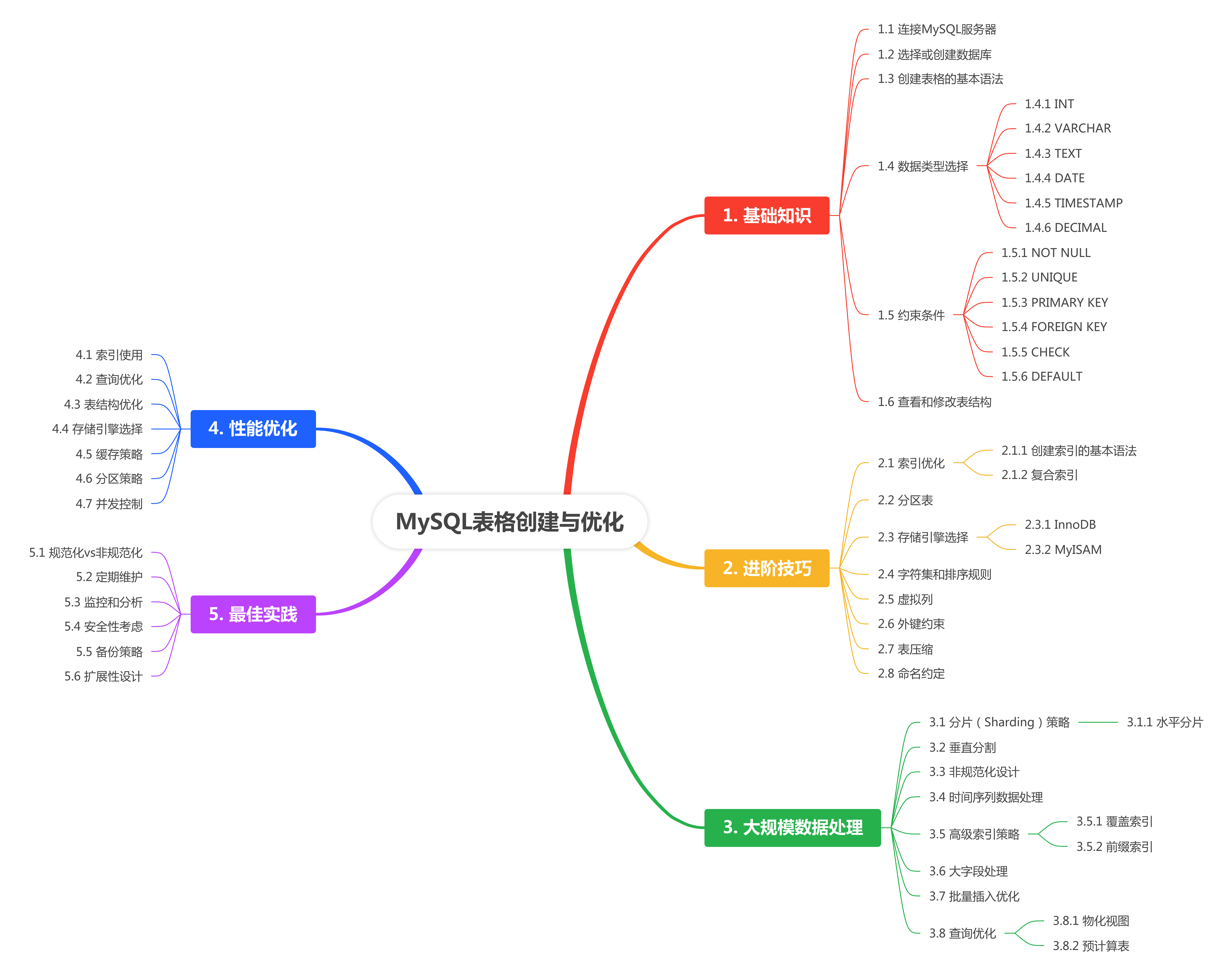
|
|
|
[年] |
在centos6下编译openssh-9.8p1的rpm包
1、创建用于rpm编译的目录
mkdir -p /root/rpmbuild/SPEC
mkdir -p /root/rpmbuild/SOURCES2、安装rpmbuild和一些其它的基本依赖
yum install gcc gcc-c++ rpm-build -y
3、上传openssh-9.8p1.tar.gz 这个源码包到centos6服务器上,并解压,解压后将SPEC文件复制到/root/rpmbuild/SPEC目录下
(源码包和askpass压缩包都在附件1里面)
将openssh-9.8的源码包和x11-ssh-askpass-1.2.4.1.tar.gz放置到 /root/rpmbuild/SOURCES 目录下
x11-ssh-askpass-1.2.4.1.tar.gz的下载地址是Index of /repo/pkgs/openssh/x11-ssh-askpass-1.2.4.1.tar.gz
以上工作做完后,试运行编译
[root@centos6666 ~]# cp openssh-9.8p1/contrib/redhat/
gnome-ssh-askpass.csh gnome-ssh-askpass.sh openssh.spec sshd.init sshd.pam
[root@centos6666 ~]# cp openssh-9.8p1/contrib/redhat/openssh.spec /root/rpmbuild/SPECS/
[root@centos6666 ~]# cd !$
cd /root/rpmbuild/SPECS/
[root@centos6666 SPECS]# rpmbuild -ba openssh.spec
warning: line 97: prereq is deprecated: PreReq: initscripts >= 5.00
error: Failed build dependencies:
/usr/include/security/pam_appl.h is needed by openssh-9.8p1-1.el6.x86_64
/usr/include/X11/Xlib.h is needed by openssh-9.8p1-1.el6.x86_64
libXt-devel is needed by openssh-9.8p1-1.el6.x86_64
imake is needed by openssh-9.8p1-1.el6.x86_64
gtk2-devel is needed by openssh-9.8p1-1.el6.x86_64
krb5-devel is needed by openssh-9.8p1-1.el6.x86_64
[root@centos6666 SPECS]# ls ../SOURCES/
openssh-9.8p1.tar.gz x11-ssh-askpass-1.2.4.1.tar.gz可以看到还是缺少很多依赖,安装以上缺少的依赖
4、安装缺少的依赖
yum install krb5-devel gtk2-devel imake libXt-devel pam pam-devel -y5、再次执行编译
这次基本就完成了rpm包的编译,非常快
Requires(rpmlib): rpmlib(CompressedFileNames) <= 3.0.4-1 rpmlib(FileDigests) <= 4.6.0-1 rpmlib(PayloadFilesHavePrefix) <= 4.0-1
Requires: libICE.so.6()(64bit) libSM.so.6()(64bit) libX11.so.6()(64bit) libXt.so.6()(64bit) libc.so.6()(64bit) libc.so.6(GLIBC_2.2.5)(64bit) libc.so.6(GLIBC_2.3)(64bit) libc.so.6(GLIBC_2.3.4)(64bit) libc.so.6(GLIBC_2.4)(64bit) rtld(GNU_HASH)
Obsoletes: ssh-extras
Processing files: openssh-askpass-gnome-9.8p1-1.el6.x86_64
Provides: config(openssh-askpass-gnome) = 9.8p1-1.el6
Requires(rpmlib): rpmlib(CompressedFileNames) <= 3.0.4-1 rpmlib(FileDigests) <= 4.6.0-1 rpmlib(PayloadFilesHavePrefix) <= 4.0-1
Requires: libX11.so.6()(64bit) libatk-1.0.so.0()(64bit) libc.so.6()(64bit) libc.so.6(GLIBC_2.2.5)(64bit) libc.so.6(GLIBC_2.3.4)(64bit) libcairo.so.2()(64bit) libfontconfig.so.1()(64bit) libfreetype.so.6()(64bit) libgdk-x11-2.0.so.0()(64bit) libgdk_pixbuf-2.0.so.0()(64bit) libgio-2.0.so.0()(64bit) libglib-2.0.so.0()(64bit) libgmodule-2.0.so.0()(64bit) libgobject-2.0.so.0()(64bit) libgthread-2.0.so.0()(64bit) libgtk-x11-2.0.so.0()(64bit) libpango-1.0.so.0()(64bit) libpangocairo-1.0.so.0()(64bit) libpangoft2-1.0.so.0()(64bit) libpthread.so.0()(64bit) librt.so.1()(64bit) rtld(GNU_HASH)
Obsoletes: ssh-extras
Processing files: openssh-debuginfo-9.8p1-1.el6.x86_64
Checking for unpackaged file(s): /usr/lib/rpm/check-files /root/rpmbuild/BUILDROOT/openssh-9.8p1-1.el6.x86_64
warning: Could not canonicalize hostname: centos6666
Wrote: /root/rpmbuild/SRPMS/openssh-9.8p1-1.el6.src.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-9.8p1-1.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-clients-9.8p1-1.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-server-9.8p1-1.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-askpass-9.8p1-1.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-askpass-gnome-9.8p1-1.el6.x86_64.rpm
Wrote: /root/rpmbuild/RPMS/x86_64/openssh-debuginfo-9.8p1-1.el6.x86_64.rpm
Executing(%clean): /bin/sh -e /var/tmp/rpm-tmp.8n4pMP
+ umask 022
+ cd /root/rpmbuild/BUILD
+ cd openssh-9.8p1
+ rm -rf /root/rpmbuild/BUILDROOT/openssh-9.8p1-1.el6.x86_64
+ exit 0
编译产出物是在/root/rpmbuild/RPMS/x86_64目录(由于我是使用的x86架构机器编译的,因此是该目录)和SRPMS目录下
root@centos6666 SPECS]# ls -alh ../RPMS/x86_64/
total 5.6M
drwxr-xr-x 2 root root 4.0K Jul 27 20:56 .
drwxr-xr-x 3 root root 4.0K Jul 27 20:56 ..
-rw-r--r-- 1 root root 541K Jul 27 20:56 openssh-9.8p1-1.el6.x86_64.rpm
-rw-r--r-- 1 root root 42K Jul 27 20:56 openssh-askpass-9.8p1-1.el6.x86_64.rpm
-rw-r--r-- 1 root root 25K Jul 27 20:56 openssh-askpass-gnome-9.8p1-1.el6.x86_64.rpm
-rw-r--r-- 1 root root 728K Jul 27 20:56 openssh-clients-9.8p1-1.el6.x86_64.rpm
-rw-r--r-- 1 root root 3.6M Jul 27 20:56 openssh-debuginfo-9.8p1-1.el6.x86_64.rpm
-rw-r--r-- 1 root root 660K Jul 27 20:56 openssh-server-9.8p1-1.el6.x86_64.rpm
[root@centos6666 SPECS]# ls -alh ../SRPMS/
total 1.9M
drwxr-xr-x 2 root root 4.0K Jul 27 20:56 .
drwxr-xr-x 8 root root 4.0K Jul 26 22:27 ..
-rw-r--r-- 1 root root 1.9M Jul 27 20:56 openssh-9.8p1-1.el6.src.rpm
下面是如何安全的在centos6操作系统下升级OpenSSH服务到最新版9.8p1
openssh服务升级到最新版本OpenSSH-9.8p1完全手册
升级步骤
必看的重要提示:
1、
建议启用telnet服务,给自己留一个后门,如果实在懒得安装,对本次sshd服务的升级比较有把握,在升级OpenSSH期间,必须保留一个可用的shell 窗口
2、
务必按照本文档的操作顺序执行升级步骤,遇到服务异常的问题,冷静对待;在升级OpenSSH完成后,按本文档的测试建议进行充分的测试,确认升级无误后在关闭shell窗口
3、
经常性的查看OpenSSH的服务状态,也就是service sshd status 及时发现升级中出现的问题,并按标准的流程解决所出现的问题,尽量使用yum的方式安装包括
4、
附件1是OpenSSH的源码安装包和强依赖askpass,也包含有ssh-copy-id 这个简单的脚本程序
附件2是 升级安装包,包含新旧两个版本的OpenSSH,还有telnet-server安装包和lrzsz文件传输工具以及详细的word形式的升级手册
附件3是OpenSSH的一个通用的配置文件,该配置文件开放的端口定义是10022,是一个比较通用的sshd服务主配置文件,建议统一使用这个配置文件
5、
请注意本文内的标红字段
第一个步骤---注入本地仓库
安装用得压缩包(也就是附件2)上传到服务器后,执行下面的命令,生成仓库,注意,压缩包要上传到root用户的根目录下
解压缩命令:
| tar xf openssh-9.8p1-centos6.tar.gz |
解压完毕后,执行以下命令,注入本地仓库
| cat >/etc/yum.repos.d/local.repo<<EOF [ssh] name=ssh baseurl=file:///root/openssh-9.8p1-centos6 enable=1 gpgcheck=0 EOF |
第二个步骤:
确认sshd版本,是否需要升级,也就是查看sshd的版本,命令如下:
| sshd -V |
一般输出如下,sshd的版本是5.3,或者其它的确定需要升级的版本:

第三个步骤---防止升级失败的首要措施(强烈建议执行,不要投机取巧):
启用telnet服务
yum install telnet-server –y
输出如下:

安装完毕后,执行以下命令,给予telnet登陆权限:
| echo pts/0>>/etc/securetty echo pts/1>>/etc/securetty echo pts/2>>/etc/securetty echo pts/3>>/etc/securetty echo pts/4>>/etc/securetty |
编辑/etc/xinetd.d/telnet,disable = yes ,yes修改为no 保存文件即可,最终如下图所示:

启动telnet服务,服务端口号是23,使用xshell等工具测试利用telnet能够成功登陆即可
telnet启动命令:
| service xinetd start |
Xshell等工具登陆示例:

第四个步骤---备份
主要是sshd服务的配置文件,如果升级OpenSSH彻底失败,需要利用此备份文件完全回退
命令如下:
| cp -r /etc/ssh{,.bak} |
第五个步骤---正式升级OpenSSH
- 执行以下命令升级安装OpenSSH-9.8p1
#使用本地仓库[1] yum install openssh-server-9.8p1 openssh-9.8p1 openssh-clients-9.8p1 -y 输出如下:
#安装lrzsz方便传输文件,安装pam-devel,以提供更多功能 yum install pam-devel lrzsz -y #不使用本地仓库,直接本地安装[2] cd openssh-9.8p1-centos6 yum localinstall openssh-9.8p1-1.el7.x86_64.rpm openssh-debuginfo-9.8p1-1.el7.x86_64.rpm openssh-clients-9.8p1-1.el7.x86_64.rpm openssh-server-9.8p1-1.el7.x86_64.rpm 这种方式不推荐,就不截图演示了
chmod 0600 /etc/ssh/ssh_host_ed25519_key chmod 0600 /etc/ssh/ssh_host_rsa_key
由于通用配置文件内容较多,请直接查看附件4,这里就不重复了
service ssdh restart
cp ssh-copy-id /usr/bin/ && chmod a+x /usr/bin/ssh-copy-id |
如果升级sshd服务彻底失败后的回退方案[7]
for i in `rpm -qa |grep openssh`;do rpm -e $i --nodeps ;done 2)安装旧版本的OpenSSH 两种安装方式任意选择一种即可,不用考虑原来的OpenSSH是哪个版本 ###安装旧版的OpenSSH方式 这种方式是使用本地仓库,执行下面的安装命令即可: yum install openssh-clients-5.3p1 openssh-server-5.3p1 openssh-5.3p1 –y 3)配置文件恢复: \cp –f /etc/ssh.bak/sshd_config /etc/ssh/ 4) 重启OpenSSH服务 service sshd restart |
检查确认是否升级成功
- 查看sshd的版本号
| sshd –V 正确的输出日志如下:
#如果和上面的日志不一致,请检查服务是否正常升级安装 |
- 重启sshd服务,查看服务状态是否有报错:
| service sshd restart && service sshd status 一般输出如下:,第一个红色可以忽略不管,只需要关心服务是否正常启动
|
sshd服务的自启动说明
,
在centos6 版本下,sshd服务是由chkconfig控制自启的,因此,自启命令为(正常情况为无输出):
| chkconfig --add sshd chkconfig sshd on |
测试sshd功能是否正常[i]
-
-
- 使用ssh命令远程连接一个服务器,看是否可以正常连接到,这是测试ssh客户端功能
- 利用xshell等运维工具,打开一个新的远程连接窗口,确认可正常登陆,这是测试ssh服务端功能
- 使用ssh-copy-id命令配置一次免密登陆,确认该工具是否正常
- 使用scp 命令传送任意的测试文件,确认sshd功能完整正常
-
清理升级过程的垃圾文件并关闭telnet服务
在确认sshd服务升级安装成功后
- 删除以上用到的仓库文件,仓库文件在/etc/yum.repos.d目录下
- 删除openssh-9.8p1-centos6.tar.gz 这个安装包
- 删除/root/ openssh-9.8p1-centos6这个目录
- 停止telnet服务,命令为service xinetd stop
输出如下:
![]()
一些常见的错误的处理流程
*(这些是centos7下升级sshd时的报错,目前在centos6,升级sshd还没有遇到任何错误,以后遇到了在记录,这些仅供参考)
- 第一种sshd服务状态错误情况(在cetos6还没遇到错误,这个是cetos7的,以后遇到了在补充):
如果有遇到sshd服务状态(systemctl status sshd命令)里带有Permissions字样的报错,例如下面这样的:
| [root@pg2 aarch64]# systemctl status sshd ● sshd.service - SYSV: OpenSSH server daemon Loaded: loaded (/etc/rc.d/init.d/sshd; bad; vendor preset: enabled) Active: active (running) since Thu 2024-07-11 12:58:12 CST; 10s ago Docs: man:systemd-sysv-generator(8) Process: 30984 ExecStop=/etc/rc.d/init.d/sshd stop (code=exited, status=0/SUCCESS) Process: 31113 ExecStart=/etc/rc.d/init.d/sshd start (code=exited, status=0/SUCCESS) Main PID: 31121 (sshd) CGroup: /system.slice/sshd.service └─31121 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups Jul 11 12:58:12 pg2 sshd[31113]: @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ Jul 11 12:58:12 pg2 sshd[31113]: Permissions 0640 for '/etc/ssh/ssh_host_ecdsa_key' are too open. Jul 11 12:58:12 pg2 sshd[31113]: It is required that your private key files are NOT accessible by others. Jul 11 12:58:12 pg2 sshd[31113]: This private key will be ignored. Jul 11 12:58:12 pg2 sshd[31113]: Unable to load host key "/etc/ssh/ssh_host_ecdsa_key": bad permissions Jul 11 12:58:12 pg2 sshd[31113]: Unable to load host key: /etc/ssh/ssh_host_ecdsa_key Jul 11 12:58:12 pg2 sshd[31121]: Server listening on 0.0.0.0 port 10022. Jul 11 12:58:12 pg2 sshd[31113]: [ OK ] Jul 11 12:58:12 pg2 sshd[31121]: Server listening on :: port 10022. |
提示有哪些报错的文件赋权,赋权后重启sshd服务,示例如下:
| chmod 0600 /etc/ssh/ssh_host_ecdsa_key systemctl restart sshd |
- 第二种sshd服务状态错误的情况:
如果sshd服务状态(systemctl status sshd命令)内有format字样,需要回退到低版本7.4p,回退步骤见上面的回退方案,然后重新生成sshd服务的证书文件,一般是四个
| [root@pg1 aarch64]# chmod -Rf 0600 /etc/ssh/ [root@pg1 aarch64]# systemctl restart sshd [root@pg1 aarch64]# systemctl status sshd ● sshd.service - SYSV: OpenSSH server daemon Loaded: loaded (/etc/rc.d/init.d/sshd; bad; vendor preset: enabled) Active: active (running) since Thu 2024-07-11 14:14:39 CST; 11s ago Docs: man:systemd-sysv-generator(8) Process: 65356 ExecStart=/etc/rc.d/init.d/sshd start (code=exited, status=0/SUCCESS) Main PID: 65364 (sshd) CGroup: /system.slice/sshd.service └─65364 sshd: /usr/sbin/sshd [listener] 0 of 10-100 startups Jul 11 14:14:39 pg1 systemd[1]: Starting SYSV: OpenSSH server daemon... Jul 11 14:14:39 pg1 sshd[65356]: Starting sshd:Unable to load host key "/etc/ssh/ssh_host_rsa_key": invalid format Jul 11 14:14:39 pg1 sshd[65356]: Unable to load host key: /etc/ssh/ssh_host_rsa_key Jul 11 14:14:39 pg1 sshd[65356]: Unable to load host key "/etc/ssh/ssh_host_ecdsa_key": invalid format Jul 11 14:14:39 pg1 sshd[65356]: Unable to load host key: /etc/ssh/ssh_host_ecdsa_key Jul 11 14:14:39 pg1 sshd[65364]: Server listening on 0.0.0.0 port 10022. Jul 11 14:14:39 pg1 sshd[65364]: Server listening on :: port 10022. Jul 11 14:14:39 pg1 sshd[65356]: [ OK ] Jul 11 14:14:39 pg1 systemd[1]: Started SYSV: OpenSSH server daemon. |
命令如下:
| ssh-keygen -t rsa -f /etc/ssh/ssh_host_rsa_key ssh-keygen -t ecdsa -f /etc/ssh/ssh_host_ecdsa_key ssh-keygen -t ecdsa -f /etc/ssh/ssh_host_ecdsa_key ssh-keygen -t ed25519 -f /etc/ssh/ssh_host_ed25519_key |
以上命令都需要先手动输入y,表示同意覆盖,然后回车直到命令结束
证书文件生成后,在利用for循环命令删除低版本sshd,然后再次升级sshd就可以正常升级完成了,如果懒得修改配置文件,直接使用附件4命令即可,建议还是重复上面的正式升级步骤
附件1:OpenSSH-9.8p1的源码安装包和askpass
链接: https://pan.baidu.com/s/1V08KtiDrm8aH_St60KMFPw?pwd=xju7 提取码: xju7
附件2:OpenSSH-9.8p1的本地仓库文件和OpenSSH-9.8p1的升级手册
链接: https://pan.baidu.com/s/1xf1ujEIEe2TqQbsfU5t4IA?pwd=5ny2 提取码: 5ny2 
附件3:
通用的sshd主配置文件:
| cat >/etc/ssh/sshd_config<<EOF # $OpenBSD: sshd_config,v 1.103 2018/04/09 20:41:22 tj Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin:/usr/local/openssh/bin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options override the # default value. #Port 22 Port 10022 #AddressFamily any #ListenAddress 0.0.0.0 #ListenAddress :: #HostKey /usr/local/openssh/etc/ssh_host_rsa_key #HostKey /usr/local/openssh/etc/ssh_host_ecdsa_key #HostKey /usr/local/openssh/etc/ssh_host_ed25519_key # Ciphers and keying #RekeyLimit default none # Logging #SyslogFacility AUTH #LogLevel INFO # Authentication: #LoginGraceTime 2m #PermitRootLogin yes #StrictModes yes #MaxAuthTries 6 #MaxSessions 10 #PubkeyAuthentication yes # The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2 # but this is overridden so installations will only check .ssh/authorized_keys AuthorizedKeysFile .ssh/authorized_keys #AuthorizedPrincipalsFile none #AuthorizedKeysCommand none #AuthorizedKeysCommandUser nobody # For this to work you will also need host keys in /usr/local/openssh/etc/ssh_known_hosts #HostbasedAuthentication no # Change to yes if you don't trust ~/.ssh/known_hosts for # HostbasedAuthentication #IgnoreUserKnownHosts no # Don't read the user's ~/.rhosts and ~/.shosts files #IgnoreRhosts yes # To disable tunneled clear text passwords, change to no here! #PasswordAuthentication yes #PermitEmptyPasswords no # Change to no to disable s/key passwords #ChallengeResponseAuthentication yes # Kerberos options #KerberosAuthentication no #KerberosOrLocalPasswd yes #KerberosTicketCleanup yes #KerberosGetAFSToken no # GSSAPI options #GSSAPIAuthentication no #GSSAPICleanupCredentials yes # Set this to 'yes' to enable PAM authentication, account processing, # and session processing. If this is enabled, PAM authentication will # be allowed through the ChallengeResponseAuthentication and # PasswordAuthentication. Depending on your PAM configuration, # PAM authentication via ChallengeResponseAuthentication may bypass # the setting of "PermitRootLogin without-password". # If you just want the PAM account and session checks to run without # PAM authentication, then enable this but set PasswordAuthentication # and ChallengeResponseAuthentication to 'no'. #UsePAM no #AllowAgentForwarding yes #AllowTcpForwarding yes #GatewayPorts no #X11Forwarding no #X11DisplayOffset 10 #X11UseLocalhost yes #PermitTTY yes #PrintMotd yes #PrintLastLog yes #TCPKeepAlive yes #PermitUserEnvironment no #Compression delayed #ClientAliveInterval 0 #ClientAliveCountMax 3 #UseDNS no #PidFile /var/run/sshd.pid #MaxStartups 10:30:100 #PermitTunnel no #ChrootDirectory none #VersionAddendum none # no default banner path #Banner none # override default of no subsystems Subsystem sftp /usr/libexec/openssh/sftp-server # Example of overriding settings on a per-user basis #Match User anoncvs # X11Forwarding no # AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server PermitRootLogin yes PubkeyAuthentication yes EOF |
[1] #安装方式可以使用本地仓库,也可以直接本地安装,不通过仓库,两种安装方式,任选一个就可以了,建议优先使用yum install这个命令,此方式会自动卸载旧的OpenSSH,可以避免一些不必要的麻烦
[2] #安装方式可以使用本地仓库,也可以直接本地安装,不通过仓库,两种安装方式,任选一个就可以了,建议优先使用yum install这个命令,此方式会自动卸载旧的OpenSSH,可以避免一些不必要的麻烦
[3] 权限不能太高,因此是0600,如果发现sshd服务状态有报错的情况下
[4] ###使用附件4,通用的OpenSSH服务配置文件,复制附件4,在shell内执行即可,可自动注入覆盖 OpenSSH的配置文件
[5] ###重新启动sshd服务,并查看sshd服务状态,如果sshd服务一切正常的话
[6] ###缺失的ssh-copy-id命令拷贝到操作系统的环境变量内
[7] 回退方案说明:如果新OpenSSH-9.8p1升级后,发现服务有异常并且在短期内无法解决的错误,例如,sshd服务异常断开,此时可以利用telnet-server 服务远程登陆服务器并按下面的步骤执行回退
[i] 建议测试的时候不要遗漏,sshd服务是重要的服务,不能容忍升级失败