感觉没怎么做密码,就每周上nss随便做点
稍微难点的会分析
[SWPU 2020]happy
import gmpy2
from Crypto.Util.number import *
import z3
c = 0x7a7e031f14f6b6c3292d11a41161d2491ce8bcdc67ef1baa9e
e = 0x872a335
#q + q*p^3 =1285367317452089980789441829580397855321901891350429414413655782431779727560841427444135440068248152908241981758331600586
#qp + q *p^2 = 1109691832903289208389283296592510864729403914873734836011311325874120780079555500202475594
a = 1285367317452089980789441829580397855321901891350429414413655782431779727560841427444135440068248152908241981758331600586
b = 1109691832903289208389283296592510864729403914873734836011311325874120780079555500202475594
p , q = z3.Ints('p q')
s = z3.Solver()
s.add(q + q*p**3 == a)
s.add(q*p + q*p**2 == b)
s.check()
print(s.model())
p = 1158310153629932205401500375817
q = 827089796345539312201480770649
print(long_to_bytes(pow(c,gmpy2.invert(e,(p-1)*(q-1)),p*q)))
[AFCTF2018]BASE
import base64
import re
b64 = re.compile(b"^[a-zA-Z0-9+/=]*$")
b16 = re.compile(b"^[0-9A-F=]*$")
b32 = re.compile(b"^[A-Z2-7=]*$")
res = open ("flag_encode.txt","rb").read()
while True:
if b16.match(res):
res = base64.b16decode(res)
elif b32.match(res):
res = base64.b32decode(res)
elif b64.match(res):
res = base64.b64decode(res)
elif b"afctf" in res:
print(res.decode())
break
[SWPUCTF 2021 新生赛]crypto2
共模
[SWPUCTF 2021 新生赛]crypto9
import itertools
#AKKPLX{qv5x0021-7n8w-wr05-x25w-7882ntu5q984}
letter_list = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ' # 字母表
# 根据输入的key生成key列表
def Get_KeyList(key):
key_list = []
for ch in key:
key_list.append(ord(ch.upper()) - 65)
return key_list
# 加密函数
def Encrypt(plaintext, key_list):
ciphertext = ""
i = 0
for ch in plaintext: # 遍历明文
if 0 == i % len(key_list):
i = 0
if ch.isalpha(): # 明文是否为字母,如果是,则判断大小写,分别进行加密
if ch.isupper():
ciphertext += letter_list[(ord(ch) - 65 + key_list[i]) % 26]
i += 1
else:
ciphertext += letter_list[(ord(ch) - 97 + key_list[i]) % 26].lower()
i += 1
else: # 如果密文不为字母,直接添加到密文字符串里
ciphertext += ch
return ciphertext
# 解密函数
def Decrypt(ciphertext, key):
plaintext = ""
key_list = Get_KeyList(key)
i = 0
for ch in ciphertext: # 遍历密文
if 0 == i % len(key_list):
i = 0
if ch.isalpha(): # 密文为否为字母,如果是,则判断大小写,分别进行解密
if ch.isupper():
plaintext += letter_list[(ord(ch) - 65 - key_list[i]) % 26]
i += 1
else:
plaintext += letter_list[(ord(ch) - 97 - key_list[i]) % 26].lower()
i += 1
else: # 如果密文不为字母,直接添加到明文字符串里
plaintext += ch
return plaintext
itrator = ["".join(i) for i in itertools.product(letter_list,repeat=3)]
for i in itrator:
res = Decrypt("AKKPLX{qv5x0021-7n8w-wr05-x25w-7882ntu5q984}","".join(i))
if "NSSCTF" in res:
print(res)
[AFCTF 2018]你能看出这是什么加密么

[SWPUCTF 2021 新生赛]crypto4
pq接近容易分解,或者factordb

[安洵杯 2019]JustBase
题目是base
然后一眼过去不是正经base
先解码试试,发现里面是可以出一些看着像是人能阅读的英语的
b'The geo\x1b\xd9\x92\x06\xd8\x81\xd1\xa1\x94\x81\x15\x85\xc9\xd1\xa0\x93 q\\\x99\x98X\xd9H\x1a\\\xc8\x19\x1b\xa5\xb9\x85ed by the partia[\x18\\\x88\x1c\x1c\x9b\xdc\x19\\\x9d\x1aY\\\xc8\x1b\xd9\x88\x16\x17FW"\x81A\xc9\x95\xc5nt on EarZ\x08\x1a[\x88\x1c\xdb\xc6\x96B\xc2\x06\xc6\x97\x17V\x96B\xc2\x06\x16\xe6B\x06E\xcd\x95\x9c\xc8\x1c\xdd\x18VW2\xc2\x07v\x17FW"\x06\x972\x06U\x85ptionally reaa\x1a]\x99K\x88\x12R\x06F\x97\r\xbd\xb1\xd9\x95\xcc\xb0\x81\xd1\xc9\x85\xb9\xcd\xc1\xb2\\\xcb\x08\x18ZB\x07\x07&V6\x97\x06\x95\x85\xd1\x95\xcc\x81\xb5\x85\x88\x18\xda\x19Z\x96\x05\xb0\x81\x8d\xbd\xb5\xc1\xbd\xd5\xa4s and is b\xe7\x11\x85\xb9\xd1\xb1\xe4\x81\xb5\xb4ifying the faaH\x1bb\x07F\x86R\x04V\x17\'F\x82\xe2\x04Wf\x17\x06\xc9\x85\xd1\x95\x90\x81\x99\xc9\xb8\x1d\x1a\x19H\x1a6V\x16\xe72\xc2\x07Eer vapl\x88\x19\x9b&\xd72\x061\xbd\xd5\x91\xcc\xb0\x81\xcd\xb9H\x1ab\x07v\x86\x966\x82\x06\x17&R\x05\xc9\x85\xb9\xc0orted by ZZB\x06er the continents. Condensation frkH\x1d\x1a\x19H\x18\xdb\x19\x91\xcc\x81\xc1\xc9\xbd\xd9\xa5\x91\x95\xcc\x81\xd1\xa1\x94\x81\x95\xcd\xc5ntial ae[\x9d\x08\x1b\xd9\x88\x18\xdbii[\x9d\x18[\x08\x19\\\x9b6\x96\xb8\xe8\x81\xc9\x85\xa5\xb8\xb9Q\xa1\x94\x81\xc9\x85\xd1\x94\x81\x85 which a mk\x19X\xd6\xc6R\x06\xd8\x81\xd1Y\\\x88\x1c\x18\\\xdcW2\x07F\x86\xd5\x9d\xa0\x81he bX\xdb\x19H\x1a\\\xc8\x1b\x98\x81\xc9\x85\xb9\x91\xbd\xb4)\x05\xb9\x90\x81\xd1\xa1\x94\x81\x99\xb1\x85\x9c\x81\xa5\xcc CTF{22$UU%E\x95T\x94\xb5A1-)!\x1d\x19\x11L\xb5\x05ia\rY\t\r}'
然后通篇没有数字,猜测是把数字换成符号了
于是脚本如下
import base64
res = open("enc.txt","rb").read().decode()
res = res.replace("!","1").replace("@","2").replace("#","3").replace("$","4").replace("%","5").replace("^","6").replace("&","7").replace("*","8").replace("(","9").replace(")","0")
print(base64.b64decode(res))
[SWPUCTF 2021 新生赛]crypto5
题只给了n c
我没辙了
看wp说是小e
爆破e
于是脚本如下
from Crypto.Util.number import *
import gmpy2
c = 25166751653530941364839663846806543387720865339263370907985655775152187319464715737116599171477207047430065345882626259880756839094179627032623895330242655333
n = 134109481482703713214838023035418052567000870587160796935708584694132507394211363652420160931185332280406437290210512090663977634730864032370977407179731940068634536079284528020739988665713200815021342700369922518406968356455736393738946128013973643235228327971170711979683931964854563904980669850660628561419
for e in range(1,2**16):
for k in range(5000):
if gmpy2.iroot((c + k*n),e)[1]:
flag = long_to_bytes(gmpy2.iroot(c + k*n,e)[0])
if b"NSSCTF" in flag:
print(flag)
break
[BJDCTF 2020]rsa
from Crypto.Util.number import *
import gmpy2
c1 = 12641635617803746150332232646354596292707861480200207537199141183624438303757120570096741248020236666965755798009656547738616399025300123043766255518596149348930444599820675230046423373053051631932557230849083426859490183732303751744004874183062594856870318614289991675980063548316499486908923209627563871554875612702079100567018698992935818206109087568166097392314105717555482926141030505639571708876213167112187962584484065321545727594135175369233925922507794999607323536976824183162923385005669930403448853465141405846835919842908469787547341752365471892495204307644586161393228776042015534147913888338316244169120
n1 = 13508774104460209743306714034546704137247627344981133461801953479736017021401725818808462898375994767375627749494839671944543822403059978073813122441407612530658168942987820256786583006947001711749230193542370570950705530167921702835627122401475251039000775017381633900222474727396823708695063136246115652622259769634591309421761269548260984426148824641285010730983215377509255011298737827621611158032976420011662547854515610597955628898073569684158225678333474543920326532893446849808112837476684390030976472053905069855522297850688026960701186543428139843783907624317274796926248829543413464754127208843070331063037
c2 = 381631268825806469518166370387352035475775677163615730759454343913563615970881967332407709901235637718936184198930226303761876517101208677107311006065728014220477966000620964056616058676999878976943319063836649085085377577273214792371548775204594097887078898598463892440141577974544939268247818937936607013100808169758675042264568547764031628431414727922168580998494695800403043312406643527637667466318473669542326169218665366423043579003388486634167642663495896607282155808331902351188500197960905672207046579647052764579411814305689137519860880916467272056778641442758940135016400808740387144508156358067955215018
c3 = 979153370552535153498477459720877329811204688208387543826122582132404214848454954722487086658061408795223805022202997613522014736983452121073860054851302343517756732701026667062765906277626879215457936330799698812755973057557620930172778859116538571207100424990838508255127616637334499680058645411786925302368790414768248611809358160197554369255458675450109457987698749584630551177577492043403656419968285163536823819817573531356497236154342689914525321673807925458651854768512396355389740863270148775362744448115581639629326362342160548500035000156097215446881251055505465713854173913142040976382500435185442521721
n2 = 12806210903061368369054309575159360374022344774547459345216907128193957592938071815865954073287532545947370671838372144806539753829484356064919357285623305209600680570975224639214396805124350862772159272362778768036844634760917612708721787320159318432456050806227784435091161119982613987303255995543165395426658059462110056431392517548717447898084915167661172362984251201688639469652283452307712821398857016487590794996544468826705600332208535201443322267298747117528882985955375246424812616478327182399461709978893464093245135530135430007842223389360212803439850867615121148050034887767584693608776323252233254261047
q = gmpy2.gcd(n1,n2)
p1 = n1 // q
p2 = n2 // q
# for e in range(1,100000):
# if pow(294,e,n1) == c2:
# print(e)
# 52361
e = 52361
print(long_to_bytes(pow(c1,gmpy2.invert(e,(p1-1)*(q-1)),n1)))
[SWPUCTF 2021 新生赛]crypto1
from Crypto.Util.number import *
import gmpy2
flag1 = 463634070971821449698012827631572665302589213868521491855038966879005784397309389922926838028598122795187584361359142761652619958273094398420314927073008031088375892957173280915904309949716842152249806486027920136603248454946737961650252641668562626310035983343018705370077783879047584582817271215517599531278507300104564011142229942160380563527291388260832749808727470291331902902518196932928128107067117198707209620169906575791373793854773799564060536121390593687449884988936522369331738199522700261116496965863870682295858957952661531894477603953742494526632841396338388879198270913523572980574440793543571757278020533565628285714358815083303489096524318164071888139412436112963845619981511061231001617406815056986634680975142352197476024575809514978857034477688443230263761729039797859697947454810551009108031457294164840611157524719173343259485881089252938664456637673337362424443150013961181619441267926981848009107466576314685961478748352388452114042115892243272514245081604607798243817586737546663059737344687130881861357423084448027959893402445303299089606081931041217035955143939567456782107203447898345284731038150377722447329202078375870541529539840051415759436083384408203659613313535094343772238691393447475364806171594
flag2 = 130959534275704453216282334815034647265875632781798750901627773826812657339274362406246297925411291822193191483409847323315110393729020700526946712786793380991675008128561863631081095222226285788412970362518398757423705216112313533155390315204875516645459370629706277876211656753247984282379731850770447978537855070379324935282789327428625259945250066774049650951465043700088958965762054418615838049340724639373351248933494355591934236360506778496741051064156771092798005112534162050165095430065000827916096893408569751085550379620558282942254606978819033885539221416335848319082054806148859427713144286777516251724474319613960327799643723278205969253636514684757409059003348229151341200451785288395596484563480261212963114071064979559812327582474674812225260616757099890896900340007990585501470484762752362734968297532533654846190900571017635959385883945858334995884341767905619567505341752047589731815868489295690574109758825021386698440670611361127170896689015108432408490763723594673299472336065575301681055583084547847733168801030191262122130369687497236959760366874106043801542493392227424890925595734150487586757484304609945827925762382889592743709682485229267604771944535469557860120878491329984792448597107256325783346904408
n = 609305637099654478882754880905638123124918364116173050874864700996165096776233155524277418132679727857702738043786588380577485490575591029930152718828075976000078971987922107645530323356525126496562423491563365836491753476840795804040219013880969539154444387313029522565456897962200817021423704204077133003361140660038327458057898764857872645377236870759691588009666047187685654297678987435769051762120388537868493789773766688347724903911796741124237476823452505450704989455260077833828660552130714794889208291939055406292476845194489525212129635173284301782141617878483740788532998492403101324795726865866661786740345862631916793208037250277376942046905892342213663197755010315060990871143919384283302925469309777769989798197913048813940747488087191697903624669415774198027063997058701217124640082074789591591494106726857376728759663074734040755438623372683762856958888826373151815914621262862750497078245369680378038995425628467728412953392359090775734440671874387905724083226246587924716226512631671786591611586774947156657178654343092123117255372954798131265566301316033414311712092913492774989048057650627801991277862963173961355088082419091848569675686058581383542877982979697235829206442087786927939745804017455244315305118437
e1e2 = 3087
for e1 in range(1, (gmpy2.iroot(3087,2)[0])):
if 3087 % e1 == 0:
e2 = 3087 // e1
k, s, t = gmpy2.gcdext(e1,e2)
m = pow(flag1,s,n) * pow(flag2,t,n) %n
m = gmpy2.iroot(m, k)[0]
flag = long_to_bytes(m)
if b"NSS" in flag:
print(flag)
[NSSCTF 2022 Spring Recruit]classic
先凯撒解出前缀,NSSCTF{NBQXMZK7MFPW42LDMVPXI4TZ_fakeflagtrybase}
说try base 那么观察前半部分
可以发现没有小写字母,应该是base32
解得have_a_nice_try
于是flag
NSSCTF{have_a_nice_try}
[NISACTF 2022]normal
ook
unicode
base64
bubblebabble
rot13
NISA{u_kn0w_wH@t_!_thinK}
[BJDCTF 2020]EasyRSA
导了一些奇怪的包
第一个sympy的Derivative导数
第二个fractions 分数
然后arctan反正切
arth反双曲正切
看起来很复杂
其实z=1 / ( 1/p2 - 1) - 1 / ( 1 - 1/q2 )
即z = p2 + q2
故可以求得p,q
from Crypto.Util.number import *
import gmpy2
c = 7922547866857761459807491502654216283012776177789511549350672958101810281348402284098310147796549430689253803510994877420135537268549410652654479620858691324110367182025648788407041599943091386227543182157746202947099572389676084392706406084307657000104665696654409155006313203957292885743791715198781974205578654792123191584957665293208390453748369182333152809882312453359706147808198922916762773721726681588977103877454119043744889164529383188077499194932909643918696646876907327364751380953182517883134591810800848971719184808713694342985458103006676013451912221080252735948993692674899399826084848622145815461035
z = 32115748677623209667471622872185275070257924766015020072805267359839059393284316595882933372289732127274076434587519333300142473010344694803885168557548801202495933226215437763329280242113556524498457559562872900811602056944423967403777623306961880757613246328729616643032628964072931272085866928045973799374711846825157781056965164178505232524245809179235607571567174228822561697888645968559343608375331988097157145264357626738141646556353500994924115875748198318036296898604097000938272195903056733565880150540275369239637793975923329598716003350308259321436752579291000355560431542229699759955141152914708362494482
n = 15310745161336895413406690009324766200789179248896951942047235448901612351128459309145825547569298479821101249094161867207686537607047447968708758990950136380924747359052570549594098569970632854351825950729752563502284849263730127586382522703959893392329333760927637353052250274195821469023401443841395096410231843592101426591882573405934188675124326997277775238287928403743324297705151732524641213516306585297722190780088180705070359469719869343939106529204798285957516860774384001892777525916167743272419958572055332232056095979448155082465977781482598371994798871917514767508394730447974770329967681767625495394441
e = 65537
p_plus_q_2 = z + 2*n
p_minus_q_2 = z - 2*n
p_plus_q = gmpy2.iroot(p_plus_q_2,2)[0]
p_minus_q = gmpy2.iroot(p_minus_q_2,2)[0]
p = (p_minus_q+p_plus_q) // 2
q = n // p
phi_n = (p-1)*(q-1)
d = gmpy2.invert(e,phi_n)
print(long_to_bytes(pow(c,d,n)))
[AFCTF 2018]Vigenère
https://www.guballa.de/vigenere-solver一把梭
key: csuwangjiang
afctf{Whooooooo_U_Gotcha!}
[UTCTF 2020]basics
第一层base64
from Crypto.Util.number import *
import gmpy2
import base64
enc = open("binary.txt","rb").read().decode()
enc_l = enc.split(" ")
enc_l = ["".join(chr(int(i,2)) for i in enc_l)]
flag = base64.b64decode(enc_l[0].split("\n")[1])
print(flag.decode())
得到
New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people). kvbsqrd, iye'bo kvwycd drobo! Xyg pyb dro psxkv (kxn wkilo dro rkbnocd...) zkbd: k celcdsdedsyx mszrob. Sx dro pyvvygsxq dohd, S'fo dkuox wi wocckqo kxn bozvkmon ofobi kvzrklodsm mrkbkmdob gsdr k mybboczyxnoxmo dy k nsppoboxd mrkbkmdob - uxygx kc k celcdsdedsyx mszrob. Mkx iye psxn dro psxkv pvkq? rsxd: Go uxyg drkd dro pvkq sc qysxq dy lo yp dro pybwkd edpvkq{...} - grsmr wokxc drkd sp iye coo drkd zkddobx, iye uxyg grkd dro mybboczyxnoxmoc pyb e, d, p, v k, kxn q kbo. Iye mkx zbylklvi gybu yed dro bowksxsxq mrkbkmdobc li bozvkmsxq drow kxn sxpobbsxq mywwyx gybnc sx dro Oxqvscr vkxqekqo. Kxydrob qbokd wodryn sc dy eco pboaeoxmi kxkvicsc: go uxyg drkd 'o' crygc ez wycd ypdox sx dro kvzrklod, cy drkd'c zbylklvi dro wycd mywwyx mrkbkmdob sx dro dohd, pyvvygon li 'd', kxn cy yx. Yxmo iye uxyg k pog mrkbkmdobc, iye mkx sxpob dro bocd yp dro gybnc lkcon yx mywwyx gybnc drkd cryg ez sx dro Oxqvscr vkxqekqo. rghnxsdfysdtghu! qgf isak cthtuike dik zknthhkx rxqldgnxsliq risyykhnk. ikxk tu s cysn cgx syy qgfx isxe kccgxdu: fdcysn{h0v_di4du_vi4d_t_r4yy_rxqld0}. qgf vtyy cthe disd s ygd gc rxqldgnxsliq tu pfud zftyethn gcc ditu ugxd gc zsutr bhgvykenk, she td xksyyq tu hgd ug zse scdkx syy. iglk qgf khpgqke dik risyykhnk!
第二层Vigenère
得到
alright, you're almost there! Now for the final (and maybe the hardest...) part: a substitution cipher. In the following text, I've taken my message and replaced every alphabetic character with a correspondence to a different character - known as a substitution cipher. Can you find the final flag? hint: We know that the flag is going to be of the format utflag{...} - which means that if you see that pattern, you know what the correspondences for u, t, f, l a, and g are. You can probably work out the remaining characters by replacing them and inferring common words in the English language. Another great method is to use frequency analysis: we know that 'e' shows up most often in the alphabet, so that's probably the most common character in the text, followed by 't', and so on. Once you know a few characters, you can infer the rest of the words based on common words that show up in the English language. hwxdnitvoitjwxk! gwv yiqa sjxjkyau tya padjxxan hngbtwdnibyg hyiooaxda. yana jk i soid swn ioo gwvn yinu asswntk: vtsoid{x0l_ty4tk_ly4t_j_h4oo_hngbt0}. gwv ljoo sjxu tyit i owt ws hngbtwdnibyg jk fvkt pvjoujxd wss tyjk kwnt ws pikjh rxwloauda, ixu jt naioog jk xwt kw piu istan ioo. ywba gwv axfwgau tya hyiooaxda!
第三层单表替换,这里用词频分析
https://quipqiup.com/
得到
congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{n0w_th4ts_wh4t_i_c4ll_crypt0}. you will find that a lot of cryptography is just building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!
[BJDCTF 2020]rsa_output
两组nc
共模
from Crypto.Util.number import *
import gmpy2
n = 21058339337354287847534107544613605305015441090508924094198816691219103399526800112802416383088995253908857460266726925615826895303377801614829364034624475195859997943146305588315939130777450485196290766249612340054354622516207681542973756257677388091926549655162490873849955783768663029138647079874278240867932127196686258800146911620730706734103611833179733264096475286491988063990431085380499075005629807702406676707841324660971173253100956362528346684752959937473852630145893796056675793646430793578265418255919376323796044588559726703858429311784705245069845938316802681575653653770883615525735690306674635167111
e1 = 2767
e2 = 3659
c1 = 20152490165522401747723193966902181151098731763998057421967155300933719378216342043730801302534978403741086887969040721959533190058342762057359432663717825826365444996915469039056428416166173920958243044831404924113442512617599426876141184212121677500371236937127571802891321706587610393639446868836987170301813018218408886968263882123084155607494076330256934285171370758586535415136162861138898728910585138378884530819857478609791126971308624318454905992919405355751492789110009313138417265126117273710813843923143381276204802515910527468883224274829962479636527422350190210717694762908096944600267033351813929448599
c2 = 11298697323140988812057735324285908480504721454145796535014418738959035245600679947297874517818928181509081545027056523790022598233918011261011973196386395689371526774785582326121959186195586069851592467637819366624044133661016373360885158956955263645614345881350494012328275215821306955212788282617812686548883151066866149060363482958708364726982908798340182288702101023393839781427386537230459436512613047311585875068008210818996941460156589314135010438362447522428206884944952639826677247819066812706835773107059567082822312300721049827013660418610265189288840247186598145741724084351633508492707755206886202876227
k, s, t = gmpy2.gcdext(e1,e2)
m = pow(c1,s,n) * pow(c2,t,n) % n
m = gmpy2.iroot(m,k)[0]
print(long_to_bytes(m))
[NSSCTF 2022 Spring Recruit]Vigenere
key: bestkasscn
[LitCTF 2023]梦想是红色的 (初级)
社会主义核心价值观解码
[NISACTF 2022]sign_crypto
https://www.latexlive.com/home
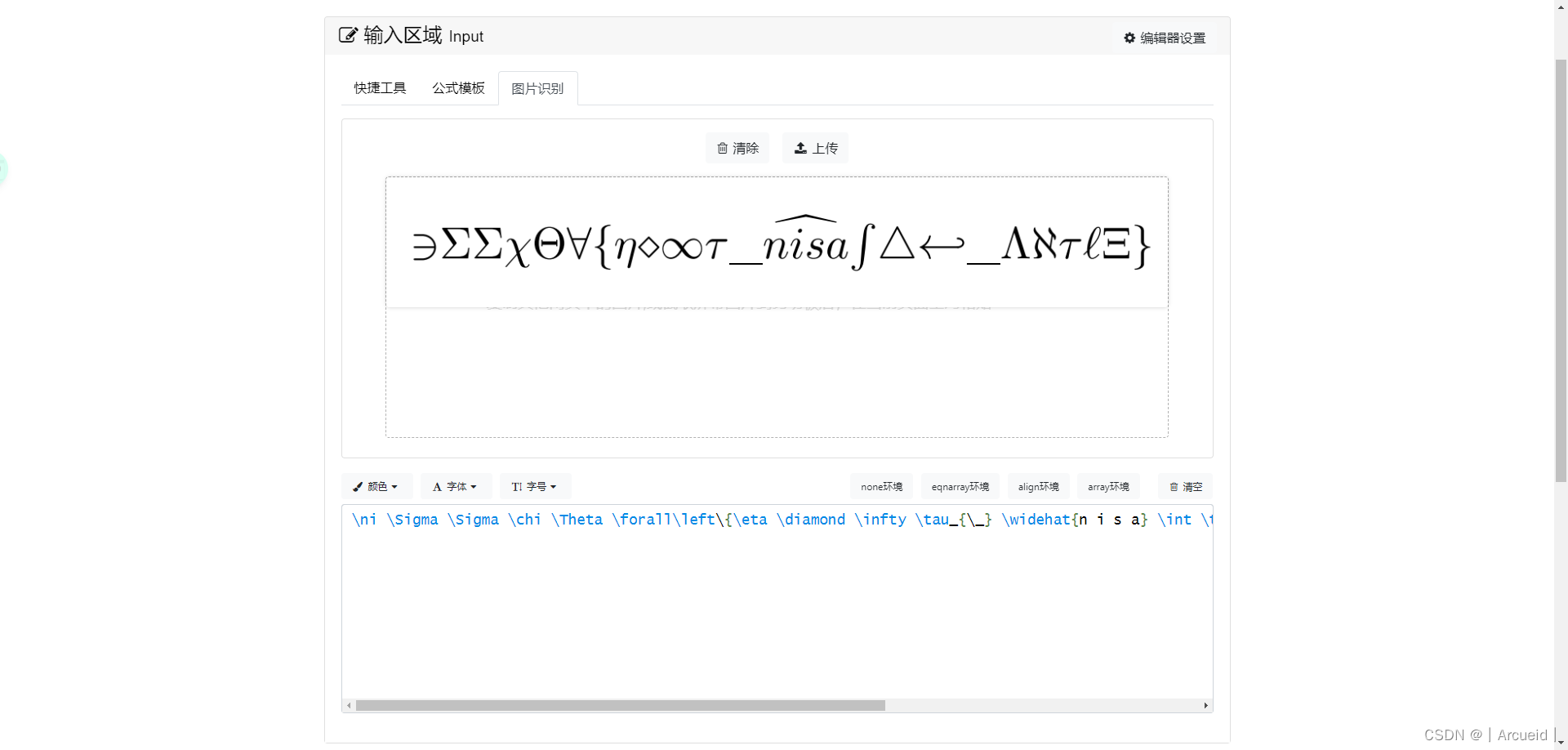
藏头
NSSCTF{EDIT_WITH_LATEX}
[WUSTCTF 2020]佛说:只能四天
新佛曰
社会主义核心价值观
rail_fence 长度为4,这里一开始用cyberchef死活出不了,才知道cyberchef是w型的,或者有不是w型的我没找到
然后凯撒 解base32
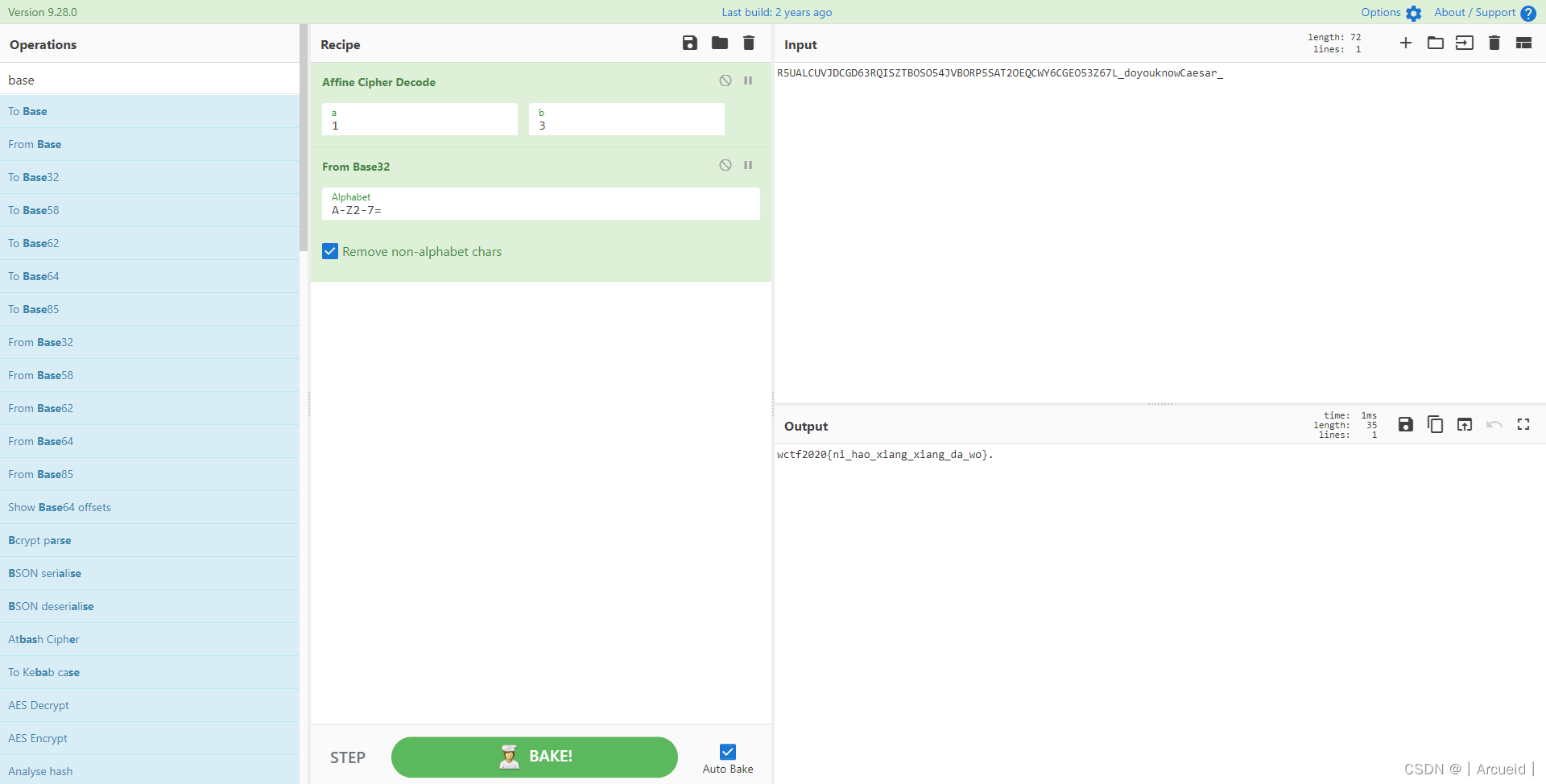
[LitCTF 2023]Hex?Hex!(初级)
long_to_bytes
[HGAME 2022 week3]RSA attack 3
from rsaAttack import rsaATTACK
import gmpy2
from Crypto.Util.number import *
n = 507419170088344932990702256911694788408493968749527614421614568612944144764889717229444020813658893362983714454159980719026366361318789415279417172858536381938870379267670180128174798344744371725609827872339512302232610590888649555446972990419313445687852636305518801236132032618350847705234643521557851434711389664130274468354405273873218264222293858509477860634889001898462547712800153111774564939279190835857445378261920532206352364005840238252284065587291779196975457288580812526597185332036342330147250312262816994625317482869849388424397437470502449815132000588425028055964432298176942124697105509057090546600330760364385753313923003549670107599757996810939165300581847068233156887269181096893089415302163770884312255957584660964506028002922164767453287973102961910781312351686488047510932997937700597992705557881172640175117476017503918294534205898046483981707558521558992058512940087192655700351675718815723840568640509355338482631416345193176708501897458649841539192993142790402734898948352382350766125000186026261167277014748183012844440603384989647664190074853086693408529737767147592432979469020671772152652865219092597717869942730499507426269170189547020660681363276871874469322437194397171763927907099922324375991793759
e = 77310199867448677782081572109343472783781135641712597643597122591443011229091533516758925238949755491395489408922437493670252550920826641442189683907973926843505436730014899918587477913032286153545247063493885982941194996251799882984145155733050069564485120660716110828110738784644223519725613280140006783618393995138076030616463398284819550627612102010214315235269945251741407899692274978642663650687157736417831290404871181902463904311095448368498432147292938825418930527188720696497596867575843476810225152659244529481480993843168383016583068747733118703000287423374094051895724494193455175131120243097065270804457787026492578916584536863548445813916819417857064037664101684455000184987531252344582899589746272173970083733130106407810619258077266603898529285634495710846838011858287024329514491058790557305041389614650730267774482954666726949886313386881066593946789460028399523245777171320319444673551268379126203862576627540177888290265714418064334752499940587750374552330008143708562065940245637685833371348603338834447212248648869514585047871442060412622164276894766238383894693759347590977926306581080390685360615407766600573527565016914830132066428454738135380178959590692145577418811677639050929791996313180297924833690095
c = 165251729917394529793163344300848992394021337429474789711805041655116845722480301677817165053253655027459227404782607373107477419083333844871948673626672704233977397989843349633720167495862807995411682262559392496273163155214888276398332204954185252030616473235814999366132031184631541209554169938146205402400412307638567132128690379079483633171535375278689326189057930259534983374296873110199636558962144635514392282351103900375366360933088605794654279480277782805401749872568584335215630740265944133347038070337891035560658434763924576508969938866566235926587685108811154229747423410476421860059769485356567301897413767088823807510568561254627099309752215808220067495561412081320541540679503218232020279947159175547517811501280846596226165148013762293861131544331444165070186672186027410082671602892508739473724143698396105392623164025712124329254933353509384748403154342322725203183050328143736631333990445537119855865348221215277608372952942702104088940952142851523651639574409075484106857403651453121036577767672430612728022444370874223001778580387635197325043524719396707713385963432915855227152371800527536048555551237729690663544828830627192867570345853910196397851763591543484023134551876591248557980182981967782409054277224
rsaATTACK.winer_attack(e,n)
p = 21298134770649658216278142296112942067147983199869944051655637057817328935819182610235462542569498569324385324409329571639600371299301899356824248143642344655442622374410310055425324677795784348676565914255070769153686678958926694461277211055311525634376131602446021339153829749451964653889079995884358945519072510825015936448152457479593557483201584178529677963719663775436340988624581240903410405998043378783910544890698820131277542597734306033931291895554315374634997718205759853380739243270624315403363705348247791948363494335781877752324962632628092187671413785054077812783546897087918010783689638260926706015913
q = 23824582553942919630850676220178643109001733415361353537841839392299606064996415886803838233068147964855219400175482264280732424187869450981451906986725084796308595805826699938124497098907397768965741168302469271928272998228311113517190888598629379930432525787072020418255919390290574878929953914018136149954421947488032931942930949955884293721160202632663062911194952115007125088928249982623306322013786936529425393146129275358939088606061079593543727354390310264157278935888913107901772969741480470747454297764934781325875916543539488214337064926875838879522936754363794195722196675211558559735431886185759667481543
d = gmpy2.invert(e,(p-1)*(q-1))
print(long_to_bytes(pow(c,d,n)))