不同的工具和方法总能给问题的解决带来希望。本文使用SSSD工具诊断Kerberos和LDAP登录问题诊断。后端(通常也称为数据提供程序)是管理和创建缓存的 SSSD 子进程。此过程与LDAP服务器通信,执行不同的查找查询并将结果存储在缓存中。它还针对 LDAP 或 Kerberos 执行联机身份验证,并将访问和密码策略应用于即将登录的用户。
了解后端组件
SSSD是System Security Services Daemon的缩写,是一个开源的守护进程程序,用于在Linux系统中提供身份验证、授权和命名解析服务。SSSD的主要功能是与LDAP、Kerberos等外部认证系统进行通信,并将这些系统的用户信息、密码策略等存储在本地缓存中以提高性能。在使用SSSD时,用户可以通过单一的认证机制登录到多个应用程序和服务,并不需要为每个应用程序和服务单独进行身份验证。SSSD还提供了本地用户管理和授权的功能,允许管理员对本地用户进行管理和授权。
后端进程及其文件
在 中 sssd.conf 配置的每个域都有一个后端进程 /usr/libexec/sssd/sssd_be 。每个后端进程管理配置文件中定义的一个 SSSD 域,以及在启动时自动发现的受信任域(称为子域)。让我们看一下此示例配置。
[sssd]
services = nss, pam, sudo
domains = IPA.PB, AD.PB
config_file_version = 2
[domain/IPA.PB]
id_provider = ipa
access_provider = ipa
ipa_domain = ipa.pb
[domain/AD.PB]
id_provider = ad
ad_domain = ad.pb
ad_server = _srv_
我们配置了两个域, IPA.PB 并且 AD.PB .每个域都有自己的缓存文件,该文件在父域及其子域及其自己的日志文件之间共享。缓存文件存储在 中 /var/lib/sss/db/$domain.ldb ,日志文件位于 /var/log/sssd/$domain.log 。
以下示例向我们展示了 SSSD 后端进程以及缓存和日志文件位置。
# ps aux | grep sssd_be
/usr/libexec/sssd/sssd_be --domain IPA.PB --uid 0 --gid 0 --debug-to-files
/usr/libexec/sssd/sssd_be --domain AD.PB --uid 0 --gid 0 --debug-to-files
# ls -l /var/log/sssd/
-rw-------. 1 root root 73870 Oct 20 10:50 sssd_IPA.PB.log
-rw-------. 1 root root 73870 Oct 20 10:50 sssd_AD.PB.log
# ls -l /var/lib/sss/db/
-rw-------. 1 root root 1286144 Oct 20 10:50 cache_IPA.PB.ldb
-rw-------. 1 root root 1286144 Oct 20 10:50 cache_AD.PB.ldb
数据提供者工作流程
后端提供了几种服务:id、auth、access等(有关服务的完整列表,请参阅sssd手册页)。每个服务通过配置选项与一个数据提供程序相关联,例如,ID 服务设置为 IPA 提供程序。 id_provider = ipa 通常只设置 id 和访问提供程序,让其他提供程序默认为与 id 相同的提供程序。数据提供程序告诉 SSSD 如何与特定的服务器实现(LDAP、IPA、Active Directory、Kerberos )通信,以及如何将其数据架构和功能转换为 SSSD 缓存。
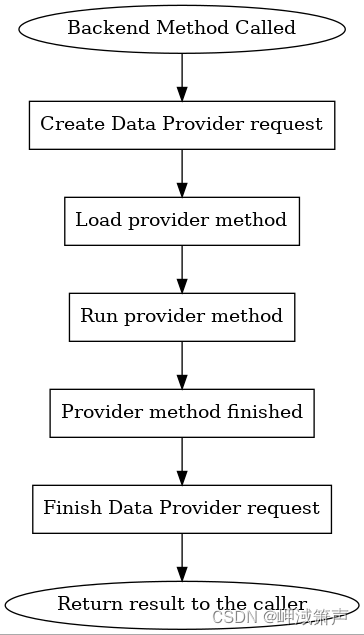
当 SSSD 响应程序调用后端方法时,将启动一系列操作。首先创建新的数据提供程序请求。此请求决定哪个提供程序模块以及此模块中的哪个方法将处理响应方的请求。然后它执行此方法并等待直到完成。之后,将构建回复并发送回响应者。
启用日志记录
首先,要实际查看日志文件中的某些内容,我们需要通过设置调试级别来启用日志记录。有两种方法可以实现此目的。
- 在 的
sssd.conf域部分中使用debug_level指令。 - 使用工具,该工具
sss_debuglevel将仅为当前SSSD实例设置级别,并在重新启动SSSD时设置原始级别。
# cat /etc/sssd.conf
...
[domain/IPA.PB]
...
debug_level = 0x3ff0
...
# systemctl start sssd.service
# sss_debuglevel 0x3ff0
调试级别 0x3ff0 包含所有基本任务的足够信息。有关输入和输出操作的更高级别提供程序的详细信息,这些操作只会产生在大多数情况下使日志难以读取的噪声,因此除非需要,否则我不建议对其进行设置。
读取日志
本节包含后端最基本部分的描述,以及日志消息如何描述它们。
验证选项
启动时,后端会将 SSSD 读取的选项及其配置的值(包括未在 中明确指定的选项)打印到域日志中 sssd.conf 。这对于查看 SSSD 的配置方式非常有用。
[dp_get_options] (0x0400): Option ldap_enumeration_search_timeout has value 60
[dp_get_options] (0x0400): Option ldap_auth_disable_tls_never_use_in_production is FALSE
[dp_get_options] (0x0400): Option ldap_page_size has value 1000
[dp_get_options] (0x0400): Option ldap_deref_threshold has value 10
[dp_get_options] (0x0400): Option ldap_sasl_canonicalize is FALSE
[dp_get_options] (0x0400): Option ldap_connection_expire_timeout has value 900
[dp_get_options] (0x0400): Option ldap_disable_paging is FALSE
[dp_get_options] (0x0400): Option ldap_idmap_range_min has value 200000
[dp_get_options] (0x0400): Option ldap_idmap_range_max has value 2000200000
[dp_get_options] (0x0400): Option ldap_idmap_range_size has value 200000
数据提供程序请求生命周期
通常,有一件事会出错。找不到用户或不允许访问用户、身份验证失败、组成员身份不包含所有成员等。最好先查看数据提供程序配置以了解正在使用哪些提供程序,然后查看数据提供程序请求本身以查看其完成情况。这将为我们指明下一步要看的地方。
-
哪些提供程序用于不同的后端服务?
[dp_load_configuration] (0x0100): Using [ipa] provider for [id] [dp_load_configuration] (0x0100): Using [ipa] provider for [auth] [dp_load_configuration] (0x0100): Using [ipa] provider for [access] [dp_load_configuration] (0x0100): Using [ipa] provider for [chpass] [dp_load_configuration] (0x0100): Using [ipa] provider for [sudo] [dp_load_configuration] (0x0100): Using [ipa] provider for [autofs] [dp_load_configuration] (0x0100): Using [ipa] provider for [selinux] [dp_load_configuration] (0x0100): Using [ipa] provider for [hostid] [dp_load_configuration] (0x0100): Using [ipa] provider for [subdomains] -
每个数据提供程序请求的开始和结束都在日志中标记。它与其他相关消息相关联,使用数字,格式
DP Request [$request-type #$request-number]。我们可以看到,在下面的示例中有一个类型的 Account 活动数据提供程序请求,并且它成功完成。完成此操作后,不再有活动请求。[dp_attach_req] (0x0400): DP Request [Account #1]: New request. Flags [0x0001]. [dp_attach_req] (0x0400): Number of active DP request: 1 ... provider specific method logs ... [dp_req_done] (0x0400): DP Request [Account #1]: Request handler finished [0]: Success [_dp_req_recv] (0x0400): DP Request [Account #1]: Receiving request data. [dp_req_reply_list_success] (0x0400): DP Request [Account #1]: Finished. Success. [dp_req_reply_std] (0x1000): DP Request [Account #1]: Returning [Success]: 0,0,Success dp_table_value_destructor] (0x0400): Removing [0:1:0x0001:1:V:ad.pb:name=user-1@ad.pb] from reply table [dp_req_destructor] (0x0400): DP Request [Account #1]: Request removed. [dp_req_destructor] (0x0400): Number of active DP request: 0 -
如果请求不成功,我们将在此处看到它:
[dp_req_reply_std] (0x1000): DP Request [Subdomains #0]: Returning [Provider is Offline]: 1,1432158212,Offline
故障转移信息
故障转移是 SSSD 的关键部分。如果 SSSD 由于无法建立与服务器的连接而脱机,则可以在此处查找原因。这可能是我们无法解析主机名或 SRV 记录的 DNS 问题。当远程服务器由于位于防火墙后面等而无法修复时,这可能是连接问题。
-
使用 SRV DNS 解析或从配置文件发现的主服务器和备份服务器
[fo_discover_srv_done] (0x0400): Got 1 servers [fo_add_server_to_list] (0x0400): Inserted primary server 'master.ipa.pb:389' to service 'IPA' -
整个故障转移过程:
# 1. 尝试解析IPA服务 [fo_resolve_service_send] (0x0100): Trying to resolve service 'IPA' # 2. 当前没有解析缓存,需寻找服务器,找到一个,解析主机名 [get_port_status] (0x1000): Port status of port 0 for server '(no name)' is 'neutral' [fo_resolve_service_activate_timeout] (0x2000): Resolve timeout set to 6 seconds #3. DNS解析请求 [resolve_srv_send] (0x0200): The status of SRV lookup is neutral [resolv_discover_srv_next_domain] (0x0400): SRV resolution of service 'ldap'. Will use DNS discovery domain 'ipa.pb' [resolv_getsrv_send] (0x0100): Trying to resolve SRV record of '_ldap._tcp.ipa.pb' [schedule_request_timeout] (0x2000): Scheduling a timeout of 6 seconds [schedule_timeout_watcher] (0x2000): Scheduling DNS timeout watcher [resolv_getsrv_done] (0x1000): Using TTL [86400][request_watch_destructor] (0x0400): Deleting request watch [fo_discover_srv_done] (0x0400): Got answer. Processing... #4. 找到一个主服务器 [fo_discover_srv_done] (0x0400): Got 1 servers [fo_add_server_to_list] (0x0400): Inserted primary server 'master.ipa.pb:389' to service 'IPA' [set_srv_data_status] (0x0100): Marking SRV lookup of service 'IPA' as 'resolved' #5. 解析主机域名 [get_server_status] (0x1000): Status of server 'master.ipa.pb' is 'name not resolved' [resolv_gethostbyname_step] (0x2000): Querying files [resolv_gethostbyname_files_send] (0x0100): Trying to resolve A record of 'master.ipa.pb' in files [set_server_common_status] (0x0100): Marking server 'master.ipa.pb' as 'resolving name' [resolv_gethostbyname_step] (0x2000): Querying files [resolv_gethostbyname_files_send] (0x0100): Trying to resolve AAAA record of 'master.ipa.pb' in files [resolv_gethostbyname_next] (0x0200): No more address families to retry [resolv_gethostbyname_step] (0x2000): Querying DNS [resolv_gethostbyname_dns_query] (0x0100): Trying to resolve A record of 'master.ipa.pb' in DNS [schedule_request_timeout] (0x2000): Scheduling a timeout of 6 seconds [schedule_timeout_watcher] (0x2000): Scheduling DNS timeout watcher [sbus_remove_timeout] (0x2000): 0x2230a70 [id_callback] (0x0100): Got id ack and version (1) from Monitor [resolv_gethostbyname_dns_parse] (0x1000): Parsing an A reply [request_watch_destructor] (0x0400): Deleting request watch [set_server_common_status] (0x0100): Marking server 'master.ipa.pb' as 'name resolved' #6. 成功, 连接服务器 [be_resolve_server_process] (0x1000): Saving the first resolved server [be_resolve_server_process] (0x0200): Found address for server master.ipa.pb: [192.1.4.8] TTL 1200 [ipa_resolve_callback] (0x0400): Constructed uri 'ldap://master.ipa.pb' [sssd_async_socket_init_send] (0x0400): Setting 6 seconds timeout for connecting [sdap_ldap_connect_callback_add] (0x1000): New LDAP connection to [ldap://master.ipa.pb:389/??base] with fd [21]. -
如果故障转移过程由于某种原因失败,它将在这些日志中可见。例如:
[fo_resolve_service_done] (0x0020): Failed to resolve server 'invalid.ipa.pb': Domain name not found [set_server_common_status] (0x0100): Marking server 'invalid.ipa.pb' as 'not working' [be_resolve_server_process] (0x0080): Couldn't resolve server (invalid.ipa.pb), resolver returned [11]: Resource temporarily unavailable [be_resolve_server_process] (0x1000): Trying with the next one! [fo_resolve_service_send] (0x0100): Trying to resolve service 'IPA' [get_server_status] (0x1000): Status of server 'invalid.ipa.pb' is 'not working' [get_server_status] (0x1000): Status of server 'invalid.ipa.pb' is 'not working' [fo_resolve_service_send] (0x0020): No available servers for service 'IPA' [be_resolve_server_done] (0x1000): Server resolution failed: [5]: Input/output error [sdap_id_op_connect_done] (0x0020): Failed to connect, going offline (5 [Input/output error]) [be_mark_offline] (0x2000): Going offline!
发现的子域
如果用途来自子域,最好知道发现了哪些子域(IPA 和 AD 术语中的受信任域)以及它们之间的关系。搜索以下调试消息以查看发现了哪些子域。
[new_subdomain] (0x0400): Creating [ad.pb] as subdomain of [IPA.PB]!
[new_subdomain] (0x0400): Creating [child.ad.pb] as subdomain of [IPA.PB]!
LDAP 操作
我们可以在日志中看到执行了哪些 LDAP 操作,它们是如何完成的,以及返回了多少结果。如果出现意外情况,我们可以采用过滤器和搜索库并运行手动LDAP搜索以查看结果是否匹配。如果 LDAP 操作失败并且我们处于联机状态,则表明服务器上存在问题(可能的 ACL 问题)。
# 1. 服务器目标
[sdap_print_server] (0x2000): Searching 192.1.4.8:389
# 2. LDAP 查询过滤器
[sdap_get_generic_ext_step] (0x0400): calling ldap_search_ext with [(&(objectClass=ipasudorule)(ipaEnabledFlag=TRUE)(|(!(memberHost=*))(hostCategory=ALL)(memberHost=fqdn=client.sssd.pb,cn=computers,cn=accounts,dc=ipa,dc=pb)(memberHost=cn=test-hg,cn=hostgroups,cn=accounts,dc=ipa,dc=pb)))][cn=sudo,dc=ipa,dc=pb].
# 3. 查询属性
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [objectClass]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [cn]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaUniqueID]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaEnabledFlag]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoOpt]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAs]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAsGroup]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [memberAllowCmd]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [memberDenyCmd]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [memberHost]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [memberUser]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [sudoNotAfter]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [sudoNotBefore]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [sudoOrder]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [cmdCategory]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [hostCategory]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [userCategory]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAsUserCategory]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAsGroupCategory]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAsExtUser]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAsExtGroup]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaSudoRunAsExtUserGroup]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [externalUser]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [entryUSN]
[sdap_get_generic_ext_step] (0x2000): ldap_search_ext called, msgid = 11
[sdap_op_add] (0x2000): New operation 11 timeout 6
# 4. 处理每一个对象
[sdap_parse_entry] (0x1000): OriginalDN: [ipaUniqueID=ea0116a4-d262-11e6-8cd7-001a4a2312a7,cn=sudorules,cn=sudo,dc=ipa,dc=pb].
[sdap_parse_range] (0x2000): No sub-attributes for [objectClass]
[sdap_parse_range] (0x2000): No sub-attributes for [cn]
[sdap_parse_range] (0x2000): No sub-attributes for [ipaUniqueID]
[sdap_parse_range] (0x2000): No sub-attributes for [ipaEnabledFlag]
[sdap_parse_range] (0x2000): No sub-attributes for [memberAllowCmd]
[sdap_parse_range] (0x2000): No sub-attributes for [memberUser]
[sdap_parse_range] (0x2000): No sub-attributes for [hostCategory]
[sdap_parse_range] (0x2000): No sub-attributes for [ipaSudoRunAsUserCategory]
[sdap_parse_range] (0x2000): No sub-attributes for [ipaSudoRunAsGroupCategory]
[sdap_parse_range] (0x2000): No sub-attributes for [entryUSN]
身份验证
如果身份验证失败,通常是由于凭据无效或过期。 clock skew 如果当客户端的时间与 KDC 时间不同时使用 Kerberos,也可能涉及可能。我们将 PAM 身份验证的每个阶段记录为单独的数据提供程序请求,以便我们可以获取失败的确切阶段。
-
进程打印每个阶段的输入数据。以下示例显示了成功的身份验证阶段。
[dp_pam_handler] (0x0100): Got request with the following data [pam_print_data] (0x0100): command: SSS_PAM_AUTHENTICATE [pam_print_data] (0x0100): domain: IPA.PB [pam_print_data] (0x0100): user: admin@ipa.pb [pam_print_data] (0x0100): service: su [pam_print_data] (0x0100): tty: pts/1 [pam_print_data] (0x0100): ruser: pbrezina [pam_print_data] (0x0100): rhost: [pam_print_data] (0x0100): authtok type: 1 [pam_print_data] (0x0100): newauthtok type: 0 [pam_print_data] (0x0100): priv: 0 [pam_print_data] (0x0100): cli_pid: 29865 [pam_print_data] (0x0100): logon name: not set [dp_attach_req] (0x0400): DP Request [PAM Authenticate #4]: New request. Flags [0000]. ... [dp_req_done] (0x0400): DP Request [PAM Authenticate #4]: Request handler finished [0]: Success [_dp_req_recv] (0x0400): DP Request [PAM Authenticate #4]: Receiving request data. [dp_req_destructor] (0x0400): DP Request [PAM Authenticate #4]: Request removed. [dp_req_destructor] (0x0400): Number of active DP request: 0 [dp_pam_reply] (0x1000): DP Request [PAM Authenticate #4]: Sending result [0][IPA.PB] -
如果与远程服务器的通信顺利,我们始终返回成功,但是 PAM 结果记录在函数中
dp_pam_reply : Sending result [0][IPA.PB]。值表示成功,其他值 0 表示问题,例如 17 表示凭据无效。您可以在此处获取 PAM 状态代码及其含义的列表。[dp_pam_reply] (0x1000): DP Request [PAM Authenticate #4]: Sending result [17][IPA.PB] -
如果找不到有关身份验证的任何调试消息,则可能是由于 PAM 配置中缺少 pam_sss (例如在 中
/etc/pam.d/system-auth)。
访问控制
如果存在未 permit 配置的访问提供程序,我们还可能找出拒绝用户访问(或相反,允许)的原因。这可能表示 IPA 上的主机基本访问控制配置错误或用户帐户已过期等。
访问控制是帐户管理 PAM 阶段和 PAM 帐户请求的一部分(对于 ipa 提供商也是 PAM SELinux 请求,因此要查看访问检查开始的位置,请查找以下消息:
[dp_pam_handler] (0x0100): Got request with the following data
[pam_print_data] (0x0100): command: SSS_PAM_ACCT_MGMT
...
[dp_attach_req] (0x0400): DP Request [PAM Account #4]: New request. Flags [0000].
...
[dp_attach_req] (0x0400): DP Request [PAM SELinux #5]: New request. Flags [0000].
帐户检查适用的规则在很大程度上取决于 的 access_provider 配置。默认情况下, permit 此提供程序设置为,这意味着所有用户都可以访问。请参阅 SSSD 手册页,了解可以设置哪些提供程序。在此示例中,我们使用提供程序, ipa 除了 LDAP 策略之外,它还涉及两项检查:1) 主机基访问控制 (HBAC) 和 2) SELinux 策略。
-
授予的访问权限示例。请注意,我们返回 0 dp_pam_reply 。
[dp_attach_req] (0x0400): DP Request [PAM Account #4]: New request. Flags [0000]. ... [hbac_evaluate] (0x0100): ALLOWED by rule [allow_all]. [hbac_evaluate] (0x0100): hbac_evaluate() >] [ipa_hbac_evaluate_rules] (0x0080): Access granted by HBAC rule [allow_all] [dp_req_done] (0x0400): DP Request [PAM Account #4]: Request handler finished [0]: Success [_dp_req_recv] (0x0400): DP Request [PAM Account #4]: Receiving request data. [dp_req_destructor] (0x0400): DP Request [PAM Account #4]: Request removed. [dp_req_destructor] (0x0400): Number of active DP request: 0 [dp_attach_req] (0x0400): DP Request [PAM SELinux #5]: New request. Flags [0000]. [dp_attach_req] (0x0400): Number of active DP request: 1 ... [dp_req_done] (0x0400): DP Request [PAM SELinux #5]: Request handler finished [0]: Success [_dp_req_recv] (0x0400): DP Request [PAM SELinux #5]: Receiving request data. [dp_req_destructor] (0x0400): DP Request [PAM SELinux #5]: Request removed. [dp_req_destructor] (0x0400): Number of active DP request: 0 [dp_pam_reply] (0x1000): DP Request [PAM Account #4]: Sending result [0][IPA.PB] -
由于缺少 HBAC 规则而被拒绝访问的示例(通知 dp_pam_reply 编号 6 在 :
[ipa_hbac_rule_info_done] (0x0080): No rules apply to this host [ipa_pam_access_handler_done] (0x0020): No HBAC rules find, denying access [dp_req_done] (0x0400): DP Request [PAM Account #5]: Request handler finished [0]: Success [_dp_req_recv] (0x0400): DP Request [PAM Account #5]: Receiving request data. [dp_req_destructor] (0x0400): DP Request [PAM Account #5]: Request removed. [dp_req_destructor] (0x0400): Number of active DP request: 0 [dp_pam_reply] (0x1000): DP Request [PAM Account #5]: Sending result [6][IPA.PB] -
如果找不到有关访问控制的任何调试消息,则可能是由于 PAM 配置中缺少 pam_sss (例如在 中
/etc/pam.d/system-auth)。
超时
许多 SSSD 操作都设置了缺省超时,通常超时是可配置的,可以在提供程序后端或 sssd.conf 手册页中找到。下面的示例日志输出显示 SSSD 由于超时而使搜索操作失败。
[sdap_op_timeout] (0x1000): Issuing timeout for 11
[sdap_op_destructor] (0x1000): Abandoning operation 11
[generic_ext_search_handler] (0x0040): sdap_get_generic_ext_recv failed [110]: Connection timed out
超时的实际 SSSD 操作可能不在日志的同一部分中,需要在日志中更早地进行搜索。我们可以在日志中搜索操作编号(以上日志中的 11),例如 msgid = 11
[sdap_print_server] (0x2000): Searching 192.1.4.8:389
[sdap_get_generic_ext_step] (0x0400): calling ldap_search_ext with [(&(cn=sudo-test)(|(objectClass=ipaUserGroup)(objectClass=posixGroup))(cn=*)(&(gidNumber=*)(!(gidNumber=0))))][cn=accounts,dc=idm,dc=example,dc=com].
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [objectClass]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [posixGroup]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [cn]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [userPassword]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [gidNumber]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [member]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaUniqueID]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaNTSecurityIdentifier]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [modifyTimestamp]
[sdap_get_generic_ext_step] (0x1000): Requesting attrs: [entryUSN]
[sssd[be[yyaw.com]]] [sdap_get_generic_ext_step] (0x1000): Requesting attrs: [ipaExternalMember]
[sssd[be[yyaw.com]]] [sdap_get_generic_ext_step] (0x2000): ldap_search_ext called, msgid = 11
[sssd[be[yyaw.com]]] [sdap_op_add] (0x2000): New operation 11 timeout 30
请注意,最后一行包含操作编号和超时值。30 秒超时与触发超时的日志消息匹配。
手动执行 LDAP 查询
使用 ldapsearch 工具手动运行与 SSSD 相同的查询通常很有用。查找名为 sdap_get_generic_ext_step 获取 SSSD 对 LDAP 服务器使用的搜索库和过滤器的函数,并查看它连接到哪个服务器 sdap_print_server 。消息的形式为:
[sdap_print_server] (0x2000): Searching $ip:$port
[sdap_get_generic_ext_step] (0x0400): calling ldap_search_ext with [$filter][$search-base]
-
匿名绑定(无身份验证)
ldapsearch -x -H ldap://$ip:$port -b $search-base '$filter' -
简单绑定(使用凭据进行身份验证)
ldapsearch -x -D "cn=Directory Manager" -w "$password" -H ldap://$ip:$port -b $search-base '$filter' -
GSSAPI(通过 Kerberos 进行身份验证)
klist -k kinit -k '$principal' ldapsearch -Y GSSAPI -H ldap://$ip:$port -b $search-base '$filter'
寻求帮助
您可以通过 sssd 用户邮件列表或 IRC 上的 #sssd 频道或联系 freenode.net。如果您提供下列所有信息以及以及您想到的可能有用的所有内容,那么您的问题解决速度速度就能加快。因为这些信息有助于开发者定位、分析、解决问题,题,它们是适当的、必要的。
- 问题描述
- 你期望会发生什么
- 您在日志中看到的内容
- 调试级别设置为的所有 SSSD 日志 0x3ff0 (请始终包含整个日志文件,而不仅仅是代码片段)
- SSSD的版本以及您使用的服务器
- 其他信息取决于调查领域
- 预期的组成员身份
- 域关系
- HBAC 规则
- 其他访问控制设置
- 您想到的可能有用的所有内容