el-table表头加红色星标
news2026/2/12 11:42:20
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。如若转载,请注明出处:http://www.coloradmin.cn/o/2207296.html
如若内容造成侵权/违法违规/事实不符,请联系多彩编程网进行投诉反馈,一经查实,立即删除!相关文章
Java idea中项目在maven执行install命令后出现Java heap space错误
Java idea中项目在maven执行install命令后出现Java heap space错误
这代表着你的maven需要足够的内存来编译和打包你的项目,而你分配的堆内存却不够用。
解决办法:
idea左上角File —> Settings Build —> Build Tools —> Maven —> Run…
【GPT提问技巧】如何高效提问GPT:掌握核心技巧,获取高质量回答的终极指南!
人工智能(AI)已经成为我们获取知识和信息的重要工具。尤其是GPT(Generative Pre-trained Transformer)等语言模型,凭借其强大的自然语言处理能力,能够为我们提供丰富的回答。然而,如何向GPT提问…
【论文分享】ShEF: Shielded Enclaves for Cloud FPGAs 22‘ASPLOS
目录 ABSTRACTINTRODUCTIONBACKGROUND AND MOTIVATIONTrusted Execution Environments (TEEs)Conventional FPGA Security MechanismsRemote FPGAs-as-a-ServiceChallenges for Secure and Customized ComputingA lack of asymmetric keys.Presence of an untrusted ShellLack …
【Vue3】 h()函数的用法
目录
介绍
参数
使用案例
1.创建虚拟 DOM 元素
2. 组件的动态渲染
3. 创建功能组件
4.渲染动态属性
5. 使用插槽
6. 创建动态标签 介绍
h() 函数用于辅助创建虚拟 DOM 节点,它是 hypescript 的简称——能生成 HTML (超文本标记语言) 的 JavaScript&#x…
开发实时美颜系统:视频美颜SDK与直播平台的集成方案详解
本文将详细介绍如何开发一个实时美颜系统,并探讨视频美颜SDK与直播平台的集成方案,帮助开发者实现流畅的美颜功能。 一、视频美颜SDK的核心功能
视频美颜SDK主要提供了一系列实时处理视频图像的算法,常见的功能包括:
1.美白、磨…
Vue3教程 - 3 HelloWorld
更好的阅读体验:点这里 ( www.foooor.com )
3 HelloWorld
下面来正式进入 Vue3 的学习。先写一个 HelloWorld。
3.1 关于Vite
Vite 是一个新型前端构建工具。
在 Vue2 中,我们主要使用 vue-cli 来构建我们的前端项目&#x…
进程的优先级详解(1)(在Linux中观察进程优先级,优先级的概念,优先级范围,进程的切换和切换的过程和理解)
文章目录 进程的优先级什么是进程的优先级?进程的优先级的划分1. 优先级的级别划分2. 动态与静态优先级 那么为什么要有优先级呢?区分 那么是怎么确定优先级的呢? Linux中的优先级Linux中的进程优先级补充 Linux优先级的范围进程的切换切换过…
四款pdf转图片在线转换免费工具推荐:
大家好!今天我来给大家推荐几款PDF转图片的在线转换工具,让你轻松将PDF文件转换成图片,无论是工作还是学习,都能派上大用场。下面,让我们来看看这几款工具吧! 一、福昕转换器
直通车(粘贴到浏览…
多线程(二):创建线程关键属性终止线程
目录
1、run & start 2、Thread类常见的属性和方法
2.1 构造方法
2.2 属性
3、后台进程 & 前台进程
4、后台线程的判断和设定——isDaemon & setDaemon
5、线程是否存活——isAlive
6、终止一个线程
6.1 lambda变量捕获
6.2 currentThread & isInterr…
atomic physics
https://www.youtube.com/watch?v6F8Wjblb0vE&listPLX2gX-ftPVXVqAS_q3OfJDmPn8-EQld_r&index18
Python 工具库每日推荐 【logging】
文章目录 引言Python日志记录的重要性今日推荐:logging模块主要功能:使用场景:快速上手基本使用代码解释实际应用案例案例:文件日志记录器案例分析高级特性日志过滤器上下文管理器扩展阅读与资源优缺点分析优点:缺点:总结【 已更新完 TypeScript 设计模式 专栏,感兴趣可…
钢管X射线 焊缝缺陷检测数据集,3408张x射线焊缝缺陷图像,也有更多的图像数据集,可以进行扩充 目标检测任务。可制作上位机软件。
钢管X射线 焊缝缺陷检测数据集,3408张x射线焊缝缺陷图像,也有更多的图像数据集,可以进行扩充 目标检测任务。可制作上位机软件。 B lowhole Undercut Broken arc Crack Overlap Slag inclusion L ack of fusion Hollow bead 钢管X射线焊缝缺陷…
正则表达式 | Python、Julia 和 Shell 语法详解
正则表达式在网页爬虫、脚本编写等众多任务中都有重要的应用。为了系统梳理其语法,以及 Python、Julia 和 Shell 中与正则表达式相关的工具,本篇将进行详细介绍。
相关学习资源:编程胶囊。
基础语法
通用语法
在大多数支持正则表达式的语…
Github 2024-10-11 Java开源项目日报 Top9
根据Github Trendings的统计,今日(2024-10-11统计)共有9个项目上榜。根据开发语言中项目的数量,汇总情况如下: 开发语言项目数量Java项目9TypeScript项目1Vue项目1C++项目1JeecgBoot 企业级低代码开发平台 创建周期:2062 天开发语言:Java, Vue协议类型:Apache License 2.…
除了Devops、DevSecOps和TestOps ,您还了解ITOps吗?
大家可能听说过Devops、DevSecOps、TestOps ,但是对于ITOps这个词儿可能会感到陌生,今天就带大家来了解一下什么事ITOps
ITOps
信息技术运营 — 通常称为 IT 运营,或是 ITOps ,是实施、管理、 交付和支持 IT 服务的过程&#x…
Odoo:免费开源的装备制造行业信息化解决方案
概述 满足装备制造行业MTO、ETO、MTS等多种业务模式,从个性化的订单选配、多层级计划管理模式、复杂的物料齐套规划、频繁的设计变更管理、精细化制造执行和用料管控、精准的售后服务等行业特性,提供一站式整体解决方案。 行业趋势洞察
个性化定制
洞察…
详细版的Jsoncpp的使用,包括在VS环境下配置
目录 准备环境VS 环境下配置编译使用 基础概述Json 数组Json 对象 Jsoncpp 的使用ValueFastWriterReader示例 如果想要 Json 部署在 Linux 上 参考: https://blog.csdn.net/2303_76953932/article/details/142703683?spm1001.2014.3001.5502 C中原生不支持 Json,所…
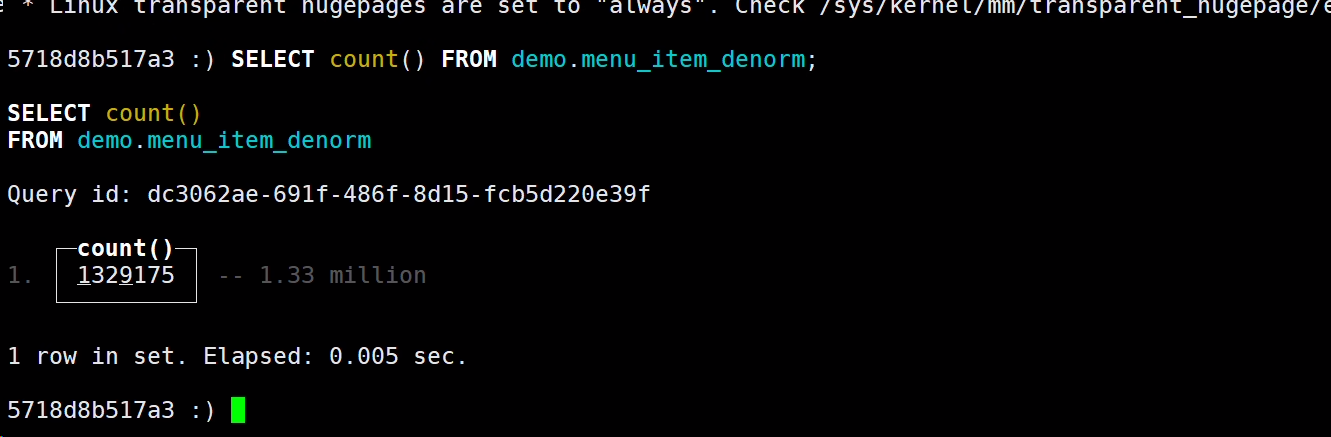
ClickHouse 数据保护指南:从备份到迁移的全流程攻略
一、背景
运行3年的clickhouse需要迁移机房,迁移单库单表的140亿条的数据。采用clickhouse-backup 的方式进行备份迁移,打包备份,再加上数据拷贝,数据恢复 一共花费30分钟。数据在一定量级,避免使用SQL 导入导出的方式…
配置 Visual studio 2022 Connector C++ 8.0环境 连接MySQL
Connector C 8.0 环境配置
1. 配置 Connector C 头文件地址
(1) 在Mysql的安装路径中找到
MySQL\Connector C 8.0\include\jdbc
例如 : C:\Program Files\MySQL\Connector C 8.0\include\jdbc (2) 打开VS2022&…