- 网址
aHR0cHM6Ly9pdC5zem9ubGluZS5uZXQvc2h1eml6aG9uZ2d1by8yMDIzMDMyOS8yMDIzMDM3ODAzNDAuaHRtbA==
- 抓包
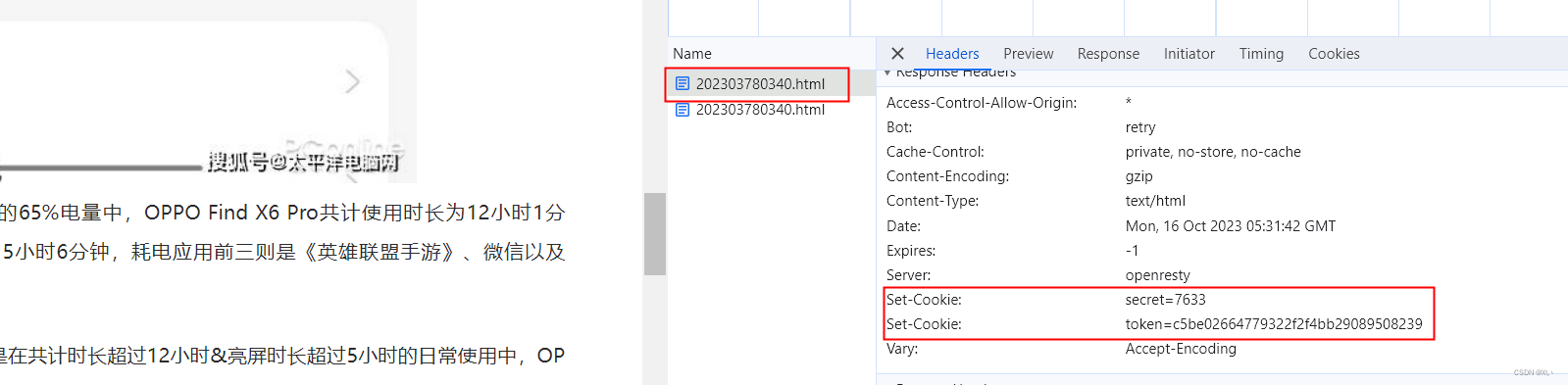
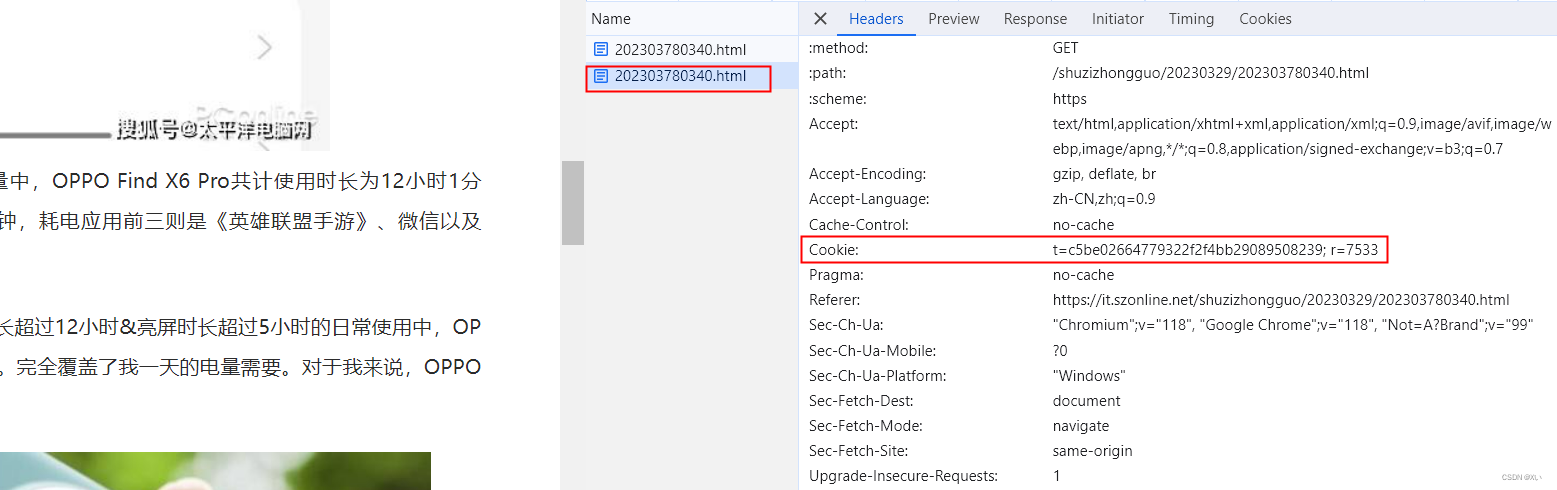
猜想:从图中对比发现取第一次请求返回的Set-Cookie作为第二次请求的cookies,不过需要把Set-Cookie中的secret-100(此时注意int和str类型的来回转换),名称变为r,把Set-Cookie中的token变为t
- 第一次请求返回:
<script language="javascript" type="text/javascript">
eval(function(p, a, c, k, e, d) {
e = function(c) {
return (c < a ? "": e(parseInt(c / a))) + ((c = c % a) > 35 ? String.fromCharCode(c + 29) : c.toString(36))
};
if (!''.replace(/^/, String)) {
while (c--) d[e(c)] = k[c] || e(c);
k = [function(e) {
return d[e]
}];
e = function() {
return '\\w+'
};
c = 1;
};
while (c--) if (k[c]) p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c]);
return p;
} ('p b(j){1 7=j+"=";1 a=3.4.o(\';\');u(1 i=0;i<a.9;i++){1 c=a[i].s();f(c.q(7)==0)g c.v(7.9,c.9)}g""}1 6=b("6");1 5=B(b("5"));f(6==""||5==""){D("8=8; ",C)}x{1 k=5-y;3.4="6=; d=e, m l n 2:2:2 h;";3.4="5=; d=e, m l n 2:2:2 h;";3.4="t="+6+";";3.4="r="+k+";";A.8.z(w)}', 40, 40, '|var|00|document|cookie|secret|token|name|location|length|ca|getCookie||expires|Thu|if|return|UTC||cname|random|Jan|01|1970|split|function|indexOf||trim||for|substring|true|else|100|reload|window|parseInt|3000|setTimeout'.split('|'), 0, {}))
</script>
js反混淆解密,见(https://blog.csdn.net/CaliXz/article/details/127405966)
function getCookie(cname) {
var name = cname + "=";
var ca = document.cookie.split(';');
for (var i = 0; i < ca.length; i++) {
var c = ca[i].trim();
if (c.indexOf(name) == 0) return c.substring(name.length, c.length)
}
return ""
} //这段代码的作用是获取指定名称的cookie值,并将其返回
var token = getCookie("token");
var secret = parseInt(getCookie("secret"));
if (token == "" || secret == "") {
setTimeout("location=location; ", 3000)
} //如果为空
else {
var random = secret - 100;
document.cookie = "token=; expires=Thu, 01 Jan 1970 00:00:00 UTC;";
document.cookie = "secret=; expires=Thu, 01 Jan 1970 00:00:00 UTC;";
document.cookie = "t=" + token + ";";
document.cookie = "r=" + random + ";";
window.location.reload(true)
}
证实上述猜想,获取cookies第二次请求得到正文内容。