规格
适用于V200R002C00及更高版本、所有形态的AR路由器。
组网需求
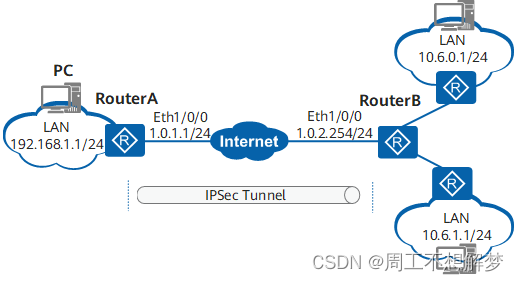
如图1所示,某企业分为总部和两个分支机构。分支机构1和分支机构2分别通过RouterB和RouterC与Internet相连。RouterA为NAT网关,总部RouterA和分支RouterB为固定公网地址,RouterC为动态公网IP地址;RouterA和RouterB以及RouterA和RouterC相互路由可达。企业要求实现如下组网需求:
- 分支机构PC2、PC3能与总部PC1之间进行安全通信。
- RouterA、RouterB以及RouterA、RouterC之间分别建立IPSec隧道。RouterB、RouterC不直接建立任何IPSec连接。
- PC1可以直接访问公网,PC2和PC3通过总部网关访问公网。
操作步骤
- 配置RouterA
<span style="color:#333333"><span style="background-color:#dddddd"># sysname RouterA # acl number 3000 rule 5 permit ip destination 10.1.2.0 0.0.0.255 rule 10 permit ip destination 10.1.3.0 0.0.0.255 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 10 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer c pre-shared-key %^%#0ljf5R_9LXP|Qe=WVA6-Y%'}%^%# ike-proposal 10 # ipsec policy-template temp 1 security acl 3000 ike-peer c proposal tran1 # ipsec policy map1 10 isakmp template temp # interface GigabitEthernet0/0/3 undo shutdown ip address 10.1.1.1 255.255.255.0 # interface GigabitEthernet0/0/1 undo shutdown ip address 1.1.3.1 255.255.255.0 ipsec policy map1 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/3 # firewall zone untrust set priority 5 add interface GigabitEthernet0/0/1 # ip route-static 0.0.0.0 0.0.0.0 1.1.3.2 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 destination-address 10.1.2.0 mask 255.255.255.0 destination-address 10.1.3.0 mask 255.255.255.0 action permit rule name policy2 source-zone untrust destination-zone trust source-address 10.1.2.0 mask 255.255.255.0 source-address 10.1.3.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 action permit rule name policy3 source-zone local destination-zone untrust source-address 1.1.3.1 mask 255.255.255.255 action permit rule name policy4 source-zone untrust destination-zone local destination-address 1.1.3.1 mask 255.255.255.255 action permit # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 destination-address 10.1.2.0 mask 255.255.255.0 destination-address 10.1.3.0 mask 255.255.255.0 action no-nat rule name policy_nat2 source-zone trust source-zone untrust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 source-address 10.1.2.0 mask 255.255.255.0 source-address 10.1.3.0 mask 255.255.255.0 action source-nat easy-ip # return</span></span> - 配置RouterB
<span style="color:#333333"><span style="background-color:#dddddd"># sysname RouterB # acl number 3000 rule 5 permit ip source 10.1.2.0 0.0.0.255 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 10 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer a pre-shared-key %^%#St4#CBb9$L>G`5W(HV*BKTnm%^%# ike-proposal 10 remote-address 1.1.3.1 # ipsec policy map1 10 isakmp security acl 3000 ike-peer a proposal tran1 # interface GigabitEthernet0/0/3 undo shutdown ip address 10.1.2.1 255.255.255.0 # interface GigabitEthernet0/0/1 undo shutdown ip address 1.1.5.1 255.255.255.0 ipsec policy map1 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/3 # firewall zone untrust set priority 5 add interface GigabitEthernet0/0/1 # ip route-static 10.1.0.0 255.255.0.0 GigabitEthernet0/0/1 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 10.1.2.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 10.1.3.0 mask 255.255.255.0 action permit rule name policy2 source-zone untrust destination-zone trust source-address 10.1.1.0 mask 255.255.255.0 source-address 10.1.3.0 mask 255.255.255.0 destination-address 10.1.2.0 mask 255.255.255.0 action permit rule name policy3 source-zone local destination-zone untrust source-address 1.1.5.1 mask 255.255.255.255 destination-address 1.1.3.1 mask 255.255.255.255 action permit rule name policy4 source-zone untrust destination-zone local source-address 1.1.3.1 mask 255.255.255.255 destination-address 1.1.5.1 mask 255.255.255.255 action permit # return</span></span> - 配置RouterC
<span style="color:#333333"><span style="background-color:#dddddd"># sysname RouterC # acl number 3000 rule 5 permit ip source 10.1.3.0 0.0.0.255 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 10 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer a pre-shared-key %^%#LV|sQ=~fUQO:M$CeqaMEnwVD%^%# ike-proposal 10 remote-address 1.1.3.1 # ipsec policy map1 10 isakmp security acl 3000 ike-peer a proposal tran1 # interface GigabitEthernet0/0/3 undo shutdown ip address 10.1.3.1 255.255.255.0 # interface GigabitEthernet0/0/1 /*configuration of obtaining IP*/ undo shutdown ipsec policy map1 # firewall zone trust set priority 85 add interface GigabitEthernet0/0/3 # firewall zone untrust set priority 5 add interface GigabitEthernet0/0/1 # ip route-static 10.1.0.0 255.255.0.0 GigabitEthernet0/0/1 # security-policy rule name policy1 source-zone trust destination-zone untrust source-address 10.1.3.0 mask 255.255.255.0 destination-address 10.1.1.0 mask 255.255.255.0 destination-address 10.1.2.0 mask 255.255.255.0 action permit rule name policy2 source-zone untrust destination-zone trust source-address 10.1.1.0 mask 255.255.255.0 source-address 10.1.2.0 mask 255.255.255.0 destination-address 10.1.3.0 mask 255.255.255.0 action permit rule name policy3 source-zone local destination-zone untrust destination-address 1.1.3.1 mask 255.255.255.255 action permit rule name policy4 source-zone untrust destination-zone local source-address 1.1.3.1 mask 255.255.255.255 action permit # return</span></span> - 验证配置结果。
- 配置完成后,PC1在任何时候都可以访问公网,可以ping通RouterB的1.1.5.1,同时在RouterA上可以查看NAT转换session表项。
<span style="color:#333333"><span style="background-color:#dddddd"><RouterA> <strong>display firewall session table</strong> Current Total Sessions : 5 icmp VPN:public --> public 10.1.1.2:61251[1.1.3.1:2048]-->1.1.5.1:2048 icmp VPN:public --> public 10.1.1.2:62019[1.1.3.1:2049]-->1.1.5.1:2048 icmp VPN:public --> public 10.1.1.2:62275[1.1.3.1:2050]-->1.1.5.1:2048 icmp VPN:public --> public 10.1.1.2:62531[1.1.3.1:2051]-->1.1.5.1:2048 icmp VPN:public --> public 10.1.1.2:62787[1.1.3.1:2052]-->1.1.5.1:2048</span></span> - PC2在任何时候可以访问到公网,可以ping通公网的IP地址(假设为1.1.6.1),同时在RouterA上可以查看NAT转换session表项。
<span style="color:#333333"><span style="background-color:#dddddd"><RouterA> <strong>display firewall session table</strong> Current Total Sessions : 5 icmp VPN:public --> public 10.1.2.2:61251[1.1.3.1:2053]-->1.1.6.1:2048 icmp VPN:public --> public 10.1.2.2:62019[1.1.3.1:2054]-->1.1.6.1:2048 icmp VPN:public --> public 10.1.2.2:62275[1.1.3.1:2055]-->1.1.6.1:2048 icmp VPN:public --> public 10.1.2.2:62531[1.1.3.1:2056]-->1.1.6.1:2048 icmp VPN:public --> public 10.1.2.2:62787[1.1.3.1:2057]-->1.1.6.1:2048</span></span> - PC2发起访问,之后PC1与PC2之间可以相互访问。
- 总部RouterA上可以查看到对应的IKE SA。
<span style="color:#333333"><span style="background-color:#dddddd"><RouterA> <strong>display ike sa</strong> IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------- 83887864 1.1.5.1:500 RD|A v2:2 IP 1.1.5.1 83887652 1.1.5.1:500 RD|A v2:1 IP 1.1.5.1 Number of IKE SA : 2 -------------------------------------------------------------------------- Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING </span></span> - 分支上RouterB可以查看到对端为总部的IKE SA,RouterB是发起方,标志位为ST。
<span style="color:#333333"><span style="background-color:#dddddd"><RouterB> <strong>display ike sa</strong> IKE SA information : Conn-ID Peer VPN Flag(s) Phase RemoteType RemoteID ------------------------------------------------------------------------- 62887864 1.1.3.1:500 RD|ST|A v2:2 IP 1.1.3.1 62887652 1.1.3.1:500 RD|ST|A v2:1 IP 1.1.3.1 Number of IKE SA : 2 ------------------------------------------------------------------------- Flag Description: RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING </span></span> - 总部RouterA上可以查看到一对双向的IPSec SA,对应分支RouterB。
<span style="color:#333333"><span style="background-color:#dddddd"><RouterA> <strong>display ipsec sa brief</strong> Current ipsec sa num:2 Spu board slot 1, cpu 1 ipsec sa information: Number of SAs:2 Src address Dst address SPI VPN Protocol Algorithm ------------------------------------------------------------------------------- 1.1.5.1 1.1.3.1 3923280450 ESP E:AES-256 A:SHA2_256_128 1.1.3.1 1.1.5.1 787858613 ESP E:AES-256 A:SHA2_256_128 </span></span> - 分支节点RouterB上可以查看到一对双向IPSec SA。
<span style="color:#333333"><span style="background-color:#dddddd"><RouterB> <strong>display ipsec sa brief</strong> Current ipsec sa num:2 Spu board slot 1, cpu 1 ipsec sa information: Number of SAs:2 Src address Dst address SPI VPN Protocol Algorithm ------------------------------------------------------------------------------- 1.1.3.1 1.1.5.1 787858613 ESP E:AES-256 A:SHA2_256_128 1.1.5.1 1.1.3.1 3923280450 ESP E:AES-256 A:SHA2_256_128 </span></span>
- 配置完成后,PC1在任何时候都可以访问公网,可以ping通RouterB的1.1.5.1,同时在RouterA上可以查看NAT转换session表项。