Android Studio avd 设置
证书生成
*.cer格式证书
openssl x509 -inform DER -subject\_hash\_old -in charles-ssl-proxying-certificate.cer
*.pem格式证书
openssl x509 -inform PEM -subject\_hash\_old -in charles-ssl-proxying-certificate.pem
会输出 `2cb30a9e` ,证书修改成 `2cb30a9e`.0系统证书
adb push 2cb30a9e.0 /sdcard/
或者
adb push 2cb30a9e.0 /data/local/tmp/
证书脚本
charles.sh
set -e # Fail on error
mkdir -m 700 /data/local/tmp/htk-ca-copy
# Copy out the existing certificates
cp /system/etc/security/cacerts/* /data/local/tmp/htk-ca-copy/
# Create the in-memory mount on top of the system certs folder
mount -t tmpfs tmpfs /system/etc/security/cacerts
# Copy the existing certs back into the tmpfs mount, so we keep trusting them
mv /data/local/tmp/htk-ca-copy/* /system/etc/security/cacerts/
# Copy our new cert in, so we trust that too
cp /data/local/tmp/2cb30a9e.0 /system/etc/security/cacerts/
# Update the perms & selinux context labels, so everything is as readable as before
chown root:root /system/etc/security/cacerts/*
chmod 644 /system/etc/security/cacerts/*
chcon u:object_r:system_file:s0 /system/etc/security/cacerts/*
# Delete the temp cert directory & this script itself
rm -r /data/local/tmp/htk-ca-copy
# rm ${injectionScriptPath}
echo "System cert successfully injected"
推送到模拟器和执行
# 推送到服务器
adb push charles.sh /data/local/tmp/
# 给权限
adb shell chmod +x /data/local/tmp/charles.sh
#本地执行
adb shell sh /data/local/tmp/charles.sh
#模拟器执行
xz:~ $ adb shell
emulator_arm64:/ $ su
emulator_arm64:/ # cd /data/local/tmp/
emulator_arm64:/data/local/tmp # ./charles.sh
System cert successfully injected
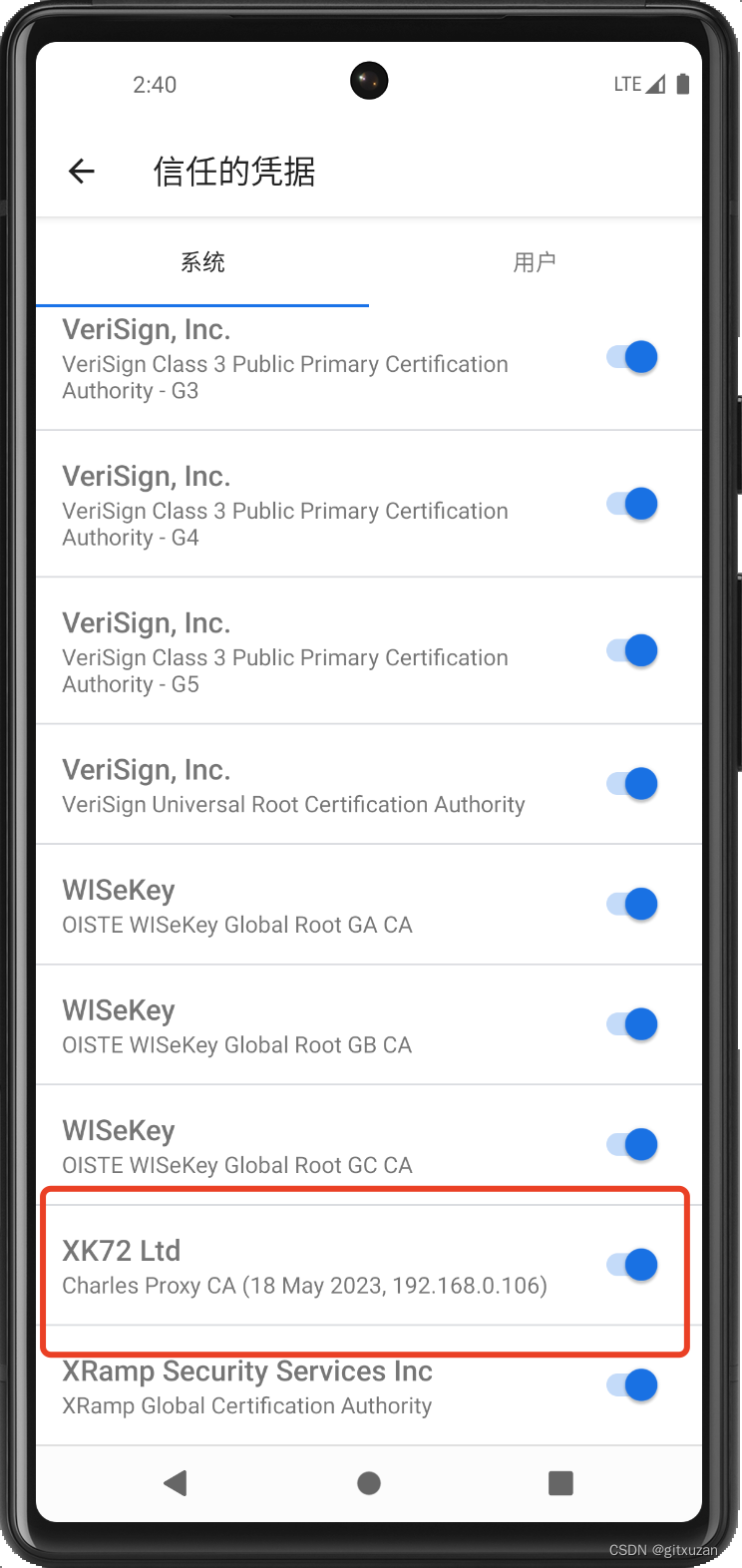
执行完成后可以在手机系统信任证书里面查看到,必须是在系统里面这一栏,用户这一栏高版本安卓系统的证书已经抓取不到https了