前言
Evil-winrm 工具最初是由 Hackplayers 团队开发的。开发该工具的目的是尽可能简化渗透测试,尤其是在 Microsoft Windows 环境中。 Evil-winrm 使用 PowerShell 远程协议 (PSRP),且系统和网络管理员经常使用Windows Remote Management 协议进行上传和管理。 WinRM 是一种基于对防火墙友好的SOAP 协议,可通过 HTTP默认 端口 5985 与 HTTP 传输一起使用。有关 PowerShell 远程处理的更多信息,请参考访问 Microsoft 的官方网站。
Enable-PSRemoting (Microsoft.PowerShell.Core) - PowerShell | Microsoft Learn This cmdlet is only available on the Windows platform. The Enable-PSRemoting cmdlet configures the computer to receive PowerShell remote commands that are sent by using the WS-Management technology. WS-Management based PowerShell remoting is currently supported only on Windows platform. PowerShell remoting is enabled by default on Windows Server platforms. You can use Enable-PSRemoting to enable PowerShell remoting on other supported versions of Windows and to re-enable remoting if it becomes disabled. You have to run this command only one time on each computer that will receive commands. You do not have to run it on computers that only send commands. Because the configuration starts listeners to accept remote connections, it is prudent to run it only where it is needed. Enabling PowerShell remoting on client versions of Windows when the computer is on a public network is normally disallowed, but you can skip this restriction by using the SkipNetworkProfileCheck parameter. For more information, see the description of the SkipNetworkProfileCheck parameter. Multiple PowerShell installations can exist side-by-side on a single computer. Running Enable-PSRemoting will configure a remoting endpoint for the specific installation version that you are running the cmdlet in. So if you run Enable-PSRemoting while running PowerShell 6.2, a remoting endpoint will be configured that runs PowerShell 6.2. If you run Enable-PSRemoting while running PowerShell 7-preview, a remoting endpoint will be configured that runs PowerShell 7-preview. Enable-PSRemoting creates two remoting endpoint configurations as needed. If the endpoint configurations already exist, then they are simply ensured to be enabled. The created configurations are identical but have different names. One will have a simple name corresponding to the PowerShell version that hosts the session. The other configuration name contains more detailed information about the PowerShell version which hosts the session. For example, when running Enable-PSRemoting in PowerShell 6.2, you will get two configured endpoints named PowerShell.6, PowerShell.6.2.2. This allows you to create a connection to the latest PowerShell 6 host version by using the simple name PowerShell.6. Or you can connect to a specific PowerShell host version by using the longer name PowerShell.6.2.2. To use the newly enabled remoting endpoints, you must specify them by name with the ConfigurationName parameter when creating a remote connection using the Invoke-Command,New-PSSession,Enter-PSSession cmdlets. For more information, see Example 4. The Enable-PSRemoting cmdlet performs the following operations: Runs the Set-WSManQuickConfig cmdlet, which performs the following tasks: Starts the WinRM service. Sets the startup type on the WinRM service to Automatic. Creates a listener to accept requests on any IP address. Enables a firewall exception for WS-Management communications. Creates the simple and long name session endpoint configurations if needed. Enables all session configurations. Changes the security descriptor of all session configurations to allow remote access. Restarts the WinRM service to make the preceding changes effective. To run this cmdlet on the Windows platform, start PowerShell by using the Run as administrator option. This cmdlet is not available on Linux or MacOS versions of PowerShell. Caution This cmdlet does not affect remote endpoint configurations created by Windows PowerShell. It only affects endpoints created with PowerShell version 6 and greater. To enable and disable PowerShell remoting endpoints that are hosted by Windows PowerShell, run the Enable-PSRemoting cmdlet from within a Windows PowerShell session. ![]() https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/enable-psremoting?view=powershell-7.3
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/enable-psremoting?view=powershell-7.3
Evil-winrm介绍
Evil-winrm 是一款使用ruby 语言开发的开源工具。 该工具具有许多很酷的功能,包括使用纯文本密码远程登录、SSL 加密登录、 NTLM 哈希登录、密钥登录、文件传输、日志存储等功能。该开发工具的作者不断更新工具并长期维护更新。 使用 evil-winrm,我们可以获得远程主机的 PowerShell命令终端会话。
GitHub下载链接: https: //github.com/Hackplayers/evil-winrm![]() https://github.com/Hackplayers/evil-winrm
https://github.com/Hackplayers/evil-winrm
Evil-winrm的使用
如果在远程主机中启用了 Winrm 服务,则会联想到使用 evil-winrm 工具。 为了确认目标系统是否开启了winrm服务,我们可以使用 nmap 查找两个默认的 winrm 服务端口 5895 和 5896 是否打开。 从 nmap 扫描结果中,我们发现 winrm 服务已启用,因此我们可以使用 evil-winrm 工具进行登录并执行我们将在横向阶段探索的其他任务。
nmap -p 5895 5896 10.129.253.226
发现服务端口存在,连接测试。
参数汇总
┌──(kali㉿kali)-[~/Desktop]
└─$ evil-winrm -h
Evil-WinRM shell v3.5
Usage: evil-winrm -i IP -u USER [-s SCRIPTS_PATH] [-e EXES_PATH] [-P PORT] [-p PASS] [-H HASH] [-U URL] [-S] [-c PUBLIC_KEY_PATH ] [-k PRIVATE_KEY_PATH ] [-r REALM] [--spn SPN_PREFIX] [-l]
-S, --ssl Enable ssl
-c, --pub-key PUBLIC_KEY_PATH Local path to public key certificate
-k, --priv-key PRIVATE_KEY_PATH Local path to private key certificate
-r, --realm DOMAIN Kerberos auth, it has to be set also in /etc/krb5.conf file using this format -> CONTOSO.COM = { kdc = fooserver.contoso.com }
-s, --scripts PS_SCRIPTS_PATH Powershell scripts local path
--spn SPN_PREFIX SPN prefix for Kerberos auth (default HTTP)
-e, --executables EXES_PATH C# executables local path
-i, --ip IP Remote host IP or hostname. FQDN for Kerberos auth (required)
-U, --url URL Remote url endpoint (default /wsman)
-u, --user USER Username (required if not using kerberos)
-p, --password PASS Password
-H, --hash HASH NTHash
-P, --port PORT Remote host port (default 5985)
-V, --version Show version
-n, --no-colors Disable colors
-N, --no-rpath-completion Disable remote path completion
-l, --log Log the WinRM session
-h, --help Display this help message
使用参数-u -p 指定用户名和密码。-i参数指定远程访问的主机。
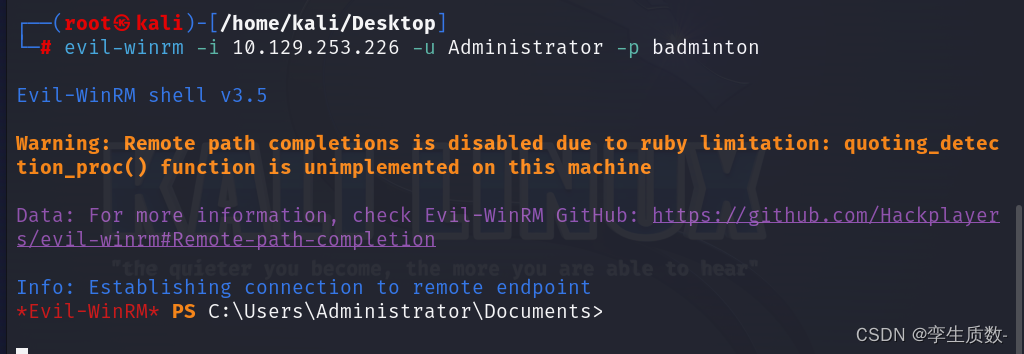
evil-winrm -i 10.129.253.226 -u Administrator -p badminton使用纯文本密码登录,成功连接。
还有启用ssl连接等等的连接方式,参考:
本文参考:红队神器-Evil-Winrm详细使用指南 - 渗透测试中心 - 博客园 (cnblogs.com)![]() https://www.cnblogs.com/backlion/p/17202253.html
https://www.cnblogs.com/backlion/p/17202253.html