逆向这东西,不太好说。
base64
这是个pyc文件(python编译后的字节码文件),这东西可以直接用各种方法反编译。也可以不弄,必竟这应该签到级别的。用notepad打开,可以看到base64的编译和两个码表。显然猜是变表的base64,感觉逆向这东西如果不是水平够高就基本猜会更好。

然后就全靠厨子

UPX!
upx是一个常见加壳工具。解的方法也是它。脱壳以后也就是个普通程序。
a = bytes.fromhex('0A08020413011C570F381E5712382C095710382F571038130838350211541514023832373F4646461A')
xor(a,b'\x67')
#moectf{0h_y0u_Kn0w_H0w_to_Rev3rse_UPX!!!}xor
__int64 __fastcall main()
{
int i; // [rsp+2Ch] [rbp-34h]
unsigned __int8 input[29]; // [rsp+30h] [rbp-30h] BYREF
int v3; // [rsp+5Ch] [rbp-4h]
_main();
v3 = 0;
memset(input, 0, sizeof(input));
printf("Please input the flag:\n");
gets(input);
for ( i = 0; i < 28; ++i )
{
if ( enc[i] != (input[i] ^ 0x39) )
{
puts("Seems not right");
exit(0);
}
}
puts("GOOD!");
return 0i64;
}a = bytes.fromhex('54565C5A4D5F4260564C665257094E6651094E664D096661096B1844')
xor(x,b'\x39')
moectf{You_kn0w_h0w_t0_X0R!}ANDRIOD
android包逆向是逆向里一个常见类型,用jadx打开可以看到java写的代码。
先打开AndroidManifest.xml这是他的启动文件,打到代码起点。
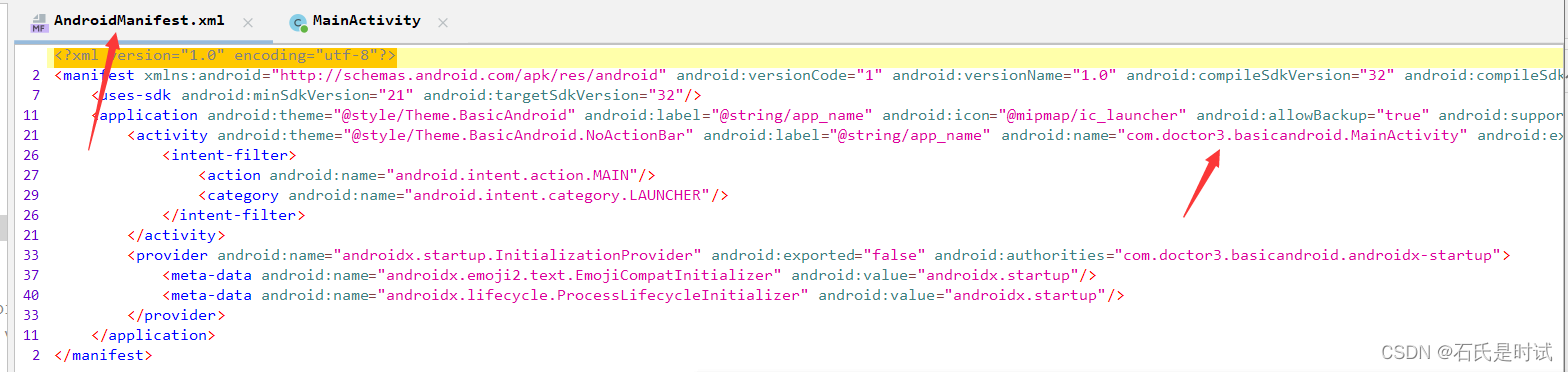
然后打开看代码。后边就跟其它的逆向一样了。也是个异或

enc = [25, 7, 0, 14, 27, 3, 16, 47, 24, 2, 9, 58, 4, 1, 58, 42, 11, 29, 6, 7, 12, 9, 48, 84, 24, 58, 28, 21, 27, 28, 16]
key = b'themoekey'
from pwn import xor
xor(bytes(enc),key)
#b'moectf{Java_in_Android_1s_easy}'RRRRc4
RC4加密是一种常见的逆向里用的加密方式。可以存个标准版。先用KEY初始S,然后生成加密流与明文进行异或。加密解密用同一断代码。
__int64 __fastcall sub_1400795E0(__int64 v5, __int64 v6, __int64 buf, int n38, __int64 v7, unsigned int n10)
{
__int64 result; // rax
int i; // [rsp+24h] [rbp+4h]
int j; // [rsp+24h] [rbp+4h]
int v9; // [rsp+24h] [rbp+4h]
int v10; // [rsp+44h] [rbp+24h]
int v11; // [rsp+44h] [rbp+24h]
char v12; // [rsp+64h] [rbp+44h]
char v13; // [rsp+64h] [rbp+44h]
int v14; // [rsp+A4h] [rbp+84h]
result = sub_14007555C(&unk_1401A7007);
v10 = 0;
v14 = 0;
for ( i = 0; i < 256; ++i )
{
*(_BYTE *)(v5 + i) = i;
*(_BYTE *)(v6 + i) = *(_BYTE *)(v7 + i % n10);
result = (unsigned int)(i + 1);
}
for ( j = 0; j < 256; ++j )
{
v10 = (*(unsigned __int8 *)(v6 + j) + *(unsigned __int8 *)(v5 + j) + v10) % 256;
v12 = *(_BYTE *)(v5 + v10);
*(_BYTE *)(v5 + v10) = *(_BYTE *)(v5 + j);
*(_BYTE *)(v5 + j) = v12;
result = (unsigned int)(j + 1);
}
v9 = 0;
v11 = 0;
while ( n38 )
{
v9 = (v9 + 1) % 256;
v11 = (*(unsigned __int8 *)(v5 + v9) + v11) % 256;
v13 = *(_BYTE *)(v5 + v11);
*(_BYTE *)(v5 + v11) = *(_BYTE *)(v5 + v9);
*(_BYTE *)(v5 + v9) = v13;
*(_BYTE *)(buf + v14++) ^= *(_BYTE *)(v5 + (*(unsigned __int8 *)(v5 + v11) + *(unsigned __int8 *)(v5 + v9)) % 256);
result = (unsigned int)--n38;
}
return result;
}
SMC
c程序由libc_start_main调用main函数,在这之前会先执行init数组里的函数,一般会在这里,或者直接在程序里写一小段代码,来恢复加密过的程序代码。这样让IDA失效。给逆向增加难度。
打开后程序是这样的,IDA处理不了

打开这个IDA处理不了的函数,
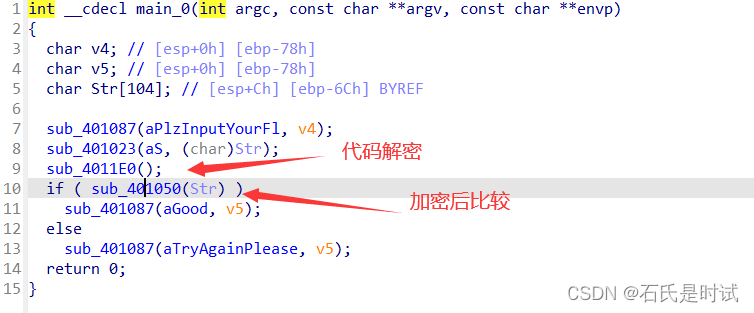
打开处理程序,然后恢复代码再看。
 得到加密逻辑
得到加密逻辑
解密
#1 恢复代码
data = list(open('SMC.exe','rb').read())
for i in range(122):
data[0x8d0+i]^=0x66
open('smc2.exe', 'wb').write(bytes(data))
#2 解密
a = bytes.fromhex('9F91A7A594A68DB5A79CA6A1BF91A453A653A5A3949B919E8F')
b = [(v^0x39)-57 for v in a]
bytes(b)
#moectf{Self_Mod1f1cation}EQUATION
将近1000行的代码
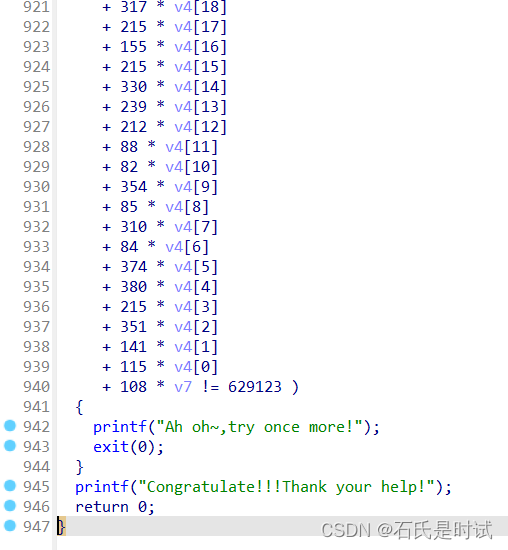
转出来用z3一把梭
from z3 import *
v4=[Int(f"v_{i}") for i in range(31)]
s=Solver()
for i in range(31):
s.add(v4[i]>0x20)
s.add(v4[i]<0x7f)
for i,v in enumerate(b'moectf{'):
s.add(v4[i] == v)
s.add(v4[30] == ord('}'))
s.add(334 * v4[28] + 100 * v4[27] + 369 * v4[26] + 124 * v4[25] + 278 * v4[24] + 158 * v4[23] + 162 * v4[22] + 145 * v4[19] + 27 * v4[17] + 91 * v4[15] + 195 * v4[14] + 342 * v4[13] + 391 * v4[10] + 204 * v4[9] + 302 * v4[8] + 153 * v4[7] + 292 * v4[6] + 382 * v4[5] + 221 * v4[4] + 316 * v4[3] + 118 * v4[2] + 295 * v4[1] + 247 * v4[0] + 236 * v4[11] + 27 * v4[12] + 361 * v4[16] + 81 * v4[18] + 105 * v4[20] + 65 * v4[21] + 67 * v4[29] + 41 * v4[30] == 596119)
s.add(371 * v4[29] + 338 * v4[28] + 269 * v4[27] + 312 * v4[26] + 67 * v4[25] + 299 * v4[24] + 235 * v4[23] + 294 * v4[22] + 303 * v4[21] + 211 * v4[20] + 122 * v4[19] + 333 * v4[18] + 341 * v4[15] + 111 * v4[14] + 253 * v4[13] + 68 * v4[12] + 347 * v4[11] + 44 * v4[10] + 262 * v4[9] + 357 * v4[8] + 323 * v4[5] + 141 * v4[4] + 329 * v4[3] + 378 * v4[2] + 316 * v4[1] + 235 * v4[0] + 59 * v4[6] + 37 * v4[7] + 264 * v4[16] + 73 * v4[17] + 126 * v4[30] == 634009)
s.add(337 * v4[29] + 338 * v4[28] + 118 * v4[27] + 82 * v4[26] + 239 * v4[21] + 58 * v4[20] + 304 * v4[19] + 330 * v4[18] + 377 * v4[17] + 306 * v4[16] + 221 * v4[13] + 345 * v4[12] + 124 * v4[11] + 272 * v4[10] + 270 * v4[9] + 229 * v4[8] + 377 * v4[7] + 373 * v4[6] + 297 * v4[5] + 112 * v4[4] + 386 * v4[3] + 90 * v4[2] + 361 * v4[1] + 236 * v4[0] + 386 * v4[14] + 73 * v4[15] + 315 * v4[22] + 33 * v4[23] + 141 * v4[24] + 129 * v4[25] + 123 * v4[30] == 685705)
s.add(367 * v4[29] + 55 * v4[28] + 374 * v4[27] + 150 * v4[24] + 350 * v4[23] + 141 * v4[22] + 124 * v4[21] + 366 * v4[20] + 230 * v4[19] + 307 * v4[18] + 191 * v4[17] + 153 * v4[12] + 383 * v4[11] + 145 * v4[10] + 109 * v4[9] + 209 * v4[8] + 158 * v4[7] + 221 * v4[6] + 188 * v4[5] + 22 * v4[4] + 146 * v4[3] + 306 * v4[2] + 230 * v4[1] + 13 * v4[0] + 287 * v4[13] + 257 * v4[14] + 137 * v4[15] + 7 * v4[16] + 52 * v4[25] + 31 * v4[26] + 355 * v4[30] == 557696)
s.add(100 * v4[29] + 191 * v4[28] + 362 * v4[27] + 55 * v4[26] + 210 * v4[25] + 359 * v4[24] + 348 * v4[21] + 83 * v4[20] + 395 * v4[19] + 350 * v4[16] + 291 * v4[15] + 220 * v4[12] + 196 * v4[11] + 399 * v4[8] + 68 * v4[7] + 84 * v4[6] + 281 * v4[5] + 334 * v4[4] + 53 * v4[3] + 399 * v4[2] + 338 * v4[0] + 18 * v4[1] + 148 * v4[9] + 21 * v4[10] + 174 * v4[13] + 36 * v4[14] + 2 * v4[17] + 41 * v4[18] + 137 * v4[22] + 24 * v4[23] + 368 * v4[30] == 538535)
s.add(188 * v4[29] + (v4[26] *2**7) + 93 * v4[25] + 248 * v4[24] + 83 * v4[23] + 207 * v4[22] + 217 * v4[19] + 309 * v4[16] + 16 * v4[15] + 135 * v4[14] + 251 * v4[13] + 200 * v4[12] + 49 * v4[11] + 119 * v4[10] + 356 * v4[9] + 398 * v4[8] + 303 * v4[7] + 224 * v4[6] + 208 * v4[5] + 244 * v4[4] + 209 * v4[3] + 189 * v4[2] + 302 * v4[1] + 395 * v4[0] + 314 * v4[17] + 13 * v4[18] + 310 * v4[20] + 21 * v4[21] + 67 * v4[27] + 127 * v4[28] + 100 * v4[30] == 580384)
s.add(293 * v4[29] + 343 * v4[28] + 123 * v4[27] + 387 * v4[26] + 114 * v4[25] + 303 * v4[24] + 248 * v4[23] + 258 * v4[21] + 218 * v4[20] + 180 * v4[19] + 196 * v4[18] + 398 * v4[17] + 398 * v4[14] + 138 * v4[9] + 292 * v4[8] + 38 * v4[7] + 179 * v4[6] + 190 * v4[5] + 57 * v4[4] + 358 * v4[3] + 191 * v4[2] + 215 * v4[1] + 88 * v4[0] + 22 * v4[10] + 72 * v4[11] + 357 * v4[12] + 9 * v4[13] + 389 * v4[15] + 81 * v4[16] + 85 * v4[30] == 529847)
s.add(311 * v4[29] + 202 * v4[28] + 234 * v4[27] + 272 * v4[26] + 55 * v4[25] + 328 * v4[24] + 246 * v4[23] + 362 * v4[22] + 86 * v4[21] + 75 * v4[20] + 142 * v4[17] + 244 * v4[16] + 216 * v4[15] + 281 * v4[14] + 398 * v4[13] + 322 * v4[12] + 251 * v4[11] + 357 * v4[8] + 76 * v4[7] + 292 * v4[6] + 389 * v4[5] + 275 * v4[4] + 312 * v4[3] + 200 * v4[2] + 110 * v4[1] + 203 * v4[0] + 99 * v4[9] + 21 * v4[10] + 269 * v4[18] + 33 * v4[19] + 356 * v4[30] == 631652)
s.add(261 * v4[29] + 189 * v4[26] + 55 * v4[25] + 23 * v4[24] + 202 * v4[23] + 185 * v4[22] + 182 * v4[21] + 285 * v4[20] + 217 * v4[17] + 157 * v4[16] + 232 * v4[15] + 132 * v4[14] + 169 * v4[13] + 154 * v4[12] + 121 * v4[11] + 389 * v4[10] + 376 * v4[9] + 292 * v4[6] + 225 * v4[5] + 155 * v4[4] + 234 * v4[3] + 149 * v4[2] + 241 * v4[1] + 312 * v4[0] + 368 * v4[7] + 129 * v4[8] + 226 * v4[18] + 288 * v4[19] + 201 * v4[27] + 288 * v4[28] + 69 * v4[30] == 614840)
s.add(60 * v4[29] + 118 * v4[28] + 153 * v4[27] + 139 * v4[26] + 23 * v4[25] + 279 * v4[24] + 396 * v4[23] + 287 * v4[22] + 237 * v4[19] + 266 * v4[18] + 149 * v4[17] + 193 * v4[16] + 395 * v4[15] + 97 * v4[14] + 16 * v4[13] + 286 * v4[12] + 105 * v4[11] + 88 * v4[10] + 282 * v4[9] + 55 * v4[8] + 134 * v4[7] + 114 * v4[6] + 101 * v4[5] + 116 * v4[4] + 271 * v4[3] + 186 * v4[2] + 263 * v4[1] + 313 * v4[0] + 149 * v4[20] + 129 * v4[21] + 145 * v4[30] == 510398)
s.add(385 * v4[29] + 53 * v4[28] + 112 * v4[27] + 8 * v4[26] + 232 * v4[25] + 145 * v4[24] + 313 * v4[23] + 156 * v4[22] + 321 * v4[21] + 358 * v4[20] + 46 * v4[19] + 382 * v4[18] + 144 * v4[16] + 222 * v4[14] + 329 * v4[13] + 161 * v4[12] + 335 * v4[11] + 50 * v4[10] + 373 * v4[9] + 66 * v4[8] + 44 * v4[7] + 59 * v4[6] + 292 * v4[5] + 39 * v4[4] + 53 * v4[3] + 310 * v4[0] + 154 * v4[1] + 24 * v4[2] + 396 * v4[15] + 81 * v4[17] + 355 * v4[30] == 558740)
s.add(249 * v4[29] + 386 * v4[28] + 313 * v4[27] + 74 * v4[26] + 22 * v4[25] + 168 * v4[24] + 305 * v4[21] + 358 * v4[20] + 191 * v4[19] + 202 * v4[18] + 14 * v4[15] + 114 * v4[14] + 224 * v4[13] + 134 * v4[12] + 274 * v4[11] + 372 * v4[10] + 159 * v4[9] + 233 * v4[8] + 70 * v4[7] + 287 * v4[6] + 297 * v4[5] + 318 * v4[4] + 177 * v4[3] + 173 * v4[2] + 270 * v4[1] + 163 * v4[0] + 77 * v4[16] + 25 * v4[17] + 387 * v4[22] + 18 * v4[23] + 345 * v4[30] == 592365)
s.add(392 * v4[29] + 385 * v4[28] + 302 * v4[27] + 13 * v4[25] + 27 * v4[24] + 99 * v4[22] + 343 * v4[19] + 324 * v4[18] + 223 * v4[17] + 372 * v4[16] + 261 * v4[15] + 181 * v4[14] + 203 * v4[13] + 232 * v4[12] + 305 * v4[11] + 393 * v4[10] + 325 * v4[9] + 231 * v4[8] + 92 * v4[7] + 142 * v4[6] + 22 * v4[5] + 86 * v4[4] + 264 * v4[3] + 300 * v4[2] + 387 * v4[1] + 360 * v4[0] + 225 * v4[20] + 127 * v4[21] + 2 * v4[23] + 80 * v4[26] + 268 * v4[30] == 619574)
s.add(270 * v4[28] + 370 * v4[27] + 235 * v4[26] + 96 * v4[22] + 85 * v4[20] + 150 * v4[19] + 140 * v4[18] + 94 * v4[17] + 295 * v4[16] + 19 * v4[14] + 176 * v4[12] + 94 * v4[11] + 258 * v4[10] + 302 * v4[9] + 171 * v4[8] + 66 * v4[7] + 278 * v4[6] + 193 * v4[5] + 251 * v4[4] + 284 * v4[3] + 218 * v4[2] + (v4[1] *2**6) + 319 * v4[0] + 125 * v4[13] + 24 * v4[15] + 267 * v4[21] + 160 * v4[23] + 111 * v4[24] + 33 * v4[25] + 174 * v4[29] + 13 * v4[30] == 480557)
s.add(87 * v4[28] + 260 * v4[27] + 326 * v4[26] + 210 * v4[25] + 357 * v4[24] + 170 * v4[23] + 315 * v4[22] + 376 * v4[21] + 227 * v4[20] + 43 * v4[19] + 358 * v4[18] + 364 * v4[17] + 309 * v4[16] + 282 * v4[15] + 286 * v4[14] + 365 * v4[13] + 287 * v4[12] + 377 * v4[11] + 74 * v4[10] + 225 * v4[9] + 328 * v4[6] + 223 * v4[5] + 120 * v4[4] + 102 * v4[3] + 162 * v4[2] + 123 * v4[1] + 196 * v4[0] + 29 * v4[7] + 27 * v4[8] + 352 * v4[30] == 666967)
s.add(61 * v4[29] + 195 * v4[28] + 125 * v4[27] + (v4[26] *2**6) + 260 * v4[25] + 202 * v4[24] + 116 * v4[23] + 230 * v4[22] + 326 * v4[21] + 211 * v4[20] + 371 * v4[19] + 353 * v4[16] + 124 * v4[13] + 188 * v4[12] + 163 * v4[11] + 140 * v4[10] + 51 * v4[9] + 262 * v4[8] + 229 * v4[7] + 100 * v4[6] + 113 * v4[5] + 158 * v4[4] + 378 * v4[3] + 365 * v4[2] + 207 * v4[1] + 277 * v4[0] + 190 * v4[14] + 320 * v4[15] + 347 * v4[17] + 11 * v4[18] + 137 * v4[30] == 590534)
s.add(39 * v4[28] + 303 * v4[27] + 360 * v4[26] + 157 * v4[25] + 324 * v4[24] + 77 * v4[23] + 308 * v4[22] + 313 * v4[21] + 87 * v4[20] + 201 * v4[19] + 50 * v4[18] + 60 * v4[17] + 28 * v4[16] + 193 * v4[15] + 184 * v4[14] + 205 * v4[13] + 140 * v4[12] + 311 * v4[11] + 304 * v4[10] + 35 * v4[9] + 356 * v4[8] + 23 * v4[5] + 85 * v4[4] + 156 * v4[3] + 16 * v4[2] + 26 * v4[1] + 157 * v4[0] + 150 * v4[6] + 72 * v4[7] + 58 * v4[29] == 429108)
s.add(157 * v4[29] + 137 * v4[28] + 71 * v4[27] + 269 * v4[26] + 161 * v4[25] + 317 * v4[20] + 296 * v4[19] + 385 * v4[18] + 165 * v4[13] + 159 * v4[12] + 132 * v4[11] + 296 * v4[10] + 162 * v4[7] + 254 * v4[4] + 172 * v4[3] + 132 * v4[0] + 369 * v4[1] + 257 * v4[2] + 134 * v4[5] + 384 * v4[6] + 53 * v4[8] + 255 * v4[9] + 229 * v4[14] + 129 * v4[15] + 23 * v4[16] + 41 * v4[17] + 112 * v4[21] + 17 * v4[22] + 222 * v4[23] + 96 * v4[24] + 126 * v4[30] == 563521)
s.add(207 * v4[29] + 83 * v4[28] + 111 * v4[27] + 35 * v4[26] + 67 * v4[25] + 138 * v4[22] + 223 * v4[21] + 142 * v4[20] + 154 * v4[19] + 111 * v4[18] + 341 * v4[17] + 175 * v4[16] + 259 * v4[15] + 225 * v4[14] + 26 * v4[11] + 334 * v4[10] + 250 * v4[7] + 198 * v4[6] + 279 * v4[5] + 301 * v4[4] + 193 * v4[3] + 334 * v4[2] + 134 * v4[0] + 37 * v4[1] + 183 * v4[8] + 5 * v4[9] + 270 * v4[12] + 21 * v4[13] + 275 * v4[23] + 48 * v4[24] + 163 * v4[30] == 493999)
s.add(393 * v4[29] + 176 * v4[28] + 105 * v4[27] + 162 * v4[26] + 148 * v4[25] + 281 * v4[24] + 300 * v4[23] + 342 * v4[18] + 262 * v4[17] + 152 * v4[12] + 43 * v4[11] + 296 * v4[10] + 273 * v4[9] + 75 * v4[6] + 18 * v4[4] + 217 * v4[2] + 132 * v4[1] + 112 * v4[0] + 210 * v4[3] + 72 * v4[5] + 113 * v4[7] + 40 * v4[8] + 278 * v4[13] + 24 * v4[14] + 77 * v4[15] + 11 * v4[16] + 55 * v4[19] + 255 * v4[20] + 241 * v4[21] + 13 * v4[22] + 356 * v4[30] == 470065)
s.add(369 * v4[29] + 231 * v4[28] + 285 * v4[25] + 290 * v4[24] + 297 * v4[23] + 189 * v4[22] + 390 * v4[21] + 345 * v4[20] + 153 * v4[19] + 114 * v4[18] + 251 * v4[17] + 340 * v4[16] + 44 * v4[15] + 58 * v4[14] + 335 * v4[13] + 359 * v4[12] + 392 * v4[11] + 181 * v4[8] + 103 * v4[7] + 229 * v4[6] + 175 * v4[5] + 208 * v4[4] + 92 * v4[3] + 397 * v4[2] + 349 * v4[1] + 356 * v4[0] + (v4[9] *2**6) + 5 * v4[10] + 88 * v4[26] + 40 * v4[27] + 295 * v4[30] == 661276)
s.add(341 * v4[27] + 40 * v4[25] + 374 * v4[23] + 201 * v4[22] + 77 * v4[21] + 215 * v4[20] + 283 * v4[19] + 213 * v4[18] + 392 * v4[17] + 224 * v4[16] + v4[15] + 270 * v4[12] + 28 * v4[11] + 75 * v4[8] + 386 * v4[7] + 298 * v4[6] + 170 * v4[5] + 287 * v4[4] + 247 * v4[3] + 204 * v4[2] + 103 * v4[1] + 21 * v4[0] + 84 * v4[9] + 27 * v4[10] + 159 * v4[13] + 192 * v4[14] + 213 * v4[24] + 129 * v4[26] + 67 * v4[28] + 27 * v4[29] + 361 * v4[30] == 555288)
s.add(106 * v4[29] + 363 * v4[28] + 210 * v4[27] + 171 * v4[26] + 289 * v4[25] + 240 * v4[24] + 164 * v4[23] + 342 * v4[22] + 391 * v4[19] + 304 * v4[18] + 218 * v4[17] + 32 * v4[16] + 350 * v4[15] + 339 * v4[12] + 303 * v4[11] + 222 * v4[10] + 298 * v4[9] + 47 * v4[8] + 48 * v4[6] + 264 * v4[4] + 113 * v4[3] + 275 * v4[2] + 345 * v4[1] + 312 * v4[0] + 171 * v4[5] + 384 * v4[7] + 175 * v4[13] + 5 * v4[14] + 113 * v4[20] + 19 * v4[21] + 263 * v4[30] == 637650)
s.add(278 * v4[29] + 169 * v4[28] + 62 * v4[27] + 119 * v4[26] + 385 * v4[25] + 289 * v4[24] + 344 * v4[23] + 45 * v4[20] + 308 * v4[19] + 318 * v4[18] + 270 * v4[17] + v4[16] + 323 * v4[15] + 332 * v4[14] + 287 * v4[11] + 170 * v4[10] + 163 * v4[9] + 301 * v4[8] + 303 * v4[7] + 23 * v4[6] + 327 * v4[5] + 169 * v4[3] + 28 * v4[0] + 365 * v4[1] + 15 * v4[2] + 352 * v4[12] + 72 * v4[13] + 140 * v4[21] + 65 * v4[22] + 346 * v4[30] == 572609)
s.add(147 * v4[29] + 88 * v4[28] + 143 * v4[27] + 237 * v4[26] + 63 * v4[24] + 281 * v4[22] + 388 * v4[21] + 142 * v4[20] + 208 * v4[19] + 60 * v4[18] + 354 * v4[15] + 88 * v4[14] + 146 * v4[13] + 290 * v4[12] + 349 * v4[11] + 43 * v4[10] + 230 * v4[9] + 267 * v4[6] + 136 * v4[5] + 383 * v4[4] + 35 * v4[3] + 226 * v4[2] + 385 * v4[1] + 238 * v4[0] + 348 * v4[7] + 20 * v4[8] + 158 * v4[16] + 21 * v4[17] + 249 * v4[23] + 9 * v4[25] + 343 * v4[30] == 603481)
s.add(29 * v4[29] + 323 * v4[26] + 159 * v4[25] + 118 * v4[20] + 326 * v4[19] + 211 * v4[18] + 225 * v4[17] + 355 * v4[16] + 201 * v4[15] + 149 * v4[14] + 296 * v4[13] + 184 * v4[12] + 315 * v4[11] + 364 * v4[10] + 142 * v4[9] + 75 * v4[8] + 313 * v4[7] + 142 * v4[6] + 396 * v4[5] + 348 * v4[4] + 272 * v4[3] + 26 * v4[2] + 206 * v4[1] + 173 * v4[0] + 155 * v4[21] + 144 * v4[22] + 366 * v4[23] + 257 * v4[24] + 148 * v4[27] + 24 * v4[28] + 253 * v4[30] == 664504)
s.add(4 * v4[29] + 305 * v4[28] + 226 * v4[27] + 212 * v4[26] + 175 * v4[25] + 93 * v4[24] + 165 * v4[23] + 341 * v4[20] + 14 * v4[19] + 394 * v4[18] + (v4[17] *2**8) + 252 * v4[16] + 336 * v4[15] + 38 * v4[14] + 82 * v4[13] + 155 * v4[12] + 215 * v4[11] + 331 * v4[10] + 230 * v4[9] + 241 * v4[8] + 225 * v4[7] + 186 * v4[4] + 90 * v4[3] + 50 * v4[2] + 62 * v4[1] + 34 * v4[0] + 237 * v4[5] + 11 * v4[6] + 336 * v4[21] + 36 * v4[22] + 29 * v4[30] == 473092)
s.add(353 * v4[29] + 216 * v4[28] + 252 * v4[27] + 8 * v4[26] + 62 * v4[25] + 233 * v4[24] + 254 * v4[23] + 303 * v4[22] + 234 * v4[21] + 303 * v4[20] + (v4[19] *2**8) + 148 * v4[18] + 324 * v4[17] + 317 * v4[16] + 213 * v4[15] + 309 * v4[14] + 28 * v4[13] + 280 * v4[11] + 118 * v4[10] + 58 * v4[9] + 50 * v4[8] + 155 * v4[7] + 161 * v4[6] + (v4[5] *2**6) + 303 * v4[4] + 76 * v4[3] + 43 * v4[2] + 109 * v4[1] + 102 * v4[0] + 93 * v4[30] == 497492)
s.add(89 * v4[29] + 148 * v4[28] + 82 * v4[27] + 53 * v4[26] + 274 * v4[25] + 220 * v4[24] + 202 * v4[23] + 123 * v4[22] + 231 * v4[21] + 169 * v4[20] + 278 * v4[19] + 259 * v4[18] + 208 * v4[17] + 219 * v4[16] + 371 * v4[15] + 181 * v4[12] + 104 * v4[11] + 392 * v4[10] + 285 * v4[9] + 113 * v4[8] + 298 * v4[7] + 389 * v4[6] + 322 * v4[5] + 338 * v4[4] + 237 * v4[3] + 234 * v4[0] + 261 * v4[1] + 10 * v4[2] + 345 * v4[13] + 3 * v4[14] + 361 * v4[30] == 659149)
s.add(361 * v4[29] + 359 * v4[28] + 93 * v4[27] + 315 * v4[26] + 69 * v4[25] + 137 * v4[24] + 69 * v4[23] + 58 * v4[22] + 300 * v4[21] + 371 * v4[20] + 264 * v4[19] + 317 * v4[18] + 215 * v4[17] + 155 * v4[16] + 215 * v4[15] + 330 * v4[14] + 239 * v4[13] + 212 * v4[12] + 88 * v4[11] + 82 * v4[10] + 354 * v4[9] + 85 * v4[8] + 310 * v4[7] + 84 * v4[6] + 374 * v4[5] + 380 * v4[4] + 215 * v4[3] + 351 * v4[2] + 141 * v4[1] + 115 * v4[0] + 108 * v4[30] == 629123 )
if s.check()==sat:
d=s.model()
print(bytes([d[v4[i]].as_long() for i in range(31)]))
#moectf{y0u_s0lv3d_Equati0ns!!!}junk_code
int __cdecl main_0(int argc, const char **argv, const char **envp)
{
char Str[18]; // [esp+E8h] [ebp-30h] BYREF
_BYTE v5[26]; // [esp+FAh] [ebp-1Eh] BYREF
__CheckForDebuggerJustMyCode(&unk_543007);
j__puts("welcome to moectf\nyour flag:");
v5[18] = 0;
sub_4591AE("%36s", Str);
if ( j__strlen(Str) >> 1 == 18 )
{
if ( check1(Str, 18) && check2(v5, 18) )
j__puts("congratulations!!!");
else
j__puts("WORNG!");
return 0;
}
else
{
j__puts("WORNG!");
return 0;
}
}
int __cdecl check1_0(char *a1, int a2)
{
char v3; // [esp+D3h] [ebp-3Dh]
int i; // [esp+DCh] [ebp-34h]
int j; // [esp+DCh] [ebp-34h]
int k; // [esp+DCh] [ebp-34h]
int v7[4]; // [esp+F4h] [ebp-1Ch] BYREF
__int16 v8; // [esp+104h] [ebp-Ch]
memset(v7, 0, sizeof(v7));
v8 = 0;
for ( i = 0; i < a2; ++i )
{
v3 = *a1++;
*((_BYTE *)v7 + i) = v3; // flag前18字节
}
for ( j = 0; j < a2; ++j )
*((_BYTE *)v7 + j) -= 5;
for ( k = 0; k < a2; ++k )
{
if ( aHjOavtPzmHQ[k] != *((_BYTE *)v7 + k) )
return 0;
}
return 1;
}
BOOL __cdecl check2_0(char *Str2, signed int MaxCount)
{
signed int i; // [esp+D4h] [ebp-8h]
for ( i = 0; i < MaxCount; ++i )
Str2[i] ^= 0x66u;
return j__strncmp(Str1, Str2, MaxCount) == 0;
}分两段加密
a = b'hj`^oavt+pZm`h+q._'
bytes([v+5 for v in a])
a = bytes.fromhex('39120E55390C13080D39055602554747471B')
bytes([v^0x66 for v in a])
#moectf{y0u_rem0v3d_th3_junk_c0d3!!!}rust

面向对象的程序读起来都极其复杂。好在这东西一般都不难,看到这个BitXor也就清楚怎么处理了,后边0x88是异或的值。
v25 = [0]*30
v25[0] = -27
v25[1] = -25
v25[2] = -19
v25[3] = -21
v25[4] = -4
v25[5] = -18
v25[6] = -13
v25[7] = -38
v25[8] = -3
v25[9] = -5
v25[10] = -4
v25[11] = -41
v25[12] = -6
v25[13] = -19
v25[14] = -2
v25[15] = -41
v25[16] = -1
v25[17] = -31
v25[18] = -28
v25[19] = -28
v25[20] = -41
v25[21] = -22
v25[22] = -19
v25[23] = -41
v25[24] = -23
v25[25] = -1
v25[26] = -18
v25[27] = -3
v25[28] = -71
v25[29] = -11
#HIBYTE(v21.pieces.length) = _$LT$$RF$u8$u20$as$u20$core..ops..bit..BitXor$LT$u8$GT$$GT$::bitxor::h0f0af3b6f52b4b37(*(u8 **)v21.fmt.gap0,0x88u);
bytes([(136^v)&0xff for v in v25])
#moectf{Rust_rev_will_be_awfu1}ezandroid
由于Android的可反编译性,为加强安全性,增加了个JUI功能,就是编译后的代码作为动态库载入。

java.apk文件本身是个zip压缩包,改扩展名为zip后解出libezandroid.so文件,然后用IDA打开找到对应的check函数
_BOOL8 __fastcall check(_BYTE *a1)
{
_BYTE *v1; // rax
bool v3; // [rsp+Fh] [rbp-19h]
char *v4; // [rsp+10h] [rbp-18h]
_BOOL4 v6; // [rsp+24h] [rbp-4h]
v4 = &asc_3C30[18];
while ( 2 )
{
v3 = 0;
if ( *a1 )
v3 = *v4 != 42;
if ( v3 )
{
v1 = a1++;
switch ( *v1 )
{
case 'a':
--v4;
continue;
case 'd':
++v4;
continue;
case 's':
v4 += 15;
continue;
case 'w':
v4 -= 15;
continue;
default:
v6 = 0;
break;
}
}
else
{
v6 = *v4 == 35;
}
break;
}
return v6;
}用上下左右来走,显然是个迷宫题,需要手搓,从@走到#就OK了,现在难的题都发展到三维迷宫了。
'''
***************
***@***********
***.***********
*...****#..****
*.********.****
*.****.....****
*.****.********
*......********
***************
'''
moectf{ssaassssdddddwwddddwwaa}GUI
原理一样,找到加密函数
int __cdecl enc(int a1, int a2)
{
int v3; // [esp+F8h] [ebp-54h]
_WORD *v4; // [esp+104h] [ebp-48h]
char v5[32]; // [esp+11Ch] [ebp-30h] BYREF
int v6; // [esp+148h] [ebp-4h]
__CheckForDebuggerJustMyCode(&unk_528026);
sub_4519E6(v5);
v6 = 0;
v4 = (_WORD *)sub_450956(a2);
v3 = sub_45017C(a2);
while ( v4 != (_WORD *)v3 )
sub_4516B7((*v4++ - 5) ^ 0x51);
sub_4510C7(v5);
v6 = -1;
sub_4529B8(v5);
return a1;
}a = bytes.fromhex('393B310F3E302713017D7070037D380E7A237C0B1A3C7D397F3C4D4D4D29')
bytes([(0x51^v)+5 for v in a])
#moectf{GU1&&W1nd0w2_Pr1m3r!!!}
unwind
这是个tea加密,就是相互加左移右移加key加delta,不过这个弄得很复杂,不仅有多次加密还有不同的key
int __cdecl sub_415700(unsigned int *a1, _DWORD *a2)
{
int i; // [esp+D0h] [ebp-68h]
unsigned int v4; // [esp+118h] [ebp-20h]
unsigned int v5; // [esp+124h] [ebp-14h]
int v6; // [esp+130h] [ebp-8h]
__CheckForDebuggerJustMyCode(&unk_41C063);
v6 = 0;
v5 = *a1;
v4 = a1[1];
for ( i = 0; i < 32; ++i )
{
v6 -= 0x61C88647;
v5 += (a2[1] + (v4 >> 5)) ^ (v6 + v4) ^ (*a2 + 16 * v4);
v4 += (a2[3] + (v5 >> 5)) ^ (v6 + v5) ^ (a2[2] + 16 * v5);
}
*a1 = v5;
a1[1] = v4;
return ++dword_41A5BC;
}
int sub_411B50()
{
__CheckForDebuggerJustMyCode(&unk_41C063);
sub_41136B((int)&unk_41A598, (int)aDx3906);
sub_41136B((int)&unk_41A5A0, (int)aDoctor3);
sub_41136B((int)&unk_41A5A8, (int)aFux1aoyun);
sub_41136B((int)&unk_41A5B0, (int)aR3verier);
return 1;
} 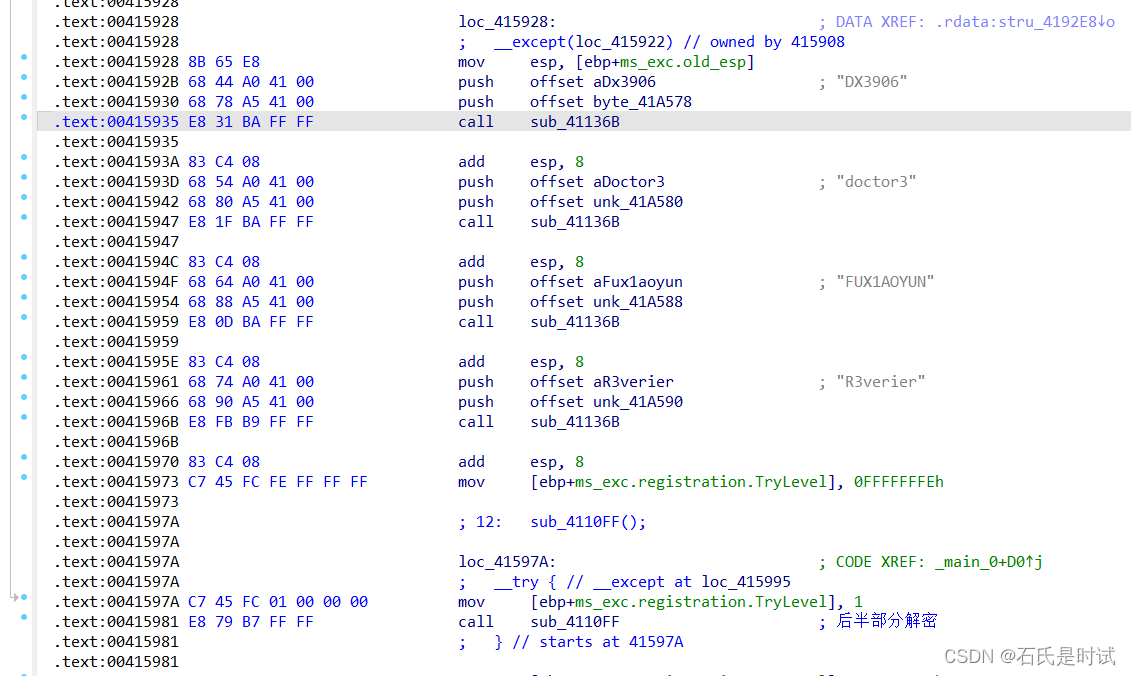
这边这块分别用4个密钥对前后部分作了4次加密
#tea
from ctypes import *
def decrypt(v, k):
v0, v1 = c_uint32(v[0]), c_uint32(v[1])
delta = 0x9e3779b9
k0, k1, k2, k3 = k[0], k[1], k[2], k[3]
total = c_uint32(delta * 32)
for i in range(32):
v1.value -= ((v0.value<<4) + k2) ^ (v0.value + total.value) ^ ((v0.value>>5) + k3)
v0.value -= ((v1.value<<4) + k0) ^ (v1.value + total.value) ^ ((v1.value>>5) + k1)
total.value -= delta
return v0.value, v1.value
keys = [b'DX3906', b'doctor3',b'FUX1AOYUN',b'R3verier', b'DX3906', b'doctor3',b'FUX1AOYUN',b'R3verier']
keys = [v.ljust(16,b'\x00') for v in keys]
#0041A000
enc = bytes.fromhex('5AE36BE40687024F43DFCDC177986BDB8F384399E39322B523FDB01CE5E3EECE2F1DAD2BA41598F9D8EB25FA6B21B772B903332ED94CEB7BF5A748F9909D38FC')
from pwn import p32,u32
for _ in range(4):
key = [u32(keys[0][i:i+4]) for i in range(0,16,4)]
v0,v1 = decrypt([u32(enc[:4]), u32(enc[4:8])],key)
print(p32(v0)+p32(v1))
keys.pop(0)
enc = enc[8:]
for _ in range(4):
key = [u32(keys[0][i:i+4]) for i in range(0,16,4)]
v0,v1 = decrypt([u32(enc[:4]), u32(enc[4:8])],key)
v0,v1 = decrypt([v0, v1],key)
print(p32(v0)+p32(v1))
keys.pop(0)
enc = enc[8:]
#moectf{WoOo00Oow_S0_interesting_y0U_C4n_C41l_M3tW1c3_BY_Unw1Nd~}