配置映射

3 测试

三 防火墙中的NAT地址池
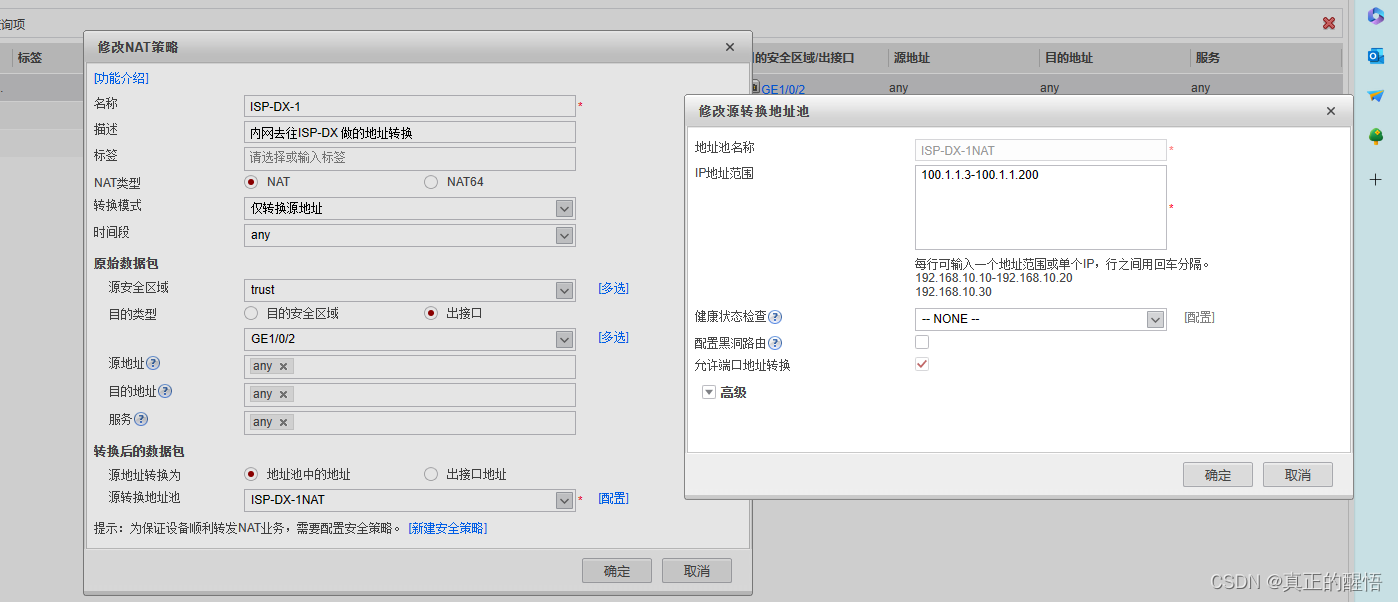
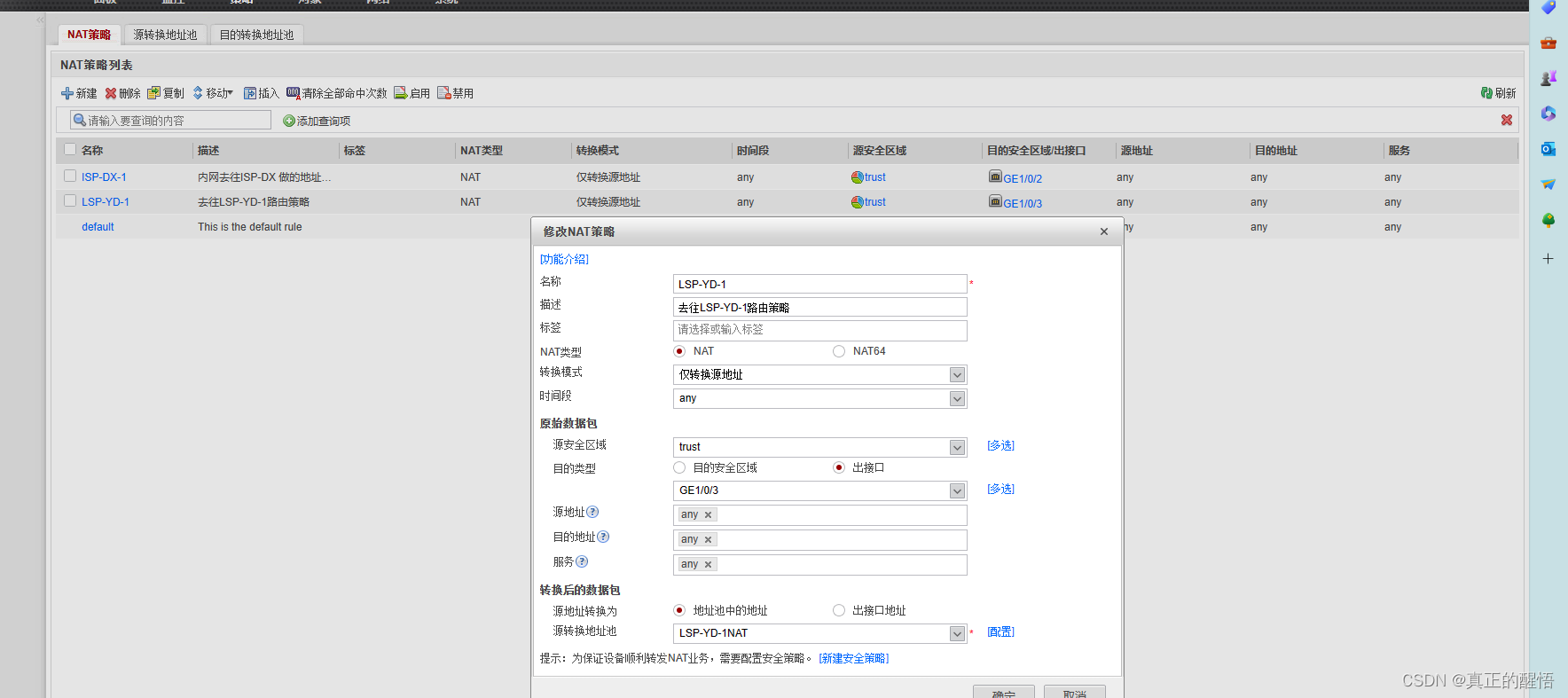

1024网络技术防火墙技术的学习防火墙中的NAT技术(第十二课)-CSDN博客
NAT介绍
NAT(Network Address Translation,网络地址转换)是一种在计算机网络中常用的技术,它将一个网络中的私有IP地址转换为公共IP地址,从而实现网络中设备的互联。
NAT主要分为三种类型:静态NAT,动态NAT和PAT(端口地址转换)。
-
静态NAT:将私有IP地址映射到一个公共IP地址上,这个映射关系是一对一的,即一台设备对应一个公共IP地址。静态NAT适用于固定的网络拓扑结构,网络设备的IP地址不会经常发生变化的场景。
-
动态NAT:动态NAT通常在一个局域网中使用,它将一个局域网中多个设备的私有IP地址映射到一个公共IP地址上,这个映射关系是多对一的。动态NAT适用于家庭和小型企业网络。
-
PAT:PAT是NAT的一种特殊形式,它通过一个公共IP地址和多个不同的端口号实现将多个设备的私有IP地址映射到公共IP地址上。PAT适用于大型网络环境中,可以使大量设备共享一个公共IP地址。
总的来说,NAT可以为网络的扩容提供了便捷性,但在一定程度上会影响到网络的性能。因此,在网络设计时需要考虑到网络规模和传输延迟等因素,以选择合适的NAT方式。
网络地址转换技术NAT(第九课)-CSDN博客
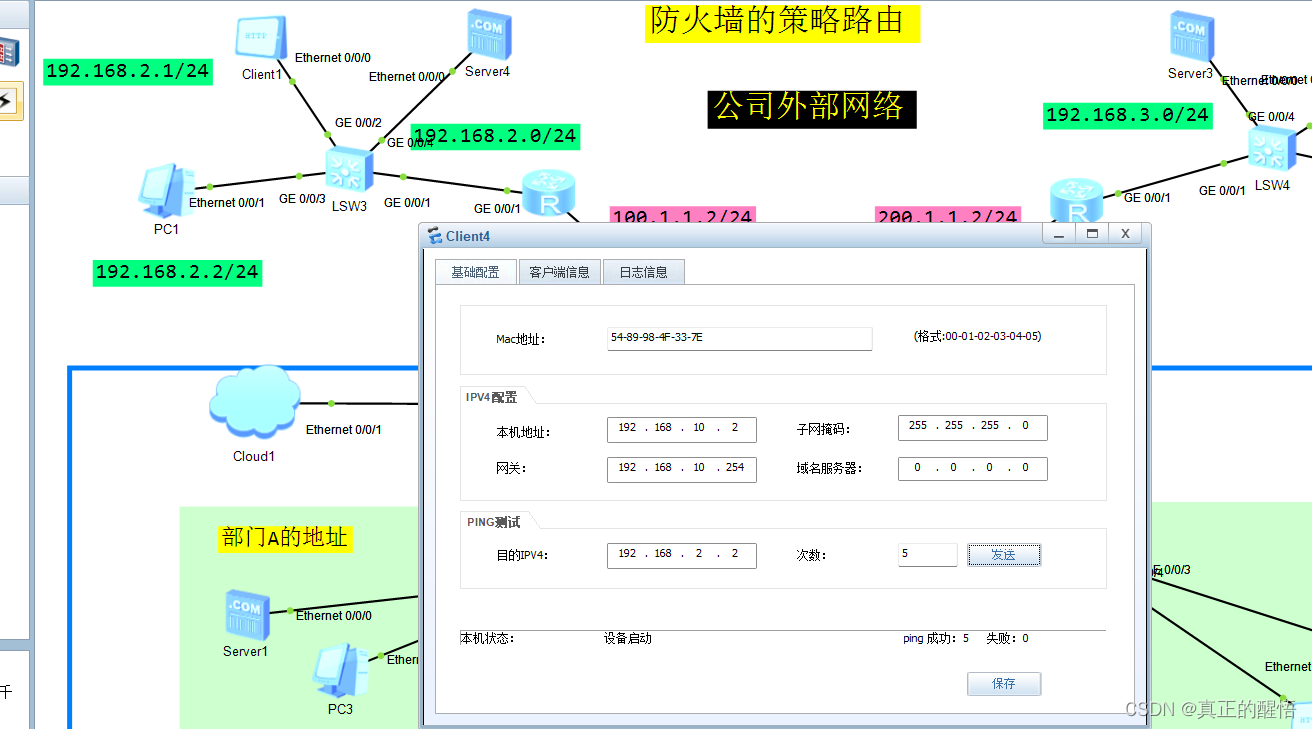
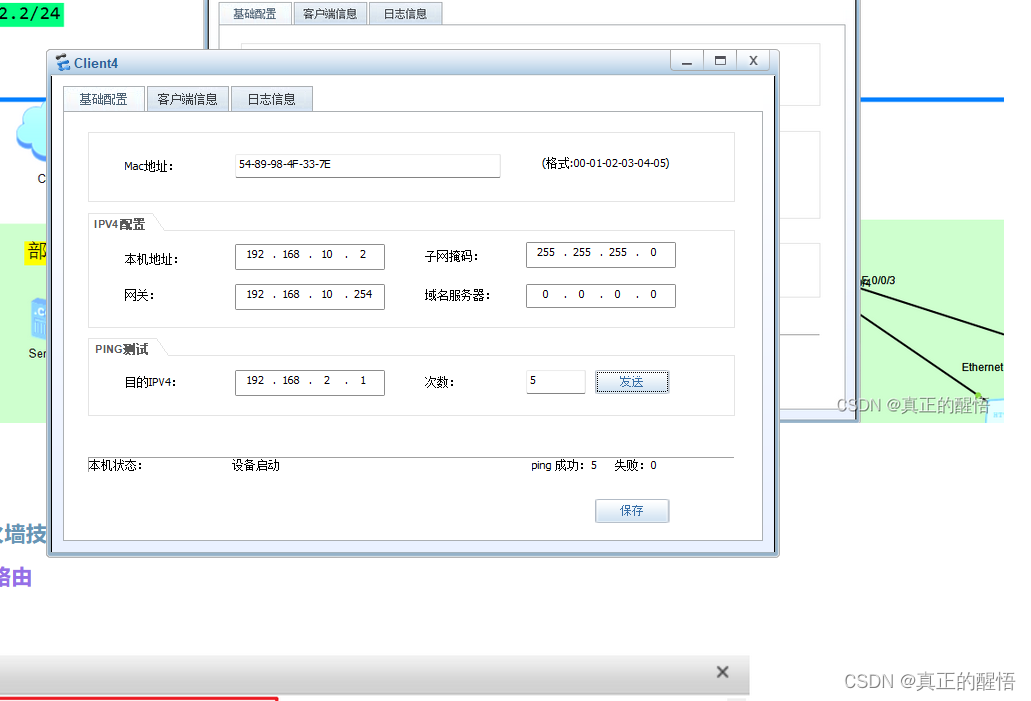
三 防火墙中的策路由
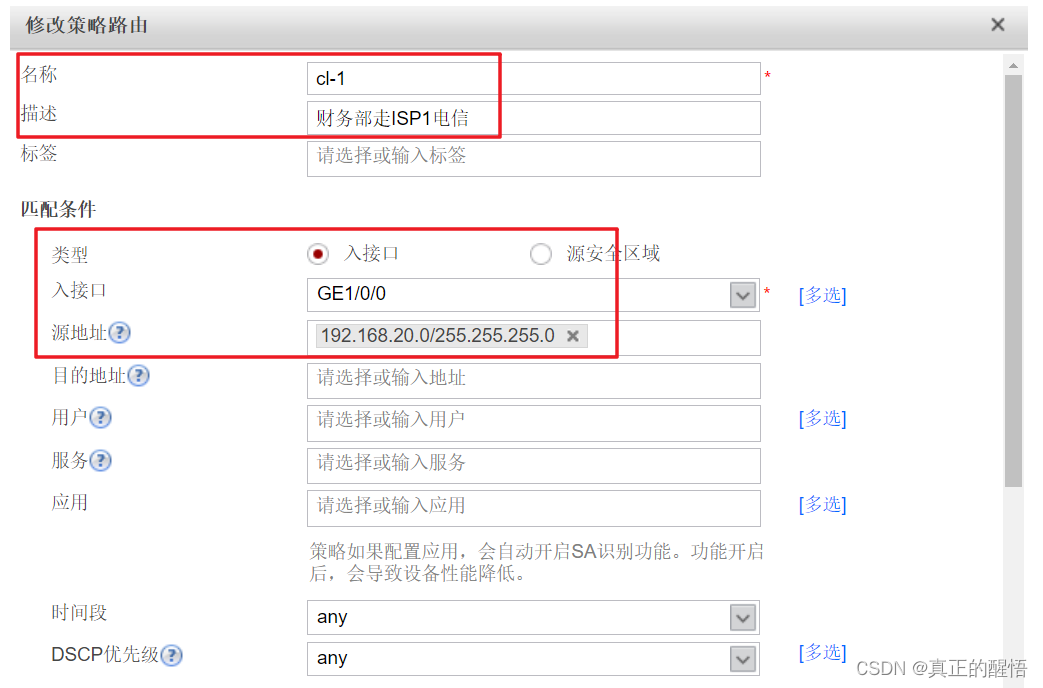
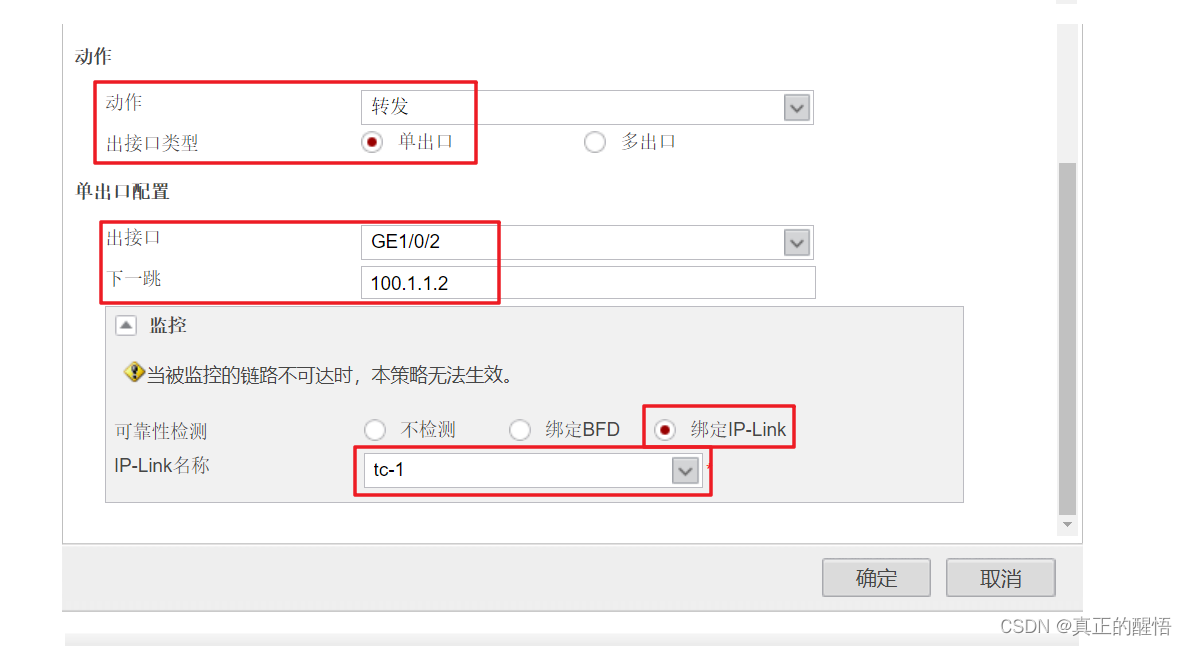
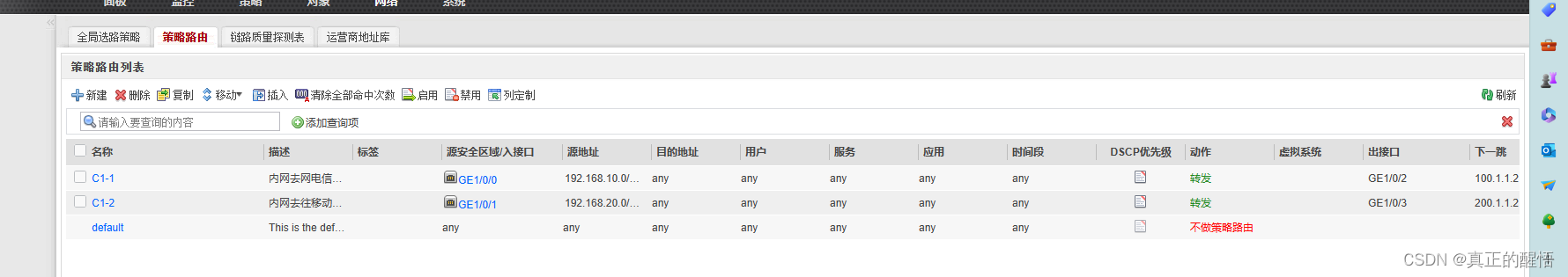
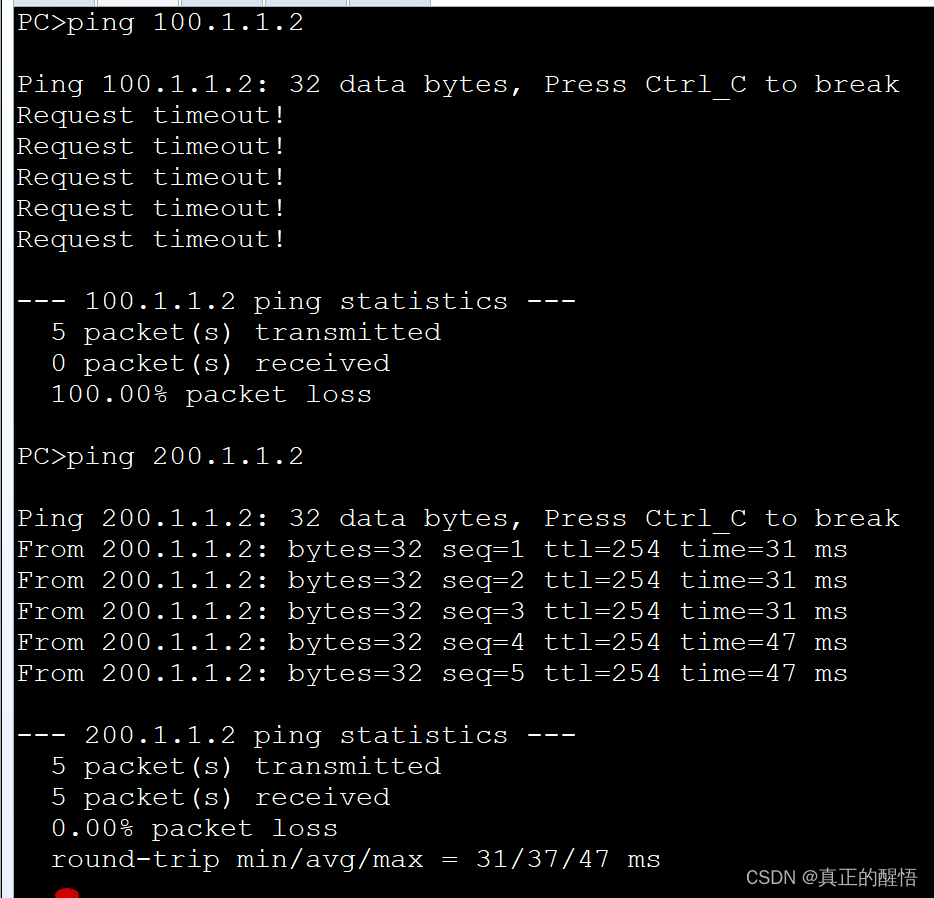
8 配置策略路由









![[计算机提升] Windows系统各种开机启动方式介绍](https://img-blog.csdnimg.cn/5a0bcc425f87495383a6c5b8ecaacb26.png)