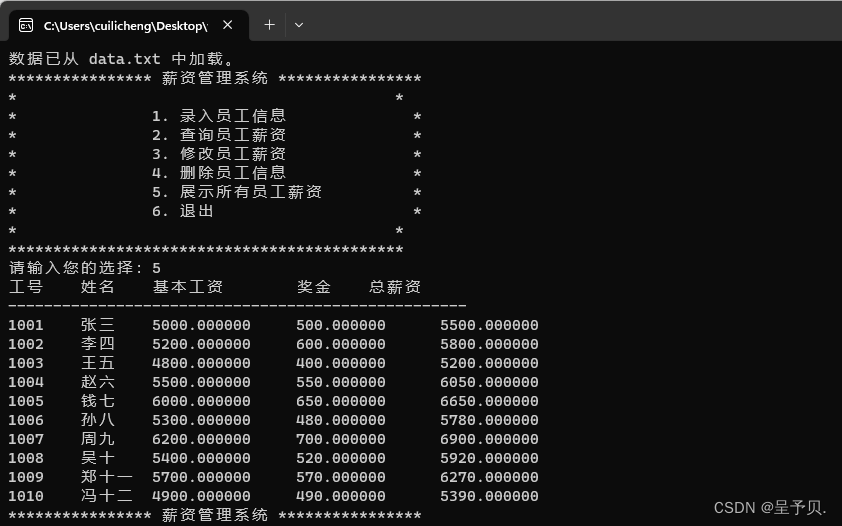
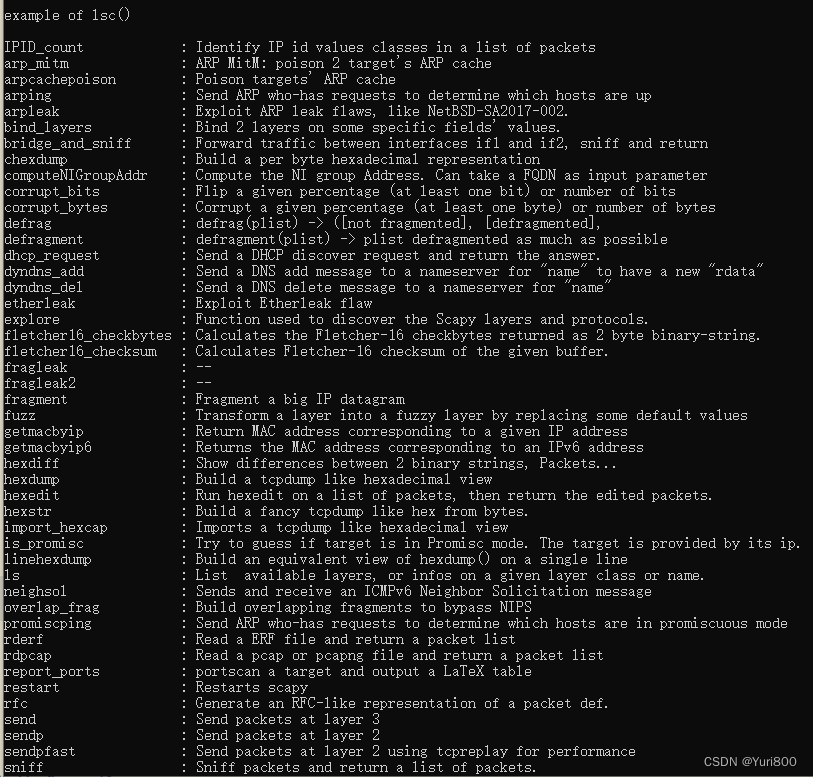
1. 演示ls()/lsc()用法:
##Exec1.py
from scapy.all import *
## 列出scapy支持的命令
def ListScapyCmd():
lsc()
## 列出指定协议的各个字段, 用于构成packet
def ListProtocolField(protoclName):
ls(protoclName)
if __name__ == "__main__":
print("\nexample of lsc()\n")
ListScapyCmd()
print("\nexample of ls()\n")
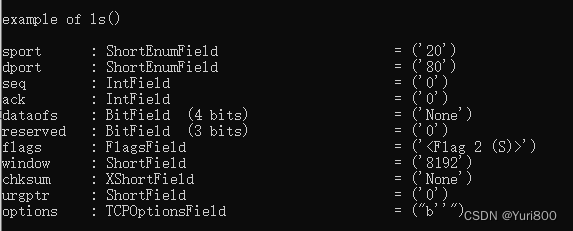
ListProtocolField(TCP)
输出:
2.Scapy "/" 符号生成数据包, sr/send发送3层包. srp/sendp发送2层包.
## Exec2.py
from scapy.all import *
ifaceName = 'VMware Network Adapter VMnet8'
dstIP = '192.168.70.134'
dstMac = '00:0C:29:FB:48:0A'
srcIP = '192.168.70.1'
srcMac = '00:50:56:C0:00:08'
def ARPPacket():
## 构造以太网层
etherLayer = Ether(dst=dstMac)
## 构造ARP-echo包
arpLayer = ARP(hwtype=1,
ptype=0x800,
hwsrc=srcMac,
psrc=srcIP,
hwdst=dstMac,
pdst=dstIP)
arpRequest = etherLayer/arpLayer
## use sendp to send level 2 packet
## 二层包需要用sendp发送
sendp(arpRequest, iface=ifaceName, loop=200)
def ICMPPacket():
ipLayer = IP(dst=dstIP)
## 模仿nmap -PP command, 构造ICMP包
icmpTimestampRequest = ICMP(type=13,code=0) ## ICMP, timestamp request
## 模仿nmap -PM command
icmpMacRequest = ICMP(type=17,code=0) ## ICMP, Mac address request
## 模仿nmap -PE command
icmpEchoRequest = ICMP(type=8,code=0) ## ICMP, echo request
for i in range(500):
pack = ipLayer/icmpTimestampRequest
send(pack,iface=ifaceName)
pack = ipLayer/icmpMacRequest
send(pack,iface=ifaceName)
pack = ipLayer/icmpEchoRequest
## use sendp to send level 3 packet
send(pack,iface=ifaceName)
def TCPPacket():
ipLayer = IP(dst=dstIP, src=srcIP)
tcpLayer = TCP(dport=[22,23,80,443,8080])
pack = ipLayer/tcpLayer
sr1(pack,iface=ifaceName,timeout=3)
def TCPPacketFlags():
## 构造IP层
ipLayer = IP(dst=dstIP, src=srcIP)
## 构造TCP层, 向192.168.70.134:22,23,80,443,8080 5个端口发送TCP reset包(flags=RST)
tcpLayer = TCP(dport=[22,23,80,443,8080],flags="R")
## 构造包
pack = ipLayer/tcpLayer
sr1(pack,iface=ifaceName,timeout=3)
if __name__ == "__main__":
TCPPacket()
TCPPacketFlags()
ICMPPacket()
ARPPacket()
Wireshark输出:
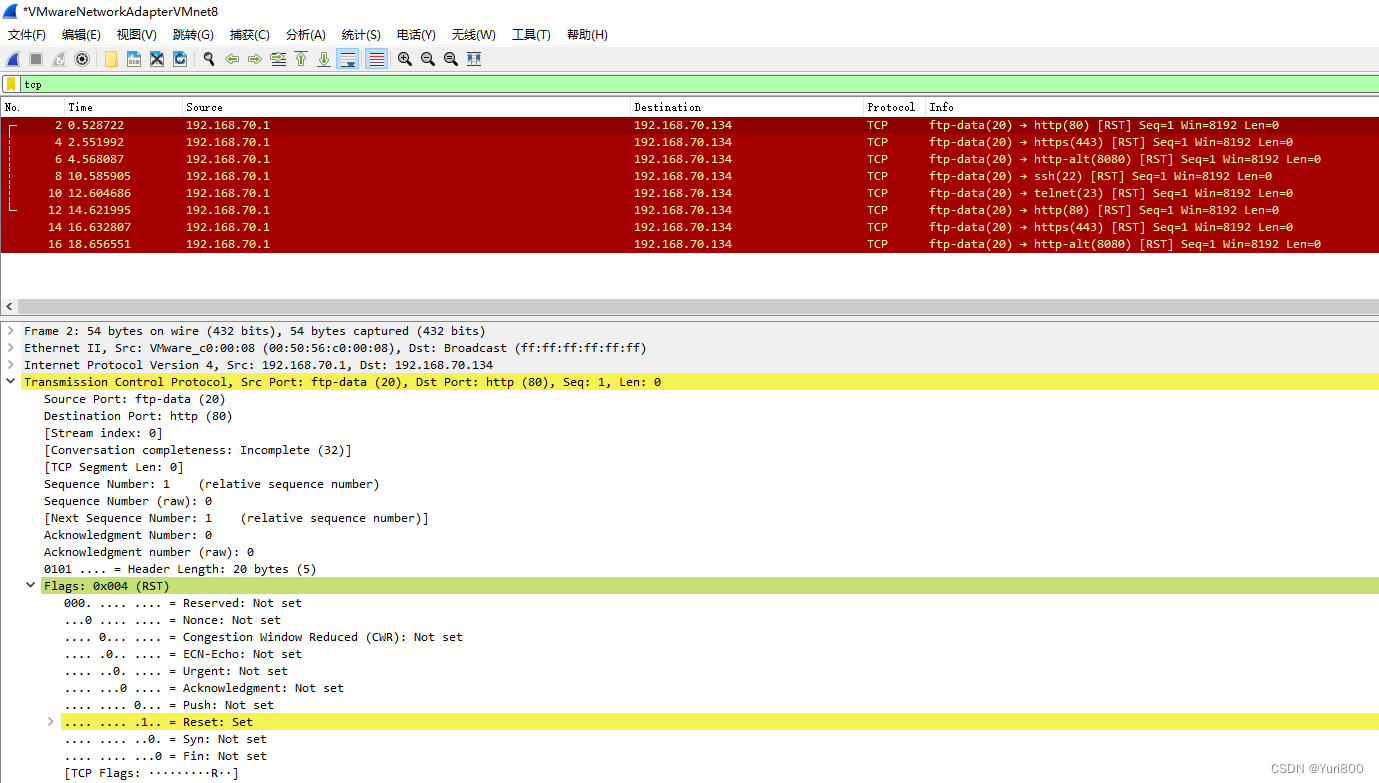
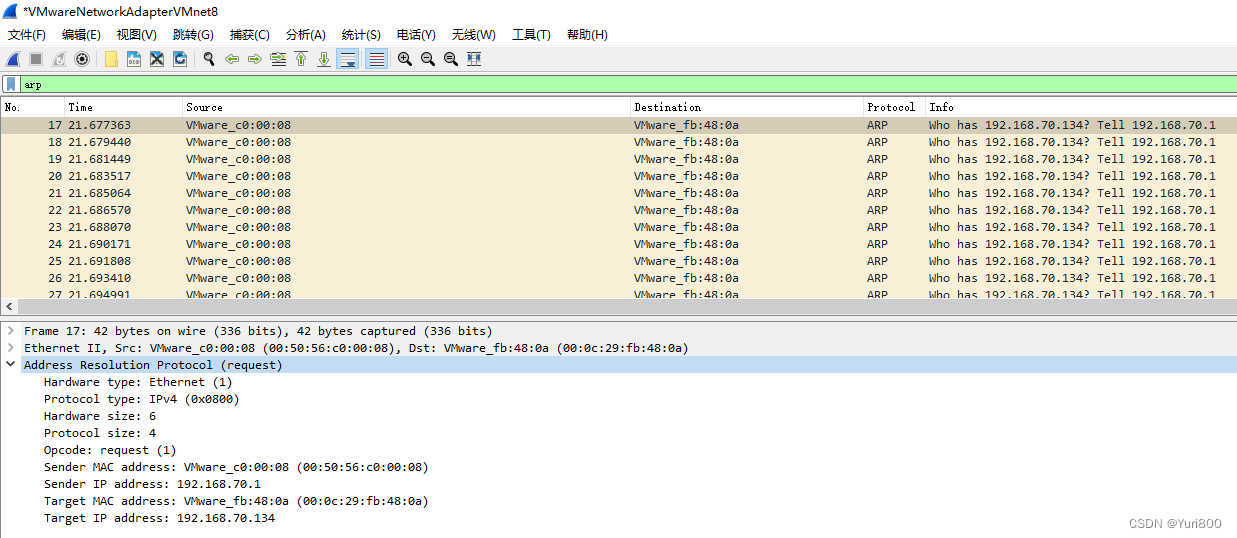
3.Scapy+PyShark实时抓包/TCPReplay. Scapy.sniff函数无法用display filter, 只能用PyShark代替. Scapy读取/重放 PyShark生成的pcap文件
## Exec3.py
from scapy.all import *
from pyshark import *
## live capture and file capture
ifaceName = 'VMware Network Adapter VMnet8'
path2tshark = 'C:\\Program Files\\Wireshark\\tshark.exe'
path2pCapFile = 'C:\\Users\\Eugene\\Desktop\\studio\\scapyMod\\1.pcap'
## scapy.sniff只能应用wireshark capture-filter,不能应用wireshark display-filter, 抓特定类型的packet需要通过pyshark中转.
## pyshark.LiveCapture一定要指定tshark_path(ex:C:\Program Files\Wireshark\tshark.exe)
## pyshark.LiveCapture.output_file指定pcap保存路径, 供scapy模块rdpcap/wrpcap使用
def PysharkLiveCapture():
capObj = LiveCapture(interface=ifaceName,
display_filter = "",
bpf_filter = "",
tshark_path = path2tshark,
output_file = path2pCapFile)
capObj.sniff(timeout=120)
def HandleLiveCapture():
capturedPacks = rdpcap(path2pCapFile)
for pack in capturedPacks:
try:
## 用haslayer判断是否为IP包
if pack.haslayer(IP) == True:
print("pack.SrcIP: "+pack[IP].src+"\tpack.DstIp: "+pack[IP].dst)
## 用haslayer判断是否为ICMP包
if pack.haslayer(ICMP) == True:
## 解析ICMP包中的各个字段
print("pack[ICMP].type:"+str(pack[ICMP].type)+" pack[ICMP].code:"+str(pack[ICMP].code))
except:
print("exception")
if __name__ == "__main__":
## PysharkLiveCapture()
HandleLiveCapture()